
On the Implementation of a Lattice-Based DAA for Vanet System
Doryan Lesaignoux and Mikael Carmona
Univ. Grenoble Alpes, CEA, Leti, MINATEC Campus, F-38054 Grenoble, France
Keywords: Signature Scheme, Lattice-Based Cryptography, Direct Anonymous Attestation, Zero-Knowledge Proof,
Software Implementation, Performances.
Abstract: Direct Anonymous Attestation (DAA) is a cryptographic protocol that enables users with a Trusted Platform
Module (TPM) to authenticate without revealing their identity. DAA has been adapted to Vehicle Ad-hoc
NETwork system (VANETs) to offer secure vehicle-to-anything communication (V2X). In this paper, we
provide an implementation of the most advanced post-quantum DAA for VANETs with a complete
parametrization and benchmark in order to embed this scheme on TPM.
1 INTRODUCTION
Direct Anonymous Attestation (DAA) is an
anonymous digital signature scheme made up of three
entities: The issuer, a set of signers and a set the
verifiers (Brickell and al., 2004). Issuer oversees
credentials distribution for each signer. A signer is a
pair of TPM and host. She proves her membership
and her trustworthy to the group with a DAA
signature including a zero-knowledge proof.
In 2004, the first RSA-based DAA (Brickell
and al., 2004) is standardized by the Trusted
Computing Group (TCG) for TPM 1.2 (Trusted
Computing Group, 2004). In 2008, Brickel, Chen and
Li published the first DAA based on Elliptic Curve
Cryptography in (Brickel and al., 2008). After several
enhancements (Chen, 2010), a series of ECC-based
DAA protocols is specified in ISO/IEC 20008-2 to be
integrated in the new generation of TPM 2.0 (Trusted
Computing Group, 2014).
From today, few Lattice-based DAA (LDAA)
have been developed. The pioneering scheme is
proposed in (El Bansarkhani and al., 2017). However,
it still requires huge storage and computing capacity.
The new framework of LDAA introduced in (Chen
and al., 2019) improves signature size by two orders
of magnitude regarding previous post-quantum DAA.
Vehicular Ad-hoc Network (VANET) is a network
enabling communication between vehicles and anything
(V2X) in order to enhance road safety and traffic
efficiency. Based on the same framework as (Chen and
al., 2019), the first post-quantum DAA applied to
VANETs is described by (Chen and al., 2021).
Due to the recent nature of LDAA, it exits only
one work (Chen and al., 2021) providing deep insight
on implementation concerns and performance. In
particular, the generation of parameters to achieve a
given security level is not straightforward. The
purpose of this paper is to provide a software
implementation of the most advanced post-quantum
DAA scheme for VANETs named V-LDAA (Chen
and al., 2021). The implementation comes with a
structured and comprehensive overview of the
scheme as well as a methodology for input parameters
generation. Also, we provide an analysis of the
performance and bottlenecks of our implementation
and a benchmark with pre-quantum DAA.
The paper is composed of two main sections.
Section 2 introduces the studied V-LDAA and
describes the methodology used to derive a set of
parameters for a given security level. Section 3
describes our software implementation of the V-
LDAA. The performance analysis allows the
bottleneck identification and a comparison with the
existing implementation from (Chen and al., 2021)
and the pre-quantum DAA.
2 STUDY OF V-LDAA SCHEME
2.1 Notations
In this paper, we define the polynomial ring ℛ =
ℤ
[
𝑋
]
/
〈
𝑋
+1
〉
and quotient ring ℛ
= ℛ/𝑞ℛ with
𝑞 a prime integer and 𝑑 an integer power of 2. For
642
Lesaignoux, D. and Carmona, M.
On the Implementation of a Lattice-Based DAA for Vanet System.
DOI: 10.5220/0012717900003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cr yptography (SECRYPT 2024), pages 642-648
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

clarity, we denote element of ℛ in lowercase letter,
vector over ℛ in bold lowercase letter and matrix
over ℛ in capital bold letter. We consider the scalar
product of two elements of ℛ as
〈
𝑎|𝑏
〉
=∑𝑎
𝑏
where 𝑎
and 𝑏
are the coefficients of polynomials 𝑎
and 𝑏. We denote the Euclidean norm over ℛ as
‖
𝑎
‖
=
‖
𝑎
‖
=
〈
𝑎|𝑎
〉
. We further define the
notation for vectors
‖
𝒂
‖
=
∑‖
𝑎
‖
and matrices
‖
𝑨
‖
=
∑‖
𝒂
𝒊
‖
.
We denote by 𝐷
Λ,𝜎,𝒄
the discrete gaussian
distribution over a lattice Λ with standard deviation
𝜎>0 and center 𝒄∈ℝ
. If 𝒄=0
, we omit it.
2.2 V-LDAA: General Framework
V-LDAA is a digital signature scheme secure under
Random Oracle Model where each user composed of
a host and a TPM can prove their trustworthiness to a
party of the network i.e. a verifier. V-LDAA is
composed of five main primitives:
• 𝐒𝐞𝐭𝐮𝐩 to initialize parameters of TPM, host
and issuer.
• 𝐉𝐨𝐢𝐧 to enable a user to join the network and
get credentials from the issuer.
• 𝐂𝐫𝐞𝐚𝐭𝐞 to build pseudonym and two
signatures for revocation process and
credentials verification.
• 𝐒𝐢𝐠𝐧/𝐕𝐞𝐫𝐢𝐟𝐲 for signing and verifying a
signature of a plain text.
• 𝐑𝐞𝐯𝐨𝐤 to revoke a user.
In the Join process, the creation of credentials is
based on the same concept as the ABB lattice-based
signature scheme (Agrawal and al., 2010) with a
slight modification. Following a Zero-Knowledge
Proof (ZKP) proving that a user has a valid
endorsement key, the issuer generates a pair
(
𝑖,𝒔
)
,
named credentials, satisfying the relation:
[
𝑨
│𝑩 + 𝑖𝒈]
𝑨
∙𝒔=𝑢+𝒖
𝑻
∙𝒆
𝑻
+𝒖
𝑯
∙𝒆
𝑯
(1)
where 𝑨
, 𝑩, 𝑢 are the issuer public key, 𝒈 is the
gadget matrix and the two pairs (𝒖
𝑻
,𝒆
𝑻
), (𝒖
𝑯
,𝒆
𝑯
)
are the public and private key of the TPM and the
host. 𝑖 is the long-term ID attributed to the new
member and 𝒔 is a secret bounded-norm vector of
polynomials proving membership. It’s important to
notice that the matrix 𝑨 is unique for each member
due to the long-term ID 𝑖. Thus, it is essential that this
matrix is known only to the issuer and the user
concerned, otherwise one could break the anonymity
of anyone by recovering 𝑖. Before signing
anonymously a message, a member need first, to
build a pseudonym by creating a Ring-LWE instance
with the TPM’s secret key and a basename. Two
signatures will be linkable if a user decides to use the
same basename for each of them. Second, they must
generate a ZKP (named attestation signature) of their
credentials to prove their legitimacy to the verifiers
with the underlying primitive 𝐁𝐥𝐢𝐧𝐝𝐬𝐢𝐠𝐧 . This
procedure is described in Create primitive. During
Sign operation, the signer sends the signature of the
message as well as the signature of the credentials.
Finally, the verifier checks each signature.
For further details, we refer the reader to the
references papers (Chen and al., 2019) and (Chen and
al., 2021).
2.3 Basics and Concepts on Lattices for
LDAA
In this section, we describe fundamental lattice-based
notions used in V-LDAA scheme.
A lattice Λ of ℝ
is a discrete additive subgroup
of ℝ
. Any lattice Λ of ℝ
is spanned on ℤ by a set of
𝑚 vectors 𝒂
𝟎
,… ,𝒂
𝒎𝟏
of ℝ
where 0<𝑛≤𝑚.
This set is a (non-unique) base for Λ. Let 𝑨∈ℤ
×
,
by definition, 𝛬
(
𝑨
)
is the lattice of ℝ
spanned by
the columns of 𝑨. Given a lattice 𝛬 with basis 𝑩 and
𝑩
the Gram-Schmidt orthogonalization of 𝑩, we
define a bound of the smoothing parameter 𝜂
of
Λ as 𝜂
(
Λ
)
< 𝑩
ln(2𝑛(1 + 1/𝜖)/𝜋) for any 𝜖>
0 (Theorem 3.1, Gentry and al., 2008).
For lattice-based cryptography applications, we
introduce two 𝑞 -ary lattices Λ
(
𝑨
)
:=
𝒙∈
ℤ
|
𝑨𝒙 = 𝟎
𝒏
𝑚𝑜𝑑 𝑞}, the set of all vectors of ℤ
orthogonal to 𝑨 and Λ
(
𝑨
)
:=
𝒗∈ℤ
|
𝑨𝒗 =
𝑢 𝑚𝑜𝑑 𝑞}, the set of all pre-images 𝒗 of 𝒖 by 𝑨. Two
problems follow from these lattices:
• Short Integer Solution problem (SIS): Given a
real 𝛽>0, find a vector 𝒙 in Λ
(
𝑨
)
such that
0 <
‖
𝒙
‖
≤𝛽.
• Learning With Error problem (LWE): Let 𝒔∈
ℤ
be a random secret vector and a gaussian
error vector 𝒆 ← 𝒟
ℤ
,
, if 𝜇𝑞 > 2
√
𝑛 , find 𝒔
from the pair (𝑨,𝑨𝒔 + 𝒆).
These two cryptographic problems are adaptable
to the polynomial case in ℛ with Ring-SIS
(Lyubashevsky and al., 2006) and Ring-LWE
(Lyubashevsky and al., 2010). They guarantee the
security of V-LDAA.
Let 𝛿 be an integer > 0, 𝒈=
(
1 𝛿 … 𝛿
)
be
the gadget matrix in ℤ
for polynomials and 𝑖 be an
invertible polynomial in 𝒮
= 𝑎
+
On the Implementation of a Lattice-Based DAA for Vanet System
643
𝑎
𝑋
/
| 𝑎
,𝑎
∈ℤ
. Notice that 𝑘=log
(
𝑞
)
. The
construction of a trapdoor is based on a matrix 𝑨 =
[
𝑨
|𝑖𝒈 − 𝑨
𝑹
]
∈ℛ
×
with 𝑨
a random uniform
matrix in ℛ
×
. The matrix 𝑹∈ ℛ
()×
is
called a 𝒈-trapdoor for 𝑨 under the tag 𝑖 and with
𝑨
𝑹
𝑰
=𝑖𝒈 (Micciancio and Peikert, 2012). Applied
to V-LDAA, we recover the same structure described
in equation
(
1
)
where 𝑹 is the issuer secret key and
𝑩= −𝑨
𝑹 . We denote this procedure by the
primitive
(
𝑨, 𝑹
)
= 𝐓𝐫𝐚𝐩𝐆𝐞𝐧(𝑛,𝑚,𝑘,𝑞,𝛽). In the
next section, we give concrete parameters of this
construction for V-LDAA.
To generate credentials for each user in the Join
process, issuer needs to generate a 𝑚-dimensional
discrete gaussian pre-image 𝒔 satisfying (1) from
𝐷
ℛ
m
,𝜎,𝒄
. This can be done using primitive
SampleGaussian(𝑨,𝑹, 𝑖,𝑢,𝛾,𝛼). In this work, we
use sampling method from (Micciancio and Peikert,
2012).
Another important notion used in DAA protocols
is zero-knowledge proof (ZKP) since they are used in
Join, Create, Sign and Revok. In lattice-based
cryptography, a ZKP is to prove the knowledge of a
low-norm secret vector 𝒔 in Λ
(
𝑨
)
without revealing
any other information. The more efficient method is
to use “Fiat-Shamir with Abort” ZKP technique from
(Lyubashevsky, 2012). It relies on proving the
knowledge of a slighty larger-norm vector 𝒔
such that
𝑨𝒔
=𝑐𝑢 where 𝑐 is a sparse polynomial challenge of
𝒞=𝑐∈𝑅
‖
𝑐
‖
=1 ∧
‖
𝑐
‖
=𝜅,2
≥
2
} . The secret key is “hidden” by creating a Ring-
LWE instance. Then, the protocol uses a rejection
sampling subroutine of standard deviation 𝜉 to assert
outputs are Gaussian distributed and independent of
the secret key and the challenge. Finally, the verifier
sets a bound of acceptance 𝛽
proportional to 𝜉 to
check the proof. We call this primitive
𝐙𝐊𝐏(𝑨, 𝒔, 𝑢,𝜉, 𝛽
).
In Create, users generate a signature with the
algorithm 𝐁𝐥𝐢𝐧𝐝𝐒𝐢𝐠𝐧 to enable verifiers to check the
authenticity of their credentials. Formally, the
protocol is a non-interactive ZKP from (Del Pino and
al., 2018) proving that the user knows a pair (𝒔, 𝑖)
satisfying (1). However, this cannot be performed
directly because verifiers need to know the value of
𝑨
│𝑩 + 𝑖𝒈 which would compromise the long-term
ID 𝑖. Therefore, the proof is applied on a commitment
value of each term of 𝑖𝒈. For simplification, we
consider 𝒈 =
(
1 𝛿
)
, the same gadget matrix as in V-
LDAA. We use the method described in (Baum and
al., 2018). The main idea is to sample two random
uniforms matrix 𝑨
𝟏
=
[
𝑰
𝒏
𝑨
𝟏
]
with
𝑨
𝟏
$
← ℛ
×()
, 𝑨
𝟐
=
[
𝟎
𝒏
1𝑨
𝟐
]
with
𝑨
𝟐
$
←ℛ
×()
and a short random vector 𝒓 in ℛ
s.t : 𝐶𝑜𝑚
(
𝑥,𝒓
)
=
[
𝑨
𝟏
𝑨
𝟐
]
𝒓+
[
0𝑥
]
=
[
𝑡
𝑡
]
=𝑡 where 𝑥 is a value to commit. Given
two commitments 𝑡= 𝐶𝑜𝑚
(
𝑖,𝒓
)
and 𝑡
=
𝐶𝑜𝑚
(
𝑖𝛿,𝒓′
)
, observe that:
𝒗
𝑻
𝒔
=𝑢
(2)
where : 𝒗
𝑻
=
[
𝑨
𝑻
|
𝑩
𝑻
+
[
𝒕
𝟐
𝒕
𝟐
]
|
−
[
𝒖
𝑻
𝒖
𝒉
]
|−
[𝒂
𝑻
𝒂
𝑯
]
]
and 𝒔
=
[
𝒔
𝟏
𝒔
𝟐
[𝒆
𝑻
𝒆
𝑯
] −
[
𝒓 𝒓
]
𝒔
𝟐
]
.
With this commitment scheme, the protocol
𝐁𝐥𝐢𝐧𝐝𝐒𝐢𝐠𝐧 creates 3 proofs of knowledge:
• Π
∶ commit values open to each committed
values 𝑥: using “Fiat-Shamir with Abort”
technique explained above, one can prove
the knowledge of a slightly larger-norm
polynomial vector 𝒓
s.t: 𝑐𝑡 =
[
𝑨
𝟏
𝑨
𝟐
]
𝒓
+ 𝑐
[
0𝑥
]
.
• Π
∶ commit values open to long-term ID 𝑖
such that 𝜎
(
𝑖
)
=𝑖 where 𝜎
:𝑋→𝑋
. The
protocol uses automorphism stability to
prove that 𝑖∈𝑆
(Corollary 4.2 from (Del
Pino and al., 2018)).
• Π
∶ user knows 𝑠
satisfying (2).
2.4 Parametrization of the V-LDAA
We now introduce the set of parameters of the V-
LDAA and we provide a practical expression for each
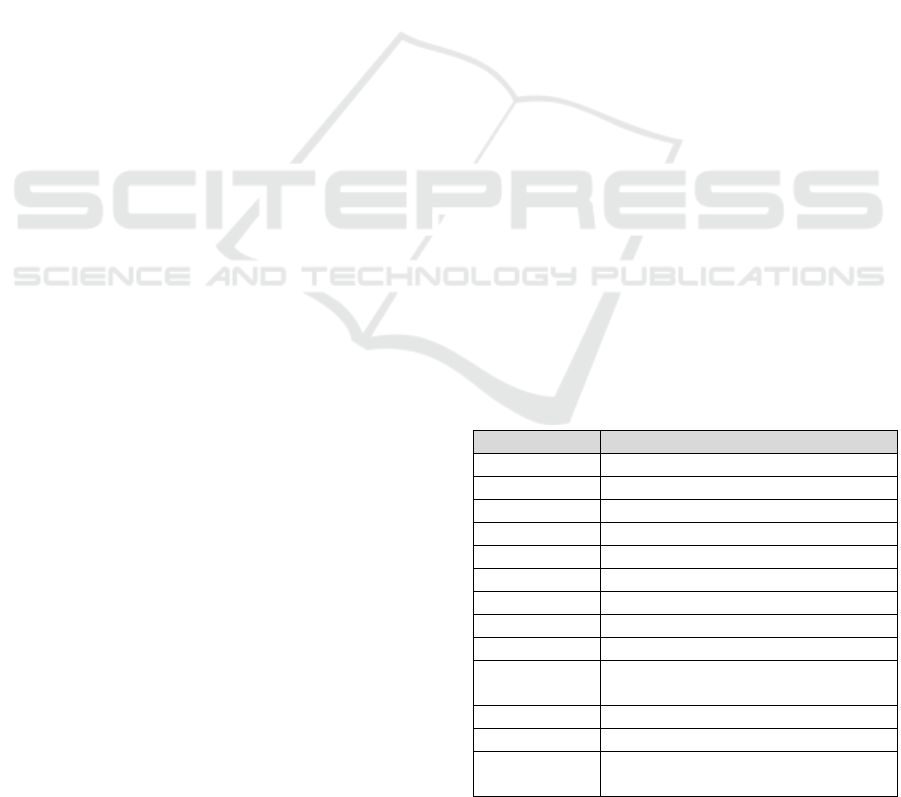
of them. Table 1 below summarizes all parameters
discussed in previous section.
Table 1: Summary of all parameters used in V-LDAA.
Parameter Description
𝝀 Level of security
𝑛 Lattice rank
𝑚 Lattice dimension
𝑑 Dimension of ℛ
𝑞 Arithmetic modulus
𝛿 Basis for gadget matrix
𝑘 Size of 𝑞 with basis 𝛿
𝜅 Cardinal of 𝒞
𝜎 Standard deviation for sampling of 𝑹
𝜉 Standard deviation for rejection
sampling
𝛽
Bound of acceptance
𝛼 Standard deviation for 𝑺𝒂𝒎𝒑𝒍𝒆𝑮
𝛾 Upper bound on the spectral norm of
α𝑹
SECRYPT 2024 - 21st International Conference on Security and Cryptography
644

V-LDAA scheme sets 𝑛 = 1, 𝑚 = 4, 𝑘 = 2 and
𝛿=
𝑞
. That is, the gadget matrix 𝒈 is a 2-
dimension vector equal to (1
𝑞
). The dimension of
the ring 𝑑 is a power of two and the arithmetic
modulus is 𝑞≡3 𝑚𝑜𝑑 4.
About standard deviation 𝜎, we use Theorem 4.1
from (Lyubashevsky and al., 2010) which state that,
for Ring-LWE instance, 𝜎 must be higher or equal to
2𝜔(
log
(
𝑑
)
). In V-LDAA, 𝜎 is not used to sample
the trapdoor 𝑹 since coefficient of 𝑹 are uniformly
chosen in
−1,0,1
}
but parameters of gaussian pre-
image sampling depend on this 𝜎.
According to Lemma 2.2 of (Del Pino and al.,
2018), we set the standard deviation of rejection
sampling to 𝜉 = 12𝜅
‖
𝑠
‖
where 𝒔 is a bounded secret
polynomial vector, and the bound of acceptance 𝛽
=
𝜉
√
2𝑑𝑚
to ensure that no information is leaked during
the ZKP. Parameter 𝜅 is chosen according to the
number of elements required to built 𝒞. In our
implementation 𝜅 is such that
|
𝒞
|
>2
to ensure that
our hash function has, at least, 2
elements.
Regarding Gaussian pre-image sampling, we
define standard deviation 𝛼 for 𝐒𝐚𝐦𝐩𝐥𝐞𝐆 and upper
bound 𝛾 on the spectral norm of α𝑹 as in (Bert and
al., 2021) i.e. 𝛼≥
√
2𝛿
(2𝛿 + 1)
𝜂
(ℤ
) and 𝛾
>
(
𝛼
+1
)
𝑠
(
𝑹
)
+𝜂
(
ℤ
)
where 𝑠
(
𝑹
)
<
1.1𝜎(
√
2𝑑
+
√
𝑑𝑘 +4.7).
The level of security 𝜆 is related to parameters
𝑛,𝜇 = 𝜎/𝑞 and 𝑞. 𝜆 is the computational complexity
to solve LWE problem parametrized by 𝑛,𝜇 and 𝑞.
This writes 𝜆= 𝐋𝐖𝐄_𝐄𝐬𝐭(𝑛,𝛼,𝛼𝑞) where
𝐋𝐖𝐄_𝐄𝐬𝐭 is the best-known algorithm for solving
LWE. 𝑛,𝛼 and 𝑞 must be to choose to achieve a level
of security greater or equal to 𝜆. We evaluated the
security of our instances using LWE-estimator
(Albrecht and al., 2015, and dedicated website). We
ran the function 𝐞𝐬𝐭𝐢𝐦𝐚𝐭𝐞_𝐥𝐰𝐞 with the following
options:
• Secret distribution = (-1,1)
• Reduction cost model = BKZ.sieve
• Number of LWE-samples: 𝑚 = 2𝑑
Below, we give two practical parameters sets (i.e.,
respecting conditions listed above) for two security
levels 𝜆 :
VLDAA-128:
𝜆 ≈ 138, 𝑑 = 512, 𝑞 = 7583, 𝛿 = 88, 𝜅 = 120
𝜎=6.0
𝛼 = 12575.899863196026
𝛾 = 5702164.533998151
VLDAA-256:
𝜆 ≈ 261, 𝑑 = 1024, 𝑞 = 14867, 𝛿 = 122, 𝜅 = 300
𝜎 = 6.324555320336759
𝛼= 28874.112529324666
𝛾 = 19125481.447302323
3 IMPLEMENTATION
3.1 Presentation of the Implementation
In this section, we provide a finer analysis of the
performance of our software implementation of the
V-LDAA and highlight implementation issues. We
also compare the results with a pre-quantum ECC-
based DAA. Similarly to the original paper, we
implemented the scheme using Sagemath.
Additionally, we use the library Hashlib for hash
primitive (Hashlib, 2001).
Our implementation has 128 bits of precision by
default for basic operations such that scalar product
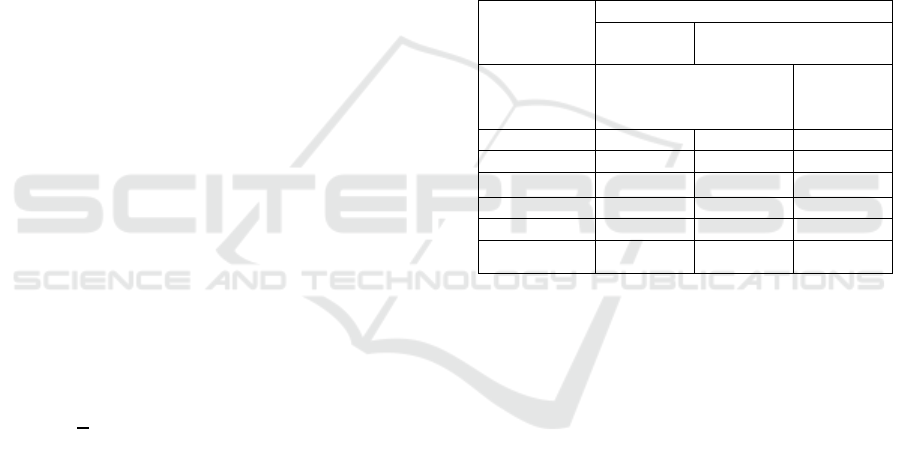
or Euclidean norm computation. Table 2 summarizes
the main primitives used for the implementation.
Table 2: Summary of all main primitives.
Primitive Implementation
Underl
y
in
g
schemes
Zero-knowled
g
e
p
roof L
y
ubashevsk
y
, 2012
Commitment Baum and al., 2018
BlindSign/Verify Del Pino and al., 2018
Lattice-Cryptography
Tra
p
Gen Micciancio and Peikert, 2012
Sam
p
leZ Sa
g
emath
Sam
p
leGaussian Guenise and Micciancio, 2019
SampleG Guenise and Micciancio, 2019
SamplePerturbZ Guenise and Micciancio, 2019
Rejection Sampling Lyubashevsky, 2012
SampleInBall Crystals-dilithium, Ducas and
al.,2018
General-Cryptography
Seed
g
eneration TRNG
Random Oracle SHAKE-128
3.1.1 SampleGaussian
Our Gaussian sampler is based on the MP framework
from (Micciancio and Peikert, 2012) instead of Klein
sampler (Klein, 2000 and Gentry and al., 2008). The
first one is known to be parallelizable and generally
faster than Klein but outputs longer vectors. We
considered that MP sampler could be more adapted
for VANET-based applications. Additionally, it
avoids possible precision problems that could be
encountered when sampling with Klein sampler,
On the Implementation of a Lattice-Based DAA for Vanet System
645
especially with the Gram-Schmidt orthogonalization
primitive (Carmona and al., 2023) and (Giraud and
al., 2005). Our implementation of MP sampler is
based on the work done in (Genise and Micciancio,
2018) which propose an algorithm adapted to ring
lattice i.e. which takes advantage of the algebraic
structure. ring structure. It also calls the primitive
𝐒𝐚𝐦𝐩𝐥𝐞𝐙(𝝈,𝒄) which outputs an integer from 𝓓
ℤ,,
and is implemented by Sagemath.
3.1.2 Zero-Knowledge Proof
For the zero-knowledge proof in 𝐉𝐨𝐢𝐧 procedure, we
implemented the “Fiat-Shamir with Abort” ZKP
scheme from (Lyubashevsky, 2012). We admit that
one could use the scheme described in (Ling and al.,
2013) proving the exact knowledge of a secret since,
even if it is not very efficient, the proof is done one
time. We justify this choice by the fact that the
general framework of (Lyubashevsky, 2012) is also
used on the others digital signature of the V-LDAA :
𝐁𝐥𝐢𝐧𝐝𝐒𝐢𝐠𝐧 and 𝐒𝐢𝐠𝐧 as well as the lattice-based
digital signature Crystals-Dilithium which has been
recently selected by the NIST (Ducas et al., 2018 and
NIST, 2024) to be standardized. To generate a
polynomial challenge, we implemented the algorithm
𝐒𝐚𝐦𝐩𝐥𝐞𝐈𝐧𝐁𝐚𝐥𝐥 used in Crystals-Dilithium.
3.1.3 Commitment
For the commitment, we use the same method used
by the authors of the V-LDAA i.e. the technique from
in (Baum and al., 2018) introduced in the previous
section. We emphasize on a particularity met on the
implementation of the commitment applied to the V-
LDAA during the 𝐂𝐫𝐞𝐚𝐭𝐞 . The framework implies
to create two commits 𝑡= 𝐶𝑜𝑚
(
𝑖,𝒓
)
and 𝑡
=
𝐶𝑜𝑚𝑖
𝑞
,𝒓′. Let 𝑨
𝟐
and 𝑨
𝟐
, the vectors in
ℛ
×
of the form
[
01ℛ
ℛ
]
(as defined in
section 3.2) and respectively associated to 𝑡 and 𝑡
.
Using equation (2) to recover equation (1), it’s easy
to see that 𝑨
𝟐
and 𝑨
𝟐
need to be equal to −[𝒂
𝑻
𝒂
𝑯
]
that contradicts the fact that those two matrix are
generated as
[
01ℛ
ℛ
]
. This issue is not
mentioned in the original paper.
The 𝐁𝐥𝐢𝐧𝐝𝐒𝐢𝐠𝐧/𝐕𝐞𝐫𝐢𝐟𝐲 protocol is
implemented as described in (Del Pino and al., 2018).
3.2 Performances Analysis
We give a performance analysis of the timing of each
primitive of V-LDAA for two sets of parameters.
First, we compare our implementation with the one
provided in (Chen and al., 2021) with the same
instances: 𝑑 = 128, 𝑞 = 114356107 ≈2
.
According to LWE-estimator, the security level is
𝜆≈42. Secondly, we tested our implementation with
a more practical (regarding security) set achieving
128 bits of security.
The implementation run on a Core i5-8265U CPU
@1.60GHz. To get execution time, we took the
average of the times recorded on 50 executions for
each primitive.
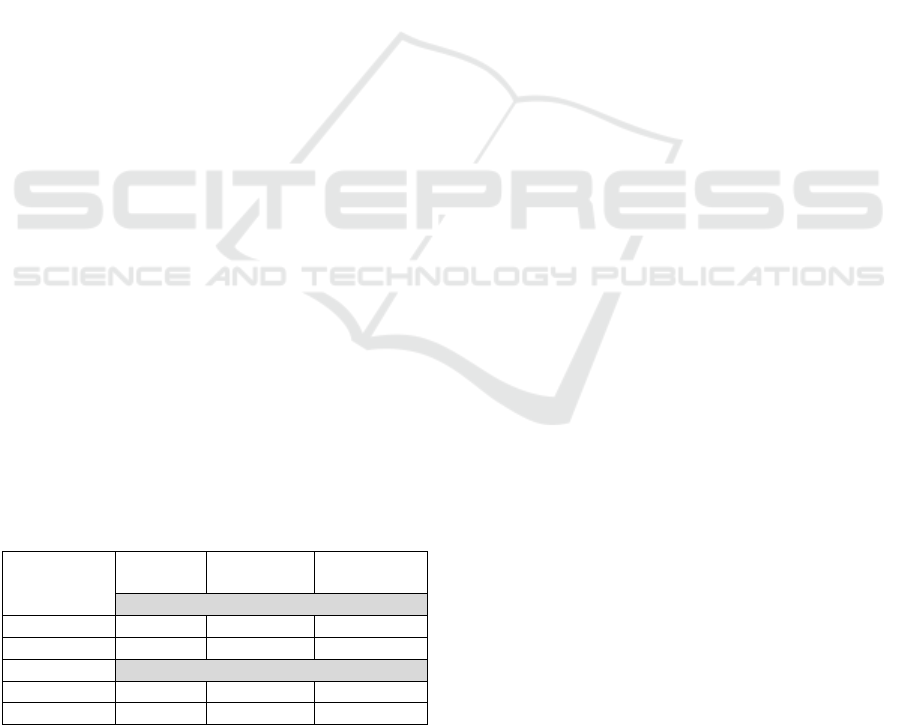
Table 3 below provides the execution time of all
primitives of the scheme. One can observe that our
implementation speeds up the 𝐉𝐨𝐢𝐧 procedure by
85% and the 𝐂𝐫𝐞𝐚𝐭𝐞 procedure by almost 80%
regarding previous work.
Table 3: Execution time of V-LDAA for two sets of
parameters and performance comparison with
implementation from (Chen and al., 2021).
Time (in seconds)
(Chen and
al., 2021)
Our implementation
Parameters
𝑛 = 128
𝑞= 2
𝜆≈44
VLDAA-
128
Setu
p
- 0.022 0.043
Join 7.45 1.19 72.05
Create 5.41 1.13 5.11
Si
g
n 0.030 0.030 0.087
Verif
y
0.047 0.069 0.68
Revoke -
1.41 + 𝑇
2.77 + 𝑇
Benchmark shows that the slower primitive is
𝐉𝐨𝐢𝐧. The bottleneck comes from the gaussian
sampler and especially from the generation of
perturbation. This is due to the number of operations
on polynomials (multiplication and inverse) executed
in the ring ℝ
[
𝑋
]
/
〈
𝑋
+1
〉
of real-coefficients
polynomial. However, in practice, the procedure 𝐉𝐨𝐢𝐧
is called one time and can be executed offline.
Additionally, the algorithm used for gaussian
sampling is parallelizable.
Execution time of primitive 𝐂𝐫𝐞𝐚𝐭𝐞 is versatile
because of the number of polynomial multiplications
and rejection sampling in 𝐁𝐥𝐢𝐧𝐝𝐒𝐢𝐠𝐧 . Using
parameters from VLDAA-128, we registered a
standard deviation of 5.05 seconds for this primitive.
𝐒𝐢𝐠𝐧 and 𝐕𝐞𝐫𝐢𝐟𝐲 are the two primitives that have
to be implemented in an embedded (i.e. resources-
constrained) environment and executed several times.
For
VLDAA-128, in signing operation, polynomial
error sampling takes 64.81% of the total time,
rejection sampling takes 20.09%, hashing takes
12.09% and multiplications takes 3.01%. 𝐕𝐞𝐫𝐢𝐟𝐲 is
slower than 𝐒𝐢𝐠𝐧 since two verifications are required:
SECRYPT 2024 - 21st International Conference on Security and Cryptography
646
on the message signature and on the signature of
credentials generated by 𝐁𝐥𝐢𝐧𝐝𝐯𝐞𝐫𝐢𝐟𝐲 . The latter
takes most of the times in the verification due to the
sixteen multiplications that takes 85.6% of the total
time.
Regarding the structure of these two primitives, it
is natural to find synergies with primitives Sign and
Verify of DILITHIUM (Ducas et al., 2018). Both
schemes sample a vector of polynomial to mask the
secret vector multiplied by a public matrix. However,
due to the specific structure of the ring and particular
choice of 𝑞 ≡ 3 𝑚𝑜𝑑 4 makes the V-LDAA not
compliant with the NTT for accelerating
multiplication operations (NTT requires 𝑞≡
1 𝑚𝑜𝑑 2𝑑).
The execution time of 𝐑𝐞𝐯𝐨𝐤 depends on 𝑇
,
the time used to encrypt the message to send to all
users for the revocation. The reference papers did not
specify the algorithm used.
3.3 Benchmark with Pre Quantum
DAA
We compare our implementation of the V-LDAA
with a pre-quantum ECC-based DAA proposed in
(Yang and al., 2021) and compliant with the TPM 2.0
specifications (Trusted Computing Group, 2014).
Benchmark of this ECC-DAA has been evaluated on
a 1.80GHz Intel Core i7-8550U CPU (host) paired
with an Infineon TPM 2.0. The implementation is in
C and uses the library ACML. TPM 2.0 specifications
include two pairing EC (Trusted Computing Group,
2014): BN_P256 and BN_P638. The first provides ≈
100 bits of security but cryptanalysis shows that
BN_P256 curve is no longer secure (Barbulescu and
al., 2018). The second guarantees 128 bits of security
but is not implemented on Infineon TPM 2.0.
Table 4: Comparison of the execution time of sign/verify
operation and size of credentials/signature between our
implementation of V-LDAA and ECC-based DAA of
(Yang and al., 2021).
VLDAA-
128
BN_P256 BN_P636
Size (in bytes)
Credentials 44,142 193 479
Sign. size 431,254
705 + 𝑜(1) 1,800 + 𝑜(1)
Time (in ms)
Sign time 87 137 -
Verif. Time 680 81 -
The size of credentials and signature remain very
large compared to those of the EC-DAA. The
signature size includes the signature of the message
(≈25 𝑘𝐵) and the attestation signature (≈406 kB).
This confirms a general impact of post-quantum
cryptography on the instance size increasing
regarding pre-quantum cryptography The sign
operation is 37% faster in V-LDAA than in EC-DAA
with BN_P256 but the verify much slower in the
lattice-based case.
4 CONCLUSIONS
We proposed a software implementation of the most
recent V-LDAA and a complete parametrization of
the scheme. The main bottleneck remains the non-
compatibility of the NTT with the algebraic structure
of the V-LDAA to improve polynomial
multiplication. Size of the instances also represents a
huge challenge especially regarding to the size of
attestation signature.
This work is a first step toward the optimization
of V-LDAA implementation to achieve TPM
requirements in terms of resources. The synergy with
DILITHIUM regarding the Sign and Verify could
bring strong enabler to accelerate the LDAA in
hardware.
REFERENCES
Agrawal, S., Boneh, D., & Boyen, X. (2010). Efficient
lattice (H) IBE in the standard model. In Advances in
Cryptology–EUROCRYPT 2010: 29th Annual
International Conference on the Theory and
Applications of Cryptographic Techniques, French
Riviera, May 30–June 3, 2010. Proceedings 29 (pp.
553-572). Springer Berlin Heidelberg.
Albrecht, R.M., Player, R., Scott, S. (2015). On the
concrete hardness of Learning with Errors, In Journal
of Mathematical Cryptology 2015. Related website:
https://lwe-estimator.readthedocs.io/en/latest/
Albrecht, M., Chase, M., Chen, H., Ding, J., Goldwasser,
S., Gorbunov, S., ... & Vaikuntanathan, V. (2021).
Homomorphic encryption standard. Protecting privacy
through homomorphic encryption, 31-62.
Bansarkhani, R. E., and Kaafarani, A. E. (2017) Direct
anonymous attestation from lattices. In Cryptology
ePrint Archive, Report 2017/1022.
Barbulescu, R., & Duquesne, S. (2019). Updating key size
estimations for pairings. Journal of cryptology, 32,
1298-1336.
Baum, C., Damgård, I., Lyubashevsky, V., Oechsner, S., &
Peikert, C. (2018, August). More efficient
commitments from structured lattice assumptions.
In International Conference on Security and
Cryptography for Networks (pp. 368-385). Cham:
Springer International Publishing.
On the Implementation of a Lattice-Based DAA for Vanet System
647

Bert, P., Eberhart, G., Prabel, L., Roux-Langlois, A., &
Sabt, M. (2021). Implementation of lattice trapdoors on
modules and applications. In Post-Quantum
Cryptography: 12th International Workshop,
PQCrypto 2021, Daejeon, South Korea, July 20–22,
2021, Proceedings 12 (pp. 195-214). Springer
International Publishing.
Brickell, E., Camenisch, J., and Chen, L. (2004). Direct
anonymous attestation. In ACM Conference on
Computer and Communications Security, CCS 2004,
ACM.
Brickell, E., Chen, L., and Li, J. (2008). A new direct
anonymous attestation scheme from bilinear maps. In
Trusted Computing - Challenges and Applications, pp.
166–178.
Carmona, M., Lesaignoux, D., & Loiseau, A. (2023, July).
On the implementation of a lattice-based revocable
hierarchical Ibe. In SECRYPT 2023-20th International
Conference on Security and Cryptography (pp. 617-
623). SCITEPRESS–Science and Technology
Publications, Lda..
Chen, L. (2010). A DAA scheme requiring less TPM
resources. In Information Security and Cryptology: 5th
International Conference, Inscrypt 2009, Beijing,
China, December 12-15, 2009. Revised Selected Papers
5 (pp. 350-365). Springer Berlin Heidelberg.
Chen, L., El Kassem, N., Lehmann, A., & Lyubashevsky,
V. (2019). A framework for efficient lattice-based daa.
In Proceedings of the 1st ACM Workshop on Workshop
on Cyber-Security Arms Race (pp. 23-34).
Chen, L., Tu, T., Yu, K., Zhao, M., and Wang, Y. (2021).
V-ldaa: A new lattice-based direct anonymous
attestation scheme for vanets system. Security and
Communication Networks, 2021, 1-13.
Del Pino, R., Lyubashevsky, V., & Seiler, G. (2018,
October). Lattice-based group signatures and zero-
knowledge proofs of automorphism stability.
In Proceedings of the 2018 ACM SIGSAC conference
on computer and communications security (pp. 574-
591).
Ducas, L., Kiltz, E., Lepoint, T., Lyubashevsky, V.,
Schwabe, P., Seiler, G., & Stehlé, D. (2018). Crystals-
dilithium: A lattice-based digital signature
scheme. IACR Transactions on Cryptographic
Hardware and Embedded Systems, 238-268.
Genise, N., & Micciancio, D. (2018). Faster Gaussian
sampling for trapdoor lattices with arbitrary modulus.
In Advances in Cryptology–EUROCRYPT 2018: 37th
Annual International Conference on the Theory and
Applications of Cryptographic Techniques, Tel Aviv,
Israel, April 29-May 3, 2018 Proceedings, Part I
37 (pp. 174-203). Springer International Publishing.
Gentry, C., Peikert, C., & Vaikuntanathan, V. (2008, May).
Trapdoors for hard lattices and new cryptographic
constructions. In Proceedings of the fortieth annual
ACM symposium on Theory of computing (pp. 197-
206).
Giraud, L., Langou, J., Rozloznik, M. (2005). The Loss of
Orthogonality in the Gram-Schmidt Orthogonalization
Process, In Computers & Mathematics with
Applications.
Hashlib, (2001), Hashlib official site: https://docs.python.o
rg/3/library/hashlib.html
He, D., Zeadally, S., Xu, B., & Huang, X. (2015). An
efficient identity-based conditional privacy-preserving
authentication scheme for vehicular ad hoc
networks. IEEE Transactions on Information Forensics
and Security
, 10(12), 2681-2691.
International Organization for Standardization. ISO/IEC
20008-2: Information technology - Security techniques
- Anonymous digital signatures – Part 2: Mechanisms
using a group public key, 2013.
Klein, P. (2000, February). Finding the closest lattice vector
when it's unusually close. In Proceedings of the
eleventh annual ACM-SIAM symposium on Discrete
algorithms (pp. 937-941).
Ling, S., Nguyen, K., Stehlé, D., & Wang, H. (2013,
February). Improved zero-knowledge proofs of
knowledge for the ISIS problem, and applications.
In International workshop on public key
cryptography (pp. 107-124). Berlin, Heidelberg:
Springer Berlin Heidelberg.
Micciancio, D., & Peikert, C. (2012, April). Trapdoors for
lattices: Simpler, tighter, faster, smaller. In Annual
International Conference on the Theory and
Applications of Cryptographic Techniques (pp. 700-
718). Berlin, Heidelberg: Springer Berlin Heidelberg.
Lyubashevsky, V., & Micciancio, D. (2006, July).
Generalized compact knapsacks are collision resistant.
In International Colloquium on Automata, Languages,
and Programming (pp. 144-155). Berlin, Heidelberg:
Springer Berlin Heidelberg.
Lyubashevsky, V., Peikert, C., & Regev, O. (2010). On
ideal lattices and learning with errors over rings.
In Advances in Cryptology–EUROCRYPT 2010: 29th
Annual International Conference on the Theory and
Applications of Cryptographic Techniques, French
Riviera, May 30–June 3, 2010. Proceedings 29 (pp. 1-
23). Springer Berlin Heidelberg.
Lyubashevsky, V. (2012, April). Lattice signatures without
trapdoors. In Annual International Conference on the
Theory and Applications of Cryptographic
Techniques (pp. 738-755). Berlin, Heidelberg: Springer
Berlin Heidelberg.
National Institute of Standards and Technology (NIST).
Module-Lattice-Based Digital Signature Standard,
2024.
Trusted Computing Group. TPM main specification version
1.2, 2004.
Trusted Computing Group. Trusted platform module
library specification, family “2.0”, 2014.
Yang, K., Chen, L., Zhang, Z., Newton, C. J., Yang, B., &
Xi, L. (2021). Direct anonymous attestation with
optimal tpm signing efficiency. IEEE transactions on
information forensics and security, 16, 2260-2275.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
648
