
Enhancing OpenID Connect for Verifiable Credentials with DIDComm
Roberto De Prisco
1 a
, Sergiy Shevchenko
1, 2 b
and Pompeo Faruolo
2
1
Computer Science Department, University of Salerno, Salerno, Italy
2
eTuitus s.r.l., Fisciano (SA), Italy
www.etuitus.it
Keywords:
OpenID Connect for Verifiable Credentials, DIDComm, Decentralized Identity, Secure Communication,
Self-Sovereign Identity, Mediator Service.
Abstract:
In the evolving landscape of digital identity management, the secure and efficient handling of verifiable creden-
tials is paramount. OpenID Connect for Verifiable Credentials (OIDC4VC) provides a foundational framework
for such interactions, yet it lacks mechanisms for robust, secure communication post-credential issuance and
verification. This paper addresses these limitations by proposing an enhancement to OIDC4VC, integrating
DIDComm to facilitate encrypted, direct communication between entities. This enhancement introduces a
novel approach by embedding an ”X-Mediation” header within the OIDC4VC response, containing the URL
of a mediator service that is essential for the continued secure exchange of messages and credentials via DID-
Comm. The proposed solution, while ensuring backward compatibility, aims to enhance the privacy, security,
and user engagement in digital identity systems by allowing credential issuance and verification processes to
be initiated through push notifications, thereby aligning OIDC4VC more closely with the decentralized ethos
of self-sovereign identity.
1 INTRODUCTION
In the digital era, the secure and efficient manage-
ment of digital identities is of paramount importance.
At the heart of this management are the interactions
between issuers and holders of Verifiable Credentials
(VCs). VCs are pivotal in advancing self-sovereign
identity, empowering individuals to control their dig-
ital identities independently of centralized authori-
ties. Despite their transformative potential, a critical
limitation within the OpenID Connect framework for
Verifiable Credentials (OIDC4VC) is its lack of pro-
vision for direct, secure communication between is-
suers and holders. This paper addresses this gap by
proposing enhancements to the OIDC4VC protocol,
aiming to foster robust, privacy-preserving commu-
nication channels that resonate with the decentralized
ethos of VCs. Through this work, we seek to optimize
digital identity verification processes, bolster security,
and encourage broader adoption of VCs.
a
https://orcid.org/0000-0003-0559-6897
b
https://orcid.org/0000-0002-0864-2919
2 BACKGROUND AND
LITERATURE REVIEW
In this section we provide some background knowl-
edge and a review of relevant literature.
2.1 Understanding Digital Identity
Systems
Digital identity systems provide the mechanisms
through which individuals and organizations can
prove and authenticate their identity in online envi-
ronments. Traditionally, these systems have been cen-
trally managed by authoritative entities, leading to
concerns over privacy, security, and user control. The
emergence of blockchain and distributed ledger tech-
nologies has spurred the development of decentral-
ized solutions, such as Self-Sovereign Identity (SSI)
(Wikipedia contributors, 2024), which provide users
with control over their personal data by employing
Verifiable Credentials (VCs).
844
De Prisco, R., Shevchenko, S. and Faruolo, P.
Enhancing OpenID Connect for Verifiable Credentials with DIDComm.
DOI: 10.5220/0012850800003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 844-849
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

2.2 The Role of OpenID Connect
OpenID Connect (OIDC) (OpenID Foundation, 2024)
is an authentication protocol built on top of OAuth
2.0 (Hardt et al., 2024) that allows clients to verify
the identity of an end-user based on the authentica-
tion performed by an Authorization Server, as well as
to obtain basic profile information about the end-user
in an interoperable and REST-like manner. OIDC has
been widely adopted due to its simplicity and effec-
tiveness in handling identities across domains.
2.3 Evolution Towards OIDC for
Verifiable Credentials
Integrating OpenID Connect (OIDC) with verifi-
able credentials (VCs) marks a significant advance-
ment in digital identity frameworks. This integra-
tion enhances user privacy and data control, lever-
aging OIDC’s widespread infrastructure alongside
blockchain capabilities. OIDC4VC (Lodderstedt
et al., 2024) bridges traditional centralized identity
providers and self-sovereign identity (SSI), emphasiz-
ing user autonomy.
OIDC4VC extends OIDC to support VC issuance,
presentation, and verification, allowing OIDC to man-
age cryptographically secure credentials across plat-
forms. By incorporating decentralized identifiers
(DIDs) (Sporny et al., 2024), OIDC4VC supports a
decentralized trust model, reducing reliance on cen-
tralized authorities and enhancing user privacy.
However, implementing OIDC4VC faces chal-
lenges such as interoperability with existing sys-
tems, managing blockchain operations, and achieving
widespread adoption among service providers (Lux
et al., 2020).
3 DIDComm: A PROTOCOL FOR
ENCRYPTED
COMMUNICATION
DIDComm (Curren et al., 2024) is a protocol for se-
cure, encrypted communication based on Decentral-
ized Identifiers (DIDs). It extends DIDs from static
identifiers to dynamic peer-to-peer messaging (Sam
Curren (Indicio), 2024). DIDComm is transport ag-
nostic, operating over protocols like HTTP, Blue-
tooth, and offline modes, ensuring broad application
flexibility.
Messages in DIDComm are encrypted for spe-
cific recipients using keys controlled by the recipi-
ent’s DID, ensuring privacy and integrity. The proto-
col includes mechanisms for message threading, error
handling, and acknowledgments, making it reliable
for critical communications. These features position
DIDComm as essential for secure, direct communica-
tion in decentralized identity systems, complementing
frameworks like Hyperledger Indy (Indy, 2024) .
3.1 Gap Analysis: Integrating
DIDComm with OIDC4VC
While OIDC4VC advances credential management,
it lacks mechanisms for secure, ongoing communica-
tion post-issuance or verification. Current OIDC4VC
implementations manage credential issuance and ver-
ification but do not support continuous interactions,
which are crucial for dynamic updates and secure ex-
changes.
DIDComm (Curren et al., 2024) addresses this
gap by providing encrypted, peer-to-peer communi-
cation, extending DIDs beyond identification to sup-
port ongoing interactions. Integrating DIDComm
with OIDC4VC could facilitate secure negotiations,
updates, and revocations of credentials, maintaining
confidentiality and integrity through strong encryp-
tion.
Challenges in this integration include technical
complexity, standardization needs, and adoption bar-
riers. Addressing these is essential for a holistic iden-
tity management solution that supports robust user in-
teractions.
4 THE GAP IN
POST-CREDENTIAL ISSUANCE
AND VERIFICATION
COMMUNICATION
The lifecycle of digital credentials in decentralized
identity systems extends beyond simple issuance and
verification. Critical interactions, such as updates, re-
vocations, and continuous authentications, are essen-
tial for maintaining the integrity and relevance of cre-
dentials over time. Despite this, current implemen-
tations of OpenID Connect for Verifiable Credentials
(OIDC4VC), exhibit significant gaps in supporting
these interactions post-credential issuance and veri-
fication.
4.1 Post-Credential Issuance
After a credential is issued, the issuer might need
to update or revoke the credential based on new in-
formation or changes in the user’s status. However,
Enhancing OpenID Connect for Verifiable Credentials with DIDComm
845

OIDC4VC does not inherently support any mecha-
nism for notifying end-users of such updates or re-
vocations. This gap can lead to scenarios where re-
voked or outdated credentials continue to be used er-
roneously or maliciously, compromising the security
and trust of the system.
4.2 Post-Credential Verification
Following the initial verification, there may be a need
for ongoing verification, especially in environments
requiring high levels of trust and security. OIDC4VC
typically concludes its role once a credential is veri-
fied, without facilitating further communications be-
tween the involved parties. This lack of ongoing in-
teraction can lead to inefficiencies and increased risk,
particularly when attributes or statuses represented by
the credentials are subject to change.
4.3 Engaging Credential Issuance or
Verification Through Notifications
The enhancement of OIDC4VC to incorporate DID-
Comm also opens up new avenues for initiating
credential issuance or verification processes directly
through notifications. This method could dramati-
cally streamline how interactions are triggered in dig-
ital identity systems.
Using DIDComm protocols, issuers and verifiers
can send push notifications to end-users for actions
that require immediate attention or participation. For
example, a credential issuer could send a notification
to a user’s device to initiate the issuance process of a
new or updated credential. Similarly, verifiers could
request re-verification of credentials through a simple
notification when necessary.
4.4 Marketing Communication Needs
Beyond the functional requirements of issuing and
verifying credentials, there is also a need for ongo-
ing marketing communication between the issuer or
verifier and the end-user. This can include notifica-
tions about new services, updates to terms of service,
or even promotional offers related to the credentials
held. Integrating marketing communication channels
into OIDC4VC could help maintain an active and en-
gaged user base, providing a direct line for issuers and
verifiers to communicate effectively and responsibly
with end-users.
4.5 Proposed Enhancements
To address these gaps, integrating continuous com-
munication channels into the OIDC4VC framework is
proposed. Utilizing technologies such as DIDComm,
could provide encrypted, peer-to-peer messaging ca-
pabilities that enable issuers to send updates or revo-
cation notices directly to end-users. Moreover, in-
corporating features like event listeners or webhook
functionalities within OIDC4VC could automate the
process of re-verification or status checks, ensuring
credentials remain valid and up-to-date.
These enhancements not only improve the secu-
rity and functionality of the credential management
system but also align with the decentralized, user-
controlled ethos of self-sovereign identities. By facil-
itating secure and continuous communication chan-
nels, OIDC4VC can evolve into a more dynamic
and responsive framework, capable of supporting the
complex needs of modern digital interactions.
5 PROPOSED SOLUTIONS TO
ENHANCE OpenID CONNECT
FOR VERIFIABLE
CREDENTIALS
This section outlines a proposed enhancement to
the OpenID Connect for Verifiable Credentials
(OIDC4VC) protocol. The modification is designed
to be lightweight and backward compatible, aimed at
enabling DIDComm-based communications once the
OIDC4VC flow has been completed. This enhance-
ment seeks to bridge the current gap in the protocol,
facilitating encrypted and secure post-verification in-
teractions between parties.
5.1 Novel Credential Exchange in
OIDC4VC for DIDComm via
Mediator
The mediator (Curren et al., 2024) plays a critical role
in the DIDComm protocol, serving as an intermediary
for secure communication between different parties,
especially crucial for mobile wallet applications. In
DIDComm, a mediator is responsible for ensuring re-
liable message delivery by facilitating encrypted com-
munication between wallet applications and issuers or
verifiers, even when direct peer-to-peer connections
are not possible. This section presents a novel ap-
proach to credential exchange within OIDC4VC, with
a specific focus on the mediator’s role in enabling se-
SECRYPT 2024 - 21st International Conference on Security and Cryptography
846

cure post-issuance and post-verification communica-
tion.
In the proposed approach, mediator information is
included in the final step of the OIDC4VC interaction,
allowing participants to engage in secure, encrypted
messaging following credential issuance or verifica-
tion. This approach aims to address the limitations of
current OIDC4VC implementations by introducing a
pathway for encrypted communication through DID-
Comm.
5.1.1 Issuance Flow
Figure 1 illustrates the interaction with a mediator and
the necessary steps with the issuer (changed or new
flows are marked in red):
• Steps 1-6: This represents the typical credential
issuance process within OIDC4VC.
• Steps 7-8: This step involves obtaining mediator
information, also known as a ”connection invita-
tion,” from the mediator to establish a secure com-
munication channel.
• Step 9: The request for credential download is
modified to include the mediator’s data, marking a
divergence from the standard process. This mod-
ification ensures that the subsequent flow has all
necessary data for DIDComm connection.
• Step 10: The final step is a standard credential
download, similar to the original issuance flow.
• Step 11: Establishment DIDComm connection
with mediator
These steps demonstrate how mediator informa-
tion is integrated into the OIDC4VC credential is-
suance flow, providing a bridge for secure communi-
cation and enabling DIDComm-based encrypted mes-
saging in a reliable and efficient manner. This ap-
proach ensures that if direct connections are not pos-
sible, communication can continue through the medi-
ator, enhancing the resilience of the entire process.
5.1.2 Verification Flow
Figure 2 illustrates the flow diagram of interactions in
the verification process (in red changed or new flows),
including steps that involve the mediator:
• Steps 1-2, 5: This portion follows the standard
steps outlined in the OIDC4VP specification for
verifiable presentations.
• Steps 3-4: These steps include obtaining mediator
information, known as a ”connection invitation,”
to establish a secure communication channel for
DIDComm-based encrypted messaging.
• Step 6: This response not only carries all the stan-
dard authorization data but also includes crucial
mediator information, thereby enabling the estab-
lishment of a DIDComm connection in next step.
• Step 7: The final step involves creating a DID-
Comm connection with the mediator, ensuring re-
liable and secure communication.
5.1.3 Header-Based Mediation Data
Transmission
A crucial aspect of this approach is the addition of an
”X-Mediation” header in the HTTP response during
the final interaction between the issuer/verifier and
the wallet. This header contains base64-encoded me-
diator data for the connection, indicating where and
how encrypted messages should be directed for fur-
ther communication via DIDComm.
• Header Name: ”X-Mediation”
• Header Value: Base64-encoded mediator data
• Purpose: To inform the wallet which media-
tor service to use and how it should be used for
DIDComm-based communication.
This header enables issuers, verifiers, and wallet
applications to establish secure communication path-
ways with a designated mediator. Despite these en-
hancements, the approach remains backward compat-
ible, ensuring issuers, verifiers or wallets not imple-
menting the new flow can continue operating without
disruptions or compatibility issues.
6 IMPLEMENTATION
OVERVIEW
While this paper is not focused on the implementa-
tion, it is essential to outline the primary considera-
tions for integrating DIDComm into OpenID Connect
for Verifiable Credentials (OIDC4VC). This section
provides a high-level overview of the components and
steps required to achieve this integration.
6.1 DIDComm and Mediator
Integration
DIDComm and mediator services are available in
multiple programming languages (Aries Mediator
Service, 2024) (Purik Pavel Minenkov, 2024), of-
fering flexibility when integrating with existing
OIDC4VC systems. Libraries implementing DID-
Comm (Identity, 2024) must be added on both the
wallet and the issuer/verifier sides to support secure
communication.
Enhancing OpenID Connect for Verifiable Credentials with DIDComm
847
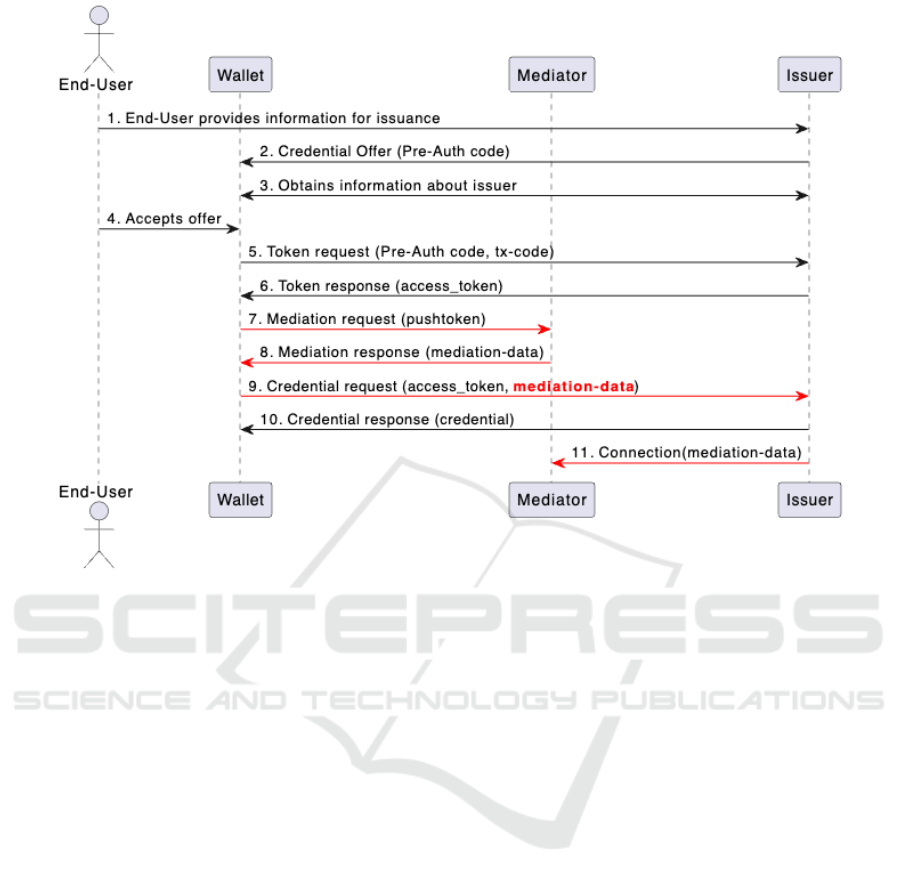
Figure 1: Novel issuance flow.
6.2 Integration with Push Systems
For mobile wallets, integrating with push notifica-
tion services like Firebase Cloud Messaging (FCM)
(Google, 2024) and Apple Notification Services
(APNs) (Apple, 2024) is essential to ensure reliable
communication. These services enable seamless mes-
sage delivery to mobile devices, even when the appli-
cation isn’t actively running.
• Firebase Cloud Messaging (FCM): A cross-
platform messaging solution that allows sending
messages and notifications to Android and iOS
devices. FCM provides a secure and scalable
way to deliver push notifications, supporting both
HTTP and WebSocket interfaces.
• Apple Notification Services (APNs): The push
notification service for iOS devices. APNs fa-
cilitates the delivery of notifications from your
server to iOS devices, requiring a secure setup
with proper authentication keys.
6.3 Modification of OIDC4VC Flow
Adding DIDComm support to OIDC4VC involves in-
cluding an ”X-Mediation” header in the HTTP re-
sponse during the last interaction between the is-
suer/verifier and the wallet.
Issuers or verifiers must implement business logic
to determine which data receive through this header,
while ensuring backward compatibility with systems
that do not support the new flow. Although this re-
quires some additional work, it does not disrupt exist-
ing operations, allowing wallets who don’t implement
DIDComm to continue using standard OIDC4VC
flows.
7 CONCLUSIONS
This paper proposes an enhancement to OIDC4VC
by integrating DIDComm to address its communi-
cation limitations post-credential issuance and veri-
fication. Introducing an ”X-Mediation” header en-
ables encrypted mediator-based communication, en-
suring secure message exchange while maintaining
backward compatibility.
The implementation requires integrating DID-
Comm mediators and push notification services like
Firebase Cloud Messaging (FCM) and Apple Noti-
fication Services (APNs) for reliable mobile wallet
communication. DIDComm library integration on
both wallet and issuer/verifier sides is essential for a
standardized approach.
Despite added complexity, these enhancements
SECRYPT 2024 - 21st International Conference on Security and Cryptography
848
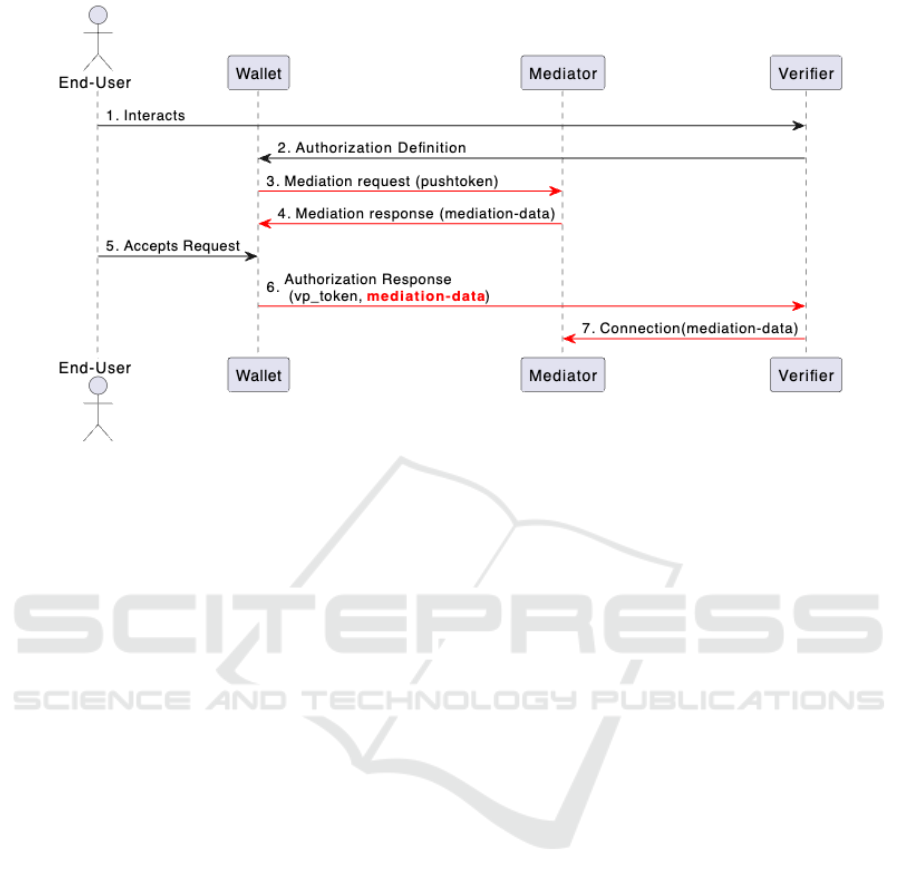
Figure 2: Novel verification flow.
significantly improve the robustness and flexibility of
digital identity systems, aligning with the decentral-
ized ethos of Self-Sovereign Identity (SSI). This ap-
proach encourages broader adoption of verifiable cre-
dentials and enhances the security and efficiency of
digital identity management.
Future work should explore additional DIDComm
use cases, address interoperability challenges, and de-
velop best practices for seamless adoption across plat-
forms.
ACKNOWLEDGEMENTS
This work was partially supported by project SER-
ICS (PE00000014) under the NRRP MUR program
funded by the EU-NGEU.
REFERENCES
Apple (2024, Accessed: 2024). User notifications. Frame-
work for pushing user-facing notifications to devices.
Aries Mediator Service (2024, Accessed: 2024). Github:
Aries mediator service.
Curren, S., Looker, T., and Terbu, O. (2024, Accessed:
2024). Didcomm messaging v2.x editor’s draft. Spec-
ification Status: DIF Ratified Specification.
Google (2024 Accessed: 2024). Firebase cloud messaging.
Cross-platform messaging solution.
Hardt, D., Parecki, A., and Lodderstedt, T. (2023 Accessed:
2024). The oauth 2.1 authorization framework.
Identity, D. (2024, Accessed 2024). Github: didcomm-
messaging. Repository for DIDComm Messaging
specifications and reference code.
Indy, H. (2024, Accessed: 2024). Hyperledger indy.
Lodderstedt, T., Yasuda, K., and Looker, T. (2024, Ac-
cessed: 2024). Openid for verifiable credentials -
specifications.
Lux, Z., Thatmann, D., Zickau, S., and Beierle, F. (2020).
Distributed-ledger-based authentication with decen-
tralized identifiers and verifiable credentials. 2020
2nd Conference on Blockchain Research & Applica-
tions for Innovative Networks and Services (BRAINS),
pages 71–78.
OpenID Foundation (2024 Accessed: 2024). What is
openid connect.
Purik Pavel Minenkov, S.-s. S. (2024, Accessed 2024).
Github: didcomm-mediator.
Sam Curren (Indicio), Tobias Looker (Mattr), O. T. C. (2020
Accessed: 2024). Didcomm messaging specifica-
tion. Specification document for DIDComm messag-
ing protocol.
Sporny, M., Longley, D., Sabadello, M., Reed, D., Steele,
O., and Allen, C. (2022 Accessed: 2024). Decentral-
ized identifiers (dids) v1.0. W3C Recommendation.
Wikipedia contributors (2024 Accessed: 2024). Self-
sovereign identity.
Enhancing OpenID Connect for Verifiable Credentials with DIDComm
849
