
Data-Driven Intrusion Detection in Vehicles: Integrating Unscented
Kalman Filter (UKF) with Machine Learning
Shuhao Bian
a
, Milad Farsi
b
, Nasser L. Azad
c
and Chris Hobbs
d
Systems Design Engineering Dep., University of Waterloo, 200 University Ave W, Waterloo, Canada
{s6bian, mfarsi, nlashgarianazad}@uwaterloo.ca, cwlh@farmhall.ca
Keywords:
UKF, Machine Learning (ML), Cyber–Physical System (CPS), Advanced Driver Assistance Systems (ADAS).
Abstract:
In the realm of Cyber–Physical System (CPS), accurately identifying attacks without detailed knowledge of
the system’s parameters remains a major challenge. When it comes to Advanced Driver Assistance Systems
(ADAS), identifying the parameters of vehicle dynamics could be impractical or prohibitively costly. To tackle
this challenge, we propose a novel framework for attack detection in vehicles that effectively addresses the
uncertainty in their dynamics. Our method integrates the widely used Unscented Kalman Filter (UKF), a well-
known technique for nonlinear state estimation in dynamic systems, with machine learning algorithms. This
combination eliminates the requirement for precise vehicle modeling in the detection process, enhancing the
system’s adaptability and accuracy. To validate the efficacy and practicality of our proposed framework, we
conducted extensive comparative simulations by introducing Denial of Service (DoS) attacks on the vehicle
systems’ sensors and actuators.
1 INTRODUCTION
Cyber–Physical System (CPS) refers to the integra-
tion of computation with physical processes. There-
fore, cyber attacks on these systems can cause se-
vere consequences. The reliable operation of Ad-
vanced Driver Assistance Systems (ADAS) depends
on the accurate functioning of various sensors and
power management systems. If these elements are
targeted by malicious attackers, passengers, pedestri-
ans and drivers could be exposed to significant safety
risks, potentially endangering their lives. This situa-
tion underscores the critical necessity for attack detec-
tion methods within autonomous driving systems. By
identifying potential threats as they occur, the system
can initiate appropriate protective actions to safeguard
passengers, pedestrians and drivers.
Denial of Service (DoS) attack is one of the most
well-known cyber attacks, and it has become more
prevalent since 2004 (Mirkovic and Reiher, 2004).
These attacks purposefully flood networks with too
much traffic, overwhelming systems and compromis-
ing service availability. DoS attacks can cause sig-
a
https://orcid.org/0009-0000-7518-0972
b
https://orcid.org/0000-0002-5909-4377
c
https://orcid.org/0000-0003-1412-7961
d
https://orcid.org/0009-0007-6175-5449
nificant operational disruptions in Autonomous Ve-
hicles (AVs) and Connected Autonomous Vehicles
(CAVs), which rely heavily on continuous and secure
communication channels for services such as naviga-
tion, real-time traffic updates, and vehicle-to-vehicle
(V2V) communication. The absence of connectivity
not only affects the safety elements essential to AV
operations but also degrades the system’s ability to
make intelligent decisions on the road. Multiple re-
cent studies can be found in the literature, providing
insight into the different classes of attacks and defense
mechanisms developed, such as (Naqvi et al., 2022;
Marcillo et al., 2022; Al-Jarrah et al., 2019; Banaf-
shehvaragh and Rahmani, 2023; Farsi. et al., 2023).
Concerning vehicle security, there exist various
applications of machine learning techniques in the lit-
erature for detecting anomalies in different networks.
One group of approaches considers the possibility of
attacks on communications between vehicles them-
selves and between vehicles and roadside infrastruc-
ture. (Canh and HoangVan, 2023) seeks to build and
evaluate a particular attack detection system that em-
ploys four specific discriminating features. A col-
lected dataset is then utilized to train and evaluate sev-
eral machine learning and statistical models, allowing
for a comparative examination of their efficacy. The
suggested strategy focuses on early detection, allow-
ing for timely and effective countermeasures.
714
Bian, S., Farsi, M., Azad, N. and Hobbs, C.
Data-Driven Intrusion Detection in Vehicles: Integrating Unscented Kalman Filter (UKF) with Machine Learning.
DOI: 10.5220/0013063900003822
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Informatics in Control, Automation and Robotics (ICINCO 2024) - Volume 1, pages 714-723
ISBN: 978-989-758-717-7; ISSN: 2184-2809
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

Another class of intrusion detection has focused
on in-vehicle communications used for exchang-
ing data between different control units of vehicles.
(Berger et al., 2018) evaluates various machine learn-
ing methods, including deep learning, for in-vehicle
intrusion detection systems. In a more recent tech-
nique, (Aldhyani and Alkahtani, 2022) implemented
deep learning approaches like Convolutional Neural
Network (CNN)s and CNN-Long Short-Term Mem-
ory (LSTM) hybrid models to detect attacks such as
spoofing, flooding, and replay attacks on the Con-
troller Area Network (CAN) bus. Other similar tech-
niques can be found in (Pawar et al., 2022). A com-
prehensive survey of the techniques presented, in the
literature, can be found in (Rajapaksha et al., 2023).
The majority of these approaches focus on net-
work traffic and data package analysis to discover re-
curring patterns in normal operation during the train-
ing stage, and then use them to detect anomalies dur-
ing the exploitation stage. Therefore, the dynamic as-
pects of different subsystems in the vehicles receive
less attention. On the other hand, dynamic models
are the foundation of vehicle design, allowing engi-
neers to predict and optimize the performance of nu-
merous vehicle systems under a variety of operating
situations. Exploiting such models for intrusion de-
tection allows us to identify anomalies by continu-
ously comparing real-time data against the predicted
normal behavior. Through this proactive strategy, in-
trusions can be detected early and promptly addressed
to reduce potential damage. (Ju et al., 2022) provides
a review of such techniques from a control perspec-
tive. In line with these approaches, in this study, we
employ a rather system dynamics model-based tech-
nique as a defense mechanism. Moreover, since the
parameters of the vehicle, such as weight, tire con-
ditions, and engine characteristics, can change over
time or under different conditions, we have found ma-
chine learning techniques particularly advantageous
as they offer high adaptability.
The Unscented Kalman Filter (UKF) has been em-
ployed successfully in various fields of applications,
such as power and automotive systems. In power sys-
tems, the UKF contributes to stability and operational
integrity by accurately evaluating the state of electri-
cal grids and identifying potential interruptions (Du
et al., 2022; Rashed et al., 2022). The UKF has played
an important role in improving cyber threat detection
in-vehicle systems (Zhang et al., 2021), particularly
AVs and CAVs. The UKF improves the system’s ro-
bustness against DoS attacks by enabling real-time,
precise anomaly detection, preventing possible threats
from causing harm. In (
ˇ
Zivkovi
´
c and Sari
´
c, 2018),
the authors employed the UKF to predict and update
state variables from a previously known state to de-
tect False Data Injection (FDI) attacks. They com-
pared the results to those obtained using a common
weighted least squares-based state estimation tech-
nique. They observed that the state variables under
attack significantly deviated between them, which can
be used to detect the attack.
In this paper, we describe a novel approach for de-
veloping an attack detection system tailored to vehi-
cles. Our proposed approach integrates the UKF with
a learning-based module to obtain a resilient adaptive
framework. This feature eliminates the requirement
for detailed vehicle modeling in the attack detection
process, simplifying implementation while retaining
accuracy. The framework’s effectiveness is strength-
ened by the use of a Cumulative Sum (CUSUM) algo-
rithm with a sliding window for responsive anomaly
detection, and by incorporating the learned dynam-
ics to predict and compare real-time data against ex-
pected behavior. By leveraging the UKF’s capabilities
in handling non-linear dynamics, our proposed algo-
rithm significantly improves the robustness and accu-
racy of intrusion detection in cyber-physical systems,
particularly in ADAS. We conducted extensive sim-
ulations using CARLA, a simulation platform com-
monly used in autonomous driving research, to eval-
uate the efficacy and feasibility of our system. This
made it possible for us thoroughly to test our struc-
ture in practical settings and make sure it can operate
dependably in actual situations.
The rest of the paper is organized in the follow-
ing order: In Section 2, we formulate the problem
by assuming a DoS attack on the actuator. Section 3
presents the attack detection framework, introducing
the main algorithm. In the following Section 4, we
discuss the detailed simulation results.
2 PROBLEM FORMULATION
The system model is described by the following equa-
tions
x
k+1
= f (x
k
,u
k
),
y
k
= h(x
k
),
(1)
where x
k
∈ R
n
, represents the state space of the vehi-
cle, and u
k
∈ R
p
, denotes the control input. y
k
∈ R
m
is
the measurement vector. Moreover, f : R
n
×R
p
→ R
n
represents the state transition function that defines the
next state x
k+1
based on the current state x
k
and the
control input u
k
. The function h : R
n
→ R
m
denotes
the measurement function that maps the current state
x
k
to the measurement vector y
k
. k gives the time step.
Data-Driven Intrusion Detection in Vehicles: Integrating Unscented Kalman Filter (UKF) with Machine Learning
715

Next, we will model the DoS attack on various
elements of the control loop.
2.1 Attack Model
Considering that the attacks are implemented in the
cyber layer, we construct the cyber attack in a discrete
space, as shown below.
2.1.1 Actuator Attack
To model the effect of the attack, the dynamics in (1)
are modified as
x
k+1
=
(
f (x
k
,a
k
), k ∈ α,
f (x
k
,u
k
), k /∈ α,
(2)
where we denote the set of time steps during which
the attack is active using α. Moreover, we assume
that DoS can arbitrarily affect a subset of components
of u
k
. This can be further described by
a
k
[i] =
(
0, i ∈ Γ
a
,
u
k
[i], otherwise,
(3)
where Γ
a
denotes the set of indices corresponding to
the actuators that are affected by the attack, and i
ranges over the set Γ
a
⊆ {1,2,..., p}. Accordingly, a
particular attack strategy can be represented by choos-
ing nonempty sets α and Γ
a
, which specify the time
of the attack and the indices of targeted actuators, re-
spectively.
2.1.2 Sensor Attack
In this section, we define the sensor attack in a similar
fashion. We modify the measurements relation given
in equation (1) to reflect the DoS attack on some spe-
cific set of sensors. The equation
y
k
=
(
y
k
a
, k ∈ β,
h(x
k
), k /∈ β,
(4)
switches the measurements to y
k
a
that may be manipu-
lated by the anomaly, at different time steps specified
by set β. Moreover, based on a particular attack pat-
tern, a list of targeted sensors is given by Γ
s
, with the
attacked components being set to zero. This is shown
below
y
k
a
[i] =
(
0, i ∈ Γ
s
,
y
k
[i], otherwise,
(5)
where Γ
s
⊆ {1,2,...,m} denotes the set of indices
corresponding to the components of y
k
that are
blocked by the attacker. Here, m refers to the dimen-
sion of the measurement vector.
2.2 Vehicle Model
In order to demonstrate the performance of the devel-
oped approach, we use the Kalman filter as a base-
line approach for comparison in Section 4. It should
be noted that we aim to obtain a sample-based tech-
nique, meaning that we treat the dynamics as a black
box without using the analytical model. However,
since the dynamic model are essential for running the
Kalman Filter, we concisely present the equations of
the vehicle in what follows.
According to (Takahama and Akasaka, 2018), a
vehicle dynamics model can be obtained as below.
The longitudinal dynamics of the vehicle is given by
M
vehicle
˙v
h
= M
vehicle
a
f
− r
travel
, (6)
where M
vehicle
is the mass of the vehicle, a
f
is the
traction force converted to acceleration and r
travel
is
the travel resistance. The model of the r
travel
can be
described as
r
travel
= r
air
(v
2
h
) + r
roll
(v
h
) + r
accel
( ˙v
h
) + r
grad
(θ),
(7)
where r
air
=
1
2
ρC
d
Av
2
h
is the air drag, ρ is the air den-
sity, C
d
is the drag coefficient, A is the frontal area of
the vehicle, and v
h
is the vehicle speed. The rolling
resistance is given by r
roll
= C
r
M
vehicle
gv
h
, where C
r
and g denote the rolling resistance coefficient and the
acceleration due to gravity, respectively.
Then, the acceleration resistance is r
accel
=
M
vehicle
˙v
h
, where ˙v
h
is the acceleration of the vehicle.
Finally, r
grad
= M
vehicle
gsin(θ), where θ is the slope
angle of the road.
3 ATTACK DETECTION
FRAMEWORK
In this section, we present the required components to
construct the attack detection framework.
3.1 Unscented Kalman Filter
In the UKF, it is not necessary to know the detailed
model. The UKF uses sigma points to sample the
input and obtain the corresponding output. It is a
method similar to the Monte Carlo approach but re-
quires only a small number of sigma points. Next, we
will provide a detailed introduction to the UKF.
3.1.1 Unscented Transformation (UT)
As described by (Wan and Van Der Merwe, 2000),
the UT is a technique developed for the generation of
ICINCO 2024 - 21st International Conference on Informatics in Control, Automation and Robotics
716

Observer/Filter
Environment
Detector
Predict
Select Sigma
Points
Update
CUSUM
Extract Sliding
Window
Standard Error
Figure 1: The flow chart of the algorithm.
sigma points that are capable of undergoing nonlinear
transformations expressed as f (x
k
,u
k
). This approach
is particularly valuable when dealing with a multitude
of random vectors, each residing in an n-dimensional
space (x
k
∈ R
n
), characterized by a mean ¯x
k
and a co-
variance matrix P
k
.
Manual Control
collect data
Figure 2: CARLA Environment.
3.1.2 Select Sigma Points
The sigma points χ
k
i
are chosen such that they capture
the true mean and covariance of the random variable
x
k
, enabling an accurate propagation through the non-
linear function f (x
k
,u
k
). This selection ensures that
the mean and covariance of the sigma points match
¯x
k
and P
k
, respectively, providing an effective mech-
anism for estimating the statistical properties of x
k+1
.
The sigma points are selected according to
χ
k
0
= ¯x
k
,
χ
k
i
= ¯x
k
+ (
p
(n + λ)P
k
)
i
i = 1, ...,n,
χ
k
i
= ¯x
k
− (
p
(n + λ)P
k
)
i
i = n + 1, ...,2n,
W
(m)
0
=
λ
n+λ
,
W
(c)
0
=
λ
n+λ
+ (1 − φ
2
+ β),
W
(m)
i
= W
(c)
i
=
1
2(n+λ)
i = 1, ...,2n.
(8)
According to (Wang et al., 2023), λ is a key pa-
rameter calculated using λ = φ
2
(n + κ) − n, φ deter-
mines the dispersion degree of σ points, and κ is typi-
cally 3−n. β is for integrating prior knowledge about
x’s distribution.
3.1.3 Predict
The predicted state and covariance are
¯x
k+1|k
=
2n
∑
i=0
W
(m)
i
χ
k+1|k
i
,
P
k+1|k
=
2n
∑
i=0
W
(c)
i
χ
k+1|k
i
− ¯x
k+1|k
χ
k+1|k
i
− ¯x
k+1|k
T
,
¯y
k+1|k
=
2n
∑
i=0
W
(m)
i
Y
k+1|k
i
,
P
k+1
yy
=
2n
∑
i=0
W
(c)
i
Y
k+1|k
i
− ¯y
k+1|k
Y
k+1|k
i
− ¯y
k+1|k
T
,
P
k+1
xy
=
2n
∑
i=0
W
(c)
i
χ
k+1|k
i
− ¯x
k+1|k
Y
k+1|k
i
− ¯y
k+1|k
T
,
(9)
where χ
k+1|k
i
= f (χ
k
i
,u
k
), Y
k+1|k
i
= h(χ
k
i
,u
k
), for i =
0,...,2n.
3.1.4 Update
The update step can be defined as
K
k+1
= P
k+1
xy
P
k+1
yy
−1
,
r
k+1
= y
k+1
− ¯y
k+1|k
,
x
k+1
= ¯x
k+1|k
+ K
k+1
r
k+1
,
P
k+1
= P
k+1|k
− K
k+1
P
k+1
xy
T
,
(10)
where K is the Kalman gain, r is the residual. These
values are updated when sensors provide new mea-
surements.
Data-Driven Intrusion Detection in Vehicles: Integrating Unscented Kalman Filter (UKF) with Machine Learning
717

Data: Sensor signal, Input signal
Result: Attack State: f
ad
(0 for no attack, 1
for attack detected)
Initialisation: ;
Initialize the cumulative sum, s
1
,s
2
← 0 ;
Initialize the attack detection flag, f
ad
← 0;
Initialize the threshold value, threshold ;
Define the window size N ;
Initialize an empty list Q, to store the last N
residuals ;
Detection Loop: ;
while each new sensor signal input y do
Perform the selecting sigma points step;
Perform the prediction step of UKF to
estimate the next state ;
Perform the update step of UKF with
signal y to obtain residual r ;
Append r to Q ;
Update the UKF model // using
equation (11) ;
if Size of Q > N then
Remove the oldest residual from Q ;
end
Update cumulative sum using residuals
within Q: s
1
←
∑
Q // using
equation (12) ;
Update standard error using residuals
within Q: s
2
← std(Q) // using
equation (13) ;
if abs(s
1
) > threshold
1
and
s
2
> threshold
2
then
f
ad
← 1 // attack detected
immediately upon detection ;
else
f
ad
← 0;
Continue monitoring ;
end
end
Algorithm 1: CUSUM Algorithm with Sliding Window for
Attack Detection.
3.2 Machine Learning (ML)
Obtaining the parameters of a vehicle might often be
infeasible or economically prohibitive. In the update
phase of the UKF, we employ ML techniques to pre-
dict the vehicle’s subsequent state.
For this purpose, we selected the multi-layer per-
ceptron (MLP) network. This neural network receives
control commands (u) — encompassing the throttle-
brake and steering angle — as well as the vehicle’s
current state, which includes velocity, angular veloc-
ity, and acceleration, as its input. The network is de-
signed to output the vehicle’s acceleration for the next
time step. Designed to predict the vehicle’s accelera-
tion at the next time step, it was necessary to account
for the delay between the input commands and the re-
sultant state changes. To address this, according to
(Xu et al., 2019), we selected a model output that re-
flects the vehicle’s acceleration 50 milliseconds after
the input, ensuring the training data adequately cap-
tures the dynamics of the system.
The MLP is structured with three distinct layers:
an input layer comprising 5 units, a hidden layer con-
taining 20 units, and a single-unit output layer. The
activation function utilized within the hidden layer is
the Rectified Linear Unit (ReLU).
With this predicted acceleration, we can determine
the vehicle’s upcoming velocity using Newton’s sec-
ond law, thereby integrating ML predictions seam-
lessly into the UKF’s update mechanism for enhanced
estimation accuracy.
3.3 Model Update Methods
In order to make the detector adaptive, we deployed
an algorithm that can make the detector update auto-
matically. In the proposed detector, we updated the
model of the vehicle when it got new sensor signals.
To make sure the model is not updated when the at-
tacker implements the DoS attack on the car model
and is updated when the car is running normally, we
update the learning rate according to
l = 1 −
1
1 + e
−S
rate
∥r∥
2
. (11)
Here, l denotes the learning rate, r represents the
residual of the car, S
rate
is the scale of the residual,
and ∥ · ∥
2
denotes the L
2
norm of a vector.
3.4 Attack Detection Method
As a widely used attack detector in many literature
(Liu et al., 2019), CUSUM is selected as the detec-
tor. In (Van Eykeren et al., 2012), they also calculated
a moving window average for the residual. In prac-
tice, there is often a gap between theoretical models
and engineering applications. Therefore, we intro-
duce W
r1
and W
r2
to fine-tune the target parameters.
Additionally, we used two tests to detect whether the
target is under attack.
Test 1 is shown by
s
k
1
=
k
∑
i=k−N+1
W
r1
r
i
, (12)
where r is the residual updated by the UKF, W
T
r1
∈ R
m
,
N is the length of the sliding window.
ICINCO 2024 - 21st International Conference on Informatics in Control, Automation and Robotics
718
Test 2 is described as
s
k
2
=
k
∑
i=k−N+1
(r
i
− ¯r)W
r2
(r
i
− ¯r)
T
, (13)
where ¯r is the average of the sliding window for the
residuals, W
r2
∈ R
m×m
is the weight of the residual.
Then s
1
and s
2
will be compared with two thresh-
olds, t
1
and t
2
, respectively. Then the alarm is trig-
gered according to
A =
(
S
p
, s
1
> t
1
and s
2
> t
2
,
S
n
, s
1
≤ t
1
or s
2
≤ t
2
.
(14)
As illustrated in Figure 1, the trained model de-
rived from historical data is subsequently integrated
into the UKF. The mechanism of the detector is de-
tailed in Algorithm 1.
4 SIMULATION RESULTS
To demonstrate the efficacy of the proposed approach
under DoS attacks, we chose CARLA (Dosovitskiy
et al., 2017) as our simulator, which can simulate real-
world dynamics and generate sensor signals in real-
time. This allows for accurate and timely responses
in the simulation environment. Moreover, to highlight
the superiority of the proposed method, we compare
it with the traditional Kalman filter.
All neural network training was conducted in
Python on the Ubuntu operating system. The hard-
ware configuration used included an AMD Ryzen 9
processor with 16 cores, clocked at 3.40 GHz, and
64GB of RAM. The Kalman filter and UKF were im-
plemented using the FilterPy library (Labbe, 2024),
while the neural network was developed with PyTorch
(Paszke et al., 2019).
In the following subsection, we detail the data
preprocessing methods, the implementation of attack
scenarios, the simulation parameters and the resulting
simulation outcomes.
4.1 Data Preprocessing
Both manual driving data and autonomous driving
data generate command signals (throttle, brake, and
steering angle), which can be used as training data.
To obtain representative data, we used manual con-
trol to generate data in the CARLA environment, as
shown in Figure 2.
In order to achieve better training results, we need
to ensure that the data are valid by removing all out-
liers.
The brake and throttle inputs are combined and
normalized into a unified control signal ranging from
0 to 1 according to
u =
T − B + 1
2
, (15)
where u is the unified control signal, T ∈ [0, 1] is the
throttle input, B ∈ [0,1] is the brake input, T
max
is
the maximum throttle value and B
min
is the minimum
brake value. When u = 0, it represents full braking,
and when u = 1, it represents full throttle.
4.2 Attack Implementation
We implemented the attack at 20 seconds in the sim-
ulation. To validate the algorithm, we chose a DoS
attack signal in the form of a Pulse Width Modulation
(PWM) structure. When the signal is 1, it indicates
that the monitor is blocked.
4.3 Parameters
To have a comparison we chose a typical Kalman fil-
ter. The parameters of equation (7) is shown as ta-
ble 1.
Table 1: Parameters of Kalman filter.
Name Value
r
air
68.9 N
r
roll
271.6 N
r
grad
0 N
If there is no slope, r
grad
= 0. Therefore, the to-
tal travel resistance r
travel
is given by r
travel
= r
air
+
r
roll
+ r
grad
= 340.5N. In order to make the detec-
tor more accurate, we have W
r1
=
1 0.01 0
T
,
W
r2
=
1 0 0
0 0.01 0
0 0 0
and we focus on the acceler-
ation residual to detect the attack.
The learning parameters are detailed in Table 2.
The optimizer used is Adam (Kingma and Ba, 2014).
Table 2: Parameters of Machine Learning.
Name Value
Learning rate 0.001
Train size/Total 0.8
Epochs 1000
MLP batch size 64
MLP epochs 1000
To improve the clarity of the results, we simplified
the model, the value of t
2
is based on t
1
, maintaining
a fixed proportional relationship as shown by
t
2
= γt
1
, (16)
Data-Driven Intrusion Detection in Vehicles: Integrating Unscented Kalman Filter (UKF) with Machine Learning
719
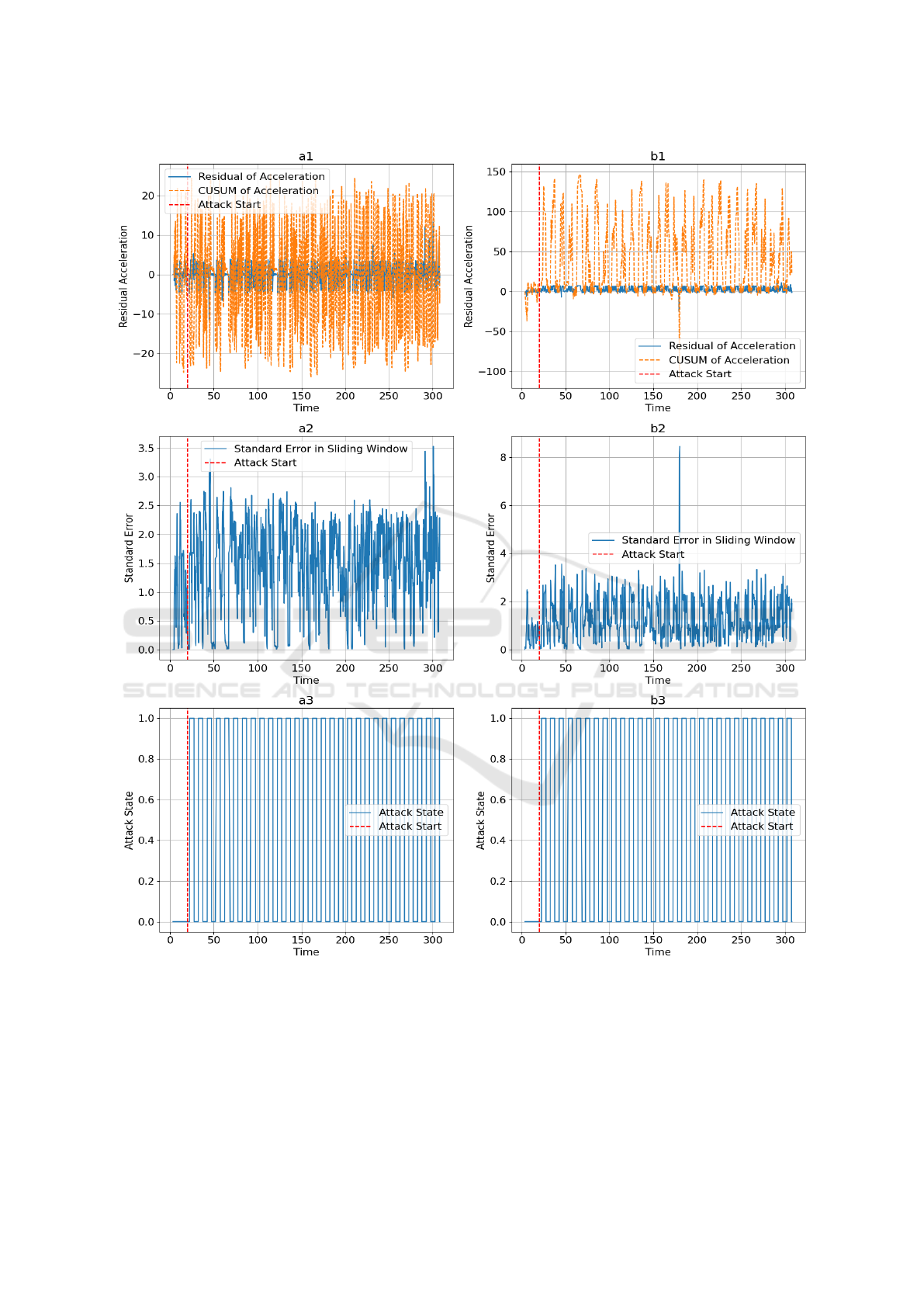
Figure 3: The results of the attack detector are as follows: for the Kalman filter, a1 represents the residual and CUSUM of
residuals in the sliding window, a2 denotes the standard error of residuals in the sliding window, and a3 indicates the attack
state; for the proposed method, b1 signifies the residual and CUSUM of residuals in the sliding window, b2 refers to the
standard error of residuals in the sliding window, and b3 denotes the attack state of the UKF.
ICINCO 2024 - 21st International Conference on Informatics in Control, Automation and Robotics
720
where γ is a tuning parameter. In this simulation, γ is
set to 0.04.
4.4 Results
In this study, the performance of the Kalman filter
and UKF for detecting attacks in autonomous vehi-
cles was evaluated. The experiments were conducted
under two scenarios: actuator attack and sensor at-
tack.
4.4.1 Actuator Attack
To validate the detector, we use four metrics to mea-
sure the performance: false positive alarm rate, true
positive alarm rate, false negative alarm rate and true
negative alarm rate.
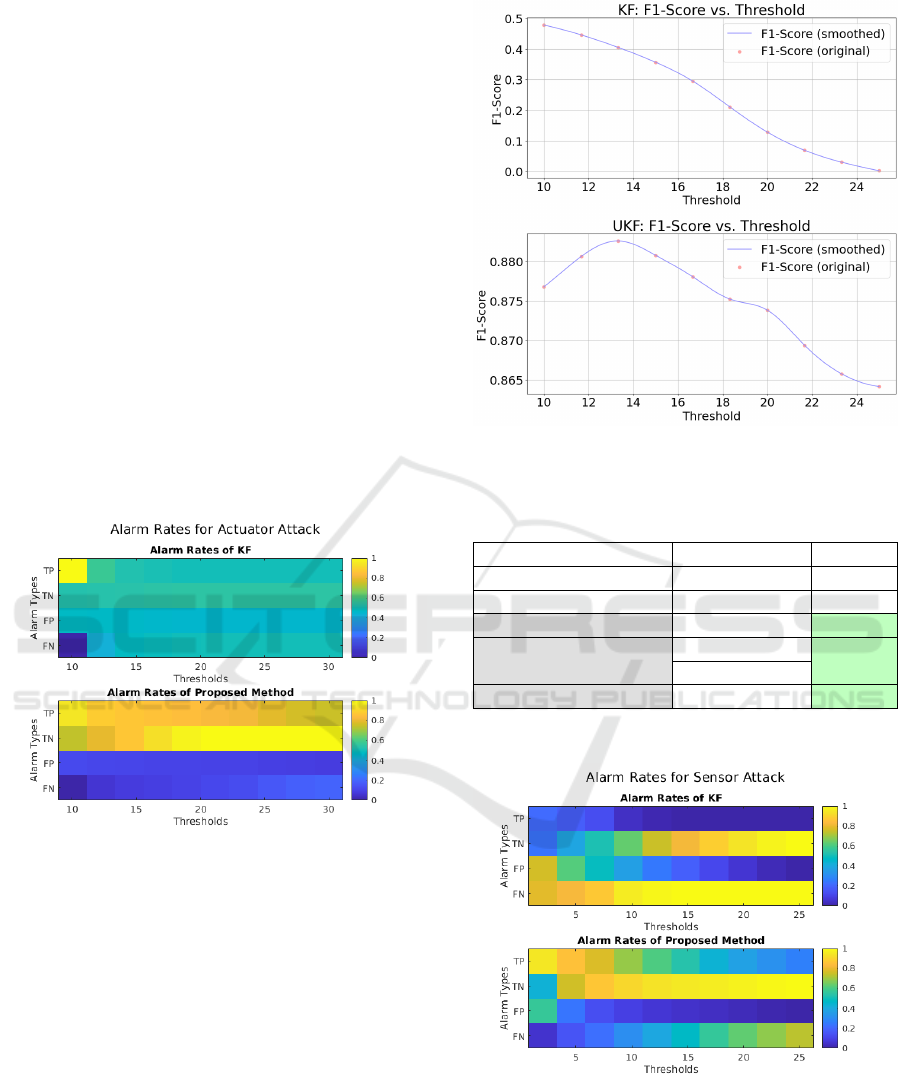
As shown in Figure 4, despite the threshold
changes from 10 to 25, the true positive alarm rate
and true negative alarm rate of the proposed method
are significantly higher than those of the Kalman filter
when using the same threshold.
Figure 4: The metrics of different detectors are defined as
follows: the true positive rate (TP), the true negative rate
(TN), the false positive rate (FP), and the false negative rate
(FN).
To achieve a more precise quantification of the
research data, we utilized the F1-score (Bishop and
Nasrabadi, 2006). As shown in Figure 5, the F1-score
of the Kalman filter shows a decreasing trend, while
the F1-score of the UKF first increases and then de-
creases. Based on this pattern, we selected the ap-
propriate thresholds for the Kalman filter and the pro-
posed method. The thresholds are 10 for the Kalman
filter and 13.33 for the proposed method.
Table 3 presents the optimal thresholds and cor-
responding values for the Kalman filter and the pro-
posed method. In this table, all metrics of the pro-
posed method significantly outperform those of the
Kalman filter.
Figure 5: F1 Score of Kalman Filter and the Proposed
Method.
Table 3: Optimal Thresholds and Confusion Matrix Values
for Kalman Filter and the Proposed Method.
Metric Kalman filter Ours
Optimal Threshold 10.0 13.33
F1-Score 0.4784 0.8826
True Positives (TP) 42.88% 93.58%
False Positives (FP) 36.41% 18.48%
True Negatives (TN) 63.59% 81.52%
False Negatives (FN) 57.12% 6.42%
4.4.2 Sensor Attack
Figure 6: The metrics of different detectors are defined as
follows: the true positive rate (TP), the true negative rate
(TN), the false positive rate (FP), and the false negative rate
(FN).
We obtained similar results for Attack Detection (AD)
on the sensor, as shown in Figure 6. Both the true
positive and true negative rates of the proposed UKF
Data-Driven Intrusion Detection in Vehicles: Integrating Unscented Kalman Filter (UKF) with Machine Learning
721

method are significantly higher than those of the
Kalman filter when choosing the best F1-Score.
5 CONCLUSION
In conclusion, we proposed a novel framework for at-
tack detection in vehicles with unknown systems. We
exploited a learning-based model to predict and com-
pare observations against expected behavior. There-
fore, compared to the Kalman filter, the proposed ap-
proach based on the UKF is capable of detecting DoS
attacks from the sensor and actuator without prior
knowledge of the system parameters. Accordingly,
by exploiting UKF’s capabilities in handling nonlin-
earity, our proposed algorithm demonstrated a signif-
icant advantage over the traditional Kalman filter for
detecting DoS attacks on sensors and actuators. In
detail, through extensive simulations of our proposed
algorithm, we observed that our method outperforms
the Kalman filter by demonstrating substantial results
in both true positive alarm rate and true negative alarm
rate. Enhancing the filtering design for vehicle in-
cursion detection can be the primary focus of future
research. By precisely simulating intricate dynam-
ics, investigating robust particle filters may improve
anomaly identification even further and strengthen ve-
hicle security. Moreover, the presented framework
can be extended to other types of attacks such as FDI.
ACKNOWLEDGEMENT
We gratefully acknowledge the financial support pro-
vided by BlackBerry and the Natural Sciences and
Engineering Research Council of Canada (NSERC).
Furthermore, we acknowledge BlackBerry QNX’s as-
sistance and cooperation with this study. Their assis-
tance has been crucial to the accomplishment of this
task.
REFERENCES
Al-Jarrah, O. Y., Maple, C., Dianati, M., Oxtoby, D., and
Mouzakitis, A. (2019). Intrusion detection systems
for intra-vehicle networks: A review. Ieee Access,
7:21266–21289.
Aldhyani, T. H. and Alkahtani, H. (2022). Attacks to au-
tomatous vehicles: A deep learning algorithm for cy-
bersecurity. Sensors, 22(1):360.
Banafshehvaragh, S. T. and Rahmani, A. M. (2023). Intru-
sion, anomaly, and attack detection in smart vehicles.
Microprocessors and Microsystems, 96:104726.
Berger, I., Rieke, R., Kolomeets, M., Chechulin, A., and
Kotenko, I. (2018). Comparative study of machine
learning methods for in-vehicle intrusion detection. In
International Workshop on Security and Privacy Re-
quirements Engineering, pages 85–101. Springer.
Bishop, C. M. and Nasrabadi, N. M. (2006). Pattern recog-
nition and machine learning, volume 4. Springer.
Canh, T. N. and HoangVan, X. (2023). Machine learning-
based malicious vehicle detection for security threats
and attacks in vehicle ad-hoc network (vanet) commu-
nications. In 2023 RIVF International Conference on
Computing and Communication Technologies (RIVF),
pages 206–211. IEEE.
Dosovitskiy, A., Ros, G., Codevilla, F., Lopez, A., and
Koltun, V. (2017). Carla: An open urban driving sim-
ulator.
Du, D., Zhu, M., Li, X., Fei, M., Bu, S., Wu, L., and Li, K.
(2022). A review on cybersecurity analysis, attack de-
tection, and attack defense methods in cyber-physical
power systems. Journal of Modern Power Systems and
Clean Energy, 11(3):727–743.
Farsi., M., Bian., S., Azad., N. L., Shi., X., and Walenstein.,
A. (2023). An efficient resilient mpc scheme via con-
straint tightening against cyberattacks: Application to
vehicle cruise control. In Proceedings of the 20th In-
ternational Conference on Informatics in Control, Au-
tomation and Robotics - Volume 1: ICINCO, pages
674–682. INSTICC, SciTePress.
Ju, Z., Zhang, H., Li, X., Chen, X., Han, J., and Yang, M.
(2022). A survey on attack detection and resilience
for connected and automated vehicles: From vehicle
dynamics and control perspective. IEEE Transactions
on Intelligent Vehicles, 7(4):815–837.
Kingma, D. P. and Ba, J. (2014). Adam: A
method for stochastic optimization. arXiv preprint
arXiv:1412.6980.
Labbe, R. (2024). filterpy: Kalman filters and other optimal
and non-optimal estimation filters in python. https:
//github.com/rlabbe/filterpy. Accessed: 20 June 2024.
Liu, Q., Mo, Y., Mo, X., Lv, C., Mihankhah, E., and Wang,
D. (2019). Secure pose estimation for autonomous
vehicles under cyber attacks. In 2019 IEEE Intelligent
Vehicles Symposium (IV), pages 1583–1588. IEEE.
Marcillo, P., Tamayo-Urgil
´
es, D., Valdivieso Caraguay,
´
A. L., and Hern
´
andez-
´
Alvarez, M. (2022). Security
in v2i communications: a systematic literature review.
Sensors, 22(23):9123.
Mirkovic, J. and Reiher, P. (2004). A taxonomy of ddos at-
tack and ddos defense mechanisms. ACM SIGCOMM
Computer Communication Review, 34(2):39–53.
Naqvi, I., Chaudhary, A., and Kumar, A. (2022). A sys-
tematic review of the intrusion detection techniques in
vanets. TEM Journal, 11(2):900.
Paszke, A., Gross, S., Massa, F., Lerer, A., Bradbury, J.,
Chanan, G., Killeen, T., Lin, Z., Gimelshein, N.,
Antiga, L., et al. (2019). Pytorch: An imperative style,
high-performance deep learning library. Advances in
neural information processing systems, 32.
Pawar, Y. S., Honnavalli, P., and Eswaran, S. (2022). Cy-
ber attack detection on self-driving cars using machine
ICINCO 2024 - 21st International Conference on Informatics in Control, Automation and Robotics
722

learning techniques. In 2022 IEEE 3rd Global Confer-
ence for Advancement in Technology (GCAT), pages
1–5. IEEE.
Rajapaksha, S., Kalutarage, H., Al-Kadri, M. O., Petrovski,
A., Madzudzo, G., and Cheah, M. (2023). Ai-based
intrusion detection systems for in-vehicle networks: A
survey. ACM Computing Surveys, 55(11):1–40.
Rashed, M., Kamruzzaman, J., Gondal, I., and Islam, S.
(2022). False data detection in a clustered smart
grid using unscented kalman filter. IEEE Access,
10:78548–78556.
Takahama, T. and Akasaka, D. (2018). Model predictive
control approach to design practical adaptive cruise
control for traffic jam. International Journal of Au-
tomotive Engineering, 9(3):99–104.
Van Eykeren, L., Chu, Q., and Mulder, J. (2012). Sen-
sor fault detection and isolation using adaptive ex-
tended kalman filter. IFAC Proceedings Volumes,
45(20):1155–1160.
Wan, E. A. and Van Der Merwe, R. (2000). The unscented
kalman filter for nonlinear estimation. In Proceed-
ings of the IEEE 2000 adaptive systems for signal
processing, communications, and control symposium
(Cat. No. 00EX373), pages 153–158. Ieee.
Wang, C., Chen, L., Li, L., Yan, Y.-H., Sun, J., Yu, C.,
Deng, X., Liang, C.-P., Zhang, X.-L., and Peng, W.-
M. (2023). Combining unscented kalman filter and
wavelet neural network for anti-slug. Petroleum Sci-
ence, 20(6):3752–3765.
Xu, J., Luo, Q., Xu, K., Xiao, X., Yu, S., Hu, J., Miao, J.,
and Wang, J. (2019). An automated learning-based
procedure for large-scale vehicle dynamics modeling
on baidu apollo platform. In 2019 IEEE/RSJ Interna-
tional Conference on Intelligent Robots and Systems
(IROS), pages 5049–5056. IEEE.
Zhang, D., Lv, C., Yang, T., and Hang, P. (2021). Cyber-
attack detection for autonomous driving using vehi-
cle dynamic state estimation. Automotive Innovation,
4:262–273.
ˇ
Zivkovi
´
c, N. and Sari
´
c, A. T. (2018). Detection of false
data injection attacks using unscented kalman filter.
Journal of Modern Power Systems and Clean Energy,
6(5):847–859.
Data-Driven Intrusion Detection in Vehicles: Integrating Unscented Kalman Filter (UKF) with Machine Learning
723
