
Decentralized Ransomware Recovery Network: Enhancing Resilience
and Security Through Secret Sharing Schemes
Sijjad Ali
1 a
, Jia Wang
1 b
, Victor Chung Ming Leung
1 c
and Asad Ali
2 d
1
College of Computer Science and Software Engineering, Shenzhen University, Yuehai Campus, Guangdong, China
2
College of Electronics and information Engineering, Shenzhen University, Yuehai Campus, Guangdong, China
Keywords:
Ransomware, Cybersecurity Defense, Decentralized Ransomware Recovery Network (DRRN),
Secret Sharing Schemes, Resilience.
Abstract:
Ransomware attacks present multiple threats to individuals such as businesses and organizations, causing
data loss, financial stress, and operational interruptions. Traditional measures to mitigate ransomware threats
usually include backups and secure applications. However, these countermeasures may not protect against
sophisticated attacks. The purpose of this article is to explore a decentralized approach for recovering from
multiple ransomware attacks. A decentralized secure approach is employed by the decentralized ransomware
recovery network (DRRN) as a platform for sharing data privacy. Backup and restoration of encryption keys
on shared domains are performed in the event of a ransomware attack. By paying for ransomware, users can
encrypt their files. Additionally, the technical design of the DRRN and its management, as well as ransomware
attacks are explored in our studies. A hybrid approach is utilized to evaluate its effectiveness and implications
for cybersecurity and data protection. Finally, we assert that our proposed scheme is more secure and effective
in the DRRN environment.
1 INTRODUCTION
In recent years, ransomware attacks have increased
significantly 68%, posing a serious threat to cyberse-
curity around the world (Teichmann et al., 2023; Hu-
mayun et al., 2021; Ali et al., 2023). There are several
characteristics of these cyberattacks that can be sum-
marized as the decryption of sensitive data, the lack
of access to legitimate users, as well as the demand
for ransom for the key to decryption. Many instances
exist where businesses, individuals, and even critical
foundations are subjected to severe financial losses,
data corruptions, and operational disruptions because
of cyber attacks (Kafi and Akter, 2023). A number
of traditional methods have been used to prevent the
spread of ransomware in recent years. An example of
these would be the need for regular backups of data
and the use of endpoint security software, as well as
incident response protocols (Ilca et al., 2023; Chen
et al., 2021). While these measures may provide some
a
https://orcid.org/0000-0002-9141-8837
b
https://orcid.org/0000-0002-0861-2496
c
https://orcid.org/0000-0003-3529-2640
d
https://orcid.org/0009-0004-5399-0156
protection, they do not succeed in the face of the in-
creasing complexity and targeted nature of contempo-
rary ransomware attacks. This underscores the need
for more comprehensive and proactive cybersecurity
measures. A proactive approach is crucial against
ransomware attacks. We propose state-of-the-art De-
centralized Ransomware Recovery Network (DRRN)
as a decentralized solution, enhancing recovery pro-
cesses, reducing attackers’ financial incentives, and
fortifying data security. DRRN decentralizes control
and utilizes secret distribution schemes, ensuring ro-
bust and permanent infrastructure for data protection
and recovery.
The Decentralized Ransomware Recovery Net-
work (DRRN) utilizes centralized storage approach
and use of secret distribution schemes to encrypt very
highly sensitive files and keys across networked edge
nodes, to making our data secure. In addition, we ap-
plied decentralized encryption approach to further se-
cure data and reduce risks of loss or damage during
ransomware attacks. The DRRN decentralized stor-
age and encryption keys enhance strength against in-
trusions, however, secret distribution approach like
secret sharing support single-point vulnerabilities.
This decrease unauthorized access within the net-
294
Ali, S., Wang, J., Leung, V. and Ali, A.
Decentralized Ransomware Recovery Network: Enhancing Resilience and Security Through Secret Sharing Schemes.
DOI: 10.5220/0012713500003705
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 9th International Conference on Internet of Things, Big Data and Security (IoTBDS 2024), pages 294-301
ISBN: 978-989-758-699-6; ISSN: 2184-4976
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

work, enhancing data security against advanced ran-
somware attacks and minimizing failure risks of net-
work.
In a ransomware attack, the Decentralized Ran-
somware Recovery Network (DRRN) utilizes dis-
tributed shares stored across its nodes to dynamically
regenerate the encryption key if it is lost or inacces-
sible. These shares, fragments of the original key,
are reconstructed through secret sharing approach, en-
abling decryption of the encrypted data. This process
allows affected users to regain access to their files
without needing to fulfill ransom demands, ensuring
fast and reliable recovery. Additionally, the DRRN
offers the option to withdraw files from the decryp-
tion process if both parties agree, providing flexibil-
ity in recovery. By neutralizing the impact of ran-
somware attacks through decentralized key regenera-
tion, the DRRN removes the financial incentive for at-
tackers and strengthens network security against such
threats.
In our proposed work, we perform a deep analy-
sis of the Decentralized Ransomware Recovery Net-
work (DRRN), which maintain its technical archi-
tecture, application scope, and practical significance.
We explore into decentralization and secret sharing
approaches, In addition, emphasizing their function
in DRRN defensive solutions against ransomware at-
tacks. Besides, we analyze DRRN efficiency through
challenges and simulations, assessing its performance
and broader impacts on cybersecurity and data pro-
tection. The goal of our analysis is to provide read-
ers with the knowledge to understand DRRN per-
formance and the potential challenges it encounters
when combating ransomware attacks in this dynamic
cyberspace ecosystem by offering evidence-based in-
sights for informed decision-making.
DRRN is a crucial initiative in ransomware
defense establishing proactive and sustainable ap-
proaches to prevent breaches and protect critical
data. By utilizing a decentralized data distribution
approach, it will build a strong defense against ran-
somware attacks, and the consequent effects will be
mitigated to a certain level. By highlighting the cru-
cial role of innovation, this scheme tends to more ef-
ficiently deal with recent hacker upgrades and even
proactively protect the networks from the threats
which may be likely to occur in the future.
2 MAJOR CONTRIBUTIONS
• The DRRN is a decentralized network of nodes all
over the network that uses InterPlanetary File Sys-
tem (IPFS) and other decentralized storage meth-
ods to offer automatic backups of files that have
been decrypted by ransomware. It ensures data
integrity and removes the risk of data loss or cor-
ruption and single point of failure network.
• The Decentralized Ransomware Recovery Net-
work (DRRN) is divided into multiple contexts by
using secret sharing principles, such as Shamar’s
secret sharing principles, which are distributed
across different nodes in the network, so that no
single entity contributes significantly to the man-
agement of the corruption process as a whole.
• When a victim of ransomware attacks is affected
by the Decentralized Ransomware Recovery Net-
work (DRRN), it restores settings in order to
relieve them from the financial burden of ran-
somware attacks, thus allowing affected users to
restore their files without making any tact to the
attackers.
3 DEFINITION OF SECRET
SHARING SCHEME
A secret sharing scheme can be mathematically de-
fined using polynomial interpolation over a finite field
(Shamir, 1979). Let’s denote;
• S as the secret to be shared.
• n as the total number of participants.
• k as the threshold, i.e., the minimum number of
participants required to reconstruct the secret.
A secret sharing scheme involves the following steps;
(1) Polynomial Generation: A polynomial f (x) of
degree k
1
is constructed over a finite field F such that;
f (x) = a
k−1
x
k−1
+ a
k−2
x
k−2
+ . . . + a
1
x + a
0
(1)
(2) Secret Allocation: Each participant is assigned
a unique x value from the finite field F, and their
share s
i
is obtained by evaluating the polynomial at
that point;
s
i
= f (x
i
) (2)
(3) Distribution of Shares: The shares s
i
are dis-
tributed among the participants.
(4) Reconstruction: To reconstruct the secret S,
any subset of k shares can be used with polyno-
mial interpolation. Suppose we have a set of shares
{
(x
1
, s
1
), (x
2
, s
2
), . . . , (x
k
, s
k
)
}
. We can construct the
Lagrange interpolation polynomial L(x) as follows;
L(x) =
k
∑
i=1
s
i
· l
i
(x) (3)
Decentralized Ransomware Recovery Network: Enhancing Resilience and Security Through Secret Sharing Schemes
295
Where l
i
(x) is the Lagrange basis polynomial
given by;
l
i
(x) =
k
∏
j=1, j̸=i
x − x
j
x
i
− x
j
(4)
The secret S can then be reconstructed as S = L(0).
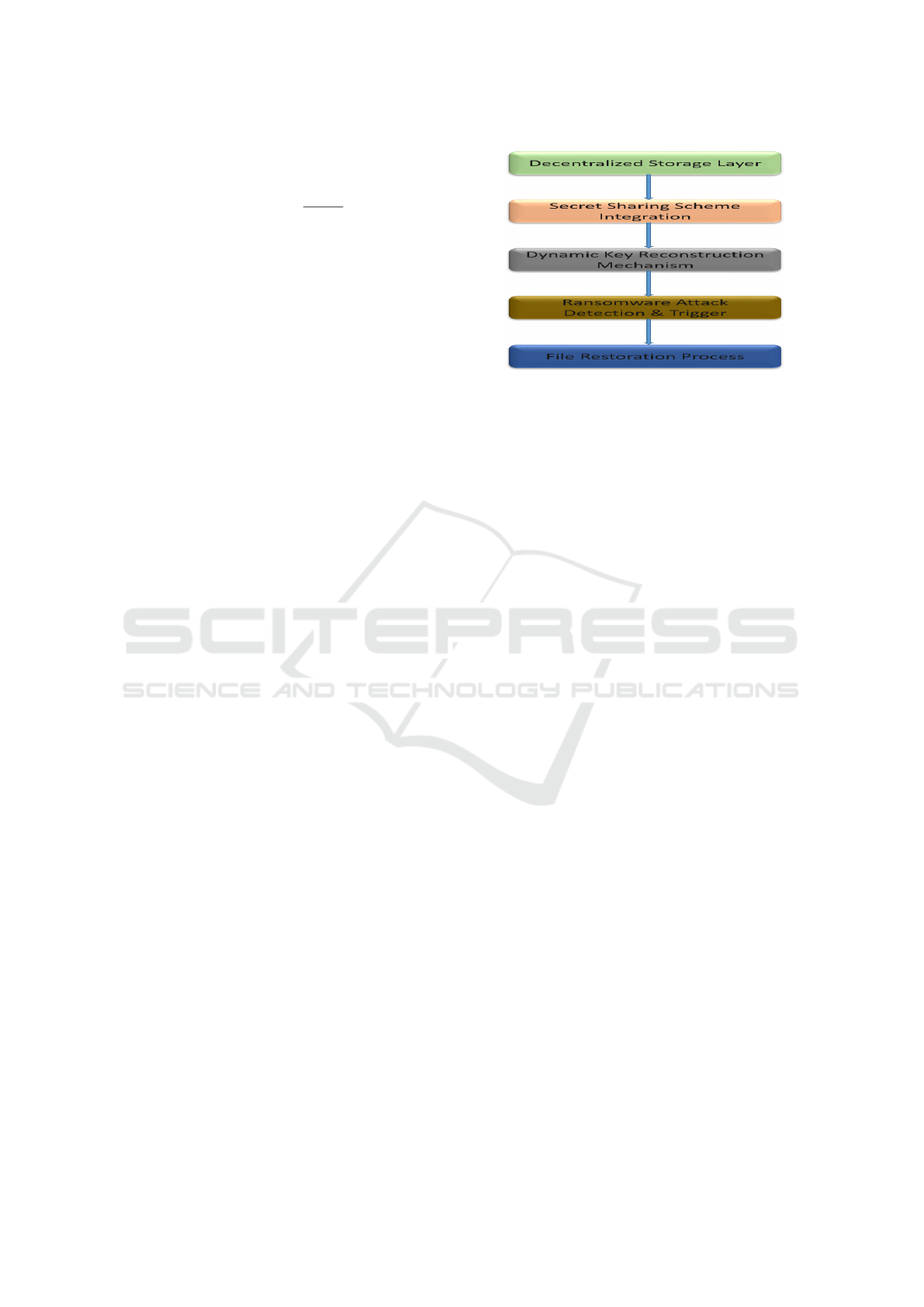
4 PROPOSED MODEL
The proposed Decentralized Ransomware Recovery
Network (DRRN) leverages decentralized storage, a
secret sharing scheme, and dynamic key reconfigu-
ration to mitigate ransomware attacks. In the DRRN
framework, N decentralized storage nodes are respon-
sible for storing confidential backups of critical files.
Employing Shamer’s secret sharing scheme with a
threshold T , a private message M is divided into
shares such that T lower shares are required to reset
the key (T ≤ M ≤ N). The key reset process, which
is T -independent, retrieves shares from a subset of
nodes post-ransomware attack. Bernoulli’s principle
is utilized to compute the overall success probability
P
success
= 1 − (1 − p)
T
, where p represents the prob-
ability of success for each share. File recovery, facil-
itated by the reset key, ensures data retrieval with a
success probability P
recovery
= P(K) × P
success
.
However, the mechanism for detecting ran-
somware attacks may not be apparent. In the DRRN,
all data are encrypted by the user. Consequently, even
if an attacker gains access to the encrypted data, their
ability to manipulate or utilize it is severely limited.
The distributed nature of data storage and the en-
cryption mechanism significantly mitigate the impact
of ransomware attacks, ensuring robustness, reducing
data loss, and facilitating recovery without compro-
mising data security. This approach effectively mini-
mizes the financial impact on both consumers and or-
ganizations. Further details of the proposed model are
explained in Figure 1.
5 PROPOSED SCHEME
To enhance reliability and recovery from ransomware
attacks, we propose a decentralized DRRN approach
that integrates cryptographic principles and mathe-
matical modeling.
5.1 Node Selection Strategy
We selects nodes N for decentralized network backup
and secret sharing based on probabilistic values p
i
,
Figure 1: Proposed Model.
considering factors like node location, network capac-
ity, and security level. This aims to maximize redun-
dancy and diversity, reducing data loss risk and en-
hancing network resilience against threats.
5.2 Secret Sharing Process
Shamir’s secret distribution method divides a key K
into M shares, where T is the minimum number of
shares required to reconstruct K. Shares are dis-
tributed among nodes based on probabilities p
i
. Each
share holds no information about the original key until
a minimum threshold of shares is gathered, ensuring
security against individual node monitoring.
5.3 Probability Modeling for Key
Reconstruction
In the context of key reconstruction within Shamir’s
Secret Sharing scheme, the probability of success-
fully reconstructing a key, denoted by P(K), is intri-
cately linked to the distribution and accessibility of
shares among nodes. Employing binomial distribu-
tions B(M, p) proves advantageous in this scenario,
with M representing the total number of shares and
p delineating the range of access to share edges. As
Shamir’s Secret Sharing scheme distribute M shares
among nodes, the efficacy of edge reconstruction
hinges upon the presence of these shares. The bi-
nomial distribution adeptly captures this essence by
accounting for the minimum number of edges (i.e.,
total shares M required for successful reconstruction
amidst a specified number of accessible shares. This
algorithmic approach not only facilitates the estima-
tion of success probability in reconstruction using
the available shares but also accommodates poten-
tial access restrictions imposed on each share. Con-
sequently, it ensures a robust level of key security
by systematically assessing the viability of key re-
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
296

construction under various share availability scenar-
ios and access constraints.
Data: M, p, availableShares
Result: Probability of successful key
reconstruction
Input : Total number of shares M,
probability of access to an edge of
each share p, number of available
shares availableShares
Output: Probability of successful key
reconstruction
Calculate Probability: probability ← 0.0;
for k ← availableShares to M do
probability ← probability +
M!
k!·(M−k )!
×
p
k
× (1 − p)
M−k
;
end
return probability;
Algorithm 1: Probability Modeling for Key Reconstruction.
5.4 Dynamic Key Reconstruction
Mechanism
In this section, the heuristic key construction mech-
anism is primarily based on the probabilistic distri-
bution of shares. This mechanism prioritizes the re-
turn of shares from nodes with a higher probability
p
i
. After detecting a ransomware attack, the device
initiates the release of shares from a fixed number of
nodes. This is aimed at joining the threshold T re-
quired for key reconstruction. This reconstruction’s
performance is set according to different factors and
considering competing users. This process simplifies
and streamlines the initiation of restructuring mea-
sures to reduce internal and external risks to share-
holders.
5.5 File Restoration Process
The importance of this proposed scheme lies in
its ability to optimize the file restoration process,
denoted P. This functionality extends beyond just
restoration information; it also prevents damages
from data modifications or updates. By efficiently
restoration data, the system not only restores lost
information but also prevents possible changes by
adversary to the data. This aspect of operational
efficiency is very critical for a security system as it
reduces the risk of future attacks that can cause more
damage, thereby ensuring revenue and total sys-
tem resilience. As a result, the ability to restoration
data with confidence and accuracy plays a crucial role
Data: p
i
, Ransomware attack detection
Result: Reconstructed key
Input : Probability distribution of shares p
i
,
Ransomware attack detection
Output: Reconstructed key
Key Construction: Initialize priority queue
Q;
for each node i do
Add node i to Q with priority p
i
;
end
Initialize empty list selectedShares;
while not ransomware attack detected do
Remove node with highest priority from
Q;
Add shares from this node to
selectedShares;
if threshold T reached then
Break loop;
end
end
Reconstruction: Reconstruct key using
shares from selectedShares;
Algorithm 2: Dynamic Key Reconstruction Mechanism.
in the stability and effectiveness of security mea-
sures. This strengthens the protection against various
threats.
Utilizing probabilistic modeling approach in de-
centralized ransomware recovery involves statisti-
cally assessing the likelihood of successfully recov-
ering encrypted data. This includes factors like the
availability and reliability of distributed shares, the
chance of each share being retrievable, and the effec-
tiveness of key reconstruction. By evaluating these
probabilities, organizations can allocate resources ef-
fectively, focusing on areas with the highest chance of
successful recovery while minimizing costs. More-
over, this approach enables adaptability to evolving
threats and infrastructure changes, refining recovery
strategies based on real-world experiences.
6 RESULTS ANALYSIS AND
COMPARISON
The data Table 1, presents the different rates of dif-
ferent parameters of the secret distribution scheme,
including share size, threshold, success rate, key re-
construction rate, and success rate.
Decentralized Ransomware Recovery Network: Enhancing Resilience and Security Through Secret Sharing Schemes
297

Data: shares[], num shares
Result: key
Input : Shares array shares[], number of
shares num shares
Output: Decrypted key key
Reconstruct Key: sum ← 0;
count ← 0;
for i ← 0 to num shares do
if shares[i].retrieved then
sum ← sum + shares[i].value;
count ← count + 1;
end
end
if count ≥ T HRESHOLD then
return sum;
end
else
return −1 ; // Threshold not met
end
Restore Files: if k ey ̸= −1 then
print ”Files successfully restored using
key: key”;
end
else
print ”Error: Key reconstruction
threshold not met”;
end
Algorithm 3: Decentralized Ransomware Recovery Algo-
rithm.
6.1 Probability of Key Reconstruction
vs. Share Size
Figure 2, shows the relationship between the part size
S and the key reconstruction probability P(K) of a se-
cret distribution scheme. In secret sharing schemes,
a secret is divided into different parts and distributed
among the participants. They can reconstruct the orig-
inal secret only if a sufficient number of parts, de-
termined by an intermediate parameter called T , are
collected. The key reconstruction probability, P(K),
predicts the probability of successfully reconstructing
a secret in the presence of a specified number of par-
titions and specified cracks. Mathematically, P(K) is
calculated using joint probability, assuming binomial
spreading, to calculate the probability of the occur-
rence of at least T valid segments out of at least S
segments. As shown in the figure, the x-axis repre-
sents the segment size, which is the number of seg-
ments distributed, while the y-axis shows the key re-
construction probability. Each numerical point on the
figure represents a specific segment size and key re-
construction probability. In general, we expect that
P(K) will show an increasing trend as the segment
size increases, indicating the probability of success-
fully reconstructing the original secret with a larger
number of segments, if the old condition fulfills. This
figure and mathematical model provide us with a re-
source in light of the relationship between part size
and key reconstruction probability.
The probability for a share size of 5 being larger
than for a share size of 7 might seem unreasonable
at first glance. However, in certain secret sharing
schemes, the relationship between share size and key
reconstruction probability can vary based on the spe-
cific parameters and assumptions of the scheme. One
possible explanation for this phenomenon could be re-
lated to the threshold parameter T . If the threshold for
successful reconstruction is lower for the share size
of 5 compared to 7, it means that fewer shares are re-
quired to reconstruct the secret. Consequently, with
fewer shares needed, there might be a higher proba-
bility of successfully reconstructing the secret with 5
shares compared to 7 shares, even though the share
size is smaller. The formula for binomial probability
is typically expressed as;
P(X ≥ T ) =
S
∑
k=T
S
k
· p
k
· (1 − p)
S−k
(5)
Figure 2: Probability of Key Reconstruction vs. Share Size.
6.2 Probability of Successful Recovery
vs. Share Size
Figure 3, shows the relationship between portion
size (S) and probability of successful recovery
P(recovery) in a secret distribution scheme. In such
a scheme, a secret is divided into different parts. The
original secret can be recovered if sufficient parts, de-
termined by an intermediate parameter, are collected.
Probability of success recovery shows the probability
that the secret can be successfully recovered with a
given part size and crack. Mathematically, we denote
the portion size as S and the probability of success
P(recovery) as the probability of success. The rela-
tionship between these variables can be modeled on a
probabilistic basis. For example, consider the proba-
bility of success in production and distribution of each
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
298
Table 1: Collected data from experiments.
Share Size (S) Threshold (T) Success Probability (p) Key Reconstruction Successful Recovery
5 3 0.8 0.85 0.70
7 2 0.6 0.75 0.55
9 4 0.7 0.90 0.80
10 5 0.9 0.95 0.85
12 3 0.8 0.90 0.75
15 6 0.5 0.60 0.45
part. Generally, as the part size increases, the proba-
bility of restoration success decreases due to possible
causes, such as increasing the number of parts to be
taken into account. This is evident in the figure, where
the x-axis shows the portion size and the y-axis shows
the probability of successful recovery. Each numeri-
cal point on the graph represents a specific portion
size and its corresponding probability of successful
recovery. Analysis of this figure and its mathemati-
cal model provides a resource for how the probability
of successful recovery changes with different segment
sizes.
Figure 3: Probability of Successful Recovery vs. Share
Size.
6.3 Probability of Key Reconstruction
and Successful Recovery vs. Share
Size (Combined)
Figure 4, shows a relationship between portion size
S and the probability of secret distribution rearrange-
ment and recovery is shown in Figure 4. It is common
in such schemes to divide a secret into different parts.
An intermediate parameter determines the number of
parts needed to recover the original secret. Reorder-
ing the keys and recovering the secret is highly likely
to be successful, based on the success recovery proba-
bilities. In this case, we assume the partition size and
crack size are specified. P(recovery) is the probability
of successful recovery, P(K) is the probability of key
reordering, and S is the chunk size. Probabilistic real-
ism can be applied to the relationship between these
variables. The probability that each part will succeed
in production and distribution, for example, is an im-
portant consideration. A decrease in key reordering
and restoration success is generally associated with
increasing part size because of factors, such as the
increased number of part geometries. According to
the graph, the x-axis represents share size, while the
y-axis represents the probability of successful recov-
ery and key reordering. There are numerical points on
the graph that represent specific segment sizes and the
probability of success for reset and recovery.
Figure 4: Probability of Key Reconstruction and Successful
Recovery vs. Share Size (Combined).
6.4 Comparison
The DRRN model and the SSS method, both intro-
duced in Table 2, are characterized by the robustness
and reliability of our proposed scheme, which excels
among all the listed research approaches in terms of
robustness and reliability. We demonstrate superior
resilience and integrity in our scheme, which is differ-
ent from those used in other articles to address similar
issues. It is evident from the high ratings it received
in both categories. Our approach is more effective
and trustworthy if we use the DRRN model and SSS
method.
6.4.1 Robustness Assessment
• The proposed scheme stands out for its high ro-
bustness level, utilizing the DRRN model and SSS
method, indicating a strong foundation and thor-
ough analysis.
• Notably, it surpasses other studies in robustness,
which range from low to medium levels.
• High robustness suggests a well-defined method-
ology, comprehensive analysis, and reliable find-
ings, providing a solid basis for the proposed
scheme’s credibility.
6.4.2 Integrity Assessment
• The proposed scheme also demonstrates high in-
tegrity, aligning with its high robustness level.
Decentralized Ransomware Recovery Network: Enhancing Resilience and Security Through Secret Sharing Schemes
299

Table 2: Comparison of proposed work.
Authors Models Methods Robustness Integrity
teichmann et al.(Teichmann
et al., 2023)
Economic models Analysis Medium High
fadziso et al.(Fadziso et al.,
2023)
Threat modeling frameworks Overview Low Medium
humayun et al.(Humayun
et al., 2021)
Ransomware propagation models Case Studies low High
duong et al.(Duong et al.,
2023)
Resilience models Assessment low High
kafi et al.(Kafi and Akter,
2023)
Risk assessment frameworks Case Studies Medium High
amoah et al.(Amoah and
Steyn, 2023)
Behavioral models Analysis Medium High
ilca et al.(Ilca et al., 2023) Threat intelligence models Analysis High low
chen et al.(Chen et al., 2021) Incident response frameworks Case Studies Medium High
bajpai et al.(Bajpai and En-
body, 2023)
Risk management frameworks Framework low High
Our scheme DRRN model SSS method High High
• High integrity implies trustworthiness, consis-
tency, and transparency in reporting, minimizing
potential biases and ensuring data reliability.
• Compared to other studies with varying levels of
integrity, the proposed scheme maintains a consis-
tent and trustworthy approach, enhancing its cred-
ibility and reliability.
7 SECURITY ANALYSIS
A decentralized cryptographic scheme can be math-
ematically recovered from ransomware attacks by
demonstrating resistance to cyber attacks, ensuring
that combined attackers cannot reset the shared secret
without the necessary information.
Let’s denote:
• n. Total number of participants.
• t. Threshold value (minimum number of shares
required to reconstruct the secret).
• S. Set of shares held by colluding adversaries.
• K. Set of honest participants.
A scheme for defense against closure attacks can be
mathematically modeled as follows.
7.1 Probability of Successful Collusion
Attack
Using these parameters, we calculate the success
probability of attackers who optimally configure the
secret without the desired crack t. This can be ex-
pressed as calculating the key rearranging probability
that |S| ≥ t given the total number of participants n
and the number of slots t. Using combined analysis,
we can estimate the probability of success rate, by de-
termining the key of |S| probabilities.
7.2 Threshold Attack
In threshold cryptography, the secret is denoted as S,
with derivatives S
1
, S
2
, . . . , S
n
. S is accessible only
when realizations meet a fixed threshold t. Subsets
below t yield no information about S, as they are sta-
tistically independent.
P(S | S
1
, S
2
, . . . , S
t−1
) = P(S) (6)
The equation suggests independence between
S
1
, S
2
, . . . , S
n
and S, ensuring adversaries with gains
¡t gain no info. With knowledge of S entropy and re-
alizations, total probabilities of secret and distributed
components can be estimated. Security relies on
the inability of combined adversaries to breach the t
threshold, ensuring secret protection. Thus, thresh-
old cryptography remains robust against tampering,
forming a strong basis for its functionality.
7.3 Entropy Analysis Attack
We explore deeper into the entropy of the secret re-
arranged by opposing adversaries, which belongs to
them. Entropy, denoted H(S), measures the uncer-
tainty or randomness associated with a random vari-
able, in this case, the rearranged secret S
′
. Consider-
ing the entropy of S
′
, denoted as H (S
′
| S
1
, S
2
, . . . , S
k
),
we can determine the extent of invisibility in the ar-
ranged secret. Mathematically, this can be expressed
IoTBDS 2024 - 9th International Conference on Internet of Things, Big Data and Security
300

as follows:
H
S
′
| S
1
, S
2
, . . . , S
k
≤ H
S
′
(7)
The fault arises when overlapping shares exist in
rearranged secret S
′
. This constrains the fault range of
S
′
, preventing oppressive opponents from breaching
absolute secrecy. Mathematical proof shows oppos-
ing adversaries lack meaningful info about the secret,
requiring access to shares.
8 CONCLUSION AND FUTURE
AVENUES
We presented a decentralized ransomware recovery
networks utilize mesh networks and secret sharing
schemes for heightened security and robustness. By
employing layers of security and distributed key man-
agement techniques, our solution effectively safe-
guards sensitive data against ransomware attacks and
malicious sharing. Through rigorous mathematical
modeling and analytics, we have demonstrated its ef-
fectiveness against cyberattacks. In ransomware sce-
narios, our approach ensures data recovery by decen-
tralizing trust and distributing encryption keys among
network nodes.
DRRN future avenues involves enhancing pri-
vacy with ICRC technologies, integrating ML and
human brain algorithms for ransomware detection,
partnering with industries for deployment and assess-
ment. Long-term studies on ransomware risk, adapt-
ing DRRN, and legal tasks are included.
ACKNOWLEDGEMENTS
This work was supported in part by the Na-
tional Key R&D Program of China under Grant
2020YFA0908700, the National Nature Science
Foundation of China under Grants 62073225,
62203134, 61972263, 62072315, the Natural Science
Foundation of Guangdong Province-Outstanding
Youth Program under Grant 2019B151502018,
the Natural Science Foundation of Guangdong
Province under Grant 2021A1515011153, the
Guangdong Pearl River Talent Recruitment Pro-
gram under Grant 2019ZT08X603, the Guang-
dong ”Pearl River Talent Plan” under Grant
2019JC01X235, the Shenzhen Science and
Technology Innovation Commission under Grant
20200805142159001, JCYJ20220531103401003,
JCYJ20210324093808021.
REFERENCES
Ali, S., Wang, J., and Leung, V. C. M. (2023). De-
fensive strategies against pcc attacks based on ideal
(t, n)-secret sharing scheme. Journal of King
Saud University-Computer and Information Sciences,
35(9):101784.
Amoah, C. and Steyn, D. (2023). Barriers to unethical and
corrupt practices avoidance in the construction indus-
try. International Journal of Building Pathology and
Adaptation, 41(6):85–101.
Bajpai, P. and Enbody, R. (2023). Know thy ransomware
response: A detailed framework for devising effective
ransomware response strategies. Digital Threats: Re-
search and Practice.
Chen, P.-H., Bodak, R., and Gandhi, N. S. (2021). Ran-
somware recovery and imaging operations: lessons
learned and planning considerations. Journal of Digi-
tal Imaging, 34(3):731–740.
Duong, A. T. B., Hoang, T.-H., Nguyen, T. T. B., Akbari,
M., Hoang, T. G., and Truong, H. Q. (2023). Supply
chain risk assessment in disruptive times: opportuni-
ties and challenges. Journal of Enterprise Information
Management, 36(5):1372–1401.
Fadziso, T., Thaduri, U., Dekkati, S., Ballamudi, V., and
Desamsetti, H. (2023). Evolution of the cyber secu-
rity threat: an overview of the scale of cyber threat.
Digitalization & Sustainability Review, 3(1):1–12.
Humayun, M., Jhanjhi, N., Alsayat, A., and Ponnusamy, V.
(2021). Internet of things and ransomware: Evolu-
tion, mitigation and prevention. Egyptian Informatics
Journal, 22(1):105–117.
Ilca, L. F., Lucian, O. P., and Balan, T. C. (2023). Enhancing
cyber-resilience for small and medium-sized organi-
zations with prescriptive malware analysis, detection
and response. Sensors, 23(15):6757.
Kafi, M. A. and Akter, N. (2023). Securing financial infor-
mation in the digital realm: case studies in cybersecu-
rity for accounting data protection. American Journal
of Trade and Policy, 10(1):15–26.
Shamir, A. (1979). How to share a secret. Communications
of the ACM, 22(11):612–613.
Teichmann, F., Boticiu, S. R., and Sergi, B. S. (2023). The
evolution of ransomware attacks in light of recent cy-
ber threats. how can geopolitical conflicts influence
the cyber climate? International Cybersecurity Law
Review, 4(3):259–280.
Decentralized Ransomware Recovery Network: Enhancing Resilience and Security Through Secret Sharing Schemes
301
