
An Evaluation of Risk Management Standards and Frameworks for
Assuring Data Security of Medical Device Software AI Models
Buddhika Jayaneththi
a
, Fergal Mc Caffery
b
and Gilbert Regan
c
Regulated Software Research Centre, Dundalk Institute of Technology, Dundalk, Ireland
Keywords: Artificial Intelligence, Data Security, Medical Device Software, Risk Management.
Abstract: Data is the backbone of Artificial Intelligence (AI) applications, including Medical Device Software (MDS)
AI models which rely on sensitive health data. Assuring security of this sensitive health data is a key require-
ment for MDS AI models and there should be a structured way to manage the risk caused by data security
compromises. Implementing a security risk management standard/framework is an effective way to develop
a solid baseline for managing security risks, measuring the effectiveness of security controls and meeting
compliance requirements. In this paper, nine risk management standards/frameworks in data/information se-
curity, AI, Medical Devices (MDs) and AI-enabled MDs domains are evaluated to identify their gaps and
implementation challenges when applying them to assure data security of MDS AI models. The results show
that currently there is no specific standard/framework that specifically addresses data security risk manage-
ment of MDS AI models, and that existing standards/frameworks have several gaps such as complexity of the
implementation process; lack of detailed threat and vulnerability catalogues; lack of a proper method for risk
calculation/estimation; and lack of risk controls and control implementation details. These gaps necessitate
the need for the development of a new data security risk management framework for MDS AI models.
1 INTRODUCTION
AI has the capability to revolutionise the healthcare
sector and enhance the productivity and efficiency of
care delivery (Spatharou et al., 2020). Integrating AI
into clinical decision making helps reveal the power
of big data, improve evidence-based decision making,
deliver value by reducing cost, enhance patient expe-
rience and outcomes, and optimise health system per-
formance (M. Chen & Decary, 2020). In the MD do-
main, software is implemented in two forms namely:
Software in a Medical Device (SiMD) and Software
as a Medical Device (SaMD) (IMDRF SaMD Work-
ing Group, 2013). The International Medical Device
Regulators Forum (IMDRF) defines SaMD as soft-
ware designed for one or more medical purposes
without necessarily being part of a hardware MD. In
contrast, SiMD is defined as a part of a hardware MD
that assist the MD to perform the intended medical
purpose (IMDRF SaMD Working Group, 2013).
a
https://orcid.org/0009-0008-7813-3942
b
https://orcid.org/0000-0002-0839-8362
c
https://orcid.org/0000-0002-5023-6914
Most devices that rely on AI/ML fall into the category
of SaMD (FDA, 2020).
MDS AI models usually rely on sensitive personal
health data including medical records, diagnostic im-
ages, and medication lists (Coventry & Branley,
2018). Exposure of this sensitive data to unauthorised
parties can ultimately lead to different issues includ-
ing medical identity theft, incorrect diagnosis and
treatments, privacy and ethical violations, and some-
times life-threatening incidents or loss of lives
(EPRS, 2022). Hence, assuring the security of this
sensitive health data is a key requirement that should
be considered when developing MDS AI models.
One of the most prominent issues that developers
face when assuring data security when developing
MDS AI models is the unavailability of a risk man-
agement standard/framework that specifically ad-
dresses the data security risk management of MDS AI
models (Zhao & Yang, 2022). The development of
such standard/framework requires the identification
of the gaps and implementation challenges in the
Jayaneththi, B., Caffery, F. and Regan, G.
An Evaluation of Risk Management Standards and Frameworks for Assuring Data Security of Medical Device Software AI Models.
DOI: 10.5220/0012756000003753
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 19th International Conference on Software Technologies (ICSOFT 2024), pages 91-99
ISBN: 978-989-758-706-1; ISSN: 2184-2833
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
91
existing standards/frameworks. The contributions of
this paper aim to fulfil the following objectives: 1) To
identify the most relevant standards/frameworks that
can be applied to the data security risk management
of MDS AI models; 2) To evaluate the identified
standards/frameworks, expose the state-of-art and
identify the gaps and implementation challenges of
the standards/frameworks and 3) To identify new re-
quirements that should be fulfilled when developing
a developer friendly data security risk management
framework for MDS AI models .
As for the remaining parts of the paper, section 2
presents challenges faced when adopting a security
standard/framework, section 3 presents the methodol-
ogy used to conduct the evaluation, section 4 the re-
sults obtained, section 5 discussion, section 6 threats
to validity and section 7 conclusion.
2 CHALLENGES FOR
ADOPTING A SECURITY RISK
MANAGEMENT
STANDARD/FRAMEWORK
This section presents a summary of the security risk
management standard/framework adoption chal-
lenges identified from the literature.
Complexity and lack of sufficient implementation
details: Most of the existing standards are complex
and difficult to be understood and implemented by the
developers as they do not provide enough implemen-
tation details (Eom & Lee, 2018; Macmahon et al.,
2018).
Lack of awareness and knowledge of security stand-
ards/frameworks: Most of the organisations that de-
velop MDS are usually small in size and often lack
knowledge and awareness of existing data security
standards and frameworks (J. Q. Chen & Benusa,
2017).
Selecting the most appropriate standard for imple-
mentation: The unavailability of a risk management
standard/framework that specifically addresses data
security risk management of MDS AI models makes
the selection process challenging as it requires rigor-
ous study of the existing ones (Djebbar & Nordstrom,
2023; Zhao & Yang, 2022).
Lack of security controls and control implementa-
tion details: In general, most of the standards/frame-
works include security controls at a very high level
with limited details related to the implementation of
the security controls (Djebbar & Nordstrom, 2023;
Macmahon et al., 2018; Yaqoob et al., 2019).
Lack of finance and top management support: Lack
of top management support (Han et al., 2020) and
limitations in the budget allocated (Benz & Chatter-
jee, 2020) also challenges the adoption process. Most
of the top management personnel are reluctant to pro-
vide necessary resources and support due to the lack
of understanding of the return on investment on ap-
plication of the standard/framework (Macmahon et
al., 2018).
Complex and dynamic data security threat land-
scape: Complex and evolving behaviour of the data
security threat landscape is also challenging the adop-
tion of an adequate security standard/framework (Sid-
diqui et al., 2021). The existing standards/frameworks
are struggling to react to the dynamically changing
security threat landscape and provide the necessary
controls for the evolving threats (Naumov &
Kabanov, 2016).
3 METHODOLOGY
The steps followed during the identification and eval-
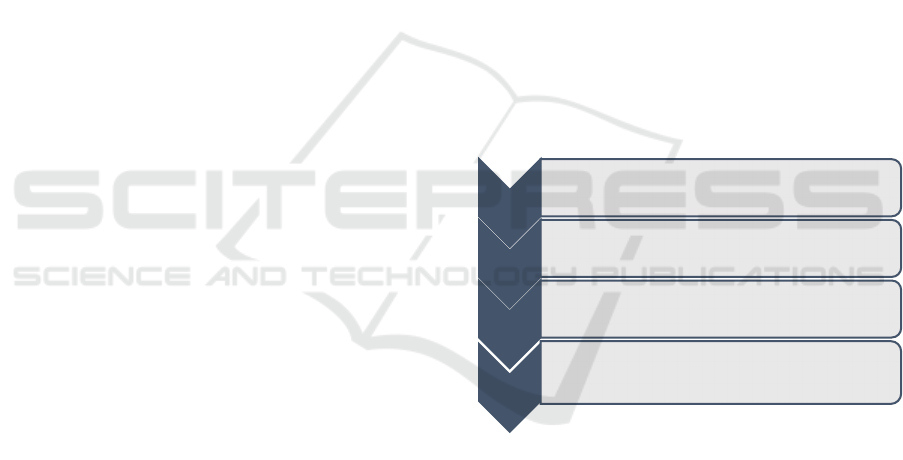
uation of the standards and frameworks are depicted
in Figure 1.
Figure 1: Methodology.
Step 01: To identify the existing risk management
standards/frameworks, a search was conducted on the
British Standard Institution (BSI) website and the
Google search engine. The search was conducted by
the lead author of the paper in October 2023, and was
overseen by members of the Regulated Software Re-
search centre (RSRC), DkIT, Ireland whom have
many years of experience in the domain of MDS risk
management. BSI provides access to British, Euro-
pean and International standards and the intention of
using Google search was to identify any stand-
ards/frameworks that were not included in BSI. The
search strings (SS) used to conduct the search are pre-
sented in Table 1.
Step 01
• Identify risk management standards/frameworks in
data/information security, AI, medical devices and
AI medical devices domains
Step 02
• Select the most suitable standards/frameworks for
the evaluation
Step 03
• Identify and develop the criteria for the evaluation
Step 04
• Conduct the evaluation based on the developed
criteria and conclude with the identified gaps and
new requirements for a data security risk
management framework
ICSOFT 2024 - 19th International Conference on Software Technologies
92
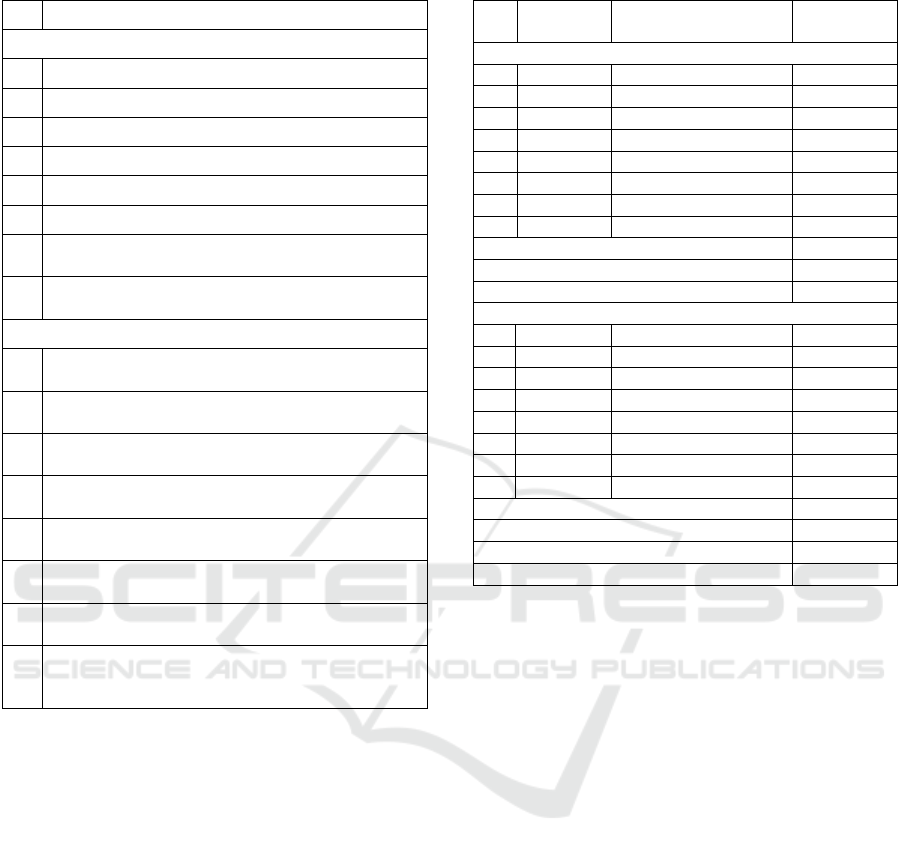
Table 1: Search strings (SS) used.
Search String
British Standard Institution
1 “data security risk management”
2 “information security risk management”
3 “artificial intelligence risk management”
4 “artificial intelligence security risk management”
5 “medical device risk management”
6 “medical device security risk management”
7 “artificial intelligence medical device security risk
mana
g
ement”
8 “artificial intelligence medical device software
data security risk management”
Google
9 “data security risk management standards and
frameworks”
10 “information security risk management standards
and frameworks”
11 “artificial intelligence risk management standards
and frameworks”
12 “artificial intelligence security risk management
standards and frameworks”
13 “medical device risk management standards and
frameworks”
14 “medical device security risk management stand-
ards and frameworks”
15 “artificial intelligence medical device security risk
management standards and frameworks”
16 “artificial intelligence medical device software
data security risk management standards and
frameworks”
An initial list of 176 standards was collected from
the BSI. The list was filtered by removing the re-
vised/withdrawn/superseded standards and duplicate
standards in each SS. An initial list of 30 standards
was collected from Google. During Google search,
millions of records were derived for each SS. The
first three pages of the search results were considered
because Google’s page ranking system usually re-
turns the highest quality and most relevant results for
a user’s search query in the first pages. Any standard
that was repeated from the BSI list was eliminated
during the initial search. Then, the list was filtered by
removing the duplicates collected for each SS. The
summary of the collected standards is presented in
Table 2.
Table 2: Summary of standards from the BSI.
SS No: of
standards
Revised/Withdrawn/
supersede
d
Remaining
BSI
1 100 27 73
2 78 20 58
32 1 1
40 0 0
5 47 16 31
6 15 2 13
70 0 0
80 0 0
Total 176
Duplicates of all search strings 85
Remaining Total 91
Google
98 0 8
10 15 0 15
11 3 0 3
12 1 0 1
13 1 0 1
14 1 0 1
15 1 0 1
16 0 0 0
Total 30
Duplicates of all search strings 9
Remaining Total 21
Final Total from BSI and Goo
g
le 112
Then an analysis was conducted by considering
the full titles, scopes and descriptions of the 112
standards/frameworks to find whether they discuss
risks/managing risks in the considered domains. Dur-
ing the analysis it was discovered that most of the
standards that appeared in the initial list do not pre-
cisely discuss about risks/managing risks in the con-
sidered domains. For example: only 11 standards
from SS 1 discuss risks/managing risks and all the 11
standards are repeated in the list of standards col-
lected from SS 5. Hence, all the standards/frame-
works that do not cover the risks/managing risks of
considered domains were removed from the list.
Based on the analysis, the initial list of standards was
reduced to a secondary list of 18 standards/frame-
works (9 from BSI and 9 from Google).
Step 02: The selected eighteen standards and frame-
works were studied in depth to determine whether
they broadly discuss a Risk Management Process
(RMP) that can be applied to managing the risks in
the considered domains. Based on this exercise, nine
out of the eighteen standards and framework were se-
lected for the evaluation. The rationale for the selec-
tion and elimination of the standards and frameworks
is summarised in Table 3.
An Evaluation of Risk Management Standards and Frameworks for Assuring Data Security of Medical Device Software AI Models
93
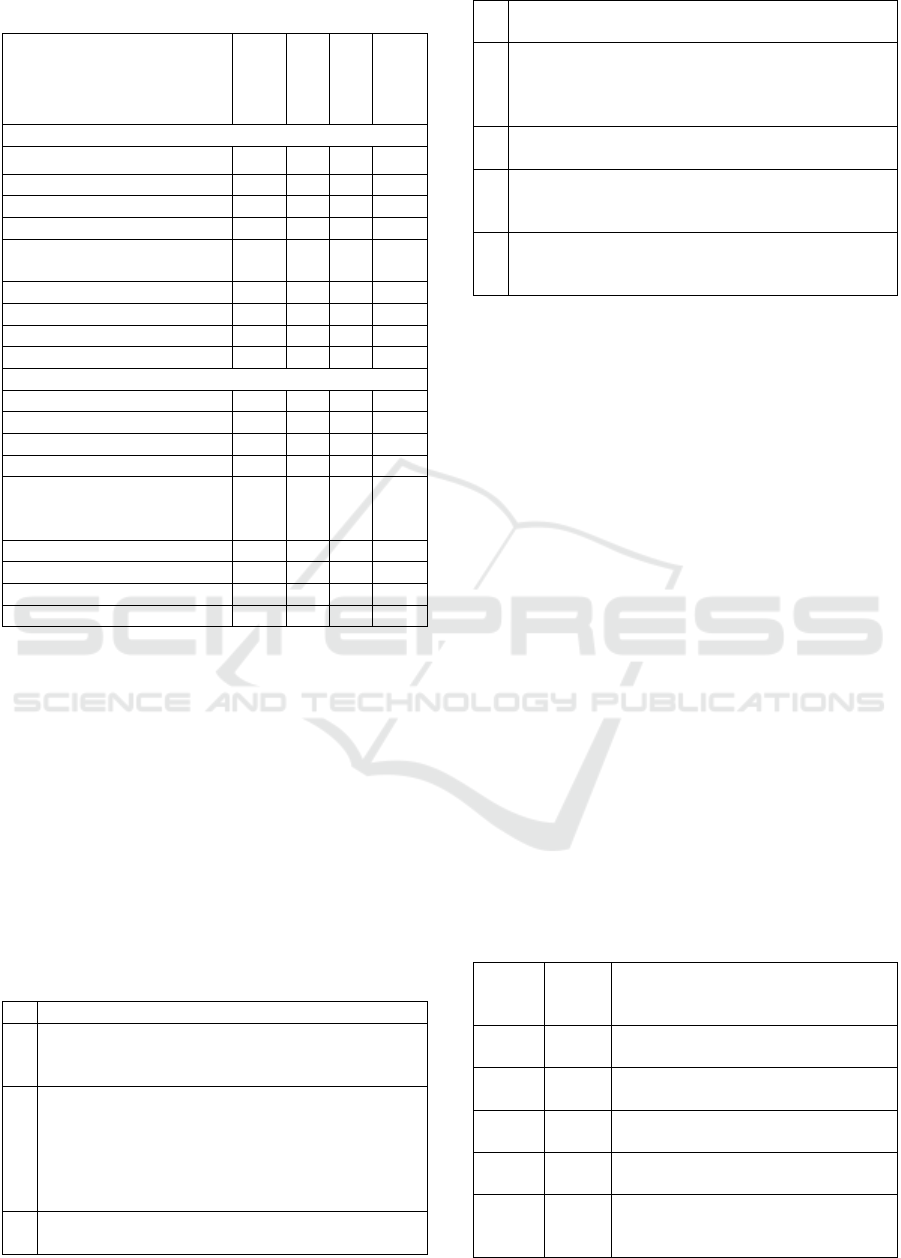
Table 3: Rationale for selection and elimination.
Standard/framework
Data/info
Sec
AI RMP
MDR MP
AI MD
RMP
Selected standards/frameworks
ISO/IEC 27005:2022
NIST SP 800-39
BS ISO/IEC 23894:2023
NIST AI 100-1
ENISA report (Securing ML
Al
g
orithms
)
ISO 14971
AAMI TIR57
IEC/TR 80002-1
BS/AAMI 34971
Eliminated standards/frameworks
ISO/IEC 38507
NIST SP 800-37
ISO/IEC 27001
ISO/IEC 27557
ITSRM² IT Security Risk
Management Methodology
V1.2
OCTAVE Alle
g
ro
OCTAVE FORTE
IEC 80001-1
MDCG 2019-16 Rev.1
Legend: - provide a RMP - does not provide a RMP
As detailed in Table 3, if the standard/framework pro-
vides a RMP in the considered domains it was in-
cluded for the evaluation. The ITSRM
2
was elimi-
nated as it provides the same RMP presented in
ISO/IEC 27005: 2022 standard.
Step 03: The evaluation criteria were developed
based on the existing literature related to risk manage-
ment standards/frameworks evaluation (ENISA,
2022a, 2022b; Karie et al., 2021; Marks, 2019) and
based on the identified adoption challenges detailed
in section 2. The developed criteria for the evaluation
are presented in Table 4.
Table 4: Criteria used for the evaluation.
Criteria
1 Does the standard/framework address data security
risk management of Medical Device Software AI
models? (Zhao & Yang, 2022)
2 Does the standard/framework outline adequate
phases of the risk management process? (ENISA,
2022a; Marks, 2019)
Adequate stages of the RMP were identified based
on the risk management process presented in ISO
31000:2018
–
Risk Mana
g
ement Guidelines.
3 Does the risk management standard/framework
p
rovide threat catalo
g
ues?
(
ENISA, 2022b
)
4 Does the risk management standard/framework
p
rovide vulnerabilit
y
catalo
g
ues?
(
ENISA, 2022b
)
5 Does the risk management standard/framework de-
scribe specific method for the calculation/estima-
tion of risk (i.e. formulas, scale, matrix)? (ENISA,
2022b, 2022a)
6 Does the standard/framework provide risk con-
trols?
(
ENISA, 2022b
)
7 Does the standard/framework provide implementa-
tion details for the risk controls? (Macmahon et al.,
2018; Mohammed et al., 2015; Yaqoob et al., 2019)
8 Does the standards/framework recommend refer-
ring to other supporting documentation for compre-
hensive/detailed information? (ENISA, 2022b)
Step 04: The nine standards/frameworks rigorously
studied against the evaluation criteria to identify
whether they meet the criteria or not. Based on the
evaluation, gaps in the nine standards/frameworks,
detailed in section 4 were identified. Furthermore,
new requirements for a developer friendly data secu-
rity risk management framework for MDS AI models
detailed in section 7 were identified.
4 RESULTS
This section presents the results of the evaluation con-
ducted on the nine selected standards.
4.1 Data/Information Security Risk
Management
4.1.1 ISO/IEC 27005:2022 - Guidance on
Managing Information Security Risks
This standard provides a RMP to conduct information
security risk management for all types of organisa-
tions regardless of type, size or sector (ISO/IEC,
2022). The results of the evaluation are presented in
Table 5.
Table 5: Results of ISO/IEC 27005 evaluation.
Criteria Meets
the
criteria
Description
1 No. It focuses on information security
risks mana
g
ement in
g
eneral.
2 Yes. It uses the same RMP outlined in the
ISO 31000:2018 standard.
3 Yes. It provides a list of possible threats in
Annex A (section A.2.5.1).
4 Yes. It provides a list of vulnerabilities in
Annex A
(
section A.2.5.2
)
.
5 Yes. Annex A provides a qualitative risk
matrix and a quantitative risk calcu-
lation scale.
ICSOFT 2024 - 19th International Conference on Software Technologies
94
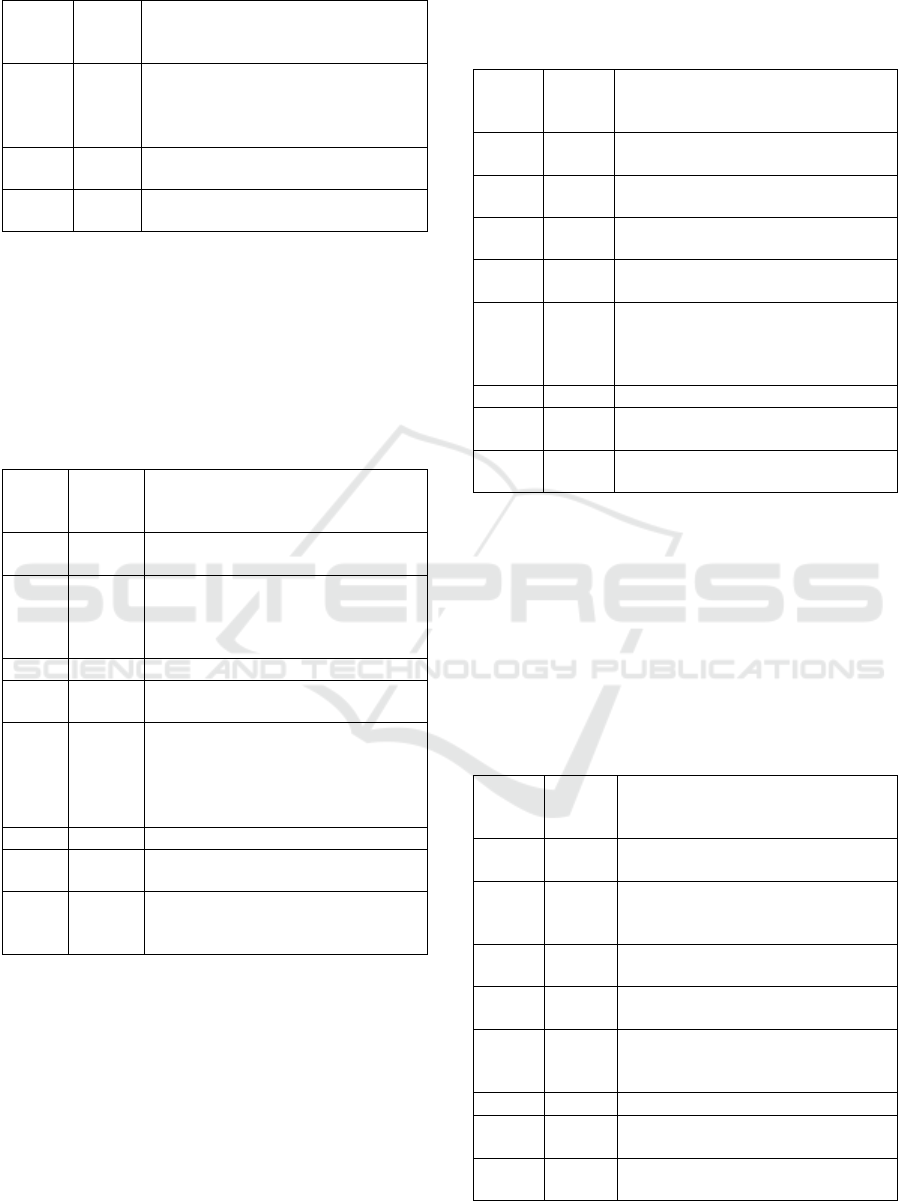
Table 5: Results of ISO/IEC 27005 evaluation (cont.).
Criteria Meets
the
criteria
Description
6 No It does not provide any risk controls.
However, it recommends referring
Annex A of ISO 27001 standard for
risk controls.
7 No. It does not provide implementation
details for risk controls.
8 Yes. It recommends referring ISO 27001
and ISO 31000 for more information
4.1.2 NIST SP 800-39 - Managing
Information Security Risks
This standard provides guidance on how organisations
can manage information security risks effectively
within their operating environments (NIST, 2011). The
results of the evaluation are presented in Table 6.
Table 6: Results of NIST SP 800-30 evaluation.
Criteria Meets
the
criteria
Description
1 No It focuses information security risks
mana
g
ement in
g
eneral.
2 Yes It presents a RMP comprised of four
core phases: framing/identifying
risk, assessing risk, responding to
risk and monitorin
g
risk.
3 No It onl
y
p
rovides threat sources.
4 No It does not provide any vulnerability
catalogues.
5 No It only states that risk is estimated by
combining the likelihood that a
threat will successfully exploit a vul-
nerability and result in an impact
with severit
y
of that im
p
act.
6 No It does not
p
rovide an
y
risk controls.
7 No It does not provide implementation
details for risk controls.
8 Yes It recommends referring NIST SP
800-37, NIST SP 800-53, NIST SP
800-53A and NIST SP 800-30.
4.2 AI Risk Management
4.2.1 ISO/IEC 23894:2023 - Information
Technology - Artificial intelligence -
Guidance on Risk Management
This standard outlines guidelines on how organisations
that develop, deploy, or utilise products and services
that employ AI can manage AI related risks (ISO/IEC,
2023). It assists organisations in integrating risk
management into their AI-related tasks and operations.
The results of the evaluation are presented in Table 7.
Table 7: Results of ISO/IEC 23894 evaluation.
Criteria Meets
the
criteria
Description
1 No It focuses on AI-related risk man-
a
g
ement in
g
eneral.
2 Yes It uses the same RMP outlined in the
ISO 31000:2018 standard.
3 No It does not provide any threat cata-
logues.
4 No It does not provide any vulnerability
catalo
g
ues.
5 No It only states that the organisations
should assess the likelihood of oc-
currence of events and outcomes
causin
g
risks.
6NoItdoes not
p
rovide an
y
risk controls.
7 No It does not provide implementation
details for risk controls.
8 Yes It recommends referring the ISO
31000 and ISO/IEC 22989:2022.
4.2.2 NIST AI 100-1 - Artificial Intelligence
Risk Management Framework (AI
RMF 1.0)
This framework provides guidance to organisations
designing, developing, deploying or using AI systems
on managing risks of AI and promoting trustworthy
development and use of AI systems (NIST, 2023).
The results of the evaluation are presented in Table 8.
Table 8: Results of NIST AI 100-1 evaluation.
Criteria
M
eets
the
criteria
Meet/does not meet the criteria
1 No It focuses on AI-related risk manage-
ment in general.
2 Yes The RMP outlined in the framework
has four core stages: govern, map,
measure and manage.
3 No It does not provide any threat cata-
logues.
4 No It does not provide any vulnerability
catalo
g
ues.
5 No It only states that the organisations
may need to develop new types of
risk measurements.
6 No It does not provide any risk controls.
7 No It does not provide implementation
details for risk controls.
8 Yes It recommends referring the NIST AI
RMF Pla
y
boo
k
.
An Evaluation of Risk Management Standards and Frameworks for Assuring Data Security of Medical Device Software AI Models
95
4.2.3 ENISA Report – Securing Machine
Learning Algorithms
This report identifies several cybersecurity threats
that could target ML algorithms, potential vulnerabil-
itiessecurity controls and some example techniques
for operational implementation of the security con-
trols (ENISA, 2021). The results of the evaluation are
presented in Table 9.
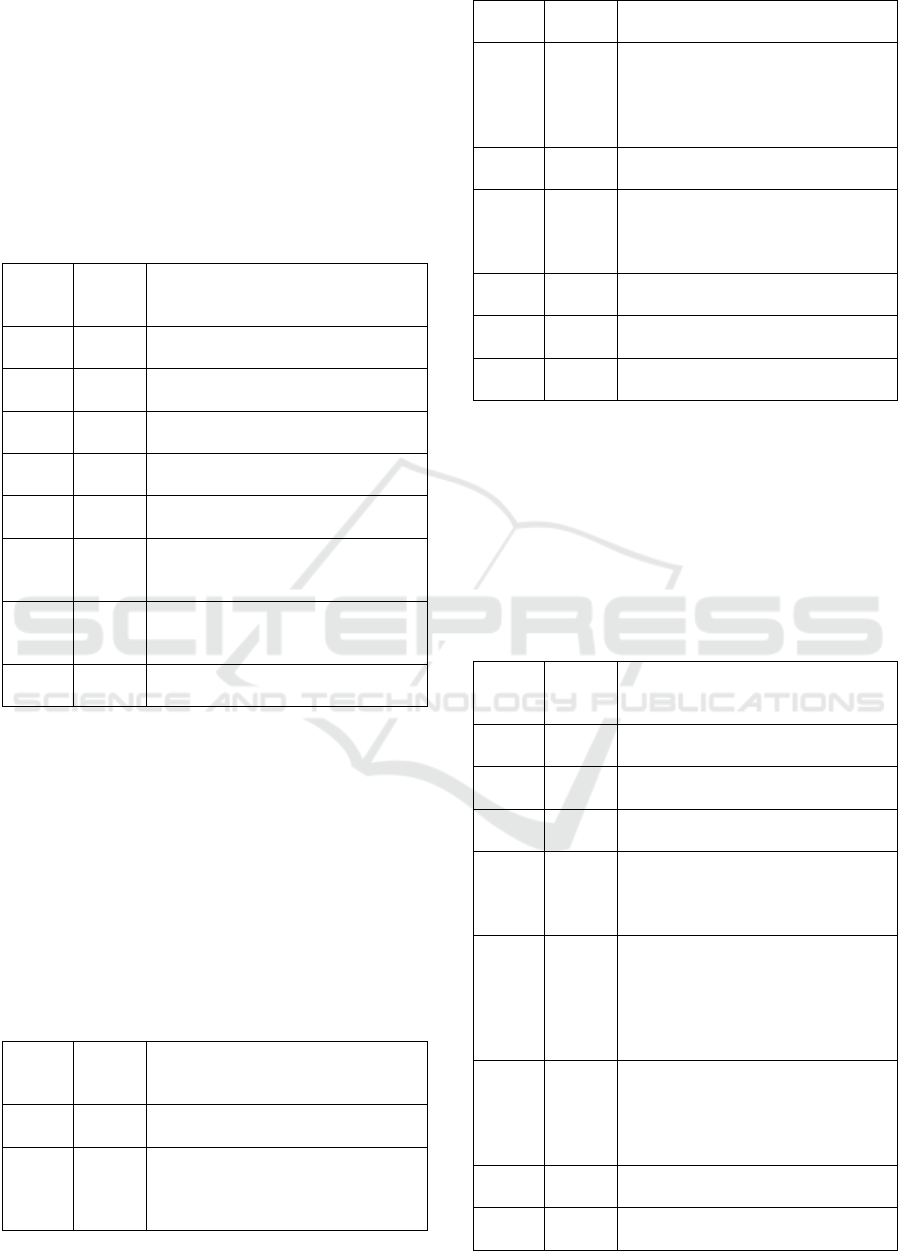
Table 9: Results of ENISA report evaluation.
Criteria Meets
the
criteria
Meet/does not meet the criteria
1 No It focuses on risks related to ML al-
g
orithms in
g
eneral AI/ML s
y
stems.
2 No It does not provide steps to conduct
risk management.
3 Yes It provides six high-level cybersecu-
rity threats and seven sub-threats.
4 Yes It provides potential vulnerabilities
associated with the identified threats.
5 No It does not provide any guidelines
for risk calculation/estimation.
6 Yes It provides a list of security controls
specific to attacks of ML algorithms
and
g
eneral attacks of AI s
y
stems.
7 Yes It provides some example tech-
niques for operational implementa-
tion of the securit
y
controls.
8 Yes It suggests referring ISO 27001/2
and NIST 800-53
4.3 Medical Device Risk Management
4.3.1 ISO 14971 - Medical Devices:
Application of Risk Management to
Medical Devices
This standard presents guidance to develop a RMP for
managing safety related risks of MDs, including Soft-
ware as a Medical Device (SaMD) and in vitro diag-
nostic MDs (ISO, 2019). The results of the evaluation
are presented in Table 10.
Table 10: Results of ISO 14971 evaluation.
Criteria Meets
the
criteria
Description
1 No It focuses on safety-related risks
management of medical devices.
2 Yes It outlines a RMP comprised of six
core phases: risk analysis, risk eval-
uation, risk control, evaluation of
overall residual risk, risk
management review and production
and
p
ost-
p
roduction activities.
3 No As it addresses safety-related risks,
Annex C provides a list of potential
hazards and foreseeable sequences
of events that might produce haz-
ardous situations and harm.
4 No It does not provide any vulnerability
catalogues
5 No It only states that the risk estimation
should be done by an analysis of the
probability of occurrence of harm
and the severity of the harm.
6 Yes It provides some general risk con-
trol o
p
tions.
7 No It does not provide implementation
details for risk controls.
8 Yes It suggests referring ISO 24971 and
ISO 13485.
4.3.2 AAMI TIR57 – Principles for Medical
Device Security Risk Management
This standard presents guidance for MD manufacturers
on methods that can be used to perform information se-
curity risk management for a MD based on the safety
RMP proposed by ISO 14971 (AAMI, 2016). The re-
sults of the evaluation are presented in Table 11.
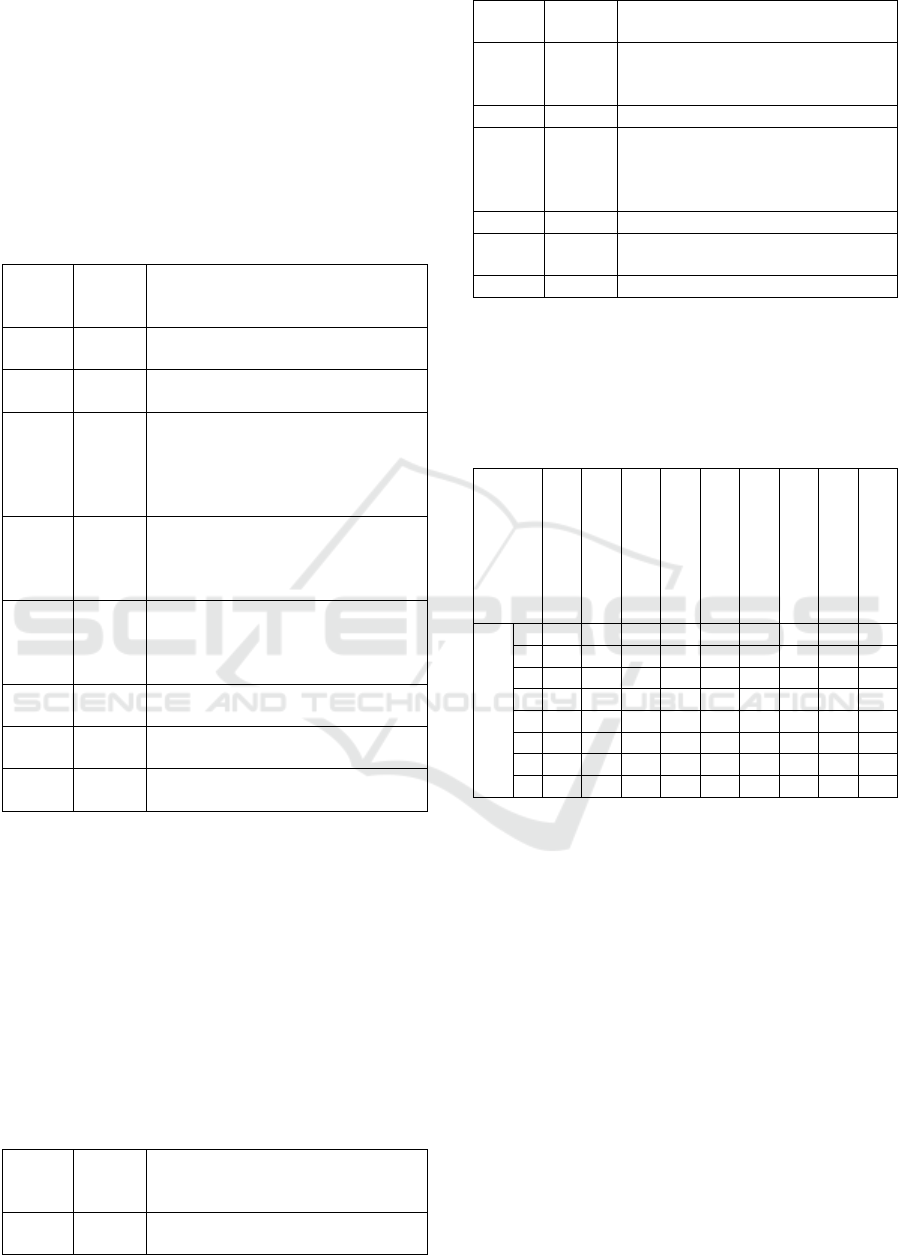
Table 11: Results of AAMI TIR 57 evaluation.
Criteria Meets
the
criteria
Description
1 No It focuses on information security
risk mana
g
ement of MDs.
2 Yes It provides the same phases outlined
in the RMP of ISO 14971 standard.
3 Yes It provides a list of possible threats
in Annex B.
4 Yes Annex B provides a list of vulnera-
bility classes can be used as a start-
ing point for the identification of
vulnerabilities
5 No It only states that the risk estimation
should be done by combining the
likelihood that a threat will success-
fully exploit a vulnerability and re-
sult in an impact with the severity of
that im
p
act.
6 Yes It provides some general security
risk control options. Annex E pro-
vides some practical examples of
risk control measures with respect
to a kidneato s
y
ste
m
.
7 No It does not provide implementation
details for securit
y
risk controls.
8 Yes It suggests referring NIST SP 800-
30 and ISO 14971.
ICSOFT 2024 - 19th International Conference on Software Technologies
96
4.3.3 IEC/TR 80002-1:2009 - Guidance on
the Application of ISO 14971 to
MediCal Device Software
This standard presents guidance on the application of
the RMP outlined in ISO 14971 to MDS with refer-
ence to IEC 62304 - Medical device software - Soft-
ware life cycle processes (ISO/IEC, 2009). The re-
sults of the evaluation are presented in Table 12.
Table 12: Results of IEC/TR 80002-1 evaluation.
Criteria Meets
the
criteria
Description
1 No It focuses on safety-related risk
management of MDS.
2 Yes It provides the same phases stated in
the RMP of the ISO 14971 standard.
3 No However, as it addresses safety-re-
lated risks, Annex A provides a list
of hazards and foreseeable se-
quences of events that can produce
hazardous situations and harm.
4 No As the standard address safety-re-
lated risks, Annex B, Table B.1 pro-
vides a list of functional areas of
software often related to hazar
d
s.
5 No It only states that the risk estimation
should be done by an analysis of the
probability of occurrence of harm
and the severit
y
of the harm.
6 Yes Annex B Table B.2 provides some
p
ossible risk control measures.
7 No It does not provide implementation
details for risk controls.
8 Yes It suggests referring ISO 14971 and
IEC 62304.
4.4 AI-Enabled Medical Device Risk
Management
4.4.1 AAMI 34971:2023 - Application of BS
EN ISO 14971 to Machine Learning in
Artificial Intelligence-Guide
This standard provides guidance for applying ISO
14971 for performing safety risk management in
AI/ML-enabled MDs (BSI, 2023). The results of the
evaluation are presented in Table 13.
Table 13: Results of ISO 34971 evaluation.
Criteria Meets
the
criteria
Description
1 No It focuses on safety risk manage-
ment of AI/ML enabled MDs
2 Yes It provides the same steps stated in
the ISO 14971 standard.
3 No As it addresses safety-related risks,
Annex B, Table B.1 gives examples
of ML-related hazards.
4 No It does not
p
rovide vulnerabilit
y
list
5 No It only states that the risk estimation
should be done by an analysis of the
probability of occurrence of harm
and the severit
y
of the harm.
6YesIt
p
rovides some ML risk controls.
7 No It does not provide implementation
details for securit
y
controls.
8YesItsu
gg
ests referrin
g
ISO 14971.
4.5 Summary of the Evaluation
A summary of the evaluation results is presented in
the following Table 14.
Table 14: Summary of the evaluation.
Standard/
framework
ISO/IEC 27005
NIST SP 800-39
ISO/IEC 23894
NIST AI 100-1
ENISA Report
ISO 14971
TIR 57
IEC/TR 80002-1
AAMI 34971
Criteria
1
2
3
4
5
6
7
8
Legend: - meet the criteria - does not meet the criteria
5 DISCUSSION
According to the results of the evaluation, it is evident
that currently there is no standard/framework that
specifically discusses data security risk management
of MDS AI models and the existing ones have several
gaps and implementation challenges.
Only three standards/frameworks provide threat
and vulnerability catalogues that can be used to un-
derstand potential threats and vulnerabilities. This is
a major gap as it is preferable to have knowledge of
the existing threats and vulnerabilities to implement a
RMP successfully.
Only one standard i.e., ISO/IEC 27005 provides a
structured method (risk matrix/risk scale/formula) for
the risk calculation/estimation of the risks. Risk
An Evaluation of Risk Management Standards and Frameworks for Assuring Data Security of Medical Device Software AI Models
97

calculation/estimation is essential to identify the risk
levels, severity of the risks and differentiate risks that
should be mitigated and that can be accepted. Hence,
it is identified as a primary gap in the existing stand-
ards/frameworks.
While five standards/frameworks provide some
possible examples of risk controls that can be used to
mitigate the identified threats and vulnerabilities,
none of them provide a detailed list of risk controls
that can be used during the implementation of the
standards/frameworks. Identifying risks is not suffi-
cient for a comprehensive RMP. It should provide
methods/approaches for controlling the identified
risks. Hence, this is identified as a major gap in the
existing standards/frameworks.
Only one standard/framework i.e., ENISA report
provides risk control implementation details that can
be used by the developers to implement risk controls.
However, these implementation details are not com-
prehensive and do not outline the necessary steps that
should be followed during the implementation of the
risk controls (it only provides some possible tech-
niques). Hence, this is identified as a primary imple-
mentation challenge of existing standards/frame-
works which makes the implementation process com-
plicated and time consuming.
All standards/frameworks recommend referring
to other standards or technical documentation for
more details. This is a major gap in the existing stand-
ards/frameworks which makes the implementation
process complex and time consuming. It necessitates
the developers to read several documents to get a
comprehensive understanding of the RMP provided
in the standard/framework. Hence, the identified gaps
and implementation challenges necessitate the devel-
opment of a new comprehensive, straightforward and
developer friendly data security risk management
framework for MDS AI models.
6 THREATS TO VALIDITY
As the evaluation was done by a single researcher,
there is a possibility for biases. The results may re-
quire validation by a panel of experts. Furthermore,
there is a possibility for biases in the search conducted
in Google due to the researcher’s browsing history.
7 CONCLUSION
Assuring data security is a key concern that should be
considered when developing MDS AI models and
there should be a well-established and structured way
to manage the risk caused by data security compro-
mises. Implementing a security risk management
standard/framework is one of the most effective ways
that is used to manage the risks effectively. However,
standards/frameworks that specifically address data
security risk management of MDS AI models do not
exist. Existing risk management standards/frame-
works have several gaps and implementation chal-
lenges which necessitates the development of a new
developer friendly data security risk management
framework for MDS AI models.
This paper identifies the need of the development
of a new developer friendly data security risk man-
agement framework for MDS AI models. This evalu-
ation was conducted as part of a PhD research which
proposes to develop a new data security risk manage-
ment framework for MDS AI models. The new
framework should contain a comprehensive list of
data security threats and vulnerabilities, a structured
method for risk calculation/estimation, and a compre-
hensive list of security risk controls with respective
implementation details. Moreover, the framework
should be as all-inclusive as possible, with minimum
references to other standards/documentations which
makes the implementation process more complex and
complicated than need be. The findings of this study
can help researchers, developers, and other relevant
stakeholders bring on further discussions on the de-
velopment of new data security risk management
standard/framework for MDS AI models and thus
contribute to AI’s trustworthiness and its adoption
within MDS development industry and society.
ACKNOWLEDGEMENTS
This study is financially supported by Ireland’s Higher Ed-
ucation Authority (HEA) Technological University Trans-
formation Fund (TUTF).
REFERENCES
AAMI. (2016). AAMI TIR 57: Principles for medical device
security risk management. Association for the Ad-
vancement of Medical Instrumentation (AAMI).
Benz, M., & Chatterjee, D. (2020). Calculated risk? A cy-
bersecurity evaluation tool for SMEs. Business Hori-
zons, 63(4), 531–540. https://doi.org/10.1016/j.bus
hor.2020.03.010
BSI. (2023). AAMI 34971: Application of BS EN ISO 14971
to machine learning in artificial intelligence ‒ Guide.
Chen, J. Q., & Benusa, A. (2017). HIPAA security compli-
ance challenges: The case for small healthcare
ICSOFT 2024 - 19th International Conference on Software Technologies
98

providers. Int. J. of Healthcare Manage., 10(2), 135–
146. https://doi.org/10.1080/20479700.2016.1270875
Chen, M., & Decary, M. (2020). Artificial Intelligence in
healthcare: an essential guide for health leaders.
Healthcare Manage. Forum, 33(1), 10–18.
https://doi.org/10.1177/0840470419873123
Coventry, L., & Branley, D. (2018). Cybersecurity in
healthcare: a narrative review of trends, threats and
ways forward. Maturitas, 113, 48–52.
https://doi.org/10.1016/j.maturitas.2018.04.008
Djebbar, F., & Nordstrom, K. (2023). A Comparative Anal-
ysis of Industrial Cybersecurity Standards. IEEE Ac-
cess, 11(July), 85315–85332. https://doi.org/10.1109/
ACCESS.2023.3303205
ENISA. (2021). Securing Machine Learning Algorithms
(Issue December). https://doi.org/10.2824/874249
ENISA. (2022a). Compendium of risk management frame-
works with potential interoperability (Issue January).
https://doi.org/10.2824/75906
ENISA. (2022b). Inteoperable EU Risk Management
Framework - Methodology for assessment of interoper-
ability among risk management frameworks and meth-
odologies (Issue January).
Eom, D., & Lee, H. (2018). A Holistic Approach to Explor-
ing the Divided Standards Landscape in E-Health Re-
search. IEEE Communications Standards Magazine,
2(4), 20–25. https://doi.org/10.1109/MCOMSTD.20
18.1800007
EPRS. (2022). Artificial Intelligence in healthcare: appli-
cations, risks, and ethical and societal impacts.
FDA. (2020). Artificial Intelligence (AI) and Machine
Learning (ML) in medical devices - executive summary
for the patient engagement advisory committee meet-
ing. Ml.
Han, L., Liu, J., Evans, R., Song, Y., & Ma, J. (2020). Fac-
tors Influencing the Adoption of Health Information
Standards in Health Care Organizations: A Systematic
Review Based on Best Fit Framework Synthesis. JMIR
Medical Informatics, 8(5), e17334. https://doi.org/
10.2196/17334
IMDRF SaMD Working Group. (2013). Software as a Med-
ical Device (SaMD): key definitions.
ISO. (2019). ISO 14971 - Medical devices - Application of
risk management to medical devices, International
Standard (Vol. 2000).
ISO/IEC. (2009). IEC/TR 80002-1:2009 - Guidance on the
application of ISO 14971 to medical device software.
https://doi.org/10.2345/9781570203718.ch1
ISO/IEC. (2022). ISO/IEC 27005:2022 - Information secu-
rity, cybersecurity and privacy protection — Guidance
on managing information security risks.
ISO/IEC. (2023).
ISO/IEC 23894:2023 - Information tech-
nology — Artificial intelligence — Guidance on risk
management.
Karie, N. M., Sahri, N. M., Yang, W., Valli, C., & Kebande,
V. R. (2021). A Review of Security Standards and
Frameworks for IoT-Based Smart Environments. IEEE
Access, 9, 121975–121995. https://doi.org/10.1109/
ACCESS.2021.3109886
Macmahon, S., Cooper, T., & McCaffery, F. (2018). Revis-
ing IEC 80001-1: risk management of health infor-
mation technology systems. Comput. Standards & In-
terfaces, 60(May), 67–72. https://doi.org/
https://doi.org/10.1016/j.csi.2018.04.013
Marks, L. (2019). The optimal risk management frame-
work. ISACA Journal, 1, 40–45.
Mohammed, D., Mariani, R., & Mohammed, S. (2015). Cy-
bersecurity challenges and compliance issues within the
U.S. healthcare sector. Int. J. of Business and Social
Res., 5(2), 55–66.
Naumov, S., & Kabanov, I. (2016). Dynamic framework for
assessing cyber security risks in a changing environ-
ment. 2016 International Conference on Information
Science and Communications Technologies, ICISCT
2016, 1–4. https://doi.org/10.1109/ICISCT.2016.777
7406
NIST. (2011). NIST SP800-39 Managing Information Se-
curity Risk. In Nist Special Publication (Issue March).
http://csrc.nist.gov/publications/nistpubs/800-39/SP80
0-39-final.pdf
NIST. (2023). Artificial Intelligence Risk Management
NIST AI 100-1 Artificial Intelligence Risk Management.
Siddiqui, F., Khan, R., & Sezer, S. (2021). Bird’s-eye view
on the Automotive Cybersecurity Landscape Chal-
lenges in adopting AI/ML. 2021 6th International Con-
ference on Fog and Mobile Edge Computing, FMEC
2021, 1–6. https://doi.org/10.1109/FMEC54266.2021.9
732568
Spatharou, A., Heironimus, S., & Jenkins, J. (2020). Trans-
forming healthcare with AI. In Reimagining Businesses
with AI (Issue March). https://doi.org/10.1002/9781
119709183.ch3
Yaqoob, T., Abbas, H., & Atiquzzaman, M. (2019). Secu-
rity Vulnerabilities, Attacks, Countermeasures, and
Regulations of Networked Medical Devices-A Review.
IEEE Communications Surveys and Tutorials, 21(4),
3723–3768.
Zhao, H., & Yang, G. (2022). Information security and le-
gal ethics of Artificial Intelligence medical devices.
Forest Chemicals Review, 236–245.
An Evaluation of Risk Management Standards and Frameworks for Assuring Data Security of Medical Device Software AI Models
99
