
Interoperable Access and Usage Control of Self-Sovereign Digital Twins
Using ODRL and I4.0 Language
Jiahang Chen
a
, Lennart Schinke
b
, Xuebilian Gong
c
, Martin Hoppen
d
and J
¨
urgen Roßmann
e
Institute for Man-Machine Interaction, RWTH Aachen University, Ahornstr. 55, 52074 Aachen, Germany
Keywords:
IoT, Interoperability, Access Control, Usage Control, Self-Sovereign Digital Twins, ODRL, I4.0 Language.
Abstract:
The trend in digital transformation catalyzes an increasing amount of Digital Twins (DTs) being intercon-
nected to share data and services. In this context, secured interconnections of DTs are a key foundation for
establishing a trustworthy environment, which necessitates fundamental technologies and concepts regarding
access control. Considering the layer of usage restrictions of data and services, traditional access control can
be extended to usage control. Here, diverse policy models utilized to formalize access and usage control result
in a lack of interoperability, especially in a decentralized Internet of Things (IoT). To address this issue, we
propose in this paper a concept that applies Open Digital Rights Language (ODRL) to describe access and
usage control policies in an interoperable way. Besides, we define a message-based communication protocol
based on Industry 4.0 (I4.0) language to flexibly enable interoperable interactions with policy engines. The
proposed concept is then integrated in an access and usage control management system and demonstrated in a
proof-of-concept manner. Here it is also shown why the proposed concept forms a basis for the implementa-
tion of self-sovereign Digital Twins (SSDTs).
1 INTRODUCTION
In the era of digital transformation, the explosion of
Digital Twins (DTs) (Singh et al., 2021; Tao et al.,
2018; Liu et al., 2021) in scale reveals their pivotal
potential in reshaping innovation across diverse do-
mains (Jones et al., 2020). These virtual counter-
parts, mirroring physical entities, are increasingly in-
terconnected to facilitate the seamless and transpar-
ent exchange of data and services, forming the back-
bone of technological advancement (VanDerHorn and
Mahadevan, 2021). Based on the concept of self-
sovereign identities (Preukschat and Reed, 2021),
self-sovereign Digital Twins (SSDTs) (Chen et al.,
2023) are proposed to promote a paradigm shift in
control dynamics. SSDTs empower assets to exercise
sovereignty, e.g., autonomy and authority in manag-
ing interconnections, using their digital counterparts.
When being interconnected, communication partici-
a
https://orcid.org/0000-0001-5970-6954
b
https://orcid.org/0009-0002-5632-5464
c
https://orcid.org/0009-0008-7372-6538
d
https://orcid.org/0000-0002-9021-1551
e
https://orcid.org/0000-0002-8780-855X
pants can be generally referred to as subject (i.e., the
initiator of the communication) and object (i.e., re-
spondent of the communication). Ensuring security
and interoperable access and usage control emerges
as a cornerstone for establishing trust and reliabil-
ity (Alam et al., 2011). Access control determines
which parties can access protected resources (Sama-
rati and de Vimercati, 2000). By integrating the layer
of usage restrictions, access control can be extended
to usage control that defines conditions (e.g., tempo-
ral and quantity limitations) regarding resources’ us-
age (Park and Sandhu, 2002). In both generalized
DTs and our specific SSDTs, robust access and us-
age control mechanisms are indispensable for safe-
guarding communication in terms of confidentiality,
integrity and availability of data and services. Our vi-
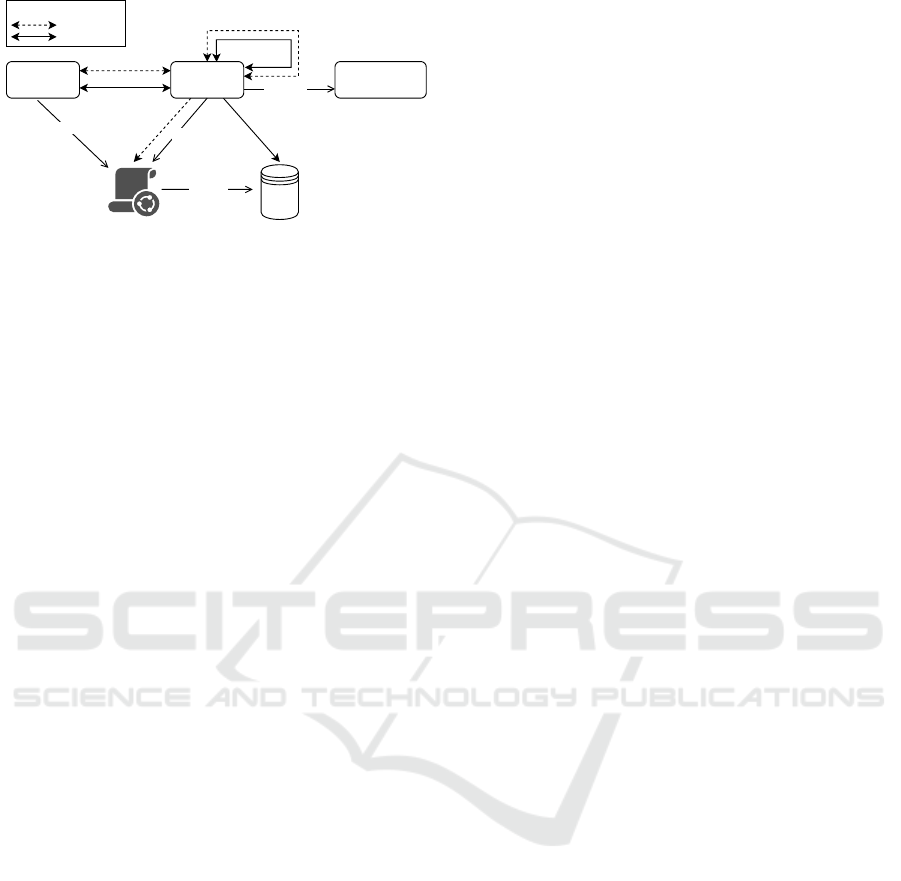
sion is interpreted in Figure 1. Here, SSDTs are posi-
tioned in the center to manage interconnections (e.g.,
from humans or other SSDTs) with the purpose of ac-
cessing the protected data resource. Additionally, it is
also possible to access the policies associated with the
resource. This is feasible because SSDTs can process
this access due to their full autonomy and authority
over their data and the attached interoperable policies.
Nonetheless, the state of the art faces a critical
Chen, J., Schinke, L., Gong, X., Hoppen, M. and Roßmann, J.
Interoperable Access and Usage Control of Self-Sovereign Digital Twins Using ODRL and I4.0 Language.
DOI: 10.5220/0012686500003705
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 9th International Conference on Internet of Things, Big Data and Security (IoTBDS 2024), pages 75-85
ISBN: 978-989-758-699-6; ISSN: 2184-4976
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
75
Humans
represent
SSDTs
attached
Physical
Assets
Legend
policy access
resource access
(ODRL-) Policy
Dataset
(Owners: Humans and/or SSDTs)
understand
understand
Figure 1: An overall diagram representing the full auton-
omy and authority of SSDTs in managing interconnections
regarding resources and the attached policies.
challenge since several years - interoperability - with
respect to policies and policy engines, see (Patil et al.,
2007; Alam et al., 2011; Azeez and Venter, 2013).
According to (Lee et al., 2021), there have not been
any standards proposed to enhance policy interoper-
ability. Although there are standardized models for
expressing access and usage control policies, it is
conceptually intricate for SSDTs governed by differ-
ent policy models to authorize each other effectively.
The reason for this is that they are not able to un-
derstand the structures and semantics of other access
control models (ACMs) (Alam et al., 2011; Esposito,
2018). For instance, an SSDT equipped with Role-
based Access Control (RBAC) (Sandhu, 1998) cannot
be requested to enforce authorization in a landscape
where SSDTs are managed using Attribute-based Ac-
cess Control (ABAC) (Hu et al., 2015). In fact, there
are also proposals which require a transformation of
access models into a certain one, like (Hafeez et al.,
2012). However, this increases the expense of imple-
mentation and enforces an understanding of the trans-
formation process. The same issue can be found in
the realm of usage control models (UCMs), see Sec-
tion 2.2. In addition, interacting with policies varies
depending on the implementation of the system ar-
chitectures. Overall, the absence of interoperability
may result in a fragmented Internet of Things (IoT)
ecosystem where data or functionalities cannot be
flexibly shared or reused, thereby limiting data analy-
sis and value extraction.
The emergence of Open Digital Rights Language
(ODRL) (Ianella, 2007), a standard language for ex-
pressing digital rights regarding permissions, obliga-
tions, and constraints, provides capabilities to enable
a formal description of policies. To bring the commu-
nication participants to the same level of interoper-
ability, a standardized interaction method is required,
e.g., via a message-based communication protocol.
The Industry 4.0 (I4.0) language standardized in VDI
2193-1 (Belyaev and Diedrich, 2019) delivers struc-
tures and vocabularies of messages (Kanaan et al.,
2023). This language is primarily intended for inter-
actions between I4.0 components. But due to its stan-
dardization, modular design, extendability, and the
adaptability for efficient data exchange (Belyaev and
Diedrich, 2019), the language can always be applied
for constructing the structures and types of communi-
cation messages for other uses (BMWi, 2018).
In this paper, our contribution is summarized as
follows. First, we present a conceptual framework
to enable formalization of interoperable access and
usage control policies on the basis of ODRL, allow-
ing to express rich rules and integrate various vocab-
ularies. For the interoperable communication of SS-
DTs regarding policy access, we define a message-
based communication protocol leveraging I4.0 lan-
guage. We then introduce an integrated access and us-
age control system architecture that incorporates the
proposed ODRL-based framework. Finally, we show
how the proposed concept provides a basis for SSDTs.
The presented paper is structured as follows: Sec-
tion 2 summarizes the state of the art. Followed by
Section 3, a concept is proposed. We demonstrate our
proof of concept in Section 4 and conclude the paper
in Section 5.
2 STATE OF THE ART
An overview of the state of the art is provided in this
section. This is intended to establish a basis for under-
standing and to identify the problem addressed in the
paper. Thus, Section 2.1 deals with ACMs and Sec-
tion 2.2 with UCMs. This is followed by an introduc-
tion to Digital Rights Expression Languages (DRELs)
in Section 2.3. Finally, this section closes with a dis-
cussion of the interaction with policies and policy en-
gines and the associated problems in Section 2.4.
2.1 Access Control Models
ACMs are utilized to formally structure and describe
polices that determine which parties are allowed to
access protected resources. Different types of ACMs
can be broadly categorized according to the right as-
signment mechanisms. In the following, we introduce
some of the widely-used ACMs (Zhang, 2023):
• In Discretionary Access Control (DAC), resource
owners assign permissions P directly to users U
(i.e., the identity of users) via P → 2
U
.
• Role-based Access Control (RBAC) (Sandhu,
1998) streamlines the management of permissions
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
76

P in a way that aligns with the roles R assigned to
users U. Here, U → 2
R
assigns a set of roles to
each user and access permissions are associated
with roles via R → 2
P
.
• Attribute-based Access Control (ABAC) (Hu
et al., 2015) manages resources R based on at-
tributes A =
{
a
1
, a
2
, ..., a
n
}
associated with users
U and R. Users grant permissions P via U × R →
{
Allow, Deny
}
.
• Capability-based Access Control (CapBAC) (Ma-
halle et al., 2013) associates capabilities C (e.g.,
API tokens and access tokens) with users U and
resources R. Using this model, Cap : U × R → 2
C
assigns a set of capabilities to each user-resource
pair.
• Access Control List (ACL) defines resources R
to specialized actions A (e.g., read and write)
and users U . Here, rules are defined as ACL =
{
(u, r, a) | u ∈ U, r ∈ R, a ∈ A
}
.
Literature research (Cai et al., 2019; Zhang et al.,
2018) reveals other types of ACMs conceptually dif-
fer in scope and depth. The diversity of ACMs results
primarily in heterogeneous adoption possibilities in
real-life setting. Here, the respective problems and
challenges related to interoperability remain to be an-
alyzed (Qiu et al., 2020).
2.2 Usage Control Models
UCMs describe what may be done with a resource.
They are, therefore, comparable to recursive ACMs,
which apply to every action associated with the re-
source during its usage. By this, UCMs extend ACMs
in two new aspects, the mutability of attributes and the
continuity of access decisions. The former means that
attributes can change over time, which can be seen as
an action related to the resource. This explains why
access decisions must be made continuously during
access. As long as the policy is satisfied, usage is
allowed. Otherwise usage is terminated (Lazouski
et al., 2010). Accordingly, from a data-centric per-
spective, policies are always attached to data. This
enables constant control over data usage (Jung and
D
¨
orr, 2022).
Among various proposed UCMs, the most promi-
nent one is the UCON
ABC
model which is consid-
ered as a family of core models consisting of 24 in-
dependent and primitive UCMs (Park and Sandhu,
2004). While other UCMs focus, for example, on spe-
cific languages like the Obligation Specification Lan-
guage (Hilty et al., 2007), UCON
ABC
remains on an
abstract level, regarding Authorizations (A), oBliga-
tions (B) and Conditions (C) that relate to attributes
of entities and resources. Authorization predicates
restrict the attributes of the entity and/or item, e.g.,
name of entity must be ”Frank” or type of item must
be ”.pdf”. Obligations define actions that must be ex-
ecuted by an entity before, during or after using an
item, e.g., an entity must delete a file after reading
it. Conditions include environmental restrictions that
must apply before or during usage, e.g., an item is
available for use in the EU only (Park and Sandhu,
2004; Lazouski et al., 2010; Sch
¨
utte and Brost, 2018).
The use of UCON
ABC
models facilitates the for-
mal expression of diverse policies and requirements.
Nevertheless, the practical implementation may pro-
ceed in various architectures or mechanisms (La-
zouski et al., 2010), as the aspect of policy implemen-
tation is not covered in this framework. Interoperabil-
ity between different implementations remains an an-
alytical concern that necessitates further examination
within the scope of deployment.
2.3 Digital Rights Expression
Languages
DRELs (Barlas, 2006) are languages designed for ex-
pressing rights (e.g., permissions and constraints) as-
sociated with digital content. MPEG-21 REL (Wang
et al., 2005), based on XML, enables the standard-
ized representation of digital rights associated with
multimedia content. The use of MPEG-21 REL is
quite limited in access and usage control due to its
specificity for multimedia domain. XrML (designed
for digital media, e-commerece, and intellectual prop-
erty management (Wang et al., 2002)) and RightsML
(designed for news and publishing industry (Kasdorf,
2015)) are faced with the same problem due to ap-
plication restrictions. In XACML, there is an offi-
cial policy language model used to express obliga-
tions and advice in addition to permissions. However,
this model doesn’t inherently support several ACMs
like RBAC (Ferrini and Bertino, 2009). Meanwhile,
the use of XACML represents a security risk for those
with a propagation feature to grant privileges to an-
other user, e.g., DAC and CapBAC (Ferraiolo et al.,
2016). In the context of UCMs, the XACML pol-
icy model necessitates enhancements to capture the
UCON
ABC
model adequately (Colombo et al., 2010).
This involves extending the original XACML policy
language model to integrate attribute mutability, per-
sistent policy evaluation, and to set conditions over
ongoing attribute updates and obligations. Overall,
for the applicability of ACMs and UCMs in XACML,
modifications are necessary to cater the authorization
requirements especially in decentralized landscapes,
as stated in (Masood et al., 2012).
Interoperable Access and Usage Control of Self-Sovereign Digital Twins Using ODRL and I4.0 Language
77

Literature review reveals the possibilities of us-
ing the ODRL information model to express different
ACMs. (Esteves et al., 2021) extend the ODRL profile
to model ACL to specify and enforce individual’s data
sharing preferences. (Alshamsi et al., 2023) propose
an approach to improve RBAC capability towards us-
age restrictions using the ODRL profile. However,
based on our observation, most research primarily fo-
cuses on the use of ODRL vocabulary and ontology
to enrich ACMs towards usage control (Steyskal and
Polleres, 2014). Only fewer consider the adoption ca-
pabilities of ODRL for expressive ACMs.
In the realm of UCMs, a variety of policy lan-
guages in the context of International Data Spaces
(IDS) (IDSA, 2023) ecosystems is notable. MYDATA
usage control technology has devised its own XML-
based policy language to articulate data usage restric-
tions (FraunhoferIESE, 2023). Concurrently, there is
also a policy language known as LUCON, designed
for controlling data flows between endpoints (Eitel
et al., 2021). The use of these technology-dependent
policy languages by different organizations makes
mutual understanding and cooperation among vari-
ous UCMs challenging. In IDS, stakeholders have
concurred on adopting ODRL, where policies are re-
ferred as Specification Level Policies, as opposed
to technology-dependent policies (e.g., MYDATA,
LUCON) as so called Implementation Level Poli-
cies (Hosseinzadeh et al., 2020; Jung and D
¨
orr, 2022).
2.4 Interaction with Policies and
Engines
Interactions with policies and engines rely on the
deployed system architectures, generally via APIs
or message-based protocols. In Open Policy Agent
(OPA) (OPA, 2023), communication aligns with
the defined OPA-specific REST APIs. Similarly,
(Moghaddam et al., 2016) proposed a policy man-
agement engine model that is reached via APIs. This
means, access to them requires an obligatory use and
understanding of the specific APIs. In XACML, de-
tails of the communication protocol and message for-
mats may vary between different XACML implemen-
tations. (Lee et al., 2015) proposed a RBAC system
for substation automation systems using XACML.
Here, the message-based communication protocol is
defined highly compatible to IEC 62351, a standard
for substation data security regarding RBAC. In LU-
CON, data flows are controlled through messages and
a rule-based engine, with a primary focus on message
labeling and routing (Sch
¨
utte and Brost, 2018). This
means that there is still an absence of a comprehen-
sive message-based protocol to cover semantics.
In the context of ODRL, there have been sev-
eral publications focusing on communication pro-
tocols. (Arnab and Hutchison, 2005) proposed
an approach to enable bi-directional message-based
communication, allowing the end users to add, re-
move, and replace rights from ODRL polices. In
IDS, there are defined subclasses of the odrl:Policy
which allow an assigner to offer a policy, i.e.,
IDS:ContractOffer. As response to the offer, the
assignee can either agree with the offer (i.e., via
IDS:ContractAgreement) or suggest a modification
(i.e., via IDS::ContractRequest). These proposals are
derived on top of the ODRL information model. For
message-based communication, we additionally con-
sider other information, such as the sender’s endpoint
and message identification. Meanwhile, the format
and content of responses are also relevant for commu-
nication with the same understanding. Using ODRL
directly for establishing messages is problematic be-
cause ODRL is not designed for messaging.
3 CONCEPT
Drawing upon the literature review summarized in
Section 2, we propose a modeling concept with
ODRL and I4.0 as the central abstraction.
3.1 Policies
The ODRL information model is selected as the
base of the modeling concept. In the current
version (ODRL 2.2), the class of rule (odrl:Rule)
can be specified into subclasses odrl:Permission,
odrl:Prohibition, and odrl:Duty. As mentioned in
Section 2.2, UCMs can be seen as an extension of
ACMs. Due to the similar foundations, the prob-
lems of ACMs explained below apply analogously to
UCMs.
ACMs are differentiated according to the assign-
ment principles of permission. To map the assign-
ment principles to the information model, we refine
assignee by specifying odrl:PartyCollection. Actu-
ally, the current ODRL information model already
provides odrl:Constraint with the primary aim to re-
fine odrl:Action, odrl:Asset, and odrl:Party. How-
ever, using this constraint, the policy cannot be sat-
isfied with hierarchical modeling (such as subroles of
a role). Moreover, types of ACMs are represented in
an implicit manner, as there is no class explicitly il-
lustrating their types.
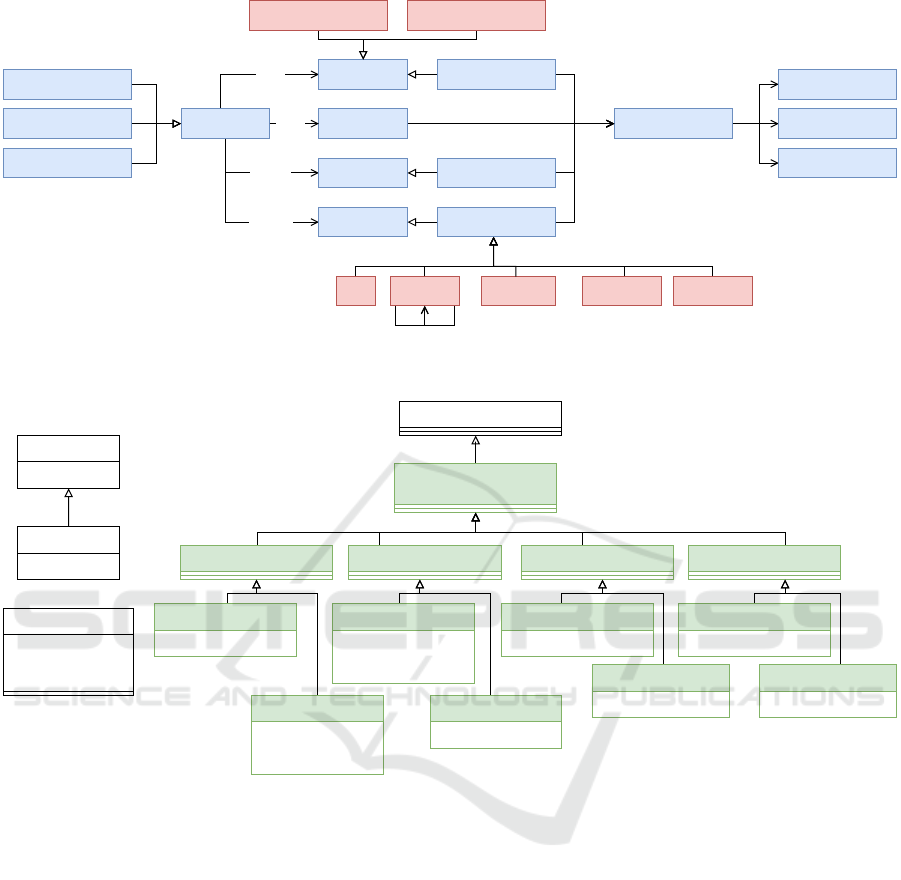
In light of this consideration, we propose
an extended modeling of the information model,
see Figure 2. The classes colored with blue
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
78

are the original part of the information model,
whereas the red part depicts our proposed extension.
First, odrl:PartyCollection, which is associated with
odrl:Rule via odrl:assignee, is specified to express
right assignments of various ACMs and UCMs. In
addition, we also consider the policy as a resource
(i.e., subclass of odrl:Asset), allowing policies them-
selves to be managed under additional policies. Thus,
we propose the specification of odrl:Asset into odrl-
ex:ResourceAsset and odrl-ex:PolicyAsset.
In addition to supporting hierarchical and explicit
modeling, the proposed concept enables the flexi-
ble combination of various ACMs and UCMs into
one policy. Listing 1 illustrates an exemplary access
control policy, restricting who is allowed to retrieve
measured values of a temperature sensor. This pol-
icy combines RBAC and ABAC to define the access
rights, see Line 6-29. Line 30-40 define who is al-
lowed to retrieve as well as update the policy.
Listing 1: An example access control policy combined with
RBAC and ABAC.
1 {
2 ... ,
3 " @type ": " set " ,
4 " u i d " : " h t t p : // examp l e . com / p o licy :4 7 11" ,
5 " per m i ssio n " : [
6 {
7 " target " :{
8 " @type ": " R esou r c eAs s e t ",
9 " @value " : " h t t p : // examp l e . com / s e nsor /
temp "
10 },
11 " action " : " r e a d " ,
12 " ass i g n er ": " http : // e x ample . com/ user :1 2 3",
13 " ass i g n ee ": [
14 {
15 " @type ": " Role ",
16 " @value " : " sma r t_h o m e_m a nag e r " ,
17 " impl i e s " :[ " s m art _ hom e _ mem b er "]
18 },
19 {
20 " @type ": " A t tribu t e " ,
21 " lef t Oper a n d ":" org : l o catio n " ,
22 " oper a t or ": " eq" ,
23 " ri g h tOpe r and ":{
24 " @type ": " xsd : s tring ",
25 " @value " : " home "
26 }
27 }
28 ]
29 },
30 {
31 " target " :{
32 " @type ": " P o licy A sset " ,
33 " @value " : " h t t p : // examp l e . com / p o licy :4 7 1
1"
34 },
35 " action " : [" read " , " w r i te " ],
36 " ass i g n ee ": [
37 {
38 " @type ": " Id " ,
39 " @value " : " h t t p : // examp l e . com / m anager :
1"
40 }
41 ]
42 }
43 ]
44 }
3.2 Message-Based Protocol
The fundamental element of the proposed message-
based protocol is VDI 2193-1, which standardizes a
basic message structure and vocabulary for a ”Lan-
guage for I4.0 components”. In this context, a mes-
sage combines a frame with so-called interaction ele-
ments. First of all, the frame comprises the basic ele-
ments necessary for communication, especially, iden-
tification of communication participants (sender and
receiver) as well as identification and reference of in-
dividual conversations and messages. The interaction
elements comprise the necessary payload data. VDI
2193-1 specifies these messages as a general basis
for automated interactions between communication
partners. Specific types of interaction scenarios are
specified in terms of so-called semantic interaction
protocols. A concrete example is a ”bidding proto-
col” specified in VDI 2193-2. Within the frame, VDI
2193-1 messages reference the applied semantic in-
teraction protocol as well as the specific message type
within the respective protocol.
Accordingly, we define four semantic interaction
protocols to interact with policies. Here, every CRUD
(Create, Update, Read, Delete) operation to access
policies combines a request with a corresponding re-
ply. Applying these protocols to VDI 2193-1 mes-
sages yields the message types as presented in Fig-
ure 3 within the namespace Interoperable Access and
Usage Control (IAU).
The structured messages provide a standardized
communication between different participants, ensur-
ing each request will be responded with an appro-
priate reply. Moreover, the proposed concept places
a strong focus on the request-reply pattern and sta-
tus management via IAU:Status. The selection of this
pattern contributes to the scalability and flexibility of
the overall system, as new functionalities can easily
be integrated. Status management triggered by replies
allows for robust error handling and recording. Over-
all, the proposed concept contributes to creating a
more organized, transparent, and reliable authoriza-
tion system.
Interoperable Access and Usage Control of Self-Sovereign Digital Twins Using ODRL and I4.0 Language
79
target
assigner
assignee
odrl:Rule
odrl:Permission
odrl:Action
action
odrl:Constraint
odrl:Asset
odrl:Party odrl:PartyCollection
odrl-ex:Role
odrl-
ex:Attribute
odrl-
ex:Capability
...
includedInimplies
odrl-ex:Id
odrl:LeftOperand
odrl:RightOperand
odrl:Operator
odrl:Prohibition
odrl:Duty
odrl:AssetCollection
refinement
odrl:Party odrl:PartyCollection
odrl-ex:RessourceAsset odrl-ex:PolicyAsset
Figure 2: The proposed extension (red) of the ODRL information model (blue).
<<abstract>>
IAU:PolicyMessage
IAU:GetPolicyMessage IAU:SetPolicyMessage IAU:CreatePolicyMessage IAU:DeletePolicyMessage
VDI2193-1: Message
IAU:GetPolicyRequest
+ pathId: string
IAU:GetPolicyReply
+ status: Status
+ policy: Policy
IAU:SetPolicyRequest
+ pathId: string
+ newPolicy: Policy
IAU:SetPolicyReply
+ status: Status
IAU:CreatePolicyRequest
+ policy: Policy
IAU:CreatePolicyReply
+ status: Status
IAU:DeletePolicyRequest
+ pathId: string
IAU:DeletePolicyReply
+ status: Status
IAU:Status
+ code: int
+ description: string
odrl:Policy
IAU:Policy
Figure 3: Message types for the proposed Interoperable Access and Usage Control (IAU) interaction protocol for policy access
(green).
4 PROOF OF CONCEPT
Based on the concept outlined in Section 3, the subse-
quent parts delve into a practical demonstration to un-
derscore the added value of our approach. Section 4.1
details the integration of our concept into an exem-
plary system architecture based on XACML. Further-
more, Section 4.2 focuses on the impact of our con-
cept on facilitating trustful data sharing. To illustrate
this, we present a data trustee as a use case, foster-
ing an interoperable data sharing environment. Sub-
sequently, Section 4.3 identifies parallels between the
given use case and SSDTs. Here, it is shown why the
proposed concept can serve as a basis for SSDTs and
where their added value lies.
4.1 System Architecture
XACML offers a comprehensive system architecture
that encompasses components like policy enforce-
ment point (PEP), policy decision point (PDP), policy
retrieval point (PRP), policy information point(PIP),
etc. This reference architecture is widely used across
different implementations in access control manage-
ment systems. The proposed concept in Section 3
can be seamlessly integrated and used in this sys-
tem architecture to enable an interoperable interac-
tion regarding policies, see Figure 4. A gateway,
representing a PEP, interrupts the data flow and for-
wards access requests as messages to a policy en-
gine. The messages are created using the proposed
message-based protocol, enabling creating, reading,
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
80
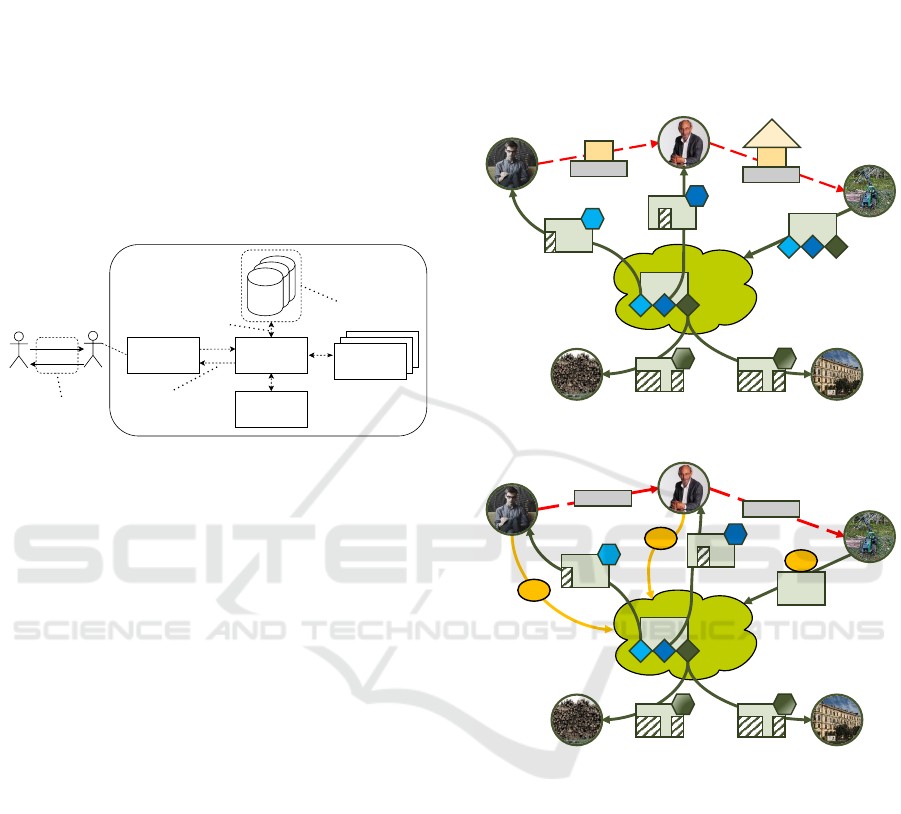
updating and deleting ODRL-based policies stored in
the PRP. The policy engine then evaluates access re-
quests by comparing the requests with the respective
policies. In some cases, the evaluation must be sup-
ported by the PIP which provides relevant attributes
associated with subjects. The ontology library pro-
vides, when needed, ontologies to semantically de-
scribe attributes used in PDP. The use of our concept
enhances the richness of policy expression in this sys-
tem. Moreover, the uniform understanding maintains
a consistent and transparent access control environ-
ment across various interfaces and interactions within
this system.
Policies
Policies
Ontology Library
Gateway
(PEP)
Policy Engine
(PDP)
Subject
Policies
(PRP)
Industry 4.0-based
messages
ODRL-based policies for
ACMs and UCMs
internal request/response
to retrieve, configure,
create, and remove policies
internal request/response
to enforce access request
Object
Data base for
attributes
(PIP)
Figure 4: An exemplary XACML-based system architecture
with the prototypical implementation of the concept pro-
vided in Section 3.
4.2 Impact on Data Trustees
Currently, various initiatives enable trustful data shar-
ing while maintaining data sovereignty. These ap-
proaches often involve concepts such as data spaces
and data trustees, mainly focusing on ensuring com-
pliance with rights during data usage, based on
UCMs (Schinke et al., 2023).
The concept of IDS addresses data sharing be-
tween two participants within a data space under a
mutually agreed contract (Eitel et al., 2021). In
practice, however, especially with machine-generated
data, there are often several entities that are consid-
ered as data owners. This increased complexity ex-
plains the simplification in the use case in forestry, as
stated in (Schinke et al., 2023). Here, there is only
one provider that sends data to a data trustee to create
offers on behalf of all owners. This process is shown
in the upper part of Figure 5, where the red dashed
lines represent the communication between the dif-
ferent owners (forest owner, contractor and harvester)
outside the data trustee’s purview. After executing
the job, the harvester combines the generated data
with individual usage rights to create various offers
(different-colored squares with ”O”). These offers are
then sent to the data trustee. Based on this, actors can
engage in negotiations to form a contract and thereby
reach an agreement (different-colored hexagons with
”A”), enabling them to access and utilize the corre-
sponding parts of the data.
Statustreffen S3I-X3
S
3
I-X
S3I-X – Use Case – ohne HSM
Data
Trustee
Forest Owner
(SP)
Contractor
Harvester
Sawmill
Photos: Pixabay
Research Institute
UR
=
Usage
rights
HPR
=
Harvester
production
data
O
=
Offer
A
=
Agreement
SP
=
Starting
point
O O
HPR
OO O
HPR
A
HPR
A
HPR
A
HPR
UR
UR
Job
UR
Job
A
HPR
O
Data
Trustee
Forest Owner
(SP)
Contractor
Harvester
Sawmill
Research Institute
O
HPR
HPR
A
HPR
A
HPR
A
HPR
Job
Job
A
HPR
OO
UR
UR
UR
Figure 5: Data trustee use case “trustful sharing of harvester
production data” before (above) and after (below) the pro-
posed extension of ODRL, use case based on (Schinke et al.,
2023).
The specification of odrl:Asset into odrl-
ex:ResourceAsset and odrl-ex:PolicyAsset proposed
in Section 3.1 provides a solution to reduce com-
plexity in the case of multiple owners. This makes
it possible for an entity to independently append
their usage rights to the provided data, by using the
message-based protocol proposed in Section 3.2.
The revised process is shown in the lower part of
Figure 5, where the orange arrows and ellipses illus-
trate the new possibility. In this way, the harvester,
responsible for data generation, is no longer burdened
with tasks of combining the individual rights and
Interoperable Access and Usage Control of Self-Sovereign Digital Twins Using ODRL and I4.0 Language
81

then creating offers. Instead, the harvester only
transfers the data along with its own usage rights
to the data trustee, initializing a policy through an
IAU:CreatePolicyRequest. An excerpt of a possi-
ble corresponding message is shown in Listing 2.
Subsequently, other stakeholders like forest owner
and contractor can append their own usage rights
to the policy using an IAU:SetPolicyRequest. An
exemplary excerpt of a corresponding message is
shown in Listing 3, where the attribute pathId defines
the part of the policy to be set. Based on the defined
policy, the data trustee then generates the resulting
offers. Similarly, an IAU:SetPolicyRequest allows
each owner to subsequently adjust their defined usage
rights themselves, e.g., more or less restrictive.
Listing 2: Excerpt from an exemplary
IAU:CreatePolicyRequest of a harvester.
1 {
2 " frame ": {
3 ...
4 " s ema n t icP r otoc o l ": " https :// ex a m p le . c om /
IAU / C reat e P oli c y " ,
5 "type " : " req u e s t " ,
6 " m e ssag e I d " : " h arve s t er :1 2 3",
7 " s e n der ": {
8 " id e n tif i c ati o n " : "12 3 ",
9 " role " : {
10 " name " : " h arves t e r "
11 }
12 },
13 " r e ceive r " : {
14 " id e n tif i c ati o n " : " data T r uste e : 456 " ,
15 " role " : {
16 " name " : " d ataT r u ste e "
17 }
18 },
19 " r e p lyBy ": 1 2 312 3 12 3 ,
20 ...
21 },
22 " in t e ra c t ion E lem e n ts " : [
23 {" p o licy ": "${odrl p o l i cy a c c . to F i g ure 2 "
}
24 ]
25 }
Listing 3: Excerpt from an exemplary
IAU:SetPolicyRequest of a forest owner.
1 {
2 " frame ": {
3 ...
4 " s ema n t icP r otoc o l ": " https :// ex a m p le . c om /
IAU / S e tPol i c y " ,
5 "type " : " req u e s t " ,
6 ...
7 },
8 " in t e ra c t ion E lem e n ts " : [
9 {
10 " pathId " : " http : // e x a m ple . c o m / polic y : 1 23 /
pe r m i ssio n [ 0] / ac t i o n "
11 " new P o licy " : " read "
12 }
13 ]
14 }
The proposed message-based protocol is also
applicable for data retrieval. First, the con-
sumer, e.g., a sawmill, needs to know the corre-
sponding policy, which is achieved by sending an
IAU:GetPolicyRequest to the data trustee. The trustee
responds with an IAU:GetPolicyReply that contains
the policy details or a rejection.
4.3 Portability to SSDTs
A closer look at Figure 5 shows that different types
of participants can be involved in data sharing. In
this example, people (forest owner, contractor), in-
stitutions (sawmill, research institute) and machines
(harvester) are participating. As direct communica-
tion between the participants and the real harvester is
not possible, this is handled by its DT. Currently, DTs
enable data sharing based on a defined policy. How-
ever, to work as automated as possible, DTs should
also be able to define and enforce policies. This is a
basic idea of the SSDT. Using the proposed message-
based protocol and integrating the system architecture
presented in Section 4.1 in SSDTs forms a basis for
this.
If all participants are represented as SSDTs, it is
imaginable that, based on the proposed concept, they
will be able to jointly define, negotiate and enforce
policies in the future. This allows each SSDT to not
only define who has the permission to use its data, but
also to specify who has the permission to decide un-
der which conditions its data can be used. For exam-
ple, one SSDT could be responsible for financial ne-
gotiations on behalf of all owners, as it has a special-
ized negotiation model. A possible negotiation could
be that the owners have agreed on a desired price of
100 C and a minimum price of 80 C for a dataset. A
consumer now wants to use the data and offers 70 C.
Through skillful negotiation, the SSDT agrees with
the consumer on a price of 90 C. At the same time,
each SSDT is able to share parts of the data that are
sensitive only to itself on other terms without obtain-
ing the permission of each owner. For example, an
SSDT could share a corresponding part of the data
with a research institute free of charge. Based on the
ideas of an SSDT, this should be automated in the fu-
ture. An active intervention by a human or a central-
ized component, such as a data trustee, is therefore no
longer necessary.
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
82

5 CONCLUSION
The presented paper proposes a conceptual frame-
work with ODRL and I4.0 language, making an ad-
vancement in managing access and usage control for
SSDTs. The use and extension of ODRL achieves
comprehensive and fine-grained structuring of poli-
cies, primarily enabling modeling of interoperable
ACMs and UCMs. The granularity in representing
policies not only refines the scalability, but also re-
duces the implementation complexity in practice, ob-
viously enhancing the flexibility of authorization sys-
tems. The realization of the protocol rooted in VDI
2193-1 promotes the independence of communica-
tion participants in decentralized systems, indirectly
decoupling the systems and increasing the fault tol-
erance of them. Standardized message formats en-
able systems built on different technologies to com-
municate seamlessly, basically enhancing the inter-
operability and flexibility in design of authorization
systems.
To implement the concept in a proof-of-concept
manner, the paper also demonstrates an application of
a data trustee, highlighting the potential of our con-
cept in facilitating interoperable and effective data
sharing in complex digital ecosystems. In the sub-
sequent phases of our research, we aim to establish
an all-encompassing definition of the term SSDT. In
addition to the core aspects that constitute an SSDT,
specialized topics are also included. For example, we
intend to develop a comprehensive approach to inter-
operably describe the relevant processes involved in
authorization, specifically tailored as integral compo-
nents of the authorization system of SSDTs. Further-
more, we plan to incorporate semantic web technolo-
gies into the framework to add semantic meanings to
the system, making it more intuitive and effective in
managing complex authorization scenarios.
REFERENCES
Alam, S., Chowdhury, M. M., and Noll, J. (2011). Interop-
erability of security-enabled internet of things. Wire-
less Personal Communications, 61:567–586.
Alshamsi, A. S., Maamar, Z., and Kuhail, M.-A. (2023).
Towards an approach for weaving open digital rights
language into role-based access control. In 2023 Inter-
national Conference on IT Innovation and Knowledge
Discovery (ITIKD), pages 1–6. IEEE.
Arnab, A. and Hutchison, A. (2005). Extending odrl
to enable bi-directional communication. Tech-
nical report, Data Network Architectures Group,
Department of Computer Science, University
of Cape Town, Rondebosch,7701 South Africa.
https://pubs.cs.uct.ac.za/id/eprint/197/1/paper.pdf.
Azeez, N. A. and Venter, I. M. (2013). Towards ensuring
scalability, interoperability and efficient access con-
trol in a multi-domain grid-based environment. SAIEE
Africa Research Journal, 104(2):54–68.
Barlas, C. (2006). Digital rights expression languages
(drels). JISC Technology and Standards Watch,
6(3):1–42.
Belyaev, A. and Diedrich, C. (2019). Specification ‘demon-
strator i4. 0-language’v3. 0. Technical Report IFAT-
LIA 07/2019, Institute for Automation Engineering,
Otto von Guericke University Magdeburg, Postfach
4120, D-39016 Magdeburg, Germany.
BMWi (2018). I4.0-sprache vokabular, nachricht-
enstruktur und semantische interaktionspro-
tokolle der i4.0-sprache. https://www.plattform-
i40.de/IP/Redaktion/DE/Downloads/Publikation/hm-
2018-sprache.pdf? blob=publicationFile&v=1.
Online, accessed on 2024-01-04.
Cai, F., Zhu, N., He, J., Mu, P., Li, W., and Yu, Y. (2019).
Survey of access control models and technologies for
cloud computing. Cluster Computing, 22:6111–6122.
Chen, J., Bektas, A. R., and Roßmann, J. (2023). From
centralized to decentralized: A did-based authentica-
tion concept in forestry 4.0. In 2023 IEEE Interna-
tional Conference on Omni-layer Intelligent Systems
(COINS), pages 1–5. IEEE.
Colombo, M., Lazouski, A., Martinelli, F., and Mori, P.
(2010). A proposal on enhancing xacml with continu-
ous usage control features. In Grids, P2P and Services
Computing, pages 133–146. Springer.
Eitel, A., Jung, C., Brandst
¨
adter, R., Hosseinzadeh, A.,
Bader, S., K
¨
uhnle, C., Birnstill, P., Brost, G., Gall,
Bruckner, F., Weißenberg, N., and Korth, B. (2021).
Usage Control in the International Data Spaces. doi:
10.5281/ZENODO.5675884, Version Number: 3.0.
Esposito, C. (2018). Interoperable, dynamic and privacy-
preserving access control for cloud data storage when
integrating heterogeneous organizations. Journal of
Network and Computer Applications, 108:124–136.
Esteves, B., Pandit, H. J., and Rodr
´
ıguez-Doncel, V. (2021).
Odrl profile for expressing consent through granular
access control policies in solid. In 2021 IEEE Euro-
pean Symposium on Security and Privacy Workshops
(EuroS&PW), pages 298–306. IEEE.
Ferraiolo, D., Chandramouli, R., Kuhn, R., and Hu, V.
(2016). Extensible access control markup language
(xacml) and next generation access control (ngac). In
Proceedings of the 2016 ACM International Workshop
on Attribute Based Access Control, pages 13–24.
Ferrini, R. and Bertino, E. (2009). Supporting rbac with
xacml+owl. In Proceedings of the 14th ACM sym-
posium on Access control models and technologies,
pages 145–154.
FraunhoferIESE (2023). MY DATA control tech-
nologies policy language documentation.
https://developer.mydata-control.de/language/.
Online, accessed on 2023-12-21.
Hafeez, K., Rajpoot, Q., and Shibli, A. (2012). Interop-
erability among access control models. In 2012 15th
Interoperable Access and Usage Control of Self-Sovereign Digital Twins Using ODRL and I4.0 Language
83

International Multitopic Conference (INMIC), pages
111–118. IEEE.
Hilty, M., Pretschner, A., Basin, D., Schaefer, C., and Wal-
ter, T. (2007). A policy language for distributed usage
control. In Biskup, J. and L
´
opez, J., editors, Computer
Security – ESORICS 2007, Lecture Notes in Computer
Science, pages 531–546. Springer. doi: 10.1007/978-
3-540-74835-9 35.
Hosseinzadeh, A., Eitel, A., and Jung, C. (2020). A system-
atic approach toward extracting technically enforce-
able policies from data usage control requirements:.
In Proceedings of the 6th International Conference
on Information Systems Security and Privacy, pages
397–405. SCITEPRESS - Science and Technology
Publications. doi: 10.5220/0008936003970405.
Hu, V. C., Kuhn, D. R., Ferraiolo, D. F., and Voas, J. (2015).
Attribute-based access control, volume 48(2). IEEE.
Ianella, R. (2007). Open digital rights language (odrl).
Open Content Licensing: Cultivating the Creative
Commons.
IDSA (2023). Ids reference architecture model
4.0. https://docs.internationaldataspaces.orgids-
knowledgebasevids-ram-4. Online, accessed on
2024-01-19.
Jones, D., Snider, C., Nassehi, A., Yon, J., and Hicks, B.
(2020). Characterising the digital twin: A systematic
literature review. CIRP journal of manufacturing sci-
ence and technology, 29:36–52.
Jung, C. and D
¨
orr, J. (2022). Data usage control. In Otto,
B., ten Hompel, M., and Wrobel, S., editors, Design-
ing Data Spaces : The Ecosystem Approach to Com-
petitive Advantage, pages 129–146. Springer Inter-
national Publishing. doi: 10.1007/978-3-030-93975-
5 8.
Kanaan, K., Wermann, J., B
¨
ar, M. A., and Colombo, A. W.
(2023). Industry 4.0-compliant digitalization of a re-
configurable and flexible laser cutter module within
a digital factory. In 2023 IEEE International Con-
ference on Industrial Technology (ICIT), pages 1–7.
IEEE.
Kasdorf, B. (2015). Navigating the publishing rights land-
scape. Publishing Research Quarterly, 31(3):190–
200.
Lazouski, A., Martinelli, F., and Mori, P. (2010).
Usage control in computer security: A sur-
vey. Computer Science Review, 4(2):81–99. doi:
10.1016/j.cosrev.2010.02.002.
Lee, B., Kim, D.-K., Yang, H., and Jang, H. (2015). Role-
based access control for substation automation sys-
tems using xacml. Information Systems, 53:237–249.
Lee, E., Seo, Y.-D., Oh, S.-R., and Kim, Y.-G. (2021). A
survey on standards for interoperability and security in
the internet of things. IEEE Communications Surveys
& Tutorials, 23(2):1020–1047.
Liu, M., Fang, S., Dong, H., and Xu, C. (2021). Review of
digital twin about concepts, technologies, and indus-
trial applications. Journal of Manufacturing Systems,
58:346–361.
Mahalle, P. N., Anggorojati, B., Prasad, N. R., and Prasad,
R. (2013). Identity authentication and capability based
access control (iacac) for the internet of things. Jour-
nal of Cyber Security and Mobility, 1(4):309–348.
Masood, R., Shibli, M. A., and Bilal, M. (2012). Usage
control model specification in xacml policy language:
Xacml policy engine of ucon. In Computer Informa-
tion Systems and Industrial Management: 11th IFIP
TC 8 International Conference, CISIM 2012, Venice,
Italy, September 26-28, 2012. Proceedings 11, pages
68–79. Springer.
Moghaddam, F. F., Wieder, P., and Yahyapour, R. (2016).
Policy engine as a service (peaas): an approach to a
reliable policy management framework in cloud com-
puting environments. In 2016 IEEE 4th International
Conference on Future Internet of Things and Cloud
(FiCloud), pages 137–144. IEEE.
OPA (2023). Open policy agent introduction.
https://www.openpolicyagent.org/docs/latest/. On-
line, accessed on 2024-01-19.
Park, J. and Sandhu, R. (2002). Towards usage control mod-
els: beyond traditional access control. In Proceed-
ings of the seventh ACM symposium on Access control
models and technologies, pages 57–64.
Park, J. and Sandhu, R. (2004). The UCONABC us-
age control model. ACM transactions on informa-
tion and system security (TISSEC), 7(1):128–174. doi:
10.1145/984334.984339.
Patil, V., Mei, A., and Mancini, L. V. (2007). Addressing in-
teroperability issues in access control models. In Pro-
ceedings of the 2nd ACM symposium on Information,
computer and communications security, pages 389–
391.
Preukschat, A. and Reed, D. (2021). Self-sovereign identity.
Manning Publications.
Qiu, J., Tian, Z., Du, C., Zuo, Q., Su, S., and Fang, B.
(2020). A survey on access control in the age of
internet of things. IEEE Internet of Things Journal,
7(6):4682–4696.
Samarati, P. and de Vimercati, S. C. (2000). Access control:
Policies, models, and mechanisms. In International
school on foundations of security analysis and design,
pages 137–196. Springer.
Sandhu, R. S. (1998). Role-based access control. In Ad-
vances in computers, volume 46, pages 237–286. El-
sevier.
Schinke, L., Hoppen, M., Atanasyan, A., Gong, X., Heinze,
F., Stollenwerk, K., and Roßmann, H.-J. (2023).
Trustful Data Sharing in the Forest-based Sector - Op-
portunities and Challenges for a Data Trustee. In
VLDBW 2023: workshops at VLDB 2023 : joint pro-
ceedings of workshops at the 49th International Con-
ference on Very Large Data Bases (VLDB 2023) : Van-
couver, Canada, August 28-September 1, 2023, vol-
ume 3462 of CEUR workshop proceedings. 2nd In-
ternational Workshop on Data Ecosystems, Vancouver
(Canada), 28 Aug 2023.
Sch
¨
utte, J. and Brost, G. S. (2018). Lucon: Data flow con-
trol for message-based iot systems. In 2018 17th IEEE
international conference on trust, security and privacy
in computing and communications/12th IEEE interna-
tional conference on big data science and engineering
(TrustCom/BigDataSE), pages 289–299. IEEE.
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
84

Sch
¨
utte, J. and Brost, G. S. (2018). LUCON:
Data flow control for message-based IoT systems.
http://arxiv.org/abs/1805.05887. Online, accessed on
2023-12-19.
Singh, M., Fuenmayor, E., Hinchy, E. P., Qiao, Y., Murray,
N., and Devine, D. (2021). Digital twin: Origin to
future. Applied System Innovation, 4(2):36.
Steyskal, S. and Polleres, A. (2014). Defining expressive
access policies for linked data using the odrl ontology
2.0. In Proceedings of the 10th International Confer-
ence on Semantic Systems, pages 20–23.
Tao, F., Zhang, H., Liu, A., and Nee, A. Y. (2018). Digital
twin in industry: State-of-the-art. IEEE Transactions
on industrial informatics, 15(4):2405–2415.
VanDerHorn, E. and Mahadevan, S. (2021). Digital twin:
Generalization, characterization and implementation.
Decision support systems, 145:113524.
Wang, X., DeMartini, T., Wragg, B., Paramasivam, M., and
Barlas, C. (2005). The mpeg-21 rights expression lan-
guage and rights data dictionary. IEEE Transactions
on Multimedia, 7(3):408–417.
Wang, X., Lao, G., DeMartini, T., Reddy, H., Nguyen, M.,
and Valenzuela, E. (2002). Xrml–extensible rights
markup language. In Proceedings of the 2002 ACM
workshop on XML security, pages 71–79.
Zhang, P., Liu, J. K., Yu, F. R., Sookhak, M., Au, M. H.,
and Luo, X. (2018). A survey on access control in
fog computing. IEEE Communications Magazine,
56(2):144–149.
Zhang, Z. (2023). Decentralized identifiers-based access
control management system for forestry 4.0. Mas-
ter’s thesis, RWTH Aachen University, Ahornstr. 55,
52074 Aachen.
Interoperable Access and Usage Control of Self-Sovereign Digital Twins Using ODRL and I4.0 Language
85
