
Fuzzy Vault Security Enhancement Avoid Statistical Biases
Sara Majbour, Morgan Barbier and Jean-Marie Le Bars
Normandie Univ, UNICAEN, ENSICAEN, CNRS, GREYC, 14000 Caen, France
Keywords:
Authentication, Biometric, Fuzzy Vault, Statistical Biases.
Abstract:
We assess the fuzzy vault’s security against the exploitation of statistical biases, conducting bias examination
through features on a sample of biometric set. Our comparative analysis quantifies the scheme’s vulnerability
to security-compromising attacks, using three bases of feature templates derived from real biometric databases
of various modalities, showcasing variable quality levels, and quantifying scheme weaknesses. This study
shows a decrease in the scheme’s security under such attacks and significantly contributes to understanding
the fuzzy vault’s limitations regarding biases in the stored set. Moreover, we propose the first solution without
requiring additional information, preserving the security of the fuzzy vault against such attacks.
1 INTRODUCTION
Biometric authentication systems enhance security
compared to traditional methods like passwords or
keys. They refer to individual traits like finger-
prints, facial features, retinal scans, and iris patterns
for identification (Dargan and Kumar, 2020; Daug-
man, 2004). To authenticate, biometric data is cap-
tured, converted into a digital template, and com-
pared to the enrolled template to confirm the individ-
ual’s identity (Sharma et al., 2015). Since biometric
templates are sensitive, various cryptographic meth-
ods are implemented to secure them (Uludag et al.,
2004). A particularly effective solution in address-
ing the variability of biometric data involves adopting
the cryptographic scheme of the fuzzy vault, devel-
oped by (Juels and Sudan, 2002). This scheme, incor-
porating error correction codes and an unordered set,
enables error-tolerant authentication while preserving
the confidentiality of the data. The standard fuzzy
vault process hides a set by connecting it to a nonce
with Reed-Solomon error correction codes. Authenti-
cation succeeds when a presented set closely matches
the reference.
Despite significant progress in studying fuzzy
vault schemes recently, each proposed approach is
tailored to the context examined and the biometrics
modalities used (Uludag et al., 2005; Nandakumar
et al., 2007a; Rathgeb et al., 2023). Numerous stud-
ies have adapted the scheme to biometrics, focusing
primarily on security (Benhammadi and Bey, 2014;
Radha et al., 2010). The original article established
an upper security bound based on the assumption of
uniform distribution. However, deviations from this
assumption in real data distributions have been noted,
which could lower the security level.
It has been recognized that biases exist, but the
correlation between their nature, magnitude, and im-
pact on fuzzy vault security is yet to be defined. Our
study quantifies the impact of the lack of a uniform
distribution on the fuzzy vault security deterioration,
highlighting its overall significance by generally ren-
dering the scheme unusable. Additionally, we un-
derscore that the attacker model proposed by Juels
and Sudan, possessing partial knowledge of the in-
formation, lacks realism and relevance. In the lit-
erature, some studies have proposed incorporating a
password as a solution to mitigate bias issues and
enhance the fuzzy vault’s security against statistical
attacks (Benhammadi and Bey, 2014; Radha et al.,
2010). However, introducing passwords fundamen-
tally establishes strong multi-factor authentication,
differing from the original fuzzy vault scheme, and
other vulnerabilities may arise with a multi-factor
scheme. No secure single-factor fuzzy vault solution
has been proposed yet. Our investigation specifically
focuses on examining the single-factor fuzzy vault
as initially proposed, to lead to a new secure single-
factor system.
Our approach manages feature templates generic
from various biometric modalities. We use three
bases of biometric templates-fingerprint, face, and
electrocardiogram, represented as feature vectors. A
distinctive attribute of the fuzzy vault is its use of
40
Majbour, S., Barbier, M. and Le Bars, J.
Fuzzy Vault Security Enhancement Avoid Statistical Biases.
DOI: 10.5220/0012715500003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 40-51
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

an unordered set of elements. In our work, the term
biometric set refers to the outcome of transforming a
biometric template of features, into a set of elements
within a finite field, as illustrated Figure 1.
Figure 1: Biometric set construction for fuzzy vault.
Our analysis focuses specifically on applying the
fuzzy vault scheme as originally proposed, without
incorporating additional information altering the au-
thentication type. For the first time, we introduce the
quantification of the significant advantage of an attack
exploiting biases by features within a sample biomet-
ric set. Our results from different template bases show
that the scheme as presented in the original article is
ineffective and lacks relevance against such attacks.
Taking into consideration these biases, we propose
the first solution for applying the fuzzy vault scheme
without passwords, using quantile methods during the
transformation into a biometric set to ensure an equi-
table distribution of elements for each feature. The
aim is to ensure the security of the single-factor fuzzy
vault authentication scheme and neutralize attacks ex-
ploiting biases by features.
The remainder of this article follows this structure:
Section 2 recalls the fuzzy vault concept and exist-
ing work on its application in biometrics. Then, Sec-
tion 3, we explain our generic methodology for any
biometric template base in a feature vector format.
Within Section 4 we outline the conditions of the up-
coming attack and the biometric templates used. Then
Section 5, we present the obtained results. This un-
derstanding of biases allows us to propose Section 6
the first solution to secure the fuzzy vault without any
additional information.
2 BACKGROUND
In this section, we aim to provide a more detailed ex-
planation of the fundamental encoding and decoding
process of the fuzzy vault scheme. Following that, we
present an extensive review of prior research on ap-
plying this cryptographic scheme in a biometric do-
main.
2.1 Fuzzy Vault
The fuzzy vault concept is a versatile crypto-
graphic approach that applies to various domains, like
privacy-protected matching, personal entropy sys-
tems, and biometrics. Its strength lies in effectively
handling differences between sets and having the ca-
pability to correct them, which is a standout feature
of this approach. Its primary objective is to authen-
ticate an individual based on a comparison between
an authentication set B, and another enrollment set
A, concealed within a vault using a nonce K . Lin-
ear error correction codes, particularly Reed-Solomon
codes (Juels and Sudan, 2002), are crucial to ensure
reliable and efficient recovery of the nonce in this
cryptographic system, allowing to handle variability
in the enrollment and authentication sets effectively.
2.1.1 Enrollment Stage
The first stage, referred to as enrollment, involves
recording user information into the system. This cor-
responds to a reference set V within the fuzzy vault,
known as the vault. To construct it, a Reed-Solomon
error correction code is employed, incorporating a
biometric set A with n elements from a finite field
F
q
, along with a random nonce vector K of length k .
where each component corresponds to a coefficient of
the polynomial P ∈ F
q
[X]. The choice of n exceeding
k introduces redundancy to permit error detection and
correction during decoding. Concurrently, to ensure
confidentiality, additional chaff points are uniformly
integrated, forming the vault V as illustrated Fig-
ure 2b. This stage consists of two steps: encoding
and adding noise.
a) Encoding: the biometric set is encoded with the
nonce K by associating the elements of A with
their polynomial evaluations. Each element x in A
is evaluated by applying the polynomial P, result-
ing in a value P(x) = y. These pairs (x,y) repre-
sent points in the fuzzy vault (Refer to Figure 2a).
b) Noise: at this step, random pairs (x
′
,y
′
) ∈ F
2
q
,
known as chaff points, are introduced into the set
V . They are specifically chosen to not correspond
to genuine points of A and do not follow the pat-
tern of polynomial evaluations: ∀x
′
/∈ A, y
′
̸=
P(x
′
) (see Figure 2b). Adding these chaff points
aims to make it challenging for attackers to dis-
cern genuine points from chaff points within set
V .
2.1.2 Authentication Stage
The subsequent stage, denoted as authentication,
serves to verify the user’s identity and grant access to
Fuzzy Vault Security Enhancement Avoid Statistical Biases
41
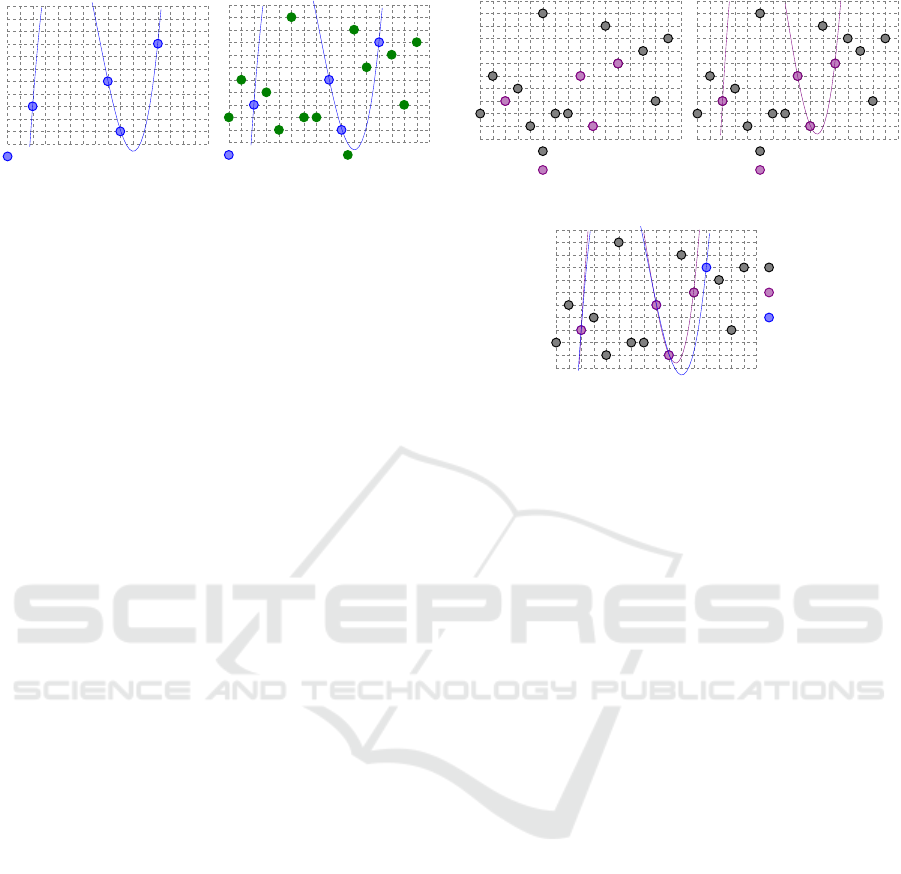
Elements of A
(a) Encoding.
Elements of A
Chaff points
(b) Noise.
Figure 2: Enrollment stage of the fuzzy vault scheme.
appropriate resources. Authentication evaluation de-
pends on the similarity between enrollment set A and
authentication set B, both of size n, irrespective of the
order of their elements.
The retrieval of the random nonce K used during
enrollment is contingent upon the similarity of these
sets. This condition is ensured by a decoding algo-
rithm associated with the codes used during the en-
rollment process, having the ability to correct up to e
errors, referred to as the decoding radius. Therefore,
to accurately recover the nonce K , we check if the
number of discrepancies between the two sets A and
B is bounded by e.
The authentication stage can be divided into three
steps: extraction, decoding, and verification.
a) Extraction: from the reference set V , we extract
pairs (x,y) where x belongs to the authentication
set B; thus, the set Q of size less than or equal to n
is composed of the extracted pairs (see Figure 3a).
b) Decoding: in this phase, a Reed-Solomon decod-
ing algorithm is employed, receiving the set Q
and the length k as inputs. The algorithm produces
a secret K
′
if there’s adequate matching, facilitat-
ing potential error correction (see Figure 3b). Al-
ternatively, it may return a null value if no polyno-
mial aligns with the decoding of the received set
Q .
c) Validation: authentication is successful, enabling
user authentication, only if the candidate nonce
K
′
is identical to the nonce K used during en-
rollment. This condition corresponds to the suffi-
cient sharing of elements between two sets A and
B (see Figure 3c).
2.2 Related Work
Original fuzzy vault scheme proposed by Juels and
Sudan, is generic and can be applied to different pur-
poses. When employed in a biometric context, it re-
quires specific adjustments, primarily driven by con-
siderations related to security, the choice of modality,
the error correction codes parameters choice, and the
Elements of V
Elements of Q
(a) Extraction.
Elements of V
Elements of Q
(b) Decoding.
Elements of V
Elements of Q
Elements of A
(c) Verification.
Figure 3: Authentication stage of fuzzy vault scheme.
concept of a set which is a fundamental characteris-
tic of the fuzzy vault. This is why numerous different
works have been done, to use it in a practical world.
Highlighting the inability to directly implement this
scheme.
The initial difficulty in implementing the fuzzy
vault lies in transforming a biometric template into
a biometric set, a process influenced by the bio-
metric modality and extraction algorithm. Notably,
the minutiae template, is extensively explored in the
fuzzy vault implementations (Uludag et al., 2005;
Nandakumar et al., 2007a; Poon and Miri, 2012; You
and Wang, 2018). Each minutia is characterized by
three values (x, y,θ). The set is achieved through the
concatenation of bits derived from x,y, or x, y and θ.
Minutiae template is a rare case where the concept of
a set is inherently present. However, alignment issues
complicate this process (Merkle et al., 2010; Nagar
et al., 2008). Many studies have investigated the ap-
plication of the fuzzy vault with biometric templates
represented as feature vectors. The type of template
we are interested in our study for different modali-
ties. For example, in study (Lee et al., 2008), a se-
cure fuzzy vault system employs local iris features
and clustering techniques for accuracy, ensuring prox-
imity between sets A and B in both biometric data
and error-correcting codes. Another instance is seen
in (Rathgeb et al., 2016), which introduces a multi-
instance iris biometric cryptosystem, requiring a par-
titioning method for subsets based on each feature set.
The secondary difficulty pertains to the parameter
selection of an error correction code and its contex-
tual relevance. Various methodologies are employed
in reconstructing the secret K from Reed-Solomon
SECRYPT 2024 - 21st International Conference on Security and Cryptography
42

codes. Some researchers, faced with issues, opt for
using a secret structured by a code such as Cyclic
Redundancy Check (CRC), involving polynomial re-
construction through exhaustive search (Nandakumar
et al., 2007a; You and Wang, 2018; V.S.Meenakshi
and Padmavathi, 2010), aiming to avoid False Rejects.
However, considerations regarding execution time are
discussed (Khalil-Hani et al., 2013). Different stud-
ies have highlighted concerns about the efficiency and
this approach’s security, suggesting the use of decod-
ing algorithms for Reed-Solomon codes (Velciu et al.,
2015).
The scheme’s security is a major concern, eval-
uated in various contexts and against different at-
tack scenarios (Nandakumar et al., 2007b; Benham-
madi and Bey, 2014; Radha et al., 2010). Studies
focus on improving biometric data integrity, espe-
cially by assessing the False Acceptance Rate (FAR).
Another approach involves evaluating min-entropy in
protected models, offering insights into leaked infor-
mation and the maximum probability of uncovering
the secret (Merkle et al., 2010; Dodis et al., 2008). In
their theoretical framework, Juels and Sudan do not
explicitly consider biases in security analysis. They
rely on a uniform distribution, establishing a security
upper bound, and acknowledging the lack of justifica-
tion for assuming uniformity. Other research supports
this assertion by noting that non-uniformity in stored
data can jeopardize the scheme’s security (Nandaku-
mar et al., 2007a; Merkle et al., 2010; Nagar et al.,
2008). To overcome this limitation, some studies pro-
pose adding a password (Reddy and Babu, 2008; Nan-
dakumar et al., 2007b; Benhammadi and Bey, 2014),
known as a Hard fuzzy vault. The user is required
to capture their biometric data and enter a password.
Currently, no proposal for a secure fuzzy vault against
such statistical attacks without additional information
is known.
3 BIOMETRIC SET AND BIAS
ASSESSMENT
This section details vault construction and its bias re-
sistance, particularly against database attacks. We
discuss the set creation function designed for feature
models, explore theoretical measures for bias assess-
ment in biometric sets, and review attacker models to
evaluate fuzzy vault security.
3.1 Construction Biometric Set
The fuzzy vault scheme is characterized by its use of
unordered sets. Our methodology employs a transfor-
mation approach tailored for feature templates from
diverse biometric modalities, conceptually similar to
the method in (Rathgeb et al., 2016) which encodes
already features as unordered sets. However, our ap-
proach differs by taking into account individual vari-
ability and specific parameters, thereby enhancing
authentication reliability and ensuring accuracy and
compatibility with various biometric systems.
Feature values in biometric templates vary across
captures from the same user. To ensure reliable identi-
fication and appropriate access, we use min-max nor-
malization to address this variability. This technique,
widely acknowledged for enhancing system reliabil-
ity through precise and consistent data representation,
is crucial for maintaining consistency in each fea-
ture’s distribution relative to the initial data and effec-
tively managing data variability (Zheng and Casari,
2018). Employing this approach also facilitates the
security assessment of the fuzzy vault system by ac-
counting for statistical biases in feature distributions
within biometric samples.
This methodology enables the grouping of multi-
ple feature values within a similar range. The normal-
ization process converts the real values of each fea-
ture i into values ranging from 0 to 1 (⋆), using the
minimum min
i
and maximum max
i
values associated
with each feature. Subsequently, the value is encoded
using m
1
bits, representing the exponent of a prime
number in our system. The selection of m
1
is based
on the template base, aiming to choose the value that
best distinguishes users. This selection results from
experiments to determine the optimal number of bits
to use, which may vary from one base to another.
Given a template containing n features, the nor-
malized value f
n
i
of each features f
i
, encoded in m
1
bits, is obtained by applying the following formula:
f
n
i
= ⌊
( f
i
−min
i
)
max
i
−min
i
× 2
m
1
⌋.
(⋆)
To construct a biometric set, we introduce the
function S that maps elements encoded with m
1
bits
into a biometric set within a finite field F
2
p
, where
each element corresponds to specific features. Let S
represent function (⋆⋆), which takes as input the m
2
bits of the index, encoded with the binary length of the
biometric template size, and the m
1
bits of the feature
value obtained from (⋆). Through the concatenation
of these input elements, this function produces an el-
ement within the finite field F
2
p
, where p = m
2
+ m
1
.
S : {0,1}
m
2
× {0, 1}
m
1
→ F
2
p
(i, f
n
i
) 7→ e = i| f
n
i
. (⋆⋆)
Fuzzy Vault Security Enhancement Avoid Statistical Biases
43

3.2 Bias Quantification
Our analysis specifically focuses on statistical biases
in biometric sets by features, aiming to understand
how they affect the fuzzy vault system’s security and
quantitatively evaluate their effects. Using a training
sample TrainingS of the biometric template, we gen-
erate the biometric set from this sample using the spe-
cific transformation function (⋆⋆). We propose quan-
tifying these biases in two distinct scenarios.
A. Scenario 1: in this context, we disregard features
and calculate the frequencies of elements in the fi-
nite field F
2
p
within biometric sets of TrainingS.
This calculation is established by scaling the repe-
titions of each element e ∈ F
2
p
(denoted as rep(e))
by the product of sample size |TrainingS | and 2
m
2
,
representing the total number of elements (Rice,
2006):
freq(e) =
rep(e)
|TrainingS| × 2
m
2
.
B. Scenario 2: in this context, the significance of the
order of features is considered. We calculate the
frequencies of elements f
n
i
for each feature, from
biometric sets of TrainingS . We compute the fre-
quencies of the 2
m
1
elements for each feature i,
using the following formula:
freq( f
n
i
) =
rep( f
n
i
)
|TrainingS|
.
To assess the overall distribution of these elements
in each scenario, we employ Shannon entropy, a met-
ric designed to measure the distribution of occur-
rences and its proximity to a uniform distribution.
Shannon entropy (Cover and Thomas, 2006), de-
noted H
b
(X,D), quantifies the uncertainty of a ran-
dom variable X with outcomes in a finite field and
their associated probabilities D = (p
1
,. .., p
n
), where
p
i
= Pr(X = e
i
). It is calculated using the base
2 logarithm to express information in bits and is
defined as: H
b
(X,D) = −
∑
n
i=1
p
i
log
2
(p
i
). Subse-
quently, for a uniform distribution D
U
, where all out-
comes are equally probable, the entropy simplifies to
H
b
(X,D
U
) = log
2
(n), serving as a benchmark to com-
pare D against an ideal scenario of equal likelihood.
Finally, we propose assessing this outcome
through the measure of statistical bias, denoted as
M (D). This measure is defined as the ratio of Shan-
non entropy of the calculated distribution to the en-
tropy of the uniform distribution, formulated as fol-
lows:
M (D) =
H
b
(X,D)
H
b
(X,D
U
)
.
The measure M generates a numerical value
lower than 1. Any deviation from M compared to
1 indicates that the distribution is far from being uni-
form. This observation facilitates the quantification of
the effect of statistical biases, thereby aiding in evalu-
ating their influence on the security of the fuzzy vault.
3.3 Authentication Attacker Models
We evaluate the impact of statistical biases on secu-
rity by introducing an attacker model that uses knowl-
edge of biometric set distribution. This model con-
trasts with Juels and Sudan’s, which is based on par-
tial knowledge and is less clear. Additionally, we pro-
pose a model based on vault knowledge alone. To
compare these models and understand how vault size
and attacker knowledge influence security, we assess
authentication efficacy across various vault sizes and
attack scenarios.
A- Distribution-Knowledge Attacker (DKA:) in this
model, the attacker, having gained access to the
vault, also possesses knowledge of the distribu-
tion of elements from the biometric set within the
finite field. To generate n elements for an authen-
tication set B, the attacker draws from the vault
according to this distribution. When the vault’s
size is smaller than the size of elements with prob-
ability in the sample, it becomes vital to concen-
trate solely on the present elements in the vault.
To address this, we use a smoothing technique (Si-
monoff, 2012) to establish a new probability dis-
tribution. This method assigns a minimal, yet
nonzero, probability to elements not found in r.
This probability is contingent on the lowest prob-
ability within the sample, signifying that absent
occurrences are improbable but not impossible.
Using this updated distribution, the attacker ran-
domly chooses elements from r to compose n ele-
ments within the authentication set.
B- Partial Knowledge Attacker (PKA:) this model,
proposed in (Juels and Sudan, 2002), formalizes
the security framework by incorporating the con-
cept of partial knowledge attributed to the ad-
versary. Authors assume that the enrollment set
is chosen according to a potentially non-uniform
distribution, but they do not quantify security with
biases, they assume a scenario where an attacker
possesses knowledge of a part of the set. How-
ever, these are two distinct concepts. To illus-
trate, consider attempting to guess a password.
Knowing the distribution of passwords provides
a significant advantage, but it doesn’t reveal spe-
cific letters in a given password from that distribu-
tion. Conversely, knowing specific letters offers
SECRYPT 2024 - 21st International Conference on Security and Cryptography
44

an additional advantage. Thus, these two forms of
knowledge appear complementary.
To identify values of the partial set α that hold
significance for the attacker and serve as a real-
istic prerequisite, we analyze this attack scenario
to evaluate the vault’s security across different
knowledge levels. Our method entails being in-
formed about different values of α elements from
A. To complete the remaining n − α elements, we
use a uniform selection from the remaining ele-
ments of V .
C- Uniform Attacker (UA:) we intend to compare
the advantage of the previous model with that ob-
served when no prior information is available. In
this context, the attacker possesses only knowl-
edge about the vault itself. To generate the au-
thentication set B, the attacker uniformly selects
n elements from the r elements contained in the
vault. This implies that each element in the vault
has an equal probability of being chosen to be part
of the authentication set B.
Studying and comparing the attacker’s advantage
in these three models provides valuable insights into
assessing the impact on the security of the fuzzy vault.
This analysis aids in identifying the most sensitive or
vulnerable information within each model, facilitat-
ing adjustments in security measures and countermea-
sures accordingly.
4 FUZZY VAULT
CONSTRUCTION
In this section, we introduce the three biometric tem-
plate bases derived from different modalities, each
exhibiting unique quality levels. Quality Quality as-
sessment of each base relies on False Rejection Rates
(FRR) and False Acceptance Rates (FAR). When
these rates are equal, they represent the Equal Error
Rate (EER). Minimizing these rates enhances the sys-
tem’s authentication performance. Next, we present
the fuzzy vault parameters obtained for each base
used.
4.1 Biometric Templates Bases
Our approach is dedicated to biometric template bases
categorized by features, We use three bases derived
from different modalities (see Table 1), each ex-
hibiting varying levels of quality in terms of EER.
These include the FVC fingerprint base, the PTB
base of electrocardiograms used in (Gernot and
Lacharme, 2022), and the higher-quality LFW base,
used in (Dong et al., 2019). Each base contains T
biometric templates for each of the N distinct individ-
uals. An extraction algorithm applied to the image
yields a feature vector of size n.
4.2 Fuzzy Vault Parameters
This section provides a concise overview of the es-
sential parameters for constructing the reference set
V , stored in the fuzzy vault. The specifications are
tailored to the specificities of each biometric template
base, as presented Table 2.
A. Biometric set size n: our set construction func-
tion establishes a mapping between each binary
feature sequence of m
1
bits and an element of the
finite field F
2
p
associated with the biometric set.
The set size corresponds to the number of features
in the template specific to the biometric template
base, denoted as n.
B. Secret length k: the secret length k is directly
linked to e and influences the authentication algo-
rithm based on Peterson-Berlekamp-Massey. This
algorithm can correct up to e = ⌊
n−k
2
⌋ errors. The
minimal intersection I between the sets A and B
is crucial, where I = n − e = ⌊
n+k
2
⌋.
To select k, we calculate the FAR and FRR rates
for various threshold values I. The objective
is to achieve a balance between security (mini-
mized FAR) and user-friendly interaction (con-
trolled FRR). The optimal threshold I is deter-
mined as the intersection between the discrete
curves of FAR and FRR, corresponding to the
(EER) with the biometric set. If achieving this
equality proves impossible, a preferred threshold
is selected to minimize FAR. Depending on each
base, different thresholds are obtained. To main-
tain these levels of authentication as indicated Ta-
ble 3, we select k with consideration to variable
I, taking into account error corrections with the
decoding algorithm, k = 2I − n.
C. Vault size r: the construction of the set V re-
lies on the addition of chaff points, dependent on
the function S and parameters (m
1
,m
2
) specific to
each biometric template base, ensuring their in-
discernibility from the biometric set’s elements.
The choice of variable m
1
is made to allow bet-
ter differentiation between biometric sets of dif-
ferent users and to manage variability among dif-
ferent templates from the same user. This decision
is also correlated with the FAR and FRR rates.
Thus, following tests on our bases, the appropri-
ate choice is m
1
= 2. As for m
2
, it represents
the smallest possible value satisfying the condi-
Fuzzy Vault Security Enhancement Avoid Statistical Biases
45
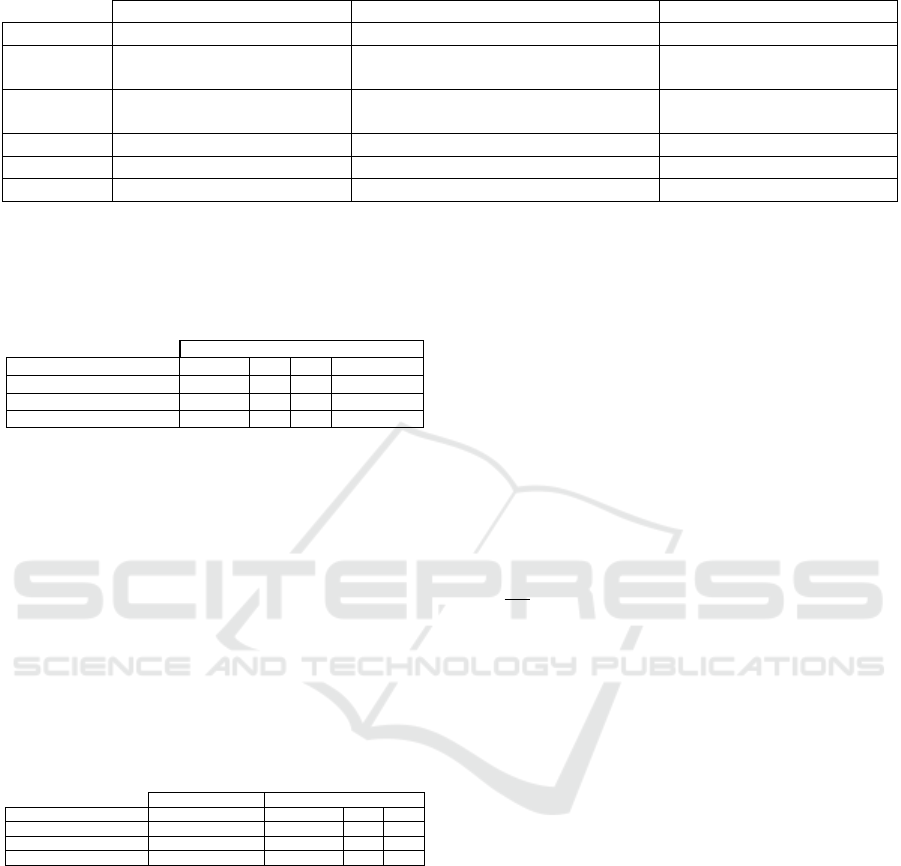
Table 1: Biometric templates bases.
FVC PTB LFW
Modality Fingerprints Electrocardiogram Face
Image
database
FVC2002 (Maio et al.,
2002)
LFW (Bousseljot et al., 1995; Gold-
berger et al., 2000)
(Huang et al., 2008)
Extraction
algorithm
Gabor filters (Belguechi
et al., 2016)
ECG wave delineation (Martinez
et al., 2004; Makowski et al., 2021)
deep network Insight-
Face (Dong et al., 2019)
N 100 158 158
T 8 7 10
n 512 990 512
tion n ≤ 2
m
2
, with n being the number of features
in the vector. Our construction of set V involves
choosing sizes ranging from n × 2 to n × 2
m
1
.
Table 2: Fuzzy vault parameters for each template base.
Fuzzy vault parameters
Biometric template base (m
1
,m
2
) n k r
FVC (2,9) 512 65 [1024,2048]
PTB (2,10) 990 273 [1980,3960]
LFW (2,9) 512 9 [1024,2048]
The objective of the fuzzy vault is to enable com-
parison for authentication. Our encoding method ef-
fectively protects data with minimal impact on au-
thentication system performance, as evidenced by the
obtained rates Table 3. The degradation in the authen-
tication rate remains limited, with an observed impact
of about 7%. For example, in the FVC base, an EER
of 17% is obtained. However, in the PTB base, our
method leads to an improvement in authentication and
a reduction of approximately 3.8% in the EER. For
the LFW base, no EER is obtained, and therefore, we
choose a threshold of k = 9 for which FAR rates are
minimal and do not impact security.
Table 3: Authentication rates.
biometric template biometric set
Biometric template base EER FAR FRR EER
FVC 10% 17% 17% 17%
PTB 10.8% 7% 7% 7%
LFW 0.2% 9.5 × 10
−4
% 4% -
5 CONDUCTING
AUTHENTICATION ATTACKS
Based on the framework from Section 4, this section
evaluates the security and practicality of the fuzzy
vault. We detail quantitative results on its resilience
against statistical biases exploited through biometric
set features. Multiple vaults are constructed for each
base, followed by authentication tests against various
attacker models previously introduced.
During each testing phase, a sample TrainingS,
comprising 60% of individuals from the base, is used
to evaluate biases in the biometric set, with one tem-
plate per person. The remaining 40% sample, referred
to as TestS, is reserved for authentication testing. This
distribution is consistently maintained across all three
template bases. The initial stage in the fuzzy vault
process is enrollment. Considering sample TestS with
|TestS| = N ∗ 40%, we construct the associated vault
by incorporating the previously presented parameters,
generating vaults with sizes r ranging from 2n to
n×2
m
1
. During authentication stage, we create 50 au-
thentication sets B for each vault. This authentication
process is conducted using the three attacker models,
depending on the specific scenario being investigated.
The validity of authentication is conditioned by
the number of common elements between the authen-
tication set B and enrolment set A. We define two
sets to be close if their intersection is at least equal
to ⌊
n+k
2
⌋, and then the decoding algorithm guarantees
the correction of other errors. To calculate the authen-
tication rate for each vault, we determine the ratio of
valid sets B to the total number of constructed sets,
which is |TestS|×50. The success rates computed for
each attacker model will be compared to analyze the
impact of the acquired knowledge, as visualized in the
graphs below.
5.1 Results
To exploit biases, we focus on two attack scenarios.
The first scenario relies on a global frequency analy-
sis, where the assembly of the biometric set is per-
formed without considering the order of elements.
Conversely, the second scenario takes into account
the specific distribution of each feature, thus adopt-
ing a more in-depth approach based on feature-based
construction. Starting from each of the three tem-
plate bases, we initially assess the biases inherent in
the associated biometric sets and perform quantitative
measurements M . Subsequently, we conduct authen-
tication by leveraging the quantified biases, as well as
considering two other attacker models. The outcomes
of the authentication rates are then presented in the
form of curve graphs for each reference vault set of
size r.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
46

Every color in graph denotes the authentication
rate associated with a specific attacker model, the red
represents an attacker with knowledge of the distri-
bution (DKA), while the black signifies a uniform at-
tacker (UA). The green, purple, and blue shades rep-
resent attackers with partial knowledge, each having
different levels of information (PKAα%).
A. Scenario 1: in this context, the order of features is
disregarded. From a sample of the biometric set,
the frequency of each element e ∈ F
2
p
is calcu-
lated, thereby determining the measure M .
The specific results for the FVC, PTB, and LFW
bases are 0.92 and 0.93, 0.94 respectively Table 4,
indicating that they deviate significantly from a
uniform distribution. Notably, there is a range of
information concentration levels observed among
the three bases, reflecting their divergence from
uniformity. This observed diversity is associated
with the quality of the base. A less pronounced
dispersion is noted in the FVC database, which
exhibits an EER rate of 17%, while the results for
the LFW database, with a FAR of 4% and an FRR
close to 0%, show greater dispersion.
Table 4: M (D) of biometric set.
template base FVC PTB LFW
M (D) 0.92 0.93 0.94
Overall, the measurements indicate pronounced
diversity within the biometric set, with significant
deviations from the uniform distribution. Specifi-
cally, pronounced disparities are observed in bi-
ases among biometric sets from different bio-
metric template bases, particularly with the FVC
showing a more marked deviation with a measure-
ment of 0.92 compared to the uniform distribu-
tion, in contrast to the set from the base LFW
with a measurement of 0.94. Through subse-
quent tests, we will seek to determine whether the
slight differences observed among these measures
will have a significant or negligible impact on the
vault’s security.
The results from Figure 4 indicate that, across all
bases, the advantages of the three applied attacker
models gradually decrease as the size of the vault
r increases. With the FVC base, it is observed
that knowledge of the set distribution, as depicted
by the red curve, provides a significant advantage
to the attacker compared to the other two bases
where this advantage decreases for sizes starting
from 3 ∗ n.
For the partial knowledge attacker model, we pos-
sess, in each case, knowledge of proportions of
25%, 40%, and 50% of the enrollment biometric
set. The results obtained reveal that for all bases,
knowledge of the distribution is always more im-
portant than knowledge of 25% of the informa-
tion (represented in green), which still constitutes
a significant bound. Even in the case of the FVC
with multiple vault size r Figure 4a, the advantage
obtained using the distribution is more significant
than knowledge of 40%, and close to 50%. On
the PTB base, we achieve the best rate with the
red curve, surpassing the advantage gained with
the knowledge of 50% of the enrollment set Fig-
ure 4b. However, it is important to note that
these knowledge percentages are unrealistic and
do not represent a plausible attacker model, un-
like knowledge of the distribution, which seems
more practical.
The fifth black curve illustrates the advantage of
a database-side attacker without any additional
information, attempting to build elements of the
set by drawing uniformly. It is observed that
the vault’s security remains intact, with the at-
tacker frequently unable to gain any advantage.
This supports the highest security threshold of the
fuzzy vault under uniform conditions, consistent
with assertions made by prior researchers. Com-
paring (DKA) and (UA) models, the red curve’s
notable advantage over the black indicates that ex-
ploiting set biases can weaken the fuzzy vault’s
security.
In connection with the base quality and measure
M , it is observed that the difference of 0.1 be-
tween the calculated measures Table 4 signifi-
cantly impacts the vault’s security against the at-
tacker model considering the distribution. This
is evident when comparing the degradation of the
red curve across the three bases.
B. Scenario 2:
In this context, the relevance of knowledge
through distribution becomes more pronounced,
allowing for the provision of specific information
regarding the distribution of each feature. We cal-
culate the M
i
metric for each feature i among the
n in the template to assess the irregularity or dis-
persion of the feature values distribution.
The results from measuring feature biases reveal
pronounced differences across the various bases.
The majority of features for all three bases showed
a M value ranging between 0.6 and 0.8, suggest-
ing significant biases when compared to a uniform
distribution. A few features, however, scored
above 0.9, indicating less bias. Notably, in the
FVC and PTB bases, some features recorded en-
tropy measures below 0.5. A few feature groups
even demonstrated distributions that were quite
Fuzzy Vault Security Enhancement Avoid Statistical Biases
47
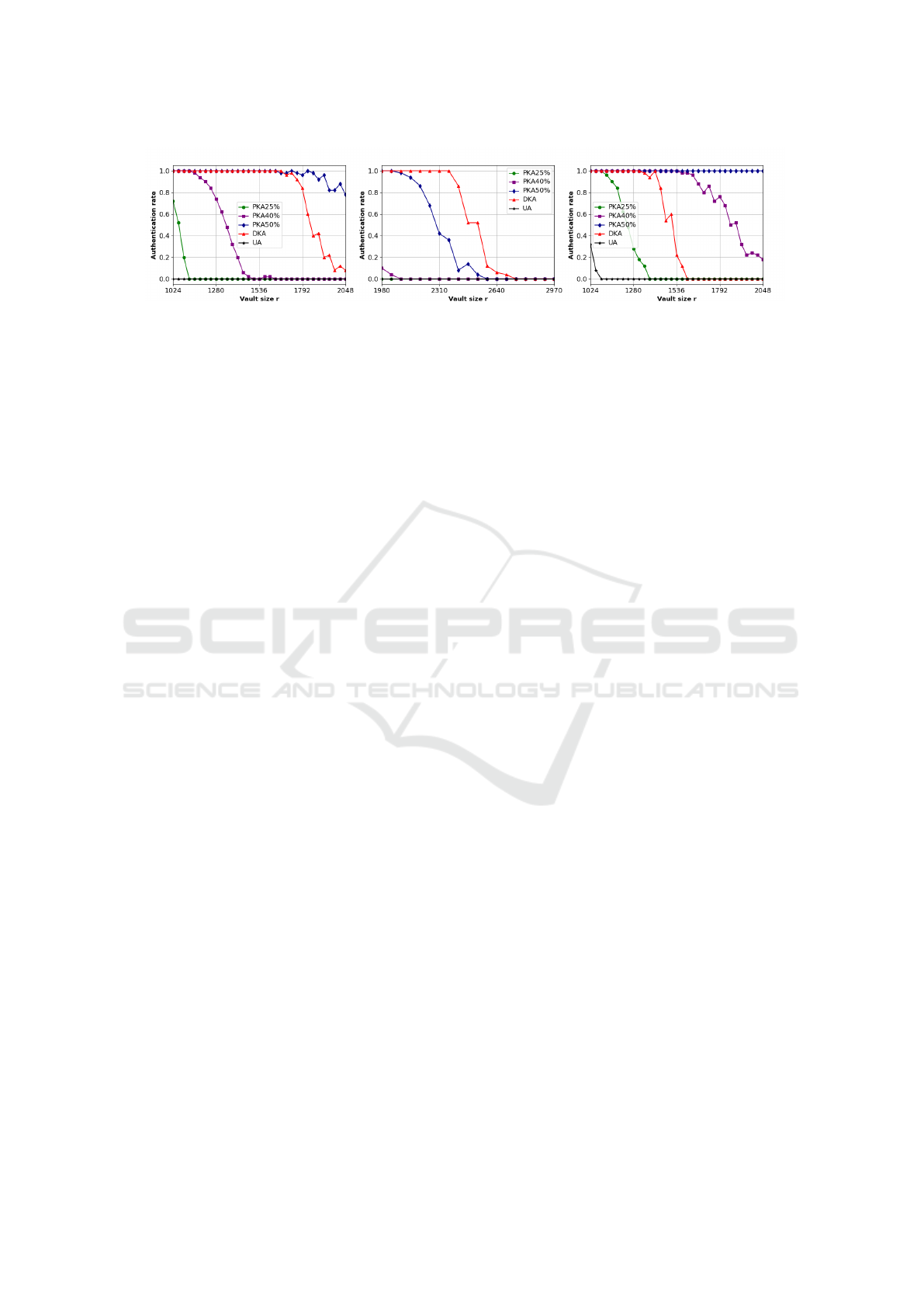
(a) FVC. (b) PTB. (c) LFW.
Figure 4: Authentication for scenario 1.
structured or condensed, with measures below
0.3. These findings will be used to assess their
impact on the security of the vault.
In establishing the construction of the authenti-
cation set based on features, using each of the
considered models. For the partial knowledge
attacker model, we assume knowledge of 25%,
30%, and 35% proportions of the enrollment set.
The results presented Figure 5 highlight a signif-
icant deterioration in the vault’s security through
this feature-based approach. The three bases cor-
roborate this observation. In general, authentica-
tion rates in this scenario are significantly higher,
attributable to additional specific information as-
sociated with each feature. With FVC Figure 5a,
success rates approach 40% for most vault sizes
and reach around 10% for sizes approaching the
maximum value of r. In this scenario, compared
to Figure 4b and 4c, we observe that more chaff
points are needed to diminish the significance of
the distribution advantage, as illustrated in Fig-
ure 5b and 5c.
Furthermore, with these bases of varying quality,
a correlation is observed between the base qual-
ity and knowledge of the distribution: the higher
the base quality, the less significant the impact of
biases. As depicted Figure 5c, knowing the distri-
bution is more advantageous than knowing 25%
of the biometric set with the LFW base, in con-
trast to the PTB and FVC bases. In these cases,
knowledge of the distribution proves to be more
advantageous than knowing 35% of the set, with
the distribution conferring a more substantial ad-
vantage over all other models.
5.2 Discussion
We have presented the results of our attack scenarios
applied to three distinct template bases, characterized
by different modalities and qualities. We assessed the
resilience of the fuzzy vault against these three differ-
ent attacker models.
Our initial observation reveals that the authenti-
cation rates obtained using the distribution model are
substantial, affirming the scheme’s inability to with-
stand such attacks, this casts doubt on its feasibility
in such conditions and raises concerns about the fuzzy
vault’s security, especially in the case of feature-based
construction, where we quantify biases related to fea-
tures.
In comparison with the model suggested by Juels
and Sudan, we illustrate that this model requires sub-
stantial knowledge to achieve a security level compa-
rable to distribution knowledge, necessitating at least
30% of the enrollment set. This significant require-
ment is less apparent in the context of individual sen-
sitive data.
In the scenario involving global data, the advan-
tage is less pronounced than with feature-based con-
struction. However, we observe a convergence of suc-
cess rates with a non-realistic information knowledge
model. This underscores the critical importance of
the model used and its direct impact on security. It
calls into question the scheme’s ability to withstand
this specific model, highlighting a potential vulnera-
bility.
6 SECURE SINGLE-FACTOR
FUZZY VAULT
The results of the previous section indicate that
the original fuzzy vault cannot be considered se-
cure, particularly when exploiting biases by features.
This quantification, along with the suggested attacker
model, helps us understand the dispersion of elements
in the set. Differently from previous studies, we
present the first solution while maintaining the orig-
inal proposition of the fuzzy vault scheme, without
modifying its inherent nature.
For our proposed solution, the goal is to avoid
significant concentration within value ranges for each
feature, thereby reducing biases in biometric sets by
ensuring a balanced distribution for each feature. We
SECRYPT 2024 - 21st International Conference on Security and Cryptography
48
(a) FVC. (b) PTB. (c) LFW.
Figure 5: Authentication for scenario 2.
rely on a quantile method, dividing the data for each
feature into intervals of equal probability, where each
integer appears with the same frequency.
6.1 Fuzzy Vault Parameters
Using the quantile method to mitigate biases in each
feature decreases dominant feature values, conse-
quently lowering the system’s authentication level.
Therefore, we reassess our selection of the value m
1
for the quantile method. Setting m
1
= 1 uses binary
encoding for each feature based on its median, which
minimizes data dispersion and aids in managing tem-
plate value variability to achieve an EER with the bio-
metric set. However, this parameter decreases the
number of image elements of the function (⋆⋆), re-
sulting in fewer chaff points for vault V . Assuming
the attacker knows all parameters, this compromises
the vault’s security. Despite reduced authentication
from increased data dispersion, for security reasons,
we choose m
1
= 2, providing four possible values cor-
responding to employing the quartile method. This di-
vides the data into four equal parts, each representing
25%. Subsequently, an integer between 0 and 2
m
1
− 1
is associated with each interval, aiming to generate a
sufficiently large finite field with function (⋆⋆). With
this choice of m
1
, we obtain the same values for n and
r as those presented Table 2.
The correlation between the secret length k and
authentication rates indicates that longer lengths are
associated with reduced error correction. Employ-
ing the quartile method reveals variations in FAR and
FRR rates. Regardless of specific k values, an in-
crease in length is associated with higher FRR and
lower FAR. During vault construction, emphasis is
placed on selecting the smallest suitable value for k,
tailored to the biometric template base. The follow-
ing Table 5 presents the FAR and FRR results ob-
tained for each base along with the corresponding k.
Overall, the three bases do not exhibit an EER,
displaying FAR rates below 2% for all bases, thereby
enhancing the fuzzy vault’s security. However, the
FRR rate has shown a significant increase for two
Table 5: Authentication rates.
biometric template biometric set
Biometric template base EER k FAR FRR
FVC 10% 5 1.3% 56%
PTB 10.8% 9 2% 6%
LFW 0.2% 4 0% 75%
databases, FVC and LFW, making usability less
straightforward, requiring the user to authenticate re-
peatedly with a more precise representation of the
biometric data until successful, while with PTB bases,
no degradation is observed Table 5. Using our method
removes biases from features, but considering the
FRR results for some bases, one approach to reducing
them could involve retaining certain biases, balancing
system usability and security against statistical biases
in features.
6.2 Results
Given that scenario 2, characterized by a feature-
based attack, poses the most formidable threat com-
promising the integrity of the fuzzy vault and render-
ing it intricate to use. In this same scenario, we aim to
quantify the biases of each feature obtained through
the application of the quartile method. Subsequently,
we intend to assess the advantages resulting from the
exploitation of these biases and determine if this com-
promises the security of the fuzzy vault scheme once
again.
The objective of our quartile method is to obtain
features with more balanced values closer to unifor-
mity. Reassessing the biases of features using the
measure M , as expected, reveals a predominance of
features with a M measurement exceeding 0.9, con-
trasting with previous results where the majority were
between 0.6 and 0.8.
To quantify the effectiveness of our proposed so-
lution, we replicate the attack on the three bases using
identical attacker models similar to those in scenario
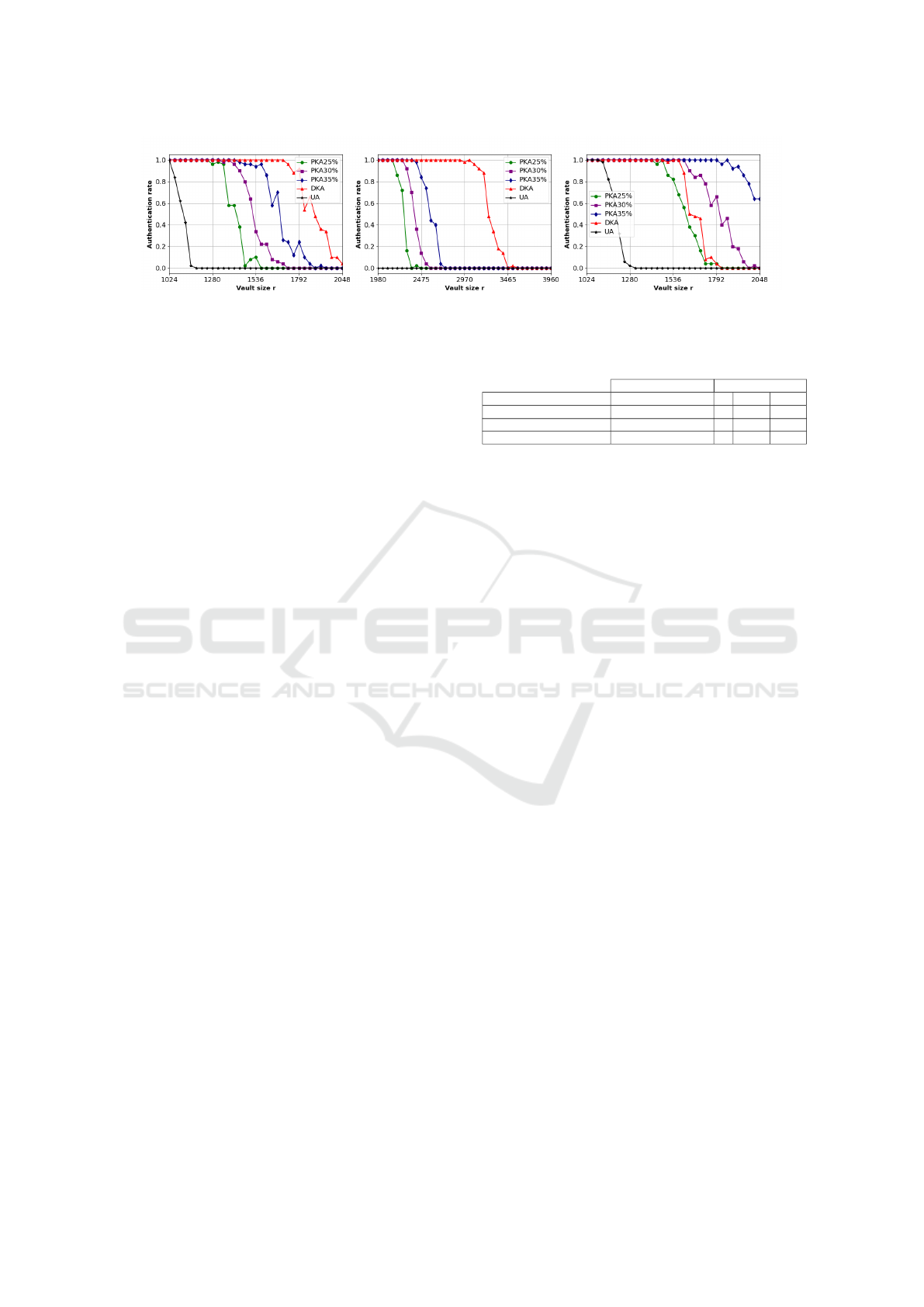
2. The results are visually presented Figure 6.
The advantage of an attacker exploiting biases de-
creases significantly. Based on the results from the
three bases, in line with our method used to remove
Fuzzy Vault Security Enhancement Avoid Statistical Biases
49
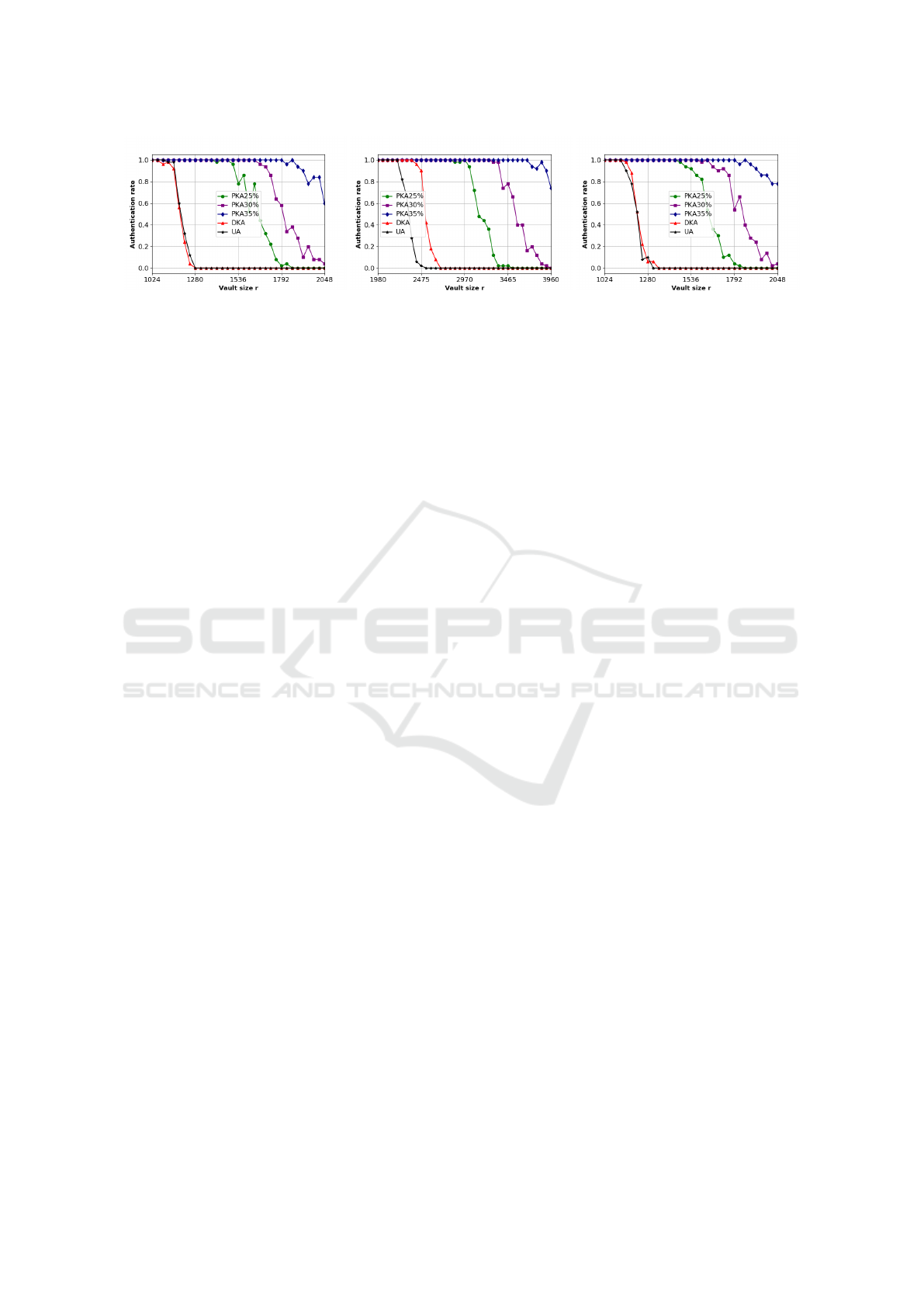
(a) FVC. (b) PTB. (c) LFW.
Figure 6: Authentication rate with quantile method.
biases by features, we achieve an advantage of the
red curve similar to that of the black curve, obtained
through uniform sampling. Specifically, with vault
sizes much smaller than n ∗ 3, it is observed that the
vault becomes more secure without the need to add
numerous chaff points. These conclusions also hold
for Scenario 1, where there is no knowledge of bi-
ases specific to the features. Thus, the quartile method
eliminates the effectiveness of bias attacks while pre-
serving the nature of the proposed original scheme.
To conclude this study, we have proposed a first
method based on eliminating biases from each feature
during the transformation of a template into a biomet-
ric set, This approach employs the quantile method
to ensure a fair presentation of each feature’s values.
Unlike methods to enhance the vault’s security by
adding passwords, our single-factor-based proposal
maintains an equivalent level of security in the case
of uniformity without requiring additional informa-
tion. We have presented a solution to mitigate biases
in each feature and mitigate attacks specifically aimed
at these features. Nonetheless, the potential for an at-
tack exploiting the correlation between features per-
sists. This scenario could render biases exploitable,
thus compromising the vault’s security.
7 CONCLUSION
In this study, we have quantified the advantage of ex-
ploiting statistical biases in the biometric sets of the
fuzzy vault, compromising its security and rendering
its use by the initial proposal unfeasible. In response
to these vulnerabilities, we have introduced a first
method for a secure single-factor fuzzy vault authenti-
cation, aligned with the initial proposition. Quantiles
were employed to achieve a balanced distribution of
the values for each feature, eliminating the need for
additional information and avoiding the use of multi-
factor authentication.
We have obtained preliminary results support-
ing the effectiveness of the single-factor fuzzy vault,
which is not sensitive to feature biases, highlighting
a significant correlation between its security and the
construction function of the biometric sets. Currently,
it is still possible to deduce the corresponding feature
of the biometric template from an element of the bio-
metric set. One method to prevent this is to add a
secret on the server side to protect the parameters of
the construction function, thereby enhancing security
while maintaining the single-factor scheme and elim-
inating attacks based on features, thus avoiding a cor-
relation attack between features. This approach also
helps avoid constraints related to parameter choices,
improving system performance.
REFERENCES
Belguechi, R., Hafiane, A., Cherrierand, E., and Rosen-
berger, C. (2016). Comparative study on texture char-
acteristics for fingerprint recognition: application to
the biohashing template protection scheme. Journal
of Electronic Imaging.
Benhammadi, F. and Bey, K. B. (2014). Password hard-
ened fuzzy vault for fingerprint authentication system.
Image and Vision Computing.
Bousseljot, R., Kreiseler, D., and Schnabel, A. (1995).
Nutzung der ekg-signaldatenbank cardiodat der ptb
¨
uber das internet.
Cover, T. M. and Thomas, J. A. (2006). Elements of infor-
mation theory. Wiley-Interscience.
Dargan, S. and Kumar, M. (2020). A comprehensive survey
on the biometric recognition systems based on phys-
iological and behavioral modalities. Expert Systems
with Applications 143.
Daugman, J. (2004). How iris recognition works. IEEE
TRANSACTIONS ON CIRCUITS and SYSTEMS FOR
VIDEO TECHNOLOGY.
Dodis, Y., Ostrovsky, R., Reyzin, L., and Smith, A. (2008).
Fuzzy extractors: How to generate strong keys from
biometrics and other noisy data. SIAM Journal on
Computing.
Dong, X., Jin, Z., and Jin, A. T. B. (2019). A genetic algo-
rithm enabled similarity-based attack on cancellable
biometrics. In IEEE Inter-BIBLIOGRAPHIE 119 na-
tional Conference on Biometrics : Theory, Applica-
tions and Systems (BTAS).
SECRYPT 2024 - 21st International Conference on Security and Cryptography
50

Gernot, T. and Lacharme, P. (2022). Biometric masterkeys.
Computers & Security.
Goldberger, A. L., Amaral, L. A., Glass, L., Hausdorff,
J. M., Ivanov, P. C., Mark, R. G., Mietus, J. E., Moody,
G. B., Peng, C. K., and Stanley, H. E. (2000). Phys-
iobank, physiotoolkit, and physionet : Components of
a new research resource for complex physiologic sig-
nals.
Huang, G. B., Mattar, M., Berg, T., and Learned-Miller,
E. (2008). Labeled faces in the wild: A database
for studying face recognition in unconstrained envi-
ronments. in Workshop on faces in’Real-Life’Images:
detection, alignment, and recognition.
Juels, A. and Sudan, M. (2002). A fuzzy vault scheme.
Proceedings IEEE International Symposium on Infor-
mation Theory.
Khalil-Hani, M., Marsono, M. N., and Bakhteri, R. (2013).
Biometric encryption based on a fuzzy vault scheme
with a fast chaff generation algorithm. Future Gener-
ation Computer Systems.
Lee, Y. J., Park, K. R., Lee, S. J., Bae, K., and Kim, J.
(2008). A new method for generating an invariant iris
private key based on the fuzzy vault system. IEEE
Transactions on Systems Man and Cybernetics Part B
(Cybernetics).
Maio, D., Maltonil, D., Cappelli, R., Wayman, J., and Jain,
A. (2002). Fvc2002: Second fingerprint verification
competition. Proceedings of the 16th International
Conference on Pattern Recognition (ICPR).
Makowski, D., Pham, T., Lau, Z., and Brammer,
J. (2021). Neurokit2 : The python tool-
box for neurophysiological signal processing.
https://github.com/neuropsychology/NeuroKit.
Martinez, J., Almeida, R., Olmos, S., Rocha, A., and La-
guna, P. (2004). A wavelet-based ecg delineator : eval-
uation on standard databases. IEEE Transactions on
Biomedical Engineering, 51(4) :570–581. 28.
Merkle, J., Niesing, M., Schwaiger, M., Ihmor, H., and Ko-
rte, U. (2010). Security capacity of the fuzzy finger-
print vault. International Journal on Advances in Se-
curity.
Nagar, A., Nandakumar, K., and Jain, A. K. (2008). Secur-
ing fingerprint template: Fuzzy vault with minutiae
descriptors. 19th International Conference on Pattern
Recognition.
Nandakumar, K., Jain, A. K., and Pankanti, S. (2007a).
Fingerprint-based fuzzy vault: Implementation and
performance. IEEE Transactions on Information
Forensics and Security.
Nandakumar, K., Nagar, A., and Jain, A. K. (2007b). Hard-
ening fingerprint fuzzy vault using password. Ad-
vances in Biometrics International Conference ICB.
Poon, H. T. and Miri, A. (2012). On efficient decoding for
the fuzzy vault scheme. 11th International Conference
on Information Science, Signal Processing and their
Applications (ISSPA).
Radha, N., Karthikeyan, S., and P.Anupriya (2010). Se-
curing retina fuzzy vault system using soft biometrics.
Global Journal of Computer Science and Technology.
Rathgeb, C., Tams, B., Merkle, J., Nesterowicz, V., Korte,
U., and Neu, M. (2023). Multi-biometric fuzzy vault
based on face and fingerprints. Computer Science.
Rathgeb, C., Tams, B., Wagner, J., and Busch, C. (2016).
Unlinkable improved multi-biometric iris fuzzy vault.
EURASIP Journal on Information Security.
Reddy, E. S. and Babu, I. R. (2008). Performance of iris
based hard fuzzy vault. IEEE International Confer-
ence on Computer and Information Technology Work-
shops CIT, 8.
Rice, J. A. (2006). Mathematical statistics and data analysis.
Duxbury Press.
Sharma, A., Raghuwanshi, A., and Sharma, V. (2015). Bio-
metric system-a review. Int. J.Comput. Sci. Inf. Tech-
nol.
Simonoff, J. (2012). Smoothing methods in statistics.
Springer Science & Business Media.
Uludag, U., Pankanti, S., and Jain, A. K. (2005). Fuzzy
vault for fingerprints. Audio- and Video-Based Bio-
metric Person Authentication.
Uludag, U., Pankanti, S., Prabhakar, S., , and Jain, A. K.
(2004). Biometric cryptosystems: issues and chal-
lenges. Proceedings of the IEEE, 92(6):948–960.
Velciu, M.-A., P
˘
atrascu, A., and Patriciu, V.-V. (2015). An
evaluation of the reed-solomon error-correcting codes
usage for bio-cryptographic algorithms. 10th Jubilee
IEEE International Symposium on Applied Computa-
tional Intelligence and Informatics.
V.S.Meenakshi and Padmavathi, D. G. (2010). Retina and
iris based multimodal biometric fuzzy vault. Interna-
tional Journal of Computer Applications.
You, L. and Wang, T. (2018). A novel fuzzy vault scheme
based on fingerprint and finger vein feature fusion.
Soft Computing.
Zheng, A. and Casari, A. (2018). Feature engineering for
machine learning: Principles and techniques for data
scientists. O’Reilly Media.
Fuzzy Vault Security Enhancement Avoid Statistical Biases
51
