
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover
Authentication in Space Information Networks
Arijit Karati
a
, Ting-Yu Chen
b
and Kai-Yao Lin
Department of Computer Science and Engineering, National Sun Yat-sen University, Kaohsiung, Taiwan
Keywords:
Authentication, Space Information Networks, Post-Quantum Security, Key Agreement, Handover
Mechanism, Access Identity Authentication, Anonymity.
Abstract:
The Space Information Network (SIN) has evolved from a terrestrial network to an extension, enhancing
communication capabilities and enabling augmented intelligence research. However, communication security
is crucial due to potential risks like inadequate implementation and high access latency. This could allow
malicious organizations to access gateways and compromise the system’s safety and privacy. This work pro-
poses a novel framework and authentication protocol to streamline the incorporation of security measures into
unencrypted wireless communication within the SIN. The proposed authentication protocol is based on sign-
cryption and HMAC, ensuring communication confidentiality, access identity validation, and anonymity. The
protocol utilizes lattice cryptography and demonstrates resilience against quantum attacks. Besides, the pro-
tocol ensures user anonymity while safeguarding identity management by considering a suitable approach to
overseeing revocable keys. The evaluated protocol satisfies message authentication, unlinkability, traceability,
and identity privacy criteria, thwarting several security risks, including replay attacks, man-in-the-middle at-
tacks, node impersonation, and quantum attacks. Compared to existing works, our protocol exhibits significant
promise in enabling secure communication with adequate functional overheads within the SIN framework.
1 INTRODUCTION
With the acceleration of communication technologies
anywhere and anytime, the space industry is reviving
services like earth observation, space-based cloud, re
mote sensing, and Internet of Things (IoT) data
collection. Standardization organizations like the
3rd Generation Partnership Project (3GPP), Interna-
tional Telecommunication Union (ITU), and Euro-
pean Telecommunications Standards Institute (ETSI)
are exploring satellite communications to integrate
space and terrestrial networks, supporting future wire-
less ecosystems (Liberg et al., 2020).
The Space Information Network (SIN) offers
global coverage and on-demand bandwidth and are
not limited by geographical conditions, unlike tradi-
tional wireless communication like road and cellular
networks (Chen et al., 2021). Improved technologies
like satellite miniaturization, reusable rocket launch,
and semiconductor technology can integrate low-orbit
satellites, drones, and airships into the SIN for ex-
tended connectivity. However, data can be received
a
https://orcid.org/0000-0001-5605-7354
b
https://orcid.org/0009-0009-6135-3508
if they pass exact detection ranges, as ground stations
are sometimes not feasible in specific locations.
Orbit Specifications. As shown in Figure 1, the
SIN combines the capabilities of ground-based wire-
less networks with satellites. It has three categories:
geo- synchronous Earth orbit (GEO), medium Earth
orbit (MEO), and low Earth orbit (LEO) satellites.
GEO satellites appear stationary over the Earth’s sur-
face, while LEO and MEO satellites are classified as
non-GSO. LEO satellites conduct communication and
scientific data sharing, while MEO spacecraft nav-
igate and share space data. Typically, GEO satel-
lites have a round-trip delay of about 550 millisec-
onds (ms), while 240 ms for LEO satellites indicates
a significant benefit in real-time applications. SIN al-
lows LEOs to interact with terrestrial networks via
satellite-ground (SG) links, inter-satellite links (ISL),
and a network control center (NCC). A ground sta-
tion (GS) connects LEOs to other Internet endpoints
and resources, serving as a ground interface for LEOs
and connecting to the NCC via terrestrial networks.
However, there are various cyberthreats while com-
municating with LEO.
298
Karati, A., Chen, T. and Lin, K.
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover Authentication in Space Information Networks.
DOI: 10.5220/0012845600003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 298-309
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

N
G
S
O
G
S
O
LEO
1
LEO
i
LEO
l
MEO
1
MEO
2
MEO
m-1
MEO
m
GEO
1
GEO
2
GEO
g
ISL
ISL
ISL
IOL
IOL
IOL
IOL
IOL
ISL: Inter-satellite link
IOL: Inter-orbit link
NCC: Network Control Center
TC: Terrestrial Controller
Cloud
Internet
Ground
station
Base Station
NCC
Car
UE
API
n
API
1
IoTD
n
LTE
Wireless core network
IoT network
Drone
IoTD
1
TC
Terrestrial Network
TAPI
IOL
SAP
SAP
ISL ISL ISL ISL
SAP
Gateway
Figure 1: A schematic diagram of the Space Information Network (SIN) where attackers compromise satellite services by ex-
ploiting public parameters and information-sharing flaws. Robust handover authentication (in red box) prevents data invasion.
Handover Between SIN Entities. Transmission
delays are less for LEO spacecraft than for GEO and
MEO satellites, making it better suited to delivering
data communication and access services in underde-
veloped countries. Communication between the user,
satellite, and GS is usually ongoing during a success-
ful authentication session where a user connects to a
satellite via a satellite access point (SAP). Typically,
SAP
SAP
V
L
c
L
n
GS
ISL
R
e
q
u
e
s
t
f
o
r
c
h
a
n
g
e
t
h
e
s
a
t
t
e
l
i
t
e
SAP
SAP
V
L
c
L
n
GS
ISL
Figure 2: Satellite only handover.
satellites move faster than Earth’s surface, creating a
dynamic network where GS offers users an interface
to the terrestrial network as a ground station. Two
wireless connections are commonly used to commu-
nicate with the user: a) between the user and SAP, and
b) between SAP and GS. These two links may fail due
to the mobility of the satellite and its users. Figure 2
defines a typical handover scenario for user U
x
.
• Satellite only Handover (S
c
↮ U
x
): The satel-
lite S
c
moves to the far end with speed v, and the
user’s distance from S
c
increases, interrupting sig-
nal. Before the signal is interrupted, U
x
applies to
S
c
for the user-ground station link to be relayed by
a new S
n
with improved communication.
Thus, it is important to provide communication safety
for U
x
when S
c
hands over session to S
n
.
1.1 Security and Privacy Requirements
Fast Handover Authentication (FHA) in SIN should
meet critical safety traits between U
i
and the ground
station GS
k
relaying S
j
for an attacker A:
F1. (Qu-safety): Quantum computers may break
classic public-key cryptosystems. So, SIN needs
strong authentication to stem quantum attacks.
F2. (Level-II Security): The key generation requires
user and NCC participation, due to the fact that
the NCC may be compromised (Girault, 1991).
F3. (Mutual Authentication (Karati et al., 2023)):
Enabling U to discern GS and vice versa is a cru-
cial trait for end-to-end authentication.
F4. (Session Key Agreement): It enables U
i
and GS
k
to convince a specific key for a single session.
F5. (Forward/Backward Safety): The former avoids
future data theft while the latter fixes past breach.
F6. (User Privacy): Accessing GS
k
makes U
i
un-
traceable and communication unlinkable for A.
F7. (Fast Handover): U
i
does not need to be reau-
thenticated to continue services from GS
k
if
its session doesn’t timeout when S
j
leaves the
range.
Further, an authentication scheme must resist attacks:
A1. (Entity Impersonation): One must repel A to mi-
mic a valid U
i
to link with GS
k
to send fake data.
A2. (Replay Attack): One must repel A to purposely
and deceptively send past data for system access.
A3. (Man-in-the-Middle Attack): One must repel A
to modify data between two parties (assuming
they covertly find a session key).
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover Authentication in Space Information Networks
299

A4. (Ephemeral Secret Leakage): One must stop A
to get ephemeral secrets to reveal sessions keys.
A5. (GPS Spoofing): Robust authentication prevents
U
i
from sending a fake location to S
j
or GS
k
.
1.2 Related Works
The surge in quantum computation has resulted in a
substantial upswing in designing cryptosystems that
protect against quantum attacks. The notion of lattice-
based signcryption under the Fiat-Shamir framework
was proposed in 2009 (Lyubashevsky, 2009), which
later was enhanced by refining the signing procedure
(Lyubashevsky, 2012). Following this, the authors
in (Bai and Galbraith, 2014) proposed a lattice-based
signcryption based on the learning with errors (LWE)
assumption. Next, the authors in (Ma et al., 2015) de-
signed public key encryption with delegated equality
test with flexible authorization, strengthening privacy
protection. In 2018, the authors in (Sato and Shikata,
2018) devised a lattice-based signcryption approach
without the random oracle model (ROM) under the
hardness of the LWE and small integer solution (SIS).
After that, the authors in (Yang et al., 2018) proposed
a roaming authentication for the SIN. It utilizes the
group signature to ensure user anonymity. Following
that, the authors in (G
´
erard and Merckx, 2018) pre-
sented a signcryption based on the work in (Bai and
Galbraith, 2014) under the Fiat-Shamir framework.
Shortly thereafter, the authors in (Duong et al., 2019)
developed a new public key encryption with equality
test (PKEET) to verify if two ciphertexts are from the
same message. Next, the authors in (Ma et al., 2019)
introduced a lattice-based access authentication for
massive IoT devices. After that, the authors in (Guo
and Du, 2020) designed an RLWE-based anonymous
mutual authentication and key agreement (AKA) pro-
tocol to support a lower cost without compromis-
ing security. Based on the work in (Duong et al.,
2019), the authors in (Le et al., 2021) found critical
issues in (Sato and Shikata, 2018) and devised a new
scheme. Next, the authors in (Le et al., 2021) pro-
posed a lattice-based signcryption with equality test
resistant to internal attacks. However, it fail to sup-
port the authorization model of the designated tester.
After that, two quantum-safe PKEET constructions
were devised that provide anonymity and secure in
the standard model based on integer and ideal lattices
(Roy et al., 2022). Subsequently, the authors in (Guo
et al., 2022) designed a secure authentication protocol
based on the randomized RLWE, which decreases the
authentication delay.
Recently, the authors in (Dharminder et al., 2023)
introduced an authentication protocol to enhance the
security of the satellite’s communication based on
the RLWE assumption. After that, the authors in
(Al-Mekhlafi et al., 2023) proposed a lattice-based
lightweight cryptosystem in 5G-enabled vehicular
networks. Most of the above works emphasize quan-
tum safety without delving into any specific applica-
tion, particularly in the context of SIN. Thus, despite
resisting quantum attacks, they might not possess the
comprehensive security attributes mentioned earlier.
1.3 Motivation and Our Contributions
Despite extensive use cases, most authentication sys-
tems in SIN do not consider modern attacks, including
quantum attacks. Some systems employ timestamps
with cumbersome time synchronization; others ignore
effective handover scenarios. Besides, many methods
are secure yet inefficient privacy measures with inad-
equate cryptographic operations. Motivated by these
security and privacy challenges, we pose a question:
Could we design a fast, anonymous authentication
protocol for the SIN, allowing secure handover au-
thentication while resisting quantum attacks?
To address the aforementioned question, we pro-
pose a novel protocol called QuDPas-FHA employing
the nonce-based challenge-response pairs (CRPs) for
authentication. We utilize the hash-based message au-
thentication code (HMAC), encryption, and singcryp-
tion to achieve specific security benefits as mentioned
in Section 1.1. Within the context of the authentica-
tion framework, we contribute the following:
• The QuDPas-FHA utilizes lattice-based opera-
tions and HMAC to achieve mutual authentication
and robust session key agreement. Besides, it at-
tains Girault’s Level-II security for cryptographic
keys by generating keys that consider the user’s
and NCC’s participation.
• It guarantees user privacy by enabling anonymous
communication during authentication, which is
untraceable and unlinkable for A.
• It satisfies the necessary security properties F1-
F7 and A1-A5 based on the decisional Ring-LWE
and HMAC assumptions.
• We assess the efficacy of QuDPas-FHA in terms
of authentication delay, handover overhead, trans-
mission, and storage costs. It achieves more se-
curity functionalities compared to existing related
works with adequate functional overheads.
The remaining paper is organized as follows. Sec-
tion 2 mentions the preliminaries. Section 3 illustrates
details of the QuDPas-FHA. Next, Section 4 provides
security discussion and Section 5 lists performance
comparison. Finally, Section 6 concludes our work.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
300

2 PRELIMINARIES
This section describes the necessary backgrounds for
comprehending the proposed work.
2.1 Cryptographic Hash Function
For some t, a cryptographic hash H ∈ H maps m(t)-
bit binary strings to l(t)-bit binary strings (Ramos-
Calderer et al., 2021). It holds the following traits:
• The length m(t) is greater than the length of l(t).
• H(·) can be computed in polynomial time t, and
• A polynomial-time algorithm A gets advantage
Pr[A(x
1
,x
2
) | x
1
̸= x
2
and H(x
1
) = H(x
2
)] ≤ ε(n)
where ε(n) is the negligible function for some n.
Definition 1 (HMAC Safety). A hash-based mes-
sage authentication code defined as HMAC(K, M) =
H(K ⊕ opad,H(K ⊕ ipad,M)) outputs a tag using a
symmetric secret K for data M, where
• ipad=64 times 0x36 and opad=64 times 0x5c
It holds the following properties:
• It is infeasible for any A to retrieve M
1
from
tag
1
= HMAC(K,M
1
) in polynomial time t.
• For any M
1
̸= M
2
V
|M
1
| = |M
2
|, we have ε(n) ≥
Pr[A(M
1
,M
2
)|HMAC(K,M
1
) = HMAC(K, M
2
)].
2.2 Notion of Lattice and Assumptions
Let x = {x
1
,·· · ,x
n
} be a set of linearly independent
vectors in m-dimensional Euclidean space R
m
that
forms a lattice X (x
1
,x
2
,·· · ,x
n
) =
∑
n
i=1
α
i
x
i
such
that α
i∈[1,n]
∈ Z where x
i∈[1,n]
∈ R
m
are known as ba-
sis vectors, and (m, n) be the (dimension,rank) of X ,
respectively (Lyubashevsky and Micciancio, 2018).
The lowest distance of X is d
min
(X )=min
x∈X \{0}
∥x∥.
A linearly independent vector set outputs X , forming
its basis. The basis vectors support: a) every X has at
least one basis, and b) basis of X is not unique.
Definition 2. Let X = [x
1
,·· · ,x
n
] ∈ Z
m×n
be a basis
matrix of a lattice where basis vectors are placed in
the column of X. Lattice X in a m-dimensional Eu-
clidean space R
m
is denoted as X (X) = [X t : t ∈ Z
n
]
where Xt represents a matrix-vector multiplication.
Post-quantum structures often use q-ary lattices
on implementation. For integer q, a lattice X (Z
n
q
⊆
X ⊆ Z
n
) supports modular arithmetic.
Definition 3. For X ∈ Z
m×n
q
under modulo q, two
different q-ary lattices X
⊥
q
and X
q
can be defined:
a) X
⊥
q
= {t ∈ Z
n
| Xt = 0 mod q},
b) X
q
= {t ∈ Z
n
, u ∈ Z
m
| t = X
T
u mod q}
Definition 4 (Inhomogeneous Small Integer Solution
(ISIS)). Given X ∈ Z
m×n
q
, an integer constant α and
a random vector u ∈ Z
m
q
, finding a vector t ∈ Z
n
\{0}
where ∥ t ∥< α and X t = u mod q is infeasible.
Definition 5 (Discrete Gaussians). Given standard
deviation σ and c ∈ Z
n
q
, the discrete Gaussian distri-
bution is D
X ,σ,c
(x) = ρ
σ,c
(x)/ρ
σ,c
(X ),∀x ∈ X , where
ρ
σ,c
(x) is a Gaussian function on Z
n
centered at c.
Ring Learning with Error. The ring learning with
errors (RLWE) is built on the polynomials arithmetic
with coefficients in a finite field. A polynomial ring is
defined as P
q
= Z
q
[x]/⟨p(x)⟩ with a narrow D of zero
mean over Z, where p(x) =
∑
n
i=0
p
i
x
i
is an irreducible
polynomial. For fast execution, we set p(x) = x
n
+ 1
and q ≡ 1 mod 2n. Assume a
i
∈ P
q
is a set of random
but known polynomials with coefficients in Z
q
and
e
i
∈P is a set of random but unknown small polyno-
mials with coefficients in D. Let s ∈ P
q
be a unknown
polynomial where b
i
∈ P
q
such that b
i
= a
i
· s + e
i
.
Definition 6 (Search-RLWE). Given (a
i
,b
i
), finding
unknown s for any polynomial-time bounded adver-
sary A is computationally infeasible. The advantage
of A in breaching the Search-RLWE is defined as
Pr[a
i
∈ P
q
,e
i
∈ P ;s ← A(a
i
,b
i
)|b
i
= a
i
· s + e
i
] ≥ ε
Definition 7 (Decisional-RLWE). Given (a
i
,b
i
), de-
ciding whether b
i
= a
i
· s + e
i
or a random b
i
∈ P
q
for
any A is infeasible. The advantage of A in breaching
the Decisional-RLWE is defined as
|Pr[A(a
i
,a
i
· s + e
i
)] − Pr[A(a
i
,b
i
)]| ≥ ε
2.3 Details of SETLA Scheme
The proposed QuDPas-FHA protocol uses some func-
tions, such as ENC[·, ·], DEC[·, ·], SetlaSC[·,·,·] and
SetlaU SC[·, ·,·] under SETLA specification (G
´
erard
and Merckx, 2018) which is discussed as below.
• KeyGen[a
1
,a
2
]: It declares two parameters a
1
and a
2
as public variables. Then, it generates s,
e
1
, and e
2
at random from P
q,[1]
, where s rep-
resents the secret parameter, and e
1
and e
2
de-
note the noise parameters. Next, it computes
t
1
← a
1
· s + e
1
and t
2
← a
2
· s + e
2
and outputs
the key pair (PK = (t
1
,t
2
),SK = (s,e
1
,e
2
)).
• SetlaSC[PK
b
,SK
a
,m]: It takes input receiver’s
public key pk
b
, sender’s keys (s
a
,e
a,1
,e
a,2
,PK
a
),
a message m, a random oracle H : ∗ → {v |
v ∈ P
q,[1]
,∥v∥
1
= ω}, and a symmetric encryp-
tion algorithm SE(·). First, it chooses K
r
←
{0,1}
256
and y
r
← P
q·[B]
. Next, it using the ran-
dom oracle to compute c ← H(⌊a
1
· y⌉
d
,⌊a
2
·
y⌉
d
,m,K,pk
a
,pk
b
). Besides it calculates z ←
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover Authentication in Space Information Networks
301

s
a
· c + y. After that, it generates w
1
= a
1
· y −
e
a,1
· c and w
2
= a
2
· y − e
a,2
· c. It verifies whether
z ̸∈ P
q,[B−ω]
and ⌊a
1
· y⌋
d
̸= ⌊w
1
⌋
d
and ⌊a
2
· y⌋
d
̸=
⌊w
2
⌋
d
. Now, it selects y
′
r
← P
q,[B]
and derives
x ← t
b,1
·y+y
′
+Encode(K). Finally, it computes
ε = SE(K,m). The output is C = (z,c,x, ε).
• SetlaUSC[SK
b
,PK
a
,m]: It takes input receiver’s
key (s
b
,PK
b
), sender’s public key PK
a
, the sign-
cryptext C = (z,c,x,ε), a random oracle H : ∗ →
{v | v ∈ P
q,[1]
,∥v∥
1
= ω}, and a symmetric de-
cryption SD. It calculates w
1
← a
1
· z − t
a,1
· c
and w
2
← a
2
· z − t
a,2
· c. Next, it decodes ε
as K = Decode(x − w
1
· s
b
). Finally, it returns
m = SD(K,ε) and if c = H(v, m, K,PK
a
,PK
b
) and
z ∈ P
q,[k−ω]
hold; otherwise, returns ⊥.
• ENC[PK,m]: Define the public key PK = a ·s +e,
where s,e
r
← D. Then, it samples y
1
, y
2
, and y
3
from D and computes c
1
← a · y
1
+ y
2
and c
2
←
PK · y
1
+ y
3
+ Encode(m). The output is (c
1
,c
2
).
• Encode[m]: Given message m = [m
1
,·· · , m
n
], it
element-wise encodes as m[i] = m[i] · ⌊
q−1
2
⌋.
• DEC[c
1
,c
2
,SK]: Define secret key SK = s, where
s
r
← D. It computes m = c
2
− c
1
· s ≈ Encode(m).
Next, it applies Decode(m) to recover original m.
• Decode[m]: It checks whether each m[i] lies
within the interval [−⌈
q
4
⌉,⌈
q
4
⌉ − 1]. If yes, it sets
m[i] = 1. Otherwise, declares m[i] = 0.
Now, we introduce our QuDPas-FHA to address,
“Could we design a fast, anonymous authentication
protocol for the SIN, allowing secure handover au-
thentication while resisting quantum attacks?”
3 OUR CONSTRUCTION
This section introduces the system model and our
QuDPas-FHA with essential notations in Table 1.
3.1 System Model Description
Our QuDPas-FHA ensures uninterrupted service to
users within a single SIN network, ensuring gener-
ality while roaming within the network. The system
model comprises five entities, as explained below.
• Trusted Third Party (TTP): The TTP is crucial in
managing public-private key pairs for GSs and
users across multiple domains, ensuring identity
verification and securing information exchange
channels through the use of cryptographic keys.
• Network Control Center (NCC): The operator seg-
ment network domain is managed by this entity,
Table 1: List of useful notations.
Notation Description
ID
i
Identity of entity i
PK
x
i
,SK
x
i
Public and secret key of the SIN entity x
i
.
q Rational integer modulus ≥ 2
D Discrete Gaussian distribution
P
q,[1]
A polynomial ring Z
q
[X]/⟨X
n
+1⟩ with a narrow D,
q ≡ 1 mod 2n, and coefficients in the range [−1, 1].
v
r
←− D v is sampled from D
F
ms
(·) Secure trapdoor: {0,1} × P
q,[1]
→ P
q,[1]
H(·) Hash oracle {0,1}
∗
→{v ∈ P
q,[1]
, ∥v∥
1
= ω}
L
s
j
List of users receive services via satellite S
j
A ⊕ B Bit-wise XOR operation A and B
A||B Concatenation between A and B
HMAC[x,M] Outputs a tag for input secret x and data M
SE[K, M],
SD[K,C]
Symmetric encryption and decryption of M
and C for secret x
ENC[PK
x
i
,M],
DEC[SK
x
i
,C]
Public-key Encryption and decryption of M
and C for key PK
x
i
and SK
x
i
, respectively
SetlaSC
[SK
x
i
,PK
y
j
,M]
SETLA signcryption of M with keys
SK
x
i
and PK
y
j
SetlaUSC
[SK
y
i
,PK
x
j
,C]
SETLA unsigncryption of C with keys
SK
x
i
and PK
y
j
which allows users to access the network through
registration and certification processes.
• Ground Station (GS): It establishes connectivity
via terrestrial networks and provides an interface
for ground-based LEO satellite access.
• Low Earth Orbit (LEO) Satellites: LEO satellites
are the endpoints for users connecting to the net-
work, and recent improvements in satellite manu-
facturing technology help execute complex tasks.
• Users: It accesses the network via LEO satellites,
enabling data sharing and exchange, thereby fos-
tering a resilient digital communication platform.
As depicted in Figure 3, the TTP oversees system pol-
icy, maintaining exclusive access to its primary secret.
It gives a high-entropy secret key to NCC, which is
crucial for securely registering SIN entities. A mu-
tual authentication process is initiated when a user
wants to access services from ground station GS
k
via
a nearby satellite S
j
. The user (U
i
) initiates anony-
mous communication by connecting to the proximate
S
j
via a predetermined protocol. S
j
assists U
i
gen-
erating session-dependent tokens, building a secure
communication with U
i
and GS
k
. Next, GS
k
veri-
fies U
i
and negotiates a session key U GSK. Once
UGSK is negotiated, S
j
acts as a relay for data ex-
change between U
i
and GS
k
. For effective service
management, each S
j
maintains its list L
s
j
of active
users. Due to its roaming nature, S
j
may move out
of the communication range of U
i
or GS
k
during an
active session c. If so, and c still is active, then S
j
for-
wards its latest L
s
j
to a new S
new
j
via ISL (protected
with a pre-negotiated key) to continue service with-
out re-authenticating U
i
. Next, S
new
j
updates its list as
L
new
s
j
= L
new
s
j
S
L
s
j
. When S
new
j
comes in the range,
U
i
sends ESL-free tokens to prove its authenticity. If
SECRYPT 2024 - 21st International Conference on Security and Cryptography
302
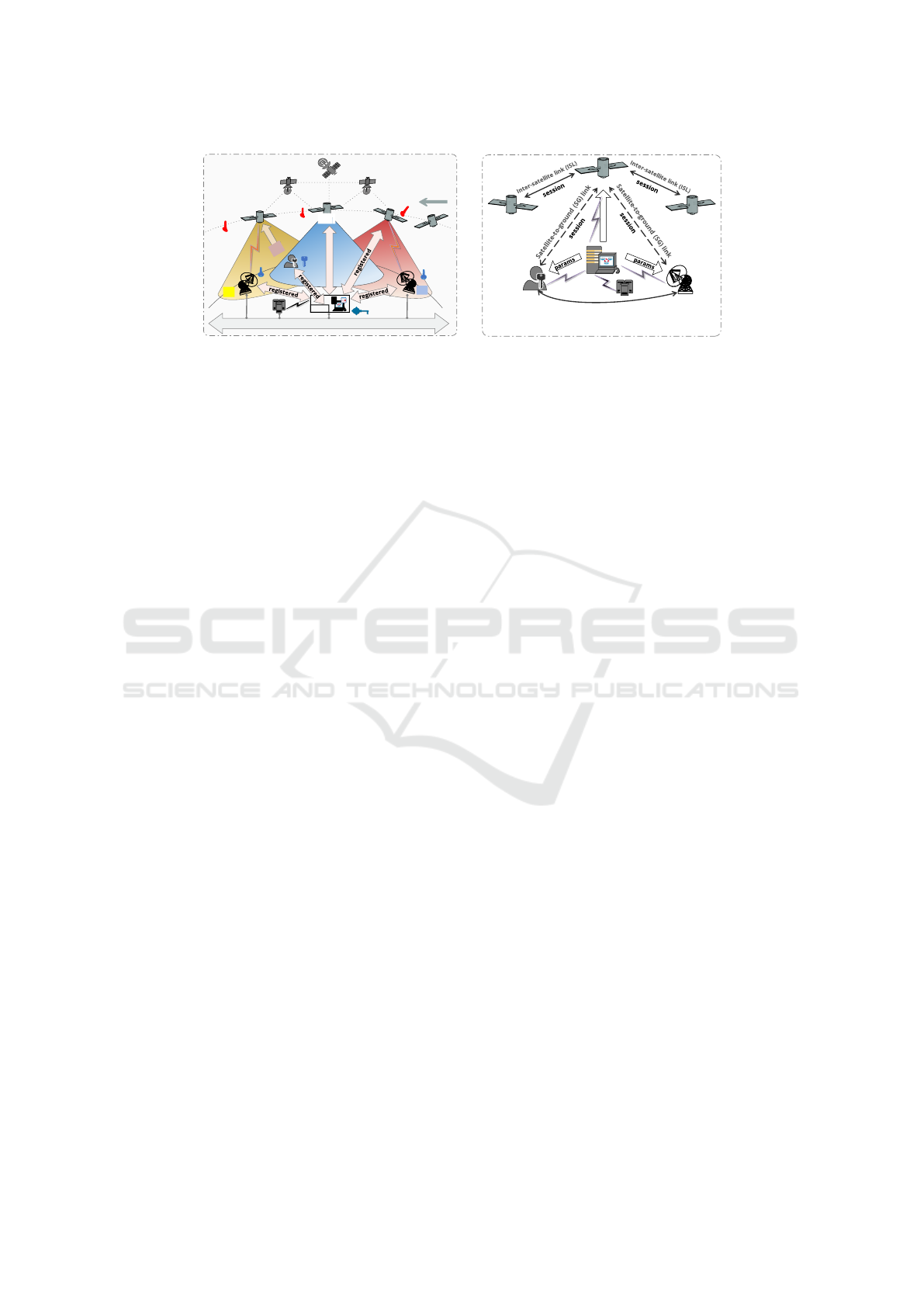
Terrestrial Transmission Network
NCC
TTP
GS
2
LEO
1
LEO
3
LEO
2
registered
new LEO
acess
request
GS
1
2
2
4
GS
SAP
NCC
3
1: Secure registration of NCC by TTP
3: SAP authentication once it finds a
new GS toward its route (implici t)
User
params
1
TTP
Session key
2: Secure registration of SIN entities
through NCC and key configuration
4: User authentication with GS through SAP
𝑴𝑺𝑲
𝑺𝑲
𝒖
𝒊
𝑺𝑲
𝒔
𝒋
𝑺𝑲
𝒈𝒔
𝒌
2
5
Figure 3: QuDPas-FHA system model overview showing crypto keys distribution for SIN entities (first part) and the commu-
nication for secure authentication (second part).
S
new
j
finds U
i
as an already authenticated user through
L
new
s
j
, it act as a relay between U
i
and GS
k
.
3.2 The QuDPas-FHA Protocol
Figure 4 depicts tokens exchange between U
i
, S
j
, and
GS
k
. Our protocol comprises five phases: NCC setup,
entity registration, authentication and key agreement,
user management as LEO constellation, and fast han-
dover authentication, each of which is discussed now.
3.2.1 NCC Setup
On input security parameter 1
γ
, the TA selects ms =
s ∈ P
q,[1]
and chooses two polynomials a
1
,a
2
∈ Z
q
[X].
Next, it chooses a trapdoor function secured with ms
as F
ms
: {0,1} × P
q,[1]
→ P
q,[1]
and sets a random
oracle as H : {0, 1}
∗
→ {v | v ∈ P
q,[1]
,∥v∥
1
= ω}.
Next, it declares the symmetric encryption and de-
cryption as SE[·,·] and SD[·,·]. Besides, it consid-
ers the Public-key encryption and decryption ENC[·,·]
and DEC[·,·], and the singcryption and unsigncryp-
tion SetlaSC[·,·,·] and SetlaUSC[·,·,·], which works
as shown in Section 2.3. Finally, it declares the global
public parameter as params = (a
1
,a
2
,H) while save
the master secret key MSK = (ms, F) securely.
3.2.2 Entity Registration
Upon obtaining user U
i
details such as identity ID
i
and other essential proofs, NCC runs UKeyGen which
returns a partial-private key s
u
i
← F(ms,ID
i
). Upon
receiving psk = s
u
i
, U
i
runs FullKEY process that gen-
erates noise parameters e
u
i
,1
,e
u
i
,2
∈ P
q,[1]
at random.
Next, it computes t
u
i
,1
← a
1
·s
u
i
+e
u
i
,1
and t
u
i
,2
← a
2
·
s
u
i
+ e
u
i
,1
. Finally, It sets its full-public-key PK
u
i
=
⟨t
u
i
,1
,t
u
i
,2
⟩ and full-secret-key SK
u
i
= ⟨s
u
i
,e
u
i
,1
,e
u
i
,2
⟩.
U
i
stores SK
u
i
in the private space securely.
Following the similar tasks, satellite S
j
processes
its keys PK
s
j
= ⟨t
s
j
,1
,t
s
j
,2
⟩ and SK
s
j
= ⟨s
s
j
,e
s
i
,1
,e
s
i
,2
⟩.
Besides, ground station GS
k
ensures its key-pair as
PK
gs
k
= ⟨t
gs
k
,1
,t
gs
k
,2
⟩ and SK
gs
k
= ⟨s
gs
k
,e
gs
k
,1
,e
gs
k
,2
⟩.
On successful registration, the credentials of SIN
entities are U
i
: (PK
u
i
,SK
u
i
), S
j
: (PK
s
j
,SK
s
j
,L
s
j
) and
GS
k
: (PK
GS
k
,SK
GS
k
), where S
j
maintains a list L
s
j
of
active users receive satellite services through S
j
.
3.2.3 Entity Authentication and Key Agreement
Entities U
i
,S
j
, and GS
k
interact among themselves to
generate a session key following the steps below:
1. User to Satellite
U
i
C
2
−−→ S
j
: To initiate a se-
cure communication, U
i
proves the authenticity.
For this, U
i
selects a nonce n
u
as ephemeral se-
cret and signcrypts n
u
with its secret key SK
u
i
and
GS
k
’s PK
GS
k
as C
1
= SetlaSC[PK
GS
k
,SK
u
i
,n
u
].
Then, it sends C
2
= ENC[PK
S
j
,C
1
||PK
u
i
] to S
j
.
2. Satellite to Ground Station
S
j
C
3
−−→ GS
k
: On
receiving a request from U
i
, satellite S
j
decrypts
with its secret SK
j
as (C
′
1
∥PK
′
u
i
) = DEC[SK
S
j
,C
2
].
Next, it selects a nonce n
s
and generates a trap-
door C
3
for GS
k
with PK
GS
k
as
C
3
= ENC[PK
GS
k
,(n
S
∥C
′
1
∥PK
′
u
i
)] (1)
and sends C
3
to GS
k
.
3. Ground Station to Satellite
GS
k
C
4
−−−−−→
⟨I
1
,I
2
⟩,I
gu
S
j
:
On receiving C
3
, GS
k
decrypts C
3
with its secret
key SK
GS
k
and retrieves certain parameters as
(n
′
S
∥C
′
1
∥PK
′
u
) = DEC[SK
GS
k
,C
3
] (2)
n
u
= SetlaUSC[SK
GS
k
,PK
′
u
i
,C
′
1
] (3)
Note that function SetlaUSC[·,·,·] fails indicates a
tampered communication by a potential foe. Else,
it confirms the user authenticity via relay S
j
. To
do this, it chooses nonce n
gs
and performs
I
1
= n
gs
⊕ n
u
⊕ n
′
S
(4)
C
4
= SetlaSC[PK
′
u
i
,SK
GS
k
,n
gs
] (5)
I
2
= HMAC[n
′
s
,C
4
] (6)
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover Authentication in Space Information Networks
303
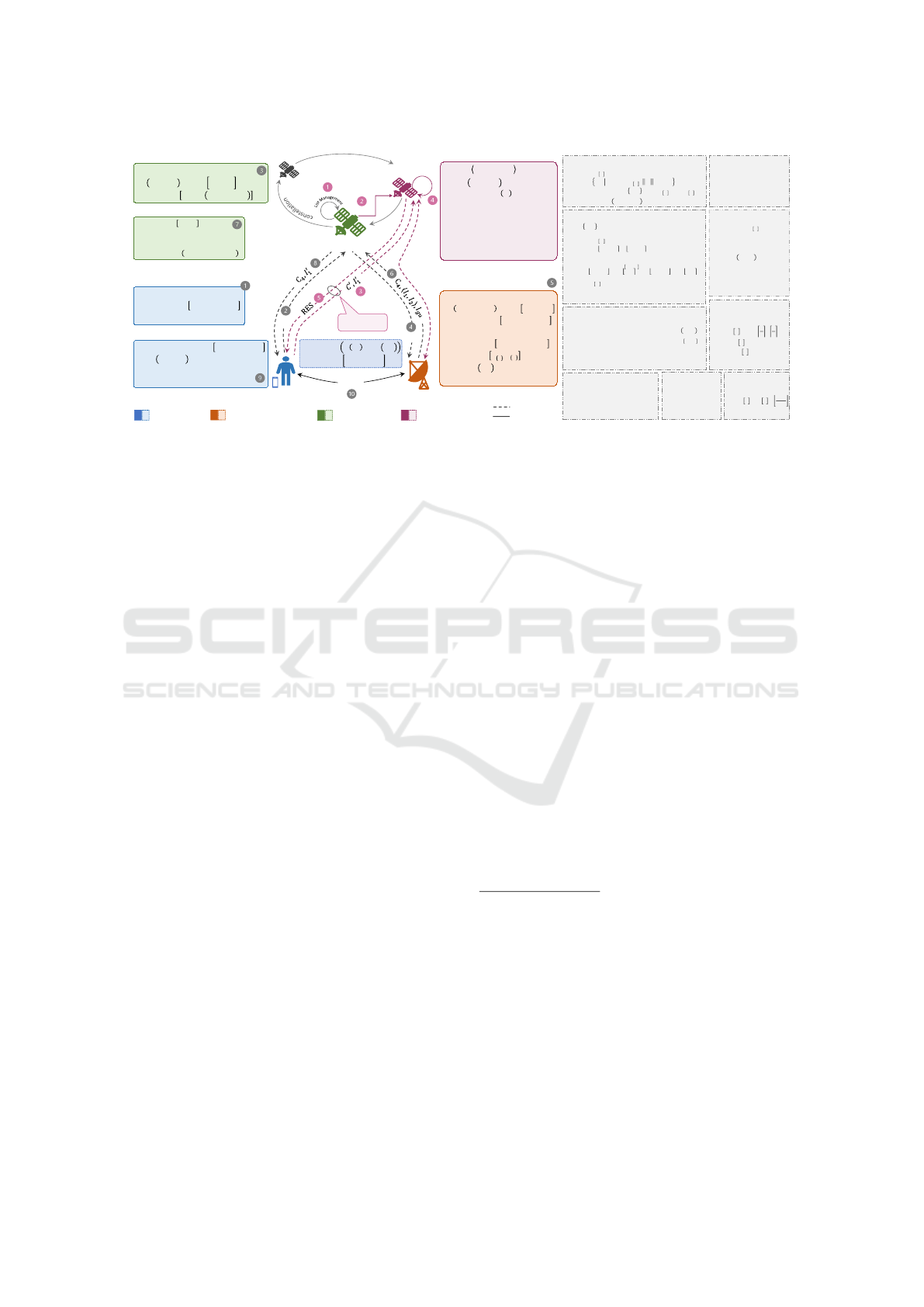
Communication
for Fast AUTH
Ground station G’s activity
UKeyGen ( ):
Return psk
SetlaSC (
, params):
, s.t.,
,
while not (
&
&
)
,
,
return C = ( )
SetlaUSC (
):
,
,
if
&
else
return D
Setup (
):
Set a trapdoor
return
)
Decode ():
for
if
̶
else
return m
DEC (
):
Decode(m)
Return
Eencode ():
for
Return m
2. if
RES = SUCC
// fast authentication
Else RES = ABORT
3. elseif next (
) = NULL
RES = ABORT
4. else GOTO 1
1.
2.
3.
1. if
Res =
2. else
Res =
1.
2.
3.
1. Gets
2. if
3. else ABORT
G : (PK
G
, SK
G
)
DetectFast
Ground Station to Satellite
User to Satellite
Session key b/w User and Ground Station
Satellite to User
Satellite to Ground station
L
i
s
t
M
a
n
a
g
e
m
e
n
t
U : (PK
u
, SK
u
)
S : (PK
S
, SK
S
)
S
new
: (
)
ISL
c
o
n
s
t
e
l
l
a
t
i
o
n
List
forward
FastAUTH
FullKEY ():
,
Return PK, SK
ENC (
):
,
+
+
Return (
)
User U’s activity
Satellite S’s activity Satellite S
new
’s activity
Public channel
Secure channel
Figure 4: SIN entity authentication and fast handover details in the QuDPas-FHA protocol.
Finally, it sends (C
4
,⟨I
1
,I
2
⟩,I
gu
= H(n
gs
) ⊕ n
′
S
)
and an acknowledgment SUCC
gsu
to S
j
. The GS
k
considers the session key as UGSK = H(n
u
||n
gs
).
4. Satellite to User
S
j
C
4
, I
′
1
−−−→ U
i
: On receiving
(C
4
,⟨I
1
,I
2
⟩), S
j
recalls n
s
. If HMAC[n
s
,C
4
]=I
2
,
then S
j
forwards (C
4
,I
′
1
= I
1
⊕ n
′
s
) to U
i
.
5. Session key between User and Ground Station
U
i
UGSK
←−−−→ GS
k
: Upon receiving C
4
from S
j
,
user U
i
unsigncrypts nonce n
gs
as
n
gs
= SetlaUSC[PK
GS
k
,SK
u
i
,C
4
] (7)
Next, it checks whether I
1
⊕ n
gs
?
= n
u
. If it hods,
the authenticity of GS
k
via relay S
j
is confirmed,
thus, U
i
sets the session key UGSK = H(n
u
||n
gs
).
Finally, it sends an acknowledgment SUCC
ugs
to
S
j
while holding (I
′
1
,n
gs
,SK) for this session.
3.2.4 User Management at LEO Constellation
Effective handover eliminates the requirement to
reauthenticate with GS
k
through below steps.
1. User Management (S
j
⇐
↶
L
s
j
↶
): If S
j
receives
both SUCC
gsu
and SUCC
ugs
, it adds U
i
in its list
L
s
j
= L
s
j
∪ {U
i,1
,U
i,2
,U
i,3
} where U
i,1
= H(I
1
),
U
i,2
= I
gu
⊕ n
s
, U
i,3
= n
s
. S
j
periodically checks
for the user’s session expiration. If it is expired
based on a threshold time limit, S
j
may remove
the added entry for specific U
i
from its list L
s
j
.
2. List Forward
S
j
L
s
j
−−→ S
new
j
: When S
j
cannot
serve U
i
owing to departing its range, it checks
whether the connected users U = {U
i
} still want
to connect with GS
k
. If it does not receive any
willingness (say, “YES”) from some users, say
U
′
⊆ U , it removes each U
j
∈ U
′
entries form L
s
j
.
For L
s
j
̸= null, S
j
sends L
s
j
to the next satellite
S
new
j
of its LEO constellation via ISL transmis-
sion. Finally, S
new
j
adds those active users’ details
in its list L
new
s
j
= L
new
s
j
S
L
s
j
. A confirmed addi-
tion disrupts service for all U
i
∈ U \U
′
from S
j
.
3.2.5 Fast Handover Authentication
This phase begins when S
j
cannot serve U
i
owing to
its communication range. A new S
new
j
from its LEO
constellation will provide services to U
i
. For our case,
U
i
∈ U \ U
′
. In a typical scenario, U
i
must reau-
thenticate to continue services from GS
k
. However,
the QuDPas-FHA does not reauthenticate users. Note
that S
j
must execute List Forward since U
i
already ver-
ified its authenticity to S
j
and its session has not timed
out. To avoid reauthentication, we enable a fast au-
thentication. Recall, U
i
holds (I
′
1
,n
gs
,SK) and sets
Tok = H(H(I
′
1
) ⊕ H(n
gs
)) (8)
C
′
= ENC[PK
s
new
j
,Tok] (9)
and sends (C
′
,I
′
1
) to S
new
j
. On receiving it, SK
new
j
de-
crypts as Tok = DEC[SK
new
j
,C
′
]. Then, it executes
DetectFast (L
new
s
j
):
S1: picks a tuple ⟨U
i,1
,U
i,2
,U
i,3
⟩ ∈ L
new
s
j
.
S2: If H (I
′
1
⊕U
i,3
) = U
i,1
, then
S2.1: Retrieves corresponding U
i,2
from L
new
s
j
.
S2.2: If Tok=H(H(I
′
1
) ⊕U
i,2
), then
– fast authentication “SUCC”.
S2.3: Else, “ABORT” session.
S3: Else, i.e., H (I
′
1
⊕U
i,3
) ̸= U
i,1
,
S3.1: If no tuple left in L
new
s
j
, S
new
j
unlinks U
i
.
S3.2: Else, GOTO step S1.
This completes the description of the QudPas-FHA
protocol. Now, we provide the security discussion.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
304

4 SECURITY ANALYSIS
The proposed QudPas-FHA protocol achieves several
security properties as mentioned in Section 1.1.
4.1 Threat Model and Assumptions
Satellite communications over unsecured links are ex-
posed to cyber threats by hostile users and active foes
(A). A can be broadly classified into two categories:
a) insiders with authorized data access, difficult to
trace, and b) outsiders with a lesser consequence. The
QuDPas-FHA targets both of these foes. Besides, ex-
istential unforgeability (EUF) assures that no one can
impersonate a legitimate SIN entity to obtain satellite
services without the respective secret key. Further, A
employs a chosen-ciphertext attack (CCA) to breach
the system’s integrity. Our protocol meets each aspect
above based on the following premises:
• Reduction capacity: QuDPas-FHA algorithms are
public. A with quantum analysis must determine
the prequisite to solve RLWE and HMAC.
• Channel security: Data over the private channel is
impenetrable by A. Conversely, A can intercept,
delete, and modify data through an open channel.
• Key safety: The user U
i
maintains the key security
and ensures that stored data retains its integrity in
the presence of computational capabilities.
• Forward/Backward secrecy: A may read keys
from a device but must be traced or denied alter-
ing session key building to avoid full invasion.
• Security level: NCC’s activity is susceptible to
monitoring by A, who may also be able to manip-
ulate the credibility of user key generation under
security Level-1 (Girault, 1991).
• Safety basics: All the conventional cryptographic
primitives are secure, thus ensuring that none ac-
quires a non-negligible advantage.
4.2 Security Properties
Theorem 1. The SETLA is (ε
′
,t
′
)−IND-SC-CCA safe
against A = (A
1
,A
2
) in the ROM under the (ε,t)−
Decisional-RLWE assumption, where ε
′
<ε and t
′
>t.
The confidentiality of SETLA can be shown with a se-
quence of games Game
0
∼ Game
3
showing semantic
security as mentioned in (G
´
erard and Merckx, 2018).
Theorem 2. Under the RLWE and HMAC assump-
tions, the QuDPas-FHA protocol meets critical secu-
rity traits, including quantum safe authentication.
Proof. The theorem follows when Lemmas 1-6 acco-
rding to Definitions 1-6 and Theorem 1 are hold.
Lemma 1 (F1: Quantum Safety). The QudPas-
FHA resists quantum attack under the random oracle
model based on the RLWE and HMAC assumptions.
Proof. The QuDPas-FHA resists quantum attacks un-
der the SETLA and HMAC framework. Based on
Theorem 1, a quantum capable A fails launching
IND-CCA for nonces n
u,0
and n
u,1
. Under Game
0
,
the simulator S chooses a binary coin b and signcrypt
n
u,b
as the original signcryption process. In Game
1
, S
just change z
r
← P
q,[B−ω]
rather z ← s
a
· c + y. In this
rejection sampling (Game
0
→ Game
1
), A achieves a
negligible advantage ε
01
. Now, in Game
2
, S changes
x ← a
′
· y + y
′
+ Encode(K) for a
′
r
← P
q
instead of
x ← t
1
· y + y
′
+ Encode(K) for public t
1
. In this
decisional-RLWE (Game
1
→ Game
2
), A gets a neg-
ligible advantage ε
12
. Similarly, in Game
3
, S up-
dates x
r
← P
q
instead of x ← a
′
· y + y
′
+ Encode(K).
Like before, A has ε
12
in Game
2
→ Game
3
due to the
DRLWE. Besides, A has a negligible advantage for
HMAC due to its strong collision-resistance trait with
secret K. Note that combining these operations does
not provide a non-negligible advantage for A. Thus,
the QuDPas-FHA ensures quantum-safety trait.
Lemma 2 (F2: Level-II Security). The QudPas-
FHA ensures Girault’s Level-II safety, avoiding key-
escrow issues in satellite communication.
Proof. Most authentications in satellite communica-
tion require a fully-trusted server to generate key-pair
(PK
u
i
,SK
u
i
). Modern approaches can avoid this issue
by choosing the public PK
u
i
and a fully-trusted third
party (TP) yielding the secret SK
u
i
. However, finding
SK
u
i
allows TP to act as a genuine user without being
traced. Thus, TP can decrypt the cipher by provid-
ing the user’s SK
u
i
. Thus, relying on a fully-trusted TP
for full-key computation could grant A accesses to a
backdoor. QuDPas-FHA views NCC a semi-trusted
entity. For each SIN entity, NCC generates a partial-
private-key psk = s
u
i
as s
u
i
← F(ms,ID
i
). Afterward,
U
i
finds the full-secret key as SK
u
i
= ⟨s
u
i
,e
u
i
,1
,e
u
i
,2
⟩
and full-public key PK
u
i
= ⟨t
u
i
,1
← a
1
· s
u
i
+ e
u
i
,1
,
t
u
i
,2
← a
2
· s
u
i
+ e
u
i
,1
⟩ using psk. Thus, even if A gets
control of NCC, it cannot find SK
u
i
needed for trans-
mission, ensuring Girault’s Level-II security.
Lemma 3 (F3: Mutual Authentication). QudPas-
FHA ensures robust mutual authentication between
users and the ground station relying satellites.
Proof. Initially, U
i
sends C
2
=ENC[PK
S
j
,C
1
∥PK
u
i
]
where C
1
=SetlaSC[PK
GS
k
,SK
u
i
,n
u
] for nonce n
u
. Due
to hardness of RLWE according to Definition 6, A
cannot reveal C
1
and PK
u
i
from C
2
. Later, GS
k
gets
C
3
=ENC[PK
GS
k
,(n
S
∥C
′
1
∥PK
′
u
i
)] from S
j
. Now, GS
k
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover Authentication in Space Information Networks
305

retrieves n
u
if SetlaUSC[SK
GS
k
,PK
′
u
i
,C
′
1
] is success-
ful. Indeed, successful unsigncryption requires in-
put PK
′
u
i
to confirm the authenticity of C
′
1
. Simi-
larly, when SetlaUSC[PK
GS
k
,SK
u
i
,C
4
] ̸=⊥, U
i
con-
firms GS
k
’s authenticity. Note, the underlying sig-
nature of SetlaSC is unforgeable (Bai and Galbraith,
2014). Under the forking lemma, A outputs two forg-
eries (z, c) and (z
′
,c
′
) for distinct random oracles but
the same random tape (thus, same q). Now (for sim-
plicity, arguing for one RLWE sample instead of two
in signature) ⌊a
1
· z − t
u
i
,1
· c⌉
d
=⌊a
1
· z
′
− t
u
i
,1
· c
′
⌉
d
=
⌊a
1
· y⌉
d
. For small e, a
1
· z − t
u
i
,1
· c=a
1
· z
′
− t
u
i
,1
· c.
For t
u
i
,1
=a
1
·s
u
i
+e
u
i
,1
, we have a
1
·(z − z
′
−s
u
i
,1
·c +
s
u
i
,1
· c
′
) + (e
u
i
,1
· (c
′
− c) + e) = 0. As shown in Sec-
tion 4.2 (Bai and Galbraith, 2014), if z − z
′
−s
u
i
,1
·c +
s
u
i
,1
· c
′
and e
u
i
,1
· (c
′
− c) + e are non-zero, a SIS so-
lution can be found. Thus, A cannot forge any signa-
ture, and (U
i
,GS
k
) uniquely identify each other with
their keys and nonce. Hence, the QuDPas-FHA meets
strong mutual authentication.
Lemma 4 (F4: Session Key Agreement). The
QudPas-FHA ensures strong session key agreement.
Proof. The robust key agreement when U
i
and GS
k
agree on session-specific random tokens never com-
municated in plaintext during authentication. On a
valid authentication, both U
i
and GS
k
agree on the key
UGSK = H(n
u
||n
gs
), where n
u
and n
gs
are ephemeral
nonce generated by U
i
and GS
k
, respectively. Besides,
GS
k
agrees on valid n
u
← SetlaUSC[SK
GS
k
,PK
u
i
,C
1
].
Note, A (even S
j
) cannot forge n
u
on behalf of U
i
as
per Lemma 3 where a
1
· (z − z
′
− s
u
i
,1
· c + s
u
i
,1
· c
′
)+
(e
u
i
,1
· (c
′
− c) + e) = 0 for two forgeries (z,c) and
(z
′
,c
′
). For valid n
gs
k
← SetlaUSC[PK
GS
k
,SK
u
i
,C
4
],
U
i
agrees on n
gs
k
. Note, when considering rapid
authentication during handover, UGSK = H(n
u
||n
g
s)
does not consider n
s
of S
j
due to the satellite’s role as
a relay for U
i
and GS
k
authentication. Thus, QuDPas-
FHA ensures strong session key agreement.
Lemma 5 (F5: Forward and Backward Secrecy).
The QudPas-FHA supports essential forward secrecy
and backward secrecy on the session key.
Proof. Forward secrecy adopted system regularly
and automatically updates encryption and decryption
keys. It safeguards essential data through session keys
even if the server’s private key is revealed. Moreover,
every user-initiated session has a unique session key;
thus, only the disclosed key is vulnerable. Note, the
compromised NCC keys cannot be used to recover
user keys according to Lemma 2. Now, consider in
past session p, U
i
and GS
k
agree on a session key
UGSK
(p)
= H(n
(p)
u
||n
(p)
gs
), where n
(p)
u
and n
(p)
gs
are the
ephemeral secrets chosen by U
i
and GS
k
, respectively.
Similarly, one considers UGSK
(c)
= H(n
(c)
u
||n
(c)
gs
) for
the current session c ≥ p + 1. Although A finds
UGSK
(c)
, it does not breach past sessions, as A can-
not find UGSK
(p)
, i.e., UGSK
(c)
̸→ U GSK
(p)
. Note,
if A still find UGSK
(p)
in c irrespective of UGSK
(c)
,
then it must breach IND-SC-CCA and EUF-SC-CMA
safety; however, it is infeasible due to Theorem 1 and
Lemma 3. Thus, QuDPas-FHA meets forward se-
crecy on session keys. Similarly for backward safety,
one finds UGSK
(c)
̸→UGSK
( f )
where f ≥ c + 1.
Lemma 6 (F6: User Privacy). QudPas-FHA ensures
anonymity, untraceability, and unlinkability traits.
Proof. Ensuring user privacy is a critical component
of SIN communication. It indicates A cannot trace
the user’s footprint during communication. Note that
user information, such as PK
u
i
, is not disclosed pub-
licly while C
2
∼ C
4
is transmitted. Besides, C
2
∼ C
4
are safeguarded under the RLWE assumption. Thus,
tracing source as PK
u
i
from C
2
∼ C
4
results in discov-
ering an RLWE solution. Moreover, by employing
nonces n
u
,n
s
, and n
gs
, C
2
∼ C
4
is rendered random for
each session. Thus, A cannot determine which data in
{C
(i)
2
∼ C
(i)
4
} is associated with the same anonymous
U
i
. Hence, user privacy is preserved .
Theorem 3. The QuDPas-FHA protocol withstands
important security attacks for the SIN.
Proof. The theorem follows when Lemmas 7-11 un-
der Definitions 1-6 and Theorem 1 are hold.
Lemma 7 (A1: Entity Impersonation). An attacker
cannot impersonate any entity to send fake data.
Proof. Suppose A impersonates U
i
and sends erro-
neous C
2
to S
j
during the authentication. Upon re-
ceiving C
2
, S
j
gets (C
′
1
∥PK
u
i
) = DEC[SK
s
j
,C
2
] where
C
′
1
= SetlaSC[PK
gs
k
,SK
u
i
,n
u
]. After receiving C
3
from S
j
, GS
k
decrypts (n
s
∥C
′
1
∥PK
u
i
) but cannot get
n
u
̸= SetlaUSC[SK
gs
k
,PK
u
i
,C
′
1
] with the derived PK
u
i
.
This is due to not generating C
′
1
with SK
u
i
. Thus, A
cannot impersonate U
i
successfully. Now, consider A
impersonates GS
k
and sends (C
4
,⟨I
1
,I
2
⟩) to S
j
where
I
1
= n
gs
⊕ n
u
⊕ n
′
s
and I
2
= HMAC[n
′
s
,C
4
]. On get-
ting it, S
j
finds HMAC[n
s
,C
4
] ̸= I
2
. Thus, it aborts
communication. Even if A breaches it, U
i
finds n
gs
̸=
SetlaUSC[PK
GS
k
,SK
u
i
,C
4
]. Therefore, QuDPas-FHA
resists U
i
and GS
k
impersonation attempts.
Lemma 8 (A2: Replay Attack). An attacker cannot
replay challenge-response pairs for system access.
Proof. During authentication, if A attempts to re-
play any of (C
2
∼ C
4
) as U
i
, it will be promptly de-
tected, and the session key agreement will be termi-
nated. Suppose, A replay C
2
= ENC[PK
S
j
,C
1
||PK
u
i
]
SECRYPT 2024 - 21st International Conference on Security and Cryptography
306
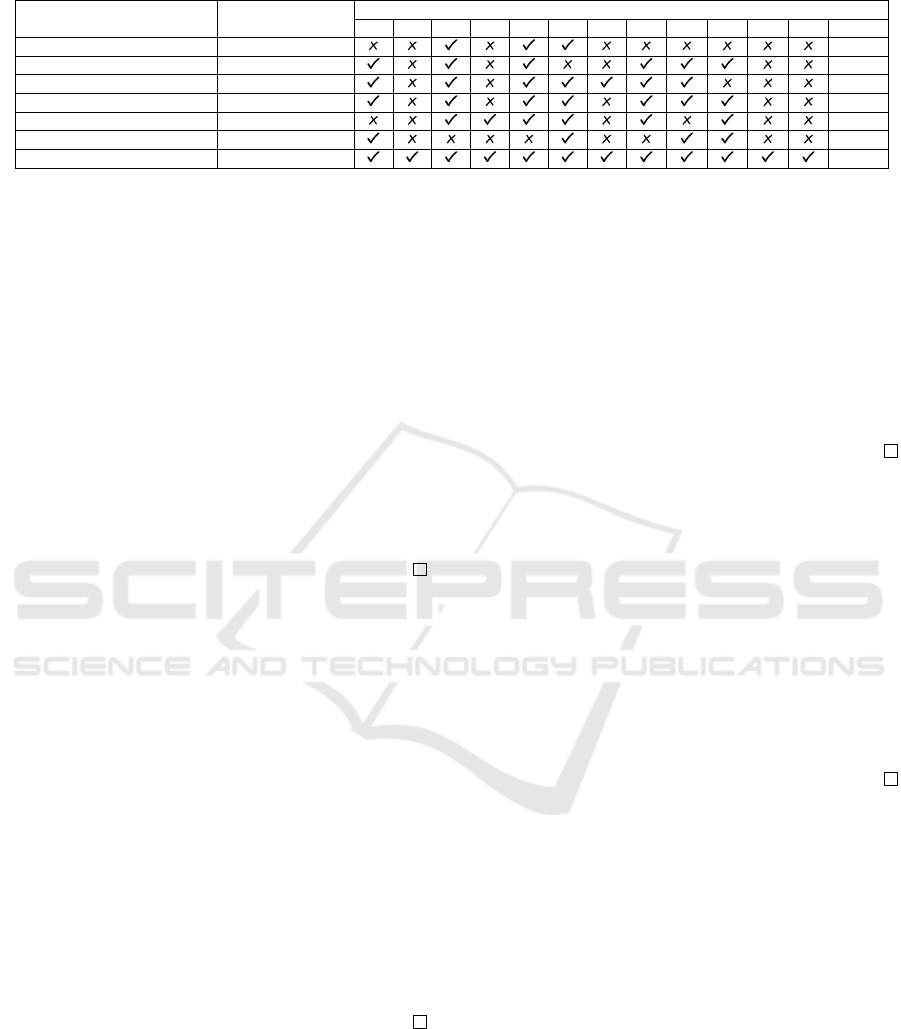
Table 2: Security functionalities comparisons of the existing schemes.
Scheme Assumption
Security Functionalities
F1 F2 F3 F4 F5 F6 F7 A1 A2 A3 A4 A5 (in %)
W1 (Yang et al., 2018) ECDSA 25
W2 (Ma et al., 2019) ISIS 50
W3 (Guo and Du, 2020) RLWE 58
W4 (Guo et al., 2022) RLWE 58
W5 (Dharminder et al., 2023) RLWE 50
W6 (Al-Mekhlafi et al., 2023) SIS and ISIS 33
The QuDPas-FHA RLWE and HMAC 100
F1: Quantum-safe, F2: Level-II Safety, F3: Mutual Authentication, F4: Session Key Agreement, F5: Forward and Backward Secrecy, F6: User Privacy,
F7: Authentication Handover, A1: Withstand Impersonation Attack, A2: Anti-Replay, A3: Withstand MitM Attack, A4: ESL-free, A5: No GPS spoofing
where C
1
= SetlaSC[PK
GS
k
,SK
u
i
,n
u
] and sends C
2
to
S
j
. While S
j
sends C
3
= ENC[PK
GS
k
,(n
S
∥C
1
∥PK
u
i
)],
GS
k
reveals (n
′
S
∥C
′
1
∥PK
′
u
) = DEC[SK
GS
k
,C
3
], n
u
=
SetlaUSC[SK
GS
k
,PK
′
u
i
,C
′
1
] from C
3
. Although, after
several processes, A retrieves (C
4
,I
′
1
), it cannot reveal
n
gs
due to unavailability of SK
u
i
. Now, consider A
replays old C
3
= ENC[PK
GS
k
,(n
old
S
∥C
′
1
∥PK
′
u
i
)], then
GS
k
can compute and submits X = (C
4
,⟨I
1
,I
2
⟩,I
gu
).
Note that A cannot alter X due to unknown n
old
S
. On
getting X, S
j
confirms HMAC[n
new
s
,C
4
] ̸= I
2
, thus,
⊥. Similarly in the new session, if A replays C
4
=
SetlaSC[PK
′
u
i
,SK
GS
k
,n
old
gs
], then S
j
confirms I
2
̸=
HMAC[n
new
s
,C
4
]. Moreover, the QuDPas-FHA flags
for replaying any communication by A between U
i
,S
j
and GS
k
. Thus, it resists replay attacks.
Lemma 9 (A3: Man-in-the-Middle Attack). An at-
tacker cannot tamper with communication to obtain
session or secret key(s) in the QuDPas-FHA protocol.
Proof. A man-in-the-middle (MitM) attack occurs
when A intercepts communication between U
i
and
GS
k
to steal the session key U GSK or produces two
keys for both without being traced. Note UGSK =
H(n
u
||n
gs
). When U
i
sends C
2
to S
j
, A alters it to
C
′
2
=ENC[PK
S
j
,C
′
A
1
||PK
u
i
] for some C
′
A
1
and sends C
′
2
instead of C
2
to S
j
. On valid decryption, S
j
retrieves
(C
′
A
1
||PK
u
i
) and use it with a nonce n
s
to send C
3
.
On receiving C
3
, GS
k
cannot retrieve user nonce n
u
as
SetlaUSC[SK
GS
k
,PK
u
i
,C
′
A
1
] →⊥. This is because A
chose random C
′
A
1
as it cannot execute SetlaSC[·, ·,·]
for n
u
due to unavailability of SK
u
i
. It is also possible
that A replays old C
old
2
during current authentication;
however, a replay is infeasible based on Lemma 8.
Hence, QuDPas-FHA resists MitM attack.
Lemma 10 (A4: Ephemeral Secret Leakage). An
attacker cannot disclose ephemeral secrets during en-
tity authentication in the QuDPas-FHA protocol.
Proof. If ephemeral secrets are leaked, A can re-
veal the session key. ESL attacks leak session keys
through eavesdropped messages. In QuDPas-FHA,
the ephemeral secrets in every session are n
u
and n
gs
where the session key is UGSK = H(n
u
∥n
gs
). Note,
n
u
is signcrypted with PK
gs
k
. Thus, A or S
j
cannot
reveal n
u
due to the hardness of RLWE assumption.
Similarly, for n
gs
. Thus, unauthorized disclosure of
n
u
and n
gs
is maintained. Beside, when authentica-
tion is delegated to S
new
j
via secure forwarding, S
new
j
’s
list is updated as L
new
j
← L
new
j
∪ L
j
. Note that L
new
j
holds the ephemeral secret of GS
k
as H(n
gs
), therefore
only U
i
and GS
k
know it, preventing leaking. Thus,
QuDPas-FHA resists ESL attacks.
Lemma 11 (A5: GPS Spoofing). A GPS location
spoofing attempt is unsuccessful during entity authen-
tication in the related protocols.
Proof. Insufficient authentication lets U
i
spoof loca-
tion data while being traced as a valid user. After au-
thentication, QuDPas-FHA prevents users from send-
ing fake locations due to strong key agreement. Else,
an RLWE solution results from its security breaches.
Note that user privacy may be impaired while sending
location data. However, QuDPas-FHA fulfills this by
making communication anonymous while identifying
U
i
uniquely. Thus, QuDPas-FHA withstands GPS lo-
cation spoofing once a user is authenticated.
5 PERFORMANCE EVALUATION
Table 2 compares the security attributes where
the QuDPas-FHA outperforms existing approaches.
Now, we examine various overheads incurred in dif-
ferent phases of the QuDPas-FHA.
Security Specification: For a minimum of 128 bits
of classical security, we use n = 1024,m = 2048, ω =
16,d = 15,B = 2
15
,q = 2
25
,κ = 131. Besides, we use
SHA-256 underlining hash function and 128-bit AES
for symmetric encryption and deciphering.
5.1 Computation Cost
U
i
executes various operations to verify its legitimacy
to GS
k
via S
j
. For this, U
i
utilizes public-key encryp-
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover Authentication in Space Information Networks
307
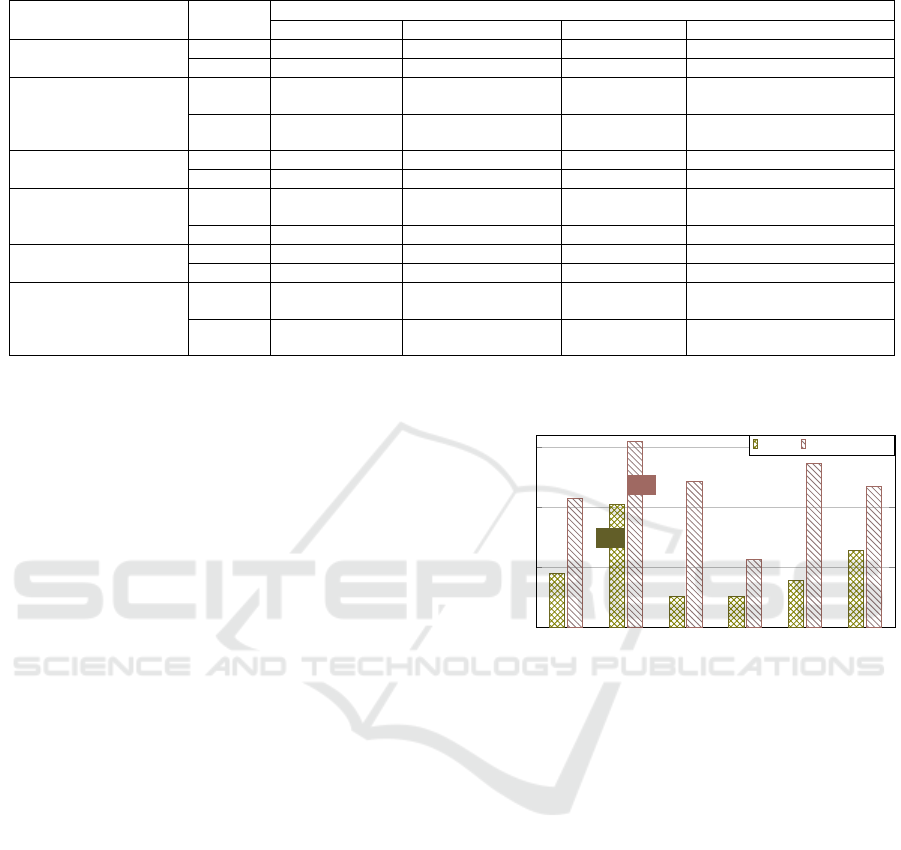
Table 3: Computation overheads of various entities in the related protocols.
Scheme
AUTH Computation Cost
Type C
U
(at U
i
side) C
S
(at S
j
side) C
GS
(at GS
k
side) Total (C
U
+C
S
+C
GS
)
W1 (Yang et al., 2018)
Regular T
h
+ T
ex
+ 2T
bp
2T
h
+ 4T
ex
+ 5T
bp
T
h
+ 5T
ex
4T
h
+ 10T
ex
+ 7T
bp
Handover T
h
+ T
ex
+ 2T
ecc
2T
h
+ 4T
ex
+ 5T
ecc
T
h
+ 5T
ex
4T
h
+ 10T
ex
+ 7T
ecc
W2 (Ma et al., 2019)
Regular 3T
h
+ 3T
la
+
3T
lm
2(|L|+ 1)T
h
+ 2|L|T
la
+ (3|L|+ 2)T
lm
T
h
+ T
la
+ T
lm
2(|L|+ 3)T
h
+ 2(|L|+ 2)T
la
+
3(|L|+ 2)T
lm
Handover 3T
h
+ 3T
la
+
3T
lm
2(|L|+ 1)T
h
+ 2|L|T
la
+ (3|L|+ 2)T
lm
T
h
+ T
la
+ T
lm
2(|L|+ 3)T
h
+ 2(|L|+ 2)T
la
+
3(|L|+ 2)T
lm
W3 (Guo and Du, 2020)
Regular 7T
h
+ T
la
+ 4T
lm
5T
h
+ T
la
+ 4T
lm
− 14T
h
+ 2T
la
+ 8T
lm
Handover 7T
h
+ T
la
+ 4T
lm
5T
h
+ T
la
+ 4T
lm
− 14T
h
+ 2T
la
+ 8T
lm
W4 (Guo et al., 2022)
Regular 5T
h
+ T
ed
+
2T
ra
+ 4T
rm
3T
h
2T
h
+ T
ed
+
2T
ra
+ 4T
rm
10T
h
+ 2T
ed
+ 4T
ra
+ 8T
rm
Handover 3T
h
4T
h
T
h
8T
h
W5
(Dharminder et al., 2023)
Regular 6T
h
+ T
la
+ 4T
lm
− 5T
h
+ T
la
+ 4T
lm
11T
h
+ 2T
la
+ 8T
lm
Handover 6T
h
+ T
la
+ 4T
lm
− 5T
h
+ T
la
+ 4T
lm
11T
h
+ 2T
la
+ 8T
lm
The QuDPas-FHA (ours)
Regular T
h
+2T
ed
+7T
la
+
6T
lm
T
hm
+2T
ed
+5T
la
+3T
lm
2T
h
+3T
ed
+T
hm
8T
la
+ 11T
lm
3T
h
+2T
hm
+7T
ed
+20T
la
+20T
lm
Handover 3T
h
+ T
ed
+
3T
la
+ 2T
lm
(|L|+ 2)T
h
− (|L|+ 5)T
h
+ 2T
ed
+
4T
la
+ 3T
lm
T
h
: Cost for one hash operation; T
ex
: Time to run modular exponentiation; T
bp
: Cost for one bilinear pairing; T
lm
: Time for matrix multiplication; T
hm
: Time
for HMAC operation; T
la
: Time for matrix addition; T
rm
: Time for ring multiplication; T
ra
: Time for ring addition; T
ed
: Time to execute Encode/Decode
tion (E), signcrypt (SC), unsigncrypt (USC), and hash
operations (H). The overhead of U
i
is C
U
=(E + SC+
USC+H). Besides, S
j
runs E, D, and HMAC (HM)
operations. The burden on S
j
is C
S
=(E + D + HM).
Further, GS
k
runs one from each of D, SC, USC, HM,
and H operations. Thus, GS
k
’s overhead is C
GS
=(D+
SC+USC+HM+2H). The authentication handover
needs U
i
to run C
FA
U
= (E+3H) operations, while S
j
has at least C
FA
S
=2H computations. Note that the
our handover authentication is much faster than re-
authentication. Table 3 exhibits a detailed comparison
between related works (W1∼W5) and QuDPas-FHA.
In this comparison, the symbols E, D,SC, and USC
are broken down into low-level operations, excluding
lightweight cryptographic operations like XOR and
concatenation, as our primary emphasis is on time-
consuming operations. It is worth noting that if any
scheme does not provide any handover authentication,
the cost is equivalent to standard authentication.
5.2 Token Exchange and Keys Storage
In QuDPas-FHA, several data are transmitted as au-
thentication tokens. For the comparison purpose, we
assume the length of various parameters as |ID
i
|=16
Bytes (B), |G|=128 B, |Z
∗
q
|=20 B, random |r|=16 B,
hash |h|=32 B, |Z
m
|=256 B, and |Z
m×n
|=32768 B.
Communication cost focuses on open channel data
size. For authentication, U
i
sends D
U
=288 B while
satellite S
j
sends D
S
= 960 B. The ground station GS
k
transfers D
GS
=800 B. Besides, U
i
sends D
FA
U
=288 B
to validate its pre-authentication status for fast au-
thentication. To store crypto keys, U
i
,S
j
, and GS
k
consider 1208 B keys to store in the private space.
W1 W2 W3 W4 W5 Ours
0
1,000
2,000
3,000
Scheme
Size (in Bytes-B)
Storage Communication
×2
5
×2
6
Figure 5: Comparison of transmission and storage costs.
Figure 5 shows detailed storage and transmission cost
comparisons between related works.
Further Discussion. Table 2 shows that the
QuDPas-FHA achieves critical security attributes.
Besides, it avoids the need for synchronizing data
for each authentication session which withstand
desynchronization attacks launched by prospective
foes. It ensures robust mutual authentication through
unique self-authentication of both the user and
ground station, generating a session key as UGSK =
H(n
u
∥n
G
S). Service undeniability is maintained by
using lattice-based signcryption with the secret keys
of the respective entities. User revocation involves
creating an explicit list with the revoked user’s public
key stored in a publicly available storage, which can
be updated by the NCC. The QuDPas-FHA distributes
diverse duties among multiple entities, reducing the
number of crypto operations at lightweight devices
compared to high-end ground stations. Although W4
requires fewer costs, as shown in Figure 5, it achieves
SECRYPT 2024 - 21st International Conference on Security and Cryptography
308

58% of total F1-F7 and A1-A5 traits, making it a fea-
sible solution with adequate functional overheads.
6 CONCLUSION AND FUTURE
RESEARCH DIRECTION
The paper introduces a robust privacy-preserved au-
thentication and key agreement for the space infor-
mation network. It offers various safety traits, includ-
ing mutual authentication, session key agreement, for-
ward/backward secrecy, and user anonymity. Under
the decisional-RLWE assumption, it withstands sev-
eral attacks, including quantum, user impersonation,
replay and man-in-the-middle attacks. Compared to
existing works, the suggested protocol provides am-
ple operational safety (at least 40% more) with ade-
quate computation, transmission, and storage costs.
Although, our protocol has comprehensive traits,
it needs more storage and processing power due to
SETLA-based approach. In the future, we will design
a more efficient authentication for undeniable services
in a zero-trust region-based multi-NCC framework.
ACKNOWLEDGEMENTS
This work was supported in part by the National Sci-
ence and Technology Council (NSTC) under grants
112-2221-E-110-027 and 112-2634-F-110-001-MBK
and by the CANSEC-LAB@NSYSU in Taiwan.
REFERENCES
Al-Mekhlafi, Z. G., Al-Shareeda, M. A., Manickam, S.,
Mohammed, B. A., and Qtaish, A. (2023). Lattice-
based lightweight quantum resistant scheme in 5G-
enabled vehicular networks. Mathematics, 11(2):399.
Bai, S. and Galbraith, S. D. (2014). An improved compres-
sion technique for signatures based on learning with
errors. In Topics in Cryptology – CT-RSA 2014, pages
28–47, Cham. Springer International Publishing.
Chen, Y.-A., Zhang, Q., Chen, T.-Y., Cai, W.-Q., Liao, S.-
K., Zhang, J., Chen, K., Yin, J., Ren, J.-G., Chen, Z.,
et al. (2021). An integrated space-to-ground quantum
communication network over 4,600 kilometres. Na-
ture, 589(7841):214–219.
Dharminder, D., Dadsena, P. K., Gupta, P., and Sankaran, S.
(2023). A post quantum secure construction of an au-
thentication protocol for satellite communication. Int.
J. Satell. Comm. N., 41(1):14–28.
Duong, D. H., Fukushima, K., Kiyomoto, S., Roy, P. S.,
and Susilo, W. (2019). A lattice-based public key en-
cryption with equality test in standard model. In In-
formation Security and Privacy–ACISP 2019, pages
138–155, Cham. Springer International Publishing.
G
´
erard, F. and Merckx, K. (2018). SETLA: Signature and
encryption from lattices. In Intl. Conf. on Cryptology
and Network Security, pages 299–320. Springer.
Girault, M. (1991). Self-certified public keys. In Ad-
vances in Cryptology – EUROCRYPT’91, pages 490–
497, Berlin, Heidelberg. Springer.
Guo, J. and Du, Y. (2020). A novel RLWE-based anony-
mous mutual authentication protocol for space infor-
mation network. Secur. commun. netw., 2020:1–12.
Guo, J., Du, Y., Wu, X., Li, M., Wu, R., and Sun, Z. (2022).
PSAA: Provable secure and anti-quantum authentica-
tion based on randomized RLWE for space informa-
tion network. arXiv preprint arXiv:2208.00901.
Karati, A., Chang, Y.-S., and Chen, T.-Y. (2023). Robust
three-factor lightweight authentication based on ex-
tended chaotic maps for portable resource-constrained
devices. In Proc. of the 20th International Confer-
ence on Security and Cryptography - SECRYPT, pages
673–682. INSTICC, SciTePress.
Le, H. Q., Duong, D. H., Roy, P. S., Susilo, W., Fukushima,
K., and Kiyomoto, S. (2021). Lattice-based signcryp-
tion with equality test in standard model. Computer
Standards & Interfaces, 76:103515.
Liberg, O., L
¨
owenmark, S. E., and Euler et al., S. (2020).
Narrowband internet of things for non-terrestrial net-
works. IEEE Commun. Mag., 4(4):49–55.
Lyubashevsky, V. (2009). Fiat-shamir with aborts: Applica-
tions to lattice and factoring-based signatures. In Intl.
Conf. on the Theory and Application of Cryptology
and Information Security, pages 598–616. Springer.
Lyubashevsky, V. (2012). Lattice signatures without trap-
doors. In Advances in Cryptology – EUROCRYPT
2012, pages 738–755, Berlin, Heidelberg. Springer.
Lyubashevsky, V. and Micciancio, D. (2018). Asymptoti-
cally efficient lattice-based digital signatures. Journal
of Cryptology, 31(3):774–797.
Ma, R., Cao, J., Feng, D., and Li, H. (2019). LAA:
lattice-based access authentication scheme for iot in
space information networks. IEEE Internet Things J.,
7(4):2791–2805.
Ma, S., Zhang, M., Huang, Q., and Yang, B. (2015). Public
key encryption with delegated equality test in a multi-
user setting. The Computer Journal, 58(4):986–1002.
Ramos-Calderer, S., Bellini, E., Latorre, J. I., Manzano, M.,
and Mateu, V. (2021). Quantum search for scaled
hash function preimages. Quantum Inf. Process.,
20(5):180.
Roy, P. S., Duong, D. H., Susilo, W., Sipasseuth, A.,
Fukushima, K., and Kiyomoto, S. (2022). Lattice-
based public-key encryption with equality test sup-
porting flexible authorization in standard model. The-
oretical Computer Science, 929:124–139.
Sato, S. and Shikata, J. (2018). Lattice-based signcryption
without random oracles. In Post-Quantum Cryptog-
raphy, pages 331–351, Cham. Springer International
Publishing.
Yang, Q., Xue, K., Xu, J., Wang, J., Li, F., and Yu, N.
(2018). AnFRA: Anonymous and fast roaming au-
thentication for space information network. IEEE
Trans. Inf. Forensics Secur., 14(2):486–497.
QuDPas-FHA: Quantum-Defended Privacy-Preserved Fast Handover Authentication in Space Information Networks
309
