
A Systematic Review to Identify Patterns Types and Analysis
Objectives for the Discovery of Business Rules from Event Logs Using
Machine Learning
Menna Wael
a
and Gamal Kassem
b
Department of Business Informatics, German University in Cairo, Cairo, Egypt
Keywords: Business Process, Event Log, Machine Learning, Systematic Literature Review, Business Rules.
Abstract: Business processes are structured and executed based on business rules. Information systems executing the
business processes store the execution data in event logs. The event logs can be analyzed using machine
learning algorithms to discover business rules in the business process execution. In which various algorithms
can be applied to event log data to discover rules/patterns related to the business process. The application of
machine learning on event log data to discover the business rules needs extensive process mining expertise
and knowledge from the process analyst; therefore, there is a need to facilitate the application of machine
learning on event log data to reach different analysis objectives. This can be done through identifying the
pattern types related to performing different machine learning tasks on event log data, and the different
analysis objectives for the discovery of business rules from event logs. However, it was found that no
systematic review was previously conducted to collect this information; therefore, the focus of this paper is
to conduct a systematic review to collect from research the different pattern/rule types within the event log
data that can be discovered and the different analysis objectives for the discovery of business rules from event
logs.
1 INTRODUCTION
Business processes are events and activities that are
performed to achieve business objectives. Business
process execution is recorded through event logs,
which are stored in information systems that support
the execution of the business processes. An event log
is composed of cases; each case consists of a number
of events that are performed as part of a case. The
business process consists of a collection of events and
cases. Furthermore, business processes are structured,
modelled, and executed based on business rules (Berti
& van der Aalst, 2023). Business rules from a
business process perspective are statements or
constraints that describe the business process
behavior (Graml et al., 2007; Campos et al., 2018).
They are incorporated in different patterns within
process data (Thi et al., 2011)
Business rules discovery is important. The
extracted rules or patterns support reaching
a
https://orcid.org/0009-0005-2250-0078
b
https://orcid.org/0009-0001-7617-5849
organizational goals, eliminating costly mistakes,
improving data-driven decision-making, performing
business process re-engineering, and checking the
compliance of the business process with legal
requirements (Polpinij et al., 2015). Mining of rules
from the business process event logs facilitates
understanding the process analysis results, as it shows
the results of the analysis as declarative business
statements. Moreover, By discovering the business
rules, it is possible to reach different process-related
analysis objectives (Bemthuis et al., 2023). The
discovery can be done through process mining
techniques. Process mining techniques analyze event
logs to perform tasks such as process discovery,
conformance checking, or process enhancement. In
addition, business rules can be discovered through
machine learning techniques, in which several
machine learning algorithms can be applied to event
logs to discover patterns or rules within event log data
(Polppinij et al., 2015; Polpinij et al., 2010). Rule
learning and rule mining are both machine learning
Wael, M. and Kassem, G.
A Systematic Review to Identify Patterns Types and Analysis Objectives for the Discovery of Business Rules from Event Logs Using Machine Learning.
DOI: 10.5220/0012857700003764
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Smart Business Technologies (ICSBT 2024), pages 131-138
ISBN: 978-989-758-710-8; ISSN: 2184-772X
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
131

techniques that are used to discover business rules
from event logs (Bozorgi et al., 2020).
Business rules may not be followed or may be in
the form of tacit knowledge. Consequently, discovery
of business rules using machine learning is important
to reveal hidden business logic (Bemthuis et al.,
2023). Moreover, Business rules discovered through
the application of machine learning algorithms are
related to different pattern types, in which each
pattern type is the result of performing different
machine learning tasks on the data (Polppinij et al.,
2015; Corea & Delfmann, 2020; Nelson and Sen,
2014; Swinnen et al., 2011; Polpinij et al., 2010).
Furthermore, the work of the process analyst to
analyze the event log data to reach different process-
related analysis objectives is not easy and
straightforward. As it requires the process analyst to
have massive process mining and machine learning
expertise and knowledge. Therefore, there is a need
to provide the process analyst with information that
would help perform process-mining tasks using
machine learning techniques. This information would
facilitate the process of analyzing event logs using
machine learning (Seeliger, 2020).
Since machine learning can be used to reach
different pattern/rule types, it is important to identify
the types of patterns and the analysis objectives that
can be discovered from event logs by performing
different machine learning tasks. This information
can facilitate utilizing machine learning algorithms to
reach process-related analysis objectives (Chen et al.,
2023).
2 RELATED WORK
One systematic review conducted by Chen et al.,
(2023) investigated the application of machine
learning algorithms to event log data to reach
different healthcare-related analysis objectives such
as chronic diseases management and prediction.
Other relevant research done regarding this topic can
be categorized into: articles that discussed the
discovery of business rules from event logs using
machine learning to achieve a specific analysis
objective or articles that investigated the application
of machine learning algorithms to event logs to
achieve analysis objectives related to a specific
domain. One example of papers that discovered
business rules from event logs using machine learning
to achieve a specific analysis objective is Abou Rida
et al., (2019), in which the article analyzed the event
log using the association rule mining algorithm to
discover access control rules. One example of papers
that investigated the application of machine learning
algorithms to event logs to achieve analysis
objectives related to a specific domain is Bemthuis et
al., (2023), in which the article focused on the
logistics domain analysis objectives.
Consequently, no previous systematic review was
conducted to guide the process analyst on how to
apply machine learning algorithms on event log data
to discover business rules related to the different
analysis objectives or pattern types. This paper aims
to fill this gap by collecting from research
information regarding types of business rules and
analysis objectives that can be discovered through the
application of different machine learning algorithms.
This paper is structured in sections: after this
introductory section, the second section is about
performing the systematic literature review. In the
third section, the findings of the systematic literature
review are presented. Finally, the last section
concludes the paper and presents limitations and
future recommendations.
3 SYSTEMATIC LITERATURE
REVIEW
The Systematic Literature Review (SLR) was
performed by following the review process proposed
by Imran et al. (2022), which comprises three main
steps: review planning, review conducting, and
review reporting. This section will focus on
discussing the first two steps, while the subsequent
section will present the findings of the review
process.
3.1 Planning the Review
In this step, the objectives of the review, the specific
review questions, and the review protocol were
established.
3.1.1 Review Objectives
This SLR aims to address the need for identifying
patterns within event log data that are associated with
different machine learning tasks and the different
analysis objectives for discovering business rules
from event logs. Performing the SLR is important as
it was found that no previous research has been
conducted to gather this information. Therefore, the
purpose of this study is to perform a Systematic
Literature Review (SLR) to identify the pattern types
found in event log data that are related to different
machine learning tasks. Additionally, the research
ICSBT 2024 - 21st International Conference on Smart Business Technologies
132

aims to identify the analysis objectives for the
discovery of business rules from the event log.
3.1.2 Review Questions
RQ1. What are the common pattern types related to
performing different machine learning tasks on
event log data to discover business rules?
RQ2. What are the analysis objectives for the
discovery of business rules from event logs?
3.1.3 Review Protocol
The SLR protocol included identifying the (search
terms, relevant databases, inclusion criteria,
exclusion criteria), which are discussed in this section
in detail.
The search terms deduced from the review
questions were (patterns, rules, business rules, event
log, data mining, machine learning, and business
process). The Boolean AND was used to connect the
search terms and the Boolean OR was used to express
alternative terms that can be used. Based on the
search terms, the following search queries were used
for searching: (“business rules” OR “rules” OR
“patterns) AND (“machine learning” OR “data
mining”) AND (“business process” OR “event log”).
Three scholarly and international online
databases, namely Science Direct, IEEE Explore, and
Google Scholar were chosen due to their recognized
relevance in the field of information technology. The
inclusion criteria were used to select papers that meet
some important requirements and the exclusion
criteria were used to remove papers that do not meet
some important requirements.
The Inclusion Criteria.
• The research paper is written in English.
• The research paper focuses on the discovery of
rules from event logs.
• The research paper uses machine learning for the
discovery of business rules from the event logs.
The Exclusion Criteria.
• The research paper focuses on the discovery of
rules from sources other than the event log
• The Research paper does not use machine
learning algorithms to discover the business rules.
3.2 Conducting the Review
The second step involved conducting the review and
extracting the necessary data to address the review
questions. In which a manual search was conducted
across the three chosen databases using the identified
search queries to retrieve conference proceedings and
journal papers. To capture all relevant articles and
ensure comprehensive coverage of relevant articles,
the review was not limited to a specific period. The
number of articles found in the three databases are
605 articles, comprising 405 from ScienceDirect, 100
from IEEE Explore, and 100 from Google Scholar
(limited to the first ten pages due to lack of relevance
in subsequent pages). Subsequent screening based on
title and abstract eliminated duplicates, resulting in
100 unique articles. Further screening based on
inclusion and exclusion criteria reduced the articles to
40 after examining full texts. Furthermore, the quality
of the articles was assessed according to the following
quality criteria: the number of citations, and the
degree of providing a clear methodology and a
thorough discussion of the results. Articles lacking
citations or with unclear methodology/results were
excluded, resulting in a total of 31 articles.
The 31 research papers were used to extract data
that answered the review questions. Data extracted
from each article were:
• The reference of the paper.
• The pattern type that was discovered from event
log data.
• Explanation of the pattern discovered.
• The machine learning task related to the discovery
of that pattern type.
• The objectives for the discovery of each pattern
type from event log data.
• The analysis objective for the discovery of the
business rules from event logs and the explanation
of each analysis objective.
4 RESULTS AND DISCUSSION
In the following subsections, findings of each review
question are presented.
4.1 First Review Question
Regarding the first review question, the results of the
review identified different pattern types within event
log data related to performing different machine
learning tasks. The identified patterns within event
log data resulted from the application of machine
learning algorithms on event log data to fulfill a
specific task. Depending on the machine learning
tasks performed on event log data, each pattern type
can be discovered in the form of patterns or rules.
Three different patterns within event log data were
commonly and repeatedly mentioned, which are
A Systematic Review to Identify Patterns Types and Analysis Objectives for the Discovery of Business Rules from Event Logs Using
Machine Learning
133
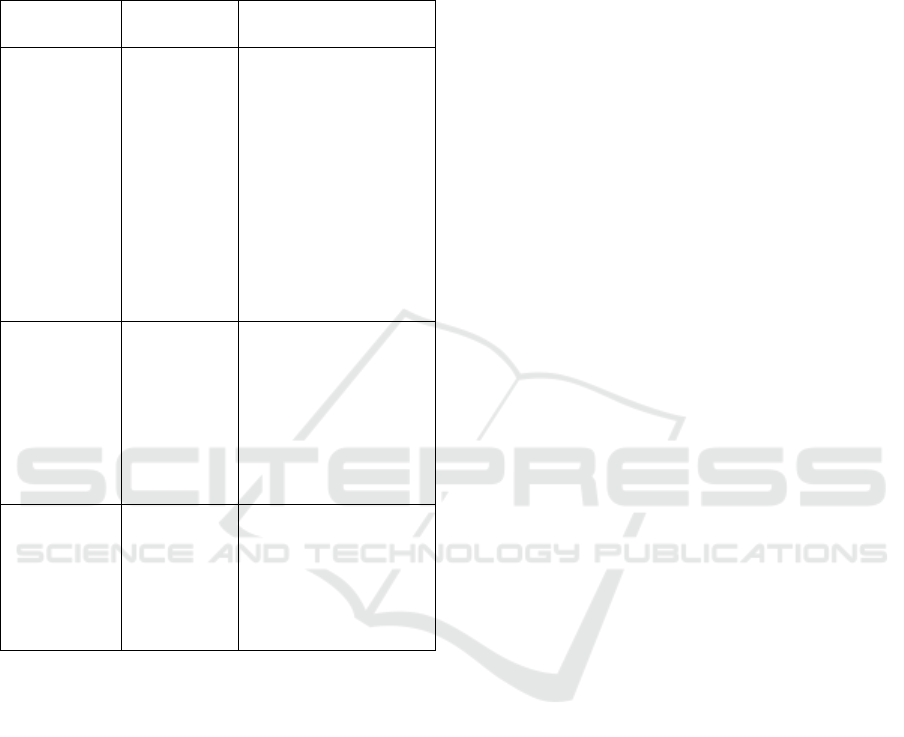
frequent patterns, rare patterns, and classification
patterns. Table 1 summarizes the results of the first
review question findings. Each pattern is explained in
details in the following sub-sections.
Table 1: Summary of first review question findings.
Pattern/Rule
type
Description
ML task needed to
extract the pattern
Frequent
patterns
Reflect
frequent
correlation
between
process
attributes.
The frequent
correlation
could be
related to
sequential or
time-ordered
attributes.
To extract frequent
association/sequential
patterns, apply:
- frequent item set
mining
- association rule
mining
- sequential pattern
mining
- sequential rule
mining
Rare patterns Reflect
correlated
attributes
that occur
infrequently
To extract rare
patterns, apply:
- rare pattern mining
- rare association rule
mining
- rare sequential
pattern mining
Classification
patterns
Reflect the
classification
of event log
attributes
according to
a class label
attribute.
To extract
classification
patterns, apply:
- rule learning
- classification rule
mining
4.1.1 Frequent Patterns Within Process
Data
Frequent patterns within process data reflect
frequently associated event log attributes (Djenouri et
al., 2018). This pattern type is related to performing
machine learning tasks such as frequent item set
mining, association rule mining, sequential pattern
mining, and sequential rule mining tasks on event log
data. Frequent patterns within process data can be
discovered in the form of frequent association rules
or frequent sequential rules.
Frequent association rules reflect frequent
correlations between process attributes such as
activities, resources, and time-related attributes
(Acheli et al., 2021; Djenouri et al., 2018). Analysis
objectives that required the discovery of frequent
association rules from event logs include:
• Discovery of frequent itemsets in an event log.
This analysis objective was satisfied by
discovering association rules that reflect
correlations between process attributes like task,
temporal, or resource-related attributes (Djenouri
et al., 2018).
• Discovery of access control policies given to
resources. This analysis objective was satisfied by
discovering association rules that detect frequent
correlations between process tasks, process data,
and the different resources (Abou Rida et al.,
2019).
• Discovery of resource allocation rules to ensure
each activity is performed by the right resource.
This analysis objective was satisfied by
discovering association rules that reflect frequent
correlations between activities and resources. (Liu
et al., 2012).
Frequent sequential patterns/rules reflect
correlated process attributes that are sequential or
time-ordered (Fournier-Viger et al., 2020; Özdağoğlu
et al., 2018; Dalmas et al., 2017). Sequential patterns
could be ordered subsequences of process events
(Fournier-Viger et al., 2020). Analysis objectives that
required the discovery of frequent sequential
patterns/rules from event logs include:
• Discovery of a process model (Acheli et al., 2021;
Fournier-Viger et al.,2020; Dalmas et al., 2017).
This analysis objective was satisfied by
discovering the sequential patterns within process
activities
• Discovery of profitable sequential process
patterns. This analysis objective was satisfied by
discovering high-utility sequential patterns within
event log data (Fournier-Viger et al.,2020;
Dalmas et al., 2017).
• Discovery of low-cost sequential process patterns
that can be used to lower process costs. This
analysis objective was satisfied by discovering
low-cost sequential patterns within event log data
(Fournier-Viger et al.,2020; Dalmas et al., 2017).
4.1.2 Rare Patterns Within Process Data
Rare patterns within process data reflect infrequent
associations of event log attributes (Djenouri et al.,
2018). Rare patterns are correlated attributes that
occur infrequently. Furthermore, they could show an
accepted behavior that should be enforced or an
unacceptable behavior that should be further analyzed
(Bezerra & Wainer, 2013). In addition, rare patterns
can reveal important information like risks and fraud
(Marin-Castro & Tello-Leal, 2021; Fani Sani et al.,
ICSBT 2024 - 21st International Conference on Smart Business Technologies
134

2018; Pourmasoumi et al., 2017; Mannhardt et al.,
2017; Abou Rida et al., 2019).
Moreover, rare patterns can be detected by
identifying patterns that have support values below a
user-specified support threshold (Fani Sani, 2018) or
by detecting rules that have low support and high
confidence values (Romero et al., 2011). This pattern
is related to performing machine learning tasks such
as rare pattern mining, rare association rule mining,
and rare sequential pattern mining tasks on event logs
to discover rare association/sequential rules that
reflect rare process patterns. Analysis objectives that
required the discovery of rare patterns within process
data in the form of association patterns/rules or
sequential patterns/rules:
• Improving process discovery results (Marin-
Castro & Tello-Leal, 2021; Fani Sani et al., 2018;
Pourmasoumi et al., 2017). This analysis
objective was satisfied by discovering rare
sequential rules within event log data, and then the
rules were examined to determine if they were
correct or noisy patterns.
• Detecting violated data access permissions given
to resources (Abou Rida et al., 2019). This
analysis objective was satisfied by discovering
rare association rules that are below the user
support and confidence values and then
examining these patterns.
• Detecting security violations like fraud and risks
(Mannhardt et al., 2017). This analysis objective
was satisfied by discovering rare patterns that are
below the user support value and then examining
these patterns.
4.1.3 Classification Patterns Within Process
Data
Classification patterns within process data reflect the
classification of event log attributes according to a
class label attribute. Classification patterns can be
discovered in the form of classification patterns or
rules, which show the relationship between a
response attribute and a set of predictor attributes
(Khanbabaei et al., 2018; Suriadi et al., 2012). Rules
discovered could be used for the prediction of unseen
event log class attributes (Márquez-Chamorro et al.,
2017). This pattern is related to performing machine
learning tasks such as rule learning and classification
pattern/rule mining tasks on event log data. Analysis
objectives that required the discovery of classification
patterns within process data:
• Discovery and prediction of process model
constructs, in which the constructs reflect activity
relations such as the parallel, exclusive choice,
and causal relations. Classification rules are
discovered through the classification of labeled
classes of relations (Acheli et al., 2021; Măruşter
et al., 2006)
• Decision point analysis that analyzes and predicts
the relationship between the event log data
attributes and the routing choices of process
execution. Decision point analysis generates
classification rules by classifying the event log
data attributes according to a class attribute which
is the different routing decisions that could be
made (Sarno et al., 2014; Sarno et al., 2013;
Rozinat & van der Aalst, 2006).
• Discovery of Resource patterns that identify the
required profile of resources to perform a process
activity instance. Classification rules are
discovered by classifying attributes like the
process tasks, organizational agents,
organizational positions, and roles into
performers or non-performers of a process activity
instance (Ly, et al., 2005).
• Discovery of classification rules that reflect the
root cause of risk incidents like overtime cases
(Suriadi et al., 2012) or analyze and explain the
deviant process cases by classifying cases into
deviant or normal (Genga et al., 2020; Gupta et
al., 2015; Nguyen et al., 2014).
4.2 Second Review Question
Regarding the second review question, the results of
the review identified a list of different analysis
objectives that can be reached through the discovery
of business rules from event logs using machine
learning; the following list summarizes and explains
the different analysis objectives:
• Process model constructs analysis and prediction:
To discover rules related to process model
constructs like sequences, parallel, and exclusive
choices (Măruşter et al., 2006).
• Process performance analysis: To discover rules
that detect patterns within process data related to
the cost, time, or quality attributes (Van der Aalst,
2016).
• Decision point analysis: To discover decision
rules that capture the effect of data attributes on
the routing of a process instance, by analyzing and
predicting the relationship between the event log
data attributes and the routing choices of a case
(Rozinat & van der Aalst, 2006).
• Discovery of low-cost/high-utility process
patterns: To discover rules that detect profitable
or low-cost patterns within process data
(Fournier-Viger et al., 2020; Dalmas et al., 2017).
A Systematic Review to Identify Patterns Types and Analysis Objectives for the Discovery of Business Rules from Event Logs Using
Machine Learning
135
• Causal relationship discovery: To discover causal
rules that detect causal relationships between
event log data attributes (Acheli et al., 2021).
• Root cause analysis: to discover rules that explain
the reason behind a specific process phenomenon
or behavior by analyzing event log data attributes
(Suriadi et al., 2012).
• Resource performance analysis: To discover rules
that reflect resource behavioral patterns within
process data. Discovered rules can reflect
productivity, and utilization of resources (Pika et
al., 2017).
• Staff assignment/Resource allocation rules
discovery: To discover rules that determine the
profile of a resource needed to perform a certain
activity. Business rules discovered help managers
allocate the right resources to the right tasks and
allocate alternative resources to a specific task if
a required resource is busy (Liu et al., 2012).
Moreover, the business rules discovered help
managers ensure each activity is performed by the
right resource (Liu et al., 2012; Huang et al., 2011;
Ly, et al., 2005).
• Organizational roles analysis: To discover rules
that determine patterns within process data related
to organizational roles, permissions, rights, and
the interaction between different roles (Zhao &
Zhao, 2014).
• Organizational structure analysis: To discover
rules that determine patterns within process data
that reflect the structure of the organization (Zhao
& Zhao, 2014).
• Detection of violated process policies: To
discover rules related to infrequent patterns within
process data that might indicate fraud, violations,
or deviation from the accepted behavior
(Mannhardt et al., 2017; Abou Rida et al., 2019;
Van der Aalst & de Medeiros, 2005).
• Access control rules discovery: To discover rules
that detect patterns within process data that are
related to granted access permissions given to
users. The discovery aims to protect against
unauthorized access to process data (Abou Rida et
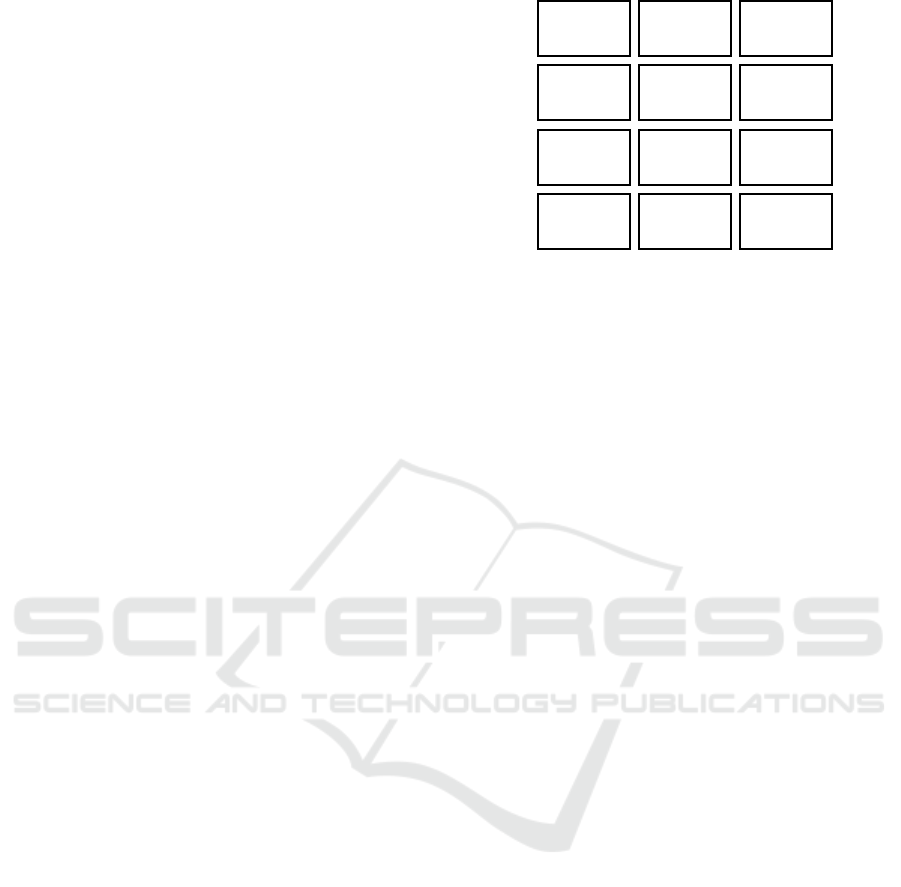
al., 2019). The below figure summarizes the
analysis objective that could be reached through
the application of machine learning algorithms to
process data.
Figure 1: Summary of analysis objectives.
5 CONCLUSION AND OUTLOOK
FOR FUTURE WORK
The paper emphasizes the need to guide process
analysts in achieving different process-related
analysis objectives through the identification of
pattern types and analysis objectives related to
applying machine learning to event log data. It also
discusses the importance of discovering business
rules from event logs. It points out the lack of research
conducting a systematic literature review to collect
information on pattern types and analysis objectives
for the discovery of business rules from event logs
using machine learning techniques.
To address this gap, a systematic literature review
was performed. The review follows a three-step
process: review planning, review conducting, and
review reporting. The objectives of the review are to
identify common pattern types associated with
different machine learning tasks on event log data and
to determine the analysis objectives for discovering
business rules from event logs. The results of the
systematic literature review revealed three common
pattern types within event log data: frequent patterns,
rare patterns, and classification patterns. These
patterns are discovered through various machine
learning tasks applied to event log data. The paper
also identifies different analysis objectives for the
discovery of business rules from event logs.
In conclusion, the systematic literature review
provides valuable insights into pattern types and
analysis objectives related to the discovery of
business rules from event logs using machine
learning. The findings contribute to guiding process
analysts in applying machine learning algorithms to
event log data and achieving several analysis
objectives. In addition, the findings will support the
development of frameworks that aim to standardize
the process of process analysis and business rules
Process
performance
analysis
Decision point
analysis
Discovery of low-
cost/high-utility
process patterns
Causal relationship
discovery
Process model
constructs analysis
and prediction
Root cause analysis
Resource
performance
analysis
Staff
assignment/Resourc
e allocation rules
Organizational roles
analysis
Organizational
structure analysis
Access control rules
discovery
Detection of violated
process policies
ICSBT 2024 - 21st International Conference on Smart Business Technologies
136

discovery from event logs using machine learning
algorithms, the frameworks can then be used to
design future process mining systems.
Limitations of this research include missing some
relevant references due to performing a manual
search process, selecting only three databases for the
search, and selecting the articles written only in the
English language. Accordingly, for future work, it is
recommended to perform an automated search
instead of a manual search, to include more databases
for the search, and to search for articles in languages
other than the English language.
REFERENCES
Abou Rida, A., Assy, N., & Gaaloul, W. (2019). Extracting
Attribute-Based Access Control Rules from Business
Process Event Logs. In BDCSIntell (pp. 38-45).
Acheli, M., Grigori, D., & Weidlich, M. (2021).
Discovering and Analyzing Contextual Behavioral
Patterns from Event Logs. IEEE Transactions on
Knowledge and Data Engineering.
Bemthuis, R., Wang, W., Iacob, M. E., & Havinga, P.
(2023). Business rule extraction using decision tree
machine learning techniques: A case study into smart
returnable transport items. Procedia Computer Science,
220, 446-455.
Berti, A., & van der Aalst, W. M. (2023). OC-PM:
analyzing object-centric event logs and process models.
International Journal on Software Tools for
Technology Transfer, 25(1), 1-17.
Bezerra, F., & Wainer, J. (2013). Algorithms for anomaly
detection of traces in logs of process aware information
systems. Information Systems, 38(1), 33-44.
Bozorgi, Z. D., Teinemaa, I., Dumas, M., La Rosa, M., &
Polyvyanyy, A. (2020, October). Process mining meets
causal machine learning: Discovering causal rules from
event logs. In 2020 2nd International Conference on
Process Mining (ICPM) (pp. 129-136). IEEE.
Campos, J., Richetti, P., Baião, F. A., & Santoro, F. M.
(2018). Discovering business rules in knowledge-
intensive processes through decision mining: an
experimental study. In Business Process Management
Workshops: BPM 2017 International Workshops, (pp.
556-567). Springer International Publishing.
Chen, K., Abtahi, F., Carrero, J. J., Fernandez-Llatas, C., &
Seoane, F. (2023). Process mining and data mining
applications in the domain of chronic diseases: A
systematic review. Artificial Intelligence in Medicine,
102645.
Corea, C., & Delfmann, P. (2020). A Taxonomy of
Business Rule Organizing Approaches in Regard to
Business Process Compliance. Enterprise Modeling
and Information Systems Architectures (EMISAJ), 15,
4-1.
Crerie, R., Baião, F. A., & Santoro, F. M. (2009).
Discovering business rules through process mining. In
Enterprise, Business-Process and Information Systems
Modeling (pp. 136-148). Springer, Berlin, Heidelberg.
Dalmas, B., Fournier-Viger, P., & Norre, S. (2017).
Twincle: A constrained sequential rule mining
algorithm for event logs. Procedia computer science,
112, 205-214
Djenouri, Y., Belhadi, A., & Fournier-Viger, P. (2018).
Extracting useful knowledge from event logs: a
frequent itemset mining approach. Knowledge-Based
Systems, 139, 132-148.
Fani Sani, M., Zelst, S. J. V., & van der Aalst, W. M. (2018,
October). Applying sequence mining for outlier
detection in process mining. In OTM Confederated
International Conferences" On the Move to Meaningful
Internet Systems" (pp. 98-116). Springer, Cham.
Fournier-Viger, P., Li, J., Lin, J. C. W., Chi, T. T., & Kiran,
R. U. (2020). Mining cost-effective patterns in event
logs. Knowledge-Based Systems, 191, 105241.
Genga, L., Potena, D., Chiorrini, A., Diamantini, C., &
Zannone, N. (2020). A latitudinal study on the use of
sequential and concurrency patterns in deviance
mining. In Complex Pattern Mining (pp. 103-119).
Springer, Cham.
Graml, T., Bracht, R., & Spies, M. (2007, October).
Patterns of business rules to enable agile business
processes. In 11th IEEE International Enterprise
Distributed Object Computing Conference (EDOC)
(pp. 365-365). IEEE
Gupta, N., Anand, K., & Sureka, A. (2015, March). Pariket:
Mining business process logs for root cause analysis of
anomalous incidents. In International Workshop on
Databases in Networked Information Systems (pp. 244-
263). Springer, Cham.
Huang, Z., Lu, X., & Duan, H. (2011). Mining association
rules to support resource allocation in business process
management. Expert Systems with Applications, 38(8),
9483-9490.
Khanbabaei, M., Sobhani, F. M., Alborzi, M., & Radfar, R.
(2018). Developing an integrated framework for using
data mining techniques and ontology concepts for
process improvement. Journal of Systems and
Software, 137, 78-95.
Imran, M., Ismail, M. A., Hamid, S., & Nasir, M. H. N. M.
(2022). Complex process modeling in Process mining:
A systematic review. In IEEE Access.
Liu, T., Cheng, Y., & Ni, Z. (2012). Mining event logs to
support workflow resource allocation. Knowledge-
Based Systems, 35, 320-331.
Ly, L. T., Rinderle, S., Dadam, P., & Reichert, M. (2005,
September). Mining staff assignment rules from event-
based data. In International Conference on Business
Process Management (pp. 177-190). Springer, Berlin,
Heidelberg.
Mannhardt, F., Leoni, M. D., Reijers, H. A., & van der
Aalst, W. M. (2017, June). Data-driven process
discovery-revealing conditional infrequent behavior
from event logs. In International conference on
advanced information systems engineering (pp. 545-
560). Springer, Cham.
A Systematic Review to Identify Patterns Types and Analysis Objectives for the Discovery of Business Rules from Event Logs Using
Machine Learning
137

Marin-Castro, H. M., & Tello-Leal, E. (2021). Event log
preprocessing for process mining: a review. Applied
Sciences, 11(22), 10556.
Márquez-Chamorro, A. E., Resinas, M., & Ruiz-Cortés, A.
(2017). Predictive monitoring of business processes: a
survey. IEEE Transactions on Services Computing,
11(6), 962-977.
Măruşter, L., Weijters, A. J., Van Der Aalst, W. M., & Van
Den Bosch, A. (2006). A rule-based approach for
process discovery: Dealing with noise and imbalance in
process logs. Data mining and knowledge discovery,
13(1), 67-87.
Nguyen, H., Dumas, M., Rosa, M. L., Maggi, F. M., &
Suriadi, S. (2014, October). Mining business process
deviance: a quest for accuracy. In OTM Confederated
International Conferences" On the Move to Meaningful
Internet Systems" (pp. 436-445). Springer, Berlin,
Heidelberg.
Özdağoğlu, G., Öztaş, G.Z. and Çağliyangil, M. (2019),
"An application framework for mining online learning
processes through event-logs", Business Process
Management Journal, Vol. 25 No. 5, pp. 860-886
Pika, A., Leyer, M., Wynn, M. T., Fidge, C. J., Hofstede,
A. H. T., & Aalst, W. M. V. D. (2017). Mining resource
profiles from event logs. ACM Transactions on
Management Information Systems (TMIS), 8(1), 1-30.
Polpinij, J., Ghose, A. K., & Dam, H. K. (2010, July).
Business rules discovery from process design
repositories. In 2010 6th World Congress on Services
(pp. 614-620). IEEE.
Polpinij, J., Ghose, A. and Dam, H.K. (2015), "Mining
business rules from business process model
repositories", Business Process Management Journal,
21(4), 820-836.
Pourmasoumi, A., Kahani, M., & Bagheri, E. (2017).
Mining variable fragments from process event logs.
Information Systems Frontiers, 19(6), 1423-1443.
Romero, C., Luna, J. M., Romero, J. R., & Ventura, S.
(2011). RM-Tool: A framework for discovering and
evaluating association rules. Advances in Engineering
Software, 42(8), 566-576.
Rozinat, A., & van der Aalst, W. M. (2006, September).
Decision mining in ProM. In the International
Conference on Business Process Management (pp. 420-
425). Springer, Berlin.
Sarno, R., Sari, P. L. I., Ginardi, H., Sunaryono, D., &
Mukhlash, I. (2013, November). Decision mining for
multi-choice workflow patterns. In 2013 International
conference on computer, control, informatics and its
applications (IC3INA) (pp. 337-342). IEEE.
Sarno, R., Sari, P. L. I., Sunaryono, D., Amaliah, B., &
Mukhlash, I. (2014, September). Mining decisions to
discover the relation of rules among decision points in
a non-free choice construct. In Proceedings of
International Conference on Information,
Communication Technology and System (ICTS) 2014
(pp. 53-58). IEEE.
Seeliger, A. (2020). Intelligent Computer-assisted Process
Mining (Doctoral dissertation, Dissertation, Darmstadt,
Technische Universität Darmstadt, 2020).
Suriadi, S., Ouyang, C., van der Aalst, W. M., & ter
Hofstede, A. H. (2012, September). Root cause analysis
with enriched process logs. In International Conference
on Business Process Management (pp. 174-186).
Springer, Berlin, Heidelberg.
Swinnen, J., Depaire, B., Jans, M. J., & Vanhoof, K. (2011,
August). A process deviation analysis–a case study. In
International Conference on Business Process
Management (pp. 87-98). Springer, Berlin, Heidelberg.
Thi, T. T. P., Helfert, M., Hossain, F., & Dinh, T. L. (2011,
June). Discovering business rules from business
process models. In Proceedings of the 12th
International Conference on Computer Systems and
Technologies (pp. 259-265).
Van der Aalst, W. (2016). Data science in action. In Process
mining (pp. 3-23). Springer, Berlin, Heidelberg.
Van der Aalst, W. M., & de Medeiros, A. K. A. (2005).
Process mining and security: Detecting anomalous
process executions and checking process conformance.
Electronic Notes in Theoretical Computer Science, 121,
(pp. 3-21).
Zhao, W., & Zhao, X. (2014). Process mining from the
organizational perspective. In Foundations of
intelligent systems (pp. 701-708). Springer
ICSBT 2024 - 21st International Conference on Smart Business Technologies
138
