
Lightweight Cryptographic Algorithms: A Position Paper
Gabriela Mendes Corr
ˆ
ea de Miranda
1
, Jos
´
e Ant
ˆ
onio Moreira Xex
´
eo
1
and Renato Hidaka Torres
2
1
Military Institute of Engineering, Rio de Janeiro, RJ, Brazil
2
Federal University of Par
´
a, Bel
´
em, PA, Brazil
Keywords:
Cryptographic Algorithms, Lightweight Cryptography, Symmetric Cryptography, Internet of Things, Metrics.
Abstract:
The massive connection of devices and huge data traffic on networks have made information susceptible to
different type of attacks in Internet of Things (IoT) ecosystem. Devices utilized in these settings introduce
complexities in implementing traditional cryptographic solutions, given their constraints such as physical size,
processing requirements, memory limitations, and energy consumption. This position paper motivates ongoing
and future research on this topic by providing a review to identify, analyze, and classify design components
of lightweight cryptographic algorithms. It emphasizes a need to define a set of evaluation metrics and gives
a further research progress in lightweight algorithms implementations in order to contribute design robust
solutions and architectures.
1 INTRODUCTION
IoT refers to a growing network of everyday physical
objects connected to the Internet (Harbi et al., 2021).
A main goal of IoT is to evolve Internet-enabled de-
vices into an interconnected ecosystem, allowing dig-
ital data to be accessible anywhere and anytime.
The number of connected IoT devices is predicted
to grow to 1 trillion by 2025 (Manyika et al., 2015).
These resource constrained devices have inherently
limited memory space, low processing capacity, and
computation power.
Cryptography enables information confidentiality
and integrity. Due to their poor processor and mem-
ory capacities, low end devices cannot support con-
ventional cryptography (Farhan and Kharel, 2019).
This clearly outlines the need to develop Lightweight
Cryptography (LWC).
LWC is a field dealing with algorithms or pro-
tocols specially designed for the usage in restricted
environments (Kouicem et al., 2018). Lightweight
cryptographic algorithms are preferred for providing
low energy consumption, processing, storage capac-
ity, and memory usage.
In this paper, an in-depth research work has been
conducted. The contributions obtained from this re-
search are to discuss: i) the evolution of LWC ciphers;
ii) the design components of existing algorithms and
iii) an analysis between hardware vs software metrics.
This work is structured as follows. Section II
presents the background of security for IoT context
and lightweight ciphers. Section III presents a litera-
ture review for lightweight primitives. Section 4 dis-
cusses research issues. And Section 5 presents the
conclusion.
2 BACKGROUND
2.1 Security for Low-Resource Devices
Security aims to preserve, restore and guarantee the
protection of information in computer systems from
malicious attacks and threats (Kouicem et al., 2018).
IoT enables to improve several applications in var-
ious fields such as healthcare, smarts grids, smart
cities, smart homes as well as other industrial appli-
cations (Sevin and Mohammed, 2021). However, in-
troducing constrained IoT devices and technologies in
such sensitive applications leads to new security and
privacy challenges.
Low-resource devices should resist against some
security challenges as vulnerabilities and heterogene-
ity of communication and information system tech-
nologies, data sensitivity and privacy, resources limi-
tations, mobility, lack of standardization and safety.
Most of IoT applications operate in highly dis-
tributed environments with the use of heterogeneous
smart objects, sensors and actuators that are limited in
terms of power and computation resources.
764
Corrêa de Miranda, G., Xexéo, J. and Torres, R.
Lightweight Cryptographic Algorithms: A Position Paper.
DOI: 10.5220/0012792900003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 764-770
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

Table 1: Characteristics of LWC algorithms.
Characteristics Lightweight
Physical (Cost)
Smaller block size
Smaller key size
Simple rounds
Simple key schedulingPerformance
Security
Adoption of one of the six
structures (SPN, FN, GFN, ARX,
NLFSR, Hybrid)
2.2 Lightweight Ciphers
The existing cryptographic primitives contain two
main categories: asymmetric and symmetric key
cryptography (Stallings, 2013). Symmetric key algo-
rithms as stream ciphers, block ciphers and authenti-
cated encryption algorithms. Asymmetric algorithms
can be divided into encryption algorithms and key dis-
tribution algorithms.
LWC is a group of cryptographic primitives,
methods, and ciphers intended to provide solutions
for resource-limited devices such as IoT (Patel and
Mistry, 2015).
There are two criteria used to determine the
lightweight of a cryptographic algorithm (Thakor
et al., 2021). The first is the software weight of the
cipher defined by the cipher’s time and memory com-
plexities. The second criterion is the hardware weight
of the cipher and it is defined by the cipher’s area and
power consumption. The cipher’s area is represented
by the number of gate equivalencies (GE) used to im-
plement the cipher and the power consumption is the
power demanded during the cipher’s execution.
In order to fulfill security needs lightweight ci-
phers adopts one of the six internal structures: Sub-
stitution Permutation Networks (SPN), Feistel Net-
works (FN), Generalized Feistel Network (GFN),
Add-Rotate-XOR (ARX), NLFSR-based or Hybrid to
immune against the security attacks (Thakor et al.,
2021). The algorithm needs to meet the lightweight
standards while having a similar performance for se-
curity attacks and security standards. The main char-
acteristics of lightweight cryptographic algorithms
are listed in Table 1.
3 LITERATURE REVIEW
3.1 Standardization
Several initiatives have been conducted for standard-
ization for LWC. In 2000 the New European Schemes
for Signatures, Integrity, and Encryption (NESSIE)
proposed a open call for a broad set of primitives pro-
viding confidentiality, data integrity, and authentica-
tion. Between 2004 and 2008, the ECRYPT Stream
Cipher Project (eSTREAM) was an effort to promote
the design of efficient and compact stream ciphers
(Biryukov and Perrin, 2017).
The National Institute of Standards and Technol-
ogy (NIST) had been investigating cryptography is-
sues for constrained environments. In 2023 NIST an-
nounces the selection of the ASCON family (Dobrau-
nig et al., 2021) for LWC standardization.
The International Organization for Standards
(ISO) and the International Electrotechnical Commis-
sion (IEC) has defined standards that include architec-
tures and techniques for information and communica-
tion security. The ISO/IEC 29192 - Lightweight cryp-
tography specifies block ciphers, stream ciphers and
hash functions suitable for lightweight cryptography.
NIST defined LWC as a cryptosystem whose fea-
tures have been optimized to meet the requirements
of resource-constrained devices (Abujoodeh et al.,
2023). Any cryptographic primitive can be consid-
ered lightweight if it can sufficiently justify its re-
source requirements to achieve the intended result.
3.2 Lightweight Cryptographic
Primitives
3.2.1 Asymmetric Encryption
Public key cryptography algorithms such as Rivest
Shamir Adleman (RSA) (Rivest et al., 1978), Elliptic
Curve Cryptography (ECC) (Miller, 1986) and Hy-
perelliptic Curve Cryptography (HECC) (Ranganatha
Rao and Sujatha, 2023) provides security services
and mechanisms such as data confidentiality, data in-
tegrity, access control and non-repudiation.
Asymmetric ciphers require significantly more
computational resources. An optimized asymmetric
algorithm such as ECC performs 100 to 1,000 times
more slowly than a symmetric cipher such as the Ad-
vanced Encryption Standard (AES) algorithm (Eisen-
barth et al., 2007).
ECC emerged as a preferred cryptographic style
due to its shorter key length and reduced power con-
sumption while maintaining a similar level of secu-
rity.
(Khan et al., 2020) and (Aswathy and
Nandagopal, 2021) are examples of proposed
methods.
Enhancing the execution speed of ECC operations
beside reducing energy consumption and memory re-
quirements can improve ECC implementations, be-
Lightweight Cryptographic Algorithms: A Position Paper
765

coming more feasible for IoT devices.
3.2.2 Hashing
Cryptographic hash functions have been implemented
in different cryptographic mechanisms as digital sig-
natures, pseudorandom number generators, key gen-
eration, password security, and blockchains.
Conventional hash function typically has a sizable
internal state size and high power consumption. A
lightweight hash function needs smaller output size
and smaller message size, thus optimized hash func-
tions for short messages might be better suited for
lightweight applications. (Singh et al., 2017).
QUARK (Aumasson et al., 2010) is a lightweight
hash function family designed for resource-
constrained hardware environments, as RFID
tags.
Hashing methods such SPONGENT (Bogdanov
et al., 2011) and PHOTON (Guo et al., 2011) pro-
duces a much smaller memory footprint.
ASCON-HASH (Dobraunig et al., 2021) is a
member of the ASCON family of cryptographic al-
gorithms proposed in the NIST LWC competition.
While a smaller hash digest results in faster com-
putations due to its reduced output size, it’s important
to balance this reduction since a smaller message di-
gest can compromise data integrity by collisions.
3.2.3 Signing
Message Authentication Code (MAC) symmetric ci-
phers are a class of keyed functions used to ensure
that a message has been sent by the true sender and
received without having been altered during transmis-
sion (Duval and Leurent, 2020).
GRAIN-128A (
˚
Agren et al., 2011) is stream ci-
pher proposed as an improvement by enhancing the
security and optional message authentication.
Hummingbird-2 (HB-2) (Engels et al., 2012), op-
tionally produces a MAC for each message processed
and is developed with both lightweight software and
hardware implementation constraints.
The Chaskey (Mouha et al., 2014) cipher is a
permutation-based LWC method for signing mes-
sages. It is patent-free and standardized in ISO/IEC
29192:2015.
The LightMAC (Luykx et al., 2016) cipher offers
compact authentication for resource-constrained plat-
forms, and also allows high-performance parallel im-
plementations.
ACORN (Shi and and, 2019) is a lightweight au-
thenticated encryption cipher finalist on the Competi-
tion for Authenticated Encryption: Security, Applica-
bility, and Robustness (CAESAR).
3.2.4 Streaming
A stream cipher encrypts and decrypts data bit by bit
which means there is continuous transmissions, and is
simpler and quicker compared to block ciphers. This
type of cipher is mainly used in applications where
plaintext size is unknown (Sehrawat and Gill, 2019).
Enocoro (Watanabe et al., 2008) is a family of
hardware-oriented pseudo-random number generator.
It is a lightweight cipher and it has a 128-bit key and
a 64-bit initialization vector value.
Trivium (De Canni
`
ere, 2006) is a hardware ori-
ented synchronous stream cipher which aims to pro-
vide a flexible trade-off between speed and area. It is a
construction based on block cipher design principles.
Enocoro and Trivium are specified as standards
for stream cipher methods within ISO/IEC 29192-
3:2012.
Stream ciphers have a speedy implementation in
hardware but due to lengthy initialization phase and to
some of the communication protocols that do not uti-
lize stream ciphers, these are less preferred over block
ciphers (Sehrawat and Gill, 2019).
Lightweight block ciphers are taking priority over
stream ciphers also due to their lower development
complexity which is an important feature of a cipher.
3.2.5 Block
Key size, block size, structure type, and the encryp-
tion/decryption rounds are the primary considerations
to evaluate a lightweight block cipher (Hatzivasilis
et al., 2018).
Data Encryption Standard (DES) is one of the first
ciphers to be investigated for LWC. The DES variant
DESX (Leander et al., 2007) uses key whitening to
increase the security level and prevent brute force at-
tacks.
CLEFIA (Shirai et al., 2007) makes functions
sharing between data scheduling and key scheduling
parts resulting reduction in the gate size and low cost.
PRESENT (Bogdanov et al., 2011) is a milestone
in the evolution of lightweight block ciphers and is
used along with AES as a benchmark for newer pro-
posals.
The SIMON and SPECK (Beaulieu et al., 2015)
family of block ciphers have multiple instantiations.
The author claimed that SPECK has the highest
throughput in software compared with any block ci-
phers in the literature and SIMON have the best per-
formance in hardware performance.
LEA (Lee et al., 2014) is a software-oriented ARX
which provides a high-speed software encryption on
general-purpose processors.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
766

The block ciphers PRESENT, CLEFIA and LEA
are part of the series of standards ISO/IEC 29192 for
lightweight cryptographic implementations.
3.3 Performance Metrics
Metrics for software and hardware implementations
of lightweight cryptographic algorithms are not iden-
tical because complexity of implementing ciphers op-
erations are different in software and hardware.
3.3.1 Software Metrics
One of the main goals of software implementations
is to keep memory and CPU needs as low as pos-
sible. Memory restrictions, however, are bound to
negatively affect performance. As small memory ele-
ments are utilized, more cycles are needed to execute
an operation.
There are some metrics to check the efficiency of
the ciphers but in general the relevant metrics are the
memory consumption, the code size and the through-
put. Optimized software implementations result in
fast speed thereby utilizing low power consumption.
There is a strong correlation between energy con-
sumption and cycle count and software implementa-
tions are conditioned by the coding style.
The software latency is measured in clock cycles
and is technology independent. However, one related
metric, throughput, may be technology dependent if
the maximum throughput is required since the maxi-
mum frequency of a design is technology dependent.
Power consumption is technology dependent metric
but it is a much less important metric than area (Mat-
sui and Murakami, 2014).
Authors in (Arora, 2012) introduced a Combined
Metric (CM) indicating a trade-off between imple-
mentation size and performance. A better cipher im-
plementation results a smaller metric value. CM is
given by using (1):
CM = codesize[bits] − encryptioncyclecount[cycles]
(1)
The authors in (Baysal and Sahin, 2015) propose
a new metric called ST/A, which is Security times
Throughput over Area. In this new metric given by
using (2), the key size is inserted to the efficiency met-
ric formula where KeySize is the bit size of key used in
the cipher, Throughput is given in bit-per-second, and
Area is gate equivalent (GE) in hardware or memory
usage in software. Hence increase in the key size in-
creases the efficiency of a cipher.
ST /A =
KeySize × T hroughput
Area
(2)
The software implementations are categorized
based on the ROM and RAM requirements. Ultra-
lightweight implementations require up to 4KB
ROM and 256 bytes RAM, low-cost implementa-
tions require up to 4KB ROM and 8KB RAM,
and lightweight implementations require up to 32KB
ROM and 8KB RAM (Hatzivasilis et al., 2018).
Standardization of metrics like throughput, la-
tency, and software efficiency is appropriate for LWC
algorithms. Effective evaluation of their characteris-
tics is required and might be done utilizing mathemat-
ical analysis.
The software implementation performance met-
rics are listed in Table 2.
3.3.2 Hardware Metrics
Hardware lightweight implementations try to reach
the required functionality with the minimum amount
of hardware real-estate (Hatzivasilis et al., 2018).
The basic performance metrics for hardware de-
signs are area, timing, and energy (Blanc et al., 2022).
Chip area is a critical factor and should have a small
value.
CMOS technology is also essential in the hard-
ware implementation of the ciphers affecting both
gate equivalence and energy consumption (Dinu et al.,
2019). It is unfair to make a comparison between two
ciphers without taking into account their CMOS tech-
nologies once the technology also influences the chip
area required in cipher’s implementation.
Power is important as it is related to the power
consumption of a device and attacks related to power
analysis. When frequency is fixed at a low value,
power consumption is directly correlated with the
chip area. A small area predisposes that the circuit
will consume low power.
Figure Of Merit (FoM) given by (Badel et al.,
2010) was used to compare different ciphers. It
was introduced considering the limitations of the effi-
ciency metric for hardware implementation. The FoM
metric is an important parameter that can use different
weight factors for execution time, RAM footprint, and
code size, and may even consider security aspects.
In (Dobraunig et al., 2021) is proposed a new
comparison metric that allows comparison of secu-
rity, time and area. The Figure of Adversarial Merit
(FoAM) combines the security provided by crypto-
graphic structures and components with their imple-
mentation properties providing a new perspective in
building hardware-friendly cryptographic primitives
according to area or FoAM metrics.
Hardware implementations metrics are generally
reflective of the application constraints. These met-
rics are relative, meaning that it is usually possible to
Lightweight Cryptographic Algorithms: A Position Paper
767
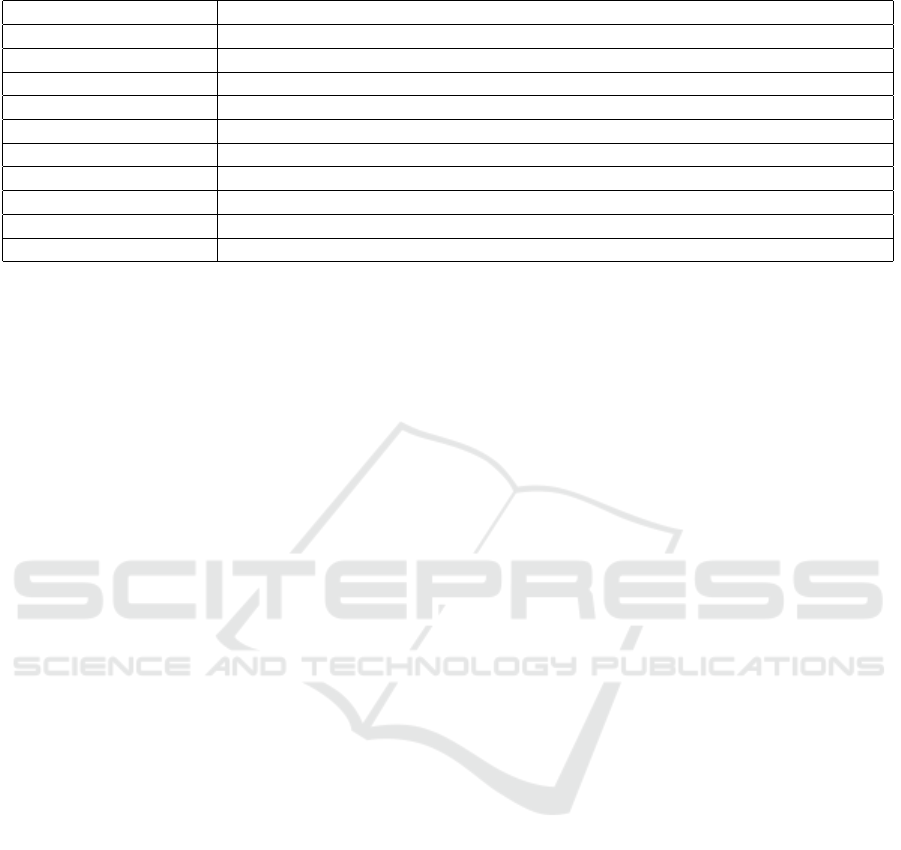
Table 2: Software implementation performance metrics.
Metric Definition
Memory Consumption The amount of data written to memory during each evaluation of the function
Code Size The fixed amount of data which is needed to evaluate the function independently
Throughput Measures the average quantity of data which is processed during each clock cycle
Cycles/byte Cycle count in encryption and decryption, one block Cycles/byte
Energy consumed Given in µJ
Latency The time taken for the computation of one block of either plain-text or cipher-text
Efficiency Requiring little storage and consuming little energy
Power Processing time x Device average power
Combined Metric (CM) A tradeoff between implementation size and performance (code size x cycle)
ST/A Security times Throughput over Area
optimize a single metric eventually, if the other ones
can be compromised. The main consequence of this
relativity is that a fair comparison of hardware im-
plementations is always specific to a particular set of
constraints.
The hardware implementation performance met-
rics are listed in Table 3.
4 DISCUSSION
Given the lightweight cryptographic algorithms chal-
lenges, this position paper highlights the following
points:
• Block sizes, key sizes, and key scheduling should
be taken into consideration and need to be small.
Small blocks and short-key length can simplify
the encryption and decryption process.
• The use of elementary operations as addition,
AND, OR, exclusive or shift are efficient because
simple operations can be applied to all elementary
platforms.
• Increasing the number of iteration rounds and the
length of the key enhances system security, but
faster and stronger ciphers typically come with
higher costs. However, more rounds mean slow-
ness in algorithms.
• For some applications either energy or power con-
sumption are critical whereas for other applica-
tions a low latency is much more important.
• Synthetic metrics are used to combine two or
more non-correlating metrics to capture various
aspects of the performance.
• The energy per bit is an appropriate metric for
energy-constrained low-resource device applica-
tions.
• Only software latency is independent of technol-
ogy, while power and area depend on technology.
• Throughput may depend on technology when the
maximum throughput is needed, as the maximum
frequency depends on the technology being used.
• It is important for a lightweight algorithm occupy
small chip area for its implementation.
In general none of the lightweight algorithms
meets all the criteria for both hardware and software
performance metrics.
A well-defined lightweight metric of cost and per-
formance might check the efficiency of a lightweight
cipher or assess its feasibility for a target application.
There are plenty of implementation choices and the
designs are optimized for specific evaluation metrics.
In contrast from classical algorithms LWC dif-
fer by assuming that lightweight primitives aren’t
designed for wide range application usage and that
there is no need to encrypt a great number of data.
For these environments lightweight implementations
might provide a better balance between security and
performance.
LWC should not be associated with weak cryp-
tography but for classic cryptographic contexts con-
ventional approaches continue to be recommended to
guarantee data security.
Metrics for evaluating the security performance
and hardware and software implementations vary
widely. As mentioned in the previous discussion, be-
cause of this condition, fair comparisons of different
algorithm implementations are a hard issue. There-
fore, standard hardware and software security and
performance metrics should be developed to analyze
LWC security and implementations.
5 CONCLUSION
This position paper presented a research to identify
the lightweight cryptographic algorithms and their de-
sign components in terms of parameters, performance
SECRYPT 2024 - 21st International Conference on Security and Cryptography
768
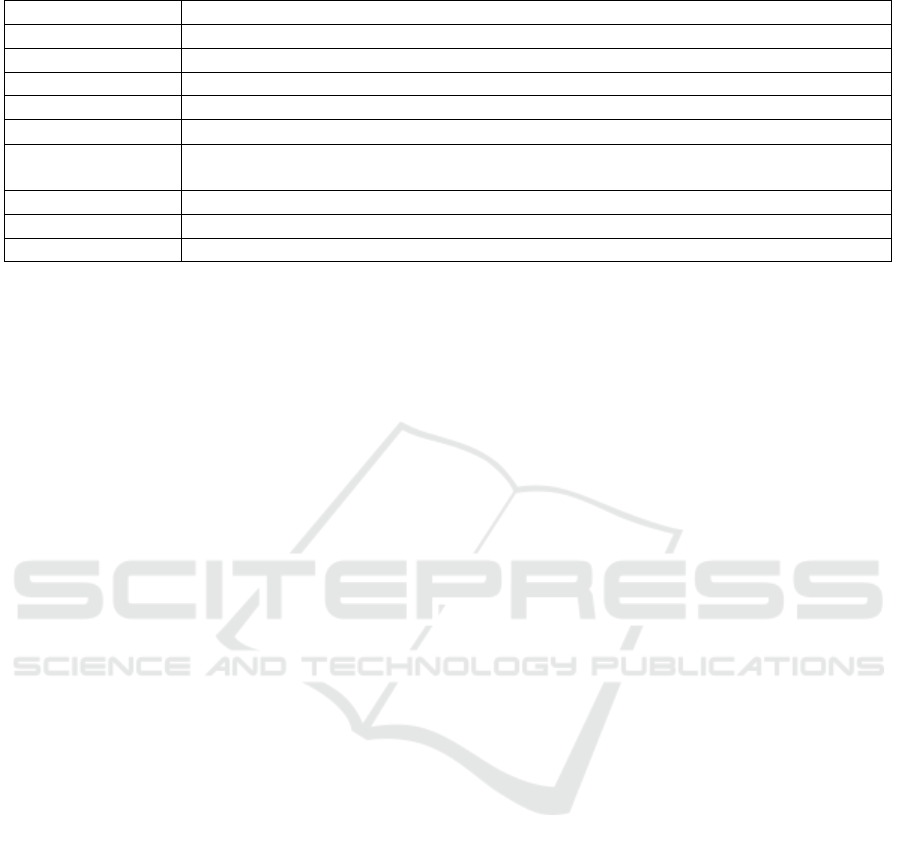
Table 3: Hardware implementation performance metrics.
Metric Definition
Area The chip area occupied is measured in the gate equivalence (GE)
Area/bit The area cost to a single bit
Throughput Measures the average quantity of data which is processed during each clock cycle
Efficiency The ratio of the throughput calculated at a fixed clock frequency over the area
FoM FoM = Throughput/GE
2
FoAM Combines the security provided by cryptographic structures and components with their
implementation properties
Power Indicates the rate of energy consumption. Power is dependent on clock frequency
Energy per bit Normalizes energy with respect to the number of bits in a cipher block
Energy x Area/Bits Combines the two constraints in one expression
and metrics. The objective is to contribute to a better
understanding of the relationship between algorithm
structures, evaluation metrics and implementations to
improve the construction of lightweight algorithms.
Evaluating an appropriate lightweight cipher for a
specific application is multidimensional issue and dif-
ficult to be completely characterized by isolated met-
rics like throughput or key size, and there is no con-
sensus on which one is more appropriate.
Numerous metrics were mentioned and a collec-
tion of the presented metrics might be taken into con-
sideration in order to scale down the device resource
consumption without overlooking the provided secu-
rity.
In this context, we concluded that there is a need
for design a set of optimal metrics that will allow
to propose suitable encryption algorithms to over-
come IoT devices resource constraints. This set must
also integrate qualitative dimensions in order to make
proper comparisons. As a future work we aim to de-
sign this environment for performance evaluation.
New developments constantly emerge, with novel
techniques and algorithms being proposed. Post-
quantum cryptography research is an important field
for IoT networks since LWC primitives and protocols
are insecure against quantum attacks. Even though it
is not our scope, we see it as an important future work.
This work intended to help researchers to improve
IoT security by designing robust solutions and archi-
tectures for resource-constrained environments.
REFERENCES
Abujoodeh, M., Tamimi, L., and Tahboub, R. (2023). To-
ward lightweight cryptography: A survey. In Dek-
oulis, G. and Yadav, J., editors, Computational Se-
mantics, chapter 6. IntechOpen, Rijeka.
Arora, A. (2012). A survey of cryptanalytic attacks on
lightweight block ciphers.
Aswathy, R. and Nandagopal, M. (2021). A design of
lightweight ecc based cryptographic algorithm cou-
pled with linear congruential method for resource con-
straint area in iot. Journal of Ambient Intelligence and
Humanized Computing, 14:1–10.
Aumasson, J.-P., Henzen, L., Meier, W., and Naya-
Plasencia, M. (2010). Quark: A lightweight hash.
In Mangard, S. and Standaert, F.-X., editors, Cryp-
tographic Hardware and Embedded Systems, CHES
2010, pages 1–15, Berlin, Heidelberg. Springer Berlin
Heidelberg.
Badel, S., Dagtekin, N., Nakahara, J., Ouafi, K., Reff
´
e,
N., Sepehrdad, P., Susil, P., and Vaudenay, S. (2010).
Armadillo: A multi-purpose cryptographic primitive
dedicated to hardware. volume 6225, pages 398–412.
Baysal, A. and Sahin, S. (2015). Roadrunner: A small and
fast bitslice block cipher for low cost 8-bit processors.
volume 9542.
Beaulieu, R., Treatman-Clark, S., Shors, D., Weeks,
B., Smith, J., and Wingers, L. (2015). The si-
mon and speck lightweight block ciphers. In 2015
52nd ACM/EDAC/IEEE Design Automation Confer-
ence (DAC), pages 1–6.
Biryukov, A. and Perrin, L. (2017). State of the art in
lightweight symmetric cryptography. IACR Cryptol.
ePrint Arch., 2017:511.
Blanc, S., Lahmadi, A., Gouguec, K., Minier, M., and
Sleem, L. (2022). Benchmarking of lightweight cryp-
tographic algorithms for wireless iot networks. Wire-
less Networks, 28.
Bogdanov, A., Kne
ˇ
zevi
´
c, M., Leander, G., Toz, D., Varıcı,
K., and Verbauwhede, I. (2011). spongent: A
lightweight hash function. In Preneel, B. and Takagi,
T., editors, Cryptographic Hardware and Embedded
Systems – CHES 2011, pages 312–325, Berlin, Hei-
delberg. Springer Berlin Heidelberg.
De Canni
`
ere, C. (2006). Trivium: A stream cipher con-
struction inspired by block cipher design principles.
In Katsikas, S. K., L
´
opez, J., Backes, M., Gritzalis, S.,
and Preneel, B., editors, Information Security, pages
171–186, Berlin, Heidelberg. Springer Berlin Heidel-
berg.
Dinu, D., Corre, Y., Khovratovich, D., Perrin, L.,
Großsch
¨
adl, J., and Biryukov, A. (2019). Triathlon
Lightweight Cryptographic Algorithms: A Position Paper
769

of lightweight block ciphers for the internet of things.
Journal of Cryptographic Engineering, 9.
Dobraunig, C., Eichlseder, M., Mendel, F., and Schl
¨
affer,
M. (2021). Ascon v1.2: Lightweight authenticated
encryption and hashing. J. Cryptol., 34(3).
Duval, S. and Leurent, G. (2020). Lightweight macs from
universal hash functions. In Bela
¨
ıd, S. and G
¨
uneysu,
T., editors, Smart Card Research and Advanced Appli-
cations, pages 195–215, Cham. Springer International
Publishing.
Eisenbarth, T., Kumar, S., Paar, C., Poschmann, A.,
and Uhsadel, L. (2007). A survey of lightweight-
cryptography implementations. IEEE Design and Test
of Computers, 24(6):522–533.
Engels, D., Saarinen, M.-J. O., Schweitzer, P., and Smith,
E. M. (2012). The hummingbird-2 lightweight authen-
ticated encryption algorithm. In Juels, A. and Paar,
C., editors, RFID. Security and Privacy, pages 19–31,
Berlin, Heidelberg. Springer Berlin Heidelberg.
Farhan, L. and Kharel, R. (2019). Internet of Things:
Vision, Future Directions and Opportunities, pages
331–347. Springer International Publishing, Cham.
Guo, J., Peyrin, T., and Poschmann, A. (2011). The pho-
ton family of lightweight hash functions. In Rogaway,
P., editor, Advances in Cryptology – CRYPTO 2011,
pages 222–239, Berlin, Heidelberg. Springer Berlin
Heidelberg.
Harbi, Y., Aliouat, Z., Refoufi, A., and Harous, S. (2021).
Recent security trends in internet of things: A com-
prehensive survey. IEEE Access, 9:113292–113314.
Hatzivasilis, G., Fysarakis, K., Papaefstathiou, I., and Man-
ifavas, H. (2018). A review of lightweight block ci-
phers. Journal of Cryptographic Engineering, 8:1–44.
Khan, M. A., Quasim, M. T., Alghamdi, N. S., and Khan,
M. Y. (2020). A secure framework for authentication
and encryption using improved ecc for iot-based med-
ical sensor data. IEEE Access, 8:52018–52027.
Kouicem, D. E., Bouabdallah, A., and Lakhlef, H. (2018).
Internet of things security: A top-down survey. Com-
puter Networks, 141:199–221.
Leander, G., Paar, C., Poschmann, A., and Schramm, K.
(2007). New lightweight des variants. volume 4593,
pages 196–210.
Lee, D., Kim, D.-C., Kwon, D., and Kim, H. (2014). Ef-
ficient hardware implementation of the lightweight
block encryption algorithm lea. Sensors, 14(1):975–
994.
Luykx, A., Preneel, B., Tischhauser, E., and Yasuda, K.
(2016). A mac mode for lightweight block ciphers.
In Peyrin, T., editor, Fast Software Encryption, pages
43–59, Berlin, Heidelberg. Springer Berlin Heidel-
berg.
Manyika, J., Chui, M., Bisson, P., Woetzel, J., Dobbs, R.,
Bughin, J., and Aharon, D. (2015). Unlocking the
potential of the internet of things. McKinsey Global
Institute, 1.
Matsui, M. and Murakami, Y. (2014). Minimalism of soft-
ware implementation. pages 393–409.
Miller, V. S. (1986). Use of elliptic curves in cryptogra-
phy. In Williams, H. C., editor, Advances in Cryp-
tology — CRYPTO ’85 Proceedings, pages 417–426,
Berlin, Heidelberg. Springer Berlin Heidelberg.
Mouha, N., Mennink, B., Van Herrewege, A., Watanabe, D.,
Preneel, B., and Verbauwhede, I. (2014). Chaskey: An
efficient mac algorithm for 32-bit microcontrollers. In
Joux, A. and Youssef, A., editors, Selected Areas in
Cryptography – SAC 2014, pages 306–323, Cham.
Springer International Publishing.
Patel, S. T. and Mistry, N. H. (2015). A survey: Lightweight
cryptography in wsn. In 2015 International Confer-
ence on Communication Networks (ICCN), pages 11–
15.
˚
Agren, M., Hell, M., Johansson, T., and Meier, W. (2011).
Grain-128a: a new version of grain-128 with op-
tional authentication. Int. J. Wire. Mob. Comput.,
5(1):48–59.
Ranganatha Rao, B. and Sujatha, B. (2023). A hybrid el-
liptic curve cryptography (hecc) technique for fast en-
cryption of data for public cloud security. Measure-
ment: Sensors, 29:100870.
Rivest, R. L., Shamir, A., and Adleman, L. (1978). A
method for obtaining digital signatures and public-key
cryptosystems. Commun. ACM, 21(2):120–126.
Sehrawat, D. and Gill, N. (2019). A review on performance
evaluation criteria and tools for lightweight block ci-
phers. International Journal of Advanced Trends in
Computer Science and Engineering, 8:630–639.
Sevin, A. and Mohammed, A. (2021). A survey on soft-
ware implementation of lightweight block ciphers for
iot devices. Journal of Ambient Intelligence and Hu-
manized Computing, 14:1–15.
Shi, T. and and, J. G. (2019). Cryptanalysis of the authen-
tication in acorn. KSII Transactions on Internet and
Information Systems, 13(8):4060–4075.
Shirai, T., Shibutani, K., Akishita, T., Moriai, S., and Iwata,
T. (2007). The 128-bit blockcipher clefia (extended
abstract). In Biryukov, A., editor, Fast Software En-
cryption, pages 181–195, Berlin, Heidelberg. Springer
Berlin Heidelberg.
Singh, S., Sharma, P., Moon, S., and Park, J. (2017).
Advanced lightweight encryption algorithms for iot
devices: survey, challenges and solutions. Journal
of Ambient Intelligence and Humanized Computing,
15:1–18.
Stallings, W. (2013). Cryptography and Network Security:
Principles and Practice. Prentice Hall Press, USA,
6th edition.
Thakor, V. A., Razzaque, M. A., and Khandaker, M.
R. A. (2021). Lightweight cryptography algorithms
for resource-constrained iot devices: A review, com-
parison and research opportunities. IEEE Access,
9:28177–28193.
Watanabe, D., Ideguchi, K., Kitahara, J., Muto, K., Fu-
ruichi, H., and Kaneko, T. (2008). Enocoro-80: A
hardware oriented stream cipher. In 2008 Third In-
ternational Conference on Availability, Reliability and
Security, pages 1294–1300.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
770
