
On Privacy of RFID-Based Authentication Protocols
Ferucio Laurent¸iu T¸ iplea
a
Faculty of Computer Science, “Alexandru Ioan Cuza” University of Ias¸i, Romania
Keywords:
RFID Protocol, Privacy, Indistinguishability.
Abstract:
RFID-based authentication protocols have started increasingly being used in various fields, such as tracking
assets, managing stock, controlling quality processes, and automotive and healthcare services. In addition to
authentication (unilateral or mutual), it is necessary that these protocols also ensure a certain level of privacy.
Very often, privacy properties are studied ad hoc or informally. In this paper, we highlight two scenarios that,
once identified in such protocols, show us that they cannot satisfy a certain level of privacy in the Hermans-
Pashalidis-Vercauteren-Preneel (HPVP) privacy model. For each scenario, general results are presented and
exemplified by existing protocols. We then analyze a recent authentication protocol based on simulatable
PUFs and prove that a simplified variant of it achieves strong privacy in the HPVP model.
1 INTRODUCTION
We probably use radio frequency identification
(RFID) technology daily in public transportation or
payment in stores, most of the time without being
aware. This technology uses the electromagnetic field
to read information from a tag associated with the ob-
ject or entity we want to identify.
Officially, the RFID technology was invented in
1983 by Charles Walton when he filed the first patent
with the word “RFID”, even if it was used in vari-
ous forms long before that. Near Field Communi-
cation (NFC), also based on RFID, debuted in 2002
and has since continued to develop. In the last 20
years, we have witnessed an impetuous development
of RFID technology. Its applications are increasingly
diverse, from big retail chains worldwide to tracking
assets, managing stock, controlling quality processes,
and automotive and healthcare services.
The emergence and development of the Internet
of Things has led to new and multiple applications of
RFID. On the other hand, we are witnessing a diver-
sification of the use of RFID technology. We are thus
talking about a backend server-based RFID archi-
tecture, where the tag reader communicates securely
with a server, and a server-less RFID architecture suit-
able for identification and verification by tag readers
that are mobile and offline. The development of cloud
technology allowed the replacement of the processing
provided by the backend server by processing data in
a
https://orcid.org/0000-0001-6143-3641
the cloud. This makes it possible to use mobile tag
readers but also fixed ones. Another aspect worthy of
consideration is the appearance of physically unclon-
able functions (PUFs), which are chips that theoret-
ically cannot be cloned, behave like pseudo-random
functions, and are tamper-resistant. They can be in-
cluded in tags, offering significant advantages in the
identification and authentication process.
In all this wealth of applications, the central role
of RFID is identification (with the provision of in-
formation about the identified object) and authenti-
cation. To this, the RFID protocols must meet spe-
cific security and privacy requirements. Various se-
curity and privacy models have been developed for
cases where RFID technology is used with a back-
end server securely connected to the tag reader. Vau-
denay’s model (Vaudenay, 2007; Paise and Vaude-
nay, 2008) and the Hermans-Pashalidis-Vercauteren-
Preneel (HPVP) model (Hermans et al., 2011; Her-
mans et al., 2014) are two of the most important.
These models can be extended to other RFID archi-
tectures proposed in recent years because, implicitly,
the security and privacy properties between tag and
reader must be preserved somehow. The communi-
cation between the reader and the server, when the
communication channel is not secure, must be further
analyzed. However, if the reader-tag communication
is not private, it cannot be private regardless of how
we extend the architecture to capture aspects of mo-
bility, cloud computing, etc.
128
Å
´
ciplea, F.
On Privacy of RFID-Based Authentication Protocols.
DOI: 10.5220/0012760500003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 128-139
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

Contribution. Even though we currently have suf-
ficiently mature security and privacy RFID models,
many authors still propose authentication protocols
based on RFID for which the analysis of security and
privacy properties is carried out ad hoc or informally.
It has often been found that such protocols have vul-
nerabilities, and their fix leads to other protocols with
vulnerabilities. In this context, establishing templates
that quickly highlight protocols that cannot be secure
or private, can significantly help RFID protocol de-
signers. However, achieving this goal may not be sim-
ple, especially for the protocols whose analysis was
carried out informally. Reporting to a reputable RFID
security and privacy model can solve the problem in
such a situation. Thus, in this paper, we will consider
the HPVP model as a reference model and establish
some “templates” that, once detected in a security
protocol, guarantee that the protocol cannot reach a
certain level of privacy in the HPVP model. For each
template, we provide theoretical proof in the HPVP
model and exemplify it abundantly through RFID pro-
tocols recently proposed in the specialized literature.
We then analyze a recent authentication protocol (Gao
et al., 2022) based on simulatable PUFs and prove that
a simplified variant of it achieves strong privacy in the
HPVP model.
Paper Organization. The paper’s second section
recalls a few basic definitions and notations in cryp-
tography, while the third section deals with the RFID
system concept, briefly presents the HPVP privacy
model, and shows how the technology of physically
unclonable functions (PUF) can be used with RFID
systems. In the fourth section, we discuss the con-
sequences on the properties of privacy of the non-
randomization of the tag identifier and the “unpro-
tected” use of global temporary variables within the
RFID tags. The fifth section is dedicated to a re-
cently proposed class of RFID authentication proto-
cols based on simulatable PUFs. We discuss one
of these protocols and propose an improvement, to-
gether with the complete proof of strong privacy in
the HPVP model. In the last section, we present the
conclusions of the paper.
2 SOME BASIC DEFINITIONS
AND NOTATION
We will briefly mention some standard cryptography
concepts and notations (for details, the reader is di-
rected to (Katz and Lindell, 2020)).
We use in our exposition probabilistic polyno-
mial time (PPT) algorithms A as defined in (Sipser,
2012) that can consult oracles. For a set A, a ← A
means that a is uniformly at random chosen from
A. If A is a probabilistic algorithm, then a ← A
means that a is an output of A for some given in-
put. The asymptotic approach to security makes use
of security parameters, denoted by λ in our paper. A
positive function f (λ) is called negligible if for any
positive polynomial poly(λ) there exists n
0
such that
f (λ) < 1/poly(λ), for any λ ≥ n
0
. f (λ) is called over-
whelming if 1 − f (λ) is negligible.
Assume that K is a key space. A family of func-
tions indexed by K is a function F that associates
to any key K ∈ K a function F
K
: {0,1}
ℓ
1
(|K|)
→
{0,1}
ℓ
2
(|K|)
, where |K| is the size of K and ℓ
1
and
ℓ
2
are two polynomials given for F. We usually de-
note F by F = (F
K
)
K∈K
. We say that F is a pseudo-
random function (PRF) if it is efficiently computable
and the input-output behavior of any function chosen
at random from F is computationally indistinguish-
able from that of a random function. To prove that F
is a PRF, we usually assume the existence of a chal-
lenger C that plays the following security game pa-
rameterized by a security parameter λ with an adver-
sary A:
1. C randomly chooses b ← {0, 1};
2. if b = 1 then C randomly chooses a key K of size
λ from the key space and sets f = F
K
; otherwise,
C randomly chooses f from the space of all func-
tions from {0,1}
ℓ
1
(λ)
to {0,1}
ℓ
2
(λ)
;
3. C provides oracle access to f for A;
4. At some point, A outputs a bit b
′
.
The adversary A wins the game if b
′
= b.
Now, F is a PRF if it is efficiently computable and
the probability to win the above security game is neg-
ligible close to 1/2, for all adversaries.
3 PRIVACY OF RFID-BASED
SYSTEMS
This section introduces the basic concepts we will use
further, such as the RFID system, physically unclon-
able functions, and privacy properties.
3.1 RFID System
For the RFID system concept, we will especially fol-
low (Vaudenay, 2007; Hermans et al., 2011; Hermans
et al., 2014). Informally, an RFID system consists of a
reader, a set of tags, and a radio frequency communi-
cation protocol between reader and tags. The reader,
which securely communicates with a database where
On Privacy of RFID-Based Authentication Protocols
129

information on the tags in the system is stored, has no
restrictions from a computational point of view. The
tags, however, are devices with very low storage ca-
pacity and computing power, generally supplied with
energy by the reader when it is in their vicinity. The
tag memory is divided into:
1. Permanent memory, which stores the state values
of the tag;
2. Temporary or volatile memory, which can be
viewed as a set of temporary (volatile) variables
used to carry out the calculations required by the
communication protocol. There are two types of
temporary variables:
(a) Local temporary variables, used by tags only to
do computations in a given protocol step;
(b) Global temporary variables, that get values in
a given protocol step and are used in another
protocol step.
Let R be a reader identifier and T be a set of tag
identifiers whose cardinal is polynomial in some secu-
rity parameter λ. An RFID scheme over (R , T ) (Vau-
denay, 2007) is a triple Σ = (SetupR, SetupT, Ident)
of PPT algorithms, where:
1. SetupR(λ) sets the reader. Starting with a secu-
rity parameter λ, it generates a triple (pk,sk,DB)
consisting of a key pair (pk, sk) and an empty
database DB. pk is public, while sk is kept secret
by reader;
2. SetupT (pk,ID) initializes the tag identified by
ID. It outputs an initial tag state S and a tag-
specific secret K. The pair (ID,K) is stored in
the reader’s database;
3. Ident(pk; R (sk,DB); ID(S)) is a communication
protocol between the reader identified by R (with
its private key sk and database DB) and a tag iden-
tified by ID (with its state S) in which the reader
ends with an output consisting of ID or ⊥. The
tag may end with no output (unilateral authenti-
cation), or it may end with an output consisting of
OK or ⊥ (mutual authentication).
The tag’s state S may be a vector of elements, and
the same K. Moreover, S and K may not necessar-
ily be disjoint. Their common part, if any, will be
called the DB-state of the tag; it will be denoted by
S|
DB
. Among other things, the DB-state is used for
synchronization between reader and tag.
The correctness of an RFID scheme refers to the
honest behavior of the reader and tag in a complete
protocol session. More precisely, regardless of how
the system is set up, after each complete and honest
execution of the interactive protocol one of the two
cases holds with overwhelming probability:
• If the tag is legitimate, the reader outputs tag’s
identity (and the tag outputs OK, in case of mu-
tual authentication);
• If the tag is illegitimate, the reader outputs ⊥.
The communication protocol is an alternating se-
quence of reader-to-tag and tag-to-reader communi-
cation steps in which the first step can be taken by
either of them. When the reader sends a message m
to the tag, we will often say that the reader queries
the tag on m. When the first protocol step is taken by
the tag, we will say that the tag answers to the empty
query (this corresponds to the tag being powered by
the reader).
An RFID system is an instantiation of an RFID
scheme.
3.2 The HPVP Privacy Model
Considerable effort has been put into the develop-
ment of security and privacy models for RFID sys-
tems. Vaudenay’s model (Vaudenay, 2007) and
the Hermans-Pashalidis-Vercauteren-Preneel (HPVP)
model (Hermans et al., 2011; Hermans et al., 2014)
are two of them, with major impact in the study of se-
curity and privacy properties of RFID systems. The
HPVP model borrows the adversary model from Vau-
denay’s model, keeps the same approach to the se-
curity property, but treats privacy in a different way.
If in Vaudenay’s model privacy is based on indistin-
guishability between the RFID system instrumented
by a challenger and the RFID system instrumented by
a blinder (who does not know the secret elements in
the system), the HPVP model treats privacy through
indistinguishability between tags in the RFID system
instrumented by a challenger. This second approach
is closer to the security approach of the usual encryp-
tion systems.
The adversary in the HPVP model is allowed to
query the following oracles:
• CreateReader(): Creates a new reader, and a
unique reference R to it is returned;
• CreateTag(ID): Creates a tag with the identifier
ID by calling SetupT (pk, ID). The tag is regis-
tered in the server’s database (that is, the oracle
creates only legitimate tags). Moreover, duplicate
tags with the same ID are accepted. A unique ref-
erence T to the tag is returned;
• RegisterTag(T, R): Registers the tag T with the
reader R;
• Launch(R): Launches a new protocol instance
with the reader R, assigns a unique identifier π to
it, and outputs π;
SECRYPT 2024 - 21st International Conference on Security and Cryptography
130

• DrawTag(T
0
,T
1
): Generate a fresh virtual tag ref-
erence vtag that refers to either the left tag T
0
or to the right tag T
1
, depending on the privacy
game where the oracle is queried. The triple
(vtag,T
0
,T
1
) is included in a list Γ of drawn tags,
and vtag is returned by the oracle.
The oracle returns ⊥ in any of the following cases:
– If one of the two tags is in the insider list;
– If one of the two tags is registered with a differ-
ent set of readers than the other tag;
– If T
0
(T
1
) is already referenced as the left-hand
(right-hand) side tag in Γ;
• Free(vtag): This oracle resets (erases the tempo-
rary state of) the tag referenced by vtag and re-
moves the corresponding triple from Γ;
• SendTag(m,vtag): Outputs the tag’s answer when
the message m is sent to the tag referred to by
vtag. When m is the empty message, this oracle
outputs the first message of the protocol instance
π, assuming that the tag does the first step in the
protocol;
• SendReader(R, m, π): Outputs the R’s reader an-
swer when the message m is sent to it as part of
the protocol instance π. When m is the empty
message, abusively but suggestively denoted by
/
0,
this oracle outputs the first message of the proto-
col instance π, assuming that the reader does the
first step in the protocol;
• Result(π): Outputs ⊥ if in session π the reader has
not yet made a decision on tag authentication (this
also includes the case when the session π does not
exist), 1 if in session π the reader authenticated
the tag, and 0 otherwise (this oracle is both for
unilateral and mutual authentication);
• Corrupt(T ): Outputs the full (permanent and
temporary) state of the tag T . Remark that the cor-
ruption is with respect to a tag, not a virtual tag.
Otherwise, it would be easy for an adversary with
corruption capabilities to distinguish between the
left and the right privacy games (Hermans et al.,
2011; Hermans et al., 2014);
• CreateInsider(ID): Creates a tag and returns a
unique reference T to it and its full state. The tag
is included in a list of insider tags. This oracle is
a method of giving the adversary the internal state
of a tag but without considering that the adversary
has used the corruption oracle.
We will now classify the adversaries as follows:
1. Adversaries with no access to CreateInsider.
These are further classified according to the way
the Corrupt oracle is used:
(a) Weak adversaries: no access to the Corrupt or-
acle;
(b) Forward adversaries: once they access the
Corrupt oracle, the only oracle they can access
is Corrupt;
(c) Destructive adversaries: after accessing the
Corrupt(T ) oracle, the tag T is destroyed (but
the information about T is kept in the database);
(d) Strong adversaries: no restrictions;
(e) Narrow weak (narrow forward, narrow de-
structive, narrow strong): as above but the ad-
versary has no access to the Result oracle;
2. Adversaries with access to CreateInsider. The
power of a destructive or strong adversary
does not increase if he is given access to the
CreateInsider oracle. As a result, we distinguish
the following two classes of adversaries:
(a) Weak-insider adversaries: weak adver-
saries with supplementary access to the
CreateInsider oracle;
(b) Forward-insider adversaries: forward ad-
versaries with supplementary access to the
CreateInsider oracle.
Some authors (Hermans et al., 2014) refer to the
classes of adversaries from (1)(a)-(d) as being wide
in the sense that the adversaries in these classes may
consult the Result oracle.
The practical use of RFID schemes requires that
they provide some level of security and privacy. Our
paper focuses only on the privacy property. However,
for completeness, we briefly recall the security prop-
erty, too. Security means that no strong adversary has
more than a negligible probability to make the reader
authenticate an uncorrupted legitimate tag without
having any tag authentication matching conversation.
When the RFID scheme is with mutual authentica-
tion, besides the above requirement, it is asked that no
strong adversary has more than a negligible probabil-
ity to make an uncorrupted legitimate tag to authenti-
cate the reader without having any reader authentica-
tion matching conversation.
As with respect to privacy, define the experiment
RFID
hpvp−prv−b
A,Σ
(λ), where b ∈ {0,1}, A is an adver-
sary, and Σ is the RFID scheme, as follows:
RFID
hpvp−prv−b
A,Σ
(λ)
1. Set up reader;
2. A gets pk;
3. A is given access to oracles. For b = 0, all tempo-
rary identities refer to the left tag drawn by adver-
sary, while for b = 1 they refer to the right tag;
On Privacy of RFID-Based Authentication Protocols
131

4. A outputs a bit b
′
;
5. Return 1 if b
′
= b, and 0, otherwise.
For b = 0 (b = 1) this experiment will also be called
the left (right) privacy game.
The advantage of A against Σ is defined as
Adv
hpvp−prv
A,Σ
(λ) =| P(RFID
hpvp−prv−0
A,Σ
(λ) = 1)+
P(RFID
hpvp−prv−1
A,Σ
(λ) = 1) − 1 |
Now, we say that Σ is C -private, where C is a class
of adversaries, if the advantage of any adversary in
class C against Σ is negligible.
The previously defined adversary classes lead to a
ranking of the privacy property of RFID schemes as
shown in the diagram in Figure 1.
3.3 PUF-Based RFID Systems
One of the primary reasons that led to the devel-
opment of physically unclonable functions (PUFs)
was to find a method of protecting the secret keys
against software and physical attacks (R
¨
uhrmair and
van Dijk, 2013). A PUF can be considered a disor-
dered physical system that can be challenged with ex-
ternal stimuli (challenges) to which it will react with
corresponding responses. Unlike standard digital sys-
tems, the reaction of a PUF to a challenge depends
on the micro- or nanoscale structural disorder of the
PUF. Ideally, it is assumed that:
1. This disorder cannot be cloned or reproduced pre-
cisely, even by PUF’s original manufacturer;
2. The response r of the PUF to a challenge c is
uniquely and uniformly at random chosen from
the space of possible responses;
3. PUFs are tamper-evident (fully invasive attacks
either damage or alter the functional behavior).
As a result, an ideal PUF defines a unique function
P. The pairs (c,r) with P(c) = r are called challenge-
response pairs (CRP).
The (ideal) properties of PUFs mentioned above,
as well as the technological progress aimed at achiev-
ing these properties, led to the proposal of security
protocols that include them in various forms. Thus,
we can mention protocols for oblivious transfer, bit
commitment, key exchange, key generation, or au-
thentication (R
¨
uhrmair and van Dijk, 2013; Delvaux,
2017; Gope and Sikdar, 2021). For example, (Del-
vaux, 2017) reviews key generators and authentica-
tion protocols based on PUFs proposed up to 2016.
Among newer protocols, we mention (T¸ iplea and
Hristea, 2021; Gao et al., 2022).
As far as we know, the first use of PUFs in RFID
systems appears in (Sadeghi et al., 2010b; Sadeghi
et al., 2010a) to provide a solution to the problem of
finding a private destructive RFID system in Vaude-
nay’s model. Later, the use of PUFs in RFID sys-
tems gained momentum (see (T¸ iplea et al., 2021) for
an ample discussion on this topic). The method of use
is as follows:
• Tags are endowed with PUFs and store secret in-
formation (usually a secret key);
• When the tag authenticates itself to the reader, it
interrogates the PUF and extracts that secret infor-
mation, which will then be used in preparing the
message for the reader.
Tags with PUFs embedded into them are usually
called PUF tags. A PUF-based RFID scheme is an
RFID scheme with PUF tags.
The previously discussed adversary model is triv-
ially extended to the case of PUF tags. We only need
to discuss the Corrupt and CreateInsider oracles:
1. Due to PUF’s tamper-evident property, no adver-
sary with the possibility of corrupting PUF tags
can obtain the secret information stored in the
PUF. So, the Corrupt(T ) oracle returns only the
full state of the tag as in the standard case;
2. Due to the non-clonability of PUFs,
CreateInsider(ID) creates a tag with the
identity ID and lets the adversary simulate its
PUF through a list of randomly generated pairs.
This makes this oracle have a behavior similar to
that of the original approach.
As a result of these, the classification and ranking of
the privacy properties in Figure 1 remains the same
for the case of PUF-based RFID schemes.
4 TWO DESIGN SCENARIOS IN
THE HPVP MODEL
In the last fifteen years, RFID-based authentication
has diversified both as a technology and in appli-
cations. If we were talking about backend server-
based RFID authentication at the beginning, we
are also talking about cloud-based RFID authentica-
tion. RFID authentication applications have pene-
trated healthcare, IoT, and automotive. PUF technol-
ogy has begun to be incorporated into RFID-based
authentication techniques. Regardless of how RFID-
based authentication is done or its applications, the
privacy component has a dominant importance. The
privacy models developed for standard RFID schemes
can easily be extended to either backend server-based,
SECRYPT 2024 - 21st International Conference on Security and Cryptography
132
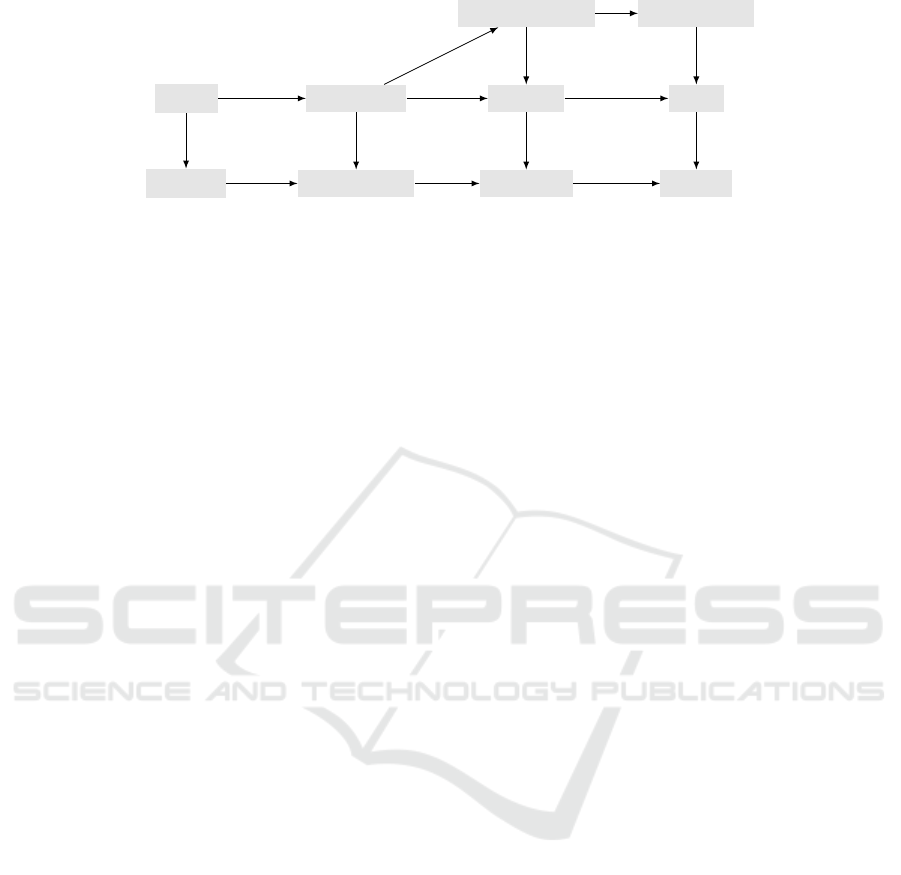
forward-insider weak-insider
strong
destructive forward weak
n-strong
n-destructive n-forward n-weak
Figure 1: Privacy levels in the HPVP model: “n-p” means “narrow p” and an arrow means “implication”.
cloud-based, or PUF-based authentication. In addi-
tion, we consider that the approach to privacy proper-
ties through the HPVP model offers at least two sig-
nificant advantages:
1. A rich palette of privacy properties covering the
most practical applications;
2. Precise proof techniques based on indistinguisha-
bility in the same line as those used in the study
of the security of other cryptographic primitives.
In this section, we will present two scenarios that,
once identified in the structure of an RFID-based au-
thentication scheme, clearly show that the scheme is
not private in the HPVP model. Each scenario is
rigorously argued and exemplified by RFID schemes
proposed in the specialized literature.
4.1 Tag Identifiers
In most cases, the first step of an RFID protocol is
performed by the reader, who sends the tag a message
that can include a fresh random. The tag’s answer
may or may not depend on the reader’s initial query,
but what is most important is that it must include a
specific information to help the reader in the tag iden-
tification process. We call this particular information
a tag identifier.
In general, any information from the permanent
memory of the tag, such as tag’s identity ID or any
secret K shared by the tag and the reader, can play the
role of tag identifier. Also, any message obtained by
applying a function that the reader can calculate on
some tag identifiers also becomes a tag identifier. For
example, h(ID), h(ID, r1) or {ID, r
1
}
K
are tag identi-
fiers, assuming that h is a known hash function, {·}
K
denotes encryption by K, and r
1
is a random number
previously transmitted by the reader and known to the
tag. However, h(ID, r
1
,r
2
) can no longer be consid-
ered a tag identifier if r
2
is a random number gener-
ated by the tag and the reader has no way to learn it.
But if the reader can learn r
2
, then h(ID, r
1
,r
2
) be-
comes a tag identifier.
Let’s now assume that we have an RFID protocol
with at least two steps, like this:
1. In the first step of the protocol, the reader gener-
ates a random number r
1
and sends it to the tag;
2. In the second step, the tag answers with h(ID, r
1
).
If an adversary can interact with the tag (in the sense
that he can impersonate the reader, for example), then
he can query the tag with a random parameter r
1
cho-
sen at his will, and after receiving the tag’s answer,
abort the protocol. He then repeats this procedure,
with the same parameter r
1
, as many times as he
wants. In this way, the adversary manages to trace the
tag. But if the tag had included a parameter r
2
ran-
domly generated for each query, i.e. its answer would
have been h(ID,r
1
,r
2
), then the adversary would not
have succeeded in tracing the tag because h(ID, r
1
,r
2
)
would have changed from session to session (r
2
is ran-
domly generated each time).
We thus arrive at the following definition. We say
that a tag identifier is non-randomized if querying the
same tag with the same message two or more times
in a row in order to obtain its tag identifier, the tag
identifier is the same.
The non-randomization of the tag identifier leads
to the total lack of privacy in the HPVP model, as
shown below. To facilitate the discussion, we will as-
sume that the tag identifier is sent to the reader in the
tag’s first message (obviously, the debate can be ex-
tended).
Theorem 4.1. Let Σ be a (PUF-based) RFID scheme
for which it can be decided in deterministic polyno-
mial time whether two tag’s answers include or not
the same tag identifier. If Σ has non-randomized tag
identifiers, then it does not achieve narrow weak pri-
vacy in the HPVP model.
Proof. Assume Σ is a (PUF-based) RFID scheme as
in the theorem and the reader takes the first step in
the communication protocol. Consider the following
narrow weak adversary A that plays the following pri-
vacy game with Σ:
1. A creates three tags T
1
, T
2
, and T
3
;
2. A draws (T
1
,T
2
) with some temporary identity
vtag
1
;
On Privacy of RFID-Based Authentication Protocols
133

3. A plays with vtag
1
until it gets the first message
that includes the tag identifier;
4. A frees vtag
1
;
5. A draws (T
1
,T
3
) with some temporary identity
vtag
2
;
6. A plays with vtag
2
until it gets the first message
that includes the tag identifier;
7. A outputs 0 (the left privacy game) if the two mes-
sages from vtag
1
and vtag
2
include the same tag
identifier, and 1, otherwise.
Step 7 above can be performed in deterministic poly-
nomial time according to the theorem’s hypothesis.
One can easily see that this adversary guesses
with overwhelming probability which privacy game
is playing. So, Σ does not achieve narrow weak pri-
vacy in the HPVP model.
There are quite a few protocols, based on PUF or
not or that use cloud support, that satisfy the require-
ments of the previous theorem. A selection of some
of these more recent ones is presented below:
1. (Xiao et al., 2016): The parameter M1 from the
first message of the tag to the reader includes the
identifier of the tag (Tid) and is non-randomized;
2. (Xu et al., 2018): The first message of the tag
contains in the clear a tag identifier, namely FID,
which changes much later;
3. (Fan et al., 2018): The T ID identifier is sent non-
randomized by tag in its first message;
4. (Fan et al., 2019): The SID identifier in M
T 1
is
sent non-randomized by tag in its first message;
5. (Fan et al., 2020): The timestamp T
t
identifies the
tag and is sent non-randomized in M(T
t
) in the
tag’s first message (the timestamp updates later
independently of the system’s local time);
6. (Zhu et al., 2020): The tag sends in its first step,
in the clear, the identifier SID;
7. (Xiao et al., 2020): The tag sends in its first step,
in the clear, the identifier FID
new
;
8. (Safkhani et al., 2020): The tag sends in its first
step, in the clear, the identifier IDS
ti
;
9. (Kumar et al., 2023): The tag sends in its first step,
in the clear, the identifier IDS.
4.2 Temporary Variables
The use of temporary variables in the construction of
protocols is generally necessary. In particular, global
temporary variables have a vital role because they
store values calculated at a specific step in the pro-
tocol to be checked in a later step. This is the case,
for example, of challenge-and-response authentica-
tion protocols.
By corrupting devices (such as RFID tags) that
use temporary variables in executing a specific pro-
tocol, the values of these variables can be obtained
(at the time of corruption). This can lead to sig-
nificant vulnerabilities in the protocol used. A gen-
eral result on this aspect has been mentioned since
2010 (Armknecht et al., 2010) within the RFID pro-
tocols. This result shows that it is impossible to ob-
tain both mutual authentication and narrow forward
privacy in Vaudenay’s model if the adversary can ob-
tain the global variables’ value used in the authen-
tication of the reader by the tag. This result draws
our attention to the use of temporary variables (es-
pecially global ones) in identification and authentica-
tion protocols, which must be done with great care.
(T¸ iplea and Hristea, 2021) proposes a general tech-
nique to protect global temporary variables. Another
technique, with a narrow spectrum, is that in (T¸ iplea
et al., 2022).
The HPVP privacy model considers the possibil-
ity of corruption by revealing the value of temporary
variables (see the Corrupt oracle in Section 3). How-
ever, there is a very subtle aspect here. Namely, the
Free oracle resets the tag referred to by the virtual
tag, and the adversary cannot corrupt the virtual tag.
As a result, the adversary might not obtain the values
of the temporary variables by corrupting the tag. Ob-
viously, this does not exclude the possibility that the
adversary can identify the tag referred to by the vir-
tual tag. The following general result applies exactly
to this situation.
Theorem 4.2. Let Σ be a (PUF-based) RFID scheme
such that given two tags, given the sequence of mes-
sages exchanged by one of them with the reader in a
protocol session until the tag has to authenticate the
reader, and given the tags’ full states, one can decide
with overwhelming probability which of the two tags
authenticates the reader. Then, Σ cannot achieve both
reader authentication and narrow forward privacy in
the HPVP model.
Proof. Under the hypothesis of Theorem 4.2, we de-
fine the following narrow forward adversary A:
1. A creates two tags T
1
and T
2
;
2. A draws the tags under the temporary identity
vtag;
3. A simulates the protocol between the reader and
vtag until the last protocol step played by reader
(including this step) is reached;
4. A frees vtag;
SECRYPT 2024 - 21st International Conference on Security and Cryptography
134

5. A corrupts both tags T
1
and T
2
and gets their full
states;
6. With the reader’s answer (previously obtained)
and the tags full state’s, A will deduce which of
the two tags authenticates the reader;
7. If A decides that the reader is authenticated by T
1
,
then it outputs 0; otherwise, it outputs 1.
One can easily see now that A can distinguish
between the left and right privacy games with over-
whelming probability. Thus, Σ cannot achieve both
reader authentication and narrow forward privacy in
the HPVP model.
We note that the hypothesis of Theorem 4.2 (as
well as its proof) do not explicitly call for the use of
temporary variables, they being included in the tag’s
full state. So, the result from Theorem 4.2 remains
valid even if (global or not) temporary variables are
not used.
There are quite a few protocols that do not take
global temporary variables into account in their anal-
ysis. We present some of them below:
1. (Jin et al., 2015): The protocol uses elliptic curve
cryptography. The verification that the tag does
in the last step to authenticate the reader can also
be done by the adversary if it corrupts the tag and
uses the messages sent between the tag and the
reader until then. More precisely, the adversary
can also calculate e
1
= H
2
(ID
T
i
,r,C, z) and then
check the congruence e
1
≡ e
1
P
R
+ z mod n. As
a result, the hypothesis of Theorem 4.2 holds for
this protocol;
2. The following protocols mentioned in the previ-
ous section also satisfy the requirements of The-
orem 4.2 (we omit the details in this regard be-
cause, anyway, they do not offer any privacy ac-
cording to the previous section): (Xiao et al.,
2016; Fan et al., 2018; Fan et al., 2019; Fan et al.,
2020; Zhu et al., 2020; Xiao et al., 2020; Kumar
et al., 2023);
3. (Aghili et al., 2019) proposed SecLAP to im-
prove the security drawbacks of its predecessor
protocol in (Fan et al., 2018). Unfortunetely, the
scheme uses temporary variables to authenticate
the reader. Later, (Safkhani et al., 2020) shows
that SecLAP is traceable and proposes an im-
proved protocol. However, this new protocol uses
the temporary variable N
1t
(assigned in the tag’s
first step) to authenticate the reader (in the last
step). This variable is sent in clear to the reader.
So, the adversary can get it and, by corrupting the
tag, can compute IS
new
ti
∥ K
n
ti
ew. It is clear then
that the hypothesis of Theorem 4.2 holds for this
protocol;
4. (Azad and Ray, 2019): The tag assigns the vari-
able R
2
in its first step and uses it in the last step
to authenticate the reader. The adversary gets
PSK
i
by corrupting the tag, computes h(PSK
i
),
gets then R
1
from M
1
, and R
2
from M
2
. It is clear
then that the hypothesis of Theorem 4.2 holds for
this protocol.
A particular aspect of this protocol is that the
reader sends, in its first message, personalized in-
formation to the tag as if it knows to which tag
it addresses. This means that the reader tries to
identify the tag by opening, in the worst case, n
sessions with the same tag, where n is the number
of tags in the system;
5. (Adeli et al., 2023): The tag assigns (R
t
)
R
in its
first step, sends it in clear to the reader, and uses
it in the last step to authenticate the reader and the
cloud. By corruption, the adversary gets all the
necessary information to recompute M
c
. So, the
hypothesis of Theorem 4.2 holds for this protocol;
6. (Wang et al., 2023): Proposes an RFID mutual au-
thentication scheme based on matrix encryption.
The scheme uses the temporary variable N
t
to do
mutual authentication. However, N
t
is encrypted
and sent to the reader. By corruption, the adver-
sary can get the encryption/decryption keys and
so it has access to N
t
. It is clear then that the hy-
pothesis of Theorem 4.2 holds for this protocol.
5 USING SIMULATABLE PUFs
In Section 3.3 we introduced the concept of ideal
PUF and used it to extend the HPVP model with
PUF tags. All the protocols mentioned in Section
4 use such PUFs. However, there are also proto-
cols in which the PUF is considered “more realisti-
cally” as a non-deterministic function whose response
depends on process variations, noise, environmental
variables, and aging. However, it is assumed that
all relevant environmental parameters are bounded,
and the evaluation time of any given PUF has an up-
per bound. Therefore, two random evaluations of
the PUF response given the same challenge might
slightly vary with a Hamming distance between them
bounded from above by a constant threshold. In such
a case, one critical attribute of a PUF is the reliability
of its responses, which estimates how consistently the
responses can be generated against varying operating
conditions.
On Privacy of RFID-Based Authentication Protocols
135

In this section we will consider the PUF as a non-
deterministic function, as described above.
A simulatable PUF (R
¨
uhrmair and van Dijk,
2013; Gao et al., 2022) is a pair consisting of a PUF
and a parameterized model SimPUF capable of com-
puting a response r and its corresponding reliability
confidence con f in polynomial time for any given
challenge c (i.e., (r,con f ) ← SimPUF(c)), such that:
1. SimPU F is constructed using one-time privileged
access by an authorized party in a secure environ-
ment and subsequent acquisition of SimPUF by
any party is disabled;
2. If r
′
← PUF(c), then r
′
is indistinguishable from
r in the sense that P(r = r
′
) is ε-close to 1;
3. The estimated con f is ε-close to the reliability
confidence of r
′
.
The use of a non-deterministic PUF P on a tag
raises the problem of selecting the answer to a chal-
lenge c. However, having stored on the reader a Sim-
PUF P
′
associated with P, there are procedures that
can decide in polynomial time the answer of P on c.
Such a procedure is TREVERSE proposed in (Gao
et al., 2022). This uses P
′
for possible responses of
P to c, and the correct selection is made based on a
pseudo-random function F. The authentication pro-
tocol is the one in Figure 2. The server initiates the
protocol by sending a challenge c to the tag. The tag
queries its (non-deterministic) PUF, obtains r ← P(c),
and responds with (x
1
,y = F
r
(x
1
)), where x
1
is a ran-
dom value and F is a pseudo-random function shared
by the server and tag. When the server receives the
tag response, it uses P
′
, the model of the PUF P, and
the TRESERVE function to determine r
t
, the possible
response of P. The check is done by “y = F
r
t
(x
1
)”.
If such a value is found, the tag is authenticated and
announced. Otherwise, the protocol is aborted. In the
case of tag authentication, it sends the server a ran-
dom value x
2
and receives z = F
r
t
(x
2
). The value z is
checked against F
r
(x
2
). If the values match, the tag
authenticates the server.
The protocol uses r and x
2
as temporary variables.
However, the Free oracle resets the virtual tag, so the
adversary cannot recover their values by corruption.
This protocol would not be narrow forward private
in Vaudenay’s model (see Theorem 3.1 in (T¸ iplea,
2022)). In the HPVP model, things are different with
this protocol. We will show that it is strongly private
in this model. Before this, we will simplify it to the
protocol in Figure 3.
In the theorem below, we will assume that the
PUF P is random. We draw attention to the fact
that in this section, we consider the PUF as a non-
deterministic process. As a result, it can answer dis-
tinct queries with the same challenge differently, but
its answer conforms to the definition adopted for sim-
ulable PUFs.
Theorem 5.1. The mutual authentication scheme in
Figure 3 provides strong privacy in the HPVP model,
provided that P behaves randomly and F is a PRF.
Proof. Let Σ be the scheme in Figure 3. Assume that
Σ is not strong private in the HPVP model, and let
A be a strong adversary that can break Σ’s privacy.
We will show that there is an adversary B that has
a non-negligible advantage in the pseudo-randomness
game with F. Let C be a challenger for the pseudo-
randomness game with F.
B will simulate Σ (will be the challenger) in the
privacy game that A plays with Σ. So, B will have to
simulate the oracles for A. B does not know the secret
parameters of the scheme but will want the simulation
it performs to be indistinguishable from the real pri-
vacy game between A and Σ. We will show below
how the oracles are simulated:
1. B keeps a list R of readers that will be created
by adversary, and a list of tags T
R
registered with
each reader R ∈ R . Initially, these lists are empty;
2. B keeps a list T of tags that will be created in
the system in the order in which they are created.
Each tag receives a fresh reference. We recall that
the HPVP model allows the creation of several
tags with the same identity. The corrupted (in-
sider) tags will be stored in a separate list cT (iT ),
initially empty;
3. B will simulate the tag T ’s PUF as a list of
challenge-response pairs. Initially, this list, de-
noted P(T ), is empty. When evaluating the PUF
on c, B looks in P(T ) a pair (c,r), for some r. If
such a pair is found, r will be returned as the value
of P on c; otherwise, a random value r is gener-
ated and (c,r) will be included in P(T ), returning
r at the same time.
It is clear that B simulates P deterministically.
However, the adversary cannot distinguish be-
tween the real simulatable PUF and the one simu-
lated by B due to the properties that a simulatable
PUF enjoys and the fact that the response given
by the tag is randomized each time by x;
4. B keeps a list (table) Γ of active triples
(vtag,T
0
,T
1
) as specified in the oracle DrawnTag.
The oracle Free(vtag) removes (vtag,T
0
,T
1
) from
Γ. We draw attention to the fact that Γ can contain
at most one triple with vtag in the first position;
5. B will keep a list Q of (query,ext answer) pairs,
where query is a query of A and ext answer is a
SECRYPT 2024 - 21st International Conference on Security and Cryptography
136

Server (Reader) (SimPUF P
′
, PRF F) Prover (Tag) (PUF P, PRF F)
1
c ← {0, 1}
ℓ
c
−−→
2 r ← P(c)
x
1
← {0,1}
m
x
1
, y
←−−−
y := F
r
(x
1
)
3 If f ail ← T REV ERSE(c,P
′
,x
1
,y)
then abort
else let r
t
be its output (i.e., y = F
r
t
(x
1
))
authenticate tag auth
−−−→
4 x
2
←−−
x
2
← {0,1}
m
5 z := F
r
t
(x
2
) z
−−→
6 if z = F
r
(x
2
)
then authenticate server
else abort
Figure 2: SimPUF-Based authentication scheme in (Gao et al., 2022).
Server (Reader) (SimPUF P
′
, PRF F) Prover (Tag) (PUF P, PRF F)
1
c ← {0, 1}
ℓ
c
−−→
2 r := P(c)
x ← {0,1}
m
x, y
←−−
y := F
r
(x,0)
3 If f ail ← T REV ERSE(c,P
′
,x,y)
then abort
else let r
t
be its output
authenticate tag
z := F
r
t
(x,1) z
−→
4 if z = F
r
(x,1)
then authenticate server
else abort
Figure 3: SimPUF-Based strong private authentication scheme in the HPVP model.
possibly detailed information from which the an-
swer to the query is extracted;
6. CreateReader(): B generates a unique reader ref-
erence R, answers to A with R, and includes R in
R . Moreover,
(CreateReader(),R)
is included in Q ;
7. CreateTag(ID): B generates a fresh tag reference
T , associates it with ID, initializes P(T ) by the
empty list, includes the pair (T,ID) in T , and an-
swers to A with T . Moreover,
(CreateTag(ID),T )
is included in Q ;
8. RegisterTag(T, R): B includes T in the list T
R
and
(RegisterTag(T, R),
/
0)
in Q ;
9. Launch(R): B generates a fresh session identifier
π, returns it to A, and includes
(Launch(R),(R, π))
in the list Q ;
10. DrawTag(T
0
,T
1
): B checks if the constraints of
the DrawTag oracle are satisfied. If they are not
satisfied, the answer ⊥ is returned. Otherwise,
B generates a fresh virtual tag reference vtag, in-
cludes (vtag,T
0
,T
1
) in Γ, and answers to A with
vtag. In Q the following pair is included
(DrawTag(T
0
,T
1
),⊥/vtag),
On Privacy of RFID-Based Authentication Protocols
137

where ⊥/vatg is for the first/second case, resp.;
11. Free(vtag): the triple whose first component is
vtag is removed from Γ (if it is in Γ). In this case,
the pair
(Free(vtag),
/
0)
is included in Q ;
12. SendTag(c,vtag): B extracts from Γ the triple
whose first component is vtag. If no such
triple exists, the answer is ⊥. Otherwise, let
(vtag,T
0
,T
1
) be this triple. B searches each list
P(T
0
) and P(T
1
) for a pair with c in the first po-
sition. If one of the lists does not contain such a
pair, B generates a random r and includes (c, r)
in that list. Now suppose that (c,r
0
) ∈ P(T
0
) and
(c,r
1
) ∈ P(T
1
). B randomly generates x, queries
C with ((r
0
,x,0),(r
1
,x,0)) and returns (x,y) to A.
In Q is included
(SendTag(c,vtag),⊥/(c,r
0
,r
1
,x,y)),
depending on one of the two cases above;
13. SendReader(R, (x, y),π): Since x is generated
randomly at each query of a tag, and y is cal-
culated from x through a PRF function, x and y
can be found in at most one tuple (c,r
0
,r
1
,x,y)
previously computed by B when R queried some
tag by c. In addition, x and y can only appear
independently with negligible probability. As a
result, if B does not find in Q a tuple like the
one above, it responds with ⊥. Otherwise, it ex-
tracts the only tuple (c,r
0
,r
1
,x,y), queries C with
((r
0
,x,1),(r
1
,x,1)), and returns the answer z of
C .
In Q , the pair below is included depending on one
of the two cases above
(SendReader(R, (x,y), π), ⊥/(c, r
0
,r
1
,x,y,z));
14. Result(π): Having the entire history of the privacy
game up to the moment of this query, B can an-
swer faithfully whether the tag was authenticated
by the reader or not, or there is another case out-
side of these. In Q , it will include
(Result(π), 1/0/⊥),
depending on the case;
15. Corrupt(T ): The tag T has no permanent vari-
ables, its only global temporary variables being c
and x. Through corruption its PUF is destroyed.
As a result, if the tag is not in T , B has nothing
to return to A. Otherwise, it returns the global
temporary variables c and x, which A has learned
from previous communications anyway. B moves
then T form T into the list cT of corrupted tags.
The pair
(Corrupt(T ),
/
0/(c,x))
is included in Q (depending on the case).
16. CreateInsider(ID): B creates a new tag reference
T , associates it with ID, returns T to A, and in-
cludes (T, ID) in iT . Moreover,
(CreateInsider(ID), T)
is included in Q .
It is as clear as possible that the probability with
which B guesses to which component, left or right,
C applied the function F is precisely the probability
with which A guesses with which tag, left or right,
played the privacy game for the Σ scheme. Therefore,
the assumption that the protocol is not strongly private
will contradict the pseudo-randomness of F. So, the
protocol must be strongly private.
6 CONCLUSIONS
Analyzing many authentication protocols based on
RFID highlights that their privacy properties are es-
tablished by ad hoc techniques or informally. Try-
ing to do this analysis uniformly in a general model
like the HPVP model, it was found that many of these
protocols do not ensure privacy. We thus identified
two major problems that lead to the lack of privacy of
these protocols; we rigorously demonstrated this and
abundantly exemplified both techniques. We then fo-
cused on a protocol based on simulatable PUFs and
showed that a simplified version of it achieves strong
privacy in the HPVP model.
Apart from those in Section 4, other scenarios that
can lead to a low degree of privacy or even its absence
are those in (Hristea and T¸ iplea, 2020; T¸ iplea, 2022).
A detailed analysis of them is undoubtedly necessary.
REFERENCES
Adeli, M., Bagheri, N., Sadeghi, S., and Kumari, S. (2023).
χperbp: a cloud-based lightweight mutual authenti-
cation protocol. Peer Peer Netw. Appl., 16(4):1785–
1802.
Aghili, S. F., Mala, H., Kaliyar, P., and Conti, M. (2019).
SecLAP: Secure and lightweight RFID authentication
protocol for medical IoT. Future Generation Com-
puter Systems, 101:621–634.
Armknecht, F., Sadeghi, A.-R., Scafuro, A., Visconti, I., and
Wachsmann, C. (2010). Impossibility results for RFID
privacy notions. In Gavrilova, M. L., Tan, C. J. K.,
and Moreno, E. D., editors, Transactions on Com-
putational Science XI, pages 39–63. Springer-Verlag,
Berlin, Heidelberg.
Azad, S. and Ray, B. (2019). A lightweight protocol for
RFID authentication. In 2019 IEEE Asia-Pacific Con-
ference on Computer Science and Data Engineering
(CSDE), pages 1–6.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
138

T¸iplea, F. L. (2022). Narrow privacy and desynchronization
in Vaudenay’s RFID model. International Journal of
Information Security, 22:563–575.
T¸iplea, F. L., Andriesei, C., and Hristea, C. (2021). Security
and privacy of PUF-based RFID systems. In Cryptog-
raphy - Recent Advances and Future Developments.
IntechOpen. ISBN 978-1-83962-566-4.
T¸iplea, F. L., Hristea, C., and Bulai, R. (2022). Privacy
and reader-first authentication in Vaudenay’s RFID
model with temporary state disclosure. Comput. Sci.
J. Moldova, 30(3):335–359.
Delvaux, J. (2017). Security analysis of PUF-based key
generation and entity authentication.
Fan, K., Jiang, W., Li, H., and Yang, Y. (2018). Lightweight
RFID protocol for medical privacy protection in
IoT. IEEE Transactions on Industrial Informatics,
14(4):1656–1665.
Fan, K., Luo, Q., Zhang, K., and Yang, Y. (2020). Cloud-
based lightweight secure rfid mutual authentication
protocol in iot. Information Sciences, 527:329–340.
Fan, K., Zhu, S., Zhang, K., Li, H., and Yang, Y. (2019).
A lightweight authentication scheme for cloud-based
RFID healthcare systems. IEEE Network, 33(2):44–
49.
Gao, Y., van Dijk, M., Xu, L., Yang, W., Nepal, S.,
and Ranasinghe, D. C. (2022). TREVERSE: TRial-
and-Error lightweight secure ReVERSE authentica-
tion with simulatable PUFs. IEEE Transactions on
Dependable and Secure Computing, 19(1):419–437.
Gope, P. and Sikdar, B. (2021). A comparative study of de-
sign paradigms for PUF-based security protocols for
iot devices: Current progress, challenges, and future
expectation. Computer, 54(11):36–46.
Hermans, J., Pashalidis, Andreasand Vercauteren, F., and
Preneel, B. (2011). A new RFID privacy model. In
Atluri, V. and Diaz, C., editors, Computer Security –
ESORICS 2011, pages 568–587, Berlin, Heidelberg.
Springer Verlag.
Hermans, J., Peeters, R., and Preneel, B. (2014). Proper
RFID privacy: Model and protocols. IEEE Transac-
tions on Mobile Computing, 13(12):2888–2902.
Hristea, C. and T¸ iplea, F. L. (2020). Privacy of stateful
RFID systems with constant tag identifiers. IEEE
Transactions on Information Forensics and Security,
15:1920–1934.
Jin, C., Xu, C., Zhang, X., and Zhao, J. (2015). A se-
cure RFID mutual authentication protocol for health-
care environments using elliptic curve cryptography.
J. Medical Syst., 39(3):24.
Katz, J. and Lindell, Y. (2020). Introduction to Modern
Cryptography. Chapman & Hall/CRC, 3rd edition.
Kumar, A., Singh, K., Shariq, M., Lal, C., Conti, M., Amin,
R., and Chaudhry, S. A. (2023). An efficient and
reliable ultralightweight RFID authentication scheme
for healthcare systems. Computer Communications,
205:147–157.
Paise, R.-I. and Vaudenay, S. (2008). Mutual authentication
in RFID: Security and privacy. In Proceedings of the
2008 ACM Symposium on Information, Computer and
Communications Security, ASIACCS ’08, pages 292–
299, New York, NY, USA. ACM.
R
¨
uhrmair, U. and van Dijk, M. (2013). PUFs in security
protocols: Attack models and security evaluations. In
2013 IEEE Symposium on Security and Privacy, pages
286–300.
Sadeghi, A.-R., Visconti, I., and Wachsmann, C. (2010a).
Enhancing rfid security and privacy by physically
unclonable functions. In Sadeghi, A.-R. and Nac-
cache, D., editors, Towards Hardware-Intrinsic Se-
curity: Foundations and Practice, pages 281–305,
Berlin, Heidelberg. Springer Berlin Heidelberg.
Sadeghi, A.-R., Visconti, I., and Wachsmann, C. (2010b).
PUF-enhanced RFID security and privacy. In Work-
shop on secure component and system identification
(SECSI), volume 110.
Safkhani, M., Rostampour, S., Bendavid, Y., and Bagheri,
N. (2020). IoT in medical and pharmaceutical: De-
signing lightweight RFID security protocols for en-
suring supply chain integrity. Computer Networks,
181:107558.
Sipser, M. (2012). Introduction to the Theory of Computa-
tion. Cengage Learning.
Vaudenay, S. (2007). On privacy models for RFID. In Pro-
ceedings of the Advances in Crypotology 13th Interna-
tional Conference on Theory and Application of Cryp-
tology and Information Security, ASIACRYPT’07,
pages 68–87, Berlin, Heidelberg. Springer-Verlag.
Wang, Y., Liu, R., Gao, T., Shu, F., Lei, X., Gui, G., and
Wang, J. (2023). A novel RFID authentication pro-
tocol based on a block-order-modulus variable matrix
encryption algorithm.
Xiao, H., Alshehri, A. A., and Christianson, B. (2016). A
cloud-based RFID authentication protocol with inse-
cure communication channels. In 2016 IEEE Trust-
com/BigDataSE/ISPA, pages 332–339.
Xiao, L., Xu, H., Zhu, F., Wang, R., and Li, P. (2020).
SKINNY-based RFID lightweight authentication pro-
tocol. Sensors, 20(5).
Xu, H., Ding, J., Li, P., Zhu, F., and Wang, R. (2018).
A lightweight RFID mutual authentication protocol
based on physical unclonable function. Sensors,
18(3).
Zhu, F., Li, P., Xu, H., and Wang, R. (2020). A novel
lightweight authentication scheme for RFID-based
healthcare systems. Sensors, 20(17).
T¸iplea, F. L. (2022). Lessons to be learned for a good design
of private RFID schemes. IEEE Transactions on De-
pendable and Secure Computing, 19(4):2384–2395.
T¸iplea, F. L. and Hristea, C. (2021). PUF protected vari-
ables: A solution to RFID security and privacy un-
der corruption with temporary state disclosure. IEEE
Transactions on Information Forensics and Security,
16:999–1013.
On Privacy of RFID-Based Authentication Protocols
139
