
Taxonomy of Governance Mechanisms for Trust Management In Smart
Dynamic Ecosystems
Dasa Kusnirakova
a
and Barbora Buhnova
b
Faculty of Informatics, Masaryk University, Brno, Czech Republic
Keywords:
Trust, Trust Management, Governance, Taxonomy, Smart Dynamic Ecosystems.
Abstract:
In our evolving society, a future is envisioned where humans and digital systems converge to shape dynamic
and unpredictable ecosystems constantly adapting to ever-changing conditions. Such smart dynamic ecosys-
tems, which seamlessly merge digital agents, physical infrastructure, and human-technology interactions, need
to enable the formation of partnerships between their members to collectively solve complex tasks. This ne-
cessitates the establishment of trust together with effective governance mechanisms on the ecosystem level,
which emerge as crucial elements to ensure the proper functioning, safety, and adherence to established rules.
However, there is currently very little understanding of what such trust-supporting governance mechanisms
could look like. In this paper, we open this promising scientific field with compiling a taxonomy of governance
mechanisms aimed at supporting trust management in smart dynamic ecosystems. By this, we take an initial
step into the development of a comprehensive governance model and stimulate further research to address this
critical aspect of managing the complex and dynamic nature of these ecosystems.
1 INTRODUCTION
Our society is moving towards the future where dig-
ital systems, physical objects and social interactions
among humans and technology all seamlessly merge
to form intelligent and adaptive ecosystems (Liu et al.,
2011; Capilla et al., 2021). These smart dynamic
ecosystems, where all the members interact, collab-
orate, and adapt to the constantly changing needs of
the environment (Xia and Ma, 2011), are however in-
herently unpredictable.
The need of ecosystem members to form partner-
ships and collaborate with others in order to collec-
tively solve complex tasks thus calls for establish-
ing trust, a crucial and yet under-researched concept
necessary to support human-to-machine and machine-
to-machine interactions (Schreieck et al., 2016; Me-
chanic, 1996).
Several studies underscore the key role of building
and maintaining trust among the members of smart
dynamic ecosystems for the successful adoption
of autonomous and intelligent technologies (Capilla
et al., 2021; Beer et al., 2014). The concept of trust
and its importance within the digital world can play
a
https://orcid.org/0000-0002-5341-902X
b
https://orcid.org/0000-0003-4205-101X
a major role, for instance, in selecting trusted in-
formation or service providers among various smart
agents in the ecosystem, or as a self-protection mech-
anism against untrusted and potentially malicious
agents (Buhnova et al., 2023), such as those designed
with the intention to cause harm or deceive and ma-
nipulate others.
Besides establishing trust among the ecosystem’s
agents, effective governance is crucial to guarantee
the proper functioning of such dynamic ecosystems
in terms of safety and adherence to established rules.
This governance includes developing strategies and
rules (Schreieck et al., 2016) based on the specific
needs of the ecosystem in question, i.e. rules for en-
tering the ecosystem, ensuring trustworthy communi-
cation and forming partnerships among ecosystem’s
members. An efficient governance model should also
encompass mechanisms for upholding moral and eth-
ical responsibility and advancing principles like sol-
idarity and fairness. Otherwise, agents might be-
have unethically or perform actions endangering other
members or disrupting the whole ecosystem. Yet, the
current understanding of the mechanisms and compo-
nents that shall form such a governance model is so
far very fragmented.
In this paper, we propose a taxonomy of gover-
nance mechanisms for trust management in smart dy-
700
Kusnirakova, D. and Buhnova, B.
Taxonomy of Governance Mechanisms for Trust Management In Smart Dynamic Ecosystems.
DOI: 10.5220/0012726100003687
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 19th International Conference on Evaluation of Novel Approaches to Software Engineering (ENASE 2024), pages 700-710
ISBN: 978-989-758-696-5; ISSN: 2184-4895
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

namic ecosystems, compiled from a review of exist-
ing literature. We believe that via interconnecting the
fragmented knowledge on the topic, this paper offers
a solid ground for the scientific community to stimu-
late further research and collaboration to address the
critical aspect of managing the complex and dynamic
nature of smart dynamic ecosystems.
The rest of this paper is organized as follows. Sec-
tion 2 summarizes the related work, while section 3
describes the methodology employed to build the pro-
posed taxonomy of governance mechanisms for smart
dynamic ecosystems. The taxonomy itself is pre-
sented in section 4. Afterward, sections 5 and 6 con-
clude the paper with a discussion of future research
directions.
2 RELATED WORK
The governance of trust management in smart dy-
namic ecosystems represents a complex research field
in its scope (i.e., what research challenges need to
be addressed), breadth (i.e., what mechanisms and in
which interplay are needed to address the challenges),
and depth of the individual mechanisms (i.e., what
are the effective ways to address the individual chal-
lenges). While attempts to the depth aspect of the
challenge exist in the literature, unless there is an un-
derstanding of the breadth and scope of the problem,
which is currently very fragmented, we can hardly
hope for an effective solution to the problem.
A notable pillar of knowledge in terms of tax-
onomies addressing the governance of quality aspects
in complex ecosystems can be traced in Social Inter-
net of Things (SIoT) (Alkhabbas et al., 2019), which
however focuses on technical-quality aspects, such
as ensuring resilience (Berger et al., 2021), secu-
rity (Williams et al., 2019; Rizvi et al., 2018), or ser-
vice discovery (Roopa et al., 2019), instead of trust.
On the other hand, the works that focus on categoriz-
ing the aspects of trust and trust management within
SIoT (Ahmed et al., 2019; Chahal et al., 2020; Ahmed
et al., 2020), recognizing trust as the fundamental
building block of SIoT (Khan et al., 2020) needed for
effective interactions and collaboration of SIoT mem-
bers, focus on particular aspects of trust such as prop-
erties, metrics, and trust attacks, leaving the gover-
nance mechanisms for trust management largely un-
explored.
Governance in the context of Internet of Things
(IoT) has been researched from the direction of
decision-making (Almeida et al., 2017), and roles
and responsibilities management (Gerber and Kansal,
2020), while unfortunately overlooking trust-based
governance. Besides, considerable research effort
has been dedicated to developing governance mech-
anisms and frameworks for Cyber-Physical-Social
Systems (CPSS) (Katina and Keating, 2018; Katina
et al., 2017). These works predominantly focus on in-
dividual systems, though, rather than holistically ad-
dressing the governance needs of entire ecosystems in
which CPSS operate, and thus lack systematic orga-
nization of the necessary mechanisms.
As for the field of software ecosystems, there ex-
ist studies addressing trust management (Hou and
Jansen, 2023) and governance (Alves et al., 2017) is-
sues. However, it is crucial to recognize that smart
dynamic ecosystems diverge from software ecosys-
tems as the former encompasses a blend of physi-
cal and digital entities, adapting to real-world con-
ditions, while the latter predominantly involves dig-
ital components and applications operating in virtual
spaces. Due to this key difference, the principles and
strategies employed in trust management and gov-
ernance within software ecosystems cannot directly
translate to the complexities presented by smart dy-
namic ecosystems but need to be addressed sepa-
rately.
To sum up, while notable sources of knowledge
exist on the fragments of the topic, there is a lack of
(1) a comprehensive taxonomy of governance mecha-
nisms, (2) tailored for smart dynamic ecosystems and
(3) centered around trust. In this paper, we fill the
gap by introducing an initial version of the taxonomy
of governance mechanisms for trust management in
smart dynamic ecosystems.
3 METHODOLOGY
To identify relevant papers, we conducted an
exploratory search across electronic academic
databases. The search utilized combinations of
keywords on trust, trust management, govern*, IoT,
and SIoT to retrieve an initial set of papers. This
collection was further expanded by incorporating
selected reference papers cited in the initial set. The
collected papers were then examined with a focus
on the identification of mechanisms essential for
the governance of trust management within smart
dynamic ecosystems.
In order to classify the collected governance
mechanisms, a classification scheme was developed
following the methodology proposed by Usman et
al. (Usman et al., 2017). Thus, we applied the fol-
lowing four phases: (1) Planning, (2) Identification
and Extraction, (3) Design and Construction, and (4)
Validation.
Taxonomy of Governance Mechanisms for Trust Management In Smart Dynamic Ecosystems
701
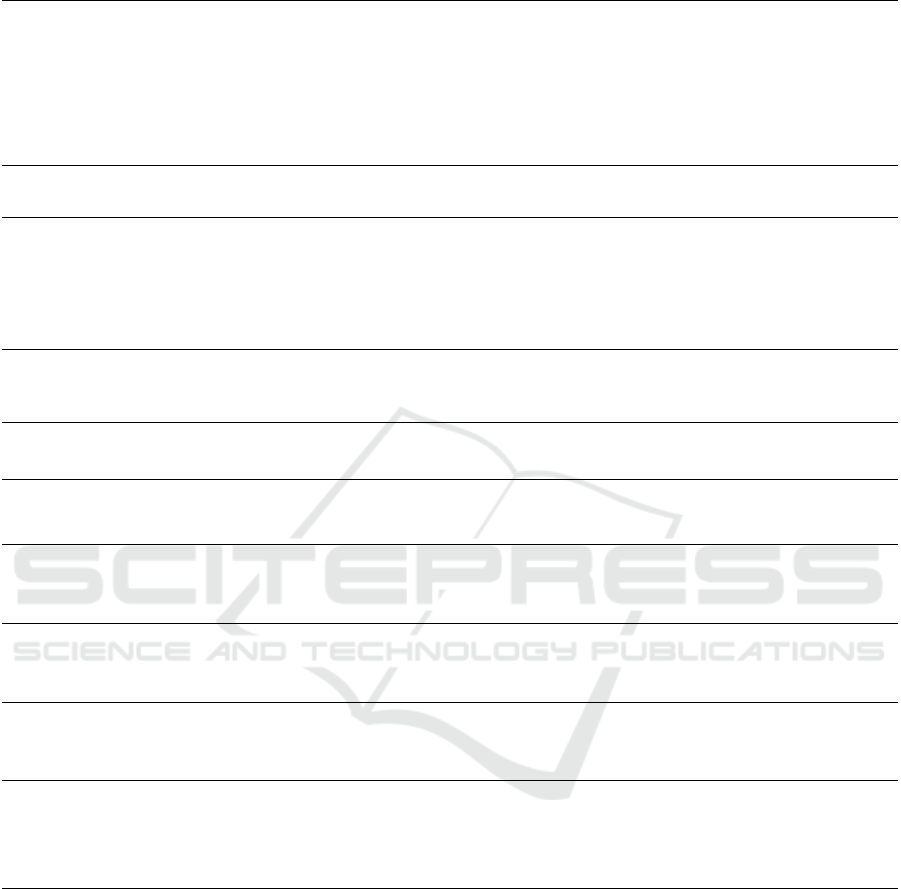
Table 1: References for Trust Score Management and Ecosystem Wellbeing Management mechanisms.
Trust Score Management
Trust Evidence
Collection
Trust Metrics
QoS Metrics Quality of Service (QoS) trust metrics (Xiao et al., 2015; Bao and Chen, 2012b)
Social Metrics
social interactions (Yan et al., 2016), social metrics (Buhnova et al., 2023), honesty (Yan
et al., 2016; Nitti et al., 2013), openness (Iqbal and Buhnova, 2022), fairness (Nwebonyi
et al., 2019)
social trust parameters (Chen et al., 2014; Bao and Chen, 2012a)
Time Dimension
Past Behaviour
past subjective experiences (Gwak et al., 2017), past behaviours (Meena Kowshalya and
Valarmathi, 2017)
Present Behaviour present experience (Buhnova, 2023), present behavior (Mehdizadeh and Farzaneh, 2022)
Future Behaviour futuristic behaviours (Meena Kowshalya and Valarmathi, 2017)
Trust Score
Computation
Local
subjective trust calculation (Ghafari et al., 2020; Bo et al., 2017), distributed computing
(Asiri and Miri, 2016)
Global centralized authority for computations (Asiri and Miri, 2016), guarantor (Clarke et al., 2013)
Trust Score
Propagation
From Members
to Central Authority
global share (Nitti et al., 2013), centralized (Resnick et al., 2000), reputation centre (Jøsang
et al., 2007)
From Members
to Members
distributed collaborating filtering (Chen et al., 2014), distributed (Kamvar et al., 2003; Men-
doza and Kleinschmidt, 2015), distributed stores (Jøsang et al., 2007)
From Central Au-
thority to Members
from central authority (Jøsang et al., 2007), intermediate or provider (Nitti et al., 2013)
Trust Score
Lifecycle
Initialization initial trust value (Chen et al., 2015), entrance of a new object (Atzori et al., 2012)
Update
trust update (Chen et al., 2014; He et al., 2020; Peng et al., 2008), value update (Namal
et al., 2015)
Erosion trust erosion (Sagar et al., 2022; Truong et al., 2017; Rana et al., 2022)
Ecosystem Wellbeing Management
Incentive Mechanisms
Reward Mechanisms
reward mechanisms (Bangui et al., 2023a; Bangui et al., 2023b; Guo et al., 2021; Zhaofeng
et al., 2019; Malik et al., 2019; Xiaoxue et al., 2010), reward system (Singh and Kim, 2018)
Punishment Mechanisms
punishment mechanisms (Bangui et al., 2023a; Bangui et al., 2023b; Guo et al., 2021; Xi-
aoxue et al., 2010), punishment (Etalle et al., 2007), penalties (Malik et al., 2019)
Safety Assurance
Isolation of Untrusted Mem-
bers
isolate untrusted devices (Banerjee et al., 2018), isolation module (Hategekimana et al.,
2020)
Isolation of Trust Management
Disruptors
isolation of attacking nodes (Muzammal et al., 2020; Alsumayt et al., 2017), isolating mali-
cious devices (Nandhini et al., 2022; Seshadri et al., 2020; Ahmed et al., 2015)
Detection of Trust
Management Disruptors
Detection of Disruptive
Members
detection of malicious nodes (Liu et al., 2019; She et al., 2019; Li et al., 2020; Wang and
Wei, 2021; Khatun et al., 2019; Illi et al., 2023)
Detection of Trust Attacks
trust attack detection (Caminha et al., 2018; Abdelghani et al., 2019; Marche and Nitti,
2020; Masmoudi et al., 2020; Magdich et al., 2021)
Trade-off Analysis in
Decision Making
Resolving Conflicting Values,
Interests and Goals
conflicting preferences (Zavvos et al., 2021), conflicting information (K
¨
okciyan and Yolum,
2020)
Detection of Discrimination
discrimination of objects (Jafarian et al., 2020; Illi et al., 2023), discrimination attack
(Marche and Nitti, 2020)
Corrective Mechanisms
Trust Score/Decision Re-
assessment
self-correction (Lochner and Smilek, 2023), trust miscomputation (Khan et al., 2015), feed-
back loop (Bangui et al., 2023a)
Correction of Trust Score
Miscomputation
self-correction (Lochner and Smilek, 2023), trust miscomputation (Khan et al., 2015)
Reparation/Compensation of
Affected Members
trust compensation (Yu et al., 2017)
The initial phase involved the planning process,
where the ideas for the classification scheme were
collected. In the second phase, the dimensions for
the classification of governance mechanisms were de-
veloped, drawn from the grouping of the mechanisms
found in the literature. This was performed iteratively
by the authors and each dimension was discussed and
agreed by the authors. Moving into the third phase,
the taxonomy was constructed by combining pro-
posed dimensions and validated in the fourth phase
by correspondence and backward snowball analysis
searches that have been used in the taxonomy descrip-
tions, as elaborated in the discussion in section 5.2.
The complete list of references for individual mecha-
nisms is provided in Table 1.
4 TAXONOMY
One of the initial findings when exploring the col-
lected governance mechanisms is the clustering of
the mechanisms around two core concepts: trust as-
sessment and trust assurance. While the governance
mechanisms connected to trust assessment can be ex-
plained as answering the question of ”Can I trust?”,
ENASE 2024 - 19th International Conference on Evaluation of Novel Approaches to Software Engineering
702
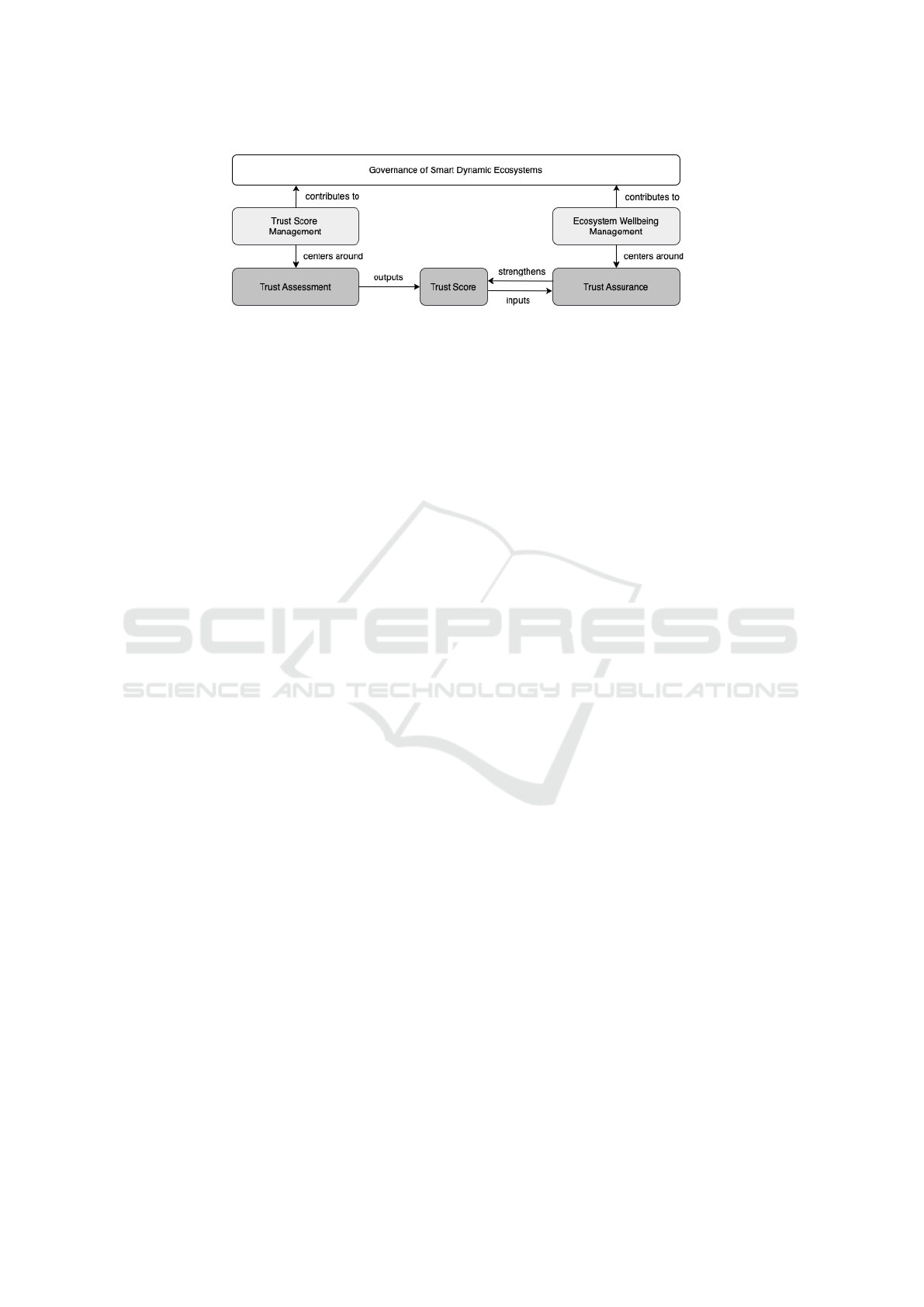
Figure 1: Relationship between Trust Assessment and Trust Assurance, and their contribution to governance.
the governance mechanisms connected to trust assur-
ance can be essentially reduced to the support of an-
swering the question of ”How to ensure I can trust?”.
The former cluster consists of mechanisms of trust
score computation, collection of trust evidence and
inputs for such computation, trust score propagation,
and management of the trust score over time, and is
referred to as Trust Score Management in our taxon-
omy introduced in section 4.1.
The latter cluster consists of incentive mecha-
nisms to motivate trustworthy behaviour (and punish
its violations), detection of untrustworthy members
and their isolation to promote safety and wellbeing
of the remaining ecosystem members, and corrective
mechanisms in case of trust misjudgement and dis-
crimination that happens in effect of that. We refer
to this cluster as Ecosystem Wellbeing Management,
which is presented in section 4.2.
The symbiotic relationship between these two
clusters is visualized in 1. Trust Score Management
activities center around trust assessment. It serves
as the foundation for the initial evaluations of each
ecosystem member’s trustworthiness. Once an entity
is assessed for trust, it is awarded a trust score, and
trust assurance comes into play. This is the center
of Ecosystem Wellbeing Management mechanisms,
whose role is to gradually increase the trustworthiness
of individual members (via motivating them to better
behaviour and expelling disruptors). Together, Trust
Score Management and Ecosystem Wellbeing Man-
agement contribute to the governance of smart dy-
namic ecosystems by creating a cycle that reinforces
and sustains the concept of trust within the ecosystem
over time.
4.1 Trust Score Management
The focus of Trust Score Management mechanisms
centers around trust assessment, i.e. awarding a trust
score to an entity. In order to do that, there need to
be mechanisms in place responsible for collecting ev-
idence that serves as input data for trust score calcu-
lation, keeping the scores updated, and propagating it
across the network.
We describe the governance mechanisms respon-
sible for trust score management in the following
paragraphs and summarize them in 2.
1. Trust Evidence Collection and Information Gath-
ering
Collecting information is a necessary prerequi-
site for the calculation of trust scores representing
the trustworthiness of individual ecosystem mem-
bers. These trust scores are calculated on the basis
of selected features called trust metrics, that are
monitored and combined in time (Meena Kow-
shalya and Valarmathi, 2017).
Trust metrics capture different qualities of inter-
actions occurring between agents. These can refer
to QoS metrics reflecting the ability of an agent
to provide quality services in terms of reliability
or accuracy (Xiao et al., 2015; Bao and Chen,
2012b). Other mechanisms focus on capturing so-
cial relationships among agents in terms of hon-
esty, openness, altruism, or unselfishness (Nitti
et al., 2013) by monitoring social metrics.
To address the time dimension, it is neces-
sary to consider mechanisms that monitor past,
present, and future behaviour. Monitoring trust
metrics over time enables the ecosystem to gain
understanding of how trust dynamics changes and
to adapt to evolving trust scenarios by feeding
design-time, runtime, and predictive models, re-
spectively, and allows for the anticipation of po-
tential malicious intentions (Meena Kowshalya
and Valarmathi, 2017).
Evidence collection also serves as a promising
tool for justifying decisions that might be opposed
by certain ecosystem agents, detecting any poten-
tial trust attacks, and proving malicious intentions
of agents before they become fully evident (Buh-
nova, 2023).
Note that in all these cases, various mechanisms
can be in place to promote the exchange of the
metrics between the trustor and the trustee. How-
ever, as trust is essentially a belief of the trustor
Taxonomy of Governance Mechanisms for Trust Management In Smart Dynamic Ecosystems
703

about the trustee’s trustworthiness, the trustor
needs to be given a way to validate the metrics
themselves, which can be supported by the trustee
by sharing an explanation of their actual or in-
tended actions (Iqbal and Buhnova, 2022).
2. Trust Score Computation
Different mechanisms must be applied to calcu-
late trust scores at different levels of the ecosys-
tem. Typically, the literature mentions local and
global trust score computation (Ghafari et al.,
2020).
Local trust scores are calculated on the ecosys-
tem member level. They are derived from agent-
to-agent relationships, which involve the assess-
ment of one agent’s trustworthiness by another,
utilizing local information such as current obser-
vations or past experience. In contrast, global
trust score extends beyond individual interac-
tions, representing an agent’s reputation within
the broader ecosystem. In this context, each
agent’s reputation is linked to the local trust scores
assigned by other agents in the ecosystem, creat-
ing a network of mutual influence on overall trust-
worthiness. These calculations are made at the
central authority level, e.g. by reputation mod-
els (Asiri and Miri, 2016).
3. Trust Score Propagation
Trust score propagation describes how trust infor-
mation spreads throughout the network. There are
various kinds of trust score propagation schemes
found in the literature – (1) centralized schemes
depending on a central node that is responsible
for gathering trust-related data and propagating it
across the network (Nitti et al., 2013), (2) decen-
tralized schemes where each ecosystem member
is responsible for trust computation and propaga-
tion on its own (Chen et al., 2014), and (3) hybrid
schemes combining centralized and decentralized
principles (Nitti et al., 2013).
While centralized schemes are vulnerable to
a single point of failure and are not suitable
for large-scale networks (Karthik and Anantha-
narayana, 2017), decentralized schemes face chal-
lenges associated with limited computational ca-
pacity of individual nodes and unbiased propa-
gation of trust scores across the network (Jøsang
et al., 2007). Since hybrid schemes are able
to mitigate the challenges of both aforemen-
tioned propagation schemes (Karthik and Anan-
thanarayana, 2017), they are frequently em-
ployed throughout the research works (Karthik
and Ananthanarayana, 2017; Mahmood et al.,
2019). It is, therefore, necessary to ensure that ap-
propriate trust score propagation mechanisms are
employed in the ecosystem. These include mech-
anisms capable of propagating individual trust
scores not only between members of the ecosys-
tem and the central authority (in both directions)
but also among the members themselves.
4. Trust Score Lifecycle
Besides the evidence collection, computation and
propagation of trust scores throughout the ecosys-
tem, governance mechanisms dealing with trust
score lifecycle need to be established, too. Trust
score lifecycle covers multiple phases, namely
the trust score (1) initialization, (2) update and
(3) erosion, and shall be implemented at both
the local levels (i.e., ecosystem members storing
the trust scores of their peers) and global levels
(i.e., trust scores managed by the global reputa-
tion model). They are responsible for ensuring the
integrity and reliability of the scoring system.
The mechanisms for trust score initialization
(sometimes referred to as bootstrapping) are re-
sponsible for assigning a trust score value to
agents newly entering the ecosystem without any
previous records (Atzori et al., 2012). Determin-
ing the appropriate initial trust score value is a
challenging task (Chen et al., 2015). If the initial
trust score is too low, new agents might experi-
ence difficulties in engaging in meaningful inter-
actions with other agents within the ecosystem, as
they are not trusted. On the other hand, setting the
initial trust score value too high may pose a risk
that malicious agents could exploit this initial trust
to inflict harm before being identified as untrust-
worthy, or abuse it to whitewash their reputation
via leaving and re-entering the ecosystem with a
clean trust score.
The update phase demands dynamic mecha-
nisms that facilitate real-time adjustments, con-
sidering evolving circumstances and agents’ be-
haviour. The updates are typically managed
through event-driven, time-driven, or hybrid ap-
proaches. In the event-driven scenario, trust
scores are updated upon the completion of an
interaction with other agents, or after a specific
event has occurred (Chen et al., 2014). How-
ever, this approach introduces the drawback of in-
creased network traffic overhead. Alternatively,
in the time-driven approach, trust is updated reg-
ularly at specific time intervals, ensuring a peri-
odic assessment of an agent’s trust score (Namal
et al., 2015). Lastly, the hybrid approach com-
bines both aforementioned approaches, enabling
trust updates at set intervals and/or in response to
ENASE 2024 - 19th International Conference on Evaluation of Novel Approaches to Software Engineering
704
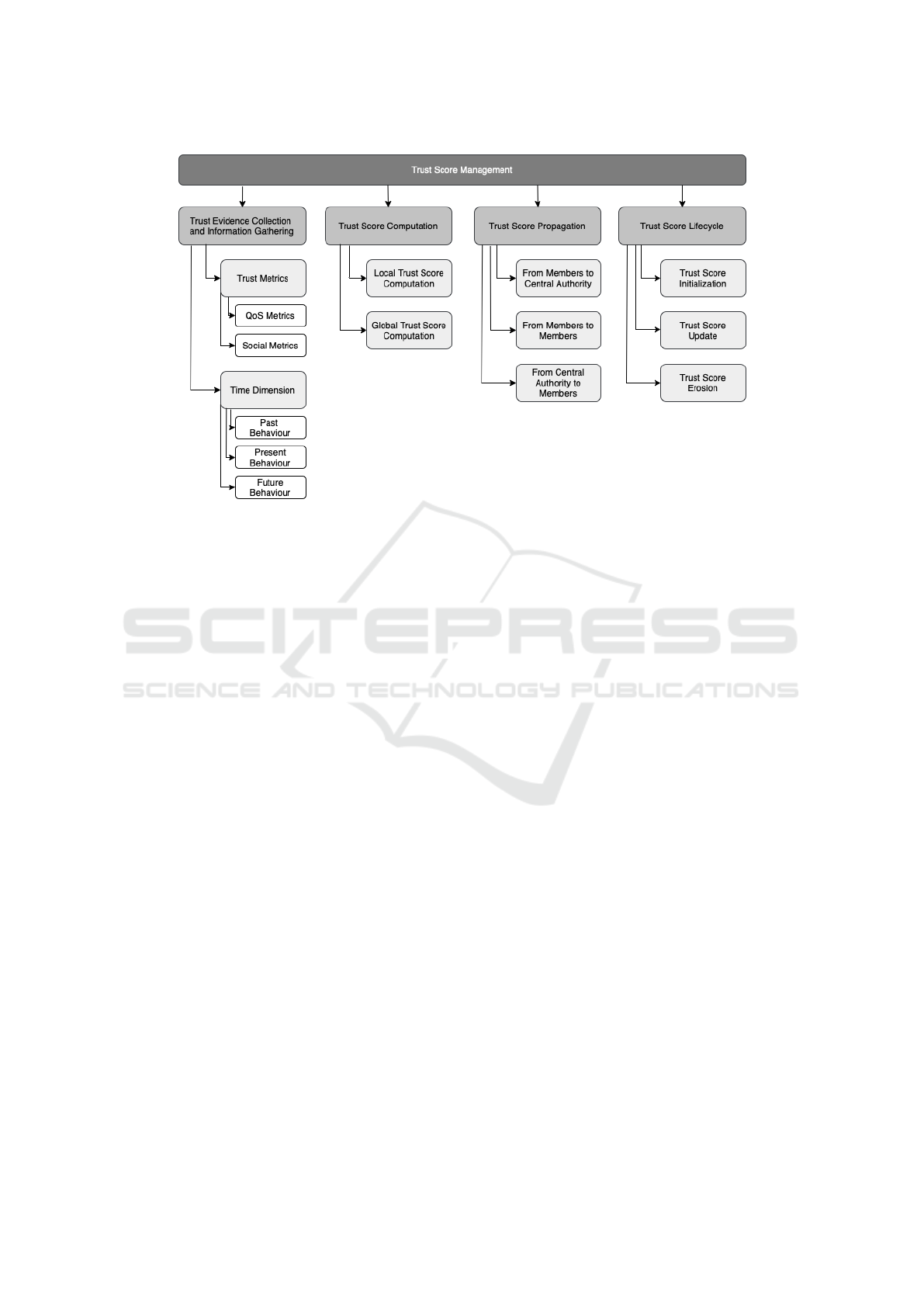
Figure 2: Taxonomy of Governance Mechanisms for Trust Score Management.
specific events or interactions (Xiao et al., 2015).
In addition to the dynamic nature of an agent’s
trust score within the ecosystem, a high trust score
or reputation shall deteriorate towards a neutral
value when an agent experiences a lack of inter-
actions or engages in too few interactions (Truong
et al., 2017). It is therefore necessary to estab-
lish mechanisms taking into account the lifespan
of trust values, whereby the trust score of inactive
agents undergoes the erosion process after a spec-
ified duration of inactivity (Sagar et al., 2022) in
order to keep the trust scores up to date.
4.2 Ecosystem Wellbeing Management
Trust represents a valuable resource influencing the
overall health of the ecosystem. It elevates various as-
pects of the ecosystem wellbeing, such as the ability
for the ecosystem members to depend on each other
and feel safe, fairness by promoting equitable interac-
tions and decision-making, or solidarity through en-
couraging collaboration and mutual support within
the ecosystem.
In the following paragraphs, we list the gov-
ernance mechanisms responsible for the ecosystem
wellbeing identified in our study. The mechanisms
are also summarized in 3.
1. Incentive Mechanisms
Encouraging behaviours aligned with ecosystem’s
rules and values belongs to the key mechanism for
enhancing the well-being of the ecosystem that
need to be established. This is being achieved
through incentives, i.e. a system of rewards and
punishments. The decision to reward or punish
an agent can be determined by various factors,
e.g. its current trust score or based on the re-
cent relative changes in it, such as an increase
or decrease (Bangui et al., 2023a; Bangui et al.,
2023b).
2. Safety Assurance
Given that trust in smart dynamic ecosystems is
understood as ”the attitude or belief of an agent
(trustor) to achieve a specific goal in interaction
with another agent (trustee) under uncertainty
and vulnerability” (Buhnova, 2023), trust man-
agement is only meaningful in the environments
where the members feel vulnerable in some way.
This lies behind the importance of safety assur-
ance on the ecosystem level, which needs to be in
place to protect vulnerable members in the pres-
ence of members with questionable trustability.
Ensuring safety within the ecosystem is closely
tied to the ability to expel or isolate untrusted
agents, which might be dangerous, or disruptors,
which are assumed to disrupt the wellbeing of the
ecosystem. In situations where trust is used to
navigate the sharing of information or provision
of services, the trustor can easily choose not to
use the knowledge or services provided by un-
trustworthy agents. However, in complex scenar-
ios involving physical safety and human lives, e.g.
avoiding collisions with malicious autonomous
Taxonomy of Governance Mechanisms for Trust Management In Smart Dynamic Ecosystems
705
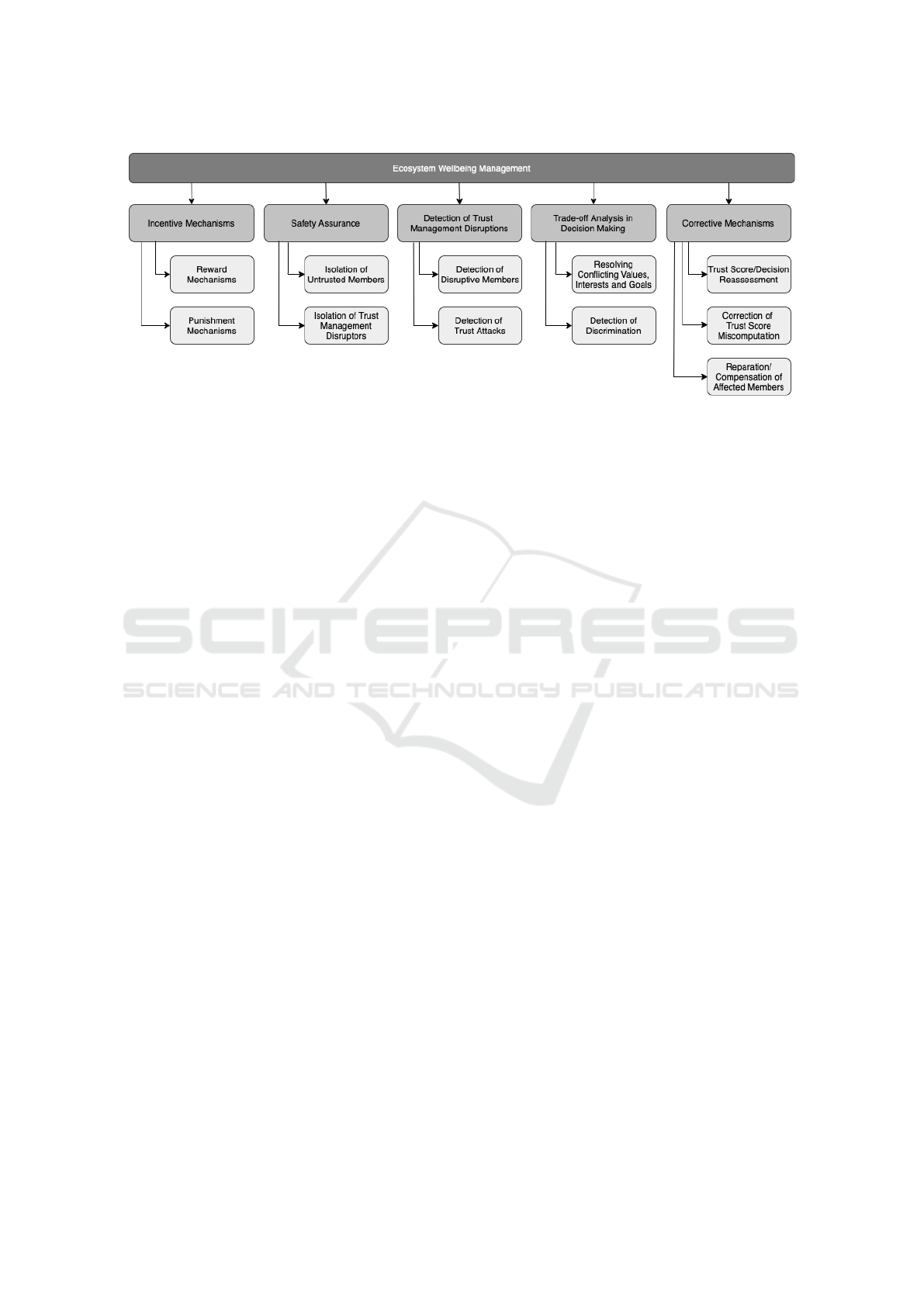
Figure 3: Taxonomy of Governance Mechanisms for Ecosystem Wellbeing Management.
vehicles, ensuring safety becomes a challenging
task. In these cases, it becomes essential to avoid
the collision by employing mechanisms of adap-
tive function restriction in order to regulate the
ability of untrusted members to cause harm (Ha-
lasz and Buhnova, 2022).
3. Detection of Trust Management Disruptions
To be able to deal with misbehaving agents, it is
first crucial to have mechanisms in place capa-
ble of identifying ongoing disruptions within the
ecosystem (Sagar et al., 2022). Detecting these
disruptions involves not only identifying mali-
cious agents as such, but also encompasses the
recognition of various trust attacks that substan-
tially undermine the fundamental pillars of the
ecosystem.
4. Corrective Mechanisms
It is essential to implement mechanisms that en-
able corrections of past trust decisions or elimi-
nations of unfairness observed in the ecosystem
in order to maintain a just and fair environment.
These mechanisms do not only include identifica-
tion and elimination of injustice such as discrim-
ination or unfairness occurring within the ecosys-
tem (e.g. newly joining agents facing issues with
earning the required trust for establishing mean-
ingful interactions), but also allow to correct trust
misjudgements (Bangui et al., 2023a) made in the
past, all by reassessing trust scores, correcting
trust score miscomputations, and providing com-
pensation to the affected agents.
5. Trade-off Analysis in Decision Making
A smart ecosystem represents a place where of-
ten the collective objectives of individual systems,
their goals, and the goals of human members in-
tersect (Tofangchi et al., 2021). Within this dy-
namic setting and all ongoing interactions, con-
flicts may arise. For instance, while the ecosystem
as a whole may prioritize efficiency, agents may
seek full control over their actions. Simultane-
ously, people may require privacy and ethical con-
siderations in their interactions with the ecosys-
tem. Effectively managing these conflicting val-
ues and finding common ground requires gover-
nance mechanisms that achieve a balance between
pursuing the goals of all involved parties. For in-
stance, trust-based trade-off analysis using incen-
tives could serve as a tool for resolving conflict-
ing values, interests, and goals within a smart dy-
namic ecosystem. Members striving toward the
ecosystem’s shared goals could be rewarded with
special tokens, which could then be replaced as a
form of currency in case a member wants to prior-
itize its own goals even if they may not align with
the goals of the ecosystem as a whole.
5 DISCUSSION
While this paper only takes the initial steps towards a
comprehensive taxonomy of governance mechanisms
for trust management in smart dynamic ecosystems,
we believe it lays a solid foundation covering the
breadth of the governance mechanisms for this chal-
lenging context, which can serve as a starting point for
the research community filling the necessary details.
5.1 Opportunities for Further Research
Building upon the initial work presented in this pa-
per, further research can focus on studying the gover-
nance of smart dynamic ecosystems in more depth,
classifying the individual mechanisms according to
more parameters and refining them to deeper levels of
ENASE 2024 - 19th International Conference on Evaluation of Novel Approaches to Software Engineering
706

categorization. Then, a possible research path is the
development of a comprehensive governance model,
systematically organizing the identified governance
mechanisms within a structured framework. Such a
model would provide a holistic understanding of the
relationships and dependencies among various gover-
nance components.
Next, there is an opportunity to explore the cre-
ation of a logical architecture that aligns with the pre-
viously mentioned governance model. Such an ar-
chitecture would facilitate the implementation of ef-
fective governance mechanisms in diverse smart dy-
namic ecosystems. The steps towards composing the
logical architecture involve the identification of the
ecosystem’s actors, defining their roles, and investi-
gating the network of the relationships among them.
The contribution of such an architecture lies in its
ability to provide the underlying structure of smart dy-
namic ecosystems, and thereby provide guidance for
the development of future governance mechanisms
tailored to these ecosystems.
Last, each of the identified governance mecha-
nisms would deserve a proper examination and re-
search of its underlying principles, especially in the
context of the governance mechanisms it shall be in-
tegrated with. Understanding these deeper levels of
detail is necessary for leading the discussion about
implementing trust management governance in terms
of both technology and policy making.
5.2 Threats to Validity
To promote the external validity of the taxonomy,
which is threatened by the possibility of overlooking
papers that could substantially impact the findings,
a proactive approach was taken to mitigate the risk.
We employed a backward snowball analysis, which
allowed us to extend our reach beyond the initially
identified papers and ensured a more comprehensive
inclusion of relevant sources. Besides, we iteratively
re-examined the identified keywords to ensure that
variations of trust governance terminology are cov-
ered.
To maximize the internal validity, which is influ-
enced by our expertise in taxonomy creation, the cor-
respondence analysis was employed, drawing on in-
sights from five reference papers (Sagar et al., 2022;
Buhnova et al., 2023; Berger et al., 2021; Ahmed
et al., 2019; Chahal et al., 2020) published in the last
four years. This methodological choice served to en-
hance the credibility of the taxonomy by aligning it
with established literature and ensuring that the dis-
tinctions made were well-founded.
6 CONCLUSION
The aim of this paper was to propose a taxonomy of
governance mechanisms desgined for trust manage-
ment in smart dynamic ecosystems. To achieve this,
we reviewed the existing literature, identified the key
governance principles and organized them in a co-
hesive structure. The proposed taxonomy serves as
a starting point for further discussion and research
within this field. Our intention is to stimulate the ex-
ploration of governance mechanisms, and fostering a
deeper understanding of the necessities and complex-
ities involved in governing trust within smart dynamic
ecosystems.
ACKNOWLEDGEMENTS
The work was supported by Grant Agency of
Masaryk University (GAMU), Interdisciplinary Re-
search Projects sub-programme, project ”Forensic
Support for Building Trust in Smart Software Ecosys-
tems” (no. MUNI/G/1142/2022).
REFERENCES
Abdelghani, W., Zayani, C. A., Amous, I., and S
`
edes, F.
(2019). Trust evaluation model for attack detection in
social internet of things. In Risks and Security of Inter-
net and Systems: 13th International Conference, CRi-
SIS 2018, Arcachon, France, October 16–18, 2018,
Revised Selected Papers 13, pages 48–64. Springer.
Ahmed, A., Abu Bakar, K., Channa, M. I., Haseeb, K., and
Khan, A. W. (2015). A survey on trust based detection
and isolation of malicious nodes in ad-hoc and sensor
networks. Frontiers of Computer Science, 9:280–296.
Ahmed, A. I. A., Ab Hamid, S. H., Gani, A., Khan, M. K.,
et al. (2019). Trust and reputation for internet of
things: Fundamentals, taxonomy, and open research
challenges. Journal of Network and Computer Appli-
cations, 145:102409.
Ahmed, K. I., Tahir, M., and Lau, S. L. (2020). Trust man-
agement for iot security: Taxonomy and future re-
search directions. In 2020 IEEE Conference on Ap-
plication, Information and Network Security (AINS),
pages 26–31. IEEE, IEEE.
Alkhabbas, F., Spalazzese, R., and Davidsson, P. (2019).
Characterizing internet of things systems through tax-
onomies: A systematic mapping study. Internet of
Things, 7:100084.
Almeida, V. A., Goh, B., and Doneda, D. (2017). A
principles-based approach to govern the iot ecosys-
tem. IEEE Internet Computing, 21(4):78–81.
Alsumayt, A., Haggerty, J., and Lotfi, A. (2017). Using
trust to detect denial of service attacks in the internet
Taxonomy of Governance Mechanisms for Trust Management In Smart Dynamic Ecosystems
707

of things over manets. International Journal of Space-
Based and Situated Computing, 7(1):43–56.
Alves, C., de Oliveira, J. A. P., and Jansen, S. (2017). Soft-
ware ecosystems governance-a systematic literature
review and research agenda. ICEIS (3), pages 215–
226.
Asiri, S. and Miri, A. (2016). An iot trust and reputation
model based on recommender systems. In 2016 14th
Annual Conference on Privacy, Security and Trust
(PST), pages 561–568. IEEE.
Atzori, L., Iera, A., Morabito, G., and Nitti, M. (2012).
The social internet of things (siot)–when social net-
works meet the internet of things: Concept, archi-
tecture and network characterization. Computer net-
works, 56(16):3594–3608.
Banerjee, M., Lee, J., Chen, Q., and Choo, K.-K. R. (2018).
Blockchain-based security layer for identification and
isolation of malicious things in iot: A conceptual de-
sign. In 2018 27th International Conference on Com-
puter Communication and Networks (ICCCN), pages
1–6. IEEE.
Bangui, H., Cioroaica, E., Ge, M., and Buhnova, B.
(2023a). Deep-learning based trust management with
self-adaptation in the internet of behavior. In Proceed-
ings of the 38th ACM/SIGAPP Symposium on Applied
Computing, pages 874–881.
Bangui, H., Ge, M., and Buhnova, B. (2023b). Deep-
learning based reputation model for indirect trust
management. Procedia Computer Science, 220:405–
412.
Bao, F. and Chen, I.-R. (2012a). Dynamic trust manage-
ment for internet of things applications. In Proceed-
ings of the 2012 international workshop on Self-aware
internet of things, pages 1–6.
Bao, F. and Chen, R. (2012b). Trust management for the
internet of things and its application to service com-
position. In 2012 IEEE international symposium on
a world of wireless, mobile and multimedia networks
(WoWMoM), pages 1–6. IEEE.
Beer, J. M., Fisk, A. D., and Rogers, W. A. (2014). Toward
a framework for levels of robot autonomy in human-
robot interaction. Journal of human-robot interaction,
3(2):74.
Berger, C., Eichhammer, P., Reiser, H. P., Domaschka, J.,
Hauck, F. J., and Habiger, G. (2021). A survey on re-
silience in the iot: Taxonomy, classification, and dis-
cussion of resilience mechanisms. ACM Computing
Surveys (CSUR), 54(7):1–39.
Bo, Z., Huan, Z., Meizi, L., Qin, Z., and Jifeng, H. (2017).
Trust traversal: a trust link detection scheme in social
network. Computer Networks, 120:105–125.
Buhnova, B. (2023). Trust management in the inter-
net of everything. In Software Architecture. ECSA
2022 Tracks and Workshops, pages 123–137, Cham.
Springer International Publishing.
Buhnova, B., Halasz, D., Iqbal, D., and Bangui, H.
(2023). Survey on trust in software engineering for
autonomous dynamic ecosystems. In Proceedings of
the 38th ACM/SIGAPP Symposium on Applied Com-
puting, pages 1490–1497.
Caminha, J., Perkusich, A., and Perkusich, M. (2018). A
smart trust management method to detect on-off at-
tacks in the internet of things. Security and Commu-
nication Networks, 2018.
Capilla, R., Cioroaica, E., Buhnova, B., and Bosch, J.
(2021). On autonomous dynamic software ecosys-
tems. IEEE Transactions on Engineering Manage-
ment, 69(6):3633–3647.
Chahal, R. K., Kumar, N., and Batra, S. (2020). Trust
management in social internet of things: A taxonomy,
open issues, and challenges. Computer Communica-
tions, 150:13–46.
Chen, R., Bao, F., and Guo, J. (2015). Trust-based ser-
vice management for social internet of things systems.
IEEE transactions on dependable and secure comput-
ing, 13(6):684–696.
Chen, R., Guo, J., and Bao, F. (2014). Trust management
for soa-based iot and its application to service com-
position. IEEE Transactions on Services Computing,
9(3):482–495.
Clarke, S., Christianson, B., and Xiao, H. (2013). Trust*:
Using local guarantees to extend the reach of trust.
In Security Protocols XVII: 17th International Work-
shop, Cambridge, UK, April 1-3, 2009. Revised Se-
lected Papers 17, pages 171–178. Springer.
Etalle, S., den Hartog, J., and Marsh, S. (2007). Trust and
punishment. In 1st International ICST Conference on
Autonomic Computing and Communication Systems.
Gerber, A. and Kansal, S. (2020). Simplify the de-
velopment of your iot solutions with iot architec-
tures. IBM. Accessed online: 6 December 2023.
Available from: https://developer.ibm.com/articles/
iot-lp201-iot-architectures/.
Ghafari, S. M., Beheshti, A., Joshi, A., Paris, C., Mahmood,
A., Yakhchi, S., and Orgun, M. A. (2020). A survey
on trust prediction in online social networks. IEEE
Access, 8:144292–144309.
Guo, L., Yang, H., Luan, K., Luo, Y., Sun, L., and Zheng,
X. (2021). A trust management model based on mu-
tual trust and a reward-with-punishment mechanism
for cloud environments. Concurrency and Computa-
tion: Practice and Experience, 33(16):e6283.
Gwak, B., Son, H., Kang, J., and Lee, D. (2017). Iot
trust estimation in an unknown place using the opin-
ions of i-sharing friends. In 2017 IEEE Trust-
com/BigDataSE/ICESS, pages 602–609. IEEE.
Halasz, D. and Buhnova, B. (2022). Rethinking safety in
autonomous ecosystems. In IEEE 17th Conference
on Computer Science and Intelligence Systems, pages
81–87.
Hategekimana, F., Whitaker, T. J., Pantho, M. J. H., and
Bobda, C. (2020). Iot device security through dy-
namic hardware isolation with cloud-based update.
Journal of Systems Architecture, 109:101827.
He, Y., Han, G., Jiang, J., Wang, H., and Martinez-Garcia,
M. (2020). A trust update mechanism based on re-
inforcement learning in underwater acoustic sensor
networks. IEEE Transactions on Mobile Computing,
21(3):811–821.
ENASE 2024 - 19th International Conference on Evaluation of Novel Approaches to Software Engineering
708

Hou, F. and Jansen, S. (2023). A systematic literature re-
view on trust in the software ecosystem. Empirical
Software Engineering, 28(1):8.
Illi, E., Qaraqe, M., Althunibat, S., Alhasanat, A., Alsafas-
feh, M., de Ree, M., Mantas, G., Rodriguez, J., Aman,
W., and Al-Kuwari, S. (2023). Physical layer security
for authentication, confidentiality, and malicious node
detection: a paradigm shift in securing iot networks.
IEEE Communications Surveys & Tutorials.
Iqbal, D. and Buhnova, B. (2022). Model-based approach
for building trust in autonomous drones through digi-
tal twins. In 2022 IEEE International Conference on
Systems, Man, and Cybernetics (SMC), pages 656–
662. IEEE.
Jafarian, B., Yazdani, N., and Haghighi, M. S. (2020).
Discrimination-aware trust management for social in-
ternet of things. Computer Networks, 178:107254.
Jøsang, A., Ismail, R., and Boyd, C. (2007). A survey of
trust and reputation systems for online service provi-
sion. Decision support systems, 43(2):618–644.
Kamvar, S. D., Schlosser, M. T., and Garcia-Molina, H.
(2003). The eigentrust algorithm for reputation man-
agement in p2p networks. In Proceedings of the 12th
international conference on World Wide Web, pages
640–651.
Karthik, N. and Ananthanarayana, V. (2017). A hybrid trust
management scheme for wireless sensor networks.
Wireless Personal Communications, 97:5137–5170.
Katina, P. F. and Keating, C. B. (2018). Cyber-physical sys-
tems governance: a framework for (meta) cybersecu-
rity design. Security by Design: Innovative Perspec-
tives on Complex Problems, pages 137–169.
Katina, P. F., Keating, C. B., Gheorghe, A. V., and Masera,
M. (2017). Complex system governance for critical
cyber-physical systems. International Journal of Crit-
ical Infrastructures, 13(2-3):168–183.
Khan, M. S., Midi, D., Khan, M. I., and Bertino, E. (2015).
Adaptive trust update frequency in manets. In 2015
IEEE 21st International Conference on Parallel and
Distributed Systems (ICPADS), pages 132–139. IEEE.
Khan, W. Z., Hakak, S., Khan, M. K., et al. (2020). Trust
management in social internet of things: Architec-
tures, recent advancements, and future challenges.
IEEE Internet of Things Journal, 8(10):7768–7788.
Khatun, M. A., Chowdhury, N., and Uddin, M. N. (2019).
Malicious nodes detection based on artificial neural
network in iot environments. In 2019 22nd Inter-
national Conference on Computer and Information
Technology (ICCIT), pages 1–6. IEEE.
K
¨
okciyan, N. and Yolum, P. (2020). Turp: Managing trust
for regulating privacy in internet of things. IEEE In-
ternet Computing, 24(6):9–16.
Li, B., Ye, R., Gu, G., Liang, R., Liu, W., and Cai, K.
(2020). A detection mechanism on malicious nodes
in iot. Computer Communications, 151:51–59.
Liu, L., Ma, Z., and Meng, W. (2019). Detec-
tion of multiple-mix-attack malicious nodes using
perceptron-based trust in iot networks. Future gen-
eration computer systems, 101:865–879.
Liu, Z., Yang, D.-s., Wen, D., Zhang, W.-m., and Mao, W.
(2011). Cyber-physical-social systems for command
and control. IEEE Intelligent Systems, 26(4):92–96.
Lochner, M. and Smilek, D. (2023). The uncertain advi-
sor: trust, accuracy, and self-correction in an auto-
mated decision support system. Cognitive Processing,
24(1):95–106.
Magdich, R., Jemal, H., Nakti, C., and Ayed, M. B.
(2021). An efficient trust related attack detection
model based on machine learning for social internet
of things. In 2021 International Wireless Communica-
tions and Mobile Computing (IWCMC), pages 1465–
1470. IEEE.
Mahmood, A., Butler, B., Zhang, W. E., Sheng, Q. Z.,
and Siddiqui, S. A. (2019). A hybrid trust manage-
ment heuristic for vanets. In 2019 IEEE International
Conference on Pervasive Computing and Communi-
cations Workshops (PerCom Workshops), pages 748–
752. IEEE.
Malik, S., Dedeoglu, V., Kanhere, S. S., and Jurdak, R.
(2019). Trustchain: Trust management in blockchain
and iot supported supply chains. In 2019 IEEE In-
ternational Conference on Blockchain (Blockchain),
pages 184–193. IEEE.
Marche, C. and Nitti, M. (2020). Trust-related attacks and
their detection: A trust management model for the so-
cial iot. IEEE Transactions on Network and Service
Management, 18(3):3297–3308.
Masmoudi, M., Abdelghani, W., Amous, I., and S
`
edes, F.
(2020). Deep learning for trust-related attacks de-
tection in social internet of things. In Advances in
E-Business Engineering for Ubiquitous Computing:
Proceedings of the 16th International Conference on
e-Business Engineering (ICEBE 2019), pages 389–
404. Springer.
Mechanic, D. (1996). The logic and limits of trust. Con-
temporary Sociology, 25(4):455.
Meena Kowshalya, A. and Valarmathi, M. (2017). Trust
management for reliable decision making among so-
cial objects in the social internet of things. IET Net-
works, 6(4):75–80.
Mehdizadeh, N. and Farzaneh, N. (2022). An evidence
theory based approach in detecting malicious con-
troller in the multi-controller software-defined inter-
net of things network. Adhoc & Sensor Wireless Net-
works, 51(4).
Mendoza, C. V. and Kleinschmidt, J. H. (2015). Mit-
igating on-off attacks in the internet of things us-
ing a distributed trust management scheme. In-
ternational Journal of Distributed Sensor Networks,
11(11):859731.
Muzammal, S. M., Murugesan, R. K., and Jhanjhi, N. Z.
(2020). A comprehensive review on secure routing
in internet of things: Mitigation methods and trust-
based approaches. IEEE Internet of Things Journal,
8(6):4186–4210.
Namal, S., Gamaarachchi, H., MyoungLee, G., and Um,
T.-W. (2015). Autonomic trust management in cloud-
based and highly dynamic iot applications. In 2015
ITU Kaleidoscope: Trust in the Information Society
(K-2015), pages 1–8. IEEE.
Taxonomy of Governance Mechanisms for Trust Management In Smart Dynamic Ecosystems
709

Nandhini, P., Kuppuswami, S., Malliga, S., and DeviPriya,
R. (2022). A lightweight energy-efficient algorithm
for mitigation and isolation of internal rank attackers
in rpl based internet of things. Computer Networks,
218:109391.
Nitti, M., Girau, R., and Atzori, L. (2013). Trustwor-
thiness management in the social internet of things.
IEEE Transactions on knowledge and data engineer-
ing, 26(5):1253–1266.
Nwebonyi, F. N., Martins, R., and Correia, M. E. (2019).
Security and fairness in iot based e-health system:
A case study of mobile edge-clouds. In 2019 Inter-
national Conference on Wireless and Mobile Com-
puting, Networking and Communications (WiMob),
pages 318–323. IEEE.
Peng, S., He, J., and Meng, Y. (2008). Reputation-based
trust update in network environment. In 2008 Interna-
tional Symposium on Electronic Commerce and Secu-
rity, pages 118–123. IEEE.
Rana, K., Singh, A. V., and Vijaya, P. (2022). Recent trust
management models for secure iot ecosystem. Inter-
national Journal of Intelligent Systems and Applica-
tions in Engineering, 10(1s):23–33.
Resnick, P., Kuwabara, K., Zeckhauser, R., and Friedman,
E. (2000). Reputation systems. Communications of
the ACM, 43(12):45–48.
Rizvi, S., Kurtz, A., Pfeffer, J., and Rizvi, M. (2018). Se-
curing the internet of things (iot): A security taxon-
omy for iot. In 2018 17th IEEE International Con-
ference On Trust, Security And Privacy In Computing
And Communications/12th IEEE International Con-
ference On Big Data Science And Engineering (Trust-
Com/BigDataSE), pages 163–168. IEEE.
Roopa, M., Pattar, S., Buyya, R., Venugopal, K. R., Iyen-
gar, S., and Patnaik, L. (2019). Social internet of
things (siot): Foundations, thrust areas, systematic re-
view and future directions. Computer Communica-
tions, 139:32–57.
Sagar, S., Mahmood, A., Sheng, Q. Z., Pabani, J. K., and
Zhang, W. E. (2022). Understanding the trustworthi-
ness management in the social internet of things: a
survey. arXiv preprint arXiv:2202.03624.
Schreieck, M., Wiesche, M., and Krcmar, H. (2016). Design
and governance of platform ecosystems-key concepts
and issues for future research. In Ecis, volume 16,
pages 12–15.
Seshadri, S. S., Rodriguez, D., Subedi, M., Choo, K.-K. R.,
Ahmed, S., Chen, Q., and Lee, J. (2020). Iotcop:
A blockchain-based monitoring framework for detec-
tion and isolation of malicious devices in internet-
of-things systems. IEEE Internet of Things Journal,
8(5):3346–3359.
She, W., Liu, Q., Tian, Z., Chen, J.-S., Wang, B., and Liu,
W. (2019). Blockchain trust model for malicious node
detection in wireless sensor networks. IEEE Access,
7:38947–38956.
Singh, M. and Kim, S. (2018). Trust bit: Reward-based in-
telligent vehicle commination using blockchain paper.
In 2018 IEEE 4th World Forum on Internet of Things
(WF-IoT), pages 62–67. IEEE.
Tofangchi, S., Hanelt, A., Marz, D., and Kolbe, L. M.
(2021). Handling the efficiency–personalization
trade-off in service robotics: A machine-learning ap-
proach. Journal of Management Information Systems,
38(1):246–276.
Truong, N. B., Um, T.-W., Zhou, B., and Lee, G. M. (2017).
From personal experience to global reputation for trust
evaluation in the social internet of things. In GLOBE-
COM 2017-2017 IEEE Global Communications Con-
ference, pages 1–7. IEEE.
Usman, M., Britto, R., B
¨
orstler, J., and Mendes, E. (2017).
Taxonomies in software engineering: A systematic
mapping study and a revised taxonomy develop-
ment method. Information and Software Technology,
85:43–59.
Wang, F. and Wei, Z. (2021). A statistical trust for detecting
malicious nodes in iot sensor networks. IEICE Trans-
actions on Fundamentals of Electronics, Communica-
tions and Computer Sciences, 104(8):1084–1087.
Williams, P., Rojas, P., and Bayoumi, M. (2019). Security
taxonomy in iot–a survey. In 2019 IEEE 62nd Inter-
national Midwest Symposium on Circuits and Systems
(MWSCAS), pages 560–565. IEEE.
Xia, F. and Ma, J. (2011). Building smart communities with
cyber-physical systems. In Proceedings of 1st interna-
tional symposium on From digital footprints to social
and community intelligence, pages 1–6.
Xiao, H., Sidhu, N., and Christianson, B. (2015). Guaran-
tor and reputation based trust model for social internet
of things. In 2015 International wireless communi-
cations and mobile computing conference (IWCMC),
pages 600–605. IEEE.
Xiaoxue, M., Zixian, W., Jing, B., and Fei, L. (2010). Trust
model based on rewards and punishment mechanism.
In 2010 Second International Workshop on Education
Technology and Computer Science, volume 2, pages
182–185. IEEE.
Yan, Z., Ding, W., Niemi, V., and Vasilakos, A. V. (2016).
Two schemes of privacy-preserving trust evaluation.
Future Generation Computer Systems, 62:175–189.
Yu, Y., Jia, Z., Tao, W., Xue, B., and Lee, C. (2017). An effi-
cient trust evaluation scheme for node behavior detec-
tion in the internet of things. Wireless Personal Com-
munications, 93:571–587.
Zavvos, E., Gerding, E. H., Yazdanpanah, V., Maple, C.,
Stein, S., et al. (2021). Privacy and trust in the in-
ternet of vehicles. IEEE Transactions on Intelligent
Transportation Systems, 23(8):10126–10141.
Zhaofeng, M., Lingyun, W., Xiaochang, W., Zhen, W., and
Weizhe, Z. (2019). Blockchain-enabled decentralized
trust management and secure usage control of iot big
data. IEEE Internet of Things Journal, 7(5):4000–
4015.
ENASE 2024 - 19th International Conference on Evaluation of Novel Approaches to Software Engineering
710
