
A Composition Algebra for Decentralized Enforcement of Access Control
Policies with an Application to Vehicular Networks
Peter Amthor
1 a
and Ren
´
e Gorges
2 b
1
Technische Universit
¨
at Ilmenau, Ilmenau, Germany
2
Friedrich Schiller University Jena, Jena, Germany
Keywords:
Security Policy, Composition, Access Control, ABAC, Boolean Algebra, Vehicular Network, Smart Vehicles.
Abstract:
Highly volatile and open distributed systems typically incorporate a significant amount of secure interac-
tions between autonomous agents. This is especially true for vehicular networks, where smart or autonomous
vehicles rely on information shared with each other or traffic infrastructure. However, controlling such decen-
tralized interaction with respect to security restrictions requires a common definition of a temporary composite
policy. As a first step towards this goal, this paper presents ACCA, a lightweight extension of Boolean algebra
which allows to precisely specify how access control policies should be composed. It enables to build vehic-
ular network systems that retain independence and autonomy of their participants while reducing the amount
of communication about policy knowledge. An implementation of a simulation prototype of ACCA serves as
a first, promising step towards tailoring the compositional semantics to specific use cases.
1 INTRODUCTION
Access control (AC) in open, distributed systems crit-
ically relies on the trustworthy and correct enforce-
ment of individual rules about assets (access control
policies). Such rules, in common terminology, pre-
cisely specify a mandatory condition to allow a sub-
ject (accessing IT activity) any operation (such as a
remote procedure call) on an object (some resource
abstraction). Especially in volatile, largely dynamic
scenarios such as in ubiquitous and mobile comput-
ing or wireless networking, these policies are speci-
fied within domains: subjects that exact (physically
or legally) control over objects and may provide other
subjects access to them by the means of specific op-
erations. As a whole, systems incorporating access
control logic extending over multiple such domain-
specific policies are logically considered a composite
policy group (or just a group) (K
¨
uhnhauser, 1999).
In practice however, correctly evaluating access
control rules in such scenarios is significantly com-
plicated by three observations:
1. spontaneous formation and mutation of a group
w. r. t. its member domains,
a
https://orcid.org/0000-0001-7711-4450
b
https://orcid.org/0009-0001-3525-8445
2. incomplete knowledge of each policy-enforcing
domain about policies defined in a foreign do-
main,
3. uncertainty about formal correctness assumptions
that any policy should satisfy from their domain’s
point of interest.
They become especially obvious in the communi-
cation between partially or fully autonomous cars or
smart vehicles (SVs). Applications where such ve-
hicles rely on information exchange and interopera-
tion with other nearby vehicles and even traffic infras-
tructure are commonly summarized under the term
vehicle-to-everything (V2X) communication. Fac-
ing mission-critical security and safety requirements,
these distributed systems heavily rely on a sound and
correct AC policy enforcement; at the same time, they
illustrate the impact of two of the above-mentioned
complications:
(1.) Groups are highly volatile in both a spatial
and a temporal sense. This renders both the prop-
erties (such as physical location or speed) and the
mere availability (presence in the system) of physi-
cally backed entities such as vehicles or their occu-
pants highly dynamic.
(2.) Following from the previous observation but
also from limited communication volume over the
available infrastructure (such as vehicular ad-hoc net-
78
Amthor, P. and Gorges, R.
A Composition Algebra for Decentralized Enforcement of Access Control Policies with an Application to Vehicular Networks.
DOI: 10.5220/0012758900003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 78-90
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

works (VANETs) (Hussein et al., 2022; Sharma and
Kaul, 2021)), domains generally cannot make access
decisions about shared resources (such as a dashboard
camera media stream) based on complete knowledge
of all group members and their respective local pol-
icy. As an example, streaming a camera image to
another vehicle or a roadside unit (RSU) for traffic
surveillance would be allowed from the camera’s ve-
hicle owner’s perspective, but not from the perspec-
tive of another vehicle whose license plate or occu-
pants’ faces would be in that footage. While the group
policy could be built rather intuitively by conjunction
of both vehicles’ policy decisions, in practice the ac-
cess domain (with the camera on board) would need
to first issue a secondary request to all other domains
of possibly affected nearby vehicles.
Concerning the third observation, it should be
noted that proving policy correctness is a problem
not restricted to the scenarios characterized above.
Nevertheless, when policy enforcement is done in a
decentralized manner – in contrast to a centralized,
non-circumventable, well-protected reference moni-
tor (Anderson, 1972) as e. g. in operating systems –
specific correctness properties must be demonstrable
over all members of a group. In spite of a plethora
of AC models tailored to analyzing and proving such
properties, no widely accepted formalism exists for
this purpose in the context of open, distributed sys-
tems and especially the V2X domain.
This problem field motivates our following contri-
butions on fundamental AC policy composition logic:
• definition of a V2X system model and, based on
it, a precise problem statement adaptable to other
applications that share the above observations;
• design and definition of ACCA (Access Control
Composition Algebra), a composition algebra for
dynamic attribute-based access control (ABAC)
models written in the DABAC modeling scheme
(Schlegel and Amthor, 2023) that addresses these
observations;
• a prototypical implementation of ACCA as a pol-
icy composition simulator, which allows for a first
understanding of runtime behavior and possible
applications of ACCA under different real-world
scenarios.
The remainder of this paper is organized as fol-
lows: In § 2, we substantiate the policy composition
problem in V2X applications with a motivating sce-
nario, which is then generalized to characteristics of
the underlying system (§ 3) and of the precise prob-
lem addressed (§ 4). We then give a brief overview
of dynamic attribute-based access control (DABAC),
an attribute-focused modeling scheme to describe AC
policy logic in § 5, and the actual algebra definition
including a formal specification of composition oper-
ators in § 6. As a first step towards feasibility assess-
ment for V2X applications, § 7 provides simulation
results on a prototypical implementation using a vir-
tual network environment. We review relevant related
literature in § 8 and conlude with § 9.
2 V2X SCENARIO
In the following section we clarify our problem state-
ment in the context of V2X communication. It should
be noted that, after a brief review of background ter-
minology, the presented scenario is just one specific
example from a plethora of use cases in the literature.
We will discuss the running use case in this paper in
detail (§ 2.3), but also hint at other scenarios equally
relevant to the policy composition problem.
2.1 Background
The term V2X (vehicle-to-everything) describes tech-
nologies which enable vehicles such as cars, trains or
airplanes to communicate with each other as well as
with road infrastructure and pedestrians (Arena and
Pau, 2019; Mazzola et al., 2015; Hussein et al., 2022).
These smart vehicles (SVs) are equipped with a vari-
ety of communication devices as well as sensors, e. g.
cameras. Naturally, all of which manage data that po-
tentially needs to be protected by an AC policy.
A common approach to integrating SVs into an
architecture which supports V2X communication and
its applications is vehicular edge computing (VEC)
(Meneguette et al., 2021). This architecture puts
RSUs, i. e. stationary communication units like traffic
lights, at the edge of a cloud network. These com-
municate with, on one side, the mobile SVs and on
the other side with cloud-based services (Zhou et al.,
2022; Yang et al., 2022). The motivation for this de-
sign is the limited computational power and storage
capacities of the SVs as well as the RSUs. SVs dele-
gate computationally or storage-wise intensive tasks
to RSUs, which in turn may delegate them to the
cloud for more elaborate tasks, e. g. such involving
augmented reality. Additionally, the cloud can utilize
a global view of the vehicles’ area (Liu et al., 2020).
2.2 Motivating Scenario
From several real V2X applications described in the
literature (Hussein et al., 2022; Alsarra et al., 2019),
consider the following scenario to exemplify the ne-
cessity of multi-stakeholders policy composition. The
A Composition Algebra for Decentralized Enforcement of Access Control Policies with an Application to Vehicular Networks
79

scenario focuses on coordinating regional traffic fol-
lowing a large-scale natural disaster, e. g. an earth-
quake. Disaster relief and emergency services typi-
cally rely on any real-time source of information, in-
cluding data provided by private SVs such as camera
images and location data. The policy involved here
is from the family of break-glass AC policies (Mari-
novic et al., 2011): Access to sensitive data should
only be permitted to specific subjects (or rather, de-
pending on the model, their roles) that are princi-
pals of emergency services and only in presence of an
emergency; at the same time, it must not be deniable
either under such conditions.
1
2.3 Running Use Case
More precisely, the above scenario can be generalized
to the following use case. Given three classes of par-
ties in an urban transportation setting:
• I: urban traffic infrastructure, which provides ser-
vices such as parking lot allocation and navigation
through mostly immovable RSUs,
• V: private and commercial vehicles,
• E: emergency services vehicles, such as firefight-
ers or ambulances.
Each individual stakeholder participating in this set-
ting would belong to exactly one of these classes and
thus form a domain on its own. While each individual
vehicle in the class V forms its own domain d
i
, we as-
sume exactly one domain d
I
and d
E
for the other two,
respectively.
Assume that, within a spatially delimited area
(e. g. bounded by wireless communication range) and
at a specific point in time, a vehicle v from V, which
is equipped with various sensors such as cameras,
records data which can be helpful for parties from E
by enabling them a quick and appropriate response to
a specific emergency situation. If the relevant data
can be transmitted to those parties (possibly through
the urban infrastructure), it should be. Consequently,
parties from E may request access to data within v’s
domain d
v
, which, if granted, would allow the transfer
of (possibly sensitive) data from d
v
to d
E
.
This use case includes two stakeholders with op-
posing interests: The owners and users of SVs want
to share as little sensitive information as possible, but
the emergency personnel has to use their sensor data
for the purpose of public safety, e. g. to aid a coor-
dinated evacuation and thus save human lives. Com-
1
The post-operational obligations typical for break-
glass policies – e. g. logging emergency vehicle UIDs and
archiving their camera footage – are relevant in practice, but
ignored in the discussion here for the sake of clarity.
bining these two goals requires the definition of an
access control policy which is a combination of both
stakeholders’ individual policies. Notably, this com-
bined policy will make decisions depending on (1)
external circumstances, e. g. emergency notifications
received by cell broadcast infrastructure, and (2) sub-
ject metadata, as the aforementioned (cryptographi-
cally authenticated) emergency role certificate.
The resulting policy is an example for a dynamic
composite policy, whereas the individual polices are
called component policies.
2.4 Other Scenarios
Apart from the scenario outlined above, which we
will refer to throughout the rest of this paper, pol-
icy composition problems are common in a number of
other V2X scenarios. As an example, use of a civil-
ian’s dashboard camera data to track down criminals
as described in (Alsarra et al., 2019) comes with the
same implications as the disaster relief scenario. An-
other scenario is outlined in (Hussein et al., 2022):
Consider a city offering an electronic parking guid-
ance system. A driver looking for a parking spot
can let their car query the system for information on
nearby parking spots. The parking guidance system
would then request necessary data from the vehicle,
for example its dimensions, mass, destination and po-
tentially license number. This may be a problematic
access though, e. g. in case the vehicle is commer-
cially operated and the owner does not consent to this
data to be passed to the system. When, on the other
hand, the driver’s highest priority is to find a parking
spot and to arrive at a business appointment on time,
multiple stakeholders with opposing interests can be
found in this scenario. A solution to this conflict by
composing their access control policies needs to re-
flect these interests.
3 SYSTEM MODEL
We describe the AC characteristics of an open, het-
erogeneous and spatially dynamic distributed system
based on VEC infrastructure by the following model.
Each stakeholder (such as drivers and owners of
SVs – who might be different – in the scenario of
§ 2.3) forms a domain. It can be intuitively un-
derstood as a collection of subjects and objects that
are spatially bound to each other and thus share co-
located (e. g. memory-based) communication infras-
tructure. More formally, we define a domain d =
⟨
E
d
,Op
d
⟩
as a tuple of entities from a set E
d
and op-
erations from a set Op
d
. Entities might be principals
SECRYPT 2024 - 21st International Conference on Security and Cryptography
80

d
1
d
2
d
3
⟨stream_dashcam, u21, v12, paramedic_r, "50.682,10.940"⟩
Figure 1: Example scenario for a group G with three do-
mains d
1...3
, one out of either private vehicles (blue), emer-
gency services (yellow), and traffic infrastructure (green).
(i. e. abstractions of human users), subjects acting on
their behalf, or technical or logical assets or other ob-
jects in the scope of d.
2
In the running use case, these
include e. g. emergency personnel, SV users, passive
occupants of emergency vehicles etc. (cf. Fig. 1). Op-
erations specified in Op
d
identify any possible techni-
cal activities that involve entities in E
d
. This includes
operations known to affect the domain’s entities, but
not necessarily implemented inside the domain.
3
All
domains whose entities, for a specific point in time,
might interact with each other within the same com-
munication infrastructure (such as a vehicular net-
work), form a group G . We define E
G
=
S
d∈G
E
d
as the group’s entity set and Op
G
=
S
d∈G
Op
d
as its
set of operations. In general and for two subsequent,
temporally discrete points in time (states of the sys-
tem) G and G
′
, we assume that G ̸= G
′
. This models
dynamic group formation und spontaneous mutation
(i. e. SVs joining or leaving the group at any time).
An access request is a tuple
⟨
op,a
1
,... ,a
n
⟩
, de-
scribing an operation op ∈ Op
G
that should be per-
formed for a vector [a
i
]
n
i=1
of parameters (specific
to each op), which might be unified with identifiers
from E
G
or any operation-specific value. Notably,
this includes – additional to unique identifiers (UIDs)
– attributes of entities or the physical environment.
Fig. 1 shows an exemplary access request with op =
stream dashcam and various parameters: UID of the
calling entity u21, UID of d
1
’s dashboard camera con-
troller v12, and two more attribute values to describe
the caller’s role (paramedic r) and GPS coordinates as
environmental context of the request.
A self-contained specification of AC rules, which
2
Note that we intentionally use “entity” to subsume the
intuitive, yet formally more restrictive distinction between
subjects (always active) and objects (always passive).
3
Our earlier example of recording video footage of an
SV, which is obviously not recorded from within its do-
main, may require consent based on its domain’s policy.
completely defines for any possible access request
⟨
op
d
,a
1
,. .. ,a
n
⟩
,op
d
∈ Op
d
if the modeled opera-
tion is allowed to be performed, is called d’s do-
main policy P
d
. Analogously, P
G
for Op
G
is called
the composite policy of group G . Finally, an ac-
cess control function (ACF) f
P
is a mapping defined
as
⟨
op,a
1
,. .. ,a
n
⟩
7→ true iff operation op is allowed
with parameters [a
1
,. .. ,a
n
] by policy P, which might
be a domain policy or a composite policy. Any AC
decision modeled by f
P
requires, from a subject’s
perspective, only operation-specific parameters, but
no knowledge about the (current state of the) group
and its composite policy. This enables a middleware
framework to transparently implement group man-
agement and composite policy evaluation.
4 PROBLEM STATEMENT
We now describe the general logical composition
problem for spatially and/or temporally independent
AC domains wich are autonomous in their respective
local policies. It is characterized by the following
properties:
Dynamic Group A group is dynamically formed
and mutated by adding or removing domains. Pol-
icy composition must be done in an ad-hoc man-
ner.
Transparent Enforcement Policy composition is
transparent for all entities to allow for group-
agnostic domain interfaces.
4
Policy composition can be recursive, which guar-
antees the same AC semantics for requests to both
a local and the composite policy.
Domain Autonomy For any access request against
the composite policy, only such component poli-
cies whose domains include entities from the re-
quest should be taken into account. This ensures
that any request whose entities are all local to one
domain is handled identical by the composite pol-
icy and that domain’s component policy; at the
same time, it prevents completely unrelated com-
ponent policies from making non-meaningful de-
cisions.
Policy Model A generic
5
formal language is agreed
upon by all domains, which is used to precisely
express and possibly verify component policies as
well as the composite policy.
4
This enables e. g. general-purpose application software
to act as an entity in the composite policy.
5
In a sense that all possible domains of some applica-
tion, such as V2X, can express their respective local poli-
cies.
A Composition Algebra for Decentralized Enforcement of Access Control Policies with an Application to Vehicular Networks
81

For the design of ACCA, we make the follow-
ing underlying assumptions. Their establishment by
communication infrastructure and hard- and software
stack in each participating domain is regarded subject
to complementary technology:
First, for any access request against the compos-
ite policy, all domains which include entities from
the request must enforce the composite policy’s de-
cision. This ensures that no domain might ignore the
composite policy and can be ensured e. g. through a
trusted execution environment (TEE) infrastructure.
Second, entity UIDs and metadata for attribution of
entities are authentic. This can be cryptographically
ensured. Third, communication between all domains
is non-repudiable and never fails, which can be ad-
dressed by a trusted, fault-tolerant middleware. It
should be mentioned that all these complementary
components will inevitably contribute to the size of
a system’s trusted computing base (TCB).
5 ACCESS CONTROL POLICY
MODEL
As already motivated before, both the component
policies and a composite policy should be open to
formal analyses of correctness properties. Amongst
the most challenging of these are dynamic proper-
ties, i. e. state reachability problems such as HRU
safety (Harrison et al., 1975; Sandhu, 1992), work-
flow satisfiability (Khan and Fong, 2012), or delega-
tion of trust (Li et al., 2005). So far, however, open
distributed systems largely rely on policy specifica-
tion languages such as XACML (OASIS, 2013) or
NGAC (INCITS, 2013; Ferraiolo et al., 2016) which
are based on ABAC semantics: since attributed-based
policies can specify rules without any prior knowl-
edge about subjects, objects, or other entities present
during enforcement time, they are by design a natural
choice for V2X access control (Ashutosh et al., 2023;
Gupta et al., 2019). Unfortunately, none of them is
formally accessible to the analysis of dynamic cor-
rectness properties.
To formally express both the knowledge and com-
positional semantics of ABAC policies, we there-
fore choose a modeling scheme which is (1) flexi-
ble enough to allow for diverse attribution semantics
(cf. § 2), (2) applicable to V2X as our target appli-
cation domain, and (3) accessible to formal verifica-
tion of dynamic properties. All these requirements
are satisfied by DABAC, which we will outline in the
remainder of this section.
5.1 DABAC Modeling Scheme
DABAC is a modeling scheme for ABAC policies
proposed in (Schlegel and Amthor, 2021). Its focus
is to reason about dynamic changes of a system con-
trolled by an ABAC policy. We will now briefly reit-
erate those aspects of DABAC relevant to this work.
Definition 1 (DABAC Policy). A DABAC
Policy with indirection degree i
max
is a tuple
EN,EN
ext
,AV,AV
ext
,AA, AA
ext
,AR
, where
• EN =
{
E
1
,. .. ,E
n
}
is a family of entity sets,
• AV =
S
i
max
i=0
AV
i
are families of attribute value sets,
AV
i
=
{
V
1
,. .. ,V
n
i
}
,
• AA =
S
i
max
i=0
AA
i
are families of attribute associa-
tion sets, where AA
0
=
att : E → V
′
0
E ∈ EN
and AA
i
=
{
att : V
i−1
→ V
′
i
|
V
i−1
∈ AV
i−1
}
such
that V
′
i
is either a set in AV
i
or a power set of a set
in AV
i
,
• Perm is a set of access permissions,
• AR =
auth
p
: [v
1
,. .. ,v
n
p
] → B,n
p
∈ N
is a set
of authorization predicates (or “access rules”), ex-
actly one for each permission p ∈ Perm, which
map a finite set of arguments v
k
to a Boolean ac-
cess decision such that ∀k ∈ [1,n
p
] : ∃V
k
∈ AV ∪
AV
ext
∧ (v
k
∈ V
k
∨ v
k
∈ 2
V
k
),
and 0 ≤ i ≤ i
max
. Analogous to above, EN
ext
, AV
ext
and AA
ext
denote policy-external entity sets, attribute
value sets, and attribute association sets.
DABAC distinguishes between entities, attribute
values and attribute associations which are physically
within the local domain (internal) and those which are
not. The latter are termed external and cannot be in-
fluenced from inside the local domain. Furthermore,
it is assumed that this distinction yields disjoint sets
of internal and external entities, attribute values and
attribute associations respectively.
In definition 1, the indirection degree of attribute
values is used. This term describes a number i ∈ N
which makes indirect attribution possible. To un-
derstand the mindset behind this design, consider
attributes which are more complex than an atomic
value, like a record containing multiple pieces of in-
formation on a car, including for example the year of
construction, vehicle identification number, fuel type
and more. It might not be desirable to split this record
into the individual values that compose it – especially
as there might be dependencies among them – but
rather treat it as one structured value. To achieve
this, such records can be modeled as attributes which
themselves have attributes, namely the elements of
the respective record. In a DABAC policy, this is done
through indirect attribution. Attribute values with in-
direction degree i = 0 are elements from or subsets
SECRYPT 2024 - 21st International Conference on Security and Cryptography
82

of a set from AV
0
or AV
ext
0
and hence atomic values.
A value i > 0 means that the corresponding attribute
value is composed of attribute values of the indirec-
tion degree i − 1, that is a structured value. In order
to determine the value of an attribute with indirection
degree i > 0, a mapping from AA
i
or AA
ext
i
has to be
evaluated. It should be noted that attribute values of
any indirection degree can be a single or a set of (pos-
sibly structured) values.
Finally, the set AR determines the rules by which
accesses are determined to be legal or not. Its el-
ements are mappings auth
p
for every permission p
from the set Perm of all permissions, which map n
p
at-
tribute values to a Boolean value. Given the attribute
values [v
i
]
n
p
i=1
, for example through an entity’s access
request and the physical environment, the permission
p ∈ Perm is granted if and only if auth
p
([v
i
]
n
p
i=1
) =
true. In order to execute an operation, all permissions
required for that operation must be granted.
Given an operation op ∈ OP and parameters
[a
i
]
n
op
i=1
required for it, the ACF of a DABAC policy
should decide whether or not the thereby requested
access is legal, where OP is the set of all operations
and n
op
denotes the number of parameters required
for op. For this decision to be made, it is necessary to
evaluate auth
p
∈ AR for every permission p ∈ Perm
required to execute op. However, this requires to
map the parameters [a
i
]
n
op
i=1
to according parameters of
auth
p
. This is achieved by mappings which are part of
the previously mentioned automaton’s state transition
function, which is not shown here. We use the no-
tation
a
1
,. .. ,a
n
op
|= op.PRE, similar to (Schlegel
and Amthor, 2021), which describes a Boolean for-
mula with variables X
1
,. .. ,X
m
op
that is satisfied by an
assignment ∀i ∈ [1,m
op
] : ∃ j ∈ [1,n
op
] : X
i
:= a
j
. Any
such formula must be a conjunction of those auth
p
which have to be satisfied in order for op to be per-
mitted. Finally, both the operation and its parameters
are the input to the ACF, where Σ is defined as the set
of all possible such inputs. A formal definition of Σ
and op.PRE is given in (Schlegel and Amthor, 2021).
Using these notations, the ACF for a DABAC
model can be defined.
Definition 2 (DABAC ACF). The access control
function of a DABAC model for a policy P is a func-
tion f
P
: Σ → B, where
f
P
(op,[a
i
]
n
op
i=1
) = true ⇔ op.PRE.
5.2 Example Policy
Given the use case described in § 2.3, we can now
define a DABAC model to represent the interests of
car owners and emergency forces when accessing a
camera (operation accessCam):
• EN =
{
C,U
}
, where C is a set of camera identi-
fiers and U is a set of user identifiers,
• AV
0
=
{
L,B
}
where L = [−90,90] × [−180,180]
is a set of geographical locations and B is the set
of Boolean values,
• AV
1
=
{
WL
}
, where WL =
{
0,1, .. ., 5
}
is the set
of possible values for a numerical system of warn-
ing levels, where 0 indicates no warning and 5 in-
dicates the highest possible warning level,
• AA
0
=
{
att
CL
,att
EF
}
, where att
CL
: C → L as-
signs a geographical location to every camera and
att
EF
: U → B assigns every user a Boolean value
indicating whether this user represents an emer-
gency force and
• AA
1
=
{
att
LWL
}
, where att
LWL
: L → WL assigns
every location a warning level.
Let P
1
be the policy of the car owner Al-
ice. Specifically, we define C =
{
cAlice
}
, U =
{
uAlice,uFireTruck
}
, att
CL
(cAlice) =
⟨
50.41,10.55
⟩
,
att
EF
(uAlice) = false, att
EF
(uFireTruck) = true,
att
LWL
(
⟨
50.41,10.55
⟩
) = 4 and accessCam.PRE(u ∈
U,c ∈ C) ⇔ u = uAlice ∧ c = cAlice for P
1
.
6
As can
be seen, P
1
only allows camera access to the camera
cAlice by the user uAlice.
Analogously, we define a policy P
2
for a fire
truck which is structurally identical to P
1
. For
P
2
, use the same sets of entities, attribute values
and attributions. Additionally, define the access
rules auth
isCriticial
and auth
isEF
as auth
isCritical
(wl ∈
WL) ⇔ wl ≥ 4 and auth
isEF
(u ∈ U) ⇔ att
EF
(u).
Furthermore, define accessCam’s precondition by
accessCam.PRE(u ∈ U,c ∈ C) ⇔ auth
isEF
(u) ∧
auth
isCritical
(att
LWL
(att
CL
(c))), i. e. P
2
allows a user u
to access a camera c iff u represents an emergency
force and c is currently in a location with a critical
warning level.
Following Def. 2, it can be seen that
f
P
1
(accessCam,
⟨
uFireTruck,cAlice
⟩
) iff
accessCam.PRE(uFireTruck,cAlice) which is
false; i. e. Alice’s policy doesn’t allow the fire
truck to access her camera. On the other hand, it
holds that f
P
2
(accessCam,
⟨
uFireTruck,cAlice
⟩
) ⇔
accessCam.PRE(uFireTruck,cAlice) ⇔ true, i. e. P
2
would grant the fire truck access to Alice’s camera.
In this scenario, it can be seen that Alice is cur-
rently in a location with a critical warning level,
which means that the fire truck should be able to ac-
cess Alice’s camera data. To achieve this, P
1
and P
2
have to be composed.
6
This is a formal simplification, as operation precon-
ditions may only operate on attribute values. A necessary,
additional layer of indirection was omitted here for brevity.
A Composition Algebra for Decentralized Enforcement of Access Control Policies with an Application to Vehicular Networks
83

6 COMPOSITION ALGEBRA
Based on the DABAC model for AC policies intro-
duced in the previous section, we define ACCA as an
extension of Boolean algebra. We will outline the de-
sign requirements (§ 6.1) and the definition of com-
position operators (§ 6.2), and finally define an exem-
plary composition scenario based on the use case in
§ 2.3 (§ 6.3).
6.1 Algebra Design
We define the following logical requirements for a
policy composition algebra. First, composition op-
erations must be associative and commutative. Other-
wise, the order in which policies enter a group would
affect access decisions, which violates the assump-
tion of dynamic group (re-) formation and group-
transparent AC decision making (§ 4). Second, com-
posite policies must be structurally identical to com-
ponent policies to allow for recursive composition and
unified AC evaluation interfaces.
Third, due to generally limited bandwidth of un-
derlying communication infrastructure, the amount of
information available about component policies is a
limiting factor for policy composition. Generally, it
is desirable to have as much information as possible
available to define a proper DABAC policy as the re-
sult of the composition, but this has the drawback that
it leads to a large amount of communication.
This is why ACCA is defined in three different
tiers, according to different amounts of information
which is available on the component policies. They
can be described as follows:
Tier 1. Only the outputs of the component poli-
cies’ ACFs are known.
Tier 2. The access rules and preconditions of op-
erations of the component policies are
known.
Tier 3. The entire component policies, that is all
their components are known.
Additional to limited information, potentially
flawed communication imposes another problem. In
tier 1, for example, outputs of ACFs are known in
the sense that they can be queried from the owner of
their respective policy. However, due to errors in the
communication – e. g. because the queried car just left
communication reach – such queries may not be met
by a proper response, which makes the queried values
unavailable.
For the rest of this paper, the symbol □ denotes a
value that is unavailable (not necessarily undefined).
There are two ways to deal with unavailable values
when composing policies: deny any access request
when at least one value necessary for the policy eval-
uation is unavailable, or ignore unavailable values.
Consider the conjunction of two policies, that is
a composite policy which grants an access iff both
component policies grant it (assuming both can make
a meaningful decision). The above distinction leads
to two different versions of the policy conjunction,
which will be introduced as ∧
M
for making the avail-
ability of all necessary values mandatory and ∧
D
for
disregarding unavailable values. Analogous, the op-
erations ∨
M
and ∨
D
will be used for the disjunction
of policies, where the disjunction of two policies is a
composite policy which grants an access iff at least
one of the component policies grant it (again assum-
ing that both can make a meaningful decision).
These four operations lead to an algebra for com-
posing policies which is more expressive than a
composition using only the trivial extensions of the
Boolean operators ∧ and ∨.
6.2 Composition Logic
As the three tiers differ in the amount of information
available, different definitions have to be made for
them; the basic idea is the same for all three, though.
Tier 1. For the tier 1 policy composition, two poli-
cies P
1
and P
2
with their respective ACF f
i
: Σ
i
→ B ∪
{
□
}
,i ∈
{
1,2
}
are given. Let f : Σ → B ∪
{
□
}
be the
ACF of the composite policy P, where Σ = Σ
1
∪ Σ
2
.
For the composition P = P
1
⊕
M
P
2
, where ⊕ ∈
{
∧,∨
}
,
the value of f (σ) for σ ∈ Σ is given by algorithm 1.
if σ ∈ Σ
1
∩ Σ
2
∧ □ /∈
{
f
1
(σ), f
2
(σ)
}
then
return f
1
(σ) ⊕ f
2
(σ)
else if σ ∈ Σ
1
\ Σ
2
∧ f
1
(σ) ̸= □ then
return f
1
(σ)
else if σ ∈ Σ
2
\ Σ
1
∧ f
2
(σ) ̸= □ then
return f
2
(σ)
else
return □
end
Algorithm 1: The specification of the ACF f of P = P
1
⊕
M
P
2
for ⊕ ∈
{
∧,∨
}
for the tier 1 composition.
As can be seen, the ACFs f
1
and f
2
are combined
using the underlying Boolean operation if both poli-
cies should be considered (i. e. σ ∈ Σ
1
∩ Σ
2
) and if
neither ACF is currently unavailable. If only one pol-
icy should be considered, then only the value of its
corresponding ACF is used, provided this value is not
unavailable. If, however, the value of an ACF is re-
quired but not available, the new ACF f evaluates to
□. Note that returning □ here is necessary to make
the composition operations associative.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
84

if σ ∈ Σ
1
∩ Σ
2
∧ □ /∈
{
f
1
(σ), f
2
(σ)
}
then
return f
1
(σ) ⊕ f
2
(σ)
else if f
1
(σ) ̸= □ ∧ (σ ∈ Σ
1
\ Σ
2
∨ σ ∈
Σ
1
∩ Σ
2
∧ f
2
(σ) = □) then
return f
1
(σ)
else if f
2
(σ) ̸= □ ∧ (σ ∈ Σ
2
\ Σ
1
∨ σ ∈
Σ
1
∩ Σ
2
∧ f
1
(σ) = □) then
return f
2
(σ)
else
return □
end
Algorithm 2: The specification of the ACF f of P = P
1
⊕
D
P
2
for ⊕ ∈
{
∧,∨
}
for the tier 1 composition.
When computing P = P
1
⊕
D
P
2
for ⊕ ∈
{
∧,∨
}
, the
value f (σ) of P’s ACF is given by algorithm 2. The
differences compared to algorithm 1 lie in the second
and third if-statement. The new ACF f uses only one
of the original policies’ ACF (provided it is available)
if either only one policy is concerned with the access
request (as before) or both are, but one ACF value is
currently unavailable.
The introduced definitions can only be meaning-
ful if two assumptions about the policies P
1
and P
2
are
met. First, all entities that may request access to any
entity must be known by both policies. Consider a car
whose owner’s policy is P
1
and whose driver’s policy
is P
2
. If P
2
contains an entity which can request ac-
cess to e. g. the car’s camera data but which is not part
of P
1
, any access request involving that entity cannot
be an element of Σ
1
. Consequently, P
1
has no influ-
ence on the decision a policy composed of P
1
and P
2
may make, presented this access request. However,
the car’s owner should be involved in this decision.
Hence, P
1
has to account for such entities.
Second, consider two policies P
1
and P
2
which
both account for an entity which can be the object
of an access request, but is external in exactly one
of both, say P
2
. This means that the access to this
entity is governed only by P
1
. In a composite policy
P = P
1
⊕
α
P
2
with α ∈
{
M,D
}
, the access to this entity
should still be governed only by P
1
. Consequently, the
ACF f
2
which P
2
provides for the composition has to
return a value which is neutral to ⊕ (i. e. the Boolean
operation upon which ⊕
α
is based) so that its decision
has no effect on the value of P’s ACF.
Tier 2. For tier 2, the two policies are of the form
P
i
=
⟨
AR
i
⟩
,i ∈
{
1,2
}
. For the policy composition,
both policies’ access rules and the preconditions of
P
1
’s and P
2
’s operations need to be redefined to
take into account the desired behaviour when en-
countering a □-value. For this, we define att(□) =
□,auth
p
(□) = □ and □ ∗ a = a ∗ □ = □ for all of
P
i
’s attributes att, access rules auth
p
as well as for all
operators ∗ ∈
{
+,−, ·,/, ==,∈, ⊆,...
}
, where ==
is the comparison operators, and according operands
a. Note that ∗ /∈
{
∧,∨, =
}
. For an access rule
auth
p
∈ AR
1
∪AR
2
, define auth
′
p
as the function which
behaves exactly like auth
p
, but returns □ if any of
the values that arise during the evaluation of auth
p
is □. Formally, if auth
p
is defined by the expres-
sion
W
n
i=1
V
m
i
j=1
ϕ
i, j
in disjunctive normal form if some
condition β is met and as □ otherwise, then auth
′
p
returns the value of auth
p
if the condition β ∧ ∀i, j :
ϕ
i, j
̸= □ is met and □ otherwise. Analogously, for
every op ∈ OP
1
∪ OP
2
, the new precondition op.PRE
′
is defined.
Then, given two policies P
i
=
⟨
AR
i
⟩
with ACF do-
main Σ
i
for i ∈
{
1,2
}
, define Σ = Σ
1
∪ Σ
2
, Perm =
Perm
1
∪ Perm
2
, AR =
F
2
k=1
auth
′
p
| auth
p
∈ AR
k
and OP = OP
1
∪ OP
2
. Lastly, for every op ∈ OP,
let op.PRE be defined by algorithm 1, where Σ
i
and
f
i
are replaced by OP
i
and op.PRE
′
i
respectively and
σ is an element of op.PRE’s domain. The policy
P = P
1
⊕
M
P
2
for ⊕ ∈
{
∧,∨
}
is defined as the policy
P =
⟨
AR
⟩
with the above defined sets of access rules
AR, permissions Perm and operations OP. Its ACF f
is given by f (op, [a
i
]
n
op
i=1
) = op.PRE([a
i
]
n
op
i=1
).
For the composition P
1
⊕
D
P
2
, the access rules
and operation preconditions have to be defined dif-
ferently to disregard the □-values that might be en-
countered during their evaluation. Given an expres-
sion
W
n
i=1
V
m
i
j=1
ϕ
i, j
in disjunctive normal form, the
components of every conjunction should be treated
as true when they evaluate to □, except for when
all parts of a conjunction evaluate to □, in which
case the whole conjunction should be treated as
false. This is realized by the expression ψ =
W
n
i=1
V
m
i
j=1
ϕ
i, j
∈
{
true,□
}
∧
W
m
i
j=1
ϕ
i, j
̸= □
. Like
before, let auth
p
be an access rule which is defined
by the expression
W
n
i=1
V
m
i
j=1
ϕ
i, j
in disjunctive nor-
mal form if some condition β is met and as □ other-
wise. Then, the function auth
′′
p
evaluates to ψ if the
condition β ∧ ∃i, j : ϕ
i, j
̸= □ is met and to □ other-
wise. Define op.PRE
′′
analogously for every opera-
tion op ∈ OP
1
∪ OP
2
.
Then, the policy P = P
1
⊕
D
P
2
for ⊕ ∈
{
∧,∨
}
is defined as the policy with the set of permis-
sions Perm = Perm
1
∪ Perm
2
, the set of operations
OP = OP
1
∪ OP
2
and the set of access rules AR =
F
2
k=1
auth
′′
p
| auth
p
∈ AR
k
. For every operation
op ∈ OP, let op.PRE be defined by algorithm 2,
where Σ
i
and f
i
are replaced by OP
i
and op.PRE
′′
i
for
i ∈
{
1,2
}
respectively and where σ is an element of
op.PRE’s domain.
Additional to the assumptions that were required
A Composition Algebra for Decentralized Enforcement of Access Control Policies with an Application to Vehicular Networks
85

for tier 1, the tier 2 composition requires that every
entity which may act as an object in an access request
has to be included in both P
1
and P
2
. This is because
then, the access rules auth
p
as well as the op.PRE
functions can return a meaningful value when pre-
sented arguments their respective policy did not orig-
inally account for.
Tier 3. The third tier composes two policies of
which all components are known. Note that this
means that no value will ever evaluate to □, as the
component policies are available locally.
For the tier 3 composition, the distinction of inter-
nal and external entities and attribute values through
the sets EN
ext
, AV
ext
and AA
ext
in DABAC as de-
scribed in § 5.1 is problematic. Composing policies
while keeping these sets means that the resulting com-
posite policy’s entities and attribute values are inter-
nal or external to either every or none of the compo-
nent policies’ domain. This, however, is not generic
enough, as access decisions may incorporate knowl-
edge on whether an entity or attribute value is internal
or external to a component policy, which should be
retained in the composite policy. Rather, it should be
possible for entities and attribute values to be inter-
nal or external to only some of those domains, i. e. the
information on externality from the component poli-
cies should be kept. To achieve this, we incorporate
according attributions and access rules into the com-
ponent policies, which makes the definition of EN
ext
,
AV
ext
and AA
ext
unnecessary. Consequently, we will
not consider these sets in the following definition.
Let P
1
=
⟨
EN
1
,AV
′
,AA
′
,AR
1
⟩
and P
2
=
⟨
EN
2
,AV
′′
,AA
′′
,AR
2
⟩
be two structurally identi-
cal policies with EN
k
=
E
k,1
,. .. ,E
k,n
for all
k ∈
{
1,2
}
as well as AV
′
i
= {V
′
i,1
,. .. ,V
′
i,n
i
} and
AV
′′
i
= {V
′′
i,1
,. .. ,V
′′
i,n
i
} for all 0 ≤ i ≤ i
max
. Define the
sets EN =
{
E
1
,. .. ,E
n
}
with E
j
= E
1, j
∪ E
2, j
for all 1 ≤ j ≤ n and AV
i
=
{
V
i,1
,. .. ,V
i,n
i
}
with V
i, j
= V
′
i, j
∪ V
′′
i, j
for all 1 ≤ j ≤ n
i
and all 0 ≤ i ≤ i
max
. Furthermore, define
AA =
{
att
′
| att ∈ AA
′
}
⊔
{
att
′
| att ∈ AA
′′
}
, where
att
′
is equal to att for all arguments from att’s
domain and undefined for all other arguments.
Then, for ⊕
α
∈
{
∧
M
,∧
D
,∨
M
,∨
D
}
, the policy
P = P
1
⊕
α
P
2
=
⟨
EN,AV,AA,AR
⟩
is the policy with
the above defined sets of entities, attribute values and
attributions and the remaining components defined as
in tier 2.
6.3 Example
Let P
1
and P
2
be the two policies defined in § 5.2. In
the scenario (as described in § 2.3), policy P
2
should
be able to overrule P
1
’s decision to deny the firetruck
represented by uFireTrack access to Alice’s camera
cAlice. To achieve this, it is reasonable to compute
a composite policy P as P = P
1
∨
M
P
2
. For tier 1,
this means that f
P
is defined by algorithm 1 with
⊕ = ∨. Let σ =
⟨
accessCam,[uFireTruck,cAlice]
⟩
be an access request. As was shown in § 5.2, it is
f
P
1
(σ) = false and f
P
2
(σ) = true. Assuming that both
values are available, it follows that f
P
(σ) = f
P
1
(σ) ∨
f
P
2
(σ) = true, i. e. the composite policy P grants the
fire truck access to Alice’s camera as policy P
2
grants
it.
For the tier 2 composition, we modify the def-
inition of accessCam.PRE in P
1
to return u ==
uAlice ∧ c == cAlice (now using == as the com-
parison operator) iff (u == uAlice) ̸= □ and (c ==
cAlice) ̸= □ and □ otherwise. This new precondi-
tion will be called accessCam.PRE
′
1
. Analogously,
we define auth
′
isCritical
, auth
′
isEF
and accessCam.PRE
′
2
for P
2
. Then, P = P
1
∨
M
P
2
is the policy with
the set of access rules AR =
auth
′
isCritical
,auth
′
isEF
and the operation accessCam. When all values
are available, all attributions and access rules of
P are identical to the original attributions and ac-
cess rules in P
1
and P
2
respectively. Further-
more, it is accessCam.PRE = accessCam.PRE
′
1
∨
accessCam.PRE
′
2
, where accessCam.PRE
′
i
is iden-
tical to the definition of accessCam.PRE in P
i
for
i ∈
{
1,2
}
, again because all necessary values are as-
sumed to be available. Then, it can be seen that
f
P
(σ) ⇔ accessCam.PRE(uFireTruck,cAlice)
⇔ accessCam.PRE
′
1
(uFireTruck,cAlice)
∨ accessCam.PRE
′
2
(uFireTruck,cAlice)
⇔ false ∨ true ⇔ true.
Again, P grants the fire truck access to Alice’s cam.
The policy which is computed using tier 3 has
identical attributions, access rules and operations (in-
cluding their preconditions) as the result of the tier 2
composition. Additionally, a set EN and AV are de-
fined. As the sets EN and AV of P
1
and P
2
are iden-
tical, the policy P = P
1
∨
M
P
2
also uses these sets.
Putting together the example evaluation for the tier 2
composition as well as the evaluation of σ in P
1
and
P
2
from § 5.2, it can be seen that P again grants the
fire truck the desired access to Alice’s camera.
7 EVALUATION
To analyze the feasibility of the proposed algebra in
the scenario described in § 2, several runtime mea-
surements were conducted on a prototype implemen-
SECRYPT 2024 - 21st International Conference on Security and Cryptography
86
tation of ACCA.
7
For the measurements, a network of n hosts, each
of which being connected to a single switch, is sim-
ulated using the software mininet. For that, a virtual
machine image running Ubuntu 20.04.1 from the offi-
cial mininet website with mininet preinstalled was set
up in Oracle VM VirtualBox 7.0.8 and executed on a
system with a 4-core AMD Ryzen 5 3500U CPU and
8 GB main memory running Pop! OS 22.04. Every
host runs an instance of the prototype implementation
and uses one of three hardcoded example policies. All
hosts compute a network-wide composite policy us-
ing the ∧
M
-operation.
In detail, the runtime of the following three oper-
ations was measured: (1) evaluating a local policy,
(2) evaluating a composite policy and (3) adding a
new host and its local policy to an already existing
network of hosts with an already established compos-
ite policy. The runtime of the first two operations
was measured for three different requests one hundred
times each. While the requests 1 and 2 can be eval-
uated and properly answered by the local policy, the
third requests access to an object that is external to the
local policy, i. e. the policy cannot make a meaningful
decision and directly responds to the request with ab-
stention. For all composite policies which were used
for the measurements, a decision could be made for
all requests.
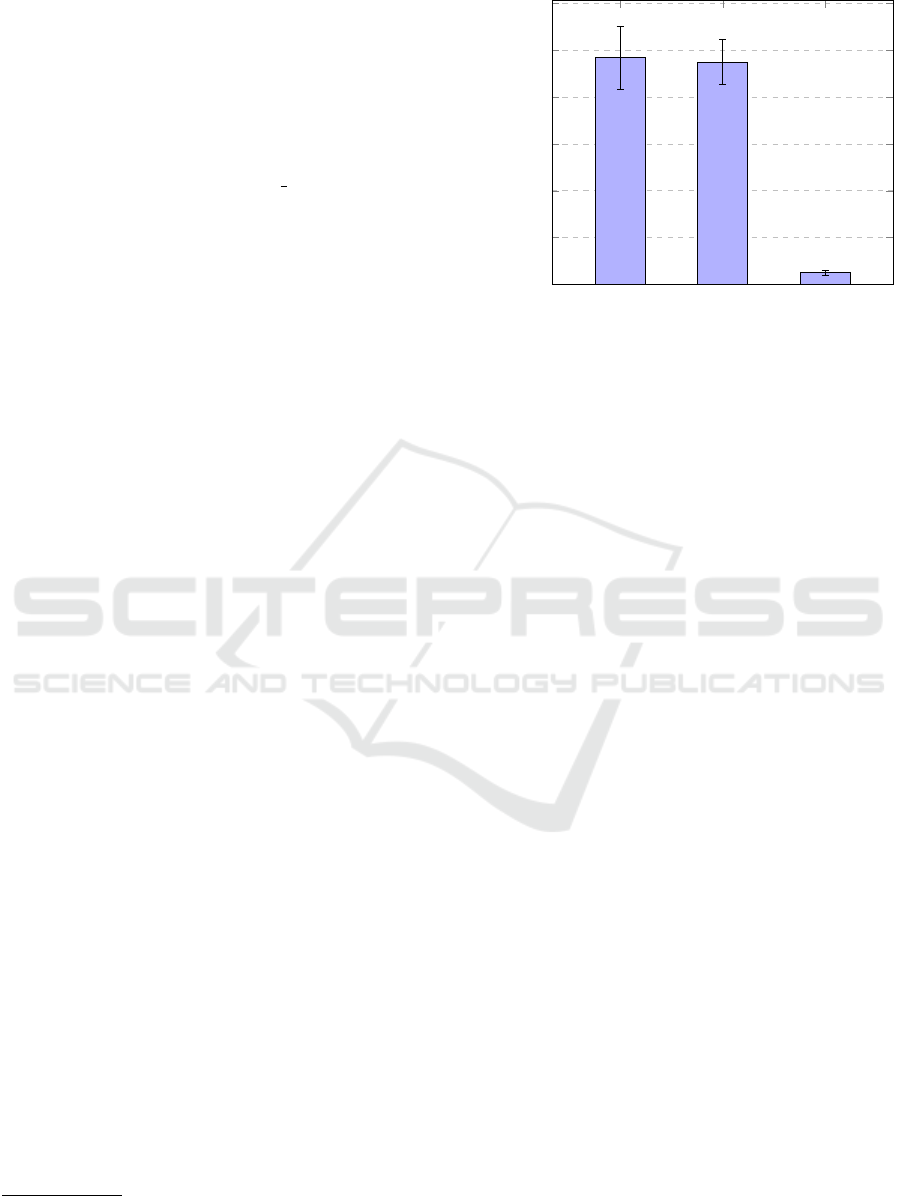
The average time it takes to evaluate a local pol-
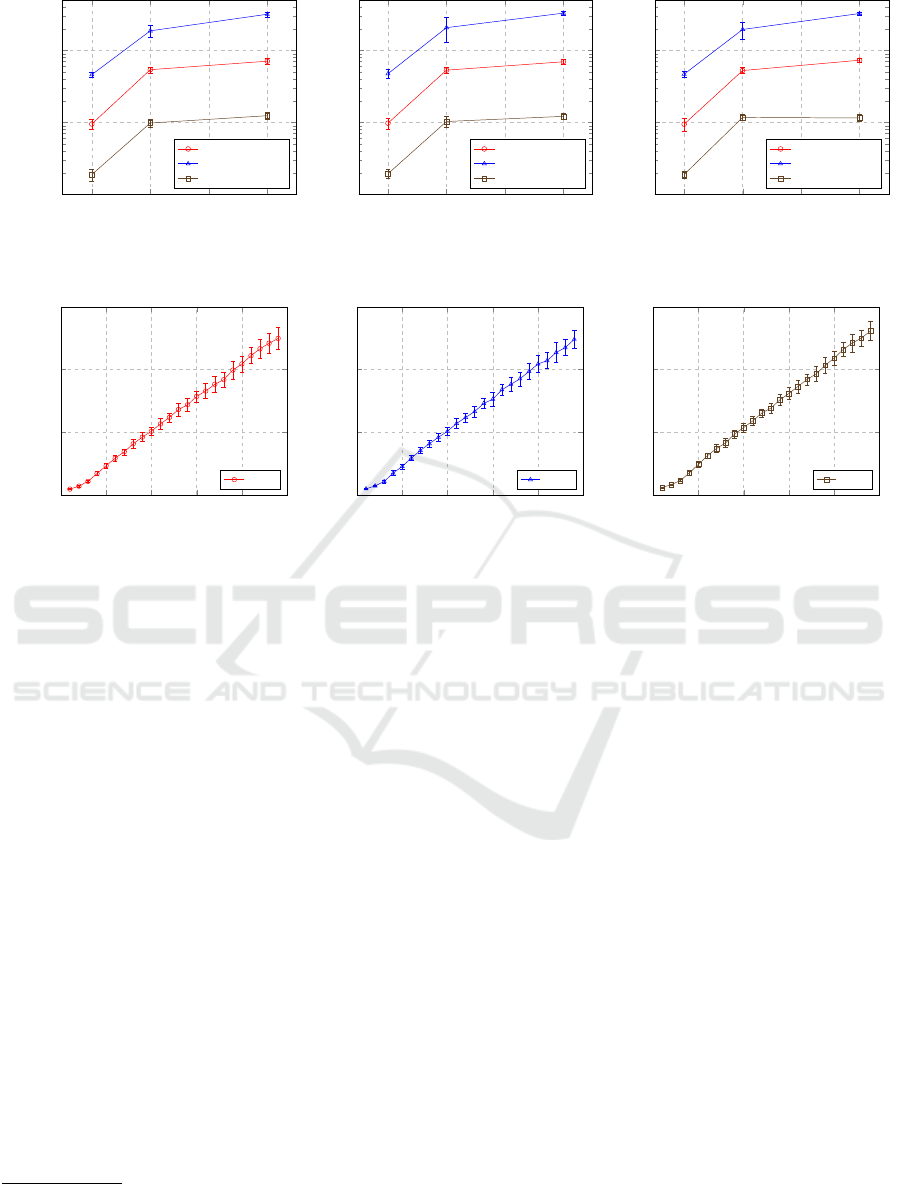
icy is displayed in Fig. 2. In Fig. 3, the average time it
takes to evaluate any of the three requests in a tier 1,
tier 2 and tier 3 composite policy with a varying num-
ber of involved component policies is shown. Lastly,
Fig. 4 shows the average time it takes for a host to join
an already established network of hosts. This group-
formation phase starts when the new host broadcasts
its initial message to the network and ends when all
hosts, including the arriving one, finished computing
the new, network-wide composite policy.
As can be seen, evaluating a local policy for a re-
quest that the policy is not concerned with takes sig-
nificantly less time than evaluating a request the pol-
icy can make a decision on.
For the latter, evaluation takes an average of
0.95 ms. In contrast to that, evaluating a composite
policy takes more time than evaluating a local policy.
As can be seen, the necessary time increases with the
number of involved component policies, which is to
be expected, as with more component policies, more
expressions have to be evaluated in order to compute a
result. However, the tier according to which the com-
ponent policies are composed significantly impacts
7
The source code is available at https://codeberg.org/
rgorges/acca.
Request 1 Request 2 Request 3
0
0.2
0.4
0.6
0.8
1
1.2
Evaluation time [ms]
Figure 2: The evaluation times for a local policy. The error
bars indicate the standard deviation.
the time needed to evaluate the resulting composite
policy. In the prototype implementation, evaluating
a tier 3 composite policy is faster than evaluating a
tier 1 composite policy, while tier 2 takes the most
amount of time. This matches the amount of com-
munication necessary when evaluating the composite
policies: In tier 1, exactly one query has to be sent for
every component policy which is part of the compos-
ite policy. This query asks the host this component
policy comes from for the result of its local policy.
For tier 2, multiple queries have to be sent for every
component policy, namely one per attribution that has
to be evaluated. Finally, in tier 3, no queries have to
be sent, as all information necessary to evaluate the
request in the composite policy are available at the
queried host. This results in the described relation of
the runtime for the three tiers.
Finally, it can be seen that the effort of incorpo-
rating a new host into an already existing network is
approximately linear in the number of involved hosts.
This is to be expected, as every host in the network
adds only a constant number of messages which have
to be sent in order to enable the proper incorpora-
tion of new hosts. Additionally, this process takes
roughly the same time for all three composition tiers,
which is because the time necessary for communica-
tion between hosts outweighs the effort for computing
a composite policy.
Note that these results suggest the use of tier 3
whenever possible, as it comes with the least run-
time for evaluating the composite policy, while the
effort of computing such a composition is compara-
ble to tiers 1 and 2. However, this is only true as long
as the component policies are static. With changing
component policies, it becomes necessary to update
their copies which were distributed among the other
hosts within the network, causing more communica-
A Composition Algebra for Decentralized Enforcement of Access Control Policies with an Application to Vehicular Networks
87
2 4
6
8
10
0
10
1
10
2
Number of component policies
Evaluation time [ms]
Tier 1, Request 1
Tier 2, Request 1
Tier 3, Request 1
2 4
6
8
10
0
10
1
10
2
Number of component policies
Evaluation time [ms]
Tier 1, Request 2
Tier 2, Request 2
Tier 3, Request 2
2 4
6
8
10
0
10
1
10
2
Number of component policies
Evaluation time [ms]
Tier 1, Request 3
Tier 2, Request 3
Tier 3, Request 3
Figure 3: Time to evaluate the three requests in a tier 1, 2 and 3 composite policy with a varying number of component policies
as well as for all three of the aforementioned requests. The error bars indicate the standard deviation.
0
5
10
15
20
25
0
500
1,000
1,500
Number of initial hosts
Time to add new host to network [ms]
Tier 1
0
5
10
15
20
25
0
500
1,000
1,500
Number of initial hosts
Time to add new host to network [ms]
Tier 2
0
5
10
15
20
25
0
500
1,000
1,500
Number of initial hosts
Time to add new host to network [ms]
Tier 3
Figure 4: Time to add a host to an already existing network of hosts using the three different composition tiers. This includes
computing the new composite policy on every host as well as the communication time. The error bars indicate the standard
deviation.
8
tion overhead, especially since policies may change
very frequently because they can incorporate e. g. reg-
ularly updated sensor values. Consequently, it is nec-
essary to design and implement such an update mech-
anism and evaluate its runtime impact to more prop-
erly investigate the suitability of the tier 3 policy com-
position.
8 RELATED WORK
Literature related to this work can be divided in three
categories: Policy composition logic in general, spe-
cific AC models tailored to distributed V2X systems,
and general work on access control technologies in
vehicular networks not directly related to policy com-
position.
Policy Composition. Since a few decades, the pol-
icy composition problem and the general semantics
of “metapolicies” has received considerable attention
(K
¨
uhnhauser, 1999; Bonatti et al., 2002; Wijesekera
and Jajodia, 2003; Ni et al., 2009; Li et al., 2009;
8
For reasons of hardware availability, these measure-
ments were conducted on an Intel system equivalent to the
one described in § 7.
Ferraiolo et al., 2011; Baracaldo et al., 2011). We
designed ACCA on basis of this foundational body of
work, but tailored towards the requirements of more
recent use cases: first, all these approaches predomi-
nantly focus on formally well-established role-based
access control (RBAC) policy semantics, which is too
restrictive when it comes to modeling object attributes
(e. g. in the scenarios described in § 2). Second, and
even more important, none of them addresses both
observations (2) and (3) as stated in § 1: incomplete
knowledge of component policies cannot be tolerated
by the policy composition logic, and/or dynamic cor-
rectness properties cannot be modeled (and therefore
analyzed).
V2X Policy Models. Despite more application-
tailored than DABAC, two AC models from the lit-
erature are directly related to the approach followed
in this work. In (Alsarra et al., 2019), a RBAC
model well-tailored to VANETs is described (“open-
RBAC”). The authors cover its formal definition, in-
herent role semantics, and hint at its date model im-
plementation and usage. We acknowledge this work
as complementary, since openRBAC – being a spe-
cialization of DRBAC (Schlegel and Amthor, 2020)
which, in turn, is generalized by DABAC – is ex-
pected to be completely coverable by ACCA. Substan-
SECRYPT 2024 - 21st International Conference on Security and Cryptography
88

tiating this claim by further incorporation of openR-
BAC policies in a practical evaluation is subject to
future work (cf. § 9). In (Gupta et al., 2019), CV-
ABAC
G
is proposed. In contrast to DABAC, this
model distinguishes between more specialized entity
classes (such as “clustering” for entity composition,
which we represent through domains in the sepa-
rate system model). On the level on attribution and
access rules semantics however, CV-ABAC
G
largely
matches the intentions of DABAC except for hierar-
chical attribution and the ability to model environ-
mental attributions (DABAC’s “ext” components). It
is therefore a valid alternative to adapt ACCA to more
specialized V2X scenarios.
General V2X AC Technology. Finally, significant
work has investigated the AC semantics involved with
V2X scenarios and VANETs, such as (Sharma and
Kaul, 2021; Li et al., 2020; Liu et al., 2022). We re-
gard this literature complementary in a sense that its
results will be of relevance for a practical deployment
and real-world evaluation of ACCA, as envisioned in
§ 9.
9 CONCLUSION
In this work we present the formal foundations for ac-
cess control policy composition in a open distributed
system, characterized by decentralized enforcement
and volatile group formation. As a basis of our ap-
proach, we leverage the automaton-based dynamic
analysis calculus embedded in the DABAC modeling
framework, which serves as a policy specification ba-
sis for ACCA, a novel composition algebra for access
control policies.
We describe the policy composition problem for
V2X applications and apply ACCA for these, which
is based on the idea of partial knowledge: for each
composition operation, it includes specialized deci-
sion making semantics for a group’s composite pol-
icy based on one of three tiers to represent the de-
gree of information received about multiple DABAC-
modeled component policies.
In a first, simulation-based study on runtime per-
formance, we evaluated the utility of these tiers w. r. t.
practical feasibility. While our first results suggest
an always-flooding-approach for policy information
distribution (tier 3), a broader and more application-
specific range of dynamic behavior might reveal the
utility of tier 1 or even tier 2 policies as a compromise
in more detailed use cases. Future work will focus
on the investigation of such side conditions and con-
straints, as well as on a practical infrastructure archi-
tecture as a testbed for evaluating a realistic deploy-
ment.
AVAILABILITY
A Rust-based implementation of ACCA and the
simulation environment used is available at https://
codeberg.org/rgorges/acca.
REFERENCES
Alsarra, S., Yen, I.-L., Huang, Y., Bastani, F., and Thurais-
ingham, B. (2019). An OpenRBAC semantic model
for access control in vehicular networks. In Proceed-
ings of the 24th ACM Symposium on Access Con-
trol Models and Technologies, SACMAT ’19, page
93–102, New York, NY, USA. Association for Com-
puting Machinery.
Anderson, J. P. (1972). Computer Security Technol-
ogy Planning Study. Technical Report ESD-TR-73-
51, Air Force Electronic Systems Division, Hanscom
AFB, Bedford, MA, USA. Also available as Vol. I,
DITCAD-758206. Vol. II DITCAD-772806.
Arena, F. and Pau, G. (2019). An overview of vehicular
communications. Future Internet, 11(2):27.
Ashutosh, A., Gerl, A., Wagner, S., Brunie, L., and Kosch,
H. (2023). XACML for mobility (XACML4M)—an
access control framework for connected vehicles. Sen-
sors, 23(4):1763.
Baracaldo, N., Masoumzadeh, A., and Joshi, J. (2011). A
Secure, Constraint-Aware Role-Based Access Control
Interoperation Framework. In Proceedings of the 5th
International Conference on Network and System Se-
curity, NSS ’11, pages 200–207. IEEE Computer So-
ciety.
Bonatti, P., De Capitani di Vimercati, S., and Samarati, P.
(2002). An Algebra For Composing Access Control
Policies. ACM Transactions on Information and Sys-
tem Security, 5:1–35.
Ferraiolo, D., Atluri, V., and Gavrila, S. (2011). The Pol-
icy Machine: A Novel Architecture and Framework
for Access Control Policy Specification and Enforce-
ment. Journal of Systems Architecture: the EUROMI-
CRO Journal, 57(4):412–424.
Ferraiolo, D., Chandramouli, R., Kuhn, R., and Hu, V.
(2016). Extensible access control markup language
(xacml) and next generation access control (ngac). In
Proceedings of the 2016 ACM International Workshop
on Attribute Based Access Control, ABAC ’16, pages
13–24, New York, NY, USA. ACM.
Gupta, M., Benson, J., Patwa, F., and Sandhu, R. (2019).
Dynamic groups and attribute-based access control
for next-generation smart cars. In Proceedings of the
Ninth ACM Conference on Data and Application Se-
curity and Privacy, CODASPY ’19, page 61–72, New
York, NY, USA. Association for Computing Machin-
ery.
A Composition Algebra for Decentralized Enforcement of Access Control Policies with an Application to Vehicular Networks
89

Harrison, M. A., Ruzzo, W. L., and Ullman, J. D. (1975).
On Protection in Operating Systems. Operating Sys-
tems Review, special issue for the 5th Symposium on
Operating Systems Principles, 9(5):14–24.
Hussein, N. H., Yaw, C. T., Koh, S. P., Tiong, S. K., and
Chong, K. H. (2022). A comprehensive survey on
vehicular networking: Communications, applications,
challenges, and upcoming research directions. IEEE
Access, 10:86127–86180.
INCITS (2013). Information technology — Next Gen-
eration Access Control — Functional Architecture
(NGAC-FA). INCITS 499–2013, American National
Standards Institute.
Khan, A. and Fong, P. (2012). Satisfiability and Feasibil-
ity in a Relationship-Based Workflow Authorization
Model. In Foresti, S., Yung, M., and Martinelli, F.,
editors, Computer Security – ESORICS 2012, volume
7459 of Lecture Notes in Computer Science, pages
109–126. Springer Berlin / Heidelberg.
K
¨
uhnhauser, W. E. (1999). Policy Groups. Elsevier Com-
puters & Security, 18(4):351–363.
Li, H., Pei, L., Liao, D., Chen, S., Zhang, M., and Xu, D.
(2020). FADB: A fine-grained access control scheme
for VANET data based on blockchain. IEEE Access,
8:85190–85203.
Li, N., Mitchell, J. C., and Winsborough, W. H. (2005). Be-
yond Proof-of-compliance: Security Analysis in Trust
Management. Journal of the ACM, 52(3):474–514.
Li, N., Wang, Q., Qardaji, W., Bertino, E., Rao, P., Lobo,
J., and Lin, D. (2009). Access Control Policy Com-
bining: Theory Meets Practice. In Proceedings of
the 14th ACM Symposium on Access Control Mod-
els and Technologies, SACMAT ’09, pages 135–144,
New York, NY, USA. ACM.
Liu, L., Chen, C., Pei, Q., Maharjan, S., and Zhang,
Y. (2020). Vehicular edge computing and network-
ing: A survey. Mobile Networks and Applications,
26(3):1145–1168.
Liu, X., Chen, W., and Xia, Y. (2022). Security-aware in-
formation dissemination with fine-grained access con-
trol in cooperative multi-RSU of VANETs. IEEE
Transactions on Intelligent Transportation Systems,
23(3):2170–2179.
Marinovic, S., Craven, R., Ma, J., and Dulay, N. (2011).
Rumpole: a Flexible Break-glass Access Control
Model. In Proceedings of the 16th ACM Symposium
on Access Control Models and Technologies, SAC-
MAT ’11, pages 73–82. ACM.
Mazzola, M., Schaaf, G., Niewels, F., and Kurner, T.
(2015). Exploration of centralized Car2X-systems
over LTE. In 2015 IEEE 81st Vehicular Technology
Conference (VTC Spring). IEEE.
Meneguette, R., Grande, R. D., Ueyama, J., Filho, G. P. R.,
and Madeira, E. (2021). Vehicular edge comput-
ing: Architecture, resource management, security, and
challenges. ACM Computing Surveys, 55(1):1–46.
Ni, Q., Bertino, E., and Lobo, J. (2009). D-algebra for
Composing Access Control Policy Decisions. In Pro-
ceedings of the 4th International Symposium on In-
formation, Computer, and Communications Security,
ASIACCS ’09, pages 298–309, New York, NY, USA.
ACM.
OASIS (2013). eXtensible Access Control Markup Lan-
guage (XACML) Version 3.0. OASIS Standard 499–
2013, Organization for the Advancement of Struc-
tured Information Standards.
Sandhu, R. S. (1992). The Typed Access Matrix Model.
In Proceedings of the 1992 IEEE Symposium on Secu-
rity and Privacy, SP ’92, pages 122–136, Washington,
DC, USA. IEEE Computer Society.
Schlegel, M. and Amthor, P. (2020). Beyond Administra-
tion: A Modeling Scheme Supporting the Dynamic
Analysis of Role-based Access Control Policies. In
Samarati, P., di Vimercati, S. D. C., Obaidat, M. S.,
and Ben-Othman, J., editors, Proceedings of the 17th
International Conference on Security and Cryptog-
raphy, SECRYPT 2020, pages 431–442. INSTICC,
SciTePress.
Schlegel, M. and Amthor, P. (2021). The Missing Piece of
the ABAC Puzzle: A Modeling Scheme for Dynamic
Analysis. In di Vimercati, S. D. C. and Samarati, P.,
editors, Proceedings of the 18th International Confer-
ence on Security and Cryptography, SECRYPT 2021,
pages 234–246. INSTICC, SciTePress.
Schlegel, M. and Amthor, P. (2023). Putting the Pieces
Together: Model-Based Engineering Workflows for
Attribute-Based Access Control Policies. In Sama-
rati, P., van Sinderen, M., di Vimercati, S. D. C., and
Wijnhoven, F., editors, E-Business and Telecommu-
nications, volume 1795 of Communications in Com-
puter and Information Science (CCIS), pages 249–
280. Springer Nature Switzerland, Cham.
Sharma, S. and Kaul, A. (2021). VANETs cloud: Architec-
ture, applications, challenges, and issues. Archives of
Computational Methods in Engineering, 28(4):2081–
2102.
Wijesekera, D. and Jajodia, S. (2003). A propositional pol-
icy algebra for access control. ACM Trans. Inf. Syst.
Secur., 6(2):286–325.
Yang, C., Jiang, P., and Zhu, L. (2022). Accelerating de-
centralized and partial-privacy data access for VANET
via online/offline functional encryption. IEEE Trans-
actions on Vehicular Technology, 71(8):8944–8954.
Zhou, Z., Gaurav, A., Gupta, B. B., Lytras, M. D., and Raz-
zak, I. (2022). A fine-grained access control and secu-
rity approach for intelligent vehicular transport in 6G
communication system. IEEE Transactions on Intel-
ligent Transportation Systems, 23(7):9726–9735.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
90
