
Secure Multiparty Computation of the Laplace Mechanism
Amir Zarei
a
and Staal A. Vinterbo
b
Norwegian University of Science and Technology, Norway
Keywords:
Secure Multiparty Computation, Differential Privacy, Laplace Mechanism.
Abstract:
Differential Privacy (DP) employs perturbation mechanisms to protect individual data, formulated as Y =
q(D) + i, where q(D) is a query result from dataset D and i is random noise. Adjusting the variance of i
ensures that an adversary cannot discern if Y originates from D or its neighboring D
′
. Complications arise
when computing Y using floating-point (FL) or fixed-point (FP) arithmetic. Such approximations mean not
every potential output for Y is feasible, leading to a mismatch between the output of q(D) + i and q(D
′
) + i
that allows the adversary to breach DP. One solution is to approximate Y as
˜
Y = q
r
(D) + ir, where q
r
(D)
is q(D) rounded to a discretization factor r = 2
−k
. However, integrating this solution into secure multiparty
computation (MPC) is still unexplored. Our work addresses this challenge by proposing an MPC protocol that
rounds an FL number to the nearest multiple of r. We show how this protocol enables secure MPC of
˜
Y by
introducing two Laplace mechanisms. These are then specifically adapted for linear queries. Importantly, our
protocols support real-valued query functions on FL inputs and are not limited to integer-valued ones. The
first protocol uses FL arithmetic to generate the noise for DP, while the second utilizes integer arithmetic. Both
offer information-theoretical security against passive adversaries and can be extended for protection against
malicious adversaries. We also analyze the complexity of our protocols to evaluate their performance. Our
protocols represent the first provably secure MPC for the Laplace mechanism managing real-valued queries.
1 INTRODUCTION
The surge in data collection, driven by artificial intel-
ligence advancements like OpenAI’s GPT (Radford
et al., 2019) and Google’s BERT (Devlin et al., 2019),
underscores the need for data security and privacy.
Secure multiparty computation (MPC) ensures sensi-
tive information remains protected from unauthorized
access during collaborative computations. Mean-
while, differential privacy (DP) (Dwork and Roth,
2014) provides a framework to release statistics with-
out jeopardizing individual privacy. The fusion of
MPC and DP ensures data security during computa-
tions as well as individual data privacy when sharing
the computed results (Dwork et al., 2006).
To illustrate the combination of MPC and DP,
consider n parties with private and random inputs
(d
1
, s
1
), . . . , (d
n
, s
n
). The secure MPC for a differ-
entially private Laplace mechanism seeks to com-
pute f (d, s) = q(d) + h(s), where q is a query func-
tion mapping a set of databases to a real number,
h is a Laplace noise sampler, d = (d
1
, . . . , d
n
) and
a
https://orcid.org/0000-0002-0287-513X
b
https://orcid.org/0000-0003-2633-2305
s = (s
1
, . . . , s
n
). Protocols based on secret sharing
over Z
q
′
were provided (Dwork et al., 2006) to realize
f , and later refined (Eriguchi et al., 2021). These pro-
tocols treat q as an integer-valued query function and
approximate the Laplace distribution using a Trun-
cated Discrete Laplace (TDL) distribution to generate
noise compatible with integer arithmetic. However,
these protocols only accept integer numbers, limiting
their use in scenarios needing precise non-integer cal-
culations. To address this, protocols were proposed
that leverage secret sharing over real numbers (Eigner
et al., 2014; Wu et al., 2016). These protocols em-
ploy floating-point (FL) and fixed-point (FP) repre-
sentations to handle real numbers. However, a crucial
drawback of these protocols lies in the lack of anal-
ysis concerning the impact of finite-precision imple-
mentations of the Laplace mechanism, which allows
an adversary to undermine DP guarantees (Mironov,
2012; Gazeau et al., 2016).
In 2020, improving on the snapping mecha-
nism (Mironov, 2012), the DP team at Google pro-
posed algorithms to approximate the Gaussian and
Laplace mechanisms (Google’sDP, 2020). We refer
to the latter as GLM in our context. GLM ensures DP
582
Zarei, A. and Vinterbo, S.
Secure Multiparty Computation of the Laplace Mechanism.
DOI: 10.5220/0012453700003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 582-593
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

under double FL arithmetic, resulting in a noisy out-
put q
r
(D) + ir. Here, q represents a real-valued query
on a database D, rounded to a resolution parameter
r, and i indicates a randomly sampled integer from
a Discrete Laplace (DL) distribution. This approach
resolves the vulnerability inherent in naive FL imple-
mentations of the Laplace mechanism and supports
real-valued queries. Despite its advantages, GLM has
not yet been implemented in MPC settings, which is
our research motivation.
2 OTHER RELATED WORKS
Two primary models implement DP in distributed set-
tings: central and local. In the central model, a trusted
party aggregates actual inputs from all parties, intro-
duces noise according to a specific distribution and
publishes the perturbed result. Our MPC protocols
function as alternatives to implementing the central
model without relying on a trusted party. On the other
hand, the local model (Kasiviswanathan et al., 2011)
involves each party independently randomizing its in-
put and sending it to a designated party that aggre-
gates noisy inputs and publishes the result. Known
mechanisms in the local model are limited to specific
functions, such as aggregate-sum queries (Shi et al.,
2011; Wang et al., 2017), and histograms (Bassily and
Smith, 2015), making them inadequate for scenarios
where more complex functions need to be computed.
Furthermore, in this model, the accuracy of the noisy
output is limited to a certain extent, affecting the pre-
cision of the final results (Beimel et al., 2008; Chan
et al., 2012). Although a recent intermediate model
called the shuffled model (Cheu et al., 2019) has been
introduced, known mechanisms within this model re-
main applicable only for simple functions like sum-
mation (Cheu et al., 2019; Balle et al., 2019), and his-
tograms (Balcer and Cheu, 2019).
In addition to GLM, alternative methods are de-
signed to thwart attacks related to the FL implemen-
tation of differentially private mechanisms, focusing
on eliminating the need for rounding. One proposal
suggested sampling from Laplace and Gaussian noise
in a manner that intensifies the computational dif-
ficulty for attackers to backtrack the output (Holo-
han and Braghin, 2021). Another method (OpenDP,
2021) was introduced to produce a Laplace or Gaus-
sian distribution that leverages an arbitrary precision
arithmetic library (MPFR’slibrary, 2021). However,
these methods remain vulnerable to a novel type of FL
threat termed precision-based attacks (Haney et al.,
2022) due to avoiding the need for rounding when
adding noise in double-precision arithmetic.
2.1 Our Results
This paper aims to deploy GLM in an MPC setting,
leveraging secret sharing and analyzing its complex-
ity. We first introduce an MPC framework for the
Laplace mechanism handling FL inputs/output(s). In
this framework, users provide input shares to com-
putation parties, which then run an MPC protocol to
compute GLM and send results to a data analyzer.
As a requirement for the MPC of GLM, we de-
scribe an MPC method to round an FL number to the
nearest multiple of a power of 2, extending the tradi-
tional rounding protocol that rounds to the nearest in-
teger (Aliasgari et al., 2013). We also showcase two
techniques for DL distribution sampling: one with FL
arithmetic and another using integer arithmetic.
Combining these elements, we formulate two
MPC protocols for GLM and tailor them specifically
for linear queries. Our protocols are primarily se-
cure against passive adversaries but can be adapted
to thwart malicious ones. We analyze our protocols
based on the number of rounds and interactive oper-
ations, revealing that the first protocol excels in in-
teractive operations while the second requires fewer
rounds. In our framework, the users employ FL num-
bers to represent their input for precise numerical
computations. We demonstrate that an alternative ap-
proach using integers leads to inherent rounding er-
rors and imprecision.
Our protocols are the first to achieve MPC of
GLM, upholding DP properties while adeptly han-
dling real-valued query functions, thereby enhancing
their applicability in real-world scenarios. Addition-
ally, our framework and rounding protocol can sup-
port the MPC of the Gaussian mechanism, requiring
only a modification in the sampling method to use a
binomial distribution instead of a DL distribution.
3 PRELIMINARIES
This section first describes the secure MPC setting in
use and discusses the primitives underlying our pro-
tocols. It then delves into the details of GLM. Finally,
it covers number representation for ensuring accuracy
in our computations.
3.1 The Secure MPC Setting
We use a linear secret sharing scheme in which
n > 2 parties P
1
, . . . , P
n
jointly compute the func-
tion f (x
1
, . . . , x
n
) = (y
1
, . . . , y
n
) using protocol Π.
Each party P
i
contributes input x
i
and receives out-
put y
i
. This scheme integrates a secure multiplica-
Secure Multiparty Computation of the Laplace Mechanism
583

tion protocol for secret values and ensures inter-party
confidentiality via perfectly secure channels. The
scheme can be implemented through Shamir’s secret
sharing (Shamir, 1979) and the protocols introduced
in (Ben-Or et al., 1988). In the (t, n) sharing scheme,
a value is shared among n parties and can be recon-
structed by t + 1 or more parties but remains con-
cealed from t or fewer, offering information-theoretic
security. We define a finite field F
q
′
, where q
′
is a
large prime. The secret sharing of a value x ∈ F
q
′
among the parties is denoted by [x]. Due to the
scheme’s inherent linearity, parties can locally com-
pute linear combinations like [x] + [y], [x]+ c, and c[x]
using their respective shares of x and y. However, the
multiplication, [x][y], needs interaction between par-
ties. Using the reconstruction (Rec) protocol, t + 1 or
more parties can reveal a shared value in FL or integer
representation.
We consider two primary metrics to measure the
complexity of a protocol Π. The first, Int(Π), in-
cludes operations like multiplication, share distribu-
tion, and secret reconstruction. The second evaluates
round complexity, capturing the protocol’s sequential
interactive tasks. Concurrent interactive actions are
accounted for as a single round. Our evaluation over-
looks overflow, underflow, invalid operation, and di-
vision by zero.
We define the security of our protocols using the
standard definition of the passive adversary model in
MPC. To support security against stronger adversary
models, we will employ various techniques discussed
in Section 5.
Definition 3.1 (t-secure) Given the n parties and
protocol Π, we define the view of party P
i
during
the protocol execution as VIEW
Π
(P
i
) = (x
i
, r
i
, M).
This includes its input x
i
, random coin tosses r
i
, and
exchanged messages M. For a coalition T of par-
ties with size t <
n
2
and combined view VIEW
Π
(T ),
protocol Π is t-secure against passive adversaries
if there exists a probabilistic polynomial-time sim-
ulator S
T
. This simulator makes the distribution
of {VIEW
Π
(T ), y
T
} computationally indistinguish-
able from {S
T
(x
T
, f (x
1
, x
2
, ..., x
n
))}, where x
T
=
∪
P
i
∈T
{x
i
} and y
T
= ∪
P
i
∈T
{y
i
}.
3.2 Known Sub-Protocols
The following sub-protocols underpin the protocols in
this paper:
• [r] ← RandInt(l) allows the parties to create
shares of a uniformly random l-bit value r ∈ Z ∩
[0, 2
l
) (Catrina and De Hoogh, 2010b).
• [r] ← RandBit() allows the parties to produce
shares of a random bit r ∈ {0, 1} (Catrina and
De Hoogh, 2010b).
• [r] ← RandBiasedBit(s, p) takes inputs p and ran-
dom unbiased bits s = (s
i1
, ..., s
id
), where i ∈
{1, ..., n} and allows the parties to generate shares
of a random bit r with bias p (Eriguchi et al.,
2021).
• [c] ← XOR([a], [b]) computes the exclusive Or of
shared bits [a] and [b] as [a] + [b] − 2[a][b].
• [c] ← OR([a], [b]) computes the Or of shared bits
[a] and [b] as [a] + [b] − [a][b].
• [c
1
], ..., [c
l
] ← PRE
∨
([b
1
], ..., [b
l
]) takes on l
shared bits [b
i
] ∈ {0, 1}, and computes shares
of the prefixes as [c
i
] = [∨
i
j=1
b
j
] for i ∈
{1, . . . , l} (Damg
˚
ard et al., 2006).
• [c
1
], ..., [c
l
] ← MULT
∗
([b
1
], ..., [b
l
]), takes l shared
values [b
i
] ∈ F
q
\{0}, and computes shares of
the prefix products as [c
i
] = [
∏
i
j=1
b
j
] for i ∈
{1, . . . , l} (Damg
˚
ard et al., 2006).
• [b] ← EQ([x], [y], l) takes on two shared l-bit val-
ues [x] and [y], and outputs shared bit [b] = 1 if
[x] = [y]. We use an implementation of this op-
eration that uses the protocol [b] ←EQZ([x
′
], l),
which outputs [b] = 1 if [x
′
] = 0 (Catrina and
De Hoogh, 2010a).
• [b] ←LT([x], [y], l) takes on two shared l-bit val-
ues [x] and [y], and outputs shared bit [b] = 1 if
[x] < [y]. We use a realization of this function that
utilizes the protocol [b] ← LTZ([x
′
], l), which out-
puts [b] = 1 if [x
′
] < 0 (Catrina and De Hoogh,
2010a).
• FLAdd, FLMul, and FLDiv enable the parties to
add, multiply, and divide two shared FL numbers.
• FLLog2 takes on a shared FL number [r] and re-
turns the shared FL number [log r],
1
or an error
when r ≤ 0.
• FLRound takes on a shared FL number [r] and a
mode parameter and computes [⌈r⌉] if mode = 1,
and [⌊r⌋] if mode = 0.
• FP2FL, Int2FL, and FL2Int enable the parties to
convert a number represented as FP, integer, or FL
to its corresponding FL or integer representation.
All the protocols that handle computation on FL
numbers are detailed in (Aliasgari et al., 2013). Ta-
ble 1 collects the exact number of rounds and interac-
tive operations required for the aforementioned pro-
tocols. Notably, these complexities can be further re-
duced through pre-computation and when an operand,
1
For any positive real number a, we denote log(a) as the
logarithm to base 2 of a, and ln(a) as the natural logarithm
of a.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
584

or its components, given to a protocol that handles FL
input(s) is not a secret.
3.3 The Laplace Mechanism (GLM)
Here is how GLM works. Let r be a resolution pa-
rameter selected according to the scale of the Laplace
distribution, i.e.,
∆
ε
. Let q(D) be a function mapping
a database D to a real number, and let q
r
(D) be q(D)
rounded to the nearest multiple of r. We define ∆ as
max
D,D
′
∥ q(D)−q(D
′
) ∥, representing the sensitivity
of q, and ∆
r
as max
D,D
′
∥ q
r
(D)−q
r
(D
′
) ∥, represent-
ing the r-sensitivity of q. We assume there is a ran-
dom noise sampler that takes a 4-tuple (ε,δ, r, ∆
r
) and
returns i according to a DL distribution. Generally, if
r = 2
k
, where k is an integer in {−1022, . . . , 1023},
and i ∼ Sampler(ε, δ, r, ∆
r
), then q
r
(D) + ir is (ε, δ)-
DP. More precisely, given a constant integer k, the al-
gorithm steps for computing GLM are as follows.
1. Set r as the smallest power of 2 greater than
ε
∆
2. Sample an integer i with a probability propor-
tional to exp(−|i|r
ε
∆
r
)
3. Compute q
r
(D) + ir
If q(D) ≤ r2
52
, i ≤ 2
52
, and r is a power of two
between 2
−1022
and 2
1023
, then GLM is ε-DP under
double FL arithmetic (see (Google’sDP, 2020) for DP
proofs). The event q(D) > r2
52
is controlled by ad-
justing r or constraining q(D). The event i > 2
52
has a probability under exp(−1000), which is ignored
or seen as the δ mechanism’s guarantee. Follow-
ing (Google’sDP, 2020), we presume the first event
would not occur and disregard the second. The value
of k determines discretization accuracy, with rec-
ommended values between 10 and 45 (Google’sDP,
2020). Parameters r, ε, ∆, ∆
r
, and k are public inputs
to our protocols.
3.4 Number Representation
A binary FL number u is represented as a quadru-
ple (v, p, z, s), where v ∈ [2
l−1
, 2
l
) is an l-bit, un-
signed, normalized significand, p ∈ Z
⟨k⟩
= {x ∈ Z |
x ∈ (−2
k−1
, 2
k+1
)} is a k-bit, signed exponent, z is
a bit set to 1 when u = 0, and s is a sign bit. The
value of the number u = (1 − 2s)(1 − z)v · 2
p
. Values
in Z
⟨k⟩
are encoded in F
q
′
by the function fld : Z
⟨k⟩
→
F
q
′
, fld(a) = a mod q
′
.
For a binary FP number w, γ denotes the bit-length
of w, and λ denotes the bit-length of the fractional
part of w. The value of the number w = ˆw · 2
−λ
,
where ˆw ∈ Z
⟨γ⟩
= {x ∈ Z | x ∈ (−2
γ−1
, 2
γ+1
)}. Val-
ues in Z
⟨γ⟩
are encoded in F
q
′
by the fld function. We
also use γ to indicate the bit-length of integer values.
We assume that γ = 2λ for FP numbers and γ = 2l
for integers and FP numbers as applications usually
need (Eigner et al., 2014; Aliasgari et al., 2013). It is
also needed that k > max(⌈log(l + λ)⌉, ⌈log(γ)⌉), and
q
′
> max(2
2l
, 2
γ
, 2
k
) (Eigner et al., 2014). The param-
eters l, k, λ, and γ are public inputs (not secrets) to the
protocols working with FL and FP numbers. As GLM
works on standard double FL arithmetic, we consider
l = 53 and k = 11 while measuring the complexity of
our proposed protocols.
4 SECURE MULTIPARTY
LAPLACE MECHANISM
This section first discusses a framework for comput-
ing the Laplace mechanism over distributed data. We
then detail a rounding technique that enables the cal-
culation of the nearest multiple of r and subroutines
for generating integer DL distribution samples. Com-
bining these concepts, we introduce two MPC pro-
tocols for the Laplace mechanism. In particular, we
specialize these protocols for linear queries and com-
prehensively analyze their complexity.
4.1 The Protocol Framework
We adopt a robust combination of MPC and DP in
a scenario aiming to derive insights for a data ana-
lyzer from users’ information while preserving data
security and privacy. To realize this approach, we
use n computation parties C
1
, . . . ,C
n
to collaboratively
compute the information in two main phases: aggre-
gation and perturbation.
Figure 1: Protocol Flow.
The protocol flow is depicted in Fig. 1. Consider
m users; each user, denoted as U
i
, has a database D
i
,
all within the shared domain D ⊆ R. A real-valued
query function q : R
m
→ R maps the users’ input to a
numerical value(s) from R. The inputs and output(s)
are represented using FL numbers to handle real data
accurately. The specific nature of q determines the ag-
gregation operations, which may involve summation,
averaging, counting, or other statistical methods.
Secure Multiparty Computation of the Laplace Mechanism
585
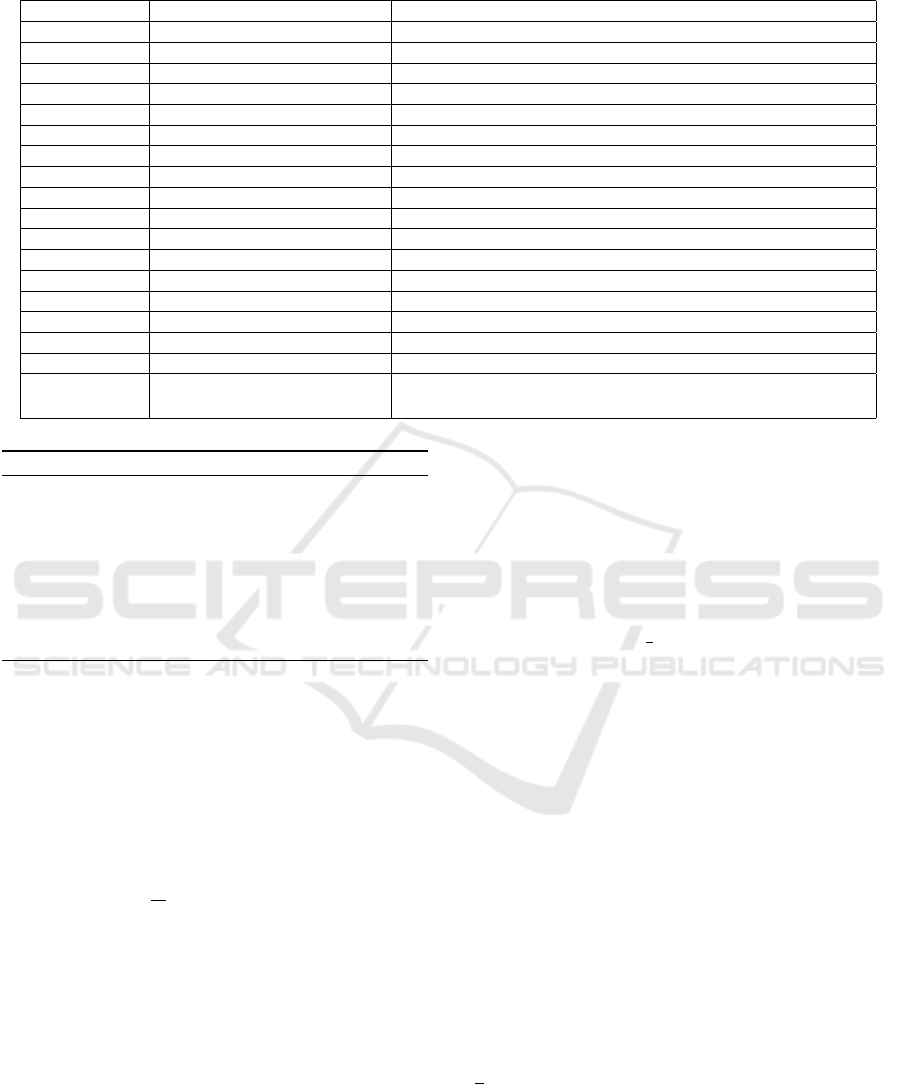
Table 1: Complexity of the employed MPC protocols in this paper.
Protocol Rounds Interactive operations
Rec 1 1
RandInt 0 0
RandBit 1 1
RandbiasedBit 11 (5n + 19)d
XOR 1 1
OR 1 1
PRE
∨
9 17l
MULT
∗
3 5l
LT 4 4l − 2
EQ 4 l + 4 log l
FLMul 11 8l + 10
FLAdd logl + log log l + 27 14l + 9k + (log l)log log l + (l + 9)log l + 4 logk + 37
FLDiv 2log l + 7 2log l(l + 2) + 3l + 8
FP2FL log l +13 logl(2l − 1) − 10
FL2Int 3log log(l) + 53 27l + 3 loglog(l) + 18 log l + 20k + 19
Int2FL log l +13 logl(2l − 1) − 11
FLRound loglog l + 30 15l + (log l)log log l +15 log l + 8k + 10
FLLog2
13.5l + 0.5l logl + 3 log l+
0.5l log log l + 3 log log l + 146
15l
2
+ 90.5l + 0.5l(log l)log log l + 0.5(logl) loglogl
+0.5l
2
logl + 11.5l logl + 4.5lk + 28k + 2l log k + 16logk + 128
Protocol 1: Π
GLM
.
Inputs: The FL representation of the private values
{d
1
, ..., d
m
} and public value r.
Output: The FL representation of q
r
(D) + ir.
1. The parties run Π
q
to compute q(D).
2. The parties run Π
rnd
to round q(D) to a multiple of r.
3. The parties run Π
i
to generate the integer noise i.
4. The parties compute q
r
(D) + ir and output the result.
Before computing q, each user securely sends shares
of its local computation result, computed as d
i
=
q(D
i
), to the computation parties. In the first phase,
aggregation, the computation parties aggregate shared
values from users and compute q. In the second phase,
perturbation, the computation parties add noise per
GLM, i.e., the outcome q
r
(d
1
, . . . , d
m
) + ir is calcu-
lated, where r represents a resolution parameter, and
i is an integer random noise from a DL distribution
related to exp
−r
ε
∆
r
.
Assuming protocols Π
q
, Π
rnd
, and Π
i
respectively
compute q(D), round q(D) to a multiple of r, and gen-
erate the noise i per the specified DL distribution, then
Π
GLM
, as shown in Protocol 1, represents a general
implementation of secure MPC for GLM.
In the literature exploring the fusion of MPC and
DP, it is well-established that a protocol which t-
securely computes an (ε, δ)-DP mechanism can offer
both the t-secrecy property and DP guarantees (refer
to (Eriguchi et al., 2021; Wu et al., 2016; Eigner et al.,
2014) for formal proofs). To abstract such a protocol,
let the parties settle on a uniformly random element s,
which can be a value in the range (0, 1] (Eigner et al.,
2014) or represented as s for a specific set S, e.g., a
set of all possible shares of 0 and 1 (Eriguchi et al.,
2021; Wu et al., 2016). Subsequently, the parties se-
curely compute a deterministic function (known as a
noise sampler), which takes s as input and generates
the necessary noise to satisfy DP. Assuming that the
distribution of this function provides (ε, δ)-DP even in
the presence of passive adversaries for a coalition T of
the parties of size t <
n
2
, we can generally construct an
(ε, δ)-DP protocol against the coalition T from pro-
tocols securely sampling s and computing the noise.
Building on this foundational approach, our protocol,
Π
GLM
, adheres to this security framework, ensuring
its alignment with the established security guarantees
of the fusion between MPC and DP. This approach
simplifies distributed noise generation by focusing on
the secure computation of deterministic functions and
generating a uniformly random element(s). For con-
ciseness, we omit the detailed proof and instead focus
on presenting our main results: protocols for imple-
menting Π
rnd
, Π
i
, Π
q
, and Π
GLM
.
4.2 The Rounding Technique
We formulate Π
rnd
to round the FL value of q(D)
to its closest multiple of r, a negative power of two.
Recall that r is the smallest power of 2 greater than
ε
∆
× 2
−k
, where k ranges from 10 to 45. The study
of (Aliasgari et al., 2013) proposed the FLRound pro-
tocol (detailed in Appendix A) to round to the nearest
integer. Building upon this, we introduce EFLRound,
an extension to round to any power of 2. EFLRound
is detailed in Protocol 2, where the secret shared value
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
586

Protocol 2: EFLRound.
Inputs: The FL representation of the private value q(D) as
⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, the public value r as ⟨v
r
, p
r
, 0, 0⟩, and
mode.
Output: The FL representation of the private value q
r
(D) as
⟨[v], [p], [z], [s]⟩.
1. [a] ← LT([p
q
], p
r
+ l − 1, k);
2. [b] ← LT([p
q
], p
r
, k);
3. ⟨[v
1
], [2
−(p
q
−(p
r
+l−1))
]⟩ ←Mod2m([v
q
], l, −[a](1 −
[b])([p
q
] − (p
r
+ l − 1));
4. [c] ←EQZ([v
1
], l);
5. [v] ← [v
q
] − [v
1
] + (1 −
[c])[2
−(p
g
−(p
r
+l−1))
](XOR(mode, [s
q
]));
6. [d] ←EQ([v], 2
l
, l + 1);
7. [v] ← [d]2
l−1
+ (1 − [d])[v];
8. [v] ← [a]((1 − [b])[v] + [b](mode−[s
q
])) + (1 − [a])[v
q
];
9. [s] ← (1 − [b]mode)[s
q
];
10. [z] ←OR(EQZ([v], l), [z
q
]);
11. [v] ← [v](1 − [z]);
12. [p] ← (([p
q
] + [d][a])(1 − [b]) + p
r
[b])(1 − [z]);
13. return ⟨[v], [p], [z], [s]⟩;
q(D) and the public r are inputted as
⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩ and ⟨v
r
, p
r
, 0, 0⟩. EFLRound
operates in mode 0 to round q(D) down and mode 1
to round it up.
Rounding may be necessary for q(D) only when
[p
q
] < p
r
+ l − 1. In this case [v
q
] is truncated by
removing the fraction [2
−(p
q
−(p
r
+l−1))
]. Therefore,
lines 1 and 2 of Protocol 2 compare the inputs’ ex-
ponent [p
q
] and p
r
. If [p
q
] < p
r
, the value of q(D)
lies in (−r, r), and thus the output should be ei-
ther 0 or ±r depending on the mode. Moreover, if
[p
q
] ≥ p
r
+ l − 1, the output of the rounding function
is equal to the input q(D). Significant computation
is necessary when p
r
≤ [p
q
] < p
r
+ l − 1, as shown
in lines 3-7. In this case, the −([p
q
] − (p
r
+ l − 1))
least significant bits of the significand [v
q
] are set to
0. This is done by first using Mod2m to calculate
v
1
= [v
q
mod [2
−(p
q
−(p
r
+l−1))
] in line 3, then comput-
ing [v
q
] − [v
1
] in line 5. Additionally, if [v
1
] is not 0 in
line 4, the protocol adds [2
−(p
q
−(p
r
+l−1))
] to [v
q
− v
1
]
based on the input’s sign and mode. Now if 2
l−1
≤
v
q
< 2
l
and the protocol is adding [2
−(p
q
−(p
r
+l−1)
], an
overflow occurs, resulting in v = 2
l
in line 6. In this
case, v is set to 2
l−1
in line 7, and the exponent is
incremented by 1 in line 12. Notice that the input’s
sign changes only if the input lies in (−r, 0) and the
mode is set to 0. In this case, line 9 sets the sign s to
0. Finally, lines 10 and 11 compute the zero bit of the
result, and line 12 adjusts the exponent.
If p
r
= −l + 1, EFLRound operates equivalently
to the FLRound protocol in (Aliasgari et al., 2013).
As for complexity, similar to the FLRound pro-
tocol, EFLRound requires 15l + (log log l)logl +
15log l +8k +10 interactive operations and log logl +
30 rounds. To achieve rounding to the nearest multi-
ple of r, we add the FL representation of
r
2
as ⟨v
r
, p
r
−
1, 0, 0⟩ to ⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, and then execute the
EFLRound protocol with mode 0. Another idea to
compute q
r
(D) is to implement q
r
(D) = r⌊
q(D)
r
+
1
2
⌋.
This requires one of each FLDiv, FLAdd, FLRound,
and FLMul, which is more expensive.
4.3 Noise Generation Techniques
We now implement Π
i
, a protocol to sample i from
a DL distribution with probability proportional to
exp(−r
ε
∆
r
). To achieve this, we introduce two tech-
niques that will subsequently provide two protocols
for computing GLM.
The FL Implementation of Π
i
. To generate a DL
random sample, the first technique reduces the prob-
lem to generating geometric samples. This is fur-
ther simplified by generating uniform random values.
Given U uniformly distributed over the interval (0, 1],
we can express two independent geometric random
variables, Y
1
and Y
2
, both with success probability p,
as Y = ⌈
ln(U)
ln(1−p)
⌉. The difference X = Y
1
−Y
2
then fol-
lows a DL distribution (Devroye, 2006). Recall that
per GLM, p = exp(−r
ε
∆
r
). We can realize a secure
MPC of this technique, termed as DL(p), by Proto-
col 3.
Lines 1-3 of Protocol 3 generate two uniform ran-
dom numbers in the interval (0, 1]. This is based on a
method by (Eigner et al., 2014), which involves gen-
erating two shared (γ + 1)-bit integers [a
1
] and [a
2
]
using RandInt. These integers are then treated as the
fractional part of two FP numbers, where the integer
parts are set to 0 (represented by λ = γ). To convert
these FP numbers into their FL representation, we use
FP2FL. Lines 3-9 calculate two geometric samples,
and line 10 generates a DL random variable. Recall
that FLLog2 computes the logarithm in base 2, while
we require the logarithm in terms of the Euler’s num-
ber (e). To address this, we multiply the results of
FLLog2 by the FL representation of α =
1
ln(1−p) log e
in lines 6 and 7. The complexity of Protocol 3 in-
volves 128870 interactive operations in 1203 rounds.
This has considered reductions in FLMul’s complex-
ity, as it now needs 8l + 7 interactive operations and
10 rounds due to one of its operands provided in the
clear, compared to its complexity in Table 1. FLMul
Secure Multiparty Computation of the Laplace Mechanism
587

Protocol 3: Discrete Laplace Sampler DL(p).
Inputs: The FL representation of the public input α =
1
ln(1−p) log e
as ⟨v
α
, p
α
, z
α
, s
α
⟩.
Output: The FL representation of the private value i ∼ DL
distribution as ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩.
1. [a
1
] ← RandInt (γ + 1); [a
2
] ← RandInt (γ + 1);
2. ⟨[v
a1
], [p
a1
], 0, 0⟩ ← FP2FL([a
1
], γ, λ = γ, l, k);
3. ⟨[v
a2
], [p
a2
], 0, 0⟩ ← FP2FL([a
2
], γ, λ = γ, l, k);
4. ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ ← FLLog2(⟨[v
a1
], [p
a1
], 0, 0⟩);
5. ⟨[v
2
], [p
2
], [z
2
], [s
2
]⟩ ← FLLog2(⟨[v
a2
], [p
a2
], 0, 0⟩);
6. ⟨[v
αln1
], [p
αln1
], [z
αln1
], [s
αln1
]⟩ ←
FLMul(⟨v
α
, p
α
, z
α
, s
α
⟩, ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩);
7. ⟨[v
αln2
], [p
αln2
], [z
αln2
], [s
αln2
]⟩ ←
FLMul(⟨v
α
, p
α
, z
α
, s
α
⟩, ⟨[v
2
], [p
2
], [z
2
], [s
2
]⟩);
8. ⟨[v
i1
], [p
i1
], [z
i1
], [s
i1
]⟩ ←
FLRound(⟨[v
αln1
], [p
αln1
], [z
αln1
], [s
αln1
]⟩, 1);
9. ⟨[v
i2
], [p
i2
], [z
i2
], [s
i2
]⟩ ←
FLRound(⟨[v
αln2
], [p
αln2
], [z
αln2
], [s
αln2
]⟩, 1);
10. ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩ ←
FLSub (⟨[v
i1
], [p
i1
], [z
i1
], [s
i1
]⟩, ⟨[v
i2
], [p
i2
], [z
i2
], [s
i2
]⟩)
11. return Rec(⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩);
Protocol 4: Discrete Laplace Sampler TDL(p, N).
Inputs: s
j
= (s
i1
, ..., s
id
) for j ∈ {0, 1, . . . , N − 1} and i ∈
{1, . . . , n}, N, α
0
=
1−p
1+p
and α
j
= 1 − p.
Output: The integer representation of the private value i ∼
DL distribution.
1. [b
j
] ← RandbiasedBit(s
j
, α
j
) for j ∈ {0, 1, . . . , N − 1};
2. [c
j
] ← PRE
∨
[b
j
] for j ∈ {0, 1, . . . , N − 1};
3. [l] = N −
∑
N−1
j=0
[c
j
];
4. Each P
i
shares [σ
i
] ∈ {0, 1} for i ∈ {1, . . . , n};
5. [σ
j
] ← MULT
∗
[σ
i
] for i ∈ {1, . . . , n}, [σ] =
∏
n
j=1
[σ
j
];
6. [i] = [σ][l];
7. return Rec([i]);
is detailed in Appendix A.
The Integer Implementation of Π
i
. A different ap-
proach to sample an integer variate from a DL dis-
tribution measures the probability of taking N coins
to obtain success. To realize this approach, the work
of (Eriguchi et al., 2021) introduce TDL(p, N) as,
Pr[L = i] =
p
|i|
(1−p)
(1+p)
if|i| < N,
p
N
1+p
if|i| = N,
0 otherwise,
and show a mechanism that adds noise from
TDL(p, N) to an integer-valued query is (ε, δ)-DP
Protocol 5: The Laplace mechanism using DL(p).
Inputs: The FL representation of the public input r as
⟨v
r
, p
r
, 0, 0⟩.
Output: The FL representation of the private value of
q
r
(D) + ir as ⟨[v], [p], [z], [s]⟩.
1. ⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩ ← Π
q
;
2. ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ ←
FLAdd (⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, ⟨v
r
, p
r
− 1, 0, 0⟩);
3. ⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩ ←
EFLRound⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩, ⟨v
r
, p
r
, 0, 0⟩, 0);
4. ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩ ← DL(p);
5. ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩ ←
FLMul(⟨v
r
, p
r
, 0, 0⟩, ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩);
6. ⟨[v], [p], [z], [s]⟩ ←
FLAdd(⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩, ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩);
7. return Rec(⟨[v], [p], [z], [s]⟩);
for p = exp(−
ε
∆
) and δ ≥ p
N
1+p
−∆
1+p
. Recall that per
GLM, q
r
(D)+ir is ε-DP, where i follows a DL distri-
bution with p = exp(−r
ε
∆
r
).
The study of (Eriguchi et al., 2021) also presents
a secure MPC protocol for sampling from TDL(p, N)
using the idea of (Dwork et al., 2006) in which one
shared biased coin is generated from d shared unbi-
ased coins. Given p and N, the MPC of TDL(p, N) is
implemented by Protocol 4, which operates on inte-
gers and requires (5n + 19)dN + 17N + 5n + 4 inter-
active operations and 15 rounds to generate one DL
sample. An extra interactive operation and round have
been considered because of the Rec protocol, com-
pared to the complexity reported by (Eriguchi et al.,
2021).
4.4 The Laplace Mechanism
Implementation
Protocol 5 is an MPC protocol for computing GLM
using DL(p).
In Protocol 5, we assume the sub-protocol Π
q
computes q(D). Lines 2 and 3 round q(D) to the
nearest multiple of r. We note that to obtain
r
2
, we
only need to subtract 1 from p
r
since r is a power
of two. Line 4 computes i, and line 5 scales the
noise as ir. Line 6 calculates q
r
(D) + ir. Finally, in
line 7, the parties reconstruct the FL representation
of q
r
(D) + ir. As for complexity, Protocol 5 can be
implemented using 132800+ Int(Π
q
) interactive oper-
ations. For FLAdd in line 2, one operand provided
in the clear reduces the number of interactive opera-
tions by 14 compared to the value in Table 1, while
the number of rounds remains the same. FLAdd is
detailed in Appendix A. Similarly, FLMul in line 5
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
588

Protocol 6: The Laplace mechanism using TDL(p, N).
Inputs: The FL representation of the public input r as
⟨v
r
, p
r
, 0, 0⟩, and the integer representation of N and p.
Output: The FL representation of the private value q
r
(D) +
ir as ⟨[v], [p], [z], [s]⟩.
1. ⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩ ← Π
q
;
2. ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ ←
FLAdd (⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, ⟨v
r
, p
r
− 1, 0, 0⟩);
3. ⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩ ←
EFLRound(⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩, ⟨v
r
, p
r
, 0, 0⟩, 0);
4. [i] ← TDL(p, N);
5. ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩ ← Int2FL([i], γ, l);
6. ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩ ←
FLMul(⟨v
r
, p
r
, 0, 0⟩, ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩);
7. ⟨[v], [p], [z], [s]⟩ ←
FLAdd(⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩, ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩);
8. return Rec(⟨[v], [p], [z], [s]⟩);
also benefits from one operand provided in the clear,
as previously discussed, reducing its complexity.
Protocol 6 is a variant of Protocol 5, which re-
places TDL(p, N) with DL(p). In line 5 of Pro-
tocol 6, Int2FL converts the integer sample i to its
FL representation. Protocol 6 can be realized with
(5n + 19)dN +17N +5n +3940 + Int(Π
q
) interactive
operations.
4.5 A Specialization of Π
q
for Linear
Queries
To simplify the presentation, we consider a class
of queries defined by q(D
1
, . . . , D
m
) = q(D
1
) + ··· +
q(D
m
). For this, we outline our algorithm for com-
puting the Laplace mechanism. The algorithm takes
m real inputs d
1
, . . . , d
m
, each representing the local
execution of q on U
i
’s database D
i
as d
i
= q(D
i
).
It also takes the resolution parameter r as an input.
The algorithm computes and returns the real output
w = q
r
(D) + ir by the following steps:
1. Compute q(D) as q(D) =
∑
m
i=1
d
i
.
2. Round q(D) to the nearest multiple of r.
3. Generate a random sample i distributed per the DL
distribution with p = exp(−r
ε
∆
r
).
4. Multiply i by r.
5. Add q
r
(D) to ir to obtain the result w.
We adopt the following approach to implement the al-
gorithm in an MPC setting. We assume the users are
connected to the computation parties by perfectly se-
cure channels. Before computation begins, users initi-
ate the (⌊
n−1
2
⌋, n) sharing scheme to distribute shares
Protocol 7: A specialization of Laplace mechanism using
DL(p).
Inputs: The FL representation of the private values d
i
as
⟨[v
d
i
], [p
d
i
], [z
d
i
], [s
d
i
]⟩ for i ∈ {1, . . . , m}, the public inputs r
as ⟨v
r
, p
r
, 0, 0⟩ and the integer value p.
Output: The FL representation of the private value q
r
(D) +
ir as ⟨[v], [p], [z], [s]⟩.
1. ⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩ ← ⟨[v
d
1
], [p
d
1
], [z
d
1
], [s
d
1
]⟩;
2. for i = 2 to m do
⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩ ← FLAdd(
⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, ⟨[v
d
i
], [p
d
i
], [z
d
i
], [s
d
i
]⟩);
3. ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ ←
FLAdd (⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, ⟨v
r
, p
r
− 1, 0, 0⟩);
4. ⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩ ←
EFLRound⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩, ⟨v
r
, p
r
, 0, 0⟩, 0);
5. ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩ ← DL(p);
6. ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩ ←
FLMul(⟨v
r
, p
r
, 0, 0⟩, ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩);
7. ⟨[v], [p], [z], [s]⟩ ←
FLAdd(⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩, ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩);
8. return Rec(⟨[v], [p], [z], [s]⟩);
of their inputs among the computation parties, ad-
hering to the honest majority assumption. The (n, n)
sharing scheme may lead to inefficiencies, as FLAdd
requires the multiplication protocol at certain stages.
Once the shares are distributed among the computa-
tion parties, each party P
k
has a share of all input val-
ues d
i
for k ∈ {1, . . . , n} and i ∈ {1, . . . , m}. The in-
put values are represented as shared FL numbers, de-
noted as ⟨[v
d
i
], [p
d
i
], [z
d
i
], [s
d
i
]⟩ to indicate the FL rep-
resentation of d
i
. Additionally, to generate the noise
i, we still rely on the honest majority assumption.
Once the parties collectively compute the shared re-
sult q
r
(D)+ ir, they can reconstruct the final result by
invoking the Rec protocol.
Protocol 7 and 8 are realizations of the Laplace
mechanism for computing q(D) using respectively
DL(p) and TDL(p, N).
To assess the complexity of Protocol 7, we divide
it into two main parts that can be executed in parallel
to reduce the number of rounds. Part (1) computes
q
r
(D) in lines 1-4, and part (2) computes ir in lines
5 and 6. Part (1) can be realized using 1262m + 980
interactive operations in 36log m + 68 rounds when
the additions in the for loop are performed in parallel.
On the other hand, part (2) can be implemented using
129300 interactive operations in 1178 rounds. Under
the assumption that m < 2
30
, the number of rounds in
part (2) is the dominant factor in computing the total
number (i.e., we disregard the number of rounds in
part (1)). Considering FLAdd and Rec in lines 7 and 8,
Secure Multiparty Computation of the Laplace Mechanism
589

Protocol 8: A specialization of Laplace mechanism using
TDL(p, N).
Inputs: The FL representation of the private values d
i
as
⟨[v
d
i
], [p
d
i
], [z
d
i
], [s
d
i
]⟩ for i ∈ {1, . . . , m}, the public inputs r
as ⟨v
r
, p
r
, 0, 0⟩ and the integer values N and p.
Output: The FL representation of the private value q
r
(D) +
ir as ⟨[v], [p], [z], [s]⟩.
1. ⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩ ← ⟨[v
r
1
], [p
r
1
], [z
r
1
], [s
r
1
]⟩;
2. for i = 2 to m do
⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩ ← FLAdd(
⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, ⟨[v
d
i
], [p
d
i
], [z
d
i
], [s
d
i
]⟩);
3. ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ ←
FLAdd (⟨[v
q
], [p
q
], [z
q
], [s
q
]⟩, ⟨v
r
, p
r
− 1, 0, 0⟩);
4. ⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩ ←
EFLRound⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩, ⟨v
r
, p
r
, 0, 0⟩, 0);
5. [i] ← TDL(p, N);
6. ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩ ← Int2FL([i], γ, l);
7. ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩ ←
FLMul(⟨v
r
, p
r
, 0, 0⟩, ⟨[v
i
], [p
i
], [z
i
], [s
i
]⟩);
8. ⟨[v], [p], [z], [s]⟩ ←
FLAdd(⟨[v
gr
], [p
gr
], [z
gr
], [s
gr
]⟩, ⟨[v
ir
], [p
ir
], [z
ir
], [s
ir
]⟩);
9. return Rec(⟨[v], [p], [z], [s]⟩);
Protocol 7 requires 1262m + 131540 interactive oper-
ations and 1250 rounds.
To analyze the complexity of Protocol 8, we set
d = 50 as recommended by (Eriguchi et al., 2021),
r = 2
−k
= 2
−10
, ε = 1, and ∆
r
= 1 to execute
TDL(p = exp(−r
ε
∆
r
), N). The number of interac-
tive operations of Protocol 8 depends on the vari-
able N. We find a suitable value for N by satisfying
δ ≥ p
N
1+p
−∆
1+p
. After numerical analysis with ε = 1,
∆
r
= 1, and r = 2
−k
= 2
−10
, aiming for δ ≤ 2
−20
, we
found that N ≥ 14196. Hence, we use N = 14196
for the complexity analysis of Protocol 8. Recall that
10 ≤ k ≤ 45 is recommended by (Google’sDP, 2020).
Note that larger values of N will be required for any
k > 10 and ε < 1 to achieve δ = 2
−20
. Protocol 8
can be divided into two main parts that can be exe-
cuted concurrently to save the number of rounds. Part
(1) computes q
r
(D) in lines 1-4, and part (2) com-
putes ir in lines 5-7. Part (1), like part (1) of Pro-
tocol 7, can be implemented using 1262m + 980 in-
teractive operations and 36log m + 68 rounds. On
the other hand, part (2) can be implemented using
3549005m + 13728000 interactive operations and 44
rounds. Since the number of rounds of part (1) is the
dominant factor, we disregard the number of rounds
of part (2) while computing the total number. Consid-
ering FLAdd and Rec in lines 8 and 9, Protocol 8 re-
quires overall 3550267m + 13730000 interactive op-
erations and 36log m + 105 rounds.
Both Protocols 7 and 8 have interactive oper-
ations of O(m). Specifically, Protocol 7 requires
1262m + 131540 interactive operations and a con-
stant of 1250 rounds. In comparison, Protocol 8 de-
mands 3550267m + 13730000 interactive operations
and 36log m + 105 rounds. While Protocol 7 has a
fixed round count, Protocol 8 realistically requires
fewer rounds, given m < 2
30
. The constants under
big-O for Protocol 8 are substantially larger than Pro-
tocol 7, such that for m = 100, 000 users, Protocol 8
needs about 2810 times more interactive operations
than Protocol 7. Despite its fewer rounds, Protocol 8
has much higher communication complexity.
5 SECURITY ANALYSIS
Our protocols are secure against passive adversaries
in the information-theoretic model. For malicious ad-
versaries, the security of our protocols depends on the
chosen verifiable secret sharing scheme. These claims
are detailed in the following.
In our MPC setting, we established a linear se-
cret sharing scheme that satisfies the t-secure property
against coalitions of size up to t passive adversaries.
Additionally, our setting relies on a secure multiplica-
tion protocol to ensure no information leakage occurs;
the only data transmitted among the parties is secret
shares. Moreover, we detailed the sub-protocols used
in section 3.2, which have previously been demon-
strated to uphold the t-secrecy property. Invoking
Canetti’s composition theorem (Canetti, 2000), one
can infer that the composition of secure sub-protocols
ensures the security of the overall solution. As is com-
mon in MPC literature, and without furnishing for-
mal proof, we claim the existence of a simulator for
our protocols. Such a simulator, when invoking sim-
ulators for the corresponding sub-protocols, would
theoretically create an environment indistinguishable
from the real protocol execution by the parties.
To ensure security against malicious adversaries,
all parties must demonstrate that every computation
step has been executed correctly. This is particularly
important when any linear combination of shares is
computed locally; each party must validate that it
has accurately carried out each multiplication on its
shares. If any party acts dishonestly or abandons the
protocol, the remaining parties should be able to re-
construct their shares and proceed with the computa-
tion. A verifiable secret sharing (VSS) scheme can ef-
fectively address these concerns (Cramer et al., 2000).
We can employ VSS schemes such as (Cramer et al.,
2000) that offer security in the information-theoretic
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
590

model or VSS schemes such as (Pedersen, 1992) that
ensure security only in the computational model. Ad-
ditionally, when parties provide input values of a par-
ticular form, they must verify that their inputs adhere
to these requirements. Such verification is crucial
when implementing specific building blocks, such as
RandInt. This verification can be achieved by existing
protocols like those in (Peng and Bao, 2010).
6 AN ALTERNATIVE SOLUTION
One might suggest that each user locally rounds its
input to the nearest integer and then shares an inte-
ger value with the computation parties. While such a
method sidesteps the complexities of FL arithmetic in
evaluating the function q, it may significantly under-
mine its accuracy. For instance, given m independent
variables d
i
where each d
i
is uniformly distributed
over [0, 1], the expected absolute error between the
sum of the original variables and the sum of their
rounded values is approximately
p
m
12
q
2
π
. A detailed
derivation of this result is as follows.
Given a variable d
i
, the error introduced by round-
ing is defined as e
i
= d
i
− round(d
i
). This error lies
in the range [−0.5, 0.5], specifically for d
i
∈ [0,0.5),
e
i
= d
i
and for d
i
∈ [0.5, 1], e
i
= d
i
− 1. The expected
value of the square of the error is
E[e
2
i
] =
Z
0.5
0
x
2
dx +
Z
1
0.5
(x − 1)
2
dx =
1
12
.
The variance of the error is
Var(e
i
) = E[e
2
i
] − (E[e
i
])
2
,
since E[e
i
] = 0, then Var(e
i
) =
1
12
.
The standard deviation of the sum of independent
errors e
i
is
σ
sum
=
p
m ×Var(e
i
) =
r
m
12
.
By Central Limit Theorem: For large m, the sum
of the errors tends toward a normal distribution with
mean 0 and standard deviation σ
sum
. The expected
absolute deviation for a standard normal distribution
is
q
2
π
σ. Combining these results, we arrive at
E[|e
1
+ e
2
+ ··· + e
m
|] ≈
r
m
12
r
2
π
.
For m = 100, 000, the error equals 72.836. There-
fore, in contexts where precision is essential, these
rounding inaccuracies can amplify, especially in sub-
sequent computations (e.g., when factoring in the ran-
dom noise introduced by the DP mechanisms), the
combined error in q may escalate. This culmination of
rounding error and noise-induced variability suggests
that such rounding might not be a favorable approach
if the accuracy of q is a priority.
7 CONCLUSION
This paper has bridged an important gap in the field
by addressing the need for secure MPC of differen-
tially private Laplace mechanisms designed explic-
itly for real-valued queries. Although prior works
have provided MPC of DP for integer-valued queries,
including real-valued queries is pivotal in many ap-
plications. Despite a few attempts to extend the
MPC of DP to accommodate real-valued queries, such
approaches are susceptible to side-channel attacks,
thereby undermining privacy guarantees. In the fol-
lowing, we will discuss some avenues for future work.
While this paper does not address the optimization
of Protocol 8, it does invite the research community to
explore methods to enhance the protocol’s efficiency.
One potential direction is to make TDL(p, N) (ε, δ =
0)-DP as δ > 0 significantly increases the protocol’s
communication complexity. Moreover, improving the
complexity of the FLLog2 primitive used in Proto-
col 7 represents a significant area for future work as
the current implementation requires over 1000 rounds
of computation (Eigner et al., 2014). While our study
has thoroughly analyzed the complexity of our proto-
cols, it is essential to emphasize the need for practical
implementation to assess their real-world efficiency
and applicability.
REFERENCES
Aliasgari, M., Blanton, M., Zhang, Y., and Steele, A.
(2013). Secure computation on floating point num-
bers. Network and Distributed System Security
(NDSS) Symposium.
Balcer, V. and Cheu, A. (2019). Separating local & shuffled
differential privacy via histograms. 1st Conference on
Information-Theoretic Cryptography (ITC 2020).
Balle, B., Bell, J., Gasc
´
on, A., and Nissim, K. (2019). The
privacy blanket of the shuffle model. In Proceedings
of 39th Annual International Cryptology Conference
(CRYPTO 2019), pages 638–667. Springer.
Bassily, R. and Smith, A. (2015). Local, private, efficient
protocols for succinct histograms. In Proceedings of
the forty-seventh annual ACM symposium on Theory
of computing, pages 127–135.
Beimel, A., Nissim, K., and Omri, E. (2008). Distributed
private data analysis: Simultaneously solving how and
what. In Proceedings of 28th Annual International
Secure Multiparty Computation of the Laplace Mechanism
591

Cryptology Conference (CRYPTO), pages 451–468.
Springer.
Ben-Or, M., Goldwasser, S., and Wigderson, A. (1988).
Completeness theorems for non-cryptographic fault-
tolerant distributed computation. In Proceedings of
the twentieth annual ACM symposium on Theory of
computing, pages 351–371.
Canetti, R. (2000). Security and composition of multiparty
cryptographic protocols. Journal of CRYPTOLOGY,
13:143–202.
Catrina, O. and De Hoogh, S. (2010a). Improved primitives
for secure multiparty integer computation. In Interna-
tional Conference on Security and Cryptography for
Networks, pages 182–199. Springer.
Catrina, O. and De Hoogh, S. (2010b). Secure multiparty
linear programming using fixed-point arithmetic. In
Proceedings of 15th European Symposium on Re-
search in Computer Security (ESORICS 2010), pages
134–150. Springer.
Chan, T. H., Shi, E., and Song, D. (2012). Optimal lower
bound for differentially private multi-party aggrega-
tion. In European Symposium on Algorithms, pages
277–288. Springer.
Cheu, A., Smith, A., Ullman, J., Zeber, D., and Zhilyaev,
M. (2019). Distributed differential privacy via shuf-
fling. In Proceedings of 38th Annual International
Conference on the Theory and Applications of Crypto-
graphic Techniques (EUROCRYPT 2019), pages 375–
403. Springer.
Cramer, R., Damg
˚
ard, I., and Maurer, U. (2000). Gen-
eral secure multi-party computation from any lin-
ear secret-sharing scheme. In Proceedings of Inter-
national Conference on the Theory and Application
of Cryptographic Techniques (EUROCRYPT 2000),
pages 316–334. Springer.
Damg
˚
ard, I., Fitzi, M., Kiltz, E., Nielsen, J. B., and Toft,
T. (2006). Unconditionally secure constant-rounds
multi-party computation for equality, comparison, bits
and exponentiation. In Theory of Cryptography Con-
ference, pages 285–304. Springer.
Devlin, J., Chang, M., Lee, K., and Toutanova, K. (2019).
BERT: pre-training of deep bidirectional transformers
for language understanding. pages 4171–4186. Asso-
ciation for Computational Linguistics.
Devroye, L. (2006). Nonuniform random variate genera-
tion. Handbooks in operations research and manage-
ment science, 13:83–121.
Dwork, C., Kenthapadi, K., McSherry, F., Mironov, I., and
Naor, M. (2006). Our data, ourselves: Privacy via
distributed noise generation. In Annual International
Conference on the Theory and Applications of Cryp-
tographic Techniques, pages 486–503. Springer.
Dwork, C. and Roth, A. (2014). The algorithmic foun-
dations of differential privacy. Found. Trends Theor.
Comput. Sci., 9(3–4):211–407.
Eigner, F., Kate, A., Maffei, M., Pampaloni, F., and Pry-
valov, I. (2014). Differentially private data aggrega-
tion with optimal utility. In Proceedings of the 30th
Annual Computer Security Applications Conference,
pages 316–325.
Eriguchi, R., Ichikawa, A., Kunihiro, N., and Nuida, K.
(2021). Efficient noise generation to achieve differ-
ential privacy with applications to secure multiparty
computation. In International Conference on Finan-
cial Cryptography and Data Security, pages 271–290.
Springer.
Gazeau, I., Miller, D., and Palamidessi, C. (2016). Preserv-
ing differential privacy under finite-precision seman-
tics. Theoretical Computer Science, 655:92–108.
Google’sDP (2020). Secure Noise Generation.
Haney, S., Desfontaines, D., Hartman, L., Shrestha, R., and
Hay, M. (2022). Precision-based attacks and interval
refining: how to break, then fix, differential privacy on
finite computers. arXiv preprint arXiv:2207.13793.
Holohan, N. and Braghin, S. (2021). Secure random
sampling in differential privacy. In Computer Se-
curity – ESORICS 2021: 26th European Symposium
on Research in Computer Security, Darmstadt, Ger-
many, October 4–8, 2021, Proceedings, Part II, page
523–542, Berlin, Heidelberg. Springer-Verlag.
Kasiviswanathan, S. P., Lee, H. K., Nissim, K., Raskhod-
nikova, S., and Smith, A. (2011). What can we learn
privately? SIAM Journal on Computing, 40(3):793–
826.
Mironov, I. (2012). On significance of the least signifi-
cant bits for differential privacy. In Proceedings of
the 2012 ACM conference on Computer and commu-
nications security, pages 650–661.
MPFR’slibrary (2021). The GNU MPFR library.
OpenDP (2021). samplers.rs – opendp.
Pedersen, T. P. (1992). Non-interactive and information-
theoretic secure verifiable secret sharing. In Feigen-
baum, J., editor, Advances in Cryptology — CRYPTO
’91, pages 129–140, Berlin, Heidelberg. Springer
Berlin Heidelberg.
Peng, K. and Bao, F. (2010). An efficient range proof
scheme. In 2010 IEEE second international confer-
ence on social computing, pages 826–833. IEEE.
Radford, A., Wu, J., Child, R., Luan, D., Amodei, D.,
Sutskever, I., et al. (2019). Language models are un-
supervised multitask learners. OpenAI blog, 1(8):9.
Shamir, A. (1979). How to share a secret. Communications
of the ACM, 22(11):612–613.
Shi, E., Chan, H., Rieffel, E., Chow, R., and Song, D.
(2011). Privacy-preserving aggregation of time-series
data. In Annual Network & Distributed System Secu-
rity Symposium (NDSS). Internet Society.
Wang, T., Blocki, J., Li, N., and Jha, S. (2017). Locally
differentially private protocols for frequency estima-
tion. In 26th USENIX Security Symposium (USENIX
Security 17), pages 729–745.
Wu, G., He, Y., Wu, J., and Xia, X. (2016). Inherit differ-
ential privacy in distributed setting: Multiparty ran-
domized function computation. In 2016 IEEE Trust-
com/BigDataSE/ISPA, pages 921–928. IEEE.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
592

APPENDIX
A FL PROTOCOLS
INTRODUCED BY (Aliasgari
et al., 2013)
Protocol 9 rounds an FL number to the nearest inte-
ger depending on its mode parameter. Protocols 10
and 11 compute respectively the product and addition
of two FL numbers as inputs.
Protocol 9: FLRound.
Inputs: The FL number ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ and mode.
Output: The FL number ⟨[v], [p], [z], [s]⟩ which is the result
of rounding the input to an integer.
1. [a] ← LTZ([p
1
], k);
2. [b] ← LT([p
1
], −l + 1, k);
3. ⟨[v
2
], [2
−p
1
]⟩ ← Mod2m([v
1
], l, −[a](1 − [b])[p
1
]);
4. [c] ← EQZ([v
2
], l);
5. [v] ← [v
1
] − [v
2
] + (1 − [c])[2
−p
1
](XOR(mode, [s
1
]));
6. [d] ← EQ([v], 2
l
, l + 1);
7. [v] ← [d]2
l−1
+ (1 − [d])[v];
8. [v] ← [a]((1 − [b])[v] + [b](mode−[s
1
])) + (1 − [a])[v
1
];
9. [s] ← (1 − [b]mode)[s
1
];
10. [z] ← OR(EQZ([v], l), [z
1
]);
11. [v] ← [v](1 − [z]);
12. [p] ← ([p
1
] + [d][a](1 − [b]))(1 − [z]);
13. return ⟨[v], [p], [z], [s]⟩;
Protocol 10: FLMul.
Inputs: The FL numbers ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ and
⟨[v
2
], [p
2
], [z
2
], [s
2
]⟩.
Output: The FL number ⟨[v], [p], [z], [s]⟩ as the result of the
product of the inputs.
1. [v] ← [v
1
][v
2
];
2. [v] ← Trunc([v], 2l, l − 1);
3. [b] ← LT ([v], 2
l
, l + 1);
4. [v] ← Trunc(2[b][v] + (1 − [b])[v], l +1, 1);
5. [c] ← OR ([z
1
], [z
2
]);
6. [v] ← XOR ([s
1
], [s
2
]);
7. [p] ← ([p
1
] + [p
2
] + l − [b])(1 − [z]);
8. return ⟨[v], [p], [z], [s]⟩;
Protocol 11: FLAdd.
Inputs: The FL numbers ⟨[v
1
], [p
1
], [z
1
], [s
1
]⟩ and
⟨[v
2
], [p
2
], [z
2
], [s
2
]⟩.
Output: The FL number ⟨[v], [p], [z], [s]⟩ as the result of the
addition of the inputs.
1. [a] ← LT ([p
1
], [p
2
], k);
2. [b] ← EQ ([p
1
], [p
2
], k);
3. [c] ← LT ([v
1
], [v
2
], l);
4. [p
max
] ← [a][p
2
] + (1 − [a])[p
1
];
5. [p
min
] ← (1 − [a])[p
2
] + [a][p
1
];
6. [v
max
] ← (1 −[b])([a][v
2
] + (1 − [a])[v
1
])+ [b]([c][v
2
] +
(1 − [c])[v
1
]);
7. [v
min
] ← (1 − [b])([a][v
1
] + (1 − [a])[v
2
]) + [b]([c][v
1
] +
(1 − [c])[v
2
]);
8. [s
3
] ← XOR ([s
1
] + [s
2
]);
9. [d] ← LT (l, [p
max
] − [p
min
], k);
10. [2
∆
] ← Pow2 ((1 − [d])([p
max
] − [p
min
]), l + 1);
11. [v
3
] ← 2([v
max
] − [s
3
]) + 1;
12. [v
4
] ← [v
max
][2
∆
] + (1 − 2[s
3
])[v
min
];
13. [v] ← ([d][v
3
] + (1 − [d])[v
4
])2
l
Inv([2
∆
]);
14. [v] ← Trunc([v], 2l + 1, l − 1);
15. [u
l+1
], . . . , [u
0
] ← BitDec([v], l +2, l + 2);
16. [h
0
], . . . , [h
l+1
] ← PreOr([u
l+1
], . . . , [u
0
]);
17. [p
0
] ← l + 2 −
∑
l+1
i=0
[h
i
];
18. [2
p
0
] ← 1 +
∑
l+1
i=0
2
i
(1 − [h
i
]);
19. [v] ← Trunc([2
p
0
][v], l + 2, 2);
20. [p] ← [p
max
] − [p
0
] + 1 − [d];
21. [v] ← (1 − [z
1
])(1 − [z
2
])[v] + [z
1
][v
2
] + [z
2
][v
1
];
22. [z] ← EQZ([v], l);
23. [p] ← ((1 − [z
1
])(1 − [z
2
])[p] + [z
1
][p
2
] + [z
2
][p
1
])(1 −
[z]);
24. [s] ← (1 −[b])([a][s
2
]+(1 −[a])[s
1
])+[b]([c][s
2
]+(1 −
[c])[s
1
]);
25. [s] ← (1 −[z
1
])(1−[z
2
])[s]+(1 −[z
1
])[z
2
][s
1
]+[z
1
](1−
[z
2
])[s
2
];
26. return ⟨[v], [p], [z], [s]⟩;
Secure Multiparty Computation of the Laplace Mechanism
593
