
Need for Speed: Leveraging the Power of Functional Encryption for
Resource-Constrained Devices
Eugene Frimpong
1 a
, Alexandros Bakas
2 b
, Camille Foucault
1 c
and Antonis Michalas
1 d
1
Tampere University, Tampere, Finland
2
Nokia Bell Labs, Espoo, Finland
Keywords:
Elliptic Curve Cryptography, Functional Encryption, Lightweight Cryptography, Wireless Sensor Networks.
Abstract:
Functional Encryption (FE) is a cutting-edge cryptographic technique that enables a user with a specific func-
tional decryption key to determine a certain function of encrypted data without gaining access to the under-
lying data. Given its potential and the fact that FE is still a relatively new field, we set out to investigate
how it could be applied to resource-constrained environments. This work presents what we believe to be the
first lightweight FE scheme explicitly designed for resource-constrained devices. We also propose a use case
protocol that demonstrates how our scheme can secure an Internet of Things (IoT) architecture where relevant
devices collect data and securely deliver them to a storage server, where an analyst can request access to the en-
crypted data. Finally, we conduct thorough experiments on two commercially available resource-constrained
devices to provide compelling evidence of our approach’s practicality and efficiency. Although the results of
our evaluations show that there is room for improvement in the proposed scheme, this work represents one of
the first attempts to apply FE to the IoT setting that can directly impact people’s daily lives and the everyday
operations of organizations.
1 INTRODUCTION
The term Internet of Things (IoT) refers to a collec-
tion of varying devices or appliances utilized in differ-
ent sectors that broaden the concept of the Internet. A
popular IoT environment, commonly referred to as a
Wireless Sensor Network (WSN), consists of a myr-
iad of resource-constrained devices deployed in var-
ious capacities, such as sensing environmental data
and monitoring human interactions. The data col-
lected by these devices often tend to be confidential
or critical, opening the network to many security and
privacy-related threats that continue to draw much at-
tention from Academia and Industry alike. For exam-
ple, consider a scenario where some sensor devices
have been deployed to monitor the health vitals of
athletes in a particular sports competition. The data
collected by these devices should be kept confiden-
tial and only available to authorized entities. How-
ever, the implementation and adoption of standard se-
curity schemes, such as public key cryptography, is
complex due to the resource constraints of the de-
a
https://orcid.org/0000-0002-4924-5258
b
https://orcid.org/0000-0002-0731-1851
c
https://orcid.org/0009-0001-6741-887X
d
https://orcid.org/0000-0002-0189-3520
vices involved (Frimpong et al., 2020). These devices
typically have limited memory, computational capa-
bilities, and power resources compared to traditional
computing systems.
One of the key challenges when proposing and de-
signing security schemes or applications for resource-
constrained devices is ensuring that the application
efficiently utilizes the device’s resources. This of-
ten involves using techniques such as code optimiza-
tion and efficient memory management. Addition-
ally, it may be necessary to limit the application’s
functionality to run efficiently on the device and uti-
lize cryptographic primitives with low memory re-
quirements and low computational overheads. An-
other challenge is to design for power efficiency and
low power consumption as these devices are often
battery-powered. This means minimizing the device’s
power usage and power-saving features is critical.
To this end, research in lightweight cryptography for
resource-constrained devices has become a mainstay
to provide privacy, trust, and integrity, focusing on re-
duced implementation sizes, energy costs, and com-
putational latencies. In a recent survey of over 54
lightweight cryptographic primitives (Dhanda et al.,
2020), a comparison was conducted between vari-
ous lightweight ciphers with micro-controller chip en-
ergy and power consumption, hardware performance,
62
Frimpong, E., Bakas, A., Foucault, C. and Michalas, A.
Need for Speed: Leveraging the Power of Functional Encryption for Resource-Constrained Devices.
DOI: 10.5220/0012626200003705
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 9th International Conference on Internet of Things, Big Data and Security (IoTBDS 2024), pages 62-74
ISBN: 978-989-758-699-6; ISSN: 2184-4976
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

and latency. From their results, the authors observed
that Elliptic Curve Cryptography (ECC) primitives
were the most suitable for building lightweight cryp-
tographic schemes. ECC schemes use an elliptic
curve defined over a finite field GF(p), for a large
prime p, denoted by E(GF(p)), containing affine
points (x, y) ∈ GF(p) × GF(p). Subsequently, the se-
curity of schemes based on ECC relies on the hard-
ness of the Elliptic Curves Discrete Logarithm Prob-
lem (ECDLP) (Darrel Hankers and Vanstone, 2004).
The primary advantage of using ECC primitives is
the utilization of shorter keys, which lead to a lower
memory requirement and faster field arithmetic oper-
ations (Lara-Nino et al., 2018). By relying on these
advantages, we are not only able to deploy traditional
ECC on constrained devices, but we take this work a
step further by designing, to the best of our knowl-
edge, the first Functional Encryption (FE) (Boneh
et al., 2011) scheme that runs efficiently on resource-
constrained devices.
FE is an emerging cryptographic technique that
allows selective computations over encrypted data.
Generally, FE schemes provide a key generation al-
gorithm that outputs decryption keys with remark-
able capabilities. More precisely, each decryption key
sk
f
is associated with a function f . In contrast to
traditional cryptographic techniques, using sk
f
on a
ciphertext Enc(x) does not recover x but a function
f (x) – thus keeping the actual value x private. While
the first constructions of FE allowed the computation
of a function over a single ciphertext, more recent
works (Goldwasser et al., 2014a) introduced the more
general notion of multi-input FE (MIFE). In a MIFE
scheme, given ciphertexts Enc(x
1
), . . . , Enc(x
n
), a
user can use sk
f
to get f (x
1
, . . . , x
n
). The function f
allows the functional key holder to only learn highly
processed data forms. Unfortunately, while MIFE
seems to be a perfect fit for many real-life applications
– such as cloud-based applications where multiple
users store large volumes of data in remote and possi-
bly corrupted entities – most of the works in the field
revolve around constructing generic schemes that do
not support devices with limited resources. Having
identified FE as an important member of the family
of modern encryption schemes that can push us into
uncharted technological terrain, we make a first at-
tempt at designing and implementing an efficient yet
secure FE scheme for resource-constrained devices.
This work seeks to smooth out the identified asymme-
tries between theory and practice while proving that
resource-constrained devices can run said schemes.
Contributions. The contributions of this paper are;
C1. We first propose and design an ECC-based
lightweight MIFE scheme for adding vectors’
components inspired by the generic ElGamal-
based FE construction presented in (Bakas
et al., 2022b).
C2. Based on the proposed MIFE scheme, we con-
struct a use-case protocol that demonstrates
the applicability of our work in a real-world
application along with extensive security anal-
ysis.
C3. Finally, we implement and evaluate the per-
formance of our scheme on two commercially
available resource-constrained devices and a
standard desktop machine to demonstrate the
proposed benefits and applicability.
2 RELATED WORK
Functional Encryption was first formalized as a gen-
eralization of public-key encryption in (Boneh et al.,
2011). Since then, numerous studies with general def-
initions and generic constructions of FE have been
proposed (Sahai and Seyalioglu, 2010; Waters, 2015;
Goldwasser et al., 2013; Goldwasser et al., 2014b;
Bakas et al., 2022a). Despite the promising works
that have been published; there is a clear lack of works
proposing FE schemes supporting use cases – a neces-
sary step that would allow FE to be deployed in real-
world applications. In particular, and to the best of
our knowledge, the number of supported functionali-
ties is currently limited to sums (Bakas et al., 2022b;
Bakas et al., 2020; Bakas and Michalas, 2020), inner
products (Abdalla et al., 2018; Abdalla et al., 2017;
Abdalla et al., 2015) and quadratic polynomials (Sans
et al., 2018). While these works are promising, un-
fortunately, we can not use any of them as a black
box in our solution. This is because most of these
works rely on cryptographic primitives over alge-
braic finite fields; hence, the size of the cryptographic
keys becomes too large to store on a constrained de-
vice. Building on the ElGamal-based FE scheme dis-
cussed in (Bakas et al., 2022b), we’ve created a new
lightweight FE scheme for addition. This new scheme
uses an elliptic curve version of the ElGamal sys-
tem. We should point out that we’re not looking at
the LWE-based scheme from the same source (Bakas
et al., 2022b), mainly because it would require larger
keys, making it a poor fit for devices with limited re-
sources.
While the problem of aggregating encrypted data
from constrained devices has been thoroughly exam-
ined in multiple works (Vinodha and Mary Anita,
2018; Castelluccia et al., 2009; Li et al., 2015;
Need for Speed: Leveraging the Power of Functional Encryption for Resource-Constrained Devices
63

Wang et al., 2022), we consider our construction
to be the first attempt to tackle the problem using
FE. For example, in (Castelluccia et al., 2009), au-
thors propose a provably secure encryption scheme
enabling additive aggregation of encrypted data. In
this work, each device in a sink-rooted spanning
tree environment sums all values it receives from
its children, with the final value sent to a sink de-
vice. Similarly, authors in (Li et al., 2015) proposed
a fully homomorphic encryption (FHE) based on a
secure data aggregation scheme with simulation re-
sults. Another work (Wang et al., 2022) designed
a non-interactive privacy-preserving data aggregation
for resource-constrained devices with the help of a
Trusted Execution Environment. Given the vast pos-
sibilities and advantages of a cryptographic primitive
such as FE, we see our work as a first step towards
capturing the true potential of FE in real-world solu-
tions. To this end, we consider our approach fresh
and unrelated to works relying, for example, on ho-
momorphic encryption or proxy servers as discussed
in existing works.
Finally, the efficient design and implementation
of lightweight cryptographic schemes on resource-
constrained devices is not new and continues to draw
much attention (Lara-Nino et al., 2018; Frimpong and
Michalas, 2020; Frimpong et al., 2020; He et al.,
2019; Frimpong et al., 2021; Dubrova et al., 2018).
In (Frimpong and Michalas, 2020), authors imple-
ment a lightweight ECC library in the Contiki-NG
operating system to secure communication between
multiple parties without needing a third party. Au-
thors in (Frimpong et al., 2020) also designed and
implemented a forward private dynamic Symmet-
ric Searchable Encryption (SSE) scheme compati-
ble with resource-constrained devices by splitting the
core functionalities of the scheme between the con-
strained devices and a fog node. In (He et al., 2019),
authors designed a lightweight certificate enrollment
protocol for constrained IoT devices that utilized the
Enrollment over Secure Transport (EST) semantics
and leveraged the existing IoT stack to optimize re-
source usage. A lightweight message authentication
scheme based on cyclic redundancy check (CRC) was
also proposed in (Dubrova et al., 2018). Further-
more, a certificateless group key distribution protocol
compatible with constrained devices was proposed
in (Frimpong et al., 2021). These works achieved ef-
ficient and secure lightweight schemes that provide
a foundation for a safe IoT ecosystem. We build on
these foundations to design and implement our pro-
posed lightweight FE scheme, which we prove to
be efficient and secure even on the most resource-
constrained devices.
3 BACKGROUND
3.1 Notation
A public/private key pair of a public-key encryption
scheme PKE is denoted as (pk, sk). If the public/pri-
vate key pair is associated with an entity E, then
we write (pk
E
, sk
E
). Vectors are denoted in bold as
x = (x
1
, . . . , x
n
). A PPT adversary ADV is a ran-
domized algorithm for which there exists a polyno-
mial p(z), such that for all valid inputs z, the running
time of ADV (z) is bounded by p(|z|). A function
negl(·) is called negligible if it grows slower than any
inverse polynomial.
3.2 Public Key Encryption
Definition 1 (Public-Key Encryption). A public-key
encryption scheme PKE for a message space X con-
sists of three algorithms PKE = (Gen, Enc, Dec). A
PKE scheme is said to be correct if:
(1)Pr[Dec(sk, c) ̸= x ∈ X ]|[(pk, sk) ← Gen(1
λ
)]
∧ [c ← Enc(pk, x)] = negl(λ)
where negl(λ) is a negligible function in the security
parameter λ.
Definition 2 (Additive Ciphertext Homomorphism
(ACH)). We say that a public-key encryption scheme
PKE is additive ciphertext homomorphic if:
(2)
n
∑
i =1
Enc(pk
i
, x
i
) = Enc
n
∑
i=1
pk
i
,
n
∑
i=1
x
i
!
where the first sum is the addition on the ciphertext
space, the second the addition on the public key space
and the third the addition on the message space.
Definition 3 (Additive Key Homomorphism (AKH)).
We say that a public-key encryption scheme PKE is
additive key homomorphic if for every two public/pri-
vate key pairs (pk
1
, sk
1
) and (pk
2
, sk
2
) generated by
PKE.Gen, we can generate a new valid public/private
key pair as (pk
1
+ pk
2
, sk
1
+ sk
2
), where pk
1
+ pk
2
is
the addition in the space of public keys and sk
1
+ sk
2
is the addition in the space of secret keys.
Definition 4 (selective-Indistinguishability-Based Se-
curity). For a PKE scheme PKE = (Gen, Enc, Dec) we
define the following experiments:
Exp
s−IND−CPA−β
(ADV )
Initialize(λ, x
0
, x
1
)
(pk, sk)
$
←− Gen(1
λ
)
Return pk
Challenge()
c
β
$
←− Enc(pk, m
β
)
Finalize
(β
′
)
β
′
= β
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
64

The advantage ε of ADV is defined as:
(3)
ε =
Pr[Exp
s−ind−CPA−0
(ADV ) = 1]
−Pr[Exp
s−ind−CPA−1
(ADV ) = 1]
We say that PKE is s-IND-CPA-β secure if
ε = negl(λ)
3.3 ElGamal over Elliptic Curves
As previously stated, the proposed construction relies
on the Elgamal cipher defined over elliptic curves.
Hence, we begin by informally recalling how the
cryptosystem works (Abdalla et al., 2015). Let E
be an elliptic curve defined over GF(p), where p is
a large prime. The ElGamal secret key is then an
element s ∈ GF(p), while the corresponding pub-
lic key is computed as Y = s · G ∈ E, where G is a
generator of E. To encrypt a message x ∈ GF(p),
we first pick a random r ∈ [1, N − 1], where N is
the order of the curve, and in the end, we compute
c = Enc(x) = (P, Q) = (r · G, x · G + r ·Y ). Finally, for
decryption, we can recover the original message using
the private key s, by computing −s · P + Q. A more
formal description is illustrated in Figure 1.
ElGamal over Elliptic Curves.
Let E be an elliptic curve of order N, defined over
GF(p), where p is a large prime. Then, the ElGa-
mal cryptosystem over elliptic curves is defined as
a tuple PKE = (Gen, Enc, Dec), such that:
PKE.Gen(1
λ
)
1. Pick a generator G
of E
2. Sample the private
key as s
$
←− GF(p)
3. Compute the public
key as Y = s · G
4. Output (s,Y )
PKE.Enc(Y, x)
1. Sample r
$
←− [1, N −
1]
2. Compute c =
(P, Q) = (r · G, x · G +
r ·Y )
3. Output c
PKE.Dec(s, c)
1. Output −s · P + Q
Figure 1: ElGamal over Elliptic Curves.
3.4 From Points to Integers
While addition over an elliptic curve is possible, we
can only add points on the curve, which is not very
useful in the context of functional encryption. To
this end, we define a mapping function as in (Ugus
et al., 2009) with the purpose of mapping elements of
GF(p) to the curve as follows:
Definition 5 (Mapping function). Let E be an elliptic
curve defined over GF(p), where p is a large prime.
Moreover, let G be a generator of E. Then we define
a mapping function f
map
: GF(p) → E such that:
∀x ∈ GF(p) : f
map
(x) = x · G = X ∈ E, (4)
where · refers to point multiplication over E. For the
rest of this paper, we write xG to simplify reading.
Note that when the curve is defined over a field
of prime order, every element in the field is a genera-
tor of the curve. Hence, finding a generator is trivial.
With the help of f
map
, we can add elements in GF(p),
using points on the curve. This is possible because by
definition, we have that:
(5)
f
map
(x
1
) + · ·· + f
map
(x
n
)
= x
1
G + · ·· + x
n
G
= (x
1
+ · ·· + x
n
)G
= f
map
(x
1
+ · ·· + x
n
),
where each x
i
∈ GF(p) and f
map
(x
i
) ∈ E. Note that,
unambiguously, we use the same notation for addition
in GF(p) and its underlying addition in E. While the
inverse function f
−1
map
exists, computing it is equiva-
lent to solving the DLP over an elliptic curve. How-
ever, when each x
i
is small (i.e. not of cryptographic
size), this is possible by relying on a list of pre-
computed values. Considering x
i
small is realistic as
data generated or collected by the devices in question
will not be of cryptographic size.
3.5 Multi-Input Functional Encryption
Definition 6 (Multi-Input Functional Encryption). A
Multi-Input Functional Encryption scheme MIFE for
a message space X , where X is a vector space of
dimension n, is a tuple of four algorithms MIFE =
(Setup, Enc, KeyGen, Dec) such that:
• Setup(1
λ
): The Setup algorithm takes a security
parameter λ as input and outputs a master pub-
lic/private key (mpk, msk).
• Enc(mpk, x): The encryption algorithm is a prob-
abilistic algorithm. Upon input the master public
key mpk and a vector x = (x
1
, . . . , x
n
) ∈ X outputs
a ciphertext c = (c
1
, . . . , c
n
).
• KeyGen(msk, f ): The key generation algorithm
KeyGen is a deterministic algorithm. Upon input
the master secret key msk and a function f , out-
puts a functional decryption key sk
f
.
• Dec(sk
f
, c) The decryption algorithm Dec is a de-
terministic algorithm. Upon input a functional
decryption key sk
f
and a ciphertext c, outputs
f (x) = f (x
1
, . . . , x
n
)
Need for Speed: Leveraging the Power of Functional Encryption for Resource-Constrained Devices
65

A MIFE scheme is said to be correct if and only
if:
Pr[Dec(sk
f
, c) ̸= f (x)]|[(mpk, msk) ← Setup(1
λ
)]
∧ [c ← Enc(mpk,x)]
∧ [sk
f
← KeyGen(msk, sk
f
)] = negl(λ)
(6)
Definition 7 (MIFE Indistinguishability-Based
Security). For a MIFE scheme MIFE =
(Setup, Enc, KeyGen, Dec), we define the following
experiments:
Exp
s−IND−FE−CPA−β
(ADV )
Initialize(λ, x
0
, x
1
)
mpk, msk
$
←−
Setup(1
λ
)
L ←
/
0
Output mpk
Key Generation( f )
L ← L ∪ { f }
sk
f
$
←− KeyGen(msk, f )
Output sk
f
Challenge()
c
β
$
←− Enc(mpk, x
β
)
Finalize(β
′
)
If ∃ f ∈ L :
yoyo f (x
0
) ̸= f (x
1
)
yoyo Output ⊥
Else
β
′
= β
The advantage ε of ADV is defined as:
ε =
Pr[Exp
s−ind−FE−CPA−0
(ADV ) = 1]
−Pr[Exp
s−ind−FE−CPA−1
(ADV ) = 1]
We say that MIFE is s-IND-FE-CPA-β secure iff
ε = negl(λ)
3.6 Generic Multi-Input Functional
Encryption Scheme for the
Summation of a Vector’s
Components
We now recall the generic construction from (Bakas
et al., 2022b), and in the next section, provide our
lightweight instantiation from ECC.
Definition 8 (MIFE for the summation of a vector’s
components (MIFE
sum
)). Let PKE = (Gen, Enc, Dec)
be an IND-CPA secure cryptosystem that also ful-
fills the ACH and AKE properties. Then we define
MIFE
sum
as MIFE
sum
= (Setup, Enc, KeyGen, Dec)
where:
1. Setup(1
λ
, n): The Setup algorithm invokes the
PKE’s Gen algorithm and generates n public/pri-
vate key pairs as (pk
1
, sk
1
), . . . , (pk
n
, sk
n
). It out-
puts a master public/private key pair as mpk, msk,
where mpk = (params, pk
1
, . . . , pk
n
) and msk =
(sk
1
, . . . , sk
n
).
2. Enc(mpk, x): The Encryption algorithm Enc,
takes as input the master public key mpk and
a vector x and outputs c = {c
1
, . . . , c
n
}, where
c
i
= Enc(pk
i
, x
i
).
3. KeyGen(msk): The Key Generation algorithm
takes as input the master secret key msk and out-
puts a functional key sk as sk =
∑
n
1
sk
i
.
4. Dec(sk, c): The Decryption Algorithm takes as in-
put the functional key sk and an encrypted vector
c and outputs PKE.Dec
sk,
n
∑
i=1
c
!
.
Theorem 1. Let PKE = (Gen, Enc, Dec) be an IND-
CPA secure public-key encryption scheme that is both
additive key and cipher homomorphic. Moreover, let
MIFE be the generic multi-input Functional Encryp-
tion scheme for the summation of a vector’s compo-
nents presented in (Bakas et al., 2022b), that can be
instantiated from PKE. Then MIFE is s-IND-FE-CPA
secure.
The proof of Theorem 1 is provided in section 7.
4 INSTANTIATION FROM ECC -
FORMAL CONSTRUCTION
4.1 Instantiation from ECC
We introduce a construction relying on the Additive
Ciphertext and Key homomorphic properties as per
definitions 2 and 3. In short, an ElGamal ciphertext
for a message x is given by:
Enc(x) = (P, Q) = (rG, xG + rY ), (7)
where r is sampled randomly in Z
∗
N
, N is the order
of the curve, G is a generator of the curve and Y is
the public key. As we see, each ciphertext consists
of two points on the curve. Thus, we need to define
a new operation that will allow us to add ciphertexts
together:
Randomness Re-Use. In a setting involving multi-
ple clients, ElGamal maintains its security even when
the same random value r is reused, as shown in (Bel-
lare et al., 2002). This differs from the traditional
single-client ElGamal setup, where reusing the same
randomness r would compromise security. However,
in scenarios with n > 1 distinct key pairs, this vulner-
ability does not apply.
Definition 9 (Addition of Elgamal Ciphertexts over
Elliptic Curves). Assuming that we have two mes-
sages x
1
and x
2
with corresponding ciphertexts
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
66

Enc(x
1
) and Enc(x
2
), we define the following oper-
ation, denoted by ⊕:
Enc(x
1
) ⊕ Enc(x
2
) = (rG, x
1
G + rY
1
)
⊕ (rG, x
2
G + rY
2
)
= (2rG, (x
1
+ x
2
)G + r(Y
1
+ Y
2
))
= (P
′
, Q
′
),
(8)
where the ‘+’ symbol on the right side of the equation,
denotes the standard addition and P
′
, Q
′
∈ E.
To prove that the generic MIFE construction can
be instantiated from ElGamal over ECC, all we need
to do is prove that the ECC variation of ElGamal is
both ACH and AKH as per definitions 2 and 3. In
particular, we prove the following theorem;
Theorem 2. Let MIFE be the generic multi-input
functional encryption scheme presented in (Bakas
et al., 2022b). Then, it is possible to instantiate MIFE
using ElGamal’s variation over elliptic curves as the
public-key encryption scheme PKE.
Proof. As already stated, we prove that ElGamal’s
variation over elliptic curves is both additive key and
cipher homomorphic as per definitions 2 and 3.
• Additive Key Homomorphic. Let s
1
, . . . , s
n
∈
GF(p) be n private keys and Y
1
, . . .Y
n
be their re-
spective public keys. Recall that Y
i
:= s
i
G, i ∈ [n].
Therefore,
n
∑
i=1
Y
i
=
n
∑
i=1
s
i
G =
n
∑
i=1
s
i
!
· G
Since GF(p) is closed under addition,
∑
n
i=1
s
i
∈
GF(p). Hence,
∑
n
i=1
s
i
is a valid secret key and
∑
n
i=1
Y
i
is a valid corresponding public key by con-
struction. Thus, the variation of ElGamal over el-
liptic curves is additive key homomorphic.
• Additive Cipher Homomorphic. Let x
1
, . . . x
n
∈
GF(p) be n measurements and c
1
, . . . c
n
be their
respective ciphertexts. Recall that c
i
:= (rG, x
i
G+
rY ), i ∈ [n], for a randomness r ∈ Z
∗
N
and the pub-
lic key Y ∈ E. Therefore,
n
M
i=1
c
i
=
n
M
i=1
(rG, x
i
G + rY)
=
n
∑
i=1
rG,
n
∑
i=1
x
i
G +
n
∑
i=1
rY
!
=
(nr) · G,
n
∑
i=1
x
i
G + (nr) ·Y
!
,
where ⊕ is the operation defined in equation 8.
Hence,
L
n
i=1
c
i
is a valid encryption of
∑
n
i=1
x
i
for
the same public key Y and a randomness nr ∈ Z
∗
N
– since Z
∗
N
is closed under addition – and thus the
variation of ElGamal over elliptic curves is addi-
tive cipher homomorphic.
A direct result of Theorem 1 and Theorem 2, is
that our instantiation is s − IND − FE −CPA-secure
as per definition 7.
4.2 System Model
Before presenting the formal use case of the proposed
construction, we first provide a description of the sys-
tem model we consider. Our setup consists of four
entities: (i) Edge Devices (ED), (ii) Data Owner (O),
(iii) Storage Server (SS), and (iv) Analyst (A).
• Edge Devices (ED). Let D = {d
1
, . . . , d
n
} be a set
of resource-constrained sensor devices deployed
in an environment to collect data x. Each device
encrypts collected data and sends it to the storage
server.
• Data Owner (O). We assume the existence of a
fully trusted data owner O, who administers and
is responsible for a set of edge devices in a spe-
cific environment. O is responsible for generating
functional decryption keys for the particular func-
tion for data collected by the devices.
• Storage Server (SS). We assume the existence
of a storage server SS, an abstract external stor-
age platform that will store encrypted data re-
ceived from each device d
i
. Once access to data
is requested, SS returns the data to the requesting
party.
• Analyst (A). Let A be an entity that wishes to
learn the result of a specific function computed for
the encrypted data collected from a set of devices
D
′
such that D
′
⊆ D.
5 USE CASE PROTOCOL
We now formally describe a detailed protocol to
demonstrate the applicability of the proposed con-
struction. For this use case, we consider a scenario
where a device owner O possesses n number of sen-
sor devices (d
1
, . . . , d
n
). Additionally, we assume the
existence of a storage server SS where encrypted data
from the sensor nodes will be stored. A complete
overview of the protocol is illustrated in Figure 2. In
the proposed use case, each device d
i
collects envi-
ronmental or event data x
i
, encrypts, and uploads the
Need for Speed: Leveraging the Power of Functional Encryption for Resource-Constrained Devices
67
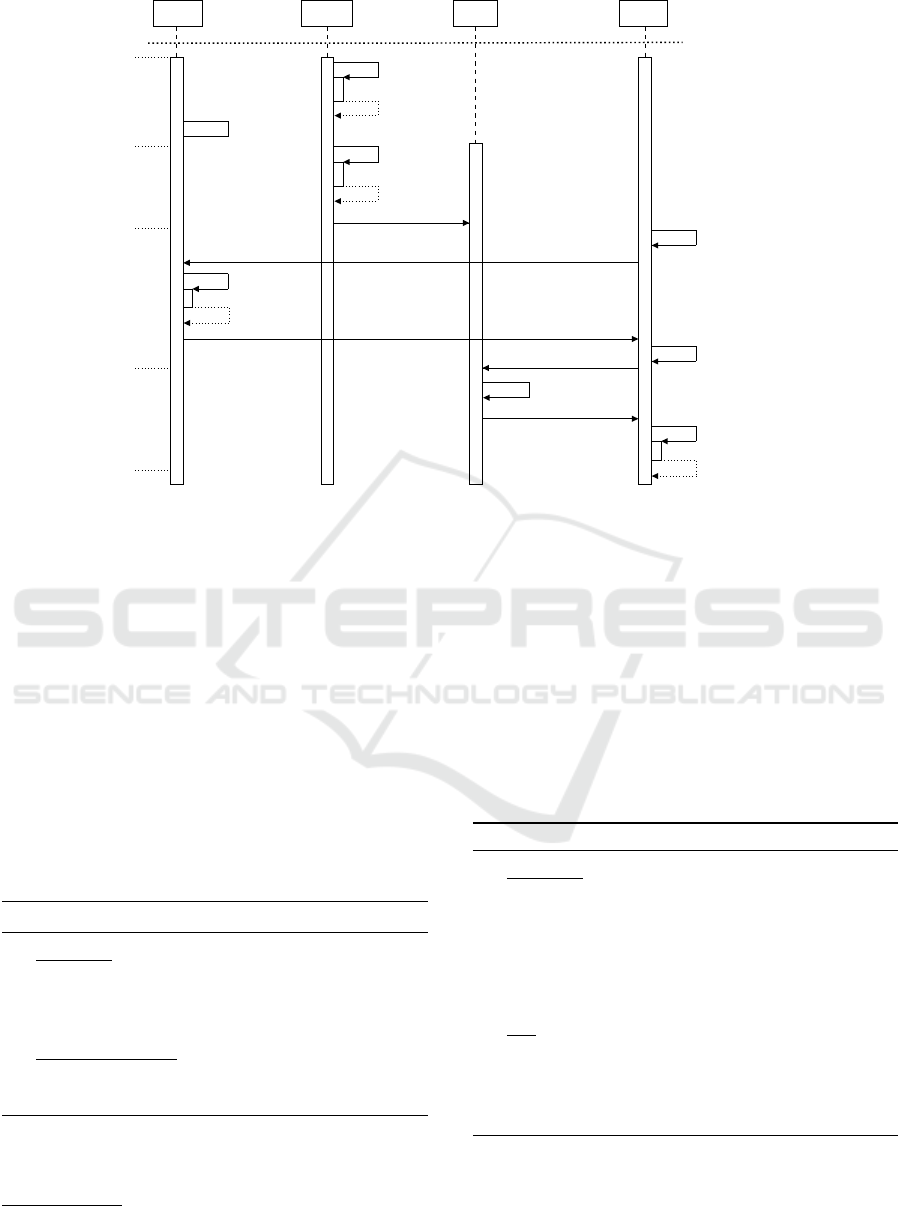
Owner Device SS Analyst
Setup
Encryption
KeyGen
Decryption
Generate Keypair
s
i
, Y
i
msk, mpk
Run Enc
c
i
m
1
= ⟨t
1
, c
i
, σ
d
i
(H(t
1
∥ c
i
))⟩
Generate Request
m
2
= ⟨t
2
, req
f
, σ
A
(H(t
2
∥ req
f
))⟩
Generate Decryption Key
sk
f
m
3
= ⟨t
3
, c
sk
f
, σ
O
(H(t
3
∥ c
sk
f
))⟩
Request Data
m
4
= ⟨t
4
, req
data
, σ
A
(H(t
4
∥ req
data
))⟩
Compute c
res
m
5
= ⟨t
5
, c
res
, σ
SS
(H(t
5
∥ c
res
))⟩
Run Dec
M
res
Figure 2: Use Case Protocol Overview.
data to SS. The main building blocks of our protocol
are as follows:
• An IND-CCA2 secure public key encryption
scheme PKE = (Gen, Enc, Dec);
• An EUF-CMA secure signature scheme S =
(sign, veri f y);
• A first and second pre-image resistant crypto-
graphic hash function H;
• A synchronized clock between all entities.
As a first step, each device d
i
runs the MIFE.Setup
algorithm to generate a private/public key pair (s
i
,Y
i
)
for ElGamal’s cryptosystem. On completion, O com-
putes msk and mpk as demonstrated in algorithm 1
1
.
Algorithm 1: Setup(1
λ
, n).
Device d
i
:
1: Generate n private keys as s
i
$
←− GF(p)
2: For each s
i
, generate the corresponding public
key as Y
i
= s
i
G ∈ E
Device Owner O:
3: Output msk as msk = (s
1
, . . . , s
n
)
4: Output mpk as mpk = (Y
1
, . . . ,Y
n
)
Subsequently, we assume that each device d
i
gener-
ates some data x
i
, e.g. generated data about an event.
1
Note: we assume the data owner has secure access to
the key pair generated by each device in its ownership.
Upon generation, d
i
computes f
map
(x
i
), samples a
random r and encrypts it as shown in line 5 of Algo-
rithm 2 to get c
i
. Finally, the encrypted measurement
is outsourced to SS via:
(9)m
1
= ⟨t
1
, c
i
, σ
d
i
(H(t
1
∥c
i
))⟩,
where t
1
is a timestamp and σ
d
i
is d
i
’s signature. Upon
reception, SS verifies the freshness and the integrity
of the message m
1
by checking the timestamp and the
signature, respectively. SS outputs ⊥ and aborts the
protocol if any verification fails. Otherwise, it will
store all c
i
.
Algorithm 2: Enc(mpk, c = (c
1
, . . . , c
n
)).
1: Device d
i
:
2: Generate a measurement m
i
∈ GF(p)
3: Compute f
map
(m
i
) = m
i
G = M
i
∈ E
4: Pick a random r ∈ Z
∗
N
, where N is the order of
the curve
5: c
i
= Enc(m
i
) = (P, Q) = (rG, M
i
+ rY
i
)
6: Send m
1
= ⟨t
1
, c
i
, σ
d
i
(H(t
1
∥c
i
))⟩ to SS
7: SS:
8: Verify the freshness and the integrity of m
1
9: If any verification fails, output ⊥ and abort the
protocol
10: Store c
i
On completion of the encryption phase, we as-
sume that an analyst A wishes to compute a function
on encrypted data collected by D
′
stored on SS. To
do so, A first requests permission from O to do so by
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
68

sending a request of the following form:
(10)m
2
= ⟨t
2
, req(f), σ
A
(H(t
2
∥req(f))⟩,
where req(f) denotes a request for the specific func-
tion f . Upon reception, O verifies the freshness and
integrity of the message. If any verification fails. O
outputs ⊥ and aborts the protocol. Otherwise, O first
computes the functional decryption key sk
f
for the
specific function by running the MIFE.KeyGen algo-
rithm as described in Algorithm 3. As a next step, O
encrypts sk
f
using the public key of the analyst A to
get a ciphertext c
sk
f
, and finally sends it to A via the
following message:
(11)m
3
= ⟨t
3
, c
sk
f
, σ
O
(H(t
3
∥c
sk
f
))⟩
Algorithm 3: KeyGen(msk).
1: Analyst A:
2: Send a request for a functional decryption key, for
a function f , to the data owner via m
2
3: Data Owner O:
4: Verify the freshness and the integrity of m
2
5: If any verification fails, output ⊥ and abort the
protocol.
6: Otherwise, compute the functional decryption
key sk
f
as sk
f
=
∑
n
1
s
i
7: Send sk
f
to A via m
3
Finally, and upon successful completion of the
previous algorithm, A holds the functional decryption
key sk
f
. At this point, A sends a request for the en-
crypted data to the SS via:
(12)m
4
= ⟨t
4
, req(data), σ
A
(H(t
4
∥req(data)))⟩
where req(data) denotes a request for encrypted
data collected by the set of devices D
′
. Upon re-
ception, SS will verify the message’s integrity and
freshness. SS will output ⊥ and abort the protocol
if the verification fails. Otherwise, SS will compute
c
res
=
L
n
i=1
c
i
= (P
res
, Q
res
) and reply to A with the
following message:
(13)m
5
= ⟨t
5
, c
res
, σ
SS
(H(t
5
∥c
res
)) .
Upon reception, A will verify the freshness and in-
tegrity of the message. If the verification fails, A will
output ⊥ and abort the protocol. Otherwise, A will
run the functional decryption algorithm as shown in
algorithm 4 using sk
f
to recover f (x
1
, . . . , x
n
) =
∑
n
1
x
i
.
Possible Extension. Our protocol can be enhanced
to also facilitate the verification of the decryption pro-
cess. This feature is crucial as it paves the way for
addressing stronger threat models. In particular, if we
assume a malicious adversary that colludes with SS,
Algorithm 4: Dec(sk
f
, c
1
, . . . , c
n
).
Analyst A:
1: Send a request for the encrypted data to SS via
m
4
Storage Server SS:
2: Verify the freshness and the integrity of m
4
3: If any verification fails, output ⊥ and abort the
protocol
4: Otherwise compute the sum of the ciphertexts as
c
res
=
L
n
i=1
c
i
= (P
res
, Q
res
), where P
res
, Q
res
∈ E
5: Send c
res
to A via m
5
Analyst A:
6: Verify the freshness and the integrity of m
5
7: If any verification fails, output ⊥ and abort the
protocol
8: Otherwise Compute n
−1
the modular inverse of n
in GF(p)
9: Compute −
n
−1
sk
f
· P
res
+ Q
res
to get X
res
∈ E
10: Run f
−1
map
(X
res
) = x
1
+ ·· · + x
n
∈ GF(p)
there’s a potential risk of releasing manipulated statis-
tics to deceive data analysts. We, therefore, argue
about the importance of an analyst, possessing only
{
Y
i
}
i∈[1,n]
, c
res
, and X
res
, confirming that f
−1
map
(X
res
)
matches
∑
n
i=1
x
i
, without additional information dis-
closures. Note that this verification can be performed
in a zero-knowledge fashion without access to the
master secret key or the functional decryption key cor-
responding to the function. More specifically, it re-
lies on a zero-knowledge proof related to a discrete
logarithm over an elliptic curve. However, the topic
of conducting zero-knowledge proofs on devices with
limited resources is not studied in this work and is left
as future work.
6 SECURITY ANALYSIS AND
THREAT MODEL
In this section, we define a threat model as a list of
attacks on our protocol and prove that our protocol is
secure against these attacks. The security analysis of
the construction relies on Theorem 1 and is proven
in section 7. Additionally, the detailed security anal-
ysis of the protocol is provided in subsection 6.1.
Now, to evaluate the security of our construction, we
consider an active adversary ADV as a probabilistic
polynomial time (PPT) algorithm and estimate its ca-
pabilities by a set of attacks she might try to launch.
We assume that ADV can interact with the messages
m
1
, . . . , m
5
and model her capabilities by the follow-
ing attacks.
Need for Speed: Leveraging the Power of Functional Encryption for Resource-Constrained Devices
69

Attack 1 (Substitution Attack). Let ADV be a PPT
adversary. ADV successfully performs a Substitu-
tion Attack on a message m
i
if she manages to replace
m
i
by m
ADV
i
in an indistinguishable way.
Attack 2 (Replay Attack). Let ADV be a PPT adver-
sary. ADV successfully launches a Replay Attack if
she can send an outdated message m
i
to a valid recip-
ient and convinces it that this message is fresh.
6.1 Security Analysis
Based on the threat model defined in section 6, we
consider an active adversary A who can interact at
each protocol step through the messages m
1
, . . . m
5
.
To demonstrate the security of our protocol, we prove
the following theorem:
Theorem 3. Let PKE = (Gen, Enc, Dec) be an IND-
CCA2 secure public key encryption scheme and
S = (sign,veri f y) be an EUF-CMA secure signature
scheme. Let H be a first and second pre-image re-
sistant cryptographic hash function, and assume that
there exists a synchronized clock between all entities.
Under these assumptions, our protocol defined in sec-
tion 5 is secure against an active PPT adversary A for
the threat model section 6.
Proof. We successively consider the attacks defined
earlier in our threat model.
Substitution Attack Soundness. Let S and R be
two distinct parties in the set {ED, O, SS, A} and
m
1
, . . . , m
5
be the messages sent during the protocol.
Remark that a message m
i
sent from S to R is of
the form m
i
= ⟨t
i
, x, σ
S
(H(t
i
∥x))⟩, where x is either
a ciphertext or a request. To successfully perform a
Substitution Attack, ADV intercepts m
i
sent by S
to R and replace x by x
ADV
. Assume that ADV is
able to generate a valid value for x
ADV
. To replace
σ
S
(H(t
i
∥x)) by σ
S
(H(t
i
∥x
ADV
)), ADV has to forge
the signature σ
S
. Since S is EUF-CMA, this can only
happen with a negligible probability. Thus, if λ is the
security parameter for S, the adversary’s advantage
for this attack is ε
1
= negl(λ).
The proof for the security against replay attack is
similar since it also relies on the unforgeability of the
signature.
Replay Attack Soundness. Let S and R be two
distinct parties in the set {ED, O, SS, A} and
m
1
, . . . , m
5
be the messages sent during the protocol.
Remark that a message m
i
sent from S to R is of
the form m
i
= ⟨t
i
, x, σ
S
(H(t
i
∥x))⟩, where x is either
a ciphertext or a request. To successfully perform a
Replay Attack, ADV eavesdrops on a message m
i
sent by S to R , store it, and send it again to R later
without him noticing that the message is outdated.
To do so, she needs to convince R that m
i
is fresh
by updating the timestamp t
i
to t
j
, i ̸= j. However,
to replace t
i
by t
j
in σ
S
(H(t
i
∥x)), ADV has to forge
the signature σ
S
. Since S is EUF-CMA, this can only
happen with a negligible probability. Thus, if λ is the
security parameter for S, the adversary’s advantage
for this attack is ε
2
= negl(λ).
Since the finite sum of negligible functions is also
a negligible function, the overall advantage of an ad-
versary ADV on this protocol is ε = negl(λ).
Now we provide the proof of the Theorem 1. Re-
mark that this proof is already provided in (Bakas
et al., 2022b) for the general construction; hence, we
follow its outline and address the specific case of ad-
dition.
7 PROOF OF THEOREM 1
Proof. Let PKE = (Gen, Enc, Dec) be a public-key
encryption scheme and A and B be two independent
PPT algorithms. We set game 1 as the game for PKE
shown in Definition 4, in which B is the adversary for
a challenger C . Besides, we set game 2 as the game
for MIFE shown in Definition 7, in which A is the
adversary and B is the challenger.
Setup of Game 1. The adversary B randomly sam-
ples an element x in the message space of PKE and
sends it to the challenger C . The latter generates a
pair of keys (pk
C
, sk
C
) ← PKE.Gen(1
λ
), randomly
picks b ←- {0, 1} and sends back both pk
C
and c
b
←
PKE.Enc(pk, b · x) to B.
Generation of Keys for Game 2. First of all, B
calls A, who provides two messages x
0
and x
1
such
that:
n
∑
i=1
x
0,i
=
n
∑
i=1
x
1,i
(14)
B generates a basis for a vector space V ∈ M
such that ∀x ∈ V ,
∑
n
i=1
x
i
= 0 in order to ensure
that every decryption key query will be made for
vectors x
0
, x
1
such that
∑
n
i=1
x
1,i
=
∑
n
i=1
x
0,i
. She
samples n − 1 independent vectors r
1
, . . . , r
n−1
, such
that ∀i ∈ [n − 1], r
i
is independent of x
1
− x
0
and
sets the basis to (x
1
− x
0
, r
1
, . . . , r
n−1
). ∀i ∈ [n], set
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
70

α
i
=
x
1,i
−x
0,i
∥x
1
−x
0
∥
2
2
. This construction induces the canoni-
cal vectors e
i
=
α
i
· (x
1
− x
0
) +
∑
n−1
1
r
j
. Finally, B
produces (pk
α
j
, sk
α
j
) ← PKE.Gen(1
λ
), ∀ j ∈ [1, n − 1]
and sets:
pk
i
= α
i
·pk
C
+
n−1
∑
j=1
pk
α
j
and mpk = (pk
1
, . . . , pk
n
).
Remark that the associated secret keys sk
i
= α
i
·
sk
C
+
∑
n−1
1
sk
α
j
are unknown from B, who does not
know sk
C
. In the end, the challenger B sets the func-
tional decryption key to sk =
∑
n−1
j=1
sk
α
j
using the pre-
vious construction.
Challenges for Game 2. The adversary A sends x
0
and x
1
such that
∑
n
i=1
x
0,i
=
∑
n
i=1
x
1,i
. B samples at
random β ←- {0, 1}. In theory, she should pick x
β
and
send back its encryption. However, in order to break
the game 1, she instead computes:
c = α · c
b
+ PKE.Enc
n−1
∑
j=1
pk
α
j
, 0
!
+ PKE.Enc(0, x
β
)
(15)
and sends c to A. Finally, the latter outputs a guess
for β. If her guess is correct, then B guesses that C
encrypted 0. If not, B guesses that C encrypted x. We
treat those cases separately.
If C encrypted 0, then equation 15 becomes:
c = PKE.Enc(α · pk
C
, 0)
+ PKE.Enc
n−1
∑
j=1
pk
α
j
, 0
!
+ PKE.Enc(0, x
β
)
= PKE.Enc(α · pk
C
+
n−1
∑
j=1
pk
α
j
+ 0, 0 + 0 + x
β
)
= PKE.Enc(pk
i
, x
β
)
In this case, B simulates a perfect view of the
environment for A. Therefore, if A guesses β in
game 2 with an advantage ε
A
, B, guesses b in game
1 with an advantage ε
B
. Finally, ε
A
= ε
B
.
If C encrypted x, then equation 15 becomes:
c = PKE.Enc(α · pk
C
, α · x)
+ PKE.Enc
n−1
∑
j=1
pk
α
j
, 0
!
+ PKE.Enc(0, x
β
)
= PKE.Enc(α · pk
C
+
n−1
∑
j=1
pk
α
j
+ 0, α · x + 0 + x
β
)
= PKE.Enc(pk
i
, α · x + x
β
)
Since α =
x
1
−x
0
∥x
1
−x
0
∥
2
2
, we have
α · x + x
β
=
x
∥x
1
− x
0
∥
2
2
(x
1
− x
0
) + x
β
=
x
∥x
1
− x
0
∥
2
2
(x
1
− x
0
) + x
0
+ β(x
1
− x
0
)
If we set µ :=
x
∥x
1
−x
0
∥
2
2
+ β, we obtain c =
PKE.Enc(pk
i
, µ ·x
1
+(1 −µ) ·x
0
), which corresponds
to the challenge ciphertext. Remark that µ · x
1
+ (1 −
µ)x
0
is well defined, as a linear combination of ele-
ments of the vector space V with unitary norm. Fi-
nally, the value of β being hidden, the advantage ε
B
of B is negligible.
Conclusion. The overall advantage of B on game 1
is thus ε
B
= ε
A
, which means that the adversary A
can break our MIFE protocol if B is able to break the
PKE construction. By contraposition, since PKE is
IND-CPA secure, our construction is also IND-CPA
secure, which concludes.
8 EXPERIMENTAL EVALUATION
This section provides an evaluation of our proposed
construction’s performance and energy efficiency on
two commercially available resource-constrained de-
vices. To this end, our test bed consisted of the
two sensor devices: an Arm Cortex-M4 nrf52840dk
board
2
, and an ARM Cortex-M3 Zolertia Re-Mote
board
3
. For the rest of this section, we refer to the
nrf52840dk board as nrf and the Zolertia Re-Mote
board simply as zolertia. Additionally, to provide
a more comprehensive evaluation of our implemen-
tation, we measured its performance on a standard
Desktop – referred to as standard.
Experiment Testbed
• zolertia: A 32 MHz ARM Cortex-M3 Zolertai Re-Mote RevB
board. Configuration: [512KB Flash, 32KB RAM].
• nrf: A 64 MHz ARM Cortex-M4 nrf52840dk board. Configura-
tion: [1MB Flash, 32KB RAM]
• standard: An Intel Core i7-4790 desktop running Ubuntu 20.04
LTS. Configuration: [8 CPUs, 16GB RAM].
To test the necessary functions, we developed a
Contiki-NG (Oikonomou et al., 2022) application us-
ing the c25519
4
cryptographic library for all crypto-
graphic operations. Due to the resource constraints
2
https://www.nordicsemi.com/Products/Development-
hardware/nrf52840-dk
3
https://docs.contiki-ng.org/en/develop/doc/platforms/
zolertia/Zolertia-RE-Mote-platform-(revision-B).html
4
https://www.dlbeer.co.nz/oss/c25519.html
Need for Speed: Leveraging the Power of Functional Encryption for Resource-Constrained Devices
71
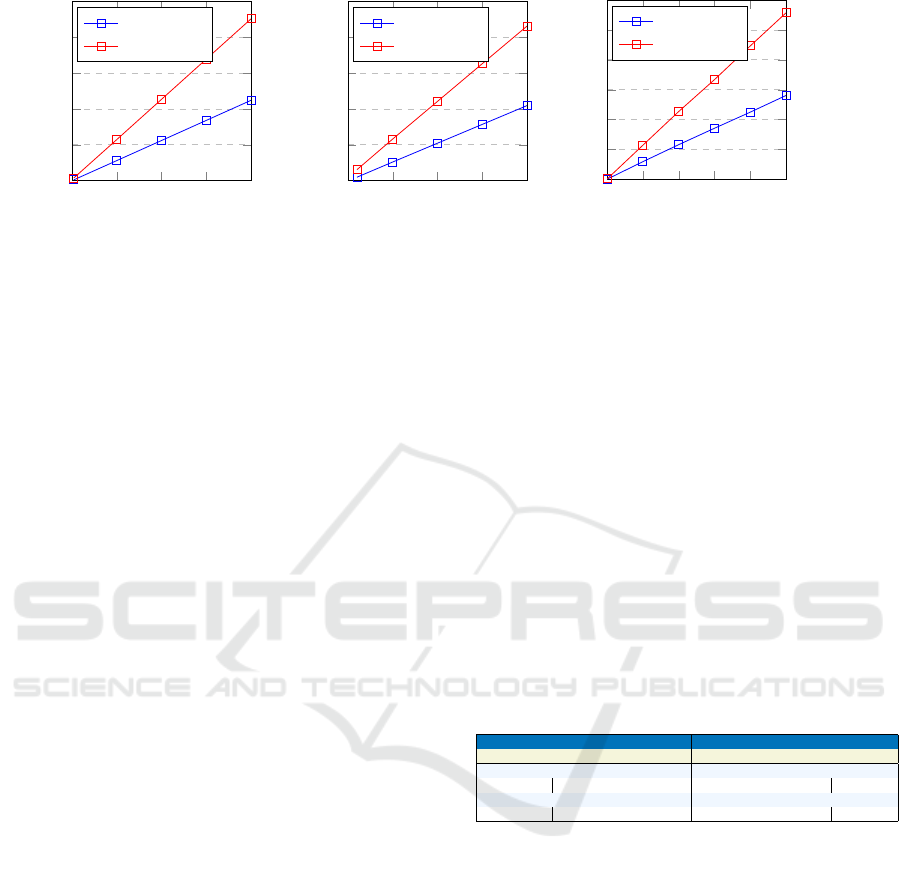
0
25 50 75
100
0
40
80
120
160
200
Number of inputs
Time (seconds)
Setup
Encryption
Figure 3: nrf.
0
5
10
15
20
0
40
80
120
160
200
Number of inputs
Time (seconds)
Setup
Encryption
Figure 4: Zolertia.
0 200 400
600
8001,000
0
1
2
3
4
5
6
Number of inputs
Time (seconds)
Setup
Encryption
Figure 5: Standard.
of the devices involved in these experiments, we fo-
cused primarily on analyzing the execution times and
energy consumption of each algorithm. Also, for each
device, we implemented all the algorithms introduced
in section 5, i.e. instead of limiting our evaluations
to only algorithms that a resource-constrained device
would ideally execute, we executed all algorithms on
each device to demonstrate the overall efficiency of
our work. All programming for this section was writ-
ten in C, and each experiment was conducted 50 times
with the average results taken.
8.1 Performance of Cryptographic
Algorithms
To measure the performance of our work, we primar-
ily focused on the computational performance of each
algorithm. More precisely, we measured each de-
vice’s time to execute a specific algorithm success-
fully. In Contiki-NG, the system time is measured in
CPU ticks and is represented as long unsigned val-
ues. As a result of this implementation feature, all
performance values observed from our experiments
were recorded in ticks and converted to seconds. The
specific figures were derived by dividing the num-
ber of recorded ticks by 128 (CPU ticks per second
is 128, as defined in Contiki-NG). For these experi-
ments, we resorted to the use case protocol described
in section 5, which we used as the basis of our eval-
uations. However, we did not measure the compu-
tational costs of the public key encryption and se-
cure signature schemes used to provide confidential-
ity and authentication of the exchanged messages or
any communication costs involved.
First, we assume that each device executes the
Setup and Encrypt ion algorithms. Subsequently, we
consider a scenario where a device, upon receiving
n number of ciphertexts, where n ∈ [2, 100] executes
the Keygen algorithm, and finally, the Decryption al-
gorithm to retrieve the results in plain. Overall, it
took the nrf board 0.97 seconds to run Setup, 3.07
seconds to run Encryption, and 1.22 seconds to run
the Decryption for 2 ciphertexts. For the zoler-
tia board, the execution times were 3.9 seconds for
Setup, 12.3 seconds for Encryption, and 5.41 seconds
for Decryption for 2 ciphertexts. Finally, on the stan-
dard machine, the execution times were 0.005 sec-
onds for Setup, 0.015 seconds for Encryption, and
0.006 seconds to run the Decryption algorithm for 2
ciphertexts (Table 1). The KeyGen algorithm was ex-
ecuted for all devices with negligible computational
overhead (e.g., for both zolertia and nrf boards, it
registered 0 ticks). These results show that the cost
of generating the functional decryption key using the
KeyGen algorithm did not incur any computational
overhead. Additionally, the most expensive algorithm
for all devices is the Encryption algorithm, which in-
volves three ECC point multiplications (Algorithm 2).
Table 1: Function Execution Times.
nrf zolertia standard
Functions CPU Ticks Time(sec) CPU Ticks Time(sec) Time(sec)
Setup 125 0.97 506 3.9 0.005
Encryption 393 3.07 1577 12.3 0.015
KeyGen 0 0 0 0 0.000
Decryption 156 1.22 693 5.41 0.006
As a next step, we measured the cost of execut-
ing the Setup and Encryption algorithms for a varying
number of inputs from 1 to 100 on the nrf board (Fig-
ure 3), 1 to 20 on the zolertia board (Figure 4), and 1
to 1000 on the standard machine (Figure 5). Exper-
iments on the zolertia board were limited to 20 due
to memory constraints; the board froze when we tried
to allocate memory for more than 20 key pairs and
ciphertexts. To generate 100 unique key pairs by exe-
cuting the Setup algorithm, it took the nrf 89.82 sec-
onds, while it took the zolertia board 83.9 seconds to
generate 20 unique key pairs. On the other hand, the
standard device required only 2.81 seconds to gener-
ate 1000 unique key pairs. Meanwhile, the nrf board
encrypted 100 inputs in 180.84 seconds, the zolertia
board encrypted 20 data inputs in 172.7 seconds, and
the standard device encrypted 1000 data inputs in 5.58
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
72

seconds. The cost of executing the Encryption algo-
rithm continued to be the most expensive operation
compared to the Setup algorithm. In our use case sce-
nario, we note that the device is only responsible for
running the Encryption algorithm.
Finally, we measured the execution times of the
KeyGen and Decryption functions for n number of ci-
phertexts, where n ∈ [2, 100]. Once again, due to re-
source constraints of the zolertia board, we could only
run both functions for 20 ciphertexts. From our exper-
iments, we observed that as the number of ciphertexts
increased, there were negligible increases in the exe-
cution time of the Decrypt ion function. For exam-
ple, the nrf board executed the Decryption function
for two ciphertexts in 1.22 seconds and 1.39 seconds
for 100 ciphertexts. Likewise, the standard machine
executed the Decryption function in 0.006 seconds for
two ciphertexts and 0.014 seconds for 1000 cipher-
texts. The results from this section prove that our pro-
posed construction is practical and efficient when de-
ployed on devices with very limited resources, much
like the devices used in our experiments.
Table 2: Energy Consumption.
nrf zolertia
Functions Time (s) Energy (mJ) Time (s) Energy (mJ)
Setup 0.97 18.2 3.9 468
Encryption 3.07 57.7 12.3 1476
KeyGen 0 0 0 0
Decryption 1.22 22.9 5.41 649.2
8.2 Energy Consumption
In this phase of our evaluations, we utilized the En-
ergest module provided by Contiki-NG to measure
the energy consumption. The Energest module pro-
vides lightweight software-based energy estimations
for resource-constrained devices by monitoring the
operations of the device’s various hardware compo-
nents (i.e., CPU and Radio). The active modes dur-
ing our evaluations were the CPU active and radio lis-
tening. We observed that the energy measurements
correlate directly to the execution times of the under-
lying algorithms (i.e., the longer it takes to run an
algorithm, the more energy is consumed). To com-
pute the energy values, we utilized current consump-
tion values for CPU active and radio listening modes
of the chosen boards. Finally, we only focused on the
nrf and zolertia boards for these experiments as these
have constrained resources, and energy consumption
is essential. The nrf board used 18.2 mJ to run Setup,
57.7 mJ to run Encryption, and 22.9 mJ to execute the
Decryption for 2 ciphertexts. While the zolertia board
consumed 468 mJ for Setup, 1.476 J for Encryption,
and 649.2 mJ to execute Decryption for 2 ciphertexts
(Table 2). Once again, from these results, we observe
that our construction is energy efficient.
Finally, we acknowledge that our experiments
would have been more comprehensive if we com-
pared our evaluations with other implementations;
however, it is worth noting that we found no FE
schemes (including the construction in (Bakas et al.,
2022b)) capable of being implemented on our sensor
devices due to key size and memory constraints (one
of the motivating factors for this work).
Open Science and Reproducible Research. To
support open science and reproducible research, the
source codes used for our evaluations have been made
available online
5
.
9 CONCLUSION
As the use of resource-constrained devices in vital set-
tings becomes widespread, the need for secure solu-
tions continues to grow. In this work, we proposed
and implemented an efficient and lightweight Func-
tional Encryption scheme using ECC primitives. Our
scheme is capable of running on resource-constrained
devices without causing excessive energy consump-
tion or computational overhead. ECC primitives were
chosen because of their low memory requirements
and smaller key sizes. Our goal was to pave the way
for the future of resource-constrained devices to rely
less on traditional cryptography and instead leverage
the power and versatility of modern cryptographic
methods such as FE. By doing so, we aim to con-
tribute to the ongoing effort to incorporate security
measures into the Internet of Things ecosystem with-
out compromising its core functionality.
ACKNOWLEDGEMENTS
This work was funded by the HARPOCRATES
(No 101069535) and FACILITATE (No 101034366)
projects, Horizon Europe
REFERENCES
Abdalla, M., , D., Fiore, D., Gay, R., and Ursu, B. (2018).
Multi-input functional encryption for inner products:
Function-hiding realizations and constructions with-
out pairings. In Advances in Cryptology – CRYPTO
2018.
5
https://github.com/iammrgenie/sumFE v2
Need for Speed: Leveraging the Power of Functional Encryption for Resource-Constrained Devices
73

Abdalla, M., Bourse, F., De Caro, A., and Pointcheval,
D. (2015). Simple functional encryption schemes for
inner products. In IACR International Workshop on
Public Key Cryptography, pages 733–751. Springer.
Abdalla, M., Gay, R., Raykova, M., and Wee, H. (2017).
Multi-input inner-product functional encryption from
pairings. In Annual International Conference on
the Theory and Applications of Cryptographic Tech-
niques. Springer.
Bakas, A. and Michalas, A. (2020). Multi-input func-
tional encryption: efficient applications from symmet-
ric primitives. In IEEE 19th International Confer-
ence on Trust, Security and Privacy in Computing and
Communications (TrustCom), pages 1105–1112.
Bakas, A., Michalas, A., and Dimitriou, T. (2022a). Pri-
vate lives matter: A differential private functional en-
cryption scheme. In Proceedings of the Twelfth ACM
Conference on Data and Application Security and Pri-
vacy, CODASPY ’22, page 300–311, New York, NY,
USA. Association for Computing Machinery.
Bakas, A., Michalas, A., Frimpong, E., and Rabaninejad, R.
(2022b). Feel the quantum functioning: Instantiating
generic multi-input functional encryption from learn-
ing with errors. In Data and Applications Security
and Privacy XXXVI: 36th Annual IFIP WG 11.3 Con-
ference, DBSec 2022, page 279–299. Springer-Verlag.
Bakas, A., Michalas, A., and Ullah, A. (2020). (f) unc-
tional sifting: A privacy-preserving reputation system
through multi-input functional encryption. In Nordic
Conference on Secure IT Systems, pages 111–126.
Bellare, M., Boldyreva, A., and Staddon, J. (2002).
Randomness re-use in multi-recipient encryption
schemeas. In Desmedt, Y. G., editor, Public Key Cryp-
tography — PKC 2003, pages 85–99, Berlin, Heidel-
berg. Springer Berlin Heidelberg.
Boneh, D., Sahai, A., and Waters, B. (2011). Functional
encryption: Definitions and challenges. In Theory of
Cryptography Conference, pages 253–273. Springer.
Castelluccia, C., Chan, A. C.-F., Mykletun, E., and Tsudik,
G. (2009). Efficient and provably secure aggregation
of encrypted data in wireless sensor networks. ACM
Transactions on Sensor Networks, 5(3):1–36.
Darrel Hankers, S. and Vanstone, A. M. (2004). Guide to el-
liptic curve cryptography. Springer Professional Com-
puting, pages XX–312.
Dhanda, S. S., Singh, B., and Jindal, P. (2020). Lightweight
cryptography: A solution to secure iot. Wireless Per-
sonal Communications, 112(3):1947–1980.
Dubrova, E., N
¨
aslund, M., Selander, G., and Lindqvist, F.
(2018). Lightweight message authentication for con-
strained devices. Proceedings of the 11th ACM Con-
ference on Security and Privacy in Wireless and Mo-
bile Networks.
Frimpong, E., Bakas, A., Dang, H.-V., and Michalas, A.
(2020). Do not tell me what i cannot do! (the
constrained device shouted under the cover of the
fog): Implementing symmetric searchable encryption
on constrained devices. Proceedings of the 5th Inter-
national Conference on Internet of Things, Big Data
and Security.
Frimpong, E. and Michalas, A. (2020). Secon-ng: Im-
plementing a lightweight cryptographic library based
on ecdh and ecdsa for the development of secure and
privacy-preserving protocols in contiki-ng. Proceed-
ings of the 35th Annual ACM Symposium on Applied
Computing.
Frimpong, E., Rabbaninejad, R., and Michalas, A. (2021).
Arrows in a quiver: A secure certificateless group key
distribution protocol for drones. Secure IT Systems,
page 31–48.
Goldwasser, S., Gordon, S. D., Goyal, V., Jain, A., Katz, J.,
Liu, F.-H., Sahai, A., Shi, E., and Zhou, H.-S. (2014a).
Multi-input functional encryption. In Nguyen, P. Q.
and Oswald, E., editors, Advances in Cryptology –
EUROCRYPT 2014, pages 578–602, Berlin, Heidel-
berg. Springer Berlin Heidelberg.
Goldwasser, S., Gordon, S. D., Goyal, V., Jain, A., Katz, J.,
Liu, F.-H., Sahai, A., Shi, E., and Zhou, H.-S. (2014b).
Multi-input functional encryption. In Annual Interna-
tional Conference on the Theory and Applications of
Cryptographic Techniques, pages 578–602. Springer.
Goldwasser, S., Kalai, Y. T., Popa, R. A., Vaikuntanathan,
V., and Zeldovich, N. (2013). How to run turing ma-
chines on encrypted data. In Annual Cryptology Con-
ference, pages 536–553. Springer.
He, Z., Furuhed, M., and Raza, S. (2019). Indraj: digi-
tal certificate enrollment for battery-powered wireless
devices. Proceedings of the 12th Conference on Secu-
rity and Privacy in Wireless and Mobile Networks.
Lara-Nino, C. A., Diaz-Perez, A., and Morales-Sandoval,
M. (2018). Elliptic curve lightweight cryptography:
A survey. IEEE Access, 6:72514–72550.
Li, X., Chen, D., Li, C., and Wang, L. (2015). Secure
data aggregation with fully homomorphic encryption
in large-scale wireless sensor networks. Sensors,
15(7):15952–15973.
Oikonomou, G., Duquennoy, S., Elsts, A., Eriksson, J.,
Tanaka, Y., and Tsiftes, N. (2022). The Contiki-NG
open source operating system for next generation IoT
devices. SoftwareX, 18:101089.
Sahai, A. and Seyalioglu, H. (2010). Worry-free encryption:
functional encryption with public keys. In Proceed-
ings of the 17th ACM conference on Computer and
communications security, pages 463–472.
Sans, E. D., Gay, R., and Pointcheval, D. (2018). Reading
in the dark: Classifying encrypted digits with func-
tional encryption. IACR Cryptology ePrint Archive,
2018:206.
Ugus, O., Westhoff, D., Laue, R., Shoufan, A., and Huss,
S. A. (2009). Optimized implementation of ellip-
tic curve based additive homomorphic encryption for
wireless sensor networks. CoRR, abs/0903.3900.
Vinodha, D. and Mary Anita, E. A. (2018). Secure data ag-
gregation techniques for wireless sensor networks: A
review. Archives of Computational Methods in Engi-
neering, 26(4):1007–1027.
Wang, M., He, K., Chen, J., Du, R., Zhang, B., and Li, Z.
(2022). Panda: Lightweight non-interactive privacy-
preserving data aggregation for constrained devices.
Future Generation Computer Systems, 131:28–42.
Waters, B. (2015). A punctured programming approach to
adaptively secure functional encryption. In Annual
Cryptology Conference, pages 678–697. Springer.
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
74
