
Verifying Artifact Authenticity with Unclonable Optical Tags
M
´
onica P. Arenas
a
, Gabriele Lenzini
b
, Mohammadamin Rakeei
c
,
Peter Y. A. Ryan
d
, Marjan
ˇ
Skrobot
e
and Maria Zhekova
SnT, University of Luxembourg, Esch-sur-Alzette, Luxembourg
Keywords:
Authenticity Verification Protocol, Authentication, Integrity, Provenance, Robustness, Formal Methods.
Abstract:
We study the challenge of authenticating objects. This problem is relevant when buyers need proof that a
purchase is authentic and not fake. Typically, manufacturers watermark their goods, give them IDs, and
provide a certificate of authenticity. Buyers, for their part, check the IDs and verify the certificate. However,
even if manufacturers are honest online registration and verification are vulnerable to hacking; servers can
leak private data; goods out-for-delivery can have the ID cloned and can be replaced with imitations. We
propose a cyber-physical solution that combines physical properties and cryptographic protocols and that
is robust against a curious registry server and attempts to physical manipulation. Security depends on two
elements: (I) a material inseparably joined with an object from which we can generate digital identities and
other cryptographic tokens; (ii) two novel cryptographic protocols that ensure data and object integrity and
authentication of agents and objects. Besides, we show that a material with all the desired security properties
exists. We can use it to coat objects, and it has optical properties, such as unclonability, from which we can
build secure cryptographic protocols. We formally prove our security claims with Proverif.
1 INTRODUCTION
Combating the counterfeiting of goods protects con-
sumers from potential harm caused by substan-
dard products, preserves the reputation of legitimate
brands, and mitigates economic losses due to parallel
markets for falsified goods.
While a robust supply chain is undeniably crucial,
equally important is to guarantee the integrity of prod-
ucts throughout their journey from manufacturers to
end-users and prevent unauthorized alterations at var-
ious points along the chain. This could be obtained
if the product, with all its features, were inimitable.
As this is a hard requirement, standard solutions ex-
ist to add marks and seals that, themselves, cannot
be reproduced or moved around easily. For example,
watermarking Huang and Wu (2007) is a widely used
practice that falls into this category. The security is
then delegated to the technology used to produce the
markings and on how hard it is to copy them with ac-
ceptable quality to fool a verifier (e.g., a human with
a
https://orcid.org/0000-0003-0221-5032
b
https://orcid.org/0000-0001-8229-3270
c
https://orcid.org/0000-0002-0015-7978
d
https://orcid.org/0000-0002-1677-9034
e
https://orcid.org/0000-0002-7132-7591
an ultraviolet lamp).
This work combines such an idea with a digital
cryptographic solution. It also assumes that objects
can be paired with tags possessing physically unclon-
able features. These features are unpredictable until
one extracts and processes them to create unique IDs.
Materials with peculiar unclonable and noisy fea-
tures are referred to as Physical Unclonable Functions
(PUFs) McGrath et al. (2019); Pappu et al. (2002).
Objects of this kind are considered sources of “ran-
domness”: natural randomness, if the object inher-
ently possesses it by nature, or artificial randomness
if the randomness is created on purpose and asso-
ciated with the object Voloshynovskiy et al. (2016).
Finding PUF-like features on an object is uncommon
McGrath et al. (2019), and where they exist, they are
very object-specific and non-transferable.
Our solution stems from recent research showing
that there is a material that is an optical PUF and that
can be used to coat objects like a varnish Schwartz
et al. (2021): thus, it is realistic to assume that ob-
jects can be enriched with natural “randomness” by
being coated. However, the problem is ensuring the
extraction of cryptographically secure IDs from nat-
ural “randomness” and guaranteeing that objects and
coats remain physically and digitally entangled.
64
Arenas, M., Lenzini, G., Rakeei, M., Ryan, P., Škrobot, M. and Zhekova, M.
Verifying Artifact Authenticity with Unclonable Optical Tags.
DOI: 10.5220/0012746500003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 64-77
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

Object Authentication Workflow and Its Weak-
nesses. The authentication of objects with natural
randomness requires two processes: enrollment and
authentication Gao et al. (2018); Tuyls et al. (2005);
Wen and Liu (2018). Enrollment happens before the
object leaves the manufacturer. Its intrinsic features
are acquired and processed, possibly to inject ran-
domness to produce unpredictable IDs together with
some helper data that will help retrieve exactly those
IDs (the re-acquisition is a process with noise, see
later). IDs and helpers are stored. Authentication is
run when the object is in the hands of the consumer.
Its intrinsic features are reacquired and re-processed.
The helper data enables the removal of noise and the
reconstruction of secret information. If the object is
authentic, this ID will match exactly that stored in the
database.
However, IDs and helpers must be processed,
stored, and exchanged and can then be stolen, leaked,
or manipulated. Additionally, when an object is in
transit for delivery, it becomes vulnerable: it can be
substituted with a less valuable imitation or it can
have some parts (e.g., the coat or tag) tampered with.
To ensure the integrity of the product and thwart any
attempts to defeat the authentication phase, stringent
measures must be put in place to protect against all
sorts of digital and physical manipulation.
1.1 Our Contribution
Our contribution is manifold: (i) we propose two pro-
tocols, one for enrollment and one for authentication.
They are secure against attackers that can tamper with
both the physical object and, as a Dolev-Yao active
adversary Dolev and Yao (1983), the execution of the
digital protocols. (ii) We prove our security claims
by model checking, and we use ProVerif Blanchet
(2001) for this purpose. (iii) We suggest an archi-
tecture and spell out how to deploy both protocols
in a real scenario. (iv) We prototype the protocols in
Python and benchmark them for robustness and reli-
ability by experimentally measuring acceptance and
rejection rates on a large dataset of PUF-like samples.
We also claim that our solution rests on a set of
realistic assumptions and it is user-friendly. In par-
ticular, the enrollment and authentication protocols
run with a trusted device manager and an honest-but-
curious registry server; the protocols require little ex-
pertise from users, simply the ability to take pictures;
the cryptographic operations are carried out by a de-
vice manager for both the enrolment and authentica-
tion phases.
The security of our protocols relies on the pres-
ence of two key elements: (i) a secure physical tag,
which is integrated into the object i.e., inseparably
bound to it, and (ii) two procedures used to extract a
robust and secure fingerprint from this tag. This fin-
gerprint represents the digital identity of the object;
which is used on cryptographic primitives together
with formal proofs to ensure secure enrollment and
authentication.
A further innovative aspect of our solution is
that it builds on previous research, enabling us to
demonstrate that a material satisfying the assump-
tions does indeed exist. Specifically, a material called
Cholesteric Spherical Reflectors (CSRs) Geng et al.
(2017); Noh et al. (2014); Schwartz et al. (2018) can
be used to coat objects giving them unclonable and
unique optical features that can be scanned with a
microscope connected to a camera. Existing work
shows that real CSR-made tags are robust and reli-
able Arenas et al. (2021, 2022a). Robust as a specific
query accepts any optical response of the same tag
despite the inevitable presence of noise and, reliable
since the system must reject any image from any other
tag. Other existing works show that uniqueness and
unpredictability of random sources can be corrected
through an error correction process based on secure
fuzzy extractors Boyen (2004); Canetti et al. (2021);
Dodis et al. (2004); Li et al. (2006).
2 RELATED WORK AND
BACKGROUND
Reliable artifact authentication poses a formidable
challenge across diverse domains, including but not
limited to luxury goods, Internet of Things (IoT) de-
vices, and more. When it comes to the protection
of goods, companies actively engage in research ef-
forts aimed at developing robust anti-counterfeiting
measures and comprehensive traceability solutions
throughout the supply chain Choi et al. (2013); Nam
et al. (2016). Different technologies such as RFID
tags and QR-codes have been devised to establish
connections between physical artifacts and their cor-
responding digital counterparts Anandhi et al. (2020);
Marktscheffel et al. (2016); Maurya and Bagchi
(2018). However, these solutions fall short in im-
portant requirements, such as unclonability and tam-
per evidence. As an alternative, PUFs have gained
prominence due to their inherent attributes of physi-
cal randomness, uniqueness, and resistance to an at-
tacker’s attempts to predict the response generated by
a challenge Gassend et al. (2002); Pappu et al. (2002).
Many solutions exploit these properties for key gen-
eration and authentication protocols Armknecht et al.
(2009); Herder et al. (2014); Suh and Devadas (2007).
Verifying Artifact Authenticity with Unclonable Optical Tags
65

The literature suggests developing secure authen-
tication protocols from fuzzy responses and convert-
ing them into stable keys to perform the verification
process Dodis et al. (2006, 2004). Such authentica-
tion protocols typically involve a sequence of steps,
such as: (i) minutiæ extraction via signal/image pro-
cessing Li et al. (2017); Tuyls and Goseling (2004),
(ii) error correction algorithms through robust meth-
ods (e.g., robust secure sketches), (iii) and, the deriva-
tion of secret information from stable responses (e.g.,
fuzzy extractors).
The entire process of obtaining a stabilized bit-
string and cryptographic keys must be implemented
in both phases: the enrollment and the authentica-
tion. The vendor must ensure reliable enrollment
and secure communication across different channels
to engender users’ trust in the products to be verified.
Despite all the efforts in using security tokens with
unique properties, designing secure protocols is not
easy to achieve as malicious entities may find inge-
nious ways to attack the systems.
2.1 Secure Building Blocks
The main cryptographic primitives we use to build
our authenticity verification protocol include robust
secure sketches and robust fuzzy extractors, as well as
hash functions and digital signatures. Pairing robust
secure sketches and fuzzy extractors yields a power-
ful error-correction process to enhance the reliability
and security of identification and authentication pro-
tocols that rely on noisy sources. Such noisy sources
may include biometric information (e.g., fingerprint
and iris data), or in a more general context, objects
that possess fingerprint-like attributes (e.g., PUFs and
CSRs).
More concretely, a robust secure sketch is a mech-
anism that allows for the reconstruction of binary
strings, despite the presence of noise. However, the
bitstrings produced by the secure sketch algorithm are
not uniformly distributed and hence they do not pos-
sess the necessary security requirements to be used
in the context of cryptographic applications. For this
purpose, a robust fuzzy extractor is used. A robust
fuzzy extractor is a provably secure mechanism to
generate error-tolerant, uniformly distributed random
bitstrings, such as cryptographic keys and tokens,
from correlated and usually noisy sources.
In particular, during the generation step, a read-
ing of a noisy source is used to generate a random
(secret) bitstring and some public data called helper
data. At a later stage, a second, usually noisy, read-
ing of the same source is used in conjunction with
the helper data to reproduce the same secret. Robust
fuzzy extractors guarantee that: 1. the helper data re-
veals no information about the derived secret, 2. the
same secret can be reproduced, as long as the differ-
ence (noise) between the two readings is smaller than
a pre-defined threshold δ and, 3. any deliberate modi-
fication of the helper data by a malicious actor will be
detected. Robust fuzzy extractors utilize robust secure
sketches to reliably reproduce secret values and hence
we briefly describe both primitives below in more de-
tail. Digital signatures and hash functions are used
to achieve authentication of participating entities in a
scenario where both symmetric and asymmetric se-
tups (e.g., via Public Key Infrastructure) are assumed.
2.1.1 Robust Secure Sketch
A secure sketch is, in essence, an error correction
technique. It consists of pair of procedures (SS, Rec)
Dodis et al. (2004), standing respectively for sketch
construction and reconstruction. A secure sketch as-
sumes the existence of a function that processes n dif-
ferent takes of the same noisy source and outputs a
single vector ω of k integer coordinates. Denoted as:
ω ← ImgProcess([take]
1
,...,[take]
n
).
The SS algorithm inputs a vector ω and returns a vec-
tor of k integer elements s, called the sketch. The
sketch is used in the function Rec to reconstruct the
exact same ω from a noisy version of the input, say ω
′
,
if and only if the difference between them is bounded
by a threshold δ. Rec should produce something un-
related to ω otherwise.
Boyen et al. Boyen et al. (2005) proposed a ro-
bust secure sketch scheme (RobustSS, RobustRec),
designed to resist tampering attempts on the sketch
vector s, in which the RobustSS algorithm also com-
putes the digest h of the robust template, yielding as
outputs h together with s. Denoted by:
(s,h) ← RobustSS(ω)
This allows one to verify in the reconstruction algo-
rithm RobustRec, whether the sketch s has been de-
liberately modified, by recomputing the digest and
checking whether it matches with the digest value
computed in the RobustSS function. We describe the
reconstruction process by
ω/⊥ ← RobustRec(ω
′
,s,h).
2.1.2 Robust Fuzzy Extractor
A robust fuzzy extractor is composed of a pair of
randomized functions (RobustGen,RobustRep). The
Generate procedure RobustGen requires as input a ro-
bust template ω. This functions triggers the robust se-
cure sketch RobustSS(ω) to generate a sketch s and
SECRYPT 2024 - 21st International Conference on Security and Cryptography
66

a digest h. The output of the RobustGen function is
a random secret string R and the public helper data
P = (s,h,r), where r is a random value. We write this
as:
(R,P) ← RobustGen(ω).
On the other hand, the Reproduce function
RobustRep takes as inputs a potentially different
(noisy) robust template ω
′
and P and reproduces the
secret R
′
, using internally the RobustRec function of
the secure sketch scheme. In other words:
R
′
← RobustRep(ω
′
,P)
The two values R and R
′
will match if and only if
the distance between ω and ω
′
are within a threshold
δ. A fuzzy extractor scheme allows obtaining non-
reversible bitstrings, which can be used as a seed to
generate cryptographic keys in either symmetric or
asymmetric setup Boyen et al. (2005); Shariati et al.
(2012).
3 ARCHITECTURE AND
THREAT MODEL
We will start by describing the overall architecture of
the artifact authenticity service, and then describe a
suitable threat model and discuss some of the poten-
tial attacks.
3.1 Authenticity Service and
Functionality
As we aim at an architecture for artifact authentic-
ity, we need to guarantee security, efficiency, scala-
bility, and reliability by proposing a system involv-
ing three primary entities ––with different security as-
sumptions: a vendor (or a manufacturer), a registry
server, and a user.
The process begins with a vendor. Once sub-
scribed to a service (referred to as a legitimate ven-
dor), the vendor is allowed to register artifacts along
with specific identifying features (some of which
must be unique). Note that artifact authenticity ser-
vice may be established for a single vendor or may
serve a consortium of vendors and manufacturers.
A registry server holds access to a database that
stores artifact records. These records encompass a
unique identifier (e.g., serial numbers, QR-codes),
registering vendor data (e.g., vendor ID, enrolment
signature), verification data, and potentially textual
description of specific identifying features (dimen-
sions, color, weight, defects, etc.) and/or video
records of the registered artifact. The database may
be instantiated using a decentralized private or con-
sortium ledger, ensuring transparency and integrity of
the authenticity verification process. Each legitimate
vendor must register an artifact through an enrollment
procedure, which can be a simple software solution or
might involve specialized hardware for added security
and efficacy.
Finally, a user interacts with the authenticity ver-
ification system via an object authentication protocol
intending to verify the authenticity of a given object.
Similarly to the enrolment procedure, authentication
may involve specific hardware solutions. We should
keep protocol efficient and with very few message
rounds for all protocol entities. This is necessary as
the artifact authenticity service should be able to han-
dle large volumes of objects, users, and vendors.
3.2 Our Threat Model
We consider five distinct threat models: 1) a mali-
cious vendor aiming to poison the record database;
2) a user attempting to trick the authentication proto-
col into returning “authenticated” when an object is
fake; 3) an honest-but-curious server whose aims to
learn as much information as possible about underly-
ing secret values used to accommodate verification;
4) any malicious entity with physical access to an ob-
ject (during the lifetime of the object) to tamper with
a physical tag embedded in the object. This includes
malicious vendors, users, or anyone else who interacts
with the object; 5) any other external attacker.
The primary objective of a malicious vendor may
be to exploit the authenticity service by register-
ing counterfeit items to obtain financial gain. An-
other objective of such an attacker may involve com-
pletely disrupting the authenticity service by compro-
mising its reliability and robustness. Therefore, the
authenticity service should implement robust authen-
tication mechanisms to prevent unauthorized enroll-
ments. Conversely, a malicious vendor may seek to
undermine a competing vendor (or manufacturer) by
impersonating them and attempting to register an item
of inferior quality as genuine. To thwart such attacks,
non-repudiation, and accountability of the enrollment
procedure must be ensured. A malicious user may
act as a seller intending to deceive a buyer into pur-
chasing a counterfeit object. Another potential attack
that the user can launch is to downgrade the value of
the object to conceal its true worth. Physical secu-
rity measures must be implemented to guard against
tampering and provide evidence of interference. Suc-
cessful tampering would enable a malicious vendor or
user to easily accomplish their objectives. Finally, an
honest-but-curious server may be compromised and
Verifying Artifact Authenticity with Unclonable Optical Tags
67

exploited to launch one of the aforementioned attacks.
Looking ahead, to reduce attack surfaces and sim-
plify the security model we introduce a trusted entity
referred to as a device manager (that can be imple-
mented as a hardware solution) acting as a bridge be-
tween vendors or users on one side and the registry
server on the other. Considering these potential at-
tacks, we formally modelled and analyzed our proto-
col in Section 5.
4 OBJECT AUTHENTICATION
PROTOCOL
Our full process for object authentication consists of
two protocols: enrollment and authentication. The
reference data from a physical object is collected dur-
ing the enrollment and the authentication is deter-
mined whether a queried response aligns with the en-
rolled reference data. We start with the assumptions
defining the context where the protocols work.
4.1 Security Assumptions
The security of our authentication protocols relies on
certain assumptions about the objects intended for au-
thentication. As anticipated in Section 1, we work
with objects with artificial randomness that is, objects
that are physically bonded with “seals” that possess
qualities typical of an optical PUF, such as random-
ness, uniqueness, and tamper evidence.
That said, we will have to assume the existence of
several reliable and secure procedures. Given a set of
possible magnified images of an object’s seal, which
we indicate with [seal]
1
,...,[seal]
n
, we assume that
by image processing is possible to generate a unique
identifying-the-object bitstring of fixed length ω de-
spite physical and digital “noise”. This processing is
abstractly represented by the ImgProcess function.
Besides, we assume two functions, RobustGen
and RobustRep, that satisfy security properties com-
ing from a fuzzy extractor scheme, as described in
Section 2.1. Here, (R,P) represent the private and
public bitstrings, respectively, generated by applying
the robust fuzzy extractor function RobustGen to ω. R
should be reliably reconstructed if and only if we pro-
cess another set of images {[seal
′
]
i
}
i∈I
taken from
the same object’s seal. Here, “reliably” means despite
the inevitable noise in the new images, a noise usually
due to environmental conditions, such as alignment,
background lights, and other distortion, and noise due
to the device manager used to take pictures.
In a nutshell, the processing of this set of new im-
ages results in a new identifying-the-object bitstring
ω
′
, which in turn generates a new secret bitstring R
′
through the RobustRep function. The process of ver-
ifying the authenticity of the object is equivalent to
checking whether the reproduced R
′
matches the ini-
tial secret bitstring R, which solely relies on how close
ω and ω
′
are with respect to a certain metric. How-
ever, because R and R
′
are private data, they cannot
be directly compared and therefore, we use their cor-
responding digests for comparison. Formally, this re-
quirement can be expressed as follows:
(R,P) ← RobustGen(ω) and
R
′
← RobustRep(ω
′
,P)
then we have:
Hash(R) = Hash(R
′
) iff dist
ω,ω
′
≤ δ (1)
where dist is a distance over the (metric) vector space
of the range of ImgProcess, and δ is the tolerated
bounded error. The chosen metric space is the Cheby-
shev distance, where dist(ω, ω
′
) = max
i
{|ω
i
− ω
′
i
|}.
Property (1) should not be satisfied when ImgProcess
is applied to a set of images taken from anything else
that is not the seal that was used to generate the ini-
tial (R,P) pair.
Satisfying property (1), requires carefully de-
signed and crafted ImgProcess, RobustGen, and
RobustRep functions that require to be theoretically
specified and experimentally tuned to work with real
objects.
That stated, we also assume that our “seal” is
physically unclonable whereas the bond object-seal
is tamper-evident: it cannot be broken without com-
promising the integrity of the seal and in particular
the validity of property (1). In the remainder, we as-
sume the availability of such seals and of functions
ImgProcess, RobustGen, and RobustRep that satisfy
property (1).
4.2 Feasibility of the Assumptions
Although this paper primarily discusses the secu-
rity analysis of an object authentication protocol, we
briefly describe a use-case material that presents un-
clonable properties. This material is based on liq-
uid crystals, which are commonly found under the
screens of our electronic devices. Once liquid crystals
are molded in a spherical shape, they are referred to
as CSRs. When mixed with a polymer, one can create
a thin varnish-like spot-shaped layer over an object.
The layer cannot be removed (e.g., be scratched out)
without ruining the internal crystalline structure of the
CSRs. In addition to being non-removable, CSRs ex-
hibit optical properties that depend on structural vari-
ations inherent to the manufacturing process, such
SECRYPT 2024 - 21st International Conference on Security and Cryptography
68

seal
859f01f4c10bbbb403
ID
seal
Figure 1: An illustrative example of an artifact, a CSR tag and its ID. In reality, the tag should be applied on the back of the
canvas. The magnified part shows the pattern observable from the illuminated CSR. It consists of small green dots. Their
exact position, color, and number are unpredictable before the first observation.
as diameter, thickness, color, and relative arrange-
ment Geng et al. (2017, 2016); Schwartz et al. (2018).
The interactions between the incident light and CSR
arrays render colourful patterns (see Figure 1) that
depend on the properties of CSRs, the lighting, and
read-out conditions. CSRs have intrinsic unclonable
properties, making them useful in security applica-
tions, including object authentication, anti-counterfeit
technologies, autonomous mobile robots, among oth-
ers Arenas et al. (2022b); Schwartz et al. (2021).
Thus, we assume to use “seals” made of CSRs
which we can apply to objects, as shown in Figure
1. The figure shows a piece of artwork with a special
CSR-made seal and a unique serial number, the for-
mer reflects lights producing unique optical patterns,
while the latter is used for identification.
4.3 Requirements and Security Goals
As far as we know there are no standard functional
requirements for an object authentication procedure
in addition to those about security that we are going
to introduce in the next paragraphs.
We assume that a vendor first registers a valuable
asset. This bootstrapping procedure assumes that any-
one can verify whether an object in their possession is
the same as the one registered. Both, the vendor and
the user, are expected to have a device manager (to
acquire pictures), which is considered a trustworthy
entity. We ensure that all the sensitive information is
processed on the device manager to produce a secure
token as a result of the image processing and a series
of cryptographic operations. This secure token is as-
sociated with a unique seal ID (ID
seal
) generated by
the registry server. Thus, once private information has
been processed, it is immediately discarded. Authen-
tication should be more efficient than enrollment as
the former is expected to be executed a larger number
of times while enrollment only once.
With this in mind, protocols should remain capa-
ble of differentiating between authentic and counter-
feit artifacts. They have been designed to satisfy the
following security properties, described informally
here and formalized and proven in Section 5.
• Uniqueness at Enrollment. Each artifact carry-
ing a seal, at registration, is given a unique ID
seal
.
This means that the process of enrollment is reliable
and no false-positive can occur.
• Reliability at Authentication. Two different
seal-embedded artifacts are never recognized as
equal even if one attempts to authenticate them us-
ing the same ID
seal
. This means that the entropy be-
tween the features extracted from the seal image is
high enough to avoid false positives.
• Robustness at Authentication. An authentic ar-
tifact cannot be seen as a counterfeit and no false neg-
atives can arise.
Verifying Artifact Authenticity with Unclonable Optical Tags
69

4.4 Protocols’ Agents and Principals
We assume four entities that participate in the proto-
col, namely the vendor, the user, the device manager,
and registry server, with the following roles and re-
sponsibilities:
• The Vendor (V) has the right to enroll seal tags
via a device manager. It can be a legitimate or a
malicious vendor.
• The User (U) initiates the authenticity verifica-
tion process by providing to the device manager
an ID
′
seal
and a seal
′
tag.
• The Device Manager (DM) is responsible for
processing the images, extracting robust features,
running the cryptographic primitives, and carry-
ing out enrollment and authentication procedures.
– During the enrollment, the DM acquires a set
of {[seal]
i
} images from a physical (seal)
tag provided by the vendor. The vendor must
have certain permissions to start the enrollment
phase.
– During the authentication, the user provides an
ID
seal
to the DM, which queries the server for
retrieving the public data linked to the claimed
seal. Then, it initiates the authentication pro-
cess by acquiring a set of {[seal
′
]
i
} images.
The DM is equipped with a pair of cryptographic
signing keys (ssk
DM
, psk
DM
). It is assumed to be
a trusted entity.
• The Registry Server (RS) responds to the enroll-
ment and authentication requests, maintains the
database and it is also responsible for generating
the ID
seal
. It is responsible for securely storing
the data during the enrollment and for retrieving
the query information requested during the au-
thentication phase. The RS is equipped with a pair
of cryptographic signing keys (ssk
RS
, psk
RS
). It is
assumed to be an honest-but-curious entity.
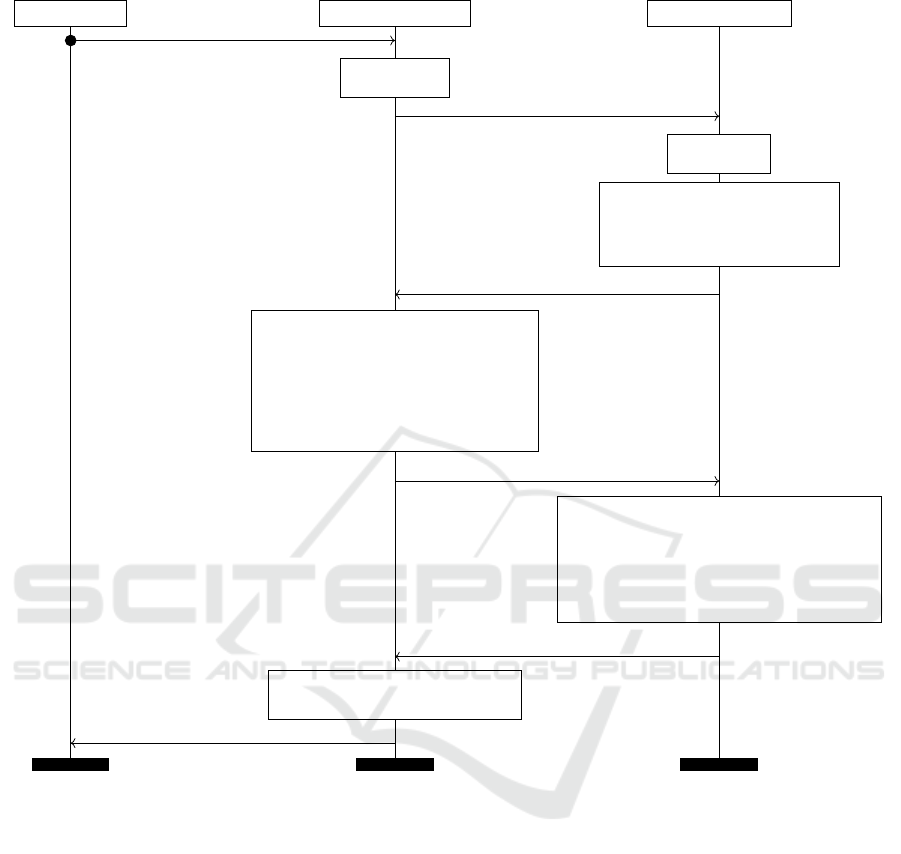
4.5 Enrollment Phase
The enrollment phase of the protocol involves a reg-
istered vendor V, a device manager, and a registry
server, as shown in Figure 2. A vendor has an arti-
fact and initiates the enrollment process by submit-
ting a set of noisy images to the DM. Upon receiv-
ing the images, DM generates a nonce n
DM
, which
is sent along with a ‘request’ message and the ven-
dor ID (V
i
) to the registry server. After receiving the
message, the RS generates on its turn a nonce n
RS
and a unique and fresh ID
seal
. The server uses its se-
cret signing key (ssk
RS
) to sign a tuple containing the
vendor identification V
i
, the ID
seal
, and concatenated
nonces n
DM
||n
RS
. The tuple and signature are then
sent back to the DM.
Upon receiving the response from the registry
server, the device manager firstly verifies the mes-
sage’s structure and signature. If the verification is
successful, it proceeds to extract a robust template ω
from a set of {[seal]
i
} images using the ImgProcess
function. Next, it runs the robust fuzzy extractor
RobustGen procedure and generates a hash value
(h
seal
) using a hash function that produces a digest
of at least 256-bits. Afterward, it signs the message
m
DM
with its secret signing key (ssk
DM
) and commu-
nicates with the RS to send the message m
DM
and the
signature σ
DM
. The device manager discards all the
processed information.
When the registry server receives the message,
it first checks the message’s structure and signa-
ture. If everything is valid, the server checks
whether its database already contains the helper
data P and the h
seal
.
1
If the signature verifica-
tion and duplicate validation checks are success-
ful, the RS’s database stores the public information
(Vi,ID
seal
,P,h
seal
), and the database is updated. Fi-
nally, the vendor receives a confirmation of successful
enrollment of a seal with its respective ID
seal
.
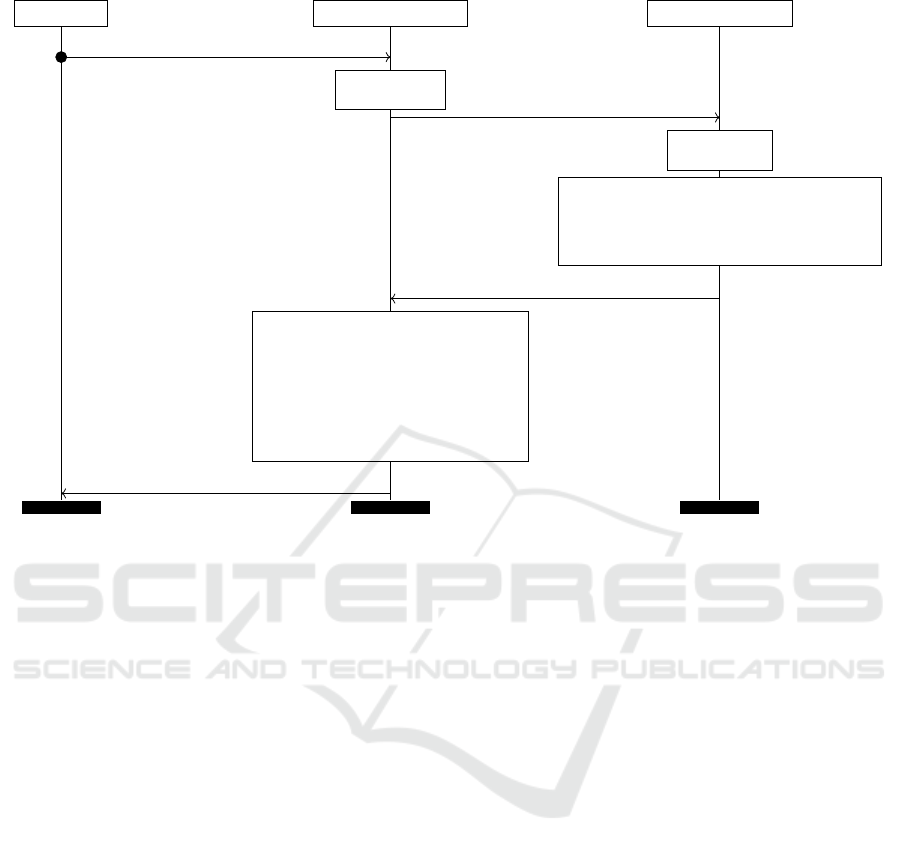
4.6 Authentication Phase
The authenticity verification phase involves a user U,
a device manager, and a registry server, as shown in
Figure 3. The user initiates the authenticity verifica-
tion process by submitting to the DM a set of fresh
images [seal
′
]
i
along with the identifier ID
seal
and
V
i
(encoded in the object). The DM generates imme-
diately a fresh nonce n
DM
and sends it along with the
ID
seal
to the registry server.
In turn, the server generates a nonce n
RS
and
queries the database with the ID
seal
. If the entry ex-
ists, DM generates the message m
seal
containing V
i
,
ID
seal
, P,h
seal
, and n
DM
||n
RS
. The nonces n
DM
and
n
RS
are added to prevent replay attacks. The RS signs
the message with its secret signing key (ssk
RS
).
The DM receives the message m
seal
together with
the signature σ
seal
and it first checks whether V
′
i
matches V
i
. If so, the device manager verifies the sig-
nature, runs the image processing algorithm, and ex-
tracts the robust template ω
′
. The reproduction proce-
dure RobustRep is executed by using the robust tem-
plate ω
′
and the helper data P as inputs, and it out-
puts the secret R
′
. Next, the device manager gener-
1
Note that one can employ data structures from Grossi
and Vitter (2000) to facilitate highly efficient duplicate
search algorithms.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
70
Vendor DM
ssk
DM
,psk
DM
RS
ssk
RS
,psk
RS
V
i
, {[seal]
i
}
n
DM
$
← Z
>0
(
′
request
′
,V
i
,n
DM
)
n
RS
$
← Z
>0
ID
seal
$
← Z
>0
m
RS
← (V
i
,ID
seal
,n
DM
||n
RS
)
σ
RS
← Sign(ssk
RS
,m
RS
)
(m
RS
,σ
RS
)
0/1 ← Verify(psk
RS
,σ
RS
,m
RS
)
ω ← ImgProcess({[seal]
i
})
(R,P) ← Gen(ω)
h
seal
← Hash(R)
m
DM
← (ID
′
seal
,P,h
seal
,n
DM
||n
RS
)
σ
DM
← Sign(ssk
DM
,m
DM
)
(m
DM
,σ
DM
)
0/1 ← Verify(psk
DM
,σ
DM
,m
DM
)
ID
′
seal
?
= ID
seal
If unique: store (V
i
,ID
seal
,P,h
seal
) and
m
′
RS
← (0/1,V
i
,ID
seal
,n
DM
||n
RS
)
σ
′
RS
← Sign(ssk
RS
,m
′
RS
)
(m
′
RS
,σ
′
RS
)
0/1 ← Verify(psk
RS
,σ
′
RS
,m
′
RS
)
Enrolled? Yes/No
Figure 2: Message sequence chart of the enrollment phase. An arrow → is a public channel; an arrow •→ is a private channel,
i.e., the parties have agreed on a session key, e.g., via Transport Layer Security (TLS).
ates a hash value h
′
seal
by using a hash function with
the seed being the secret value R
′
. Finally, the de-
vice manager compares the new hash value with the
one received from the registry server (h
seal
?
= h
′
seal
).
A successful comparison confirms the genuineness of
the artifact and the user receives a confirmation of
successful authentication.
5 SECURITY ANALYSIS
We will discuss security against specific adversaries
and adversarial models and we start with the defini-
tions of the adversary types.
Definition 1. A semi-honest adversary, or honest-
but-curious adversary Goldreich (2009), is a type of
attacker who can perform any passive attack on a sys-
tem and can gather as much data as possible without
breaking the prescribed definition of the protocol.
Definition 2. A malicious adversary is the strongest
type of adversary Goldreich (2009). Such an adver-
sary can deviate from the protocol’s definition and use
any effective strategy to gain further knowledge about
private data belonging to other parties or manipulate
the computation’s outcome.
5.1 Adversary Model
We assume a Dolev-Yao adversary Dolev and Yao
(1983), a standard choice in security protocol anal-
ysis. It represents an external active intruder that con-
trols the communication channels between the other
Verifying Artifact Authenticity with Unclonable Optical Tags
71
User DM
ssk
DM
,psk
DM
RS
ssk
RS
,psk
RS
ID
seal
,V
′
i
,{[seal
′
]
i
}
n
DM
$
← Z
>0
(ID
seal
,n
DM
)
n
RS
$
← Z
>0
ID
seal
?
∈ DB
m
seal
← (V
i
,ID
seal
,P,h
seal
,n
DM
||n
RS
)
σ
seal
← Sign(ssk
RS
,m
seal
)
(m
seal
,σ
seal
)
V
′
i
?
= V
i
0/1 ← Verify(psk
RS
,σ
seal
,m
seal
)
ω
′
← ImgPro cess({[seal
′
]
i
})
R
′
← Rep(ω
′
,P)
h
′
seal
← Hash(R
′
)
0/1 ← Compare(h
′
seal
,h
seal
)
Authenticated? Yes/No
Figure 3: Message sequence chart of the authenticity verification phase. An arrow → is a public channel; an arrow •→ is a
private channel, i.e., the parties have agreed on a session key, e.g., via TLS.
principals: the intruder can intercept, modify, cre-
ate/inject, and destroy messages, but he cannot create
signatures unless he knows the appropriate keys.
We also assume that our adversary can ma-
nipulate objects. Although it has already been
stated that tampering with the “seal” is not pos-
sible without compromising its integrity, the in-
truder can still modify the ID that an object
o carries together with its seal, something we
write as o[seal, ID
seal
]. In short, the intruder
can change ID
seal
: TamperID(o[seal,ID
seal
]) →
o[seal,ID
′
seal
].
Instead, we assume that the adversary cannot tam-
per with the device manager. That said, we also as-
sume that the adversary can act as a Vendor, a User,
or an external attacker with goals of: (i) learning sen-
sitive parameters: [seal]
i
, ω, and R; (ii) enrolling the
object at the RS by bypassing DM; (iii) impersonat-
ing the RS in the enrollment phase; and (iv) succeed-
ing to authenticate an object without previously being
enrolled.
Instead, we assume that the registry server is
honest-but-curious which means it obeys the proto-
col but is trying to obtain knowledge about [seal]
i
,
ω, and R. Moreover, in our protocol, we assume that
the communication channel between the vendor and
the DM, as well as the user and the DM, are private.
We also assume that the secret information (e.g., ω,R)
extracted from each seal is discarded once the mes-
sage is digitally signed. This requires that we trust the
device manager to be stateless.
5.2 Formal Analysis by ProVerif
We formally prove that our design satisfies the pro-
tocol’s main goal, as we stated in Section 4.3. We
check the security of our protocol using ProVerif
model-checker Blanchet (2001). ProVerif is a for-
mal verification tool that can prove the secrecy, au-
thentication, and privacy properties of a protocol and
supports an unbounded number of messages and ses-
sions. It takes as input the description of a protocol in
a cryptography-enhanced extension of the applied π-
calculus Abadi et al. (2017) and automatically trans-
lates this description into Horn clauses, which is used
to prove the desired properties in the Dolev-Yao ad-
versarial model. ProVerif is sound, which means that
if it proves a certain property holds, then this property
is satisfied.
Cryptographic primitives in ProVerif are modeled
using equational theories. Table 1 shows the equa-
tional theories used in our model. The security re-
quirements that we aim to achieve in our protocol
are secrecy and authentication properties. ProVerif
verifies the secrecy of a parameter by querying the
reachability of all possible traces in the protocol to
SECRYPT 2024 - 21st International Conference on Security and Cryptography
72

find a trace where the target secret is known to the
attacker. To prove authentication properties, the veri-
fier uses correspondence assertions on events. Events
in ProVerif are internal messages, not accessible to
the attacker, that flag the protocol state within a trace
without affecting the protocol behavior. They may
contain arguments as inputs to precisely capture a
state inside a process.
Table 1: Equational theories in our protocol model.
Primitive Equational Theory
Signature
getmess(sign(m,ssk)) = m
checksign(sign(m,ssk), pk(ssk)) = m
Reproduction rep(ω,genP(ω)) = genR(ω)
The following list of events is used in our ProVerif
model:
- serverChallenged: raised by the RS upon re-
ceiving a request from the DM.
- serverVerified: raised by the DM after suc-
cessfully verifying the RS’s signature on the mes-
sage m
RS
.
- enrolRequested(V
i
,ID
seal
,P,h
seal
): raised
by the DM when it sends the enrollment request for
an object with (ID
seal
,P,h
seal
) parameters issued
by the vendor’s identity, V
i
.
- enrolVerified(V
i
,ID
seal
,P,h
seal
): raised by
the RS when it successfully verifies the signature of
the DM on the message m
DM
.
- resultVerified(V
i
,ID
seal
): raised by the
DM when it successfully verifies the signature of
the RS on the message m
′
RS
.
- recordSent(V
i
,ID
seal
,P,h
seal
): raised by the
RS when it sends the message, m
seal
.
- recordVerified(V
i
,ID
seal
,P,h
seal
) raised
by the DM when the validity checks for h
seal
and
V
i
are true and it successfully verifies the signature
of the RS on the message m
seal
.
- honestVendors(V
i
,csrH) This event is used
to distinguish an honest vendor process, enrolling
an object with csrH image, from the vendor pro-
cess controlled by the attacker. This event helps
ProVerif to discard false attacks during the secrecy
check.
5.3 Security Properties
As we mentioned in Section 5.2, we investigate sev-
eral secrecy and authentication properties in our pro-
tocol. The first step to verify the authentication prop-
erties is to formally define them in a proper mathemat-
ical expression. Here, we present a formal definition
of three authentication properties and later in Section
5.4, we show the result of ProVerif analysis based on
these definitions.
Definition 3 (RS Authenticity). The Registry
Server Authenticity holds if each occurrence of the
serverVerified event is preceded by a unique
occurrence of the serverChallenged event.
One of the key authentication requirements for our
protocol is that the DM should assure that it indeed
enrolls an object to a server that possesses the pair
of {ssk
RS
,psk
RS
} keys. The RS Authenticity guar-
antees that the message m
RS
, received by the DM, is
genuinely generated by the RS, hence the server is au-
thentic for the DM. This property is injective which
means that there is a one-to-one correspondence be-
tween the serverVerified and serverChallenged
events. In other words, the injective constraint is used
to prevent replay attacks.
inj-serverVerified ⇝ inj-serverChallenged
Definition 4 (Enrollment Authentication). The
Enrollment Authentication is valid if each oc-
currence of the resultVerified(V
i
,ID
seal
)
event is preceded by a unique occurrence
of the enrolVerified(V
i
,ID
seal
,P,h
seal
)
and each occurrence of the event
enrolVerified(V
i
,ID
seal
,P,h
seal
) is
preceded by a unique occurrence of the
enrolRequested(V
i
,ID
seal
,P,h
seal
) event.
This important security requirement in the enroll-
ment phase of our protocol says that only an authentic
DM must be able to enroll an object to the RS and the
integrity of the sent record must be preserved. In ad-
dition, it implies that when the RS returns the enroll-
ment result to the DM, the DM makes sure that this
result is genuinely generated by the RS for the same
object. More precisely, the Enrollment Authentica-
tion property assures the RS that the message m
DM
received by the RS is generated by a legitimate DM
and its content (V
i
,ID
seal
,P,h
seal
) has not been ma-
nipulated by the attacker, hence this record is authen-
tic and can be stored in the database. On the other
side, this mutual authentication property guarantees
the DM that the message m
′
RS
is generated by the RS
and contains the result of the enrollment request for
the object with (V
i
,ID
seal
) information.
inj-resultVerified (V
i
,ID
seal
) ⇝
(inj-enrolVerified (V
i
,ID
seal
,P,h
seal
) ⇝
inj-enrolRequested (V
i
,ID
seal
,P,h
seal
))
Definition 5 (Object Authentication). The Ob-
ject Authentication holds if each occurrence
of the recordVerified(V
i
,ID
seal
,P,h
seal
)
event is preceded by a unique occurrence of the
recordSent(V
i
,ID
seal
,P,h
seal
) event.
Verifying Artifact Authenticity with Unclonable Optical Tags
73

Table 2: ProVerif results of the proposed authenticity verification protocol.
Secrecy Authentication
Properties
{[seal]
i
} ω R Reg. Server Enrollment Object
✓ ✓ ✓ ✓ ✓ ✓
This property assures to the device manager that
(i) The message m
seal
is generated by the registry
server and its content is not manipulated by an at-
tacker. (ii) The hash term h
seal
derived from the
user’s provided input [seal
′
]
i
matches the one re-
trieved from the registry server’s database. (iii) The
vendor ID V
′
i
, presented by the user is the same as the
vendor ID V
i
, stored in the registry server’s database
for the object with the identity of ID
seal
.
inj-recordVerified (V
i
,ID
seal
,P,h
seal
) ⇝
inj-recordSent (V
i
,ID
seal
,P,h
seal
)
5.4 ProVerif Results
Our ProVerif model
2
is composed by the User, Ven-
dor, DM, and RS, with definitions provided in Section
4.4, and two types of adversaries whose power are de-
fined in Definition 1 and 2.
Proving secrecy properties in ProVerif is a
straightforward procedure and ProVerif just needs to
check if a target parameter is not reachable to the
attacker for all possible traces. The analysis results
show that the secrecy of [seal]
i
, ω, and R in both ma-
licious and semi-honest attacker models are satisfied,
as depicted in Table 2.
To prove the authentication properties in our
ProVerif model, we express three RS Authenticity,
Enrollment Authentication, and Object Authentica-
tion definitions as standard correspondence queries.
ProVerif successfully proves that all these three prop-
erties hold in our protocol which means: (i) all enroll-
ments are done by an authentic registry server; (ii) if
an enrollment record is stored in the database then this
record has been enrolled by a trusted DM and its in-
tegrity is preserved; (iii) if an authentication request
for an object claimed to be produced by a vendor is
successful, then this object has previously been en-
rolled in the authentic RS by the same vendor. This
result is very important because it guarantees that an
attacker cannot authenticate a fake object or manipu-
late the vendor’s ID associated with an authentic ob-
ject.
2
ProVerif and Python codes available in https://edu.lu/
u7ue8.
6 IMPLEMENTATION
DISCUSSION
A proof-of-concept (POC) of the proposed proto-
col was implemented in Python 3.9.7
2
on a ma-
cOS Unix machine (Apple M1 Pro chip with 32 GB
RAM). The protocol consists of seals made up of
CSRs, which can be extended to other materials with
similar noisy behavior. As demonstrated by the au-
thors in another paper Arenas et al. (2022b), the image
processing is the most computationally expensive op-
eration in both enrollment and authentication phases.
In contrast, other operations like signing, verifying,
and hashing are highly efficient, taking only a frac-
tion of a second to complete.
6.1 Hash Function
The hash function used in the secure sketch scheme
(RobustSS,RobustRec) and the enrollment routine
can be selected from well-known families of hash
functions. These families provide resistance to preim-
age and collision attacks, such as the SHA-2 and
SHA-3 families. In the classical setting, i.e., when no
adversaries with quantum capabilities are assumed,
the digest size should be at least 256-bits. In this case,
the choice of SHA-256 is sufficient.
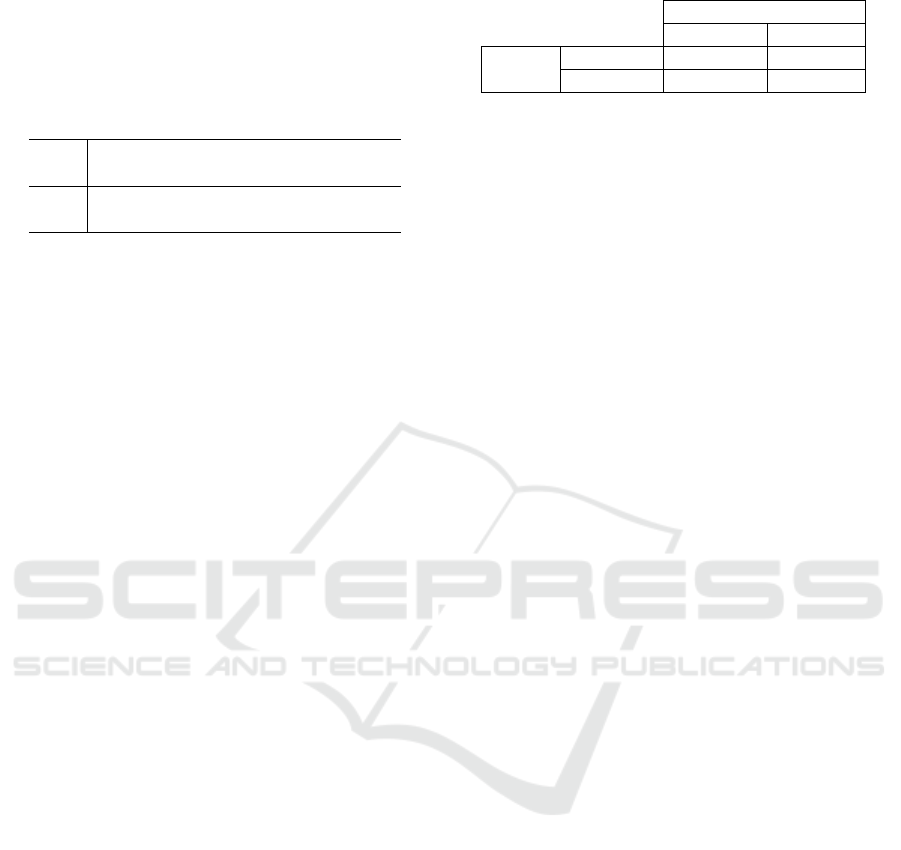
6.2 Entropy
The entropy of a biometric vector is calculated via the
relation m = n log
2
(kaN), where N is the length of
the number line, k is the interval’s length, a is a fixed
constant, and n is the size of the biometric vector, as
well described by Li et al. (2017). Further, the entropy
heavily relies on the density of the minutiæ and their
distribution on the number line. As mentioned, the
use-case material is made up of CSRs, composed of
spherical particles called blobs, where each CSR im-
age contains arrays with different blob densities and
blob diameters (k). The image processing involves the
blob’s extraction and the creation of the robust tem-
plate ω. To create this template, the extracted blobs
from i−images are embedded into a grid that is a
product of two number lines, each of length N, in a
similar way as Li et al. (2017). The entropy of the ro-
bust template ω in this instance relies on the length N
SECRYPT 2024 - 21st International Conference on Security and Cryptography
74
of each number line, the size of each square, as well as
the number of blobs contained in the CSR image and
its average blobs’ diameter. Table 3 reports the mini-
mum and maximum min-entropy values of the robust
template vector ω extracted from our dataset.
Table 3: Entropy of ω.
N k
Num. of
blobs
Min-entropy
min 15 8 5 3 108-bits
max 70 24 201 104 999-bits
6.3 Robustness and Reliability
We developed in Arenas et al. (2021, 2022a) a reli-
able process to extract the information from images
captured under different lighting and environmental
conditions, a methodology also adopted in this paper.
We acquired a reference image from 30 different CSR
tags and, to have a larger dataset, we generated a set
of images by artificially injecting noise into each ref-
erence image. The dataset was generated by adding
similarity and Gaussian noise. For the former, we ran-
domly added rotation, illumination changes, and blur-
ring effect (lack of focus). For the Gaussian noise, we
introduced values with a standard deviation ranging
from 0.0 to 0.3 —values chosen considering realistic
conditions.
We assumed that the enrollment is executed in a
single attempt, from which five noisy images were
generated. And, for the authentication phase, 20 at-
tempts were considered at different time intervals,
while five images were also acquired from each at-
tempt. This experimental setup ensures the extraction
of robust information.
The robustness of our system was benchmarked
by comparing 600 pairs of related CSR retakes and
our system’s reliability was evaluated by comparing
600 pairs of unrelated CSR retakes. A robust authen-
tication process should be able to accept any image of
an optical response from the same CSR despite the
presence of noise during the readout. Similarly, a
reliable authentication process should reject any im-
age generated by any other CSR. The results of these
comparisons are presented in Table 4. The protocol’s
acceptance rate for related CSR images was 93.75%,
and the false-negative rate of 6.25% was due to the
difference between ω and ω
′
. Our authentication pro-
tocol also rejected all incorrect (CSR, ID
CSR
) pairs,
resulting in a false-positive ratio of 0%, confirming
the reliability of our system.
Table 4: Confusion Matrix
Actual Value
Accepted Rejected
Result
Accepted 93.75% 0%
Rejected 6.25% 100%
7 CONCLUSION AND FUTURE
WORK
We studied the problem of how to authenticate objects
even in the presence of adversaries that have an inter-
est in tampering with the physical items and the data.
We proposed two procedures, one for enrollment and
one for authentication. Their security features rely on
physical elements that are natural PUFs (i.e., special
tags we called “seal”), on secure information extrac-
tion algorithms, and on specific cryptographic proto-
cols.
We are interested in securing the procedures
against two sources of attacks: physical and cyber-
physical. In the former, an adversary tries to phys-
ically transfer a seal from one artwork to another.
Based on the assumption that the seal are tamper evi-
dent, we guarantee object integrity, making it difficult
for the attacker to succeed. In the latter, the cyber-
physical attack, a Dolev-Yao adversary tries to fool
the communication channels between two key parties:
the device manager and the registry server. Never-
theless, our procedures preserve data secrecy of sen-
sitive data, that is, the set of images taken from the
seal, the robust features ω, and the secret value R
obtained via the fuzzy extractor primitive. They also
satisfy registry server authenticity, enrollment authen-
tication, and object authentication. All our security
claims have been formally verified using the formal
verification tool ProVerif.
There is still future work to do. In our analysis,
we did not consider an adversary that can tamper with
the process of extracting information, for instance, by
corrupting the camera so that the device will return a
constant value ω. This corruption can be implemented
e.g., by forcing ImgProcess to work always on the
same set of images injected by the adversary. In our
message chart, this assumption is reflected in the in-
teraction between the vendor or user and the device
manager being a private channel, where the device is
assumed trustworthy. If we admitted a device’s being
corrupted, that is, if we assumed the vendor-device
(or user-device) channel be in clear in our model, we
expect that the overall security collapses: there is, ab-
stractly speaking, no difference between corrupting
the seal or the pictures taken from the seal. An open
Verifying Artifact Authenticity with Unclonable Optical Tags
75

question for future work is how to model a large set of
physical adversarial capabilities, including code cor-
ruption of a device in a way that is realistically aligned
with what can be done in terms of software vulnera-
bilities.
ACKNOWLEDGEMENTS
The authors acknowledge the financial support
from the Luxembourg National Research Fund
(FNR) on the Secure and Verifiable Electronic
Testing and Assessment Systems –SEVERITAS
(INTER/ANR/20/14926102 ANR-20-CE39-
009-03). Marjan
ˇ
Skrobot received support
from the FNR under the CORE Junior project
(C21/IS/16236053/FuturePass). Peter Y.A. Ryan
received support from FNR under the CORE project
(C21/IS/16221219/ ImPAKT). The authors also
acknowledge Prof. Dr. J. Lagerwall and the ESMP
group for providing the CSR images.
REFERENCES
Abadi, M., Blanchet, B., and Fournet, C. (2017). The ap-
plied pi calculus: Mobile values, new names, and se-
cure communication. Journal of the ACM (JACM),
65(1):1–41.
Anandhi, S., Anitha, R., and Sureshkumar, V. (2020).
An Authentication Protocol to Track an Object with
Multiple RFID Tags Using Cloud Computing En-
vironment. Wireless Personal Communications,
113(4):2339–2361.
Arenas, M., Demirci, H., and Lenzini, G. (2021).
Cholesteric Spherical Reflectors as Physical Unclon-
able Identifiers in Anti-counterfeiting. In 16th Inter-
national Conference on ARES, pages 1–11. ACM.
Arenas, M., Demirci, H., and Lenzini, G. (2022a). An Anal-
ysis of Cholesteric Spherical Reflector Identifiers for
Object Authenticity Verification. Machine Learning
and Knowledge Extraction, 4(1):222–239.
Arenas, M. P., Bingol, M. A., Demirci, H., Fotiadis, G., and
Lenzini, G. (2022b). A Secure Authentication Proto-
col for Cholesteric Spherical Reflectors using Homo-
morphic Encryption. In AFRICACRYPT.
Armknecht, F., Maes, R., Sadeghi, A. R., Sunar, B., and
Tuyls, P. (2009). Memory leakage-resilient encryption
based on physically unclonable functions. In Interna-
tional Association for Cryptologic Research, volume
5912 LNCS, pages 685–702.
Blanchet, B. (2001). An efficient cryptographic protocol
verifier based on prolog rules. In Proc. 14th IEEE
Computer Security Foundations Workshop, volume 1,
pages 82–96, Nova Scotia. Citeseer, IEEE.
Boyen, X. (2004). Reusable cryptographic fuzzy extractors.
In Atluri, V., Pfitzmann, B., and McDaniel, P. D., edi-
tors, Proceedings of the 11th CCS, 2004, pages 82–91.
ACM.
Boyen, X., Dodis, Y., Katz, J., Ostrovsky, R., and Smith,
A. D. (2005). Secure remote authentication using
biometric data. In Cramer, R., editor, Advances in
Cryptology - EUROCRYPT 2005, 24th Annual Inter-
national Conference on the Theory and Applications
of Cryptographic Techniques, Aarhus, Denmark, May
22-26, 2005, Proceedings, volume 3494 of Lecture
Notes in Computer Science, pages 147–163. Springer.
Canetti, R., Fuller, B., Paneth, O., Reyzin, L., and Smith, A.
(2021). Reusable Fuzzy Extractors for Low-Entropy
Distributions. Journal of Cryptology, 34(1):2.
Choi, S., Yang, B., Cheung, H., and Yang, Y. (2013).
Data management of RFID-based track-and-trace
anti-counterfeiting in apparel supply chain. In 8th
International Conference for Internet Technology and
Secured Transactions (ICITST-2013), pages 265–269.
Dodis, Y., Katz, J., Reyzin, L., and Smith, A. (2006). Ro-
bust fuzzy extractors and authenticated key agreement
from close secrets. In Dwork, C., editor, Advances in
Cryptology - CRYPTO 2006, pages 232–250, Berlin,
Heidelberg. Springer Berlin Heidelberg.
Dodis, Y., Reyzin, L., and Smith, A. (2004). Fuzzy extrac-
tors: How to generate strong keys from biometrics and
other noisy data. In International conference on the
theory and applications of cryptographic techniques,
pages 523–540. Springer.
Dolev, D. and Yao, A. (1983). On the security of public key
protocols. IEEE Transactions on information theory,
29(2):198–208.
Gao, Y., Su, Y., Xu, L., and Ranasinghe, D. C. (2018).
Lightweight (Reverse) Fuzzy Extractor with Multiple
Referenced PUF Responses. arXiv:1805.07487 [cs].
Gassend, B., Clarke, D., van Dijk, M., and Devadas, S.
(2002). Controlled physical random functions. In 18th
Annual Computer Security Applications Conference,
2002. Proceedings., pages 149–160. ISSN: 1063-
9527.
Geng, Y., Noh, J., Drevensek-Olenik, I., Rupp, R., and
Lagerwall, J. (2017). Elucidating the fine details of
cholesteric liquid crystal shell reflection patterns. Liq-
uid Crystals, 44(12-13):1948–1959.
Geng, Y., Noh, J., Drevensek-Olenik, I., Rupp, R., Lenzini,
G., and Lagerwall, J. P. (2016). High-fidelity spherical
cholesteric liquid crystal Bragg reflectors generating
unclonable patterns for secure authentication. Scien-
tific Reports, 6:1–9.
Goldreich, O. (2009). Foundations of cryptography. 2: Ba-
sic applications. Cambridge Univ. Press, Cambridge.
Grossi, R. and Vitter, J. S. (2000). Compressed suffix ar-
rays and suffix trees with applications to text indexing
and string matching (extended abstract). In Yao, F. F.
and Luks, E. M., editors, Proceedings of the Thirty-
Second Annual ACM Symposium on Theory of Com-
puting, May 21-23, 2000, Portland, OR, USA, pages
397–406. ACM.
Herder, C., Yu, M. D., Koushanfar, F., and Devadas,
S. (2014). Physical unclonable functions and ap-
SECRYPT 2024 - 21st International Conference on Security and Cryptography
76

plications: A tutorial. Proceedings of the IEEE,
102(8):1126–1141.
Huang, S.-Y. and Wu, J. (2007). Optical watermarking for
printed document authentication. IEEE Transactions
on Information Forensics and Security, 2(2):164–173.
Li, N., Guo, F., Mu, Y., Susilo, W., and Nepal, S. (2017).
Fuzzy extractors for biometric identification. In 2017
IEEE 37th International Conference on Distributed
Computing Systems (ICDCS), pages 667–677. IEEE.
Li, Q., Sutcu, Y., and Memon, N. (2006). Secure sketch
for biometric templates. Lecture Notes in Computer
Science, 4284 LNCS:99–113.
Marktscheffel, T., Gottschlich, W., Popp, W., Werli, P.,
Fink, S. D., Bilzhause, A., and de Meer, H. (2016).
QR code based mutual authentication protocol for In-
ternet of Things. In 2016 IEEE 17th International
Symposium on A World of Wireless, Mobile and Mul-
timedia Networks (WoWMoM), pages 1–6.
Maurya, P. K. and Bagchi, S. (2018). A Secure PUF-Based
Unilateral Authentication Scheme for RFID System.
Wireless Personal Communications, 103(2):1699–
1712.
McGrath, T., Bagci, I. E., Wang, Z. M., Roedig, U., and
Young, R. J. (2019). A PUF taxonomy. Applied
Physics Reviews, 6(1):011303–(1–25).
Nam, H., Song, K., Ha, D., and Kim, T. (2016). Inkjet Print-
ing Based Mono-layered Photonic Crystal Patterning
for Anti-counterfeiting Structural Colors. Scientific
Reports, 6(1).
Noh, J., Liang, H.-L., Drevensek-Olenik, I., and Lagerwall,
J. P. (2014). Tuneable multicoloured patterns from
photonic cross-communication between cholesteric
liquid crystal droplets. Journal of Materials Chem-
istry C, 2(5):806–810.
Pappu, R., Recht, B., Taylor, J., and Gershenfeld, N.
(2002). Physical One-Way Functions. Science,
297(September):2026–2031.
Schwartz, M., Geng, Y., Agha, H., Kizhakidathazhath, R.,
Liu, D., Lenzini, G., and Lagerwall, J. P. F. (2021).
Linking Physical Objects to Their Digital Twins via
Fiducial Markers Designed for Invisibility to Humans.
Multifunctional Materials.
Schwartz, M., Lenzini, G., Geng, Y., Rønne, P. B., Ryan,
P. Y., and Lagerwall, J. P. (2018). Cholesteric Liquid
Crystal Shells as Enabling Material for Information-
Rich Design and Architecture. Advanced Materials,
30(30):1–19.
Shariati, S., Standaert, F. X., Jacques, L., and Macq, B.
(2012). Analysis and experimental evaluation of
image-based PUFs. Journal of Cryptographic Engi-
neering, 2(3):189–206.
Suh, G. E. and Devadas, S. (2007). Physical Unclonable
Functions for Device Authentication and Secret Key
Generation. In 2007 44th ACM/IEEE Design Automa-
tion Conference, pages 9–14. ISSN: 0738-100X.
Tuyls, P., Akkermans, A. H., Kevenaar, T. A., Schrijen,
G. J., Bazen, A. M., and Veldhuis, R. N. (2005). Prac-
tical biometric authentication with template protec-
tion. Lecture Notes in Computer Science, 3546:436–
446.
Tuyls, P. and Goseling, J. (2004). Capacity and examples
of template-protecting biometric authentication sys-
tems. Lecture Notes in Computer Science (including
subseries Lecture Notes in Artificial Intelligence and
Lecture Notes in Bioinformatics), 3087:158–170.
Voloshynovskiy, S., Holotyak, T., and Bas, P. (2016). Phys-
ical object authentication: Detection-theoretic com-
parison of natural and artificial randomness. In 2016
IEEE International Conference on Acoustics, Speech
and Signal Processing (ICASSP), pages 2029–2033,
Shanghai. IEEE.
Wen, Y. and Liu, S. (2018). Robustly Reusable Fuzzy
Extractor from Standard Assumptions. In Peyrin, T.
and Galbraith, S., editors, Advances in Cryptology
– ASIACRYPT 2018, volume 11274, pages 459–489.
Springer International Publishing, Cham. Series Title:
Lecture Notes in Computer Science.
Verifying Artifact Authenticity with Unclonable Optical Tags
77
