
K-Resilient Public Key Authenticated Encryption with Keyword Search
Koon-Ming Chan
a
, Swee-Huay Heng
b
, Syh-Yuan Tan
c
and Shing-Chiang Tan
d
Faculty of Information Science and Technology, Multimedia University,
Jalan Ayer Keroh Lama, 75450 Melaka, Malaysia
Keywords:
PEKS, PAEKS, KGA.
Abstract:
The public key encryption with keyword search (PEKS) scheme is a cryptographic primitive introduced to se-
curely store and allow specific searches within encrypted data. Traditional encryption prioritises confidential-
ity but complicates search operations, requiring decryption before searches can be conducted. PEKS scheme
addresses this limitation by enabling authorised users to search for specific keywords within encrypted data
without compromising the underlying encryption. This facilitates efficient and secure data retrieval without
the need to decrypt the entire dataset. However, PEKS is susceptible to the keyword guessing attack (KGA),
exploiting the deterministic nature of the PEKS trapdoor so the adversary can correctly guess the keyword
encrypted in a trapdoor. To enhance PEKS security to counter KGA, various schemes have been proposed.
A notable one is public key authenticated encryption with keyword search (PAEKS). PAEKS combines au-
thentication and encryption with keyword-based search functionalities, ensuring data source authentication,
encrypted information security, and keyword-based searches. This approach offers a more robust and secure
alternative to traditional PEKS. However, many existing PAEKS schemes rely on computationally exhaustive
bilinear pairing. In this paper, we propose a PAEKS scheme based on k-resilient identity-based encryption
without bilinear pairing. By using the provable security approach, we show that our proposed PAEKS scheme
satisfies keyword privacy and trapdoor privacy. Furthermore, we also present a performance evaluation of our
proposed PAEKS scheme with other related PAEKS schemes and show the efficiency of our proposed scheme.
1 INTRODUCTION
Public key encryption with keyword search (PEKS)
is a cryptographic primitive proposed by Boneh et
al. (Boneh et al., 2004) that is designed to allow se-
cure storage of encrypted data while enabling specific
searches within the encrypted content. Traditional en-
cryption methods provide confidentiality but hinder
search operations, as they necessitate decryption be-
fore conducting any searches. PEKS was proposed to
address the limitations of traditional encryption meth-
ods, where conducting searches on encrypted data
was either impractical or required decryption, leading
to potential security risks. It provides a solution to the
challenge of securely searching data without compro-
mising the underlying encryption. Its primary objec-
tive is to permit authorised users to search for spe-
cific keywords within encrypted data without reveal-
a
https://orcid.org/0000-0002-0367-4129
b
https://orcid.org/0000-0003-3627-2131
c
https://orcid.org/0000-0003-1182-1210
d
https://orcid.org/0000-0002-1267-1894
ing the encrypted content. PEKS allows users to en-
crypt data with a public key and perform searches on
the encrypted data for specific keywords by an autho-
rised party who possesses the corresponding private
key, without the need to decrypt the entire dataset.
The Keyword Guessing Attack (KGA) on the
PEKS scheme is a vulnerability that exploits the de-
terministic nature of the PEKS trapdoor. This vulner-
ability was pointed out by Byun et al. (Byun et al.,
2006), then followed by several attacks performed on
a number of PEKS schemes showing vulnerability to
KGA (Byun et al., 2006; Yau et al., 2008; Yau et al.,
2013; Lu et al., 2019). In a KGA, adversaries repet-
itively guess and encrypt potential keywords, then
by observing the resulting ciphertexts, the attackers
can analyse and compare these encrypted keywords
to glean patterns or similarities, enabling them to de-
duce potential matches between the ciphertext and
the trapdoor. This attack compromises the security
of PEKS by potentially revealing matches between
guessed keywords and the trapdoor, potentially lead-
ing to unauthorised access to sensitive information.
Several related schemes have been proposed in the
Chan, K., Heng, S., Tan, S. and Tan, S.
K-Resilient Public Key Authenticated Encryption with Keyword Search.
DOI: 10.5220/0012716100003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 381-388
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
381

literature to enhance the security of PEKS and counter
the KGA attack. One significant scheme is a pub-
lic key authenticated encryption with keyword search
(PAEKS), introduced by Huang and Li (Huang and
Li, 2017). It is designed to provide both authentica-
tion and encryption capabilities alongside keyword-
based search functionalities. PAEKS allows users
to authenticate the data source, encrypt the informa-
tion, and perform searches based on keywords, ensur-
ing both the confidentiality and integrity of the data.
The advantage of PAEKS lies in its ability to com-
bine authenticated encryption with keyword search,
providing a more robust and secure approach com-
pared to traditional PEKS. Up to now, many PAEKS
schemes have been proposed (Lu and Li, 2022; Ma
and Kazemian, 2021; Noroozi and Eslami, 2019; Qin
et al., 2020) but most of the schemes are based on bi-
linear pairing which is known for its exhaustive com-
putation.
In the effort to fill in the research gap of propos-
ing a bilinear pairing-free PEKS scheme, in this pa-
per, we mainly focus on the PAEKS scheme. We first
propose the k-resilient PAEKS scheme without bilin-
ear pairing based on the k-resilient PEKS scheme of
(Yau et al., 2013) which was developed from Heng
and Kurosawa’s k-resilient identity-based encryption
scheme (Heng and Kurosawa, 2004). We then follow
the rigorous security analysis and show that our pro-
posed PAEKS scheme satisfies keyword privacy and
trapdoor privacy which also implies that it can resist
KGA. Subsequently, we conduct a performance eval-
uation of our proposed PAEKS scheme with other re-
lated PAEKS schemes.
2 RELATED WORK
One effective method to prevent KGA is by resort-
ing to a PAEKS scheme introduced earlier. A PAEKS
scheme uses two sets of key pairs, the PAEKS scheme
ciphertext requires a sender’s private key and a re-
ceiver’s public key to generate and vice versa for
the trapdoor. It is for this reason that the PAEKS
scheme was able to prevent KGA even from mali-
cious servers. Li et al. (Li et al., 2019) proposed
a designated-server identity-based PAEKS scheme
that integrated the designated identity-based PEKS
scheme with a PAEKS scheme. Noroozi and Eslami
(Noroozi and Eslami, 2019) noted that Huang and Li’s
PAEKS scheme (Huang and Li, 2017) was insecure
against KGA in a multi-user setting and they have also
proposed an improvement to the scheme that fixed the
issue. Qin et al. (Qin et al., 2020) also noted that
Huang and Li’s PAEKS scheme (Huang and Li, 2017)
was vulnerable to multi-ciphertext attack. They pro-
posed the first scheme in order to fix the vulnerabil-
ity, followed by a second scheme that simplifies the
management of the data sender’s public key. Lu and
Li (Lu and Li, 2022) proposed a designated PAEKS
scheme without bilinear pairing. Instead of using only
the sender’s key pair and the receiver’s key pair, it
also requires an additional server’s key pair. This
limits their test algorithm to run on the designated
server only. Huang et al. (Huang et al., 2023) pro-
posed a more efficient PAEKS scheme using bilinear
pairing. They incorporated ciphertext deduplication
and inverted index to lower the storage cost and ac-
celerate the searching process. Pu et al. (Pu et al.,
2023) proposed a PAEKS scheme that was suitable
for industrial IoT devices because it has one bilinear
pairing operation in the testing algorithm. Bai et al.
(Bai et al., 2024) also proposed a designated PAEKS
scheme and their proposed scheme is more efficient
than Lu and Li’s designated PAEKS scheme (Lu and
Li, 2022).
3 PRELIMINARIES
3.1 PAEKS Scheme
A PAEKS scheme consists of the following six algo-
rithms:
• Setup (1
λ
): This algorithm takes security param-
eter 1
λ
as the input to generate the common pa-
rameters cp that are required for the scheme.
• SenderKeyGen (cp): This algorithm takes the
common parameters cp to generate a set of public
key and private key for the sender.
• ReceiverKeyGen (cp): This algorithm takes the
common parameters cp to generate a set of public
key and private key for the receiver.
• PAEKS (cp, w, sk
sender
, pk
receiver
): This algo-
rithm takes in the common parameters cp, a key-
word w, sender’s private key sk
sender
, and re-
ceiver’s public key pk
receiver
as input to generate
a searchable ciphertext of the keyword C
w
as an
output.
• Trapdoor (cp, w, pk
sender
, sk
receiver
): This algo-
rithm takes in the common parameters cp, a key-
word w, sender’s public key pk
sender
, and re-
ceiver’s private key sk
receiver
as input to generate a
trapdoor of the keyword T
w
as an output.
• Test (cp, C
w
, T
w
): This algorithm is run by the
server. It takes in a searchable ciphertext C
w
and
a trapdoor T
w
to perform the matching operation.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
382

If the searchable ciphertext matches with the trap-
door, it will output 1 else 0.
3.2 Security Models
3.2.1 Indistinguishability Under Chosen
Keyword Attack (IND-CKA)
This model is defined by the following game between
an adversary A and a challenger B:
Setup: The challenger B inputs the security parame-
ter 1
λ
to the Setup algorithm to compute the common
parameters cp. Then, it runs the SenderKeyGen and
ReceiverKeyGen algorithms to generate key pairs
(sk
sender
, pk
sender
, sk
receiver
, pk
receiver
). In the end of
this phase, B transfers (cp, pk
sender
, pk
receiver
) to the
adversary A.
Phase 1: In this phase, the adversary A can adaptively
query to the Ciphertext Oracle O
C
and Trapdoor Ora-
cle O
T
.
• Ciphertext Oracle O
C
: This oracle takes a key-
word w as an input and outputs the ciphertext C
w
by running the PAEKS algorithm. Finally, it re-
turns the ciphertext C
w
to A.
• Trapdoor Oracle O
T
: This oracle takes a keyword
w as an input and outputs the trapdoor T
w
by run-
ning the Trapdoor algorithm. Finally, it returns
the trapdoor T
w
to A.
Challenge: The adversary selects two keywords
{w
0
, w
1
} ∈ W as the challenge keywords. The only
restriction is that the challenge keywords should
not have been queried for ciphertext and trapdoor
previously. The challenger randomly chooses a bit
b ∈ {0, 1} and returns the C
w
b
to the adversary A.
Phase 2: In this phase, the adversary can still
adaptively query to the O
C
and O
T
for any keywords
except for the challenge keywords, i.e. w ̸= {w
0
, w
1
}.
Guess: The adversary outputs a guess bit b
′
∈ {0, 1}.
If b
′
= b, it wins the game.
We say that a PAEKS scheme possesses keyword
privacy, that is, it achieves indistinguishability against
a chosen keyword attack if any polynomial-time ad-
versary A has a negligible advantage ε in the IND-
CKA game, where
Adv
IND−CKA
A
= |Pr[b = b
′
] −
1
2
|≤ ε (1)
3.2.2 Indistinguishability Under Keyword
Guessing Attack (IND-KGA)
This model is defined by the following game between
an adversary A and a challenger B:
Setup: The challenger B inputs the security parame-
ter 1
λ
to the Setup algorithm to compute the common
parameters cp. Then, it runs the SenderKeyGen and
ReciverKeyGen algorithms to generate key pairs
(sk
sender
, pk
sender
, sk
receiver
, pk
receiver
). In the end of
this phase, B transfers (cp, pk
sender
, pk
receiver
) to the
adversary A.
Phase 1: In this phase, the adversary A can adaptively
query to the Ciphertext Oracle O
C
and Trapdoor Ora-
cle O
T
.
Challenge: The adversary selects two keywords
{w
0
, w
1
} ∈ W as the challenge keywords. The only
restriction is that the adversary cannot ask for the
ciphertext of the challenge keywords C
w
0
and C
w
1
.
The challenger randomly chooses a bit b ∈ {0, 1} and
returns the T
w
b
to the adversary A.
Phase 2: In this phase, the adversary can still
adaptively query to the O
C
and O
T
for any keywords
except for the challenge keywords, i.e. w ̸= {w
0
, w
1
}.
Guess: The adversary outputs a guess bit b
′
∈ {0, 1}.
If b
′
= b, it wins the game.
We say that a PAEKS scheme possesses trapdoor
privacy, that is, it achieves indistinguishability against
a keyword guessing attack if any polynomial-time ad-
versary A has a negligible advantage ε in the IND-
KGA game, where
Adv
IND−KGA
A
= |Pr[b = b
′
] −
1
2
|≤ ε (2)
4 PROPOSED KR-PAEKS
SCHEME
Heng and Kurosawa (Heng and Kurosawa, 2004)
first proposed the k-resilient identity-based encryp-
tion scheme in the standard model. It is well known
in the literature that any anonymous identity-based
encryption scheme can be transformed into a PEKS
scheme following the transformation technique pro-
posed by Abdalla et al. (Abdalla et al., 2005). Us-
ing the Heng and Kurosawa’s scheme and Abdalla et
al.’s transformation technique, Khader (Khader, 2006)
proposed the k-resilient PEKS scheme. Khader’s
K-Resilient Public Key Authenticated Encryption with Keyword Search
383

scheme (Khader, 2006) was later improved by Yau
et al. (Yau et al., 2012). They improved Khader’s
scheme (Khader, 2006) efficiency by removing and
simplifying some unnecessary and complex steps in
her overall scheme construction. However, the pro-
posed k-resilient PEKS scheme is still vulnerable to
KGA because it does not possess trapdoor privacy.
We then propose the KR-PAEKS scheme possesses
keyword privacy and trapdoor privacy based on Yau
et al.’s (Yau et al., 2012) scheme.
Our proposed KR-PAEKS scheme consists of the
following six algorithms:
KR-Setup: Choose a generator g
1
∈ G and a random
a ∈ Z
∗
q
to compute g
2
= g
a
1
. Choose a random k. Set
the common parameters cp = ⟨G, g
1
, g
2
, k⟩.
KR-SenderKeyGen: Choose two random k-degree
polynomials over Z
q
:
p
1
(x) = Σ
k
t=0
d
t
x
t
; p
2
(x) = Σ
k
t=0
d
′
t
x
t
(3)
Then, compute D
t
= g
d
t
1
g
d
′
t
2
, for 0 ≤ t ≤ k. Set the
private key sk
sender
= ⟨p
1
, p
2
⟩ and the public key
pk
sender
= ⟨g
1
, g
2
, D
0
, ..., D
k
⟩.
KR-ReceiverKeyGen: Choose two random k-degree
polynomials over Z
q
:
ˆp
1
(x) = Σ
k
t=0
ˆ
d
t
x
t
; ˆp
2
(x) = Σ
k
t=0
ˆ
d
′
t
x
t
(4)
Then, compute
ˆ
D
t
= g
ˆ
d
t
1
g
ˆ
d
′
t
2
, for 0 ≤ t ≤ k. Set the
private key sk
receiver
= ⟨ ˆp
1
, ˆp
2
⟩ and the public key
pk
receiver
= ⟨g
1
, g
2
,
ˆ
D
0
, ...,
ˆ
D
k
⟩.
KR-PAEKS: Choose a random r ∈ Z
∗
q
. For a chosen
keyword w, compute
C
1
= (Π
k
t=0
ˆ
D
w
t
t
)
p
1
(w)r
= (g
ˆp
1
(w)
1
· g
ˆp
2
(w)
2
)
p
1
(w)r
, (5)
C
2
= (Π
k
t=0
ˆ
D
w
t
t
)
p
2
(w)r
= (g
ˆp
1
(w)
1
· g
ˆp
2
(w)
2
)
p
2
(w)r
, (6)
and
u =
p
2
(w)
p
1
(w)
. (7)
Lastly, output the searchable ciphertext
C = ⟨C
1
, C
2
, u⟩.
KR-Trapdoor: Choose a random r
′
∈ Z
∗
q
. For a cho-
sen keyword w, compute
T
1
= (Π
k
t=0
D
w
t
t
)
ˆp
1
(w)r
′
= (g
p
1
(w)
1
· g
p
2
(w)
2
)
ˆp
1
(w)r
′
, (8)
T
2
= (Π
k
t=0
D
w
t
t
)
ˆp
2
(w)r
′
= (g
p
1
(w)
1
· g
p
2
(w)
2
)
ˆp
2
(w)r
′
, (9)
and
ˆu =
ˆp
2
(w)
ˆp
1
(w)
. (10)
Lastly, output the trapdoor T
w
= ⟨T
1
, T
2
, ˆu⟩.
KR-Test: Upon receiving a trapdoor T
w
, the server
will test for a matching searchable ciphertext C by
performing (C
1
)
u
· T
2
= (T
1
)
ˆu
·C
2
. It will output “1”
if the result matches, else output “0”. The correctness
of the equation is as follows:
(C
1
)
u
· T
2
= (T
1
)
ˆu
·C
2
(11)
(g
ˆp
1
(w)
1
· g
ˆp
2
(w)
2
)
p
1
(w)r
p
2
(w)
p
1
(w)
· (g
p
1
(w)
1
· g
p
2
(w)
2
)
ˆp
2
(w)r
′
=
(g
p
1
(w)
1
· g
p
2
(w)
2
)
ˆp
1
(w)r
′
ˆp
2
(w)
ˆp
1
(w)
· (g
ˆp
1
(w)
1
· g
ˆp
2
(w)
2
)
p
2
(w)r
(12)
(g
ˆp
1
(w)
1
· g
ˆp
2
(w)
2
)
p
2
(w)r
· (g
p
1
(w)
1
· g
p
2
(w)
2
)
ˆp
2
(w)r
′
=
(g
p
1
(w)
1
· g
p
2
(w)
2
)
ˆp
2
(w)r
′
· (g
ˆp
1
(w)
1
· g
ˆp
2
(w)
2
)
p
2
(w)r
(13)
5 SECURITY ANALYSIS
This section presents the security proof of IND-CKA
security and IND-KGA security of our scheme. It can
guarantee that the keyword ciphertext and the trap-
door are indistinguishable repectively.
Theorem 1. The proposed KR-PAEKS scheme
achieves ciphertext indistinguishability under chosen
keyword attack (IND-CKA) if the DDH assumption
holds.
Proof. Suppose there exists an adversary A who can
(t, ε)-break the KR-PAEKS scheme in the IND-CKA
security model, then we can construct a simulator B
to (t
′
, ε
′
)-solve the DDH problem. Given as input
a DDH instance (g, g
x
, g
y
, Z) over the cyclic group
(G, g, p), B runs A and works as follows.
Setup: B sets the common parameters cp = ⟨G, g
1
=
g, g
2
= g
x
, k⟩. Then, it runs the SenderKeyGen and
ReceiverKeyGen algorithms to generate key pairs
(sk
sender
, pk
sender
, sk
receiver
, pk
receiver
). In the end of
this phase, B transfers (cp, pk
sender
, pk
receiver
) to the
adversary A.
Phase 1: In this phase, the adversary A can adaptively
query to the Ciphertext Oracle O
C
and Trapdoor Ora-
cle O
T
of any keyword w.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
384

Challenge: The adversary selects two keywords
{w
0
, w
1
} ∈ W as the challenge keywords. The only
restriction is that the challenge keywords should not
have been queried for ciphertext and trapdoor previ-
ously. B randomly chooses a bit b ∈ {0, 1} and returns
the C
∗
w
b
to the adversary A as
C
∗
w
b
= {C
∗
1
, C
∗
2
, u} =
(g
y· ˆp
1
(w
b
)·p
1
(w
b
)
· Z
ˆp
2
(w
b
)·p
1
(w
b
)
),
(g
y· ˆp
1
(w
b
)·p
2
(w
b
)
· Z
ˆp
2
(w
b
)·p
2
(w
b
)
),
p
2
(w
b
)
p
1
(w
b
)
,
(14)
where g
y
and Z are from the problem instance. The
ciphertext correctness can be verified as follows:
C
∗
w
b
=
(g
y· ˆp
1
(w
b
)·p
1
(w
b
)
· Z
ˆp
2
(w
b
)·p
1
(w
b
)
),
(g
y· ˆp
1
(w
b
)·p
2
(w
b
)
· Z
ˆp
2
(w
b
)·p
2
(w
b
)
),
p
2
(w
b
)
p
1
(w
b
)
=
(g
r· ˆp
1
(w
b
)·p
1
(w
b
)
· g
x·r· ˆp
2
(w
b
)·p
1
(w
b
)
),
(g
r· ˆp
1
(w
b
)·p
2
(w
b
)
· g
x·r· ˆp
2
(w
b
)·p
2
(w
b
)
),
p
2
(w
b
)
p
1
(w
b
)
=
(g
ˆp
1
(w
b
)
1
· g
ˆp
2
(w
b
)
2
)
p
1
(w
b
)r
, (g
ˆp
1
(w
b
)
1
·g
ˆp
2
(w
b
)
2
)
p
2
(w
b
)r
,
p
2
(w
b
)
p
1
(w
b
)
.
(15)
where r = y if Z = g
xy
, and r ∈ Z
∗
q
is random if
Z ∈ G is random. Therefore, C
∗
w
b
is a valid challenge
ciphertext whose encrypted keyword is w
b
.
Phase 2: In this phase, the adversary A can still
adaptively query to the O
C
and O
T
for any keywords
except for the challenge keywords, i.e. w ̸= {w
0
, w
1
}.
Guess: The adversary A outputs a guess bit
b
′
∈ {0, 1}. The simulation outputs 1 if b
′
= b.
Otherwise, it outputs 0.
This completes the simulation and the solution.
The correctness is analysed as follows.
Probability of A Winning the Game.
• If Z = g
xy
, the simulation is indistinguishable
from the real attack, and thus the adversary A runs
in time t and has a probability of ε +
1
2
in guess-
ing the encrypted keyword correctly.
• If Z is random, the challenge ciphertext is a one-
time pad from the adversary’s viewpoint. There-
fore, the adversary A runs in time t and has a prob-
ability of
1
2
in guessing the encrypted keyword
correctly.
Advantage and Time Cost. When A wins the game,
the simulator B (t
′
, ε
′
)-solves the DDH problem in
time t
′
= t and
ε
′
= Pr[A wins]
= |Pr[b = b
′
] −
1
2
|
=| Pr[Z = g
xy
] − Pr[Z is random] |= ε
as required. This completes the proof of the Theo-
rem1.
Theorem 2. The proposed KR-PAEKS scheme
achieves trapdoor indistinguishability under keyword
guessing attack (IND-KGA) if the DDH assumption
holds.
Proof. Suppose there exists an adversary A who can
(t, ε)-break the KR-PAEKS scheme in the IND-KGA
security model, then we can construct a simulator
B to (t
′
, ε)-solve the DDH problem. Given as input
a DDH instance (g, g
x
, g
y
, Z) over the cyclic group
(G, g, p), B runs A and works as follows.
Setup: B runs the Setup algorithm to compute the
common parameters cp = ⟨G, g
1
= g, g
2
= g
x
, k⟩.
Then, it runs the SenderKeyGen and Re-
ceiverKeyGen algorithms to generate key pairs
(sk
sender
, pk
sender
, sk
receiver
, pk
receiver
). In the end of
this phase, B transfers (cp, pk
sender
, pk
receiver
) to the
adversary A.
Phase 1: In this phase, the adversary A can adaptively
query to the Ciphertext Oracle O
C
and Trapdoor Ora-
cle O
T
of any keyword w.
Challenge: The adversary selects two keywords
{w
0
, w
1
} ∈ W as the challenge keywords. The only
restriction is that the adversary cannot ask for the ci-
phertext of the challenge keywords C
w
0
and C
w
1
. The
challenger randomly chooses a bit b ∈ {0, 1} and re-
turns the T
∗
w
b
to the adversary A as
T
∗
w
b
= ⟨T
∗
1
, T
∗
2
, ˆu⟩ =
(g
y· ˆp
1
(w
b
)·p
1
(w
b
)
· Z
ˆp
1
(w
b
)·p
2
(w
b
)
),
(g
y· ˆp
2
(w
b
)·p
1
(w
b
)
· Z
ˆp
2
(w
b
)·p
2
(w
b
)
),
ˆp
2
(w
b
)
ˆp
1
(w
b
)
(16)
where g
y
and Z are from the problem instance. The
K-Resilient Public Key Authenticated Encryption with Keyword Search
385

trapdoor correctness can be verified as follows:
T
∗
w
b
=
(g
y· ˆp
1
(w
b
)·p
1
(w
b
)
· Z
ˆp
1
(w
b
)·p
2
(w
b
)
),
(g
y· ˆp
2
(w
b
)·p
1
(w
b
)
· Z
ˆp
2
(w
b
)·p
2
(w
b
)
),
ˆp
2
(w
b
)
ˆp
1
(w
b
)
=
(g
r
′
· ˆp
1
(w
b
)·p
1
(w
b
)
· g
x·r
′
· ˆp
1
(w
b
)·p
2
(w
b
)
),
(g
r
′
· ˆp
2
(w
b
)·p
1
(w
b
)
· g
x·r
′
· ˆp
2
(w
b
)·p
2
(w
b
)
),
ˆp
2
(w
b
)
ˆp
1
(w
b
)
=
(g
p
1
(w
b
)
1
· g
p
2
(w
b
)
2
)
ˆp
1
(w
b
)r
′
, (g
p
1
(w
b
)
1
·g
p
2
(w
b
)
2
)
ˆp
2
(w
b
)r
′
,
ˆp
2
(w
b
)
ˆp
1
(w
b
)
(17)
where r
′
= y if Z = g
xy
, and r ∈ Z
∗
q
is random if
Z ∈ G is random. Therefore, T
∗
w
b
is a valid challenge
trapdoor for the keyword w
b
.
Phase 2: In this phase, the adversary can still
adaptively query to the O
C
and O
T
for any keywords
except for the challenge keywords, i.e. w ̸= {w
0
, w
1
}.
Guess: The adversary output a guess bit b
′
∈ {0, 1}.
The simulation outputs 1 if b
′
= b. Otherwise, it
outputs 0.
This completes the simulation and the solution.
The correctness is analysed as follows.
Probability of A Winning the Game.
• If Z = g
xy
, the simulation is indistinguishable
from the real attack, and thus the adversary A has
a probability of ε +
1
2
in guessing the trapdoor
correctly.
• If Z is random, the challenge ciphertext is a one-
time pad from the adversary’s viewpoint. There-
fore, the adversary A has a probability of
1
2
in
guessing the trapdoor correctly.
Advantage and Time Cost. When A wins the game,
the simulator B (t
′
, ε
′
)-solves the DDH problem in
time t
′
= t and
ε
′
= Pr[A wins]
= |Pr[b = b
′
] −
1
2
|
=| Pr[Z = g
xy
] − Pr[Z is random] |= ε
as required. This completes the proof of the Theorem
2.
Table 1: Notation Used.
Notation Description
M Scalar multiplication operation in G
M
t
Scalar multiplication operation in G
T
m Modular multiplication operation in
Z
q
A Point addition operation in G
a Point addition operation in Z
q
exp Exponentiation operation in Z
q
H Hash operation
P Bilinear pairing operation
inv Modular inverse operation in Z
q
6 PERFORMANCE EVALUATION
We compare our scheme with some related schemes
in terms of computing efficiency. Table 1 defines the
list of notation used in the performance evaluation.
Table 2 shows the comparison analysis of our scheme
with some related schemes in terms of the compu-
tational cost. In Table 2, we only consider the cost
of Encryption algorithm, Trapdoor algorithm and the
Test algorithm. We do not consider Setup algorithm
and Key Generation algorithms in the comparison as
they are executed once only.
To the best of our knowledge, our PAEKS scheme
is the first construction without bilinear pairing. To
perform a conservative comparison, although our
scheme can be initialised with more efficient non-
pairing curves such as ED25519 (which uses 256-bit
modulus), we assume a pairing curve such as BLS-12
(which uses 392-bit modulus) is used. Subsequently,
for clarity purposes, we standardise the complexity
unit as the relative computation costs in equivalents
of scalar multiplication in G
1
under BLS-12 curve at
128-bit security (Tan and Groß, 2020). In precise, an
exponentiation (M
t
) in G
T
is about the same as com-
puting 6 scalar multiplication (M) in G
1
, and a pair-
ing (P) is approximately 9M. Table 3 shows the result
after applying the conversion. The hashing and the
operations in Z
q
are typically not as significant com-
pared to that in G but we keep it for completeness
purposes.
From Table 3, it is evident that Pu et al.’s scheme
(Pu et al., 2023) still has the advantage in the com-
putation cost for the Encryption algorithm and the
Trapdoor algorithm. However, a notable strength of
our proposed scheme is in the Test algorithm, our
scheme only requires 4M as compared to Pu et al.’s
9M. Nevertheless, it is imperative to acknowledge
that Pu et al.’s scheme holds a natural efficiency ad-
vantage over our proposed scheme due to their their
SECRYPT 2024 - 21st International Conference on Security and Cryptography
386
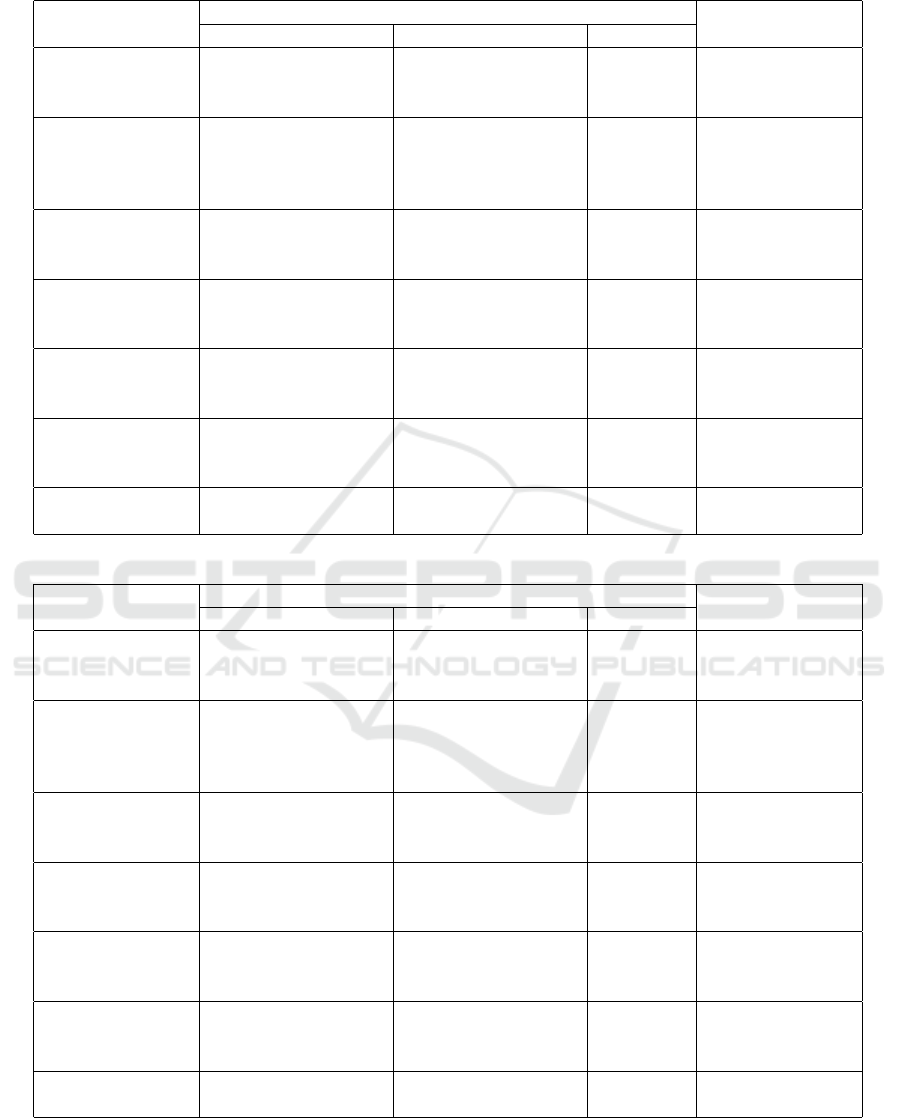
Table 2: Comparison Analysis of Computation Cost.
Scheme
Computation Cost
Security Model
Encryption Trapdoor Test
Huang and Li
(2017) (Huang
and Li, 2017)
3M + H M + H + P 2P Random Oracle
Noroozi and
Eslami (2019)
(Noroozi and
Eslami, 2019)
3M + H M + H + P 2P Random Oracle
Qin et al. (2020)
1(Qin et al.,
2020)
3M + 2H + P 2M +H H + P Random Oracle
Qin et al. (2020)
2(Qin et al.,
2020)
2M + 2H + 2P M + H + P H + P Random Oracle
Huang et al.
(2023)(Huang
et al., 2023)
3M + H 3M + H 2P Random Oracle
Pu et al.
(2023)(Pu et al.,
2023)
3M + M
t
M P Random Oracle
Proposed 2((k + 1)M) + 2(k +
1)exp + m + inv
2((k + 1)M) + 2(k +
1)exp + m + inv
4M Standard
Table 3: Comparison Analysis in the Standardised Complexity Unit.
Scheme
Computation Cost
Security Model
Encryption Trapdoor Test
Huang and Li
(2017) (Huang
and Li, 2017)
3M + H 10M + H 18M Random Oracle
Noroozi and
Eslami (2019)
(Noroozi and
Eslami, 2019)
3M + H 10M + H 18M Random Oracle
Qin et al. (2020)
1(Qin et al.,
2020)
12M + 2H 2M + H 9M + H Random Oracle
Qin et al. (2020)
2(Qin et al.,
2020)
20M + 2H 10M + H 9M + H Random Oracle
Huang et al.
(2023)(Huang
et al., 2023)
3M + H 3M + H 18M Random Oracle
Pu et al.
(2023)(Pu et al.,
2023)
9M M 9M Random Oracle
Proposed 2((k + 1)M) + 2(k +
1)exp + m + inv
2((k + 1)M) + 2(k +
1)exp + m + inv
4M Standard
K-Resilient Public Key Authenticated Encryption with Keyword Search
387

scheme is provably secure in the random oracle model
whereas our proposed scheme is provably secure in
the standard model. Note that, we can further reduce
the computation cost of our scheme by applying the
multiple exponentiation algorithm (Menezes et al.,
1996) for the Encryption algorithm and Trapdoor al-
gorithm which can be reduced to 1.5((k + 1)M) +
1.5(k+1)exp +m +inv for both Encryption algorithm
and Trapdoor algorithm.
ACKNOWLEDGEMENT
This work was supported by the Telekom Malaysia
Research & Development Grant (RDTC/221045).
REFERENCES
Abdalla, M., Bellare, M., Catalano, D., Kiltz, E., Kohno,
T., Lange, T., Malone-Lee, J., Neven, G., Paillier, P.,
and Shi, H. (2005). Searchable encryption revisited:
Consistency properties, relation to anonymous ibe,
and extensions. In Advances in Cryptology–CRYPTO
2005: 25th Annual International Cryptology Confer-
ence, Santa Barbara, California, USA, August 14-18,
2005. Proceedings 25, pages 205–222. Springer.
Bai, L., Yong, L., Chen, Z., and Shao, J. (2024). Pairing-
free public-key authenticated encryption with key-
word search. Computer Standards & Interfaces,
88:103793.
Boneh, D., Di Crescenzo, G., Ostrovsky, R., and Per-
siano, G. (2004). Public key encryption with keyword
search. In Advances in Cryptology-EUROCRYPT
2004: International Conference on the Theory and
Applications of Cryptographic Techniques, Inter-
laken, Switzerland, May 2-6, 2004. Proceedings 23,
pages 506–522. Springer.
Byun, J. W., Rhee, H. S., Park, H.-A., and Lee, D. H.
(2006). Off-line keyword guessing attacks on re-
cent keyword search schemes over encrypted data. In
Workshop on secure data management, pages 75–83.
Springer.
Heng, S.-H. and Kurosawa, K. (2004). k-resilient identity-
based encryption in the standard model. In Topics
in Cryptology–CT-RSA 2004: The Cryptographers’
Track at the RSA Conference 2004, San Francisco,
CA, USA, February 23-27, 2004, Proceedings, pages
67–80. Springer.
Huang, Q., Huang, P., Li, H., Huang, J., and Lin, H. (2023).
A more efficient public-key authenticated encryption
scheme with keyword search. Journal of Systems Ar-
chitecture, 137:102839.
Huang, Q. and Li, H. (2017). An efficient public-key
searchable encryption scheme secure against inside
keyword guessing attacks. Information Sciences,
403:1–14.
Khader, D. (2006). Public key encryption with keyword
search based on k-resilient ibe. In International Con-
ference on Computational Science and Its Applica-
tions, pages 298–308. Springer.
Li, H., Huang, Q., Shen, J., Yang, G., and Susilo, W.
(2019). Designated-server identity-based authenti-
cated encryption with keyword search for encrypted
emails. Information Sciences, 481:330–343.
Lu, Y. and Li, J. (2022). Lightweight public key au-
thenticated encryption with keyword search against
adaptively-chosen-targets adversaries for mobile de-
vices. IEEE Transactions on Mobile Computing,
21(12):4397–4409.
Lu, Y., Wang, G., and Li, J. (2019). Keyword guessing at-
tacks on a public key encryption with keyword search
scheme without random oracle and its improvement.
Information Sciences, 479:270–276.
Ma, Y. and Kazemian, H. (2021). Public key authenticated
encryption with multiple keywords search using mam-
dani system. Evolving Systems, 12(3):687–699.
Menezes, A. J., Van Oorschot, P. C., and Vanstone, S. A.
(1996). Handbook of applied cryptography. CRC,
Boca Raton, 17.
Noroozi, M. and Eslami, Z. (2019). Public key authenti-
cated encryption with keyword search: revisited. IET
Information Security, 13(4):336–342.
Pu, L., Lin, C., Chen, B., and He, D. (2023). User-friendly
public-key authenticated encryption with keyword
search for industrial internet of things. IEEE Internet
of Things Journal.
Qin, B., Chen, Y., Huang, Q., Liu, X., and Zheng, D.
(2020). Public-key authenticated encryption with key-
word search revisited: Security model and construc-
tions. Information Sciences, 516:515–528.
Tan, S.-Y. and Groß, T. (2020). Monipoly—an expressive q-
sdh-based anonymous attribute-based credential sys-
tem. In International Conference on the Theory and
Application of Cryptology and Information Security,
pages 498–526. Springer.
Yau, W.-C., Heng, S.-H., and Goi, B.-M. (2008). Off-line
keyword guessing attacks on recent public key en-
cryption with keyword search schemes. In Autonomic
and Trusted Computing: 5th International Confer-
ence, ATC 2008, Oslo, Norway, June 23-25, 2008 Pro-
ceedings 5, pages 100–105. Springer.
Yau, W.-C., Heng, S.-H., Tan, S.-Y., Goi, B.-M., and Phan,
R. C.-W. (2012). Efficient encryption with keyword
search in mobile networks. Security and Communica-
tion Networks, 5(12):1412–1422.
Yau, W.-C., Phan, R. C.-W., Heng, S.-H., and Goi, B.-M.
(2013). Keyword guessing attacks on secure search-
able public key encryption schemes with a designated
tester. International Journal of Computer Mathemat-
ics, 90(12):2581–2587.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
388
