
Computing: Looking Back and Moving Forward
Muhammed Golec
a
and Sukhpal Singh Gill
b
School of Electronic Engineering and Computer Science, Queen Mary University of London, London, U.K.
{m.golec, s.s.gill}@qmul.ac.uk
Keywords:
Modern Computing, Cloud Computing, Fog Computing, Edge Computing, Serverless Computing, Quantum
Computing.
Abstract:
The Internet and computer commercialization have transformed the computing systems area over the past sixty
years, affecting society. Computer systems have evolved to meet diverse social needs thanks to technological
advances. The Internet of Things (IoT), cloud computing, fog computing, edge computing, and other emerg-
ing paradigms provide new economic and creative potential. Therefore, this article explores and evaluates
the elements impacting the advancement of computing platforms, including both long-standing systems and
frameworks and more recent innovations like cloud computing, quantum technology, and edge AI. In this arti-
cle, we examine computing paradigms, domains, and next-generation computing systems to better understand
the past, present, and future of computing technologies. This paper provides readers with a comprehensive
overview of developments in computing technologies and highlights promising research gaps for the advance-
ment of future computing systems.
1 INTRODUCTION
Revolutionary developments such as the discovery
of fire, the invention of writing, and the printing
press have shaped human history. One of these de-
velopments is computing technologies, which find a
place in almost every field today (Gill et al., 2024b).
Finance, where daily transactions are carried out,
healthcare, where patient records are kept and anal-
yses are performed, and social media areas can be
given as some examples (Golec et al., 2021). One of
the revolutionary developments in information tech-
nology is Artificial Intelligence (AI), which can think
like a human and perform certain tasks for now. Be-
cause it can be applied to many fields, it has the ad-
vantage of being faster and more effective than hu-
mans in solving complex problems (Iftikhar et al.,
2023). It is thought that if AI is integrated with quan-
tum computing, another technologically revolution-
ary development, it can increase the quality of life for
humanity in many areas (Gill et al., 2024a).
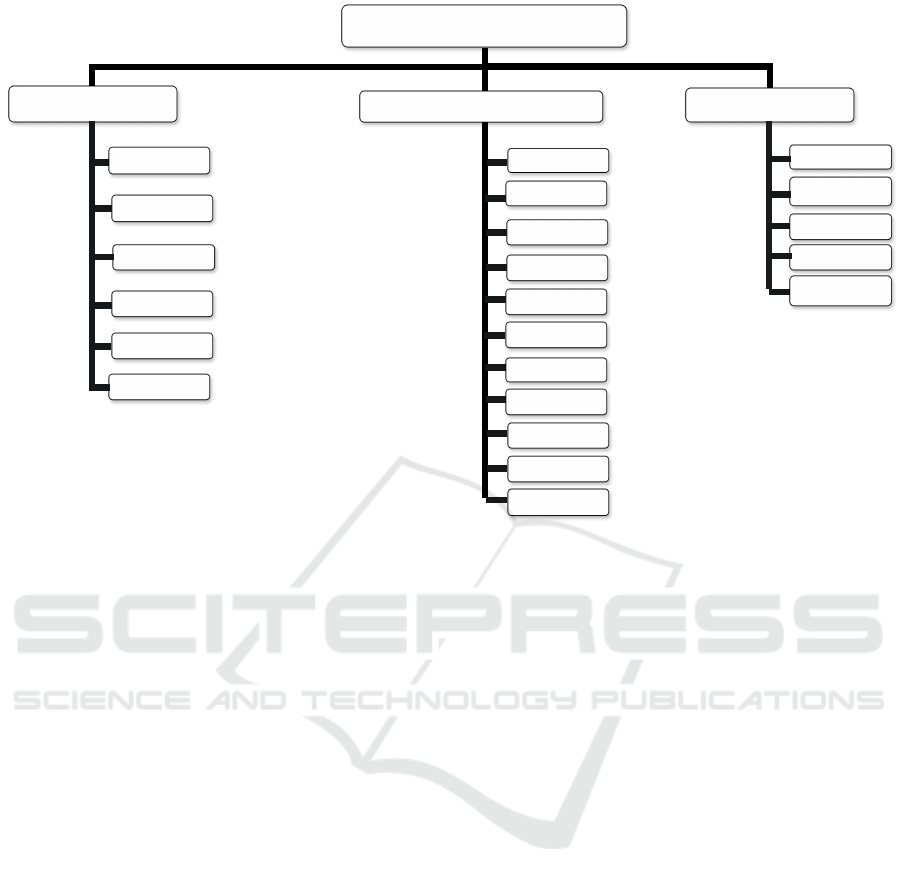
This article gives readers a general perspective
by examining the developments in the computing
paradigm from the past to the present, current tech-
nology applications, trends, and challenges, and next-
generation computing concepts. Figure 1 shows an
a
https://orcid.org/0000-0003-0146-9735
b
https://orcid.org/0000-0002-3913-0369
overview of the advancements in computing systems
and technologies. First, existing technologies and do-
mains such as Internet of Things (IoT), Blockchain,
and quantum computing are examined. We then dis-
cuss how these technologies shape computing. In the
last part, we will examine new generation computing
trends and challenges, such as Industry 4.0 and Quan-
tum Internet, which are the future of computing.
2 COMPUTING PARADIGMS
In this section, we examine the main paradigms to
better explain the evolution in computing technology.
2.1 Grid Computing
To complete complicated activities or find solutions
to big issues, grid computing is a distributed comput-
ing paradigm that permits the sharing and coordinated
use of the same networked computing resources (Gill
et al., 2024b). Many different fields, such as weather
forecasting and the financial industry, utilize it for
quick fixes like risk assessments and the examination
of massive volumes of data. Several benefits of this
paradigm have drawn the interest of both academic
and private-sector researchers, including the follow-
ing (Jacob et al., 2005):
Golec, M. and Gill, S.
Computing: Looking Back and Moving Forward.
DOI: 10.5220/0012855200003764
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Smart Business Technologies (ICSBT 2024), pages 7-14
ISBN: 978-989-758-710-8; ISSN: 2184-772X
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
7
COMPUTING SYSTEMS
PARADIGMS
Cloud Computing
Fog Computing
Edge Computing
Serverless Computing
Quantum Computing
TECHNOLOGIES AND IMPACT AREAS
NEW TRENDS
IoT
Autoscaling
Virtualization
Fault Tolerance
Energy Efficiency
Security and Privacy
AI-driven Computing
Large Scale Machine
Learning
Edge AI
Industry 4.0
Quantum Internet
Grid Computing
Microservices
Software-defined
Networks
Blockchain
Federated Learning
QoS and SLA
Figure 1: The Overview of Advancements in Computing Systems and Technologies.
• The Ability to Scale: Resources can be adjusted in
size to meet shifting demands and workloads.
• The Use of Resources: Distributed resources are
pooled to enhance resource utilization, which
lowers the free capacity to maintain optimal ef-
ficiency.
• The Economy of Cost: Using available resources,
we can solve tasks requiring a lot of computing
at a low cost, eliminating the need for specialized
infrastructure.
In addition to these advantages, it still brings chal-
lenges that need to be solved, such as risks to security,
complexity, and variability in performance.
2.2 Cloud Computing
In contrast to traditional computing systems, Infor-
mation Technology (IT) based this paradigm allows
computing resources to be pooled and made avail-
able over the Internet, and transactions to take place
on distant servers (Golec et al., 2023d). Many do-
mains of civil and commercial applications, including
web and enterprise applications, have widely adopted
cloud computing. Users can benefit in a number of
ways, including (i) cost savings through a reduction
in hardware and infrastructure expenses, (ii) resource
scalability to adapt to variations in demand, and (iii)
access from any location with Internet access (Mu-
rugesan et al., 2024). However, it also presents draw-
backs such as resource management, privacy, and se-
curity issues that require attention.
Three main categories typically classify different
cloud delivery models, which offer consumers vary-
ing degrees of service (Golec et al., 2023a):
• IaaS (Infrastructure as a Service): In this ser-
vice model, consumers rent cloud service provider
(CSP) resources such as virtual machines and
storage. CSPs are responsible for the server’s in-
frastructure operations, while users are only re-
sponsible for infrastructure management.
• PaaS (Platform as a Service): It’s a service
paradigm that keeps customers away from in-
frastructure management so they may concentrate
solely on developing applications. A PaaS ap-
proach gives users access to the required devel-
opment environments and software tools.
• FaaS (Function as a Service): This completely
isolates users from infrastructure and service ad-
ministration. This relieves users of all infrastruc-
ture management responsibilities and allows them
to concentrate entirely on developing code. Un-
der this service paradigm, users upload single-
function bits of code to the platform using an
event-driven architecture.
ICSBT 2024 - 21st International Conference on Smart Business Technologies
8

2.3 Fog Computing
With the increase in IoT-based applications, the
amount of data that needs to be processed has reached
gigantic proportions. Research shows that there will
be 24 billion enterprise IoT connections by 2030
(Vailshery, 2024). When cloud systems utilize re-
mote servers, an increase in data processing leads
to a decrease in Quality of Service (QoS) parame-
ters like latency (Golec et al., 2023c). Fog comput-
ing is emerging as an alternative to cloud computing
to solve this problem. Fog computing expedites re-
sponse times by situating data processing and stor-
age near the data generation sources (Iftikhar et al.,
2022b). Time-sensitive applications and Industrial In-
ternet of Things (IIoT), which process large amounts
of data, benefit greatly from this approach. While
it offers users benefits like reduced latency and en-
hanced security by bringing processing power closer
to the data source, it also presents challenges like re-
source constraints and compatibility issues due to the
use of heterogeneous and distributed devices.
2.4 Edge Computing
The concept of edge computing emerged to solve
problems such as bandwidth and latency in solutions
such as cloud computing, where processing power
and storage move away from the data source (Nand-
hakumar et al., 2024). For this reason, edge devices
such as sensors and smartphones are positioned close
to data sources. Today, it has wide usage areas such as
IIoT and time-sensitive healthcare applications (Walia
et al., 2024). Edge computing provides advantages
such as (i) Reducing latency by moving the process-
ing power closer to the data source, (ii) Reducing un-
necessary bandwidth usage because it only transmits
data that requires high processing power to the cloud,
and (iii) Providing data security because it processes
the data locally (Iftikhar et al., 2022a). In addition
to these advantages, it brings challenges such as re-
source management, security and privacy, and coor-
dinated work arising from the distributed architecture
of IoT, which are still waiting to be solved.
The reasons and goals of Fog computing and Edge
computing are very similar. For this reason, the two
concepts are often confused. When both IT models
are examined carefully, it is seen that they differ from
each other as follows (Buyya and Srirama, 2019):
• Although both computing models aim to reduce
latency and unnecessary bandwidth usage, the
main difference between them is related to where
data is processed and stored. In fog computing,
data processing locations are closer to the data
source than in cloud, but further away than in edge
computing. Examples are gateways and city data
centers. In edge computing, the place of data pro-
cessing is usually IoT and mobile devices where
data is produced.
• Fog computing is often used in large-scale sys-
tems such as IIoT, where data processing and stor-
age are handled at a middleware. Edge computing
has a more distributed approach.
2.5 Serverless Computing
Cloud computing has introduced delivery models
with various advantages since the day it was first in-
troduced. More information about these models is
given in Section 2.2. One of these delivery models is
Serverless computing, which isolates server mainte-
nance and infrastructure management from customers
and combines Backend as a Service (BaaS) and Func-
tion as a Service (FaaS) services (Golec et al., 2023d).
In this way, customers can focus only on code de-
velopment by being isolated from all infrastructure
management processes. Serverless computing first
emerged in 2014 when Amazon Web Services intro-
duced the Lambda model. This service model uses an
event-driven architecture and code developers write
their codes as functions. Today, serverless-based ap-
plications are used in a wide variety of fields such as
finance and education.
It has the following advantages over traditional
cloud service models (such as IaaS, and PaaS) (Golec
et al., 2021):
• The pay-as-you-go pricing model charges only ac-
cording to the time resources are used,
• The auto-scalability feature allows for the dy-
namic increase or decrease of computing re-
sources in response to an increasing number of
requests,
• Ease of management, complete isolation of infras-
tructure operations from customers.
In addition to all these advantages, studies con-
tinue in the academy and private sector to solve chal-
lenges such as cold start latency, security and privacy,
and monitoring and debugging.
2.6 Quantum Computing
It is a computing paradigm in quantum physics that
works based on the principle of using particles in su-
perposition, called qubits and has recently attracted
attention in academia (Gill et al., 2024a). It has the
potential to solve problems that require a long time
Computing: Looking Back and Moving Forward
9

to be solved in a very short time compared to classi-
cal computers where all operations are processed with
binary bit (0 and 1) logic (Gill et al., 2022a). For this
reason, it can be used in complex areas such as Cryp-
tography, AI, and Molecular Biology that require high
processing power.
Quantum computers have advantages over clas-
sical computers such as parallel processing ability,
quantum superposition, and quantum teleportation.
Thanks to these advantages, it provides advantages
such as high speed, parallel processing, and new al-
gorithm discoveries (Gill, 2024). On the other hand,
quantum computers are still in the research phase and
must overcome the challenges described below to be-
come widely available (O’brien, 2007):
• High Cost: Creating a more powerful quantum
computer is directly proportional to the number
of qubits to be added. However, adding qubits is
very costly.
• Quantum-Induced Challenges: Quantum comput-
ers, which operate on the principles of quantum
mechanics, involve sensitive processes such as en-
suring qubit stability and quantum errors. Due
to these technical difficulties, quantum computers
have not yet been produced on a large scale.
• Insulation and Cooling: Quantum stability and
Quantum errors are very quickly affected by envi-
ronmental factors such as heat and noise. There-
fore, insulation and cooling technologies must be
developed to provide these conditions.
3 COMPUTING TECHNOLOGIES
AND IMPACT AREAS
Computing technologies have made a huge impact in
various research fields and transformed the way of
working. Some of these areas are examined under
subheadings in this section.
3.1 QoS and SLA
Quality of Service (QoS) refers to metrics such as
latency, throughput and response rate used to show
the performance of an application or network ser-
vice. Service Level Agreement (SLA) is an agreement
made between a service/application and customers
that guarantees the quality and reliability of the ser-
vice. Computing technologies have various impacts
on QoS & SLA (Golec et al., 2023c).
• Security and Privacy: Computing technologies
support SLA with security methods to ensure the
security of applications and user privacy.
• Efficiency: Computing technologies can improve
QoS parameters with high-capacity processors
and infrastructure to increase the performance of
applications.
• Application Flexibility: Computing technologies
can make services/applications more flexible by
increasing resources to meet demand fluctuations.
3.2 IoT
All devices that can connect to the Internet and com-
municate data with each other are called IoT (Sen
and Yamin, 2021). It has many uses in civilian and
military areas, from smart home appliances to au-
tonomous vehicles. Computer technologies have a
very wide impact on IoT.
• Data Analytics: IoT devices analyze the data col-
lected through sensors and obtain valuable infor-
mation as a result of this analysis. For example, in
an IIoT scenario where production is monitored,
predictive maintenance can detect the engine that
will fail and thus prevent production disruption.
• Smart Health Applications: Patient monitoring
and disease diagnosis studies are carried out using
IoT devices and sensors. In this way, it is aimed
to prevent unnecessary health expenses and fatal
diseases through early and accurate diagnosis.
• Smart City Applications: Includes sustainable so-
lutions such as city infrastructure and energy man-
agement, such as traffic lights in cities and energy
optimization in homes.
3.3 Autoscaling
The concept of autoscaling refers to the automatic in-
crease or decrease of system resources to meet de-
mand fluctuations, which is frequently used in com-
puting technologies (Golec et al., 2023c). Generally,
it occurs when launching new instances during de-
mand fluctuations in order to meet SLAs in cloud ser-
vices. This is also necessary for resource and cost
optimization of applications and services.
3.4 Virtualization
It is a computing technology that allows the resources
in a system to be used efficiently and divided into dif-
ferent operating systems (Chiueh and Brook, 2005).
It is especially popular in IaaS-based delivery models
provided to users by major cloud providers.
ICSBT 2024 - 21st International Conference on Smart Business Technologies
10

3.5 Fault Tolerance
It refers to measures that can tolerate service interrup-
tions caused by errors that may occur in a system. It
includes backup processes called Redundant Array of
Independent Disks (RAID) in cloud systems to pre-
vent data loss due to interruptions that may occur in
the system (Plank, 1997; Chouikhi et al., 2015).
3.6 Energy Efficiency
It refers to a system performing the same work with
less energy. Values such as energy spent while per-
forming a task and CO
2
emissions are critical in re-
ducing environmental pollution (Golec et al., 2023a;
Feng et al., 2012). This has led to the proposal of new
technological advances such as green IoT and green
cloud computing.
3.7 Security and Privacy
Security and privacy are two of the most fundamen-
tal problems in IT systems. Security includes com-
prehensive issues such as unauthorized access to a
system and theft or modification of data in the sys-
tem. Privacy refers to all situations that may jeopar-
dize user privacy, such as biometric data (Golec et al.,
2022; De Guzman et al., 2019).
3.8 Microservices
It refers to a form of architecture designed to make
applications more flexible and easier to develop. Es-
sentially, it aims to divide and develop the applica-
tion into smaller and independent applications (Golec
et al., 2023d; Pallewatta et al., 2023). By dividing the
application into smaller services, advantages such as
debugging and the ability to use different technologies
for each scenario are provided.
3.9 Software-Defined Networks
Software-defined Networks (SDN) is a centralized
and software-oriented management approach to en-
sure more efficient management of resources in a net-
work (Fernandes et al., 2018). Computing technolo-
gies have various impacts on SDNs.
• Ease of Network Operation: SDN provides traffic
optimization and dynamic resource allocation to
increase the operational capability of the network
(Sarabia-J
´
acome et al., 2024).
• Network Scaling: SDN ensures the scalability of
the infrastructure to increase the efficiency of net-
work resources (Dhadhania et al., 2024).
• QoS and SLA Improvement: SDN provides opti-
mization in traffic management to improve QoS
and SLA in network applications (Wang et al.,
2016).
3.10 Blockchain
It is a computing technology that essentially consists
of interconnected blocks containing the hash of the
previous block and can be thought of as a digital
ledger (Golec et al., 2023b). The data in each block
is connected to each other with the hash value of the
previous block and a new hash value is obtained for
the next block. In this way, any change in any data
in the blocks affects all blocks, and data immutability
is ensured. Blockchain technologies are used in many
areas today (Doyle et al., 2022; Reyna et al., 2018):
• Financial Sector: Blockchain provides a decen-
tralized platform for digital assets such as cryp-
tocurrencies (Bitcoin etc.). This eliminates inter-
mediaries in buying and selling transactions, en-
suring safe transfers.
• Smart Contracts: These are contracts that are de-
centralized and kept on the blockchain network
(CR et al., 2024). As a result, all transactions
are public. In addition, trust and data security are
ensured between the parties by taking advantage
of the data immutability advantage provided by
Blockchain.
• Product Supply: Quality control is increased by
monitoring supply chains with blockchain-based
systems and fraud can be reduced with the prin-
ciple of data immutability (Wang et al., 2024). In
this way, confidence in supply chains and com-
mercial activities can be increased.
• Identity Authentication and Voting: With
blockchain-based voting systems, user privacy
is ensured by storing personal data securely
(Hossain Faruk et al., 2024). Additionally,
manipulations in elections held in countries can
be prevented.
3.11 Federated Learning
Federated Learning (FL) is a Machine Learning (ML)
technique used in distributed architectures (Li et al.,
2020). While in ML techniques a centralized system
is used for model training, in FL distributed devices
are used for model training. FL, a field of computing
technologies, has a variety of advantages (Mammen,
2021):
• Security and Privacy: Since a central system is
Computing: Looking Back and Moving Forward
11

not used when training FL models, data security
and user privacy risks are lessened.
• Fast Training: Model training is faster because
FL is trained in distributed systems close to data
sources.
• Accessibility: Since FL are trained in dis-
tributed systems, model training is also possible
in Internet-limited environments.
4 NEXT GENERATION
COMPUTING: CHALLENGES
AND NEW TRENDS
This section briefly discusses next-generation com-
puting paradigms, their challenges and new trends.
4.1 AI-Driven Computing
AI-driven computing is the integration of AI, ML,
and Natural Language Processing (NLP) models into
computer systems to process big data and produce so-
lutions for complex models (Firouzi et al., 2022). It
brings many advantages to the system into which it is
integrated (Gill et al., 2022b):
• Prediction Performance: It is important to ana-
lyze data in areas such as finance and health and
make predictions with high performance. AI-
driven computing increases prediction success
rates, resulting in a noticeable increase in risk as-
sessments.
• Cost and Efficiency: AI-driven computing can re-
duce costs and increase production efficiency by
preventing interruptions in production processes,
such as predictive maintenance scenarios.
• Opportunities: With its innovative solutions, AI-
driven computing has the potential to create new
business areas and expertise.
Apart from all these advantages, AI-driven com-
puting also includes challenges such as ethical issues
and new algorithms for optimization in complex op-
erations.
4.2 Large Scale Machine Learning
Traditional ML techniques trained on large datasets
have low model performance due to factors such
as hyperparameter setting, computational power, and
large features. As a result, it is necessary to use tech-
niques such as parallel computing for ML models in
large data sets. Large-scale machine learning methods
provide advantages such as improving prediction per-
formance and optimizing transaction cost and speed
(Wang et al., 2020). Besides these advantages, chal-
lenges such as feature selection and ensuring data in-
tegrity are still waiting to be investigated (Liu et al.,
2024).
4.3 Edge AI
AI-based applications are generally processed in cen-
tralized systems with high processing power. Edge AI
is an approach that proposes to process data close to
the data source, such as IoT and smartphones (Bibri
et al., 2024). This is because it provides advantages
such as lower latency, and security, and reduces un-
necessary bandwidth usage compared to centralized
systems such as the cloud (Singh and Gill, 2023). On
the other hand, Edge AI systems offer lower process-
ing power and storage space than cloud-based sys-
tems. Also, since it has a distributed architecture,
it also brings with it challenges such as the mainte-
nance and management of devices and resource man-
agement.
4.4 Industry 4.0
It is the use of new computing technologies such as AI
and IoT by integrating them into production processes
to make production more efficient and economical
(Teoh et al., 2021). Predictive maintenance is a good
example of an Industry 4.0 application. By using sen-
sors and ML models, errors are detected in advance
in predictive maintenance scenarios, and production
disruptions are prevented. Likewise, production op-
timization is achieved through data analysis methods
using data received from sensors. Thus, by enhancing
service quality, we can promptly respond to customer
demands. In addition to all these advantages, it should
not be forgotten that Industry 4.0 brings with it prob-
lems that still need to be solved, such as cost, cyber
security, and integration.
4.5 Quantum Internet
It is an Internet model that works with quantum prin-
ciples (Wehner et al., 2018). It is expected to replace
the classical Internet in the future with its higher se-
curity and speed. In the Quantum Internet, quantum
cryptography is used to ensure security in communi-
cation protocols. Compared to the classical Internet,
much faster communication speeds are achieved with
quantum teleportation techniques. In addition to all
these advantages, quantum computing, and the quan-
tum Internet are still in the research phase. And its
ICSBT 2024 - 21st International Conference on Smart Business Technologies
12

integration for long-distance communications is still
a challenge (Li et al., 2024).
5 CONCLUSIONS
Computing technologies continue to shape human
history with the transformations they offer from the
past to the present. This effect can be seen every-
where, from healthcare applications like early diag-
nosis and medical imaging to military vehicles like
unmanned planes. Additionally, technologies such as
IoT and AI continue to trend with the opportunities
they offer in various industries and processes. Quan-
tum technologies, one of the next-generation devel-
opments in computing and still in their infancy, have
recently attracted attention for their potential to shape
the future. However, embracing these next-generation
trends and dealing with their challenges will require
separate efforts. In this paper, we take an overview
of computing technologies from the past to the future
and highlight challenges for researchers.
ACKNOWLEDGEMENTS
Muhammed Golec would express his thanks to the
Ministry of Education of the Turkish Republic, for
their support and funding.
REFERENCES
Bibri, S. E., Krogstie, J., Kaboli, A., and Alahi, A. (2024).
Smarter eco-cities and their leading-edge artificial in-
telligence of things solutions for environmental sus-
tainability: A comprehensive systematic review. En-
vironmental Science and Ecotechnology, 19:100330.
Buyya, R. and Srirama, S. N. (2019). Fog and edge comput-
ing: principles and paradigms. John Wiley & Sons.
Chiueh, S. N. T.-c. and Brook, S. (2005). A survey on vir-
tualization technologies. Rpe Report, 142.
Chouikhi, S., El Korbi, I., Ghamri-Doudane, Y., and
Saidane, L. A. (2015). A survey on fault tolerance in
small and large scale wireless sensor networks. Com-
puter Communications, 69:22–37.
CR, A., Pani, A. K., and Kumar, P. (2024). Blockchain-
enabled smart contracts and the internet of things: Ad-
vancing the research agenda through a narrative re-
view. Multimedia Tools and Applications, pages 1–51.
De Guzman, J. A., Thilakarathna, K., and Seneviratne, A.
(2019). Security and privacy approaches in mixed re-
ality: A literature survey. ACM Computing Surveys
(CSUR), 52(6):1–37.
Dhadhania, A., Bhatia, J., Mehta, R., Tanwar, S., Sharma,
R., and Verma, A. (2024). Unleashing the power of
sdn and gnn for network anomaly detection: State-of-
the-art, challenges, and future directions. Security and
Privacy, 7(1):e337.
Doyle, J., Golec, M., and Gill, S. S. (2022). Blockchainbus:
A lightweight framework for secure virtual machine
migration in cloud federations using blockchain. Se-
curity and Privacy, 5(2):e197.
Feng, D., Jiang, C., Lim, G., Cimini, L. J., Feng, G., and
Li, G. Y. (2012). A survey of energy-efficient wireless
communications. IEEE Communications Surveys &
Tutorials, 15(1):167–178.
Fernandes, E. L., Antichi, G., Castro, I., and Uhlig, S.
(2018). An sdn-inspired model for faster network
experimentation. In Proceedings of the 2018 ACM
SIGSIM Conference on Principles of Advanced Dis-
crete Simulation, pages 29–32.
Firouzi, F., Farahani, B., and Marin
ˇ
sek, A. (2022). The con-
vergence and interplay of edge, fog, and cloud in the
ai-driven internet of things (iot). Information Systems,
107:101840.
Gill, S. S. (2024). Quantum and blockchain based server-
less edge computing: A vision, model, new trends
and future directions. Internet Technology Letters,
7(1):e275.
Gill, S. S. et al. (2024a). Quantum computing: Vision and
challenges. arXiv preprint arXiv:2403.02240.
Gill, S. S., Kumar, A., Singh, H., Singh, M., Kaur, K., Us-
man, M., and Buyya, R. (2022a). Quantum comput-
ing: A taxonomy, systematic review and future direc-
tions. Software: Practice and Experience, 52(1):66–
114.
Gill, S. S., Wu, H., Patros, P., Ottaviani, C., Arora, P., Pu-
jol, V. C., Haunschild, D., Parlikad, A. K., Cetinkaya,
O., Lutfiyya, H., et al. (2024b). Modern computing:
Vision and challenges. Telematics and Informatics Re-
ports, page 100116.
Gill, S. S., Xu, M., Ottaviani, C., Patros, P., Bahsoon, R.,
Shaghaghi, A., Golec, M., Stankovski, V., Wu, H.,
Abraham, A., et al. (2022b). Ai for next generation
computing: Emerging trends and future directions. In-
ternet of Things, 19:100514.
Golec, M., Chowdhury, D., Jaglan, S., Gill, S. S., and Uh-
lig, S. (2022). Aiblock: Blockchain based lightweight
framework for serverless computing using ai. In
2022 22nd IEEE International Symposium on Clus-
ter, Cloud and Internet Computing (CCGrid), pages
886–892. IEEE.
Golec, M., Gill, S. S., Cuadrado, F., Parlikad, A. K., Xu,
M., Wu, H., and Uhlig, S. (2023a). Atom: Ai-powered
sustainable resource management for serverless edge
computing environments. IEEE Transactions on Sus-
tainable Computing.
Golec, M., Gill, S. S., Golec, M., Xu, M., Ghosh, S. K.,
Kanhere, S. S., Rana, O., and Uhlig, S. (2023b).
Blockfaas: Blockchain-enabled serverless computing
framework for ai-driven iot healthcare applications.
Journal of Grid Computing, 21(4):63.
Computing: Looking Back and Moving Forward
13

Golec, M., Iftikhar, S., Prabhakaran, P., Gill, S. S., and Uh-
lig, S. (2023c). Qos analysis for serverless comput-
ing using machine learning. In Serverless Computing:
Principles and Paradigms, pages 175–192. Springer.
Golec, M., Ozturac, R., Pooranian, Z., Gill, S. S., and
Buyya, R. (2021). Ifaasbus: A security-and privacy-
based lightweight framework for serverless comput-
ing using iot and machine learning. IEEE Transac-
tions on Industrial Informatics, 18(5):3522–3529.
Golec, M., Walia, G. K., Kumar, M., Cuadrado, F.,
Gill, S. S., and Uhlig, S. (2023d). Cold start la-
tency in serverless computing: A systematic review,
taxonomy, and future directions. arXiv preprint
arXiv:2310.08437.
Hossain Faruk, M. J., Alam, F., Islam, M., and Rahman,
A. (2024). Transforming online voting: a novel sys-
tem utilizing blockchain and biometric verification for
enhanced security, privacy, and transparency. Cluster
Computing, pages 1–20.
Iftikhar, S., Gill, S. S., Song, C., Xu, M., Aslanpour, M. S.,
Toosi, A. N., Du, J., Wu, H., Ghosh, S., Chowdhury,
D., et al. (2023). Ai-based fog and edge computing:
A systematic review, taxonomy and future directions.
Internet of Things, 21:100674.
Iftikhar, S., Golec, M., Chowdhury, D., Gill, S. S., and Uh-
lig, S. (2022a). Fogdlearner: A deep learning-based
cardiac health diagnosis framework using fog comput-
ing. In Proceedings of the 2022 Australasian Com-
puter Science Week, pages 136–144. ACM.
Iftikhar, S., Raj, U., Tuli, S., Golec, M., Chowd-
hury, D., Gill, S. S., and Uhlig, S. (2022b).
Tesco: Multiple simulations based ai-augmented
fog computing for qos optimization. In 2022
IEEE Smartworld, Ubiquitous Intelligence &
Computing, Scalable Computing & Communica-
tions, Digital Twin, Privacy Computing, Meta-
verse, Autonomous & Trusted Vehicles (Smart-
World/UIC/ScalCom/DigitalTwin/PriComp/Meta),
pages 2092–2099. IEEE.
Jacob, B., Brown, M., Fukui, K., Trivedi, N., et al. (2005).
Introduction to grid computing. IBM redbooks, pages
3–6.
Li, L., Fan, Y., Tse, M., and Lin, K.-Y. (2020). A review
of applications in federated learning. Computers &
Industrial Engineering, 149:106854.
Li, Y., Zhang, H., Zhang, C., Huang, T., and Yu, F. R.
(2024). A survey of quantum internet protocols from
a layered perspective. IEEE Communications Surveys
& Tutorials.
Liu, J., Liu, M., Liu, J.-P., Ye, Z., Wang, Y., Alexeev, Y.,
Eisert, J., and Jiang, L. (2024). Towards provably
efficient quantum algorithms for large-scale machine-
learning models. Nature Communications, 15(1):434.
Mammen, P. M. (2021). Federated learning: Opportunities
and challenges. arXiv preprint arXiv:2101.05428.
Murugesan, S. S., Velu, S., Golec, M., Wu, H., and Gill,
S. S. (2024). Neural networks based smart e-health
application for the prediction of tuberculosis using
serverless computing. IEEE Journal of Biomedical
and Health Informatics.
Nandhakumar, A. R., Baranwal, A., Choudhary, P., Golec,
M., and Gill, S. S. (2024). Edgeaisim: A toolkit
for simulation and modelling of ai models in edge
computing environments. Measurement: Sensors,
31:100939.
O’brien, J. L. (2007). Optical quantum computing. Science,
318(5856):1567–1570.
Pallewatta, S., Kostakos, V., and Buyya, R. (2023). Place-
ment of microservices-based iot applications in fog
computing: A taxonomy and future directions. ACM
Computing Surveys, 55(14s):1–43.
Plank, J. S. (1997). A tutorial on reed–solomon coding for
fault-tolerance in raid-like systems. Software: Prac-
tice and Experience, 27(9):995–1012.
Reyna, A., Mart
´
ın, C., Chen, J., Soler, E., and D
´
ıaz, M.
(2018). On blockchain and its integration with iot.
challenges and opportunities. Future generation com-
puter systems, 88:173–190.
Sarabia-J
´
acome, D., Gim
´
enez-Ant
´
on, S., Liatifis, A., Grasa,
E., Catal
´
an, M., and Pliatsios, D. (2024). Progressive
adoption of rina in iot networks: Enhancing scalability
and network management via sdn integration. Applied
Sciences, 14(6):2300.
Sen, A. A. A. and Yamin, M. (2021). Advantages of us-
ing fog in iot applications. International Journal of
Information Technology, 13:829–837.
Singh, R. and Gill, S. S. (2023). Edge ai: a survey. Internet
of Things and Cyber-Physical Systems, 3:71–92.
Teoh, Y. K., Gill, S. S., and Parlikad, A. K. (2021). Iot and
fog-computing-based predictive maintenance model
for effective asset management in industry 4.0 using
machine learning. IEEE Internet of Things Journal,
10(3):2087–2094.
Vailshery, L. S. (2024). Global iot connections 2030, by
application.
Walia, G. K., Kumar, M., and Gill, S. S. (2024). Ai-
empowered fog/edge resource management for iot ap-
plications: A comprehensive review, research chal-
lenges, and future perspectives. IEEE Communica-
tions Surveys & Tutorials, 26(1):619–669.
Wang, D., Ding, H., Yang, Y., Mi, Z., Liu, L., and Xiong, Z.
(2016). Qos and sla aware web service composition
in cloud environment. KSII Transactions on Internet
and Information Systems (TIIS), 10(12):5231–5248.
Wang, M., Fu, W., He, X., Hao, S., and Wu, X. (2020).
A survey on large-scale machine learning. IEEE
Transactions on Knowledge and Data Engineering,
34(6):2574–2594.
Wang, Y., Gao, J., Cheng, T., Gong, Y., and Wu, T.-H.
(2024). Does blockchain technology need to be intro-
duced in the closed-loop supply chain based on prod-
uct lifecycle management? Computers & Industrial
Engineering, 188:109881.
Wehner, S., Elkouss, D., and Hanson, R. (2018). Quan-
tum internet: A vision for the road ahead. Science,
362(6412):eaam9288.
ICSBT 2024 - 21st International Conference on Smart Business Technologies
14
