
MATRaCAE: Time-Based Revocable Access Control in the IoT
Cl
´
ementine Gritti
1
, Emanuel Regnath
2
and Sebastian Steinhorst
3
1
INSA Lyon, France
2
Siemens, Munich, Germany
3
Technical University of Munich, Germany
Keywords:
Attribute-Based Encryption, Time-Based Access Control, Direct Revocation, Internet of Things.
Abstract:
Internet of Things (IoT) promises a strong connection between digital and physical environments. Neverthe-
less, this framework comes with security vulnerabilities, due to the heterogeneous nature of devices and the
diversity of their provenance. Furthermore, technical constraints (e.g. devices’ limited resources) require to
lighten the design of the underlying security protocols. Liu et al. presented a system for data access with
time-based control and direct user revocation that are beneficial features in IoT. In this paper, we propose an
extension of this system, called MATRaCAE, that involves multiple authorities and considers binary time cre-
dentials. Doing so, we mitigate the key escrow problem and comes with a better trade-off between key update
frequency and number of revoked users, which limited the applicability of Liu et al.’s scheme in IoT. Our solu-
tion can be proved secure under the Decisional Bilinear Diffie-Hellman Exponent assumption. Subsequently,
we implement and evaluate MATRaCAE to demonstrate its suitability to IoT frameworks.
1 INTRODUCTION
Technologies for the Internet of Things (IoT) have
been explored eagerly to offer better efficiency and
productivity, but expand vulnerabilities and threats
along with technical challenges (Ali et al., 2015).
75 billion devices will be in the IoT world by 2025
and 127 new IoT devices are connected every second
to the Internet, yielding the management demanding
(Patel et al., 2017). In addition, those devices have
various manufacturing origins, not always well de-
fined, and have constrained computing and commu-
nication resources (Pham et al., 2016). Those ob-
servations make IoT dependability, in particular re-
liability and availability, challenging (Macedo et al.,
2014). Devices continuously collect and exchange a
huge amount of data, that is combined and refined
through data analytics. IoT has produced more than
500 zettabytes of data per year since 2020, and that
number grows exponentially. Developing IoT for cap-
italizing fresh precious information brings extra se-
curity concerns (Hwang, 2015). Consequently, we
are interested in developing an efficient access control
system for secure data exchanges in IoT networks.
Yet, our solution must be developed carefully.
Due to devices’ ubiquity and vulnerable high config-
urations, IoT networks have been involved in many
cyber attacks (Pa et al., 2015). Access control in IoT
usually implies a centralized architecture, raising sin-
gle points of failure with unpredictable threats. The
large number of devices and dynamicity of IoT net-
works force to go beyond basic identity assignment
techniques as for the Public Key Infrastructure. Triv-
ial key management is restricting since each device
should maintain a substantial number of keys to in-
teract with the network. In addition, it is essential
to achieve low latency and high reliability. When
time-sensitive data is collected, data processing may
produce results too late to be useful. For instance,
some control decisions in autonomous vehicles re-
quire sub-microsecond response times, while indus-
trial control systems need response in tens of mi-
croseconds to avoid damage and ensure safety (Mekki
et al., 2019). Hence, our access control system should
consider time as an essential feature along with effec-
tive key management and device revocation to over-
come the aforementioned limitations.
In this paper, we introduce MATRaCAE
1
, a Multi-
Authority Time-based Revocable Ciphertext-Policy
Attribute-based Encryption scheme for fine-grained
access control in IoT, which extends the work pro-
posed in (Liu et al., 2018). An effective balance be-
1
The full version can be found at https://eprint.iacr.org/
2021/140
274
Gritti, C., Regnath, E. and Steinhorst, S.
MATRaCAE: Time-Based Revocable Access Control in the IoT.
DOI: 10.5220/0012825700003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 274-285
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
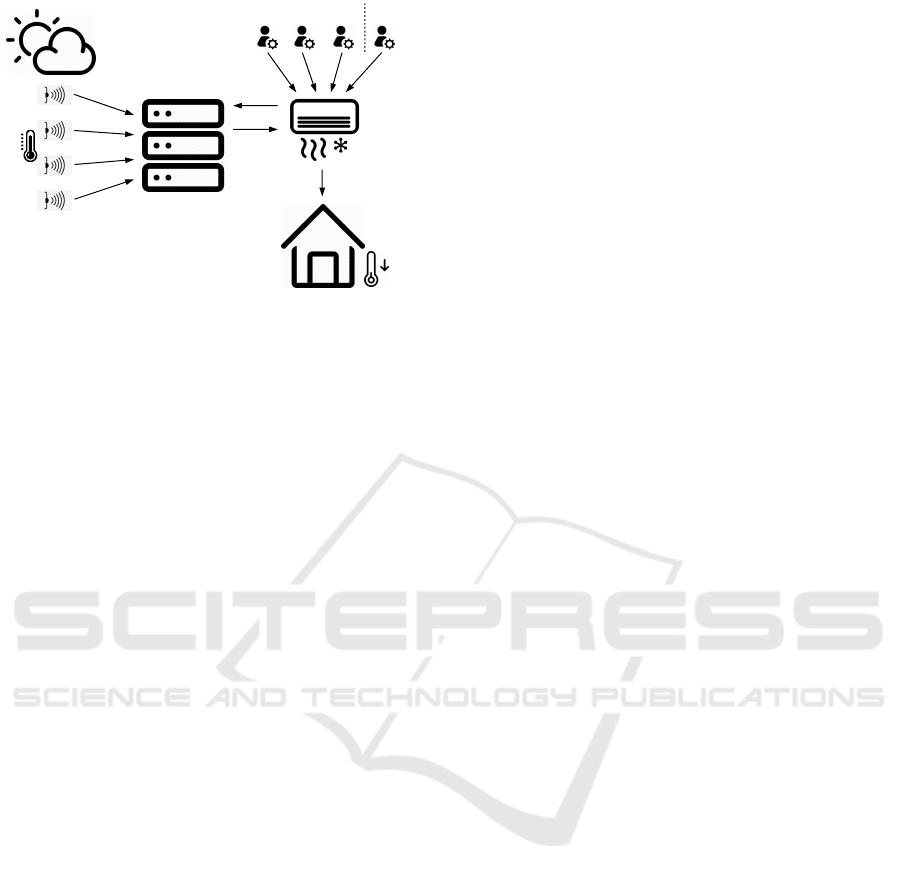
Role authorities Time authority
Sensors
Actuator
Proxy
Request
Credentials
Encrypted
Data
Encrypted
Data
Decrypted
Data
Figure 1: In a smart home, multiple temperature sensors are
scattered and an actuator adjusts temperature in response to
sensors’ collected data.
tween key updates and device revocation permits to
offer security guarantees against the above risks while
satisfying IoT dependability. Specifically, an access
control is built on top of devices’ role credentials (e.g.
sensing temperature), allowing to share collected data
securely within an IoT network. Multiple authori-
ties are in charge of distributing key material to de-
vices, averting the key escrow problem. Direct device
revocation keeps sensitive data protected even when
a device’s secret key is compromised. Moreover,
time credentials are used in addition to role creden-
tials, emphasizing the ephemeral value of shared data,
while avoiding recurrent communication between de-
vices and authorities. Having short time periods of
access allows faster expiration of corrupt device keys,
improving device management in IoT networks.
IoT Use Case. Figure 1 illustrates an example of
our access control system in a smart home. Several
temperature sensors are scattered in a house. They
collect temperature values once every few minutes.
They encrypt their time-sensitive data according to an
access policy, containing roles and time periods. An
actuator is connected to these sensors (possibly indi-
rectly, via a gateway). The actuator has received role
and time credentials from multiple authorities. Hav-
ing limited storage capacity, the sensors upload their
encrypted data to a proxy (e.g. a cloud server), seen as
an intermediary between sensors and actuator. Within
the rest of the paper, we assume that the proxy exists
and is intimately linked to sensors, hence we omit to
mention it explicitly. The actuator sends requests to
the proxy for access to sensors’ data every short time
interval, of the order of minutes. The proxy replies
to the actuator’s requests by forwarding the encrypted
collected data. The actuator is able to recover the data
in plain if and only if it has been granted with cre-
dentials satisfying sensors’ assigned access policies.
Having the plain data, the actuator adjusts the tem-
perature accordingly.
1.1 Contributions
We propose an extension, called MATRaCAE, of the
access control system presented in (Liu et al., 2018)
(referred as LYZL) with the following features to bet-
ter fit in IoT:
• Device access control is built on top of role and
time credentials, as in (Liu et al., 2018).
• The participation of multiple role authorities,
rather than a unique one as in (Liu et al., 2018), allevi-
ates the key escrow problem. Nonetheless, authorities
must uniquely identify devices. Indeed, an unautho-
rised device must not access data using a credential
from a role authority that incorrectly matches a cre-
dential from another role authority.
• A novel time-based access control is designed
using binary trees, instead of 31-ary trees as in (Liu
et al., 2018), to better apply to IoT frameworks. Mov-
ing the time structure from 31-ary trees (based on
the Gregorian calendar) to 2-ary trees obliges to care-
fully specify a process for setting time periods. How-
ever, the result is more efficient and adaptable to time-
sensitive IoT use cases.
• A direct approach based on a publicly available
list for device revocation limits damages from com-
promised devices’ secret keys, as in (Liu et al., 2018).
• Asymmetric pairings are chosen, rather than
symmetric pairings as in (Liu et al., 2018), to in-
crease the system security and efficiency, as proved in
(Guillevic, 2013). Shifting from symmetric pairings
to asymmetric pairings incur less versatility in com-
puting components. Indeed, inputs must be ordered to
ensure that pairing calculations are still possible (e.g.
successful decryption).
We obtain a better balance between key update
and device revocation compared to (Liu et al., 2018),
making MATRaCAE suitable for IoT networks. We
adapt the Ciphertext-Policy Attribute-Based Encryp-
tion (CP-ABE) scheme and security model from (Liu
et al., 2018) to follow the multi-authority setting, and
prove our scheme secure under the Decisional Bi-
linear Diffie-Hellman Exponent (BDHE) assumption.
We also implement and evaluate MATRaCAE to con-
firm its dependability in IoT.
1.2 Related Work
Attribute-Based Encryption. Identity-Based En-
cryption (IBE) (Shamir, 1985) is a public-key cryp-
tographic primitive that uses some unique informa-
tion about the user identity as her public key. The
MATRaCAE: Time-Based Revocable Access Control in the IoT
275

corresponding secret key is generated by a trusted au-
thority, based on the public key. Attribute-Based En-
cryption (ABE) (Sahai and Waters, 2005; Bethencourt
et al., 2007) is a variant of IBE. The user secret key
and ciphertext are dependent upon attributes. The de-
cryption of a ciphertext is possible if and only if the
attributes of the key match the attributes of the cipher-
text. There are two types of ABE schemes, that are
closely related. Their difference comes from the ac-
cess policy being linked either to the key (KP-ABE)
or to the ciphertext (CP-ABE).
Multi-authority ABE schemes have been proposed
over the last decade (Rouselakis and Waters, 2015;
Datta et al., 2021; Ambrona and Gay, 2023), but with-
out incorporating revocation and time-based mecha-
nisms. On the other hand, several revocable ABE
schemes have been presented (Sahai et al., 2012;
Yang and Jia, 2014; Liu et al., 2018; Liu et al., 2020;
Zhang et al., 2019; Zhang et al., 2022b), but are prone
to the key escrow problem. In (Sahai et al., 2012),
revocation is made possible through time-related bi-
nary trees, but in the case of KP-ABE only. In (Yang
and Jia, 2014), revocation, conducted by the attribute
authorities, implies to update the secret keys of non-
revoked users. In (Liu et al., 2018), a time-based CP-
ABE is combined with direct revocation tools. How-
ever, time design choices induce ineffective trees. In
(Liu et al., 2020; Zhang et al., 2019), direct revocation
is provided but the solutions suffer from ineffecient
time-based control. In (Zhang et al., 2022b), revoca-
tion is possible but key updates must be performed by
specific authorities.
Attribute-Based Encryption in IoT. In (Yao et al.,
2015), an ABE scheme without any pairing opera-
tion is presented to save costs and possibly be used
for IoT. (Oualha and Nguyen, 2016) extends (Bethen-
court et al., 2007) with a focus on IoT, but pre-
computed values, generated by a trusted authority, in-
cur extra storage. More recently, IoT access control
solutions (Lu et al., 2021; Zhang et al., 2021; Zhang
et al., 2023) have been proposed combining ABE with
new technologies such as blockchain and lightweight
cryptography. However, all the aforementioned works
lack of essential features, such as device revocation
and key escrow mitigation. Other ABE-based IoT
systems (AboDoma et al., 2021; Zhang et al., 2022a;
Yan et al., 2023) with revocation and computation
outsourcing have been presented. Nevertheless, com-
putation outsourcing requires trust assumptions and
key escrow issues are not considered.
2 BUILDING BLOCKS
Multiple Authorities. We enhance LYZL by in-
volving multiple authorities. In (Liu et al., 2018), one
fully trusted authority is responsible of generating the
key material of users. Such a configuration may be
subject to key escrow and single point of failure. By
sharing the generation of devices’ keys among sev-
eral authorities, we reduce trust assumptions made on
these authorities while enforcing the security of MA-
TRaCAE. We assume that one authority remains hon-
est at all time to keep MATRaCAE secure.
Revocation. Reasons for revocation can be diverse:
(i) The device left the IoT network, thus the key
should no longer be usable; (ii) The device lost its
key and was attributed a new one, hence the old key
should no longer be usable; (iii) The device has one
of its credentials changed and thus has received a new
key with this new credential, and the old key should
no longer be usable.
Existing revocation approaches rely on key up-
dates of non-revoked devices or cloud assistance.
However, the former does not allow direct revocation
while the latter encounters management issues when
the number of devices becomes huge. Another ap-
proach allows to revoke devices by appending their
identities in a public list. Such a list is included in
each ciphertext in its latest version. Hence, key up-
date is not needed, avoiding communication burdens.
However, the list may grow significantly over time,
in particular in large IoT networks. A solution, sug-
gested in (Liu et al., 2018), is to find a balance be-
tween the frequency of key updates and the length of
the revocation list. This list accepts a maximum num-
ber of revoked devices such that, once reached, new
keys are distributed and the list is emptied. Key up-
dates are defined such that they happen just before the
list is full. A time period is specified with an expiry
date such that, once passed, the device is no longer
able to access data. Devices’ keys are updated with
a new time period. If a device is revoked before its
key expires, then its identity is added to and kept in
the revocation list until the next key update. Note that
a device may be revoked definitely from the network,
and its key is no longer updated. This direct revoca-
tion mechanism is used in MATRaCAE.
Access Tree. In (Liu et al., 2018), a continuous time
period is defined during encryption such that only
users with time credentials completely covering that
time period can decrypt. If a user has time creden-
tial “January 2024” while the encryptor has set “from
01 to 15 January 2024”, then the former successfully
SECRYPT 2024 - 21st International Conference on Security and Cryptography
276

Days:
Root with initial time 01/01/2024
1 …... 31
Janv ...… Dec dum ...… dum
1 …...
2024 2025 dum …… dum
Janv ...… Dec dum ...… dum
Months:
Years:
31
Figure 2: Tree set for 2 years, from “01 January 2024” un-
til “31 December 2025” (included) (Liu et al., 2018). Let
”dum” denote dummy nodes.
decrypts. Such properties are kept when designing
MATRaCAE. A set cover approach is used to select
the minimum number of tree nodes that represent the
valid time periods. The root node is implicitly set
as a starting time. Each non-root node accounts for
a time period such that leaves are days, leaves’ par-
ents are months and leaves’ grand-parents are years.
Let T be the depth of the tree and each node have
z children. The time is represented as a z-ary string
{1,2,·· · , z}
T −1
and a time period is denoted with a
z-ary element (τ
1
,τ
2
,· ·· ,τ
η
) for some η < T . No
numerical value is given in (Liu et al., 2018), hence
we propose to make some assumptions from the read-
ing. A 2-year interval between two key updates is
claimed to be reasonable and time periods are based
on year, month and day. We infer that T = 4 and
z = 31 (there are at most 31 days in a month). Thus,
the root and nodes representing years have z = 31
children, even if intervals are 2 years long and years
comprise 12 months. This approach is cumbersome
because there are 31 − 2 = 29 dummy nodes at the
year level, 29 ∗ (31 − 12) = 551 dummy nodes at the
month level and 29 ∗ 19 ∗ 31 = 17081 dummy nodes
at the day level. Figure 2 illustrates the above 2-year
period example from LYZL.
We now describe the LYZL access tree depicting
time intervals. The set cover mechanism allows to
find the minimum number of nodes representing the
time validity range. Let a validity time range be from
“30 November 2024” until “31 December 2025”. The
selected nodes in Figure 2 would be the node “30”
with parent “November” and grand-parent “2024”,
the node “December” with parent “2024”, and the
node “2025”. Let η
τ
be the number of selected nodes
and T be the depth of the tree such that η
τ
< T . Let
T = (τ
1
,τ
2
,· ·· ,τ
η
τ
) be the set cover representing the
time validity range. Following the above example,
η
τ
= 3 such that τ
1
= “30 November 2024“, τ
2
=
”December 2024“, and τ
3
= ”2025“. We have not
mentioned the presence of the dummy nodes to not
overload the understanding. However, they must be
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
Days:
2 2 2 2 2 2 2 2
4 4 4 4
8 8
16
Root with initial time 01/01/2024
Access time period
Figure 3: Tree set from “01 January 2024” until “16 January
2024” (included). A time period is defined for 7 days. Keys
correspond to nodes with blue-line circles.
included in the set cover, thus η
τ
>> 3.
In MATRaCAE, a tree is also used for time-based
access control. A time authority manages trees and
assigns time intervals as devices’ credentials. We
choose a binary structure rather than a 31-ary struc-
ture, avoiding the presence of dummy nodes. In ad-
dition, we focus on short time periods (of the order
of days) according to our IoT time-sensitive data sce-
nario. The root defines a starting time and the number
of leaves determines the amount of days between two
key updates. To keep the tree with a reasonable depth
T , the number of leaves must be relatively small. A
path from the root to a node is denoted as a string
in {0, 1}
T −1
where 0 denotes the left child and 1 de-
notes the right child of a given node. Following the
above 2-year period example, our binary tree would
have 730 leaves, so a depth T = 10. A complete bi-
nary tree of depth T = 10 has 1023 nodes (includ-
ing dummies). However, following (Liu et al., 2018),
a 31-ary tree with 29791 nodes (including dummies)
would be built, making computation and storage costs
noticeably worse than ours.
In Figure 3, the tree has depth T = 5, hence 16
leaves (thus 16 days). The time interval starts on “01
January 2024” and ends on “16 January 2024” (in-
cluded). Here, a device receives some time key ma-
terial for a time validity range of 7 days, from “04
January 2024” until “10 January 2024” (included).
The device is given 3 key components as illustrated
by blue circles: one for the leaf node representing day
4, one for the grand-parent from day 5 until day 8, and
one for the parent for days 9 and 10. Following (Liu
et al., 2018), a 31-ary tree of depth T = 4 would incur
7 keys, one for each day, for the same time interval.
Similarly to (Liu et al., 2018), an access tree repre-
sents time periods in MATRaCAE. Rather than using
31-ary strings {1,2, ·· · , 31}
T −1
, we consider binary
strings {0,1}
T −1
such that a node represented as 0
MATRaCAE: Time-Based Revocable Access Control in the IoT
277

means going to the left child and as 1 means going to
the right child. Let the validity time range be from “04
January 2024” until “10 January 2024”. The selected
nodes are the ones circled in blue in Figure 3. Here,
T = (τ
1
,τ
2
,τ
3
) where τ
1
= (0,0,1,1), τ
2
= (0,1) and
τ
3
= (1, 0,0).
Bilinear Pairing and Group. Let G
1
, G
2
and G
T
be multiplicative cyclic groups of prime order p. A
pairing e is a map e : G
1
× G
2
→ G
T
such that: (i)
Given g
1
∈ G
1
, g
2
∈ G
2
and a, b ∈ Z
p
, e(g
a
1
,g
b
2
) =
e(g
1
,g
2
)
ab
(bilinearity); (ii) There exist g
1
∈ G
1
and
g
2
∈ G
2
such that e(g
1
,g
2
) ̸= 1
G
T
(non-degeneracy);
(iii) There exists an efficient algorithm to compute
e(g
1
,g
2
) for all g
1
∈ G
1
and g
2
∈ G
2
(computability).
Given as input a security parameter 1
λ
, the algo-
rithm Gen outputs the tuple (p,G
1
,G
2
,G
T
,e) where
G
1
,G
2
, G
T
are multiplicative cyclic groups of prime
order p and e : G
1
× G
2
→ G
T
is a pairing.
When G
1
= G
2
, the pairing is symmetric, as in
(Liu et al., 2018). When G
1
̸= G
2
, the pairing is asym-
metric. Designing a scheme with asymmetric pairings
(rather than symmetric pairings) offers better perfor-
mances and improves the security (Guillevic, 2013).
MATRaCAE extends LYZL with asymmetric pairings
to enhance its security in IoT.
Decisional q-BDHE Assumption. Given
⃗
P =
(g
1
,g
s
1
,g
a
1
,· ·· ,g
a
q
1
,g
a
q+2
1
,· ·· ,g
a
2q
1
,g
2
,g
s
2
,g
a
2
,· ·· ,g
a
q
2
,
g
a
q+2
2
,· ·· ,g
a
2q
2
) ∈ G
2q+1
1
× G
2q+1
2
and Q ∈ G
T
, where
s,a ∈ Z
p
, g
1
∈ G
1
and g
2
∈ G
2
, the Decisional q-
Bilinear Diffie-Hellman Exponent (BDHE) problem
is defined as to decide whether Q = e(g
1
,g
2
)
sa
q+1
or a
random element in G
T
. The security of MATRaCAE
relies on the Decisional q-BDHE assumption.
Access Structure and Linear Secret Sharing. Let
P = {P
1
,P
2
,· ·· ,P
n
} be a set of parties. A collection
C ⊆ 2
P
is monotone if for all A,B, such that A ∈ C and
A ⊆ B then B ∈ C. An access structure is a collection
C ⊆ 2
P
\ {
/
0}. The sets in C are said to be authorized.
In MATRaCAE, this structure represents access poli-
cies and is used for role-based access control.
A Secret Sharing Scheme (SSS) Π over a set of
parties P is a Linear SSS (LSSS) if the following con-
ditions hold (Beimel, 1996): (i) The shares of the par-
ties form a vector over Z
p
; (ii) There are a l ×ν matrix
M and a function ρ that maps the i-th row, for i ∈ [1,l],
to an associated party ρ(i). Let s ∈ Z
p
be a secret to
be shared, and γ
2
,· ·· ,γ
ν
be random exponents from
Z
p
. Let ⃗v = (s,γ
2
,· ·· ,γ
ν
) be a column vector and M⃗v
be the vector of l shares of the secret s according to Π
such that the share (M⃗v)
i
belongs to party ρ(i).
We define the linear reconstruction property as
follows. Let Π be an LSSS for an access structure
C, S ∈ C be an authorized set and I = {i; ρ(i) ∈ S} ⊂
[1,l]. There exist constants {ω
i
∈ Z
p
}
i∈I
such that,
if {λ
i
} are valid shares of any secret s according to
Π, then
∑
i∈I
ω
i
λ
i
= s. The constants ω
i
can be found
in time polynomial in the size of M. Moreover, for
any unauthorized set S /∈ C, the secret s should be in-
formation theoretically hidden from the parties in S.
Let the vector (1, 0,0, ·· · ,0) be the target vector for
LSSS. Given an authorized set of rows I in the ma-
trix M, the target vector is in the span of I. On the
other side, given an unauthorized set of rows I, the
target vector is not in the span of the rows of I. Also,
there is a vector ⃗w such that ⃗w(1,0,0,··· ,0) = −1 and
⃗wM
i
= 0 for all i ∈ I. In MATRaCAE, the LSSS ma-
trix has rows labeled by role attributes.
Role Attributes and Indexation. In (Liu et al.,
2018), an attribute universe is associated with the
unique authority such that attributes are all different.
In MATRaCAE, each role authority A
k
has its own
attribute universe U
k
such that the union of all the
attribute universes forms the network universe U =
∪
A
k
U
k
. Attribute universes are all disjoint by defin-
ing attributes uniquely as follows. Let a role be “tem-
perature” and two authorities refer to “Room A” and
“Room B” respectively. Hence, the two attributes are
determined uniquely as “RoomA||temperature” and
“RoomB||temperature” respectively. The authorities
define their own universes and assign role credentials
based on those universes in devices’ keys. Key up-
dates w.r.t. roles are not frequent (e.g. “temperature”
remains for a dedicated sensor but its location may
change). Devices can decrypt data if the access pol-
icy contains their role attributes.
Indexation works as follows. Let N be the num-
ber of role authorities. Let A
k
be the role author-
ity with universe U
k
containing U
k
attributes, for
k ∈ [1,N]. Attribute indices in U
k
associated with
A
k
are (
∑
k−1
j=1
U
j
+1), ·· · , (
∑
k−1
j=1
U
j
+U
k
). To simplify
the reading, let k||i = (
∑
k−1
j=1
U
j
+ i) for i ∈ [1,U
k
].
Let I = {i; ρ(i) ∈ S} ⊆ [1,l] and {ω
i
∈ Z
p
}
i∈I
be
the set of constants such that if the set {λ
i
} con-
tains valid shares of a value s according to the ma-
trix M, then
∑
i∈I
ω
i
λ
i
= s, as defined previously. Let
A be the set of role authorities whose attributes are
in the access structure. Let π : k → π(i) be defined
as ∃!(A
k
∈ A, j ∈ [1,U
k
]) such that ρ(i) = k|| j. This
surjective function exists since each attribute is de-
fined uniquely in the network universe U = ∪
A
k
U
k
.
An attribute in U is uniquely controlled by one au-
thority A
k
. To explain the functionality of the func-
tion π, there exists a publicly computable function
SECRYPT 2024 - 21st International Conference on Security and Cryptography
278

F
π
: U → A
k
that maps one attribute to a specific role
authority (Rouselakis and Waters, 2015). From this
mapping, let a second labeling of rows be defined in
the access structure ((M,ρ), ρ
′
) such that it maps rows
to attributes through ρ(·) = F
π
(ρ
′
(·)).
3 MATRaCAE
An overview of MATRaCAE is given in Figure 4.
MATRaCAE is composed of seven algorithms run
over three phases:
Initialization. This phase, run only once, sets the
system parameters.
• Setup(1
ζ
,R) → PP. The algorithm Setup gen-
erates the public parameters made available to all au-
thorities and devices. Let R − 1 be the maximum
number of revoked devices. On inputs the secu-
rity parameter 1
ζ
and R, the algorithm Setup out-
puts the public parameters PP. First, run the al-
gorithm Gen and obtain two bilinear groups G
1
,G
2
of prime order p with generators g
1
and g
2
respec-
tively, along with a third group G
T
of prime order
p and a pairing e : G
1
× G
2
→ G
T
. Pick at random
δ,α
1
,· ·· ,α
R
∈
R
Z
p
. Set
⃗
α = (α
1
,· ·· ,α
R
)
⊤
and
⃗
F =
g
⃗
α
1
= (g
α
1
1
,· ·· ,g
α
R
1
)
⊤
= ( f
1
,· ·· , f
R
)
⊤
. The public pa-
rameters are PP = (p,G
1
,G
2
,G
T
,e,g
1
,g
δ
1
,g
2
,
⃗
F).
• RAKeyGen(PP,U
k
) → (PK
k
,SK
k
). The algo-
rithm RAKeyGen generates the public and secret keys
of each role authority. Let U
k
be the number of role
attributes in the universe U
k
associated with the role
authority A
k
. On inputs the public parameters PP and
U
k
, the algorithm RAKeyGen outputs the public key
PK
k
and the secret key SK
k
of A
k
. Pick at random
κ
k
∈
R
Z
p
and h
k||1
,· ·· ,h
k||U
k
∈
R
G
1
(these elements
h
k||i
will be used for role-based access control w.r.t.
A
k
). The public key is PK
k
= (e(g
1
,g
2
)
κ
k
,h
k||1
,· ·· ,
h
k||U
k
) and the secret key is SK
k
= κ
k
.
• TAKeyGen(PP,T ) → (PK,SK). The algorithm
TAKeyGen generates the public and secret keys of
the time authority. Let T be the depth of the binary
tree associated with the time authority B. The time
is represented as a binary string {0,1}
T −1
. On in-
puts the public parameters PP and T , the algorithm
TAKeyGen outputs the public key PK and the se-
cret key SK of B. Pick at random σ ∈
R
Z
p
and
V
0
,V
1
,· ·· ,V
T
∈
R
G
1
(the elements V
j
will be used for
time-based access control w.r.t. B). The public key is
PK = (e(g
1
,g
2
)
σ
,V
0
,V
1
, ·· · ,V
T
) and the secret key is
SK = σ.
Key Generation. The authorities create devices’
key material. For 1 ≤ k ≤ N, the role authority A
k
generates keys based on roles, defined in the universe
U
k
. Role-based key updates for non-revoked devices
are run occasionally (e.g. every few months). The
time authority B generates keys based on time inter-
vals, denoted as T
ID
where ID is the device identity.
Time-based key updates are run more frequently (e.g.
every few days/weeks).
• RUKeyGen(PP,(PK
k
,SK
k
),ID,S
ID,k
) →
RSK
ID,k
. The algorithm RUKeyGen generates the
secret key of the device w.r.t. its roles. Let S
ID,k
be
the role attribute set of a device with identity ID and
associated with the role authority A
k
. Let k||x ∈ S
ID,k
denote the attribute uniquely defined in the network
universe U = ∪
A
k
U
k
by determining the associated
authority A
k
and the role x within U
k
. On inputs
the public parameters PP, the public and secret keys
PK
k
and SK
k
of A
k
, ID and S
ID,k
, the algorithm
RUKeyGen outputs the secret key RSK
ID,k
of the
device with identity ID, role attribute set S
ID,k
and
associated with A
k
. First, pick at random u
k
,t
k
∈
R
Z
p
.
Then, compute the following:
D
k,0
= g
t
k
2
D
′
k,0
= g
u
k
2
D
k,1
= g
κ
k
1
g
δt
k
1
f
u
k
1
= g
κ
k
1
g
δt
k
1
g
α
1
u
k
1
K
k,x
= h
t
k
k||x
for k||x ∈ S
ID,k
F
k,i
= ( f
−ID
i−1
1
f
i
)
u
k
for i ∈ [2, R]
The secret key is RSK
ID,k
=
(D
k,0
,D
′
k,0
,D
k,1
,{K
k,x
}
k||x∈S
ID,k
,{F
k,i
}
i∈[2,R]
) and
includes a description of S
ID,k
.
• TUKeyGen(PP, (PK, SK),ID,T
ID
) → T SK
ID
.
The algorithm TUKeyGen generates the secret key of
the device w.r.t. its access time period. Let T
ID
be the
time validity range of the device with identity ID and
associated with the time authority B. On inputs the
public parameters PP, the public and secret keys PK
and SK of B, ID and T
ID
, the algorithm TUKeyGen
outputs the secret key T SK
ID
of the device with iden-
tity ID, time validity range T
ID
and associated with B.
Let T be the set cover representing T
ID
which consists
of time elements τ = (τ
1
,· ·· ,τ
η
τ
) ∈ {0, 1}
η
τ
where
η
τ
< T for any τ ∈ T. First, pick at random β, v
τ
∈
R
Z
p
for τ ∈ T. Then, compute the following:
D
0,τ
= g
v
τ
2
for τ ∈ T
D
1,τ
= g
σ
1
f
β
1
(V
0
η
τ
∏
j=1
V
τ
j
j
)
v
τ
for τ ∈ T
D
2
= g
β
2
L
j,τ
= V
v
τ
j
for j ∈ [η
τ
+ 1,T ] and τ ∈ T
MATRaCAE: Time-Based Revocable Access Control in the IoT
279

Phase Algorithm Role Authority Time Authority Sensor Actuator
Initialization
Setup PP PP PP PP
RAKeyGen PK
k
,SK
k
TAKeyGen PK, SK
Key Generation
RUKeyGen
RSK
ID,k
−−−−−−−−−−−−−−−−→
TUKeyGen
T SK
ID
−−−−−−−−→
Encryption-Decryption
Encrypt
CT
−−−−−−→
Decrypt m
Figure 4: Overview of MATRaCAE.
E
i
= ( f
−ID
i−1
1
f
i
)
β
for i ∈ [2, R]
The secret key is T SK
ID
=
({D
0,τ
,D
1,τ
}
τ∈T
,D
2
,{L
j,τ
}
j∈[η
τ
+1,T ],τ∈T
, {E
i
}
i∈[2,R]
)
and includes a description of T
ID
.
Encryption-Decryption. Let an access policy be
(M,ρ) where M is a l × ν matrix and the function ρ
associates rows of the matrix M to role attributes. Let
a decryption time period be T
dec
. A device encrypts
collected data m based on (M, ρ) and T
dec
, along with
the up-to-date revocation list R (with up to R − 1 re-
voked devices), resulting in a ciphertext CT . Another
device, granted with role and time credentials satisfy-
ing (M,ρ) and T
dec
respectively, successfully decrypts
CT and recovers m.
• Encrypt(PP,{PK
k
}
A
k
∈A
,PK,m, R ,(M,ρ),T
dec
) →
CT . The algorithm Encrypt generates a ciphertext
of the message m. Let A be the set of role au-
thorities whose role attributes are in the access
policy. Let m be the message to be encrypted. Let
R = (ID
1
,· ·· ,ID
r
) be the revocation list containing
r < R revoked devices. Let (M, ρ) be a LSSS access
structure, defining the role access policy. Let T
dec
be the decryption time period of the ciphertext. On
inputs the public parameters PP, the public keys
PK
k
of the role authorities A
k
∈ A, the public key
PK of the time authority B, m, R , (M,ρ) and T
dec
,
the algorithm Encrypt outputs a ciphertext CT . Let
τ
dec
= (τ
1
,· ·· ,τ
η
dec
) ∈ {0,1}
η
dec
be the binary rep-
resentation of T
dec
, where η
dec
< T . First, choose a
secret s from Z
p
and pick at random γ
2
,· ·· ,γ
ν
∈
R
Z
p
.
Set the vector ⃗v = (s,γ
2
,· ·· ,γ
ν
). Then, for i ∈ [1,l],
compute λ
i
= ⟨⃗v, M
i
⟩, where M
i
is the i-th row of M.
Let F
R
(Z) = (Z − ID
1
) · (Z − ID
2
)· ·· (Z − ID
r
) =
y
1
+ y
2
Z + ··· + y
r
Z
r−1
+ y
r+1
Z
r
be a polynomial
defining the revocation list. If r + 1 < R, then set the
coefficients y
r+2
,· ·· ,y
R
equal to 0. Then, compute
the following:
C
0
= m · e(g
1
,g
2
)
σs
·
∏
A
k
∈A
e(g
1
,g
2
)
κ
k
s
C
′
0
= g
s
2
C
′′
0
= ( f
y
1
1
·· · f
y
R
R
)
s
C
′′′
0
= (V
0
η
dec
∏
j=1
V
τ
j
j
)
s
C
i
= g
δλ
i
1
h
−s
ρ(i)
for i ∈ [1, l]
The ciphertext is CT =
(C
0
,C
′
0
,C
′′
0
,C
′′′
0
,{C
i
}
i∈[1,l]
,(M, ρ)) and includes
descriptions of T
dec
and A.
• Decrypt(PP,CT,R , {RSK
ID,k
}
A
k
∈A
,T SK
ID
) →
m/ ⊥. The algorithm Decrypt attempts to recover the
message m from the ciphertext using appropriate se-
cret parameters. On inputs the public parameters PP,
the ciphertext CT , the revocation list R , the role se-
cret keys RSK
ID,k
of the device with identity ID and
associated with A
k
∈ A and the time secret key T SK
ID
of the device with identity ID and associated with B,
the algorithm Decrypt outputs m or ⊥.
Let
⃗
X = (1, ID,··· , ID
R−1
) for the identity ID and
⃗
Y = (y
1
,· ·· ,y
R
) where the exponents y
i
have been de-
fined during the encryption phase. Hence, ⟨
⃗
X,
⃗
Y ⟩ =
y
1
+ y
2
ID + ··· + y
r
ID
r−1
+ y
r+1
ID
r
= F
R
(ID). If
r + 1 < R, then the coefficients y
r+2
,· ·· ,y
R
are equal
to 0. Let S
ID
= ∪
A
k
∈A
S
ID,k
be the disjoint union of all
the role attribute sets S
ID,k
of the device with identity
ID and associated with A
k
∈ A. Let τ
dec
be the binary
representation for the decryption time period T
dec
and
T be the set cover representing the time validity range
T
ID
. Let us define the following conditions:
• Insufficient roles attributes: S
ID
does not satisfy
(M,ρ);
• Revoked device: ID ∈ R , that is ⟨
⃗
X,
⃗
Y ⟩ =
F
R
(ID) = 0;
• Invalid access time period: T
dec
is not com-
pletely covered in T
ID
, that is τ
dec
and all its prefixes
are not in T.
If any of the above conditions occurs, then output
⊥ and abort. Otherwise, since ⟨
⃗
X,
⃗
Y ⟩ ̸= 0, compute
the following:
F
k
=
R
∏
i=2
F
y
i
k,i
= ( f
−⟨
⃗
X,
⃗
Y ⟩
1
R
∏
i=1
f
y
i
i
)
u
k
SECRYPT 2024 - 21st International Conference on Security and Cryptography
280

ξ
k,1
=
e(F
k
,C
′
0
)
e(C
′′
0
,D
′
k,0
)
!
−1
⟨
⃗
X,
⃗
Y ⟩
= e(g
1
,g
2
)
α
1
su
k
E =
R
∏
i=2
E
y
i
i
= ( f
−⟨
⃗
X,
⃗
Y ⟩
1
R
∏
i=1
f
y
i
i
)
β
ξ
′
1
=
e(E,C
′
0
)
e(C
′′
0
,D
2
)
−1
⟨
⃗
X,
⃗
Y ⟩
= e(g
1
,g
2
)
α
1
sβ
Let I ⊆ [1,l] be defined as {i;ρ(i) ∈ S
ID
} and {ω
i
∈
Z
p
}
i∈I
be the set of constants such that if the set {λ
i
}
contains valid shares of a value s according to the ma-
trix M, then
∑
i∈I
ω
i
λ
i
= s. In addition, there is a sur-
jective function from I to A determined as follows.
Let π : k → π (i) be defined as ∃!(A
k
∈ A, j ∈ [1,U
k
])
such that ρ(i) = k|| j. Such function exists since each
attribute is defined uniquely in the network universe
U = ∪
A
k
U
k
. Then, compute:
ξ
2
=
∏
i∈I
e(C
i
,D
π(i),0
) · e(K
ρ(i)
,C
′
0
)
ω
i
=
∏
A
k
∈A
e(g
1
,g
2
)
δst
k
If τ
dec
= (τ
1
,· ·· ,τ
η
dec
) ∈ T, then D
1,τ
dec
should be
one component of the secret key T SK
ID
. Otherwise,
let τ
′
dec
= (τ
1
,· ·· ,τ
η
′
dec
) denote the prefix such that
η
′
dec
< η
dec
and τ
′
dec
∈ T. Then, derive a key com-
ponent D
1,τ
dec
from T SK
ID
with respect to τ
′
dec
by
calculating D
1,τ
dec
= D
1,τ
′
dec
∏
η
dec
j=η
′
dec
+1
L
τ
j
j,τ
′
dec
and set
τ
dec
= τ
′
dec
. Finally, recover the message m as fol-
lows:
m = C
0
· ξ
2
·
e(D
0,τ
dec
,C
′′′
0
) · ξ
′
1
e(D
1,τ
dec
,C
′
0
)
·
∏
A
k
∈A
ξ
k,1
e(D
k,1
,C
′
0
)
Correctness. We first calculate F
k
. Implicitly, the
device must not have been revoked to get a correct re-
sult F
k
=
∏
R
i=2
F
y
i
k,i
= ( f
−⟨
⃗
X,
⃗
Y ⟩
1
∏
R
i=1
f
y
i
i
)
u
k
. Using the
above result, we calculate ξ
k,1
=
e(F
k
,C
′
0
)
e(C
′′
0
,D
′
k,0
)
−1
⟨
⃗
X,
⃗
Y ⟩
=
e(g
1
,g
2
)
α
1
su
k
. If the device has been revoked, then we
cannot calculate it since we need ⟨
⃗
X,
⃗
Y ⟩ ̸= 0. We then
calculate E =
∏
R
i=2
E
y
i
i
= ( f
−⟨
⃗
X,
⃗
Y ⟩
1
∏
R
i=1
f
y
i
i
)
β
. Using
the above result, we calculate ξ
′
1
=
e(E,C
′
0
)
e(C
′′
0
,D
2
)
−1
⟨
⃗
X,
⃗
Y ⟩
=
e(g
1
,g
2
)
α
1
sβ
. If the device has been revoked, then we
cannot calculate it since we need ⟨
⃗
X,
⃗
Y ⟩ ̸= 0. Using
the linear reconstruction property of the LSSS access
structure, meaning that role credentials are prepared
for verification, we calculate ξ
2
=
∏
i∈I
e(C
i
,D
π(i),0
)·
e(K
ρ(i)
,C
′
0
)
ω
i
=
∏
A
k
∈A
e(g
1
,g
2
)
st
k
δ
. Finally, we
recover the message m by computing C
0
· ξ
2
·
e(D
0,τ
dec
,C
′′′
0
)·ξ
′
1
e(D
1,τ
dec
,C
′
0
)
·
∏
A
k
∈A
ξ
k,1
e(D
k,1
,C
′
k,0
)
= m where the role
attributes cancel out with the ones embedded in the
access policy (linear reconstruction property), while
the time interval fits in the decryption time period (set
cover mechanism).
Security Model. To prove MATRaCAE secure, ei-
ther one role authority whose some attributes are in-
cluded in the access policy is honest or the time au-
thority is honest. If all authorities are malicious and
collude, then the key generation can easily be altered
to the advantage of these authorities. W.l.o.g., we as-
sume that there is an honest role authority.
We consider a selective security model defined by
a game between an adversary E and a challenger C
(Waters, 2011). E first selects a challenged access
structure (M
∗
,ρ
∗
), a challenged revocation list R
∗
, a
challenged set A
∗
of role authorities whose attributes
are in (M
∗
,ρ
∗
), and a challenged decryption time pe-
riod T
∗
dec
. She then receives the public parameters and
authorities’ public keys. E can query devices’ secret
keys that cannot be used to decrypt CT
∗
. E selects an
honest authority A
k
∗
∈ A
∗
(Chase, 2007). Therefore,
she can request secret keys for a device with identity
ID and attribute set S
ID
as long as the device has in-
sufficient attributes from A
k
∗
to decrypt.
Initialization: E submits (M
∗
,ρ
∗
), R
∗
and T
∗
dec
to
C . She also determines A
∗
of role authorities whose
attributes are in (M
∗
,ρ
∗
) and one honest authority
A
k
∗
∈ A
∗
.
Setup: C runs the algorithms Setup, RAKeyGen and
TAKeyGen and gives to E the public parameters PP,
the public keys PK
k
for all A
k
and the public key PK
for B.
Query Phase 1: E makes secret key queries corre-
sponding to the device with identity ID such that:
• The secret keys RSK
ID,k
result from the role at-
tribute sets S
ID,k
;
• The secret key T SK
ID
results from the time
range T
ID
.
At least one of the following conditions must hold:
• Let S
ID
= ∪
A
k
∈A
∗
S
ID,k
be the disjoint union of
all the role attribute sets S
ID,k
of the device with iden-
tity ID and associated with A
k
∈ A
∗
. S
ID
does not
satisfy (M
∗
,ρ
∗
), meaning that there must be at least
one honest authority A
k
∗
∈ A
∗
from which E never
requests enough attributes to decrypt CT
∗
. The hon-
est authority A
k
∗
replies such that S
ID,k
∗
does not sat-
isfy (M
∗
,ρ
∗
), meaning that (M
∗
,ρ
∗
) cannot contain
attributes from A
k
∗
only. In addition, E never queries
the same authority twice with the same identity ID.
• ID ∈ R
∗
, meaning that the device has been re-
voked.
• T
∗
dec
is not completely covered in T
ID
, meaning
that τ
∗
dec
and all its prefixes are not in the set cover T
MATRaCAE: Time-Based Revocable Access Control in the IoT
281

of T .
Challenge: E submits two messages m
0
and m
1
of
equal length. C picks a random bit b ∈ {0,1} and
encrypts m
b
using (M
∗
,ρ
∗
), R
∗
, T
∗
dec
and A
k
∗
∈ A
∗
.
The challenged ciphertext CT
∗
is given to E .
Query Phase 2: This phase is similar to Phase 1.
Guess: E outputs b
′
∈ {0, 1} and wins if b
′
= b.
The advantage of E in the game is defined as
Adv
E
= Pr[b
′
= b] − 1/2. MATRaCAE is said to be
selectively secure if no probabilistic polynomial-time
E has non-negligible advantage in the above game.
Security Proof Sketch. We only sketch the tricks
used in our security proof due to page limitation.
Let a reduction be as follows: if one can break
MATRaCAE, then one can break the Decisional q-
BDHE assumption. Assuming that the Decisional q-
BDHE assumption holds, then there is no probabilis-
tic polynomial-time E that can selectively break MA-
TRaCAE with a challenged access structure (M
∗
,ρ
∗
),
a challenged revocation list R
∗
and a challenged de-
cryption time period T
∗
dec
, along with a set A
∗
of role
authorities whose attributes are in (M
∗
,ρ
∗
) and an
honest authority A
k
∗
∈ A
∗
.
When proving our solution secure, we need the
reduction to program the challenged ciphertext CT
∗
into the public parameters PP. An attribute may be
associated with multiple rows in the challenged ma-
trix M
∗
, meaning that the function ρ
∗
is not injective.
This is similar to a value appearing in different leaves
in a tree. For instance, let ρ
∗
(i) = z for f
z
based on
the i-th row of the matrix M
∗
. If z = ρ
∗
(i) = ρ
∗
( j)
for some i, j such that i ̸= j, then this is a problem
since we have to program both rows i and j. In the
reduction, the above conflict is solved by using differ-
ent elements in the Decisional q-BDHE assumption.
We can thus program different rows of the matrix M
∗
into one element corresponding to an attribute.
4 EXPERIMENTAL ANALYSIS
While MATRaCAE extends LYZL (Liu et al., 2018),
we choose to not compare the two schemes. By de-
sign, LYZL is more efficient than MATRaCAE. The
participation of multiple authorities (rather than a sin-
gle one) in MATRaCAE makes key generation an
heavier process by design. We showed in Section 2
that our choice of binary trees rather than 31-ary trees
is more pertinent and effective for our time-sensitive
IoT use cases. Note that only a theoretical analysis
was given in (Liu et al., 2018), making the claims
about its deployability in realistic environments (e.g.
a business) limited.
Environment. We test our solution on a Raspberry
Pi 4B with a Quad Core ARM64 Cortex-A72 CPU
running at 1.5 GHz with 8 GB of 3200 MHz SDRAM.
The Raspberry Pi is a low-cost accessible device and
is a realistic assumption of the type of computational
power that IoT devices will have in a near future. In-
deed, it has been claimed recently that IoT devices’
CPU and GPU double every 3-4 years (Sun et al.,
2020). The programming language is Python3.6 and
the library is Python-based Charm Crypto (Akinyele
et al., 2011). For all our benchmarks, we execute 1000
tests and calculate the average time (in milliseconds).
Parameters. In IoT, access policies contain up to
30 attributes and devices are allocated around 10 at-
tributes (Ambrosin et al., 2016; Yao et al., 2015).
Roles can be related to the IoT functionalities, loca-
tions and permissions to specific operations such as
Read and Write. Our implementation considers short
time intervals. Algorithms RAKeyGen and RUKey-
Gen can be run in parallel, hence, we only test MA-
TRaCAE with one role authority. Unless specified,
we consider the following parameters for our testing:
(i) The role authority A
k
has 4 attributes; (ii) The de-
vice has 2 attributes w.r.t. the role authority A
k
; (iii)
The time period consists of 16 days (T = 5); (iv) The
access policy contains 4 attributes (M has 4 rows);
(v) Decryption requires 2 attributes (2 rows will be
used). We choose to not test bigger numbers of at-
tributes, since we aim for closely matching realistic
IoT frameworks (Ambrosin et al., 2016; Yao et al.,
2015). Moreover, the efficiency of MATRaCAE will
be impacted with large attribute numbers since many
components (e.g., keys, ciphertexts) depend on those
numbers.
Elliptic Curves. Implementing MATRaCAE re-
quires to generate cyclic groups of prime orders built
from an elliptic curve. We selected the following el-
liptic curves (Miyaji et al., 2000; Galbraith, 2001;
Akinyele et al., 2011): (i) SS512 and SS1024 with
512-bit and 1024-bit base fields respectively; (ii)
MNT curves with 159-bit, 201-bit and 224-bit base
fields respectively. The results are shown in Figure
5. We provide the security level (in bits) in brack-
ets aside the name of the elliptic curve. RAKeyGen
and TAKeyGen have similar time results for all ellip-
tic curves. Except with SS1024, Setup and Encrypt
also get comparable time outputs. While SS1024 of-
fers the highest security level, the running times of
most of the algorithms are noticeably impacted. De-
cryption with curves MNT159 and MNT201 requires
around twice the time with SS512, for a similar secu-
rity level. While MNT224 guarantees a higher secu-
SECRYPT 2024 - 21st International Conference on Security and Cryptography
282
Curve/Algorithm Setup RAKeyGen TAKeyGen RUKeyGen TUKeyGen Encrypt Decrypt
SS512 (80) 8.1 4.0 9.4 21.3 31.7 26.8 18.7
SS1024 (112) 92.7 4.3 5.8 240.6 387.9 193.7 300.4
MNT159 (70) 7.5 2.3 3.5 12.9 21.8 21.0 37.8
MNT201 (90) 10.1 3.0 3.9 16.6 27.9 23.5 41.9
MNT224 (100) 13.0 3.8 5.0 21.5 36.7 28.1 61.2
Figure 5: Running times (ms) of all algorithms w.r.t. elliptic curves.
rity level than SS512, the decryption algorithm takes
3 times longer than the former. Based on a trade-off
between efficiency and security, we select the curve
SS512 for subsequent tests.
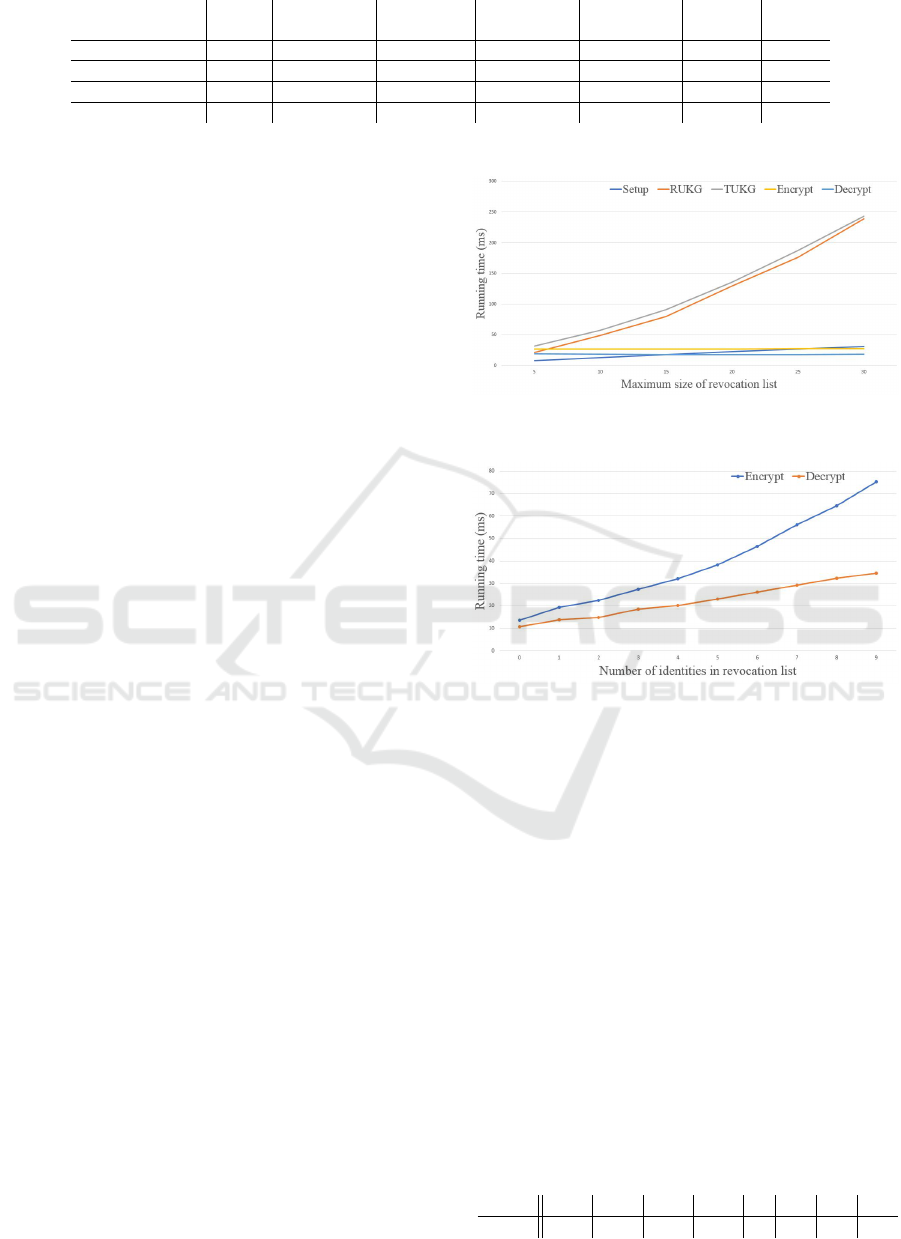
Revocation. Let R − 1 be the maximum number of
revoked devices. We are interested in observing how
the parameter R affects the execution time of MATRa-
CAE. We test all algorithms except RAKeyGen and
TAKeyGen for which R is not an input. We conduct
a first experiment with R ∈ {5,10, 15,20, 25,30}. Re-
sult are shown in Figure 6. We observe that R has
a low impact on encryption and decryption, as ex-
pected. Indeed, they rather depend on the value r = 4
that is fixed in the experiment. The running time of
Setup depends on R, with a light increase with larger
values. The running times of RUKeyGen and TUKey-
Gen are linear in R. Hence, R must remain reason-
able to permit an interesting trade-off between the fre-
quency of key updates and the length of the list R .
We suggest that R can be up to 15 to keep the run-
ning time of RUKeyGen below 100 ms. A larger value
would negatively impact the applicability of MATRa-
CAE by noticeably slowing down device key man-
agement in the IoT network. We conduct a second
experiment with R = 10 (i.e. the maximum number
of revoked devices is 9) and r ∈ [1,9]. R and r are
inputs of Encrypt and Decrypt only. We are interested
in seeing how those two algorithms are affected by r.
The results are shown in Figure 7. Encryption and de-
cryption timings linearly increase with r. The effect
is stronger for encryption than for decryption. Larger
the number of revoked devices is, more computing re-
sources are needed for encryption.
Binary tree. We vary the tree depth T in [5, 12].
TAKeyGen and TUKeyGen depend on T. The exe-
cution time of those algorithms is impacted by the
construction of the tree and the execution of the set
cover to find the minimum number of nodes to repre-
sent the time interval. The results are shown in Table
1. For T ∈ [5,8], the time required to build the binary
tree and to find the minimum cover set is strictly less
than 1 ms. For T = 9 and above, the time increases
exponentially, since the number of leaves scales with
2
T
. In IoT, it is important to keep the time required to
Figure 6: Running times (ms) of Setup, RUKeyGen, TUKey-
Gen, Encrypt and Decrypt w.r.t. R.
Figure 7: Running times (ms) of Encrypt and Decrypt w.r.t.
r.
build the binary tree below 1 ms. For instance, tem-
perature sensors collect data once every few minutes,
thus require very short time periods for access (few
days), so small trees. Defining trees with reasonable
depth moderates storage costs, hence T = 5 is a judi-
cious choice.
Key Generation. The number of attributes con-
trolled by a role authority A
k
has a linear influence
on the time needed to generate the keys PK
k
and SK
k
.
Let this number vary in [1,20]. The results are shown
in Figure 8. Each attribute adds around 1 ms in com-
puting the keys. The number of role attributes per
device has an impact on the time required to generate
the key RSK
ID,k
. Let the number of attributes from
A
k
be 15 and the number of role attributes per device
Table 1: Running times (ms) of combined TAKeyGen and
TUKeyGen w.r.t. T .
T 5 6 7 8 9 10 11 12
Time < 1 < 1 < 1 < 1 1 2 3 6
MATRaCAE: Time-Based Revocable Access Control in the IoT
283
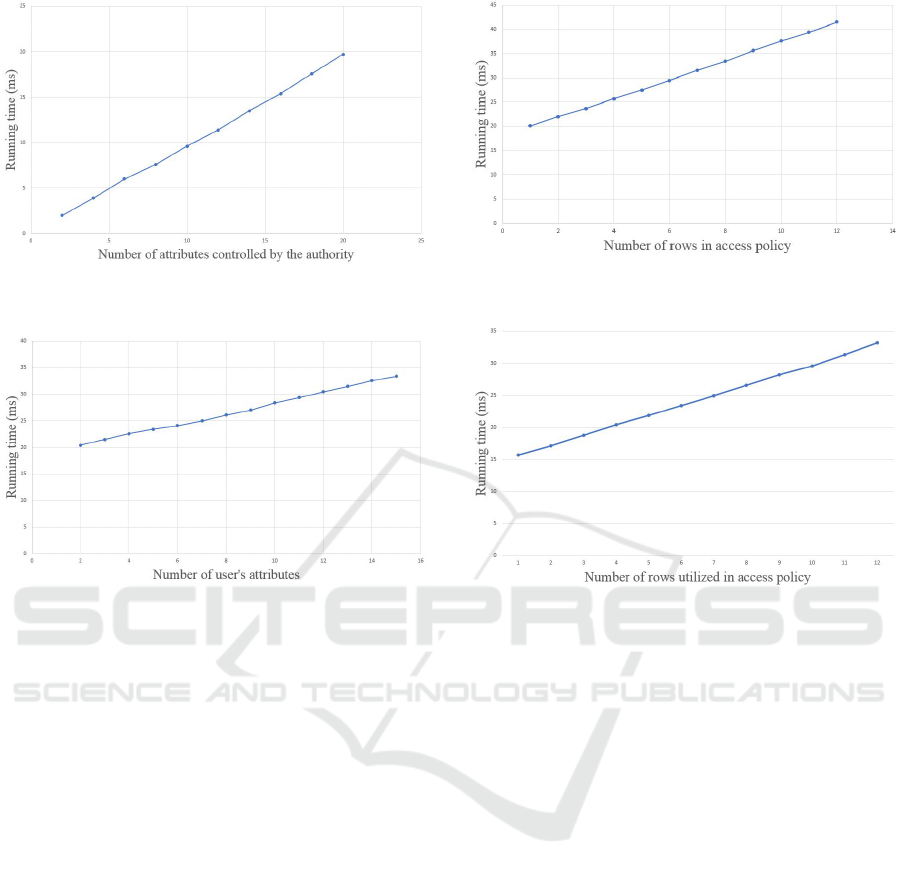
Figure 8: Running times (ms) of RAKeyGen w.r.t. role at-
tributes (authority).
Figure 9: Running times (ms) of RUKeyGen w.r.t. role at-
tributes (device).
vary in [2,15]. The results are shown in Figure 9. We
observe that the time needed to generate RSK
ID,k
is
linear in the number of role attributes given to the de-
vice. Each attribute adds around 1 ms in computing
the key. By having multiple role authorities, we man-
age to dispatch all the role attributes among them such
that each role authority has only a small attribute sub-
set and shares the computing resources to compute the
devices’ keys.
Encryption-Decryption. Let the number of at-
tributes in the access policy vary in [1,12]. This num-
ber (i.e. the number of rows in the matrix M) has an
effect on the running time of Encrypt. The results are
shown in Figure 10. The running time of Encrypt is
linear in this number. 2 ms are added for each extra
attribute. There could be up to 30 attributes in the ac-
cess policy (Ambrosin et al., 2016; Yao et al., 2015).
With 30 attributes, a message could be encrypted in
76 ms, which is reasonable. Decrypt depends on the
number of matrix rows needed to recover the mes-
sage. Let the number of attributes for decryption (i.e.
the number of rows) vary in [1, 12]. The results are
shown in Figure 11. The running time of Decrypt is
linear in the number of attributes needed for decryp-
Figure 10: Running times (ms) of Encrypt w.r.t. number of
attributes in the access policy (rows).
Figure 11: Running times (ms) of Decrypt w.r.t. number of
attributes for decryption (rows).
tion. 1.5 ms are added for each extra attribute. There
could be up to 10 attributes needed to decrypt a ci-
phertext (Ambrosin et al., 2016; Yao et al., 2015).
With 10 attributes, a message could be recovered in
30 ms, which is rational.
5 CONCLUSION
In this paper, we designed a new solution called MA-
TRaCAE for secure access control in IoT, using CP-
ABE with attributes representing device roles and
time intervals and equipped with a direct revocation
mechanism. We devised a novel approach based
on binary trees for securing time-sensitive data ex-
changes in IoT. This allows us to find an interesting,
yet effective, trade-off between the frequency of key
updates and the length of the revocation list. We gave
the intuition to prove MATRaCAE secure under the
Decisional BDHE assumption. Implementation and
evaluation showed that MATRaCAE is fully deploy-
able in IoT.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
284

REFERENCES
AboDoma, N., Shaaban, E., and Mostafa, A. (2021). Adap-
tive time-bound access control for internet of things in
fog computing architecture. Int. J. of Comp. and App.,
pages 1–12.
Akinyele, J. A., Green, M. D., and Rubin, A. D.
(2011). Charm: A framework for rapidly prototyp-
ing cryptosystems. Cryptology ePrint Archive, Report
2011/617.
Ali, Z. H., Ali, H. A., and Badawy, M. M. (2015). Internet
of Things (IoT): Definitions, Challenges and Recent
Research Directions. Int. J. of Comp. App., 128(1):37–
47.
Ambrona, M. and Gay, R. (2023). Multi-authority abe for
non-monotonic access structures. In PKC’23, pages
306–335.
Ambrosin, M., Anzanpour, A., Conti, M., Dargahi, T.,
Moosavi, S. R., Rahmani, A. M., and Liljeberg, P.
(2016). On the Feasibility of Attribute-Based En-
cryption on Internet of Things Devices. IEEE Micro,
36(6):25–35.
Beimel, A. (1996). Secure Schemes for Secret Sharing and
Key Distribution. PhD thesis, Israel.
Bethencourt, J., Sahai, A., and Waters, B. (2007).
Ciphertext-policy attribute-based encryption. In
SP’07, pages 321–334.
Chase, M. (2007). Multi-authority attribute based encryp-
tion. In TCC’07, pages 515–534.
Datta, P., Komargodski, I., and Waters, B. (2021). Decen-
tralized multi-authority abe for dnfs from lwe. In EU-
ROCRYPT’21, pages 177–209.
Galbraith, S. D. (2001). Supersingular curves in cryptogra-
phy. In ASIACRYPT’01, pages 495–513.
Guillevic, A. (2013). Comparing the pairing efficiency over
composite-order and prime-order elliptic curves. In
ACNS’13, pages 357–372.
Hwang, Y. H. (2015). IoT Security & Privacy: Threats and
Challenges. In IoTPTS’15.
Liu, J. K., Yuen, T. H., Zhang, P., and Liang, K.
(2018). Time-based direct revocable ciphertext-policy
attribute-based encryption with short revocation list.
In ACNS’18, pages 516–534.
Liu, Z., Wang, F., Chen, K., and Tang, F. (2020). A
new user revocable ciphertext-policy attribute-based
encryption with ciphertext update. Secur. Commun.
Netw., 2020:1–11.
Lu, X., Fu, S., Jiang, C., and Lio, P. (2021). Security and
privacy challenges for intelligent internet of things de-
vices view this special issue. Sec. and Comm. Netw.,
2021.
Macedo, D., Guedes, L. A., and Silva, I. (2014). A depend-
ability evaluation for internet of things incorporating
redundancy aspects. In ICNSC’14, pages 417–422.
Mekki, K., Bajic, E., Chaxel, F., and Meyer, F. (2019).
A comparative study of lpwan technologies for large-
scale iot deployment. ICT Express, 5(1):1–7.
Miyaji, A., Nakabayashi, M., and Takano, S. (2000).
Characterization of elliptic curve traces under FR-
reduction. In ICISC’00, pages 90–108.
Oualha, N. and Nguyen, K. T. (2016). Lightweight
attribute-based encryption for the internet of things.
In ICCCN’16, pages 1–6.
Pa, Y. M. P., Suzuki, S., Yoshioka, K., Matsumoto,
T., Kasama, T., and Rossow, C. (2015). IoT-
POT: Analysing the Rise of IoT Compromises. In
WOOT’15, pages 9–9.
Patel, M., Shangkuan, J., and Thomas, C. (2017). What’s
new with the Internet of Things? Technical report,
McKinsey.
Pham, C., Lim, Y., and Tan, Y. (2016). Management ar-
chitecture for heterogeneous iot devices in home net-
work. In GCCE’16, pages 1–5.
Rouselakis, Y. and Waters, B. (2015). Efficient statically-
secure large-universe multi-authority attribute-based
encryption. In FC’15, pages 315–332.
Sahai, A., Seyalioglu, H., and Waters, B. (2012). Dynamic
credentials and ciphertext delegation for attribute-
based encryption. In CRYPTO’2012, pages 199–217.
Sahai, A. and Waters, B. (2005). Fuzzy identity-based en-
cryption. In EUROCRYPT’05, pages 457–473.
Shamir, A. (1985). Identity-based cryptosystems and signa-
ture schemes. In CRYPTO’84, pages 47–53.
Sun, Y., Agostini, N. B., Dong, S., and Kaeli, D. (2020).
Summarizing CPU and GPU design trends with prod-
uct data. arXiv 1911.11313.
Waters, B. (2011). Ciphertext-policy attribute-based en-
cryption: An expressive, efficient, and provably se-
cure realization. In PKC’11, pages 53–70.
Yan, X., Tu, S., Alasmary, H., and Huang, F. (2023). Multi-
authority ciphertext policy-attribute-based encryption
(MA-CP-ABE) with revocation and computation out-
sourcing for resource-constraint devices. MDPI Appl.
Sc., 13(20).
Yang, K. and Jia, X. (2014). Expressive, efficient, and re-
vocable data access control for multi-authority cloud
storage. IEEE Trans. on Paral. and Dist. Syst.,
25(7):1735–1744.
Yao, X., Chen, Z., and Tian, Y. (2015). A lightweight
attribute-based encryption scheme for the internet of
things. Future Gener. Comput. Syst., 49(C):104–112.
Zhang, J., Li, T., Jiang, Q., and Ma, J. (2022a). Enabling
efficient traceable and revocable time-based data shar-
ing in smart city. Eurasip J. on Wirel. Comm. and
Netw., 2022(3).
Zhang, Q., Wang, S., Zhang, D., Wang, J., and Zhang, Y.
(2019). Time and Attribute Based Dual Access Con-
trol and Data Integrity Verifiable Scheme in Cloud
Computing Applications. IEEE Access, 7:137594–
137607.
Zhang, R., Li, J., Lu, Y., Han, J., and Zhang, Y. (2022b).
Key escrow-free attribute based encryption with user
revocation. Inf. Sc., 600:59–72.
Zhang, T., Wang, C., and Chandrasena, M. I. U. (2023).
Blockchain-assisted data sharing supports deduplica-
tion for cloud storage. Connect. Sc., 35(1).
Zhang, Y., Nakanishi, R., Sasabe, M., and Kasahara, S.
(2021). Combining IOTA and Attribute-Based En-
cryption for Access Control in the Internet of Things.
MDPI Sensors, 21(15):50–53.
MATRaCAE: Time-Based Revocable Access Control in the IoT
285
