
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event
Processing Systems
Majid Lotfian Delouee
1 a
, Victoria Degeler
2 b
, Peter Amthor
3 c
and Boris Koldehofe
3 d
1
Bernoulli Institute, University of Groningen, Groningen, Netherlands
2
Informatics Institute, University of Amsterdam, Amsterdam, Netherlands
3
Department of Computer Science and Automation, Technische Universit
¨
at Ilmenau, Ilmenau, Germany
fi
Keywords:
Distributed Complex Event Processing, Stream Processing, Privacy, Pattern, Adaptation.
Abstract:
Although privacy-preserving mechanisms endeavor to safeguard sensitive information at the attribute level,
detected event patterns can still disclose privacy-sensitive knowledge in distributed complex event processing
systems (DCEP). Events might not be inherently sensitive, but their aggregation into a pattern could still breach
privacy. In this paper, we study in the context of APP-CEP the problem of integrating pattern-level privacy in
event-based systems by selective assignment of obfuscation techniques to conceal private information. Com-
pared to state-of-the-art techniques, we seek to enforce privacy independent of the actual events in streams.
To support this, we acquire queries and privacy requirements using CEP-like patterns. The protection of pri-
vacy is accomplished through generating pattern dependency graphs, leading to dynamically appointing those
techniques that have no consequences on detecting other sensitive patterns, as well as non-sensitive patterns
required to provide acceptable Quality of Service. Besides, we model the knowledge that might be possessed
by potential adversaries to violate privacy and its impacts on the obfuscation procedure. We assessed the
performance of APP-CEP in a real-world scenario involving an online retailer’s transactions. Our evaluation
results demonstrate that APP-CEP successfully provides a privacy-utility trade-off. Modeling the background
knowledge also effectively prevents adversaries from realizing the modifications in the input streams.
1 INTRODUCTION
Interpreting the individual’s data to generate insight-
ful information has attracted interest in various ap-
plication fields such as e-commerce, public health-
care, and the Internet of Things (IoT). Such appli-
cations typically involve distributed, timely process-
ing of data for preventive or predictive use, with con-
straints ranging from mere least-latency up to real-
time requirements (Lotfian Delouee et al., 2022).
One of the state-of-the-art paradigms for analyzing
data in a distributed manner in real-time is Dis-
tributed Complex Event Processing (DCEP): Streams
of simple events (e.g., IoT raw data) are analyzed
and transformed into complex events representing
situations of interest (e.g., queries over sensor data
streams). This transformation is performed using a
a
https://orcid.org/0000-0003-1326-7540
b
https://orcid.org/0000-0001-7054-3770
c
https://orcid.org/0000-0001-7711-4450
d
https://orcid.org/0000-0002-1588-2056
set of processing logic called CEP rules (Lotfian De-
louee et al., 2023a). For example, a traffic moni-
toring system can infer a road congestion via sim-
ple events: Average Vehicles Speed < 20 km/h and
Vehicles Density > Normal Density.
A key challenge in the analysis of such informa-
tion is privacy. It leads to a conflict of goals: On
the one hand, users of a DCEP system should be
provided an optimal Quality of Service (QoS). As
an example from the e-commerce domain, product
managers should be able to detect and reason about
varying sales. On the other hand, disclosing specific
events (e.g., purchase details) might violate the pri-
vacy of data owners (e.g., customers of a webshop)
(Lotfian Delouee et al., 2023b). Similar examples
can be found for medical data of hospital patients
or health insurance clients (Palanisamy et al., 2018).
They share an honest-but-curious type of adversary,
represented by users as well as nodes of a distributed
CEP middleware.
Hence, DCEP requires Privacy Preserving Mech-
anisms (PPM) to protect the privacy of data owners.
486
Lotfian Delouee, M., Degeler, V., Amthor, P. and Koldehofe, B.
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event Processing Systems.
DOI: 10.5220/0012358700003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 486-497
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

Despite most PPMs (e.g., access control) operating on
the level of single events (i.e., by protecting event at-
tributes), privacy requirements are often represented
by a combination of events through complex event
patterns. A pattern is the CEP representation of a
complex event with a set of one or more operations
over simple events (e.g., filtering special events) to
detect a situation. For instance, a sequence pattern
equals the occurrence of specific events in a prede-
fined order over single or joint streams, such as a pur-
chase of a pregnancy test followed by children’s toys.
Those privacy-sensitive patterns that data owners
want to conceal are called private patterns. Con-
versely, public patterns are non-privacy-sensitive pat-
terns that must be detected accurately and timely to
deliver the promised services, e.g., query results. Re-
garding the accuracy of complex event detection, fail-
ing to detect a complex event that occurred in the real
world (i.e., False Negative, FN) and false detection of
events that did not actually happen (i.e., False Posi-
tive, FP) are the main QoS metrics by which the per-
formance of a DCEP system can be evaluated.
In this work, we demonstrate that a feasible trade-
off between concealing private patterns and detecting
public patterns cannot be comprehensively provided
by a single, statically applied PPM. To this end, our
approach is based on a dynamic assignment of differ-
ent obfuscation techniques (OT) to optimize the fol-
lowing constraints.
First, complex event patterns share causal depen-
dencies. This forbids a na
¨
ıve solution based on just
one OT, e.g., event reordering, which fails in case the
reordered event stream cannot allow for any meaning-
ful public pattern detection. Second, an adversary’s
background knowledge must be taken into account
when choosing an OT. For example, for any event
e
1
dropped in the result of one query, but not of an-
other, an adversary could possibly infer parts of the
original stream based on the combined knowledge of
both. Third, DCEP systems are by nature dynamic:
Public and private patterns can be dynamic due to
changes in active queries or the data owners’ privacy
requirements. Input stream sources might vary spon-
taneously. Finally, an adversary’s background knowl-
edge monotonically increases over time.
In this paper, we present APP-CEP as a solution
to these challenges. Our contributions are as follows:
1. A PPM that obtains privacy requirements and sit-
uations of interest in the form of event patterns as
input and specifies the most efficient OT to con-
ceal each private pattern when delivering the re-
sults to the queries.
2. OT selection in our proposed PPM based on a
graph structure, used to model pattern dependen-
cies and extract the input stream’s features to pre-
dict the switching time between OTs to avoid pri-
vacy violations and meet scalability requirements.
3. A structure for data owners to dynamically model
the adversary’s potential background knowledge
based on an event dependency set and possible
statistical event-related information gathered from
the available event streams’ history.
4. Performance evaluation based on a real-world
dataset to show the ability of APP-CEP to boost
the performance of the DCEP systems in real-
world scenarios.
The remainder of this paper is structured as fol-
lows. We further detail the problem, particularly
for an online shop scenario, and motivate the need
for pattern-level privacy in DCEP systems in Sec-
tion 2. We introduce an overview of the APP-CEP
system model in Section 3. We formalize the prob-
lem statement in Section 4. Section 5 presents the de-
tailed overview of APP-CEP. The evaluation results
of APP-CEP are exhibited in Section 6. The related
work is presented in Section 7. Finally, Section 8 con-
cludes our paper and points to our future work.
2 CASE STUDY: WEBSHOP
In a recent project by the National Statistical Insti-
tute of Norway (Gundersen, 2022), several grocery
chains have been ordered to share all their receipt data
with this statistics agency. To protect privacy, this in-
stitute claims that by performing pseudonymization,
the account number, which can identify a person, will
be changed to another unique number (i.e., attribute-
level access control). However, pattern-level corre-
lation plus background knowledge would enable the
adversaries to realize customers’ identities, violating
their privacy.
In this section, we introduce a scenario based on
the transaction set of an online retailer that demon-
strates the application of APP-CEP in real-world sit-
uations similar to the mentioned Norwegian example
(see Figure 1). In such a scenario, a state-of-the-art
PPM fails to provide an acceptable level of privacy
protection since they mainly protect at the level of
events (e.g., by controlling the access using event at-
tributes obfuscation). We consider all transactions of
a retailer selling all-occasion gifts as the input stream
and attempt to detect predefined public and private
patterns. Any user (e.g., webshop’s manager) can is-
sue a query to detect situations of interest (e.g., top-
selling products in a particular period) that are active
for a specific time. On the other hand, data owners are
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event Processing Systems
487

Transac�on Set
Webshop
Manager
Customers
…
…
Figure 1: Webshop Scenario. The system aims to pro-
tect customers’ privacy while answering webshop manager
queries.
customers of the webshop, and each of their purchases
triggers an event in this scenario (i.e., using their cus-
tomer ID) and is labeled with a timestamp. Lining
up the purchase records according to their timestamp
generates a transaction set event stream, which is an-
alyzed to detect valuable real-time correlations.
By employing APP-CEP, a customer can specify
the privacy requirements, e.g., concealing a Christ-
mas party. In this scenario, we assume the sensitive
information can be represented by CEP patterns (e.g.,
sequence, conjunction, negation, etc.). For instance,
a Christmas party can be represented by CONJ (In-
vitation Card, Christmas Ribbon, Christmas Deco-
rations). To conceal such sensitive information, the
chosen obfuscation technique (e.g., drop event for In-
vitation Cards) might influence the results of non-
sensitive queries (e.g., top-selling products). More-
over, various parameters (e.g., pattern dependencies,
event distribution in the input stream, etc.) should be
considered carefully. Hence, the goal of APP-CEP is
to answer user queries intelligently in such a way that
the privacy of customers is not violated.
3 SYSTEM MODEL
This section presents the components of APP-CEP,
the model of event sources, and obfuscation models.
3.1 APP-CEP Model
We consider a typical DCEP system with multiple
producers (e.g., IoT sensors) that advertise the simple
event streams they can provide. Each of these streams
is related to one or more Data Owners (DO), meaning
the provided data belongs to this data owner(s) from a
privacy protection point of view. For example, the lo-
cation event stream of a car belongs to its driver. Cor-
respondingly, consumers (e.g., applications, services,
etc.) submit their situations of interest as continuous
queries to the system. Hence, the set Q = {q
1
, ..., q
n
}
denotes the set of running queries that must be re-
sponded to by processing the events of current input
streams. In addition, a set of brokers (e.g., CEP en-
gines) perform event processing tasks (e.g., drop, re-
order, union, tamper, etc.) by hosting corresponding
operators and delivering the resulting stream(s) to the
next step.
A query q
i
determines the logic to detect complex
events by applying standard CEP operators over sim-
ple events’ attributes (e.g., pattern matching). To this
end, each detection logic needs to be hosted by a spe-
cific operator to be executed. Moreover, each data
owner is able to describe its privacy requirements and
deliver them to the system. Such requirements should
be accompanied by a normalized weight that shows
their importance. Hence, the set
PR(DO
i
) = {(pr
1
, w
pr
1
), ..., (pr
m
, w
pr
m
)}
shows the privacy requirements specified by data
owner DO
i
along with their corresponding weights.
As another query feature, the importance of queries
might vary due to their priorities. That is why detect-
ing such query patterns is of more significance to the
system instead of concealing privacy requirements,
e.g., life-related queries in a healthcare scenario.
3.2 Event Source Model
Producers, also called event sources, are the ori-
gin of the events that generate simple event streams.
As an example, if we implement our mechanism in
an IoT scenario, the sensors that measure a specific
phenomenon (e.g., location of a target) act as event
sources. Regarding the number of targets that can be
covered, we categorized the event sources into two
groups: DO-Specific and Multi-DO. For the former,
the event source can only be used for queries related
to the corresponding data owner. In other words, the
generated stream will not reveal privacy-sensitive in-
formation about other targets (i.e., data owner). For
instance, a cellphone’s GPS signal can only be used
for tracking a specific target. For the latter, informa-
tion about multiple targets can be acquired by analyz-
ing such event source streams. For instance, a sta-
tionary security camera delivers data related to vari-
ous targets. These event sources should be used cau-
tiously in any privacy-aware data analysis approaches.
In addition, the event sources here are intercon-
nected to the system over a wireless network and must
be registered in the system due to privacy concerns.
Besides, each data owner can act as a CEP consumer
by submitting queries. CEP operators can also be
hosted in nodes with sufficient computing capabili-
ties, e.g., on the cloud or fog node in an IoT scenario.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
488

3.3 Obfuscation Model
An obfuscation technique is a real-time modification
in the order, occurrences, or values of event attributes
that results in concealing sensitive information (i.e.,
private patterns). Such a modification can be applied
to event streams, executed prior to the CEP middle-
ware. More importantly, the obfuscation technique
should be placed on the earliest available, trustworthy
resources to the producers, preventing inconsistencies
in the delivered streams. Among common obfusca-
tion techniques, we consider a PPM is able to hire the
following techniques:
• Suppression. Removing the occurrence of events
by dropping them from the event stream, e.g., re-
moving the event HomePage Visit
c
1
to conceal
page navigation behavior of customer c
1
.
• Reordering. Changing the order of two events
by swapping their timestamps, e.g., changing the
occurrence time of an event Buy
c
1
i
with the event
Buy
c
1
j
to conceal the order of purchases for a spe-
cific customer c
1
.
• Injection. Introducing fake events and inserting
them in unique places in the stream, e.g., inject-
ing the event Buy
c
1
j
multiple times to conceal a
specific interest to item i. It shows the person c
1
interested in both items, i.e., i and j.
• Tampering. Changing attributes of an event
to a wrong value or noise injection in event
timestamps, e.g., changing the value of item
type i in Add To Basket
c
1
i
to j which produces
Add To Basket
c
1
j
in order to conceal unhealthily
shopping habit of a diabetic customer from an in-
surance company.
• Generalization. Anonymizing the event’s at-
tributes by changing to a general value, e.g., gen-
eralizing an event Buy
c
2
apple
to Buy
c
2
f ruit
to conceal
a customer’s shopping interests.
• Hybrid. A combination of thereof, e.g., sup-
pression of event Buy
c
2
medicine
and injecting event
Buy
c
2
drink
to conceal a customer’s decease.
4 PROBLEM STATEMENT
Consider as inputs of a stream processing system sets
of public and private patterns. Basically, a PPM re-
quires checking the actual events in the input stream
to compare and assign OTs on the fly (i.e., by limiting
the stream dimension using windowing) (Palanisamy,
2020). Therefore, adaptive decisions for maintaining
the privacy-QoS trade-off should be performed at run-
time by exchanging between the best possible PPMs.
Such run-time changes are also referred to as tran-
sitions (Alt et al., 2019). Performing transitions be-
tween PPMs requires careful treatment regarding the
required time and resources. Moreover, transitions
can impose gaps during which PPM cannot meet the
privacy requirements (i.e., periods with no applied ob-
fuscation). Also, it will lead to an oscillation between
obfuscation techniques that will worsen by scaling up
the pattern sets since it will drastically increase the
number of switches. Consequently, finding a solution
to predict transition points is necessary to minimize
the overhead and prevent oscillation.
Moreover, the adversary’s background knowledge
level is determined in such systems in the initial stage.
However, an Omnipresent adversary can increase its
knowledge by issuing more and more queries and try-
ing to correlate the generated results. This indicates
another weakness of current approaches that do not
consider this dynamicity. In addition, it again ap-
proves the idea of adaptive assignment of OT models
to private patterns since new knowledge obtained by
adversaries should be taken into account in the assign-
ment procedure. So, a comprehensive PPM should
also provide enough means for dynamic modeling of
the adversary’s background knowledge.
Therefore, the main problem this paper solves is
obtaining data owners’ privacy requirements in run-
time in the form of patterns and trying to conceal
them in a way that leads to maximizing the Quality
of Service (QoS) (i.e., utility) while considering po-
tential adversary’s knowledge. Here, the comparison
metric is calculated based on the number of truly de-
tected matches of public patterns (i.e., T P
PUB
) and
False Positives (FP) in detecting public patterns (i.e.,
FP
PUB
). In addition, regarding private patterns, the
number of truly obfuscated matches of private pat-
terns (i.e., T O
PRIV
) and wrongly created new pri-
vate patterns after applying obfuscation models (i.e.,
FR
PRIV
) are being involved. Finally, the last consid-
ered metric is the number of matches for private pat-
terns that can be derived using the adversary’s back-
ground knowledge.
Each of these event types (e.g., TP) has its own
group weight (e.g., W
T P
). The rationale behind these
coefficients is in some applications, the importance
of true detection of a phenomenon is not equal to the
wrong extra detection or vice versa. The same can
be defined as concealing a private pattern over gen-
erating not true new private patterns. For example,
in a healthcare scenario, vital situations of patients
(i.e., public patterns) must be detected regardless of
the individual’s privacy protection (i.e., private pat-
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event Processing Systems
489
terns). Besides, the significance of private patterns
within their set is not equal (i.e., pattern priority). To
consider this fact, we define a unique weight for each
pattern (e.g., w
to
). The same also applies to public
patterns (e.g., w
t p
).
According to the mentioned event groups, a
Privacy-Utility Trade-off (PUT) function is formu-
lated as an optimization problem to make the perfor-
mance of each OT model comparable. We extend the
objective function formulation in (Palanisamy, 2020)
i) to deal with the dynamicity of matched private and
public patterns, ii) and quantify the adversary’s back-
ground knowledge.
More formally, the resulting formula is:
Max
(
W
T P
∑
t p∈T P
PUB
w
t p
−
W
FP
∑
f p∈FP
PUB
w
f p
+
W
TO
∑
to∈T O
PRIV
w
to
−
W
FR
∑
f r∈FR
PRIV
w
f r
−
W
Adv
∑
p∈PRIV
w
p
)
This objective function generally can be used in
any application context. In other words, the last part
is calculated by estimating the number of already ob-
fuscated private pattern matches, which can be re-
vealed based on the adversary’s background knowl-
edge. However, if such a piece of knowledge is not
available enough, the last part of this objective func-
tion can be skipped to make a fair comparison.
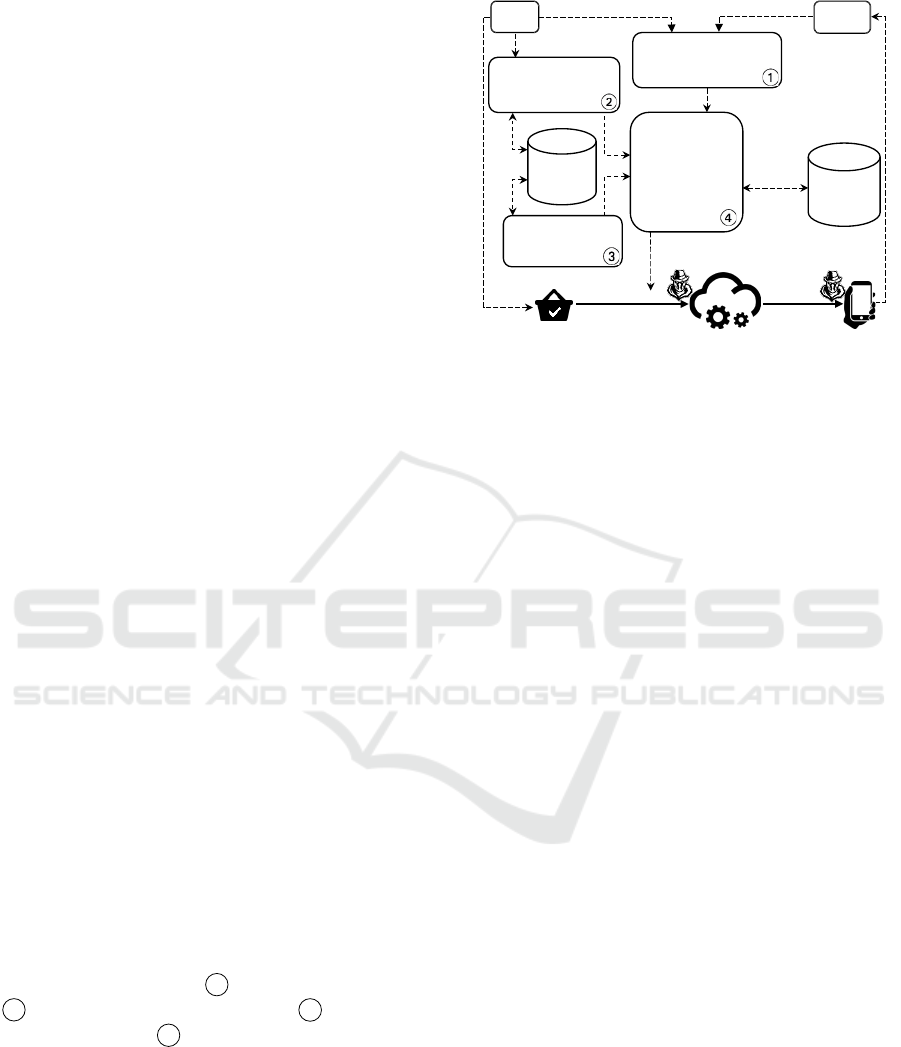
5 THE APP-CEP DESIGN
In Figure 2, we illustrate the main functionalities of
APP-CEP. Parts of our system are built on existing
concepts for converting the privacy requirements and
situations of interest in natural language to a CEP-
like pattern representation (Stach and Steimle, 2019).
Therefore, we assume that data owners and users are
able to feed the system with public and private pat-
terns. The main goal of APP-CEP is to gather re-
lated information about 1 patterns’ dependencies,
2 event dependency set, as well as 3 input stream
features to opt for 4 obfuscation techniques which
satisfy PUT, even without knowledge about the actual
events in the input streams and adapt the selection
based on the obfuscation results in execution time.
This section will further elaborate on the functionality
of these four components of APP-CEP.
Here, there are two dynamic databases, namely
stream database and OT database, which assist
APP-CEP in the obfuscation procedure by providing
up-to-date information. In the former, all previous
OT Deployment
OT
Adaptation
OT
Database
Pattern
Dependency
Graph Generator
DO
Private Patterns
Public Patterns
User
Stream Feature
Extractor
Event
Dependency
Extractor
Stream
Database
Obfuscation
Technique
Assigner
DCEP
Middleware
Consumer
Results
Input stream
Producer
Figure 2: The APP-CEP Proposed System Design. The
solid lines indicate the data/event flow, while the dashed in-
dicates the control flow.
events are collected (e.g., the transaction history of
the webshop) for further analysis, such as extracting
event dependencies and stream features. In the lat-
ter, all available models of applying obfuscation tech-
niques (e.g., dropping the first event is a private pat-
tern) are gathered to support performance analysis of
deployed obfuscation technique and make adaptation
decisions. Moreover, we presume a data owner has
sufficient skills to support APP-CEP by dynamically
providing event dependencies to facilitate the obfus-
cation procedure in the execution time. For example,
a webshop customer can provide information about
his preferred pick-up point for purchases that will be
delivered in the working days since such information
should be considered while obfuscating the patterns
in location tracking applications.
In preliminary approaches on multiple pattern-
type privacy protection (Palanisamy, 2020) , a PPM is
only able to calculate a utility value by inspecting the
actual events in the input streams. Therefore, assign-
ing the best obfuscation technique for each private
pattern is achievable by comparing the utility values.
However, a significant disadvantage of such strategies
is the complexity of designing a low-overhead adapta-
tion procedure to maintain the privacy protection per-
formance at an acceptable level concerning the sys-
tem’s dynamics, e.g., changing data owners’ privacy
requirements . To appropriately respond to dynamics,
a greedy idea would be to switch between obfusca-
tion techniques whenever a model with a higher util-
ity value is provided by the corresponding component
(i.e., Obfuscation Technique Assigner). The main pit-
falls with this approach are, firstly, time and resource
overhead for transitions and, secondly, oscillation be-
tween obfuscation techniques that downgrade the ob-
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
490

pu
3
pu
1
pr
2
pu
2
pr
3
pr
1
Figure 3: The global pattern dependency graph represents
the impacts of obfuscating each private pattern on related
public/private patterns.
fuscation performance.
To overcome the mentioned challenges, one could
realize that relying only on the actual events that ap-
pear in the input streams causes transition overheads
and oscillation issues. In other words, if a PPM is
able to predict the obfuscation techniques’ transition
time, the data/operator migration can be performed
ahead of time in order to minimize inefficiency in both
time and resource utilization. Such prediction can be
achieved by realizing the correlation between patterns
as well as events. Moreover, extracting input stream
features will enable a PPM to prevent unnecessary
obfuscation transitions, leading to performance effi-
ciency. For example, the number of pattern matches
can roughly be estimated by extracting the event dis-
tribution in each event stream. This will prevent os-
cillation in obfuscation assignment, which might be
produced by transition from dropping to reordering
and quickly returning to dropping.
Nevertheless, generating more up-to-date insights
about patterns and also events helps APP-CEP to
wisely adapt the system to maximize the overall per-
formance of the obfuscation procedure.
5.1 Pattern Dependency Graph
Predicting the obfuscation transition time is possible
by determining the potential dependencies between
private and public patterns. To be more precise, con-
sider the following public and private patterns.
PUBLIC = { {pu
1
| Buy
p
i
CD
→ Return
p
i
CD
′
},
{pu
2
| Buy
∗
BC
→ Buy
∗
BC
→ Buy
∗
BC
},
{pu
3
| Buy
p
i
AD
|| Buy
p
i
FJ
} }
PRIVAT E = { {pr
1
| Buy
p
1
IC
|| Buy
p
1
CR
|| Buy
p
1
CD
},
{pr
2
| Buy
p
1
IC
|| Buy
p
1
BC
},
{pr
3
| Buy
p
1
AD
→ Buy
p
1
DM
} }
These sample pattern sets indicate the following event
correlations:
PlP-CEP
15
pu
pu
pu
pr
Reorder (e
1
,e
2
)
pu
pu
pr
pu
pr
pr
Suppression (e
2
)
pu
pu
pr
pu
pr
pr
Suppression (e
1
)
pu
pu
pu
pr
Tamper (e
3
)
Figure 4: The alternative pattern dependency sub-graphs
represent the obfuscation impacts based on enforcing a spe-
cific obfuscation technique.
• pu
1
. A causal relationship between buying and re-
turning two types of Christmas decorations (CD)
with the same customer ID, which shows the cus-
tomers’ interests.
• pu
2
. Multiple purchases of the same product (i.e.,
birthday candle (BC)) by different customers,
which helps recommendation systems.
• pu
3
. The concurrent ordering of alcoholic drinks
(AD) and fruit juice (FJ) with the same customer
ID, which detects customers’ drinking interests.
• pr
1
. Simultaneous purchasing of invitation cards
(IC), Christmas ribbons (CR), and Christmas dec-
orations, which reveals a Christmas party.
• pr
2
. The concurrent purchase of invitation cards
and birthday candles, which reveals a birthday
party.
• pr
3
. A causal ordering dependency of alcoholic
drinks and diabetic medicine (DM) reveals a bad
lifestyle for a diabetic person.
The respective pattern dependency graph for the
mentioned patterns is depicted in Figure 3. Here, the
submitted privacy requirements belonging to an indi-
vidual customer (i.e., p
1
) have been used to define
private patterns. Besides, queries represented as pub-
lic patterns are generally defined, not for a specific
customer ID. Signs (→) and (||) indicate the causal
dependency in a sequence pattern and parallel occur-
rence of events in a conjunction pattern, respectively.
To construct a pattern dependency graph, we as-
sume that nodes of the graph are patterns, and for
each private pattern, outgoing edges are one-way ar-
rows from this private pattern to all dependent pub-
lic/private patterns. A pattern is called the neighbor
of private pattern pr if an edge exists going from pr to
this specific node. For instance, if we plan to obfus-
cate private pattern pr
1
, suppression of event Buy
p
1
IC
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event Processing Systems
491

helps to obfuscate private pattern pr
1
(positive im-
pact). However, suppression of the event Buy
p
1
CD
will
result in false negatives in the detection of public pat-
tern pu
1
(negative impact).
The graph representation of pattern dependencies
supports deriving insights that can be helpful in OT
model selection. For example, the outgoing edges of
each node indicate the detection of how many patterns
will be influenced. In a particular case, disconnected
nodes (i.e., nodes with no neighbor) do not have any
relationship with other nodes. Hence, the obfuscation
selection is much easier and even static in such cases
until their connectivity changes in the updated pattern
dependency graph. Any available obfuscation tech-
nique can be chosen in such situations since they all
support the PUT goal.
On the other side, if a private pattern has one
or more outgoing edges in the global dependency
graph, an alternative solution would be to break down
the global dependency graph into obfuscation-specific
sub-graphs (e.g., suppression(e
1
) graph, which drops
the first event of all matches). This way, APP-CEP
can find a sub-graph in which this specific node has
no neighbors. Figure 4 shows the generated graphs
of four different obfuscation techniques as examples
of sub-graphs. Here, nodes pr
1
and pr
3
are discon-
nected nodes in the Suppression(e
2
), and pr
2
has no
neighbors in the Suppression(e
1
). Therefore, these
OT models are potential candidates for correspond-
ing private patterns. Note that Reorder(e
1
, e
2
) is not
among available OT models for pr
1
and pr
3
because
the conjunction operator is used in the definition of
those patterns between the first and second events,
and such obfuscation technique is not able to conceal
these patterns. Similarly, Tamper(e
3
) is not applicable
for patterns of length 2, e.g., pr
2
and pr
3
.
5.2 Event Dependencies
Modeling the adversaries’ background knowledge is
a complicated task that has yet to be well-studied in
this field. Some research works have been conducted
to statistically predict special privacy attacks to model
the adversary (Palanisamy, 2020). For example, an
adversary might infer several event types’ true mean
inter-arrival time from stream history. Then, he can
realize enforced pattern obfuscation by computing
statistical metrics like the suppression probability of
this event type and try reconstructing the original in-
put stream. However, the potential data owners’ infor-
mation is not exploited to complement the final adver-
sary model.
To this end, APP-CEP supports the runtime ex-
pression of event dependencies. This facilitates mod-
eling the possible information that an adversary might
use to derive insights related to data owners. For in-
stance, the regular shopping habits of a customer, e.g.,
buying two products always together, give a hint to the
system not to drop one while publishing the other. In
more detail, four types of event dependencies can be
introduced to be considered in the obfuscation assign-
ment phase.
5.2.1 Causal Dependency (→)
In this category, a relationship between two events
can be specified in two ways: firstly, one event is the
reason for occurrences of the other (i.e., cause and
effect), and secondly, one event always happens be-
fore the other. For example, in our use-case scenario,
a causal dependency can be derived from history as:
CD (Submit Order
c
1
i
, Payment Success f ul
c
1
i
)
which means the event of submitting an order is the
cause, and the successful payment event is the ef-
fect. Also, a customer c
1
might express that he always
checks the available balance before adding a product
p to the shopping basket. Therefore, the customer c
1
can provide a causal dependency to the system as:
CD (Check Balance
c
1
, Add To Basket
c
1
i
)
In these cases, APP-CEP considers the depen-
dency, e.g., does not suppress the cause event and
keeps the effect event or reorders these two events.
5.2.2 Parallel Occurrence ( || )
Special events (two or more) happen always, or at
least with a high probability, simultaneously or in a
short period. This means an intelligent obfuscation
assignment should consider them as a single com-
bined event, e.g., reorder all events instead of one. As
an example in the proposed webshop scenario, a cus-
tomer c
1
might express that he always buys products
p and q together. This leads to a parallel occurrence
of the corresponding two events, represented as:
PO (Add To Basket
c
1
p
, Add To Basket
c
1
q
).
5.2.3 Infeasible Events (↛)
Another type of event relationship also shows the
impossible occurrences of one or several events or
patterns. For instance, when a customer c
1
is nav-
igated to the bank payment page as a result of the
Submit Order event with id i, it is not possible
to observe two events of Payment Success f ul and
Payment Re jected afterward for this special order
submission in the stream, that can be expressed by:
IE [CD (Submit Order
c
1
i
, Payment Success f ul
c
1
i
),
CD (Submit Order
c
1
i
, Payment Re jected
c
1
i
)]
Such dependencies usually cannot be expressed
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
492

by a data owner, but require help from domain experts
in the application scenario.
5.2.4 Periodic Events (
¯
X)
Apart from dependencies between events, this type of
information shows insights can be derived as a result
of statistical calculation over a specific event type for
a unique data owner. We assume that the adversary
has the required computing resources and access to
the data history to correlate the statistical dependen-
cies for a particular data owner. For example, a cus-
tomer c
1
might have a shopping habit of buying a spe-
cial product p each day. Hence, such a habit can be
expressed by:
PE (Buy
c
1
p
, day )
Therefore, applying any obfuscation technique re-
lated to dropping or altering such events (e.g., sup-
pression, tampering, generalization, etc.) will lead to
violating the privacy of data owner by revealing the
stream modification on the adversary side, whereas
obfuscation techniques like reordering still might be
applicable in such situations.
5.3 Stream Features
Even if we know the privacy requirements of data
owners and the dependencies between patterns and
events, the input streams also bring up another dy-
namicity that should be considered. In more detail,
the number of matches for a pattern determines an-
other vital dimension. For example, a Christmas party
is more likely to be revealed during Christmas. There-
fore, obfuscating a private pattern that increases the
reveal of any Christmas party at another time of the
year (e.g., in July) would be acceptable because the
detection probability of such a party is very low in
other periods.
Hence, extracting input stream features helps a
PPM to assign the OT model more efficiently. To
do so, APP-CEP investigates the stream database and
analyzes the input streams online to adapt the fea-
tures. As mentioned earlier, one significant feature
of streams is the average number of matches for each
pattern. For instance, the number of matches for a
Christmas party pattern is calculated weekly, which
helps dynamically assign weight to this private pat-
tern in the PUT function.
Apart from patterns, event-related stream features
bring up the benefits, causing a more brilliant OT
model selection. For instance, the event distribution
helps estimate a more accurate weight for each sup-
pression model of a private pattern (He et al., 2011).
If the event e on a private pattern pr has a higher
frequency in history, suppression of e tends to create
Algorithm 1: Obfuscation Technique Assignment.
1: Initialization:
P U , P R ← ∅;
D ← Event Dependencies;
O ← Obfuscation Techniques;
2: upon (Submit(Q
i
)) do
3: P U ← P U ∪ CEP-Pattern(Q
i
); ▷ Query
4: OT Assigner (P U, PR , D);
5: upon (Submit(Pr
i
)) do
6: P R ← P R ∪ CEP-Pattern(Pr
i
); ▷ Priv Req
7: OT Assigner (P U, PR , D);
8: upon (Submit(d
i
)) do
9: D ← D ∪ d
i
; ▷ Event Dependency
10: OT Assigner (P U, PR , D);
11: function OT ASSIGNER(P U, P R , D)
12: G ← Pattern Dependency Graphs;
13: F ← Input Stream Features;
14: for pr ∈ P R do
15: O
pr
← O;
16: for ot ∈ O do
17: if ot violates D|F then
18: O
pr
← O
pr
− ot ;
19: OT
pr
← ∅;
20: for ot ∈ O
pr
do
21: if OutDeg
pr
g
ot
= 0 then
22: OT
pr
← OT
pr
∪ ot;
23: if O T
pr
̸= ∅ then
24: α
pr
← O T
pr
1
;
25: else
26: α
pr
← Random(O
pr
);
27: α ← {(pr
1
, α
pr
1
), ..., (pr
n
, α
pr
n
)}; ▷ Solution
more FN in detecting neighbors of pr which contain e.
Such an idea can also be extended to subsets of each
private pattern instead of a single event by checking
its distribution for other types of obfuscation (e.g., a
two-event subset for reordering).
5.4 Obfuscation Technique Assignment
In connection with the OT database, the obfuscation
technique assigner module, which is the core com-
ponent of APP-CEP, acts as the system’s brain. It
aggregates the information collected from the other
three modules (i.e., 1 pattern dependency graph gen-
erator, 2 event dependency extractor, and 3 stream
feature extractor) to decide which OT model should
be chosen regardless of the current input streams for
each private pattern.
In Algorithm 1, the sets of public and private pat-
terns are initialized, and the event dependencies de-
rived from streams’ history alongside the available
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event Processing Systems
493
obfuscation operators are delivered as inputs (line
1). Upon receiving new public or private patterns,
APP-CEP updates the obfuscation technique assign-
ment (lines 2-7). Here, we also accept the event de-
pendencies the data owner enters at runtime (lines 8-
10). The OT Assigner function generates pattern de-
pendency graphs for each OT model and updates them
on runtime based on changes in both public and pri-
vate sets. Also, it extracts input stream features based
on history and updates those features using the current
streams (lines 12-13).
According to the event dependency set and stream
features, for each private pattern pr, APP-CEP per-
forms the following tasks: first, it removes those
OT models whose obfuscation can be realized by an
adversary (lines 16-18). For example, if the result
of reordering violates a causal dependency, such an
OT model will be removed from the list of available
OTs. In the remaining OT model space (i.e., O
pr
),
APP-CEP looks for a member whose dependency
graph has a node with an out-degree equal to zero for
pr, so-called zero-out-degree (ZOD) node (lines 20-
22). One of the OT models containing such a node
will be assigned to the pr. A random OT model will
be assigned to a pr if no ZOD node has been found for
this private pattern (lines 23-26). Finally, the assigned
OT model for each private pattern is determined and
will be updated upon any change in patterns or event
dependencies.
Although APP-CEP is a restrictive approach since
the idea of selecting a ZOD node does not achieve the
maximum QoS, finding these nodes guarantees both
obfuscating each private pattern and trying to detect
as many public patterns as possible. In addition, cal-
culating the exact PUT value requires considering the
exact number of pattern matches in each input stream,
whose disadvantages have been discussed earlier. In
case of finding no ZOD node, we believe assigning
the best OT model is outside the scope of our paper.
Therefore, we randomly assign the OT model in such
a worst-case scenario.
6 EVALUATION
The evaluation investigates the following questions:
1. Can graph-based pattern-level privacy provide a
trade-off between privacy concerns and the sys-
tem’s promised QoS?
2. What limitations are involved in applying pattern-
level privacy in real-world scenarios?
We created a single Virtual Machine (VM) in Or-
acle VM Virtual Box Manager, in which we installed
0
10
20
30
40
50
60
70
80
90
100
3*3 6*3 9*3 12*3 15*3
TOTAL REVEALED PRIVATE
PATTERN MATCHES (%)
# OF PUBLIC PATTERNS * # OF PRIVATE PATTERNS
APP-CEP Graph-based Window-based
Figure 5: Percentage of total revealed private pattern
matches Vs. The increasing number of public patterns.
Ubuntu version 20 OS. We allocated 6 CPU cores
with 100 percent execution capacity and 24 GB of
main memory to the VM. Furthermore, for event de-
tection, we build on FlinkCEP (Flink, 2017), a library
implemented on top of Apache Flink. We evaluated
our ideas by analyzing a publicly available real-world
dataset (Chen et al., 2012), transactions of an online
retailer selling all-occasion gifts. A part of this dataset
is selected for this evaluation, including 12000 cus-
tomer purchase records. We selected the 50 most fre-
quent patterns (length 3) from which public and pri-
vate pattern sets were randomly formed. We also per-
formed another statistical analysis to extract the most
parallel purchased items and periodically purchased
items as dependencies considered for the adversary’s
background knowledge. We executed the event detec-
tion process ten times for each combination of public
and private patterns and stated the average results.
Since modeling the adversary’s background
knowledge and graph-based OT assignment have not
been addressed before, we selected two baseline ap-
proaches to analyze the performance of APP-CEP.
The first technique, called Window-based, simulates
the performance of the state-of-the-art mechanisms
(Palanisamy, 2020; Palanisamy et al., 2018), which
relies on splitting the input stream into multiple fi-
nite windows of events. This approach tries to se-
lect an obfuscation technique for each private pat-
tern match precisely based on a utility value calcu-
lated according to the expected number of matches
for all patterns after applying that specific obfusca-
tion technique. The second approach, called Graph-
based, performs the obfuscation technique selection
similar to APP-CEP but without considering the ad-
versary’s background knowledge (i.e., event depen-
dencies). It only checks the pattern dependency graph
or OT-specific sub-graphs, if needed, and makes a de-
cision accordingly.
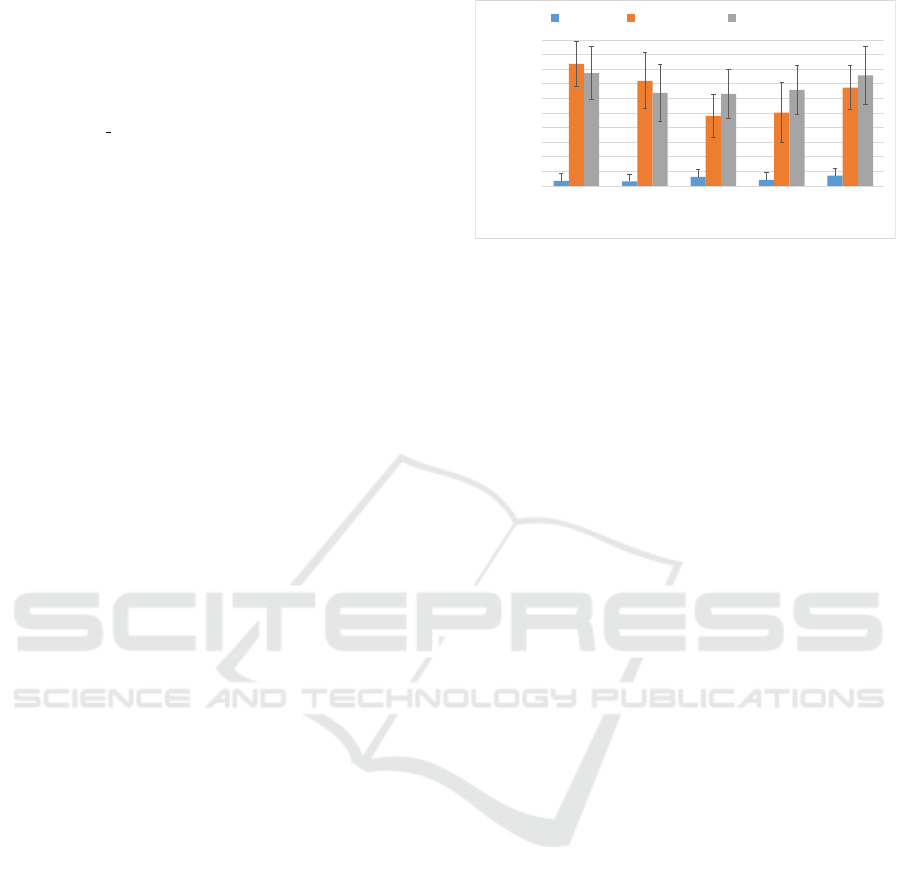
Figure 5 indicates the total percentage of re-
vealed private pattern matches (i.e., the summation of
matches for data owners’ privacy requirements added
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
494

0.5
0.6
0.7
0.8
0.9
1
1.1
3*3 6*3 9*3 12*3 15*3
F1-SCORE IN DETECTING PUBLIC
PATTERN MATCHES
# OF PUBLIC PATTERNS * # OF PRIVATE PATTERNS
APP-CEP Graph-based Window-based
Figure 6: F1-score in detecting public pattern matches Vs.
The increasing number of public patterns.
to the number of matches revealed by the adversary’s
background knowledge, totally divided by the actual
matches) while the number of public patterns is in-
creasing. Error bars also indicate the standard devia-
tion of ten rounds of simulations for each approach. It
can be seen that modeling and considering the adver-
sary’s background knowledge helps APP-CEP to sig-
nificantly reveal less (i.e., conceal more) private pat-
terns than other approaches. By adding more queries
to the system, Graph-based and Window-based tech-
niques fluctuate, but APP-CEP’s results stay around
ten percent. The random assignment of obfuscation
techniques when APP-CEP cannot find a ZOD node
in the global dependency graph or in obfuscation-
specific sub-graphs shows its impacts in the last three
bars. That is why complementing our algorithm with
an intelligent solution for such situations would be
challenging but necessary for our future work to solve
the potential scalability issue.
Similar to FN and FP, F1-score is a well-
known performance measure in machine learning ap-
proaches. It combines the other two measures, pre-
cision and recall, which are mainly employed to
distinguish between classifiers (Li et al., 2020) in
terms of accuracy. Therefore, the F1-score can be
used in stream processing to compare mechanisms
in terms of accuracy. From the public pattern de-
tection’s accuracy point of view, by increasing the
number of involved queries, all three approaches fluc-
tuate but gradually degrade; thereby, there is not a
specific front-runner, illustrated in Figure 6. How-
ever, APP-CEP’s detection accuracy is mostly equal
to or better than the Window-based approach when
increasing the number of involved queries (i.e., public
patterns), which confirms a slight improvement over
the literature, even in this challenging comparison.
The effects of increasing the knowledge of the ad-
versary are depicted in Figure 7. It can be seen that
APP-CEP reveals significantly fewer matches than
the other two approaches. By involving more de-
pendencies in query processing, the percentage of
0
20
40
60
80
100
20 40 60 80 100
REVEALED PRIVATE PATTERNS
MATCHES BY ADVERSARY (%)
# OF INVOLVED DEPENDENCIES
APP-CEP Graph-based Window-based
Figure 7: Percentage of revealed private pattern matches
by adversary Vs. The increasing adversary’s background
knowledge (number of dependencies).
0
200
400
600
800
1000
3*3 6*3 9*3 12*3 15*3
PRIVACY-UTILITY TRADE-OFF
# OF PUBLIC PATTERNS * # OF PRIVATE PATTERNS
APP-CEP Graph-based Window-based
Figure 8: Privacy-Utility Trade-off Vs. The increasing
number of public patterns.
expected revealed private pattern matches unexpect-
edly rises slightly but is still negligible compared to
Graph-based and Window-based approaches. Here,
the Graph-based approach reveals little more private
pattern matches than the Window-based, but gen-
erally, both approaches show similar performance.
Adding more dependencies corresponds to a more
knowledgeable adversary that even impacts the per-
formance of APP-CEP. Protecting against such an ad-
versary is almost impossible without sacrificing util-
ity in the system. However, the proposed approach
shows such a trade-off can be achievable even inde-
pendently of the actual events in the stream. More-
over, note that it becomes hard to compensate for the
revealed matches without modeling the adversary’s
additional background knowledge.
Last, Figure 8 accumulates the previous results to
compare the privacy-utility trade-off of the three ap-
proaches. As discussed in Section 4, the main goal
of this paper is to provide a method to maximize the
trade-off value (cf. PUT equation).
The computation of such a value requires the
system designer to opt for an optimized value for
weights. We decided to set equal weights for re-
vealed private pattern matches and expected revealed
matches by the adversary. This weight is the ratio of
the average of actual public matches to the average
of actual private matches for each pattern set com-
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event Processing Systems
495

bination. For instance, the weight for the scenario in
which we have 3 public patterns and 3 private patterns
was calculated as 1.0301. Also, we set the weight for
the detected public pattern matches equal to 1.
Here, the results indicate that APP-CEP is capa-
ble of achieving the expected PUT even by scaling up
the system’s involved queries. Although the Window-
based approach had a good start, the bars fall once
more public pattern matches are going to be detected,
as the amount of revealed private matches by the ad-
versary significantly impacts the PUT value. The
Graph-based approach seemingly had a better perfor-
mance than the Window-base. However, its results
also had a downward ending for the same reason.
Ultimately, the evaluation results prove the
expected improvements provided by graph-based
pattern-level privacy protection, solving the litera-
ture’s PUT gap. APP-CEP performs better in almost
all aspects discussed in this section than approaches
presented in previous studies due to considering both
pattern dependencies and modeling the adversary’s
background knowledge.
7 RELATED WORK
Although sharing data between stakeholders increases
the utility of IoT applications, ensuring efficient
preservation of privacy is still challenging (Tran et al.,
2023). Similarly, providing privacy in DCEP systems
requires establishing a trade-off concerning QoS since
protecting an individual’s privacy should not sacrifice
the application’s functionality, which lays on more
data to maximize the quality (Plagemann et al., 2022;
Schilling et al., 2013). Therefore, PPMs are required
to be lightweight and do not prevent any application
from detecting query patterns adequately. Moreover,
although data owners have been recently becoming
more aware of how their data will be analyzed and
being able to control it (Tokas et al., 2023; Leicht and
Heisel, 2023; Barber and Furnell, 2022), providing
sufficient means for them to express their privacy con-
cerns is still poorly studied.
The initial idea of preserving the individual’s pri-
vacy by employing patterns was introduced more than
a decade ago (He et al., 2011). It was theoretically
proved that by employing a probabilistic model, the
choice of event suppression can be estimated to max-
imize the utility alongside a window-based approach,
which makes the obfuscation decision according to
the actual events. Similar methods computed the
event distribution using advanced pattern match car-
dinality estimation techniques (Wang et al., 2013).
Other obfuscation operators (e.g., Reordering) have
been discovered in the literature as an alternative to
suppression operator (Palanisamy et al., 2018). The
main drawback of the mentioned studies is they failed
to obfuscate various pattern types since they focused
only on sequence type. In addition, they were highly
dependent on the input streams to apply obfuscation
techniques, i.e., they failed to obfuscate various kinds
of private patterns well in an environment with dy-
namic input event streams. Moreover, they have not
supported simultaneous obfuscation techniques cus-
tomized for each private pattern.
Recently, the idea of multi-operator multi-pattern
privacy protection has been introduced (Palanisamy,
2020). Although this ILP-based approach maximizes
the QoS while preserving privacy, it is limited to three
pattern types and three obfuscation operators. Be-
sides, it suffers from oscillation between OT mod-
els since they change the deployment as soon as they
detect a change in the input stream. This instability
in the deployed OT models degrades performance by
imposing unnecessary transition overhead. Besides,
the adversary’s background knowledge, which might
be used to realize the obfuscation, needed to be con-
sidered thoroughly.
8 CONCLUSION
In this work, we proposed APP-CEP, which repre-
sents how to enable dynamic integration of pattern-
level privacy in event-based systems to protect privacy
while providing an acceptable level of QoS. In ad-
dition, by producing pattern dependency graphs, our
mechanism is able to assign obfuscation techniques to
conceal sensitive patterns selectively and make an ob-
fuscation plan ahead of time. Our evaluation results
demonstrated that APP-CEP outperforms two base-
line techniques, namely Window-based and Graph-
based approaches, in the total percentage of revealed
private pattern matches and performed slightly bet-
ter in the number of detection errors of public pattern
matches. Moreover, by involving more background
knowledge, APP-CEP achieves a significant perfor-
mance in the expected revealed private matches by the
adversary. Furthermore, the PUT results prove that
APP-CEP successfully provides a solution to the gap
mentioned in this study and envisions a new era in this
field for adaptively assigning obfuscation techniques
regardless of actual events in the streams effectively.
In our future work, we will consider designing
an intelligent algorithm to select the best obfuscation
technique in case the dependency sub-graphs do not
offer a ZOD node. That can be achievable by in-
troducing a comparison metric by which both posi-
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
496

tive and negative effects of obfuscations can be com-
puted and labeled in the sub-graphs. Besides, Enhanc-
ing the suitability for real-world applications requires
thoughtful consideration of the stakeholders and their
respective interests when selecting input representa-
tions. Moreover, we plan to extend our evaluation to
different use cases to figure out other aspects of this
problem as well as APP-CEP limitations in fulfilling
various applications’ requirements.
ACKNOWLEDGEMENTS
This work has been supported by the Research Coun-
cil of Norway as part of the project Parrot (311197).
REFERENCES
Alt, B., Weckesser, M., Becker, C., Hollick, M., Kar, S.,
Klein, A., Klose, R., Kluge, R., Koeppl, H., Kold-
ehofe, B., et al. (2019). Transitions: A protocol-
independent view of the future internet. In Proceed-
ings of the IEEE, 107(4):835–846.
Barber, F. and Furnell, S. (2022). Benchmarking con-
sumer data and privacy knowledge in connected and
autonomous vehicles. In Proceedings of the 8th Inter-
national Conference on Information Systems Security
and Privacy (ICISSP’22), pages 426–434.
Chen, D., Sain, S. L., and Guo, K. (2012). Data mining for
the online retail industry: A case study of rfm model-
based customer segmentation using data mining. Jour-
nal of Database Marketing & Customer Strategy Man-
agement, 19:197–208.
Flink (2017). Flink-cep. https://nightlies.apache.org/flink/
flink-docs-master/docs/libs/cep/, Accessed on Oct
9th, 2023.
Gundersen, M. (2022). Statistics norway demands to
know exactly what norwegians buy in the grocery
store. https://nrkbeta.no/2022/05/28/ssb-krever-a-fa-
vite-noyaktig-hva-nordmenn-kjoper-i-matbutikken/,
Accessed on Oct 9th, 2023.
He, Y., Barman, S., Wang, D., and Naughton, J. F. (2011).
On the complexity of privacy-preserving complex
event processing. In Proceedings of the 13th ACM
SIGMOD-SIGACT-SIGART symposium on Principles
of database systems, pages 165–174.
Leicht, J. and Heisel, M. (2023). P2bac: Privacy policy
based access control using p-lpl. In Proceedings of the
9th International Conference on Information Systems
Security and Privacy (ICISSP’23), pages 686–697.
Li, L., Zhong, B., Hutmacher Jr, C., Liang, Y., Horrey, W. J.,
and Xu, X. (2020). Detection of driver manual distrac-
tion via image-based hand and ear recognition. Acci-
dent Analysis & Prevention, 137:p. 105432.
Lotfian Delouee, M., Koldehofe, B., and Degeler, V. (2022).
Towards adaptive quality-aware complex event pro-
cessing in the internet of things. In Proceedings of
the 18th International Conference on Mobility, Sens-
ing and Networking (MSN’22), pages 571–575. IEEE.
Lotfian Delouee, M., Koldehofe, B., and Degeler, V.
(2023a). Aqua-cep: Adaptive quality-aware complex
event processing in the internet of things. In Pro-
ceedings of the 17th ACM International Conference
on Distributed and Event-Based Systems (DEBS’23),
page 13–24. ACM.
Lotfian Delouee, M., Koldehofe, B., and Degeler, V.
(2023b). Poster: Towards pattern-level privacy pro-
tection in distributed complex event processing. In
Proceedings of the 17th ACM International Confer-
ence on Distributed and Event-Based Systems, page
185–186. ACM.
Palanisamy, S. M. (2020). Towards multiple pattern
type privacy protection in complex event processing
through event obfuscation strategies. In Data Privacy
Management, Cryptocurrencies and Blockchain Tech-
nology: ESORICS 2020 International Workshops,
DPM 2020 and CBT 2020, Guildford, UK, Septem-
ber 17–18, 2020, Revised Selected Papers 15, pages
178–194. Springer.
Palanisamy, S. M., D
¨
urr, F., Tariq, M. A., and Rothermel,
K. (2018). Preserving privacy and quality of service
in complex event processing through event reordering.
In Proceedings of the 12th ACM International Confer-
ence on Distributed and Event-based Systems, pages
40–51.
Plagemann, T., Goebel, V., Hollick, M., and Koldehofe, B.
(2022). Towards privacy engineering for real-time an-
alytics in the human-centered internet of things. arXiv
preprint arXiv:2210.16352.
Schilling, B., Koldehofe, B., Rothermel, K., and Ra-
machandran, U. (2013). Access policy consolidation
for event processing systems. In 2013 Conference on
Networked Systems, pages 92–101. IEEE.
Stach, C. and Steimle, F. (2019). Recommender-based
privacy requirements elicitation-epicurean: an ap-
proach to simplify privacy settings in iot applica-
tions with respect to the gdpr. In Proceedings of the
34th ACM/SIGAPP Symposium on Applied Comput-
ing, pages 1500–1507.
Tokas, S., Erdogan, G., and Stølen, K. (2023). Privacy-
aware iot: State-of-the-art and challenges. In Proceed-
ings of the 9th International Conference on Informa-
tion Systems Security and Privacy (ICISSP’23), pages
450–461.
Tran, T., Nguyen, P., and Erdogan, G. (2023). A system-
atic review of secure iot data sharing. In Proceed-
ings of the 9th International Conference on Informa-
tion Systems Security and Privacy (ICISSP’23), pages
95–105.
Wang, D., He, Y., Rundensteiner, E., and Naughton, J. F.
(2013). Utility-maximizing event stream suppression.
In Proceedings of the 2013 ACM SIGMOD Interna-
tional Conference on Management of Data, pages
589–600.
APP-CEP: Adaptive Pattern-Level Privacy Protection in Complex Event Processing Systems
497
