
Cybersecurity Challenges in Critical Infrastructure: A Perspective on
Regulations and Competence in Luxembourg
Maxime Naval, Erik Perjons
a
and Simon Hacks
b
Department of Computer and System Sciences, Stockholm University, Stockholm, Sweden
Keywords:
Critical Infrastructure, Cyber-Security Challenges, Luxembourg, Thematic Analysis.
Abstract:
Critical infrastructure (CI) faces a growing threat of cyber-attacks as digitalization expands across industries,
necessitating robust cyber-security measures. This study focuses on the challenges of securing CI in Luxem-
bourg, exploring both regulatory and organizational aspects. Semi-structured interviews with chief informa-
tion security officers (CISOs) within Luxembourg’s CI sectors were conducted to gather insights. Thematic
analysis revealed six key challenge themes: Regulatory Compliance, Industry Landscape and Adaptation,
Resource Management, External Collaboration and Support, IT Infrastructure Management, and Operational
Governance. The findings underscore the need for a comprehensive, multi-faceted approach involving inter-
national regulation alignment, streamlined reporting, enhanced national cyber-security support, government
initiatives, and ongoing harmonization efforts across nations to address cyber-security challenges in critical
infrastructure effectively.
1 INTRODUCTION
Critical infrastructure (CI) can be defined as “the
body of systems, networks, and assets that are so es-
sential that their continued operation is required to
ensure the security of a given nation, its economy,
and the public’s health and/or safety” (Grigalashvili,
2022). Examples of CI are systems, networks, and
assets in energy supply, telecommunications, trans-
portation, water and wastewater management, health-
care, finance, emergency and security services, and
digital infrastructure. Cyber-attacks targeting CI can
devastate nations and their citizens (Riggs et al.,
2023). Therefore, ensuring CI security against cyber
threats is paramount.
Recent trends indicate a rise in cyber-attacks
on critical infrastructure (Serpanos and Komninos,
2022), prompting various sectors of society to en-
hance their cybersecurity measures for defense.
While larger European countries have been dealing
with significant cyber-attacks on CI for many years,
Luxembourg, which is in focus in this study, has only
recently been the victim of such targets (Creos, 2022;
Kollwelter, 2022).
Governments and international organizations have
a
https://orcid.org/0000-0001-9044-5836
b
https://orcid.org/0000-0003-0478-9347
proposed new legislation and regulations for securing
CI. For instance, the recently adopted NIS2 directive
by the EU mandates all EU member states to integrate
its provisions into national law (European Parliament
and the Council of the European Union, 2022). As
a result, all EU member states are required to imple-
ment this new directive into national law. The new
legislation builds on the first NIS directive, adopted
in 2016 (European Parliament and the Council of the
European Union, 2016). Further, NIS2 broadens the
definition of CI sectors, thus increasing the number of
societal actors affected by these changes. Challenges
may arise during implementation in various CI sec-
tors under this new legislative environment due to the
added complexity of coordinating efforts between or-
ganizations and government agencies (Kshetri, 2015;
Peters, 2018; Laegreid et al., 2015).
Digitalization has increased the interconnections
between IT systems across industries, escalating the
complexity of managing IT assets. However, the
human resources required to oversee IT infrastruc-
ture have not always kept pace with this growing de-
mand (Gurpree et al., 2019). Today, nearly every em-
ployee interacts with some form of IT system to per-
form their work tasks, which amplifies overall vul-
nerabilities. Consequently, organizations are increas-
ingly focusing on training personnel to mitigate cyber
incidents. The effectiveness of these efforts, however,
Naval, M., Perjons, E. and Hacks, S.
Cybersecurity Challenges in Critical Infrastructure: A Perspective on Regulations and Competence in Luxembourg.
DOI: 10.5220/0013091500003899
In Proceedings of the 11th International Conference on Information Systems Security and Privacy (ICISSP 2025) - Volume 1, pages 15-26
ISBN: 978-989-758-735-1; ISSN: 2184-4356
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
15

largely depends on the available resources and the in-
ternal business culture (Sohrabi Safa et al., 2015).
Within an organization, these challenges are usu-
ally managed by the chief information security officer
(CISO). The CISO is tasked with devising and execut-
ing the organization’s information security strategy
and overseeing its cyber-security operations (May-
nard et al., 2018). In the rapidly evolving technolog-
ical landscape impacting CI, CISOs face new chal-
lenges involving managing increasing IT assets and
implementing regulatory requirements. Adequate fi-
nancial and human resources are crucial for CISOs to
successfully fulfill this mission, representing the pri-
mary constraints to achieving robust information se-
curity (Johnson and Goetz, 2007).
Accordingly, this paper investigates cyber-
security vulnerabilities and regulations in CI and
issues related to human competence, focusing on
Luxembourg. Therefore, we will answer the fol-
lowing research question: What are the challenges
associated with implementing cybersecurity measures
in critical infrastructure, and which are the potential
solutions to address them?
The rest of the paper is structured as follows. First,
we overview common cybersecurity vulnerabilities in
CI. Next, we examine EU legislation addressing these
vulnerabilities. Then, we present a qualitative analy-
sis of interviews with Luxembourg’s CI CISOs, high-
lighting challenges and solutions for implementing
cybersecurity measures. Finally, we discuss the re-
sults’ implications and suggest future research direc-
tions.
2 BACKGROUND
2.1 Cyber-Security Vulnerabilities in
Critical Infrastructure
Most industries have fully embraced digital transfor-
mation in recent years, making the business world in-
creasingly reliant on a highly intricate network of in-
terconnected technologies. This digital transforma-
tion has also extended to CI, where information and
communication technologies (ICT) have enhanced ef-
ficiency and flexibility. Integrating advanced comput-
ing and industrial automation has contributed to in-
creased output. Additionally, these advancements en-
able predictive and remote maintenance, addressing
issues before they escalate into more costly problems
that could lead to severe outages (Antova, 2020).
Implementing ICT has brought numerous benefits
to daily operations in CI, including real-time remote
maintenance and monitoring, system interconnectiv-
ity, and enhanced communication with external net-
works. However, these advancements have also intro-
duced new attack vectors (Stergiopoulos et al., 2020).
Recent trends show a concerning rise in cyber-attacks
on CI, with significant implications for affected states.
For example, in Germany, the Federal Office for In-
formation Security (BSI) reported 452 cyber-security
incidents affecting CI in 2022. However, many inci-
dents are believed to go unreported due to concerns
about reputational damage (Bundesamt f
¨
ur Sicher-
heit in der Informationtechnik, 2022). The estimated
damage from cyber-attacks on CI in the same year
amounted to over 200 billion euros in Germany (Beil,
2023).
Although tools are essential to a cyber-security
strategy within CI, human resources remain the most
crucial security component (Alessandro et al., 2020).
In a security context, human error can be defined us-
ing the insider anomaly concept, distinguishing un-
intentional, intentional, and malicious human errors.
Unintentional human error arises from a lack of or-
ganized information or operational skills, which can
lead to inadvertent mistakes. This type of error may
persist as unintentional or evolve into intentional or
malicious actions. Intentional human error occurs
when a user knowingly engages in risky activities or
misuses resources. While these actions may not im-
mediately impact the organization, they can poten-
tially violate privacy rights or other regulations. The
most severe form of human error involves deliberate
actions aimed at causing harmful consequences (Ait
Maalem Lahcen et al., 2020). The level of exposure to
IT systems varies according to each role. Still, in to-
day’s highly digitalized work environment, every em-
ployee poses a potential vulnerability within the over-
all cyber-security strategy.
Different reports estimate that 82 % to 95 % of or-
ganizational data breaches can be attributed to human
error (Verizon, 2022; Tessian, 2020; World Economic
Forum, 2022). The most common vectors involving
a human factor in cyber-security incidents are phish-
ing attacks, misuse of credentials, and scans and ex-
ploits (IBM Security, 2023). Another crucial aspect
of human error is evident in incident response. Upon
discovering an incident, executing a well-defined re-
sponse plan that adheres to internal cyber-security
policies and procedures is essential. The absence of
such policies can result in delayed responses to alerts,
inadequate adherence to incident response protocols,
or errors during the investigation phase, all of which
increase security risks.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
16
2.2 European Cyber-Security
Legislation
The NIS2 directive (European Parliament and the
Council of the European Union, 2022) broadens
objectives and scope of applicability compared to
NIS1. NIS2 imposes new cyber-security obligations
on companies, state-owned enterprises, and public au-
thorities in critical sectors across the EU, which are
vital to the economy and society. Additionally, NIS2
extends coverage to include medium-sized and large
institutions that NIS1 does not fully cover. The di-
rective mandates enhanced requirements for cyber-
security risk management measures and reporting
obligations in response to online attacks and result-
ing data breaches. This includes audit requirements,
risk assessments, and timely installation of updates
and certifications.
The Cyber-security Act (European Parliament
and the Council of the European Union, 2019) was in-
troduced in 2017 as part of a comprehensive package
of measures to enhance cyber-security and strengthen
resilience against cyber-attacks by the EU. It poses an
EU framework for IT security certification of prod-
ucts, services, and processes while considering their
criticality.
The Cyber Resilience Act (European Commis-
sion, 2022) aims to complement the NIS2 directive
by regulating connected devices, which have garnered
attention due to their security vulnerabilities. Many
manufacturers of these products have been found to
prioritize cost, or lack sufficient expertise in cyber-
security. This could lead to vulnerabilities that expose
sensitive personal data to malicious hackers or facili-
tate other cyber attacks too easily.
2.3 Cyber-Security in Luxembourg
ENISA, the European Union Agency for Cybersecu-
rity, serves as a coordinator at the European level.
ENISA provides expert network and information se-
curity advice to national authorities and EU institu-
tions. It also acts as a forum for exchanging best
practices and facilitates communication between EU
institutions, public authorities, and organizations.
On a national level, Luxembourg established the
High Commission for National Protection (HCPN) in
2016, effectively serving as the National Agency for
Information Systems Security. The HCPN’s primary
mission includes issuing recommendations for imple-
menting information security policies and guidelines
to government agencies. It also plays a crucial role in
supporting the implementation of the State’s general
information security policy. Upon request, the HCPN
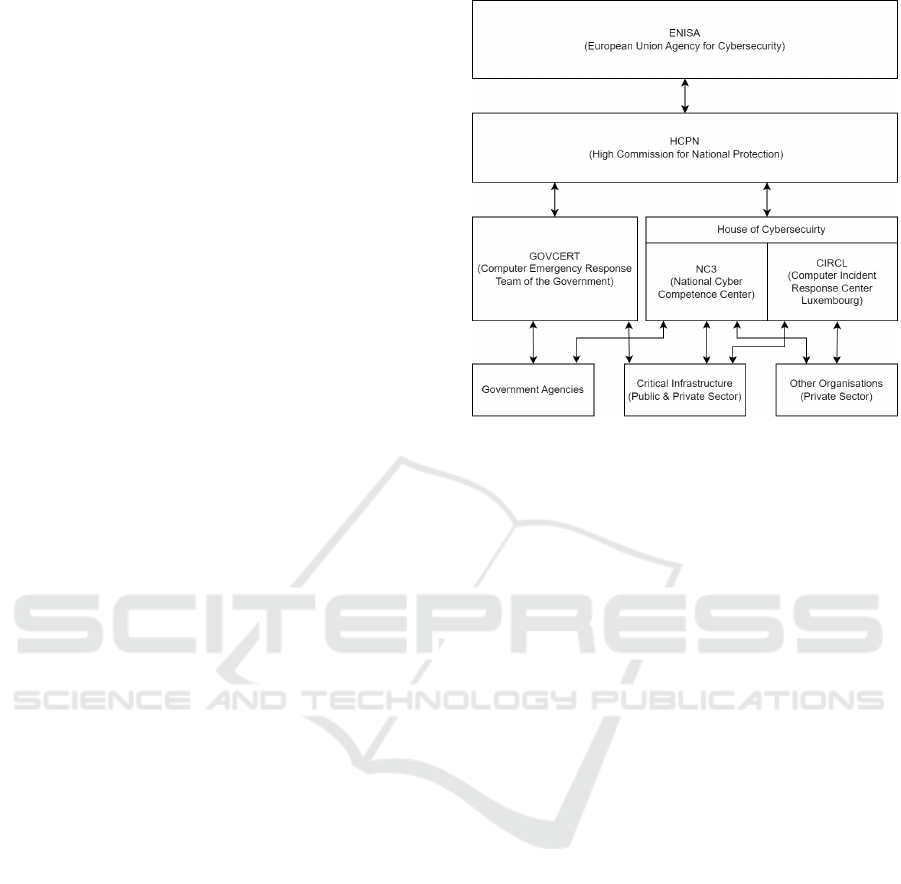
Figure 1: Hierarchical Model of the Coordination between
Entities in Luxembourg.
advises public agencies and critical infrastructure (CI)
institutions on network and information system secu-
rity and associated risks (Haut-Commissariat
`
a la pro-
tection nationale, 2023).
Figure 1 illustrates the organizational structure
of cyber-security entities in Luxembourg. Under
the HCPN, the Governmental Computer Emergency
Response Team (GOVCERT) manages incidents for
government agencies and selected CI institutions
within both public and private sectors (CERT gov-
ernmental Luxembourg, 2023). The Computer Inci-
dent Response Center Luxembourg (CIRCL) handles
incidents from non-CI private sector entities. Both
CIRCL and the National Cyber Competence Center
(NC3) operate under the Luxembourg House of Cy-
bersecurity, serving as a cornerstone for advancing
cyber resilience in Luxembourg. The Luxembourg
House of Cybersecurity fosters innovation, enhances
competencies, and promotes collaboration across all
societal levels (Luxembourg House of Cybersecurity,
2023).
The coordination among these cyber-security
agencies and stakeholders in Luxembourg is articu-
lated in the current 4th national cyber-security strat-
egy, covering the period up to 2025 as published by
the Luxembourgish Government. This strategy out-
lines guidelines and initiatives to enhance cyber-space
security through coordinated efforts among stake-
holders (Cybersecurity Luxembourg, 2020).
Cybersecurity Challenges in Critical Infrastructure: A Perspective on Regulations and Competence in Luxembourg
17

2.4 Related Work
(Teixeira et al., 2019) conducted a systematic litera-
ture review of 32 studies to identify critical success
factors in implementing GDPR. Their findings reveal
that GDPR compliance is frequently intricate and sub-
jective, leading to extensive and time-consuming pro-
cesses. The study underscores the substantial finan-
cial and human resources required for effective im-
plementation, highlighting challenges stemming from
a lack of privacy knowledge and expertise.
Another relevant literature review by (Hussain
et al., 2020), analyzed 33 articles to delineate cyber-
security challenges and emerging threats. The review
emphasizes the significance of comprehending how
these challenges are perceived and tackled, especially
within cyber-security. Identified challenges encom-
pass cyber-security governance, robust risk manage-
ment practices, and promoting a culture of aware-
ness. Effective governance is essential for organiza-
tions handling critical global data, providing a secure
operational framework.
While raising awareness is crucial in cybersecu-
rity, the effectiveness of training can vary significantly
depending on its format and approach. (Chowdhury
and Gkioulos, 2021) analyzed 68 articles to assess
the effectiveness of cyber-security training in CI sec-
tors. Their findings indicate that hands-on training
in team-based scenarios, often using simulation and
virtualization platforms, is among the most effective
methods. However, they also noted a lack of consen-
sus among researchers regarding the optimal train-
ing solutions. A significant barrier to implementing
cyber-security training is the insufficient allocation of
resources, and the associated costs (Chowdhury and
Gkioulos, 2021).
The results of these literature review studies were
also found in more focused research papers exam-
ining CI. In the water sector, incidents often stem
from inadequate security skills and insufficient train-
ing (Amin et al., 2020). Similarly, the healthcare sec-
tor faces cybersecurity challenges exacerbated by lim-
ited budget allocations for cyber-security measures
(Javaid et al., 2023). Additionally, the lack of support
from executive management, who control budgets and
policies, poses a critical obstacle (Chaudhary et al.,
2023).
(Rawindaran et al., 2023) explore the cyber-
security challenges of Wales’s small and medium en-
terprises (SMEs). They highlight that government cy-
bersecurity policies and regulations often cater more
to large organizations, leaving SMEs struggling to
properly adopt policies within their sector or comply
with regulatory requirements. Given that the Luxem-
bourgish government and its critical infrastructure or-
ganizations can be classified as SMEs, this study aims
to extend Rawindaran et al.’s research by providing an
international perspective.
Makrakis et al. (Makrakis et al., 2021) provide an
in-depth analysis of vulnerabilities and attacks target-
ing critical infrastructures, highlighting the increased
risks introduced by integrating operational technol-
ogy with modern IT frameworks. Their work em-
phasizes the complexities of defending aging sys-
tems against modern cyber threats. In a comple-
mentary study, Kampourakis et al. (Kampourakis
et al., 2023) conduct a systematic review of wireless
security testbeds in cyber-physical systems (CPS),
addressing the dual challenges of leveraging wire-
less technologies for flexibility and mitigating the ex-
panded attack surface they create. Their findings un-
derscore the need for modular and robust testbed ar-
chitectures to enhance CPS security research.
The contribution of this article is distinguished
from the other works mentioned in related research
by its focus on the specific context of Luxembourg’s
critical infrastructure (CI) cybersecurity challenges,
particularly from a regulatory and organizational per-
spective. Unlike previous studies, such as (Teixeira
et al., 2019), which examined the broader challenges
of implementing GDPR across multiple sectors, or
(Hussain et al., 2020), which explored general cyber-
security challenges and governance issues, this study
provides a localized and detailed analysis of Luxem-
bourg’s unique cybersecurity landscape. It builds on
existing frameworks but dives deeper into how regu-
lations like the NIS2 directive are being interpreted
and applied in Luxembourg’s CI sectors, and how
the country’s smaller size and resource limitations af-
fect the ability of CISOs to implement cybersecurity
measures effectively. The article further expands on
(Rawindaran et al., 2023) by offering insights into the
international and European harmonization challenges
faced by Luxembourg, a country with a comparatively
lower IT maturity level, adding valuable localized in-
sights to the global discourse on CI cybersecurity.
3 METHOD
We opted for a survey research strategy (Denscombe,
2021) to answer the research question. The survey al-
lowed for the exploration of the perceptions of CISOs
in various CI sectors across Luxembourg, provid-
ing rich insights into their perspectives on regulatory
and organizational challenges related to cybersecu-
rity. The semi-structured interview approach was se-
lected to enable participants to share their experiences
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
18

and opinions flexibly and in-depth, capturing the nu-
ances of cybersecurity implementation.
Participant selection involved purposive sampling,
where CISOs from different CI sectors defined by
the NIS2 directive were contacted. The goal was to
ensure representation from sectors such as financial,
healthcare, energy, communications, and wastewater
treatment. Seven CISOs agreed to participate, offer-
ing a diverse yet focused sample size. Despite the
limited number of participants, including key sec-
tors, valuable insights into the cybersecurity chal-
lenges specific to Luxembourg’s CI landscape were
provided.
The data collection process involved semi-
structured interviews conducted via Zoom and MS
Teams, lasting between 30 and 45 minutes to accom-
modate the busy schedules of CISOs. Interviews were
conducted in English, French, and Luxembourgish,
depending on the participant’s preference, which ne-
cessitated translation and transcription. The questions
(cf. Appendix) were designed around two main areas:
organizational aspects, which included collaboration
and external partnerships, and regulatory aspects, fo-
cusing on compliance, legislation, and resource man-
agement.
Data analysis was conducted using thematic anal-
ysis (Denscombe, 2021). This method involved mul-
tiple stages, including familiarization with the data,
coding, and theme development. In the initial coding
phase, 197 codes were identified. Through an iter-
ative process, redundant or overlapping codes were
refined and rephrased, resulting in 165 codes. These
codes were then grouped into broader themes aligned
with the study’s focus on regulatory compliance, re-
source management, industry landscape adaptation,
and external collaboration.
4 RESULTS
The thematic analysis resulted in six main themes and
their sub-themes (cf. Figure 2), which will be ex-
plained below. Moreover, challenges and, in some
cases, solutions were identified for each sub-theme.
Cited statements have been paraphrased and trans-
lated into English.
4.1 Regulatory Challenges and
Compliance
Different National Transpositions: The European
Directives NIS1 and NIS2 require implementation
into national legislation. However, participants
noted that interpretations of these directives can vary
among member states. Differences in the expertise
of national regulatory bodies significantly influence
these interpretations. One participant highlighted
that Luxembourg generally has a lower IT maturity
level than Anglo-Saxon countries, impacting various
sectors and organizations, and posing challenges in
interactions with regulatory bodies. Two participants
also mentioned that varying business process require-
ments complicate collaboration with international
partners. For example, one participant stated, “...
we have partners in Germany or France, which
have different processes, which make collaboration
difficult.”
Extra-European Markets: While most partici-
pants advocated for greater harmonization within
the European market, two participants highlighted
challenges related to operations outside the European
Market, the so-called extra-European markets. This
can lead to significant resource constraints because
companies operating in extra-European markets
must ensure compliance with diverse regulatory
requirements across multiple jurisdictions. One
participant stated, ”Since we operate in the EU and
US markets, we sometimes find ourselves running
compliance audits for different regulatory entities in
both markets, which requires a lot of time and effort.”
Therefore, two participants expressed a desire for
more international harmonization of regulation.
Cloud-Related Compliance Issues: The adoption
of cloud solutions continues to rise across all sectors,
driven by their potential to enhance operational
efficiency and increase value generation. However,
one participant highlighted a significant concern:
“There are not many players around, and the biggest
ones are all American and do not meet all the
regulatory requirements imposed by the EU.” A
prominent example is the recently enacted Cloud
Act by the US (115th Congress of the United States,
2018), which requires US companies to grant US
intelligence agencies access to their data. This
mandate contradicts EU privacy laws and prohibits
personal data transfer from EU users to the US. As
the EU and the US negotiate new agreements, Euro-
pean organizations may face challenges where they
cannot avoid using certain business solutions without
compromising regulatory compliance: ”If you take
Office365 or M365 as an example, most organiza-
tions have no way around these solutions, yet these
cloud solutions are not completely GDPR compliant.”
Financial Penalties: Financial penalties can be
imposed on organizations for non-compliance with
Cybersecurity Challenges in Critical Infrastructure: A Perspective on Regulations and Competence in Luxembourg
19

Figure 2: Thematic Analysis Results.
regulations, adding extra pressure on cyber-security
and compliance teams, according to two participants,
and is expressed in the following way by one of
them: ”The risk of being fined add pressure to
decision-makers, which ultimately is passed on to the
team and increases the stress.” Another participant
noted that this enforcement of regulations is ”unfor-
tunately necessary as it is sometimes the only way
to compel decision-makers within an organization to
take appropriate action.”
4.2 Industry Landscape and Adaptation
Increasingly Complex Environment: Two par-
ticipants highlighted a growing concern over
cyber-attacks targeting infrastructure, stressing the
urgency as malicious actors exploit vulnerabilities.
These threats are becoming more sophisticated,
using advanced techniques that require constant
vigilance. CI systems have also become increasingly
interconnected, facing greater complexity in cyber-
security, exposing them to multiple threat vectors.
Additionally, two participants noted the rapid intro-
duction of new regulations, which demand significant
resources for assessment and implementation. The
interconnected nature of CI sectors also raises the
risk of cascading disruptions. Therefore, operators
must balance the imperative to modernize their
systems with the need to secure them effectively, en-
suring the stability and resilience of essential services.
Aligning IT and Business Strategies: Aligning IT
with business strategies presents significant cyber-
security challenges. Both areas must work closely
to ensure that technology projects align with overall
organizational objectives, as stressed by two partic-
ipants. Two participants also mentioned difficulties
in gaining organizational decision-makers’ support
for such alignment, although one did not face this
issue. One participant emphasized the need to foster
a collaborative culture and improve communication
to secure support from decision-makers. Further-
more, two participants highlighted the importance of
conducting regular risk assessments and integrating
security measures into strategic planning. This
helps to ensure that IT and business strategies work
together effectively.
Talent Acquisition Challenges: Two participants
highlighted that the IT industry’s growing complexity
and rapid adoption of new technologies necessitate or-
ganizations to recruit new personnel for project man-
agement and robust cyber-security operations. Fur-
thermore, investments in training and upskilling ex-
isting staff are crucial to adapt to the evolving threat
landscape. However, the participants identified three
key challenges in talent acquisition. First, specific
technologies require rare skill sets that are challeng-
ing to find in the market. Secondly, the field of cyber-
security is expanding rapidly, leading to a general
shortage of professionals. Thirdly, even when talent
is available in the Luxembourg job market, organiza-
tions struggle to meet or sustain competitive salary
expectations, making it difficult to attract and retain
skilled professionals. As stated by one participant:
”Some experts are very hard to come by, and even
when you find them, it is not easy to make them an
offer that they accept.” Another participant claimed
that the lack of new talent needs to be tackled on a
national basis.
4.3 Resource Management
Managing Financial Resources: Financial con-
straints pose a significant challenge in achieving
complete cyber-resilience for CI operators. One
participant explained that limited budgets, influenced
by various operational and economic factors, often
hinder their ability to upgrade IT infrastructure or
implement comprehensive protection strategies: ”If
you look at the regulatory requirements, you often
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
20

find yourself wanting to revise your entire infrastruc-
ture, but are limited by budget constraints.” Despite
these constraints, CI operators rely on rigorous risk
assessments to prioritize security initiatives based
on the criticality of assets and potential impact.
According to one participant, balancing investments
in security technologies with maintaining operational
efficiency is an ongoing struggle, exacerbated by
the continuous updates required to defend against
evolving cyber threats, further stretching already tight
financial resources.
Managing Human Resources: Two participants em-
phasized that the CISO role should be part of se-
nior management, enabling easier collaboration with
department supervisors and better integrating cyber-
security strategies into overall business planning.
This structure is common in larger organizations with
dedicated departments for specific tasks due to their
larger staff numbers. However, smaller organiza-
tions cannot create dedicated departments for opera-
tions. Therefore, the individual responsible for cyber-
security in these organizations often handles addi-
tional roles and remains closely involved in daily IT
operations, not solely focused on security tasks: ”We
are a small team, where it is not feasible to dedi-
cate the supervision of information security to a single
role.”
4.4 External Collaboration and Support
Collaboration with National Security Agencies:
The level of guidance from national security agen-
cies varied significantly. Participants wanted more
information sharing from agencies for assistance
with new regulations and security processes. CIRCL
was the most frequently mentioned partner, cited
by six participants, while GovCert, HCPN, and
ENISA were each named by four. The amount and
frequency of information exchanged also varied.
CIRCL was noted for its assistance with security
processes and best practices. One participant re-
ceived regular vulnerability updates from CIRCL
without direct collaboration. GovCert and ENISA
were praised for providing relevant cybersecurity
information, with one organization participating in
an ENISA-led emergency simulation. Two organiza-
tions regularly exchanged information with HCPN,
which oversees process implementations. Next to
the four cybersecurity agencies mentioned above,
the Institut Luxembourgeois de R
´
egulation (ILR)
was also named a frequent exchange partner by six
organizations. As the main regulatory body, the ILR
has been described as overseeing compliance with
regulations and providing some guidance towards
implementation strategies.
Sector-Overlapping Activities: A common concern
among participants was the unclear scope of each
agency. While GovCert handles the public sector and
CIRCL the private sector, both interact with organi-
zations in both areas. Some organizations are state
and privately owned, making it unclear which agency
to contact for assistance: ”Since we are partly public,
partly private, it is not always clear if we fall into
the CIRCL’s or GovCert’s scope, which sometimes
feels like being a second class client for both of them.”
Different Reporting Methods: Six participants re-
ported having to file reports to at least one agency
and facing challenges due to differing reporting meth-
ods. One participant noted that HCPN and ILR re-
quire different risk management approaches, leading
to multiple reports for the same event. Addition-
ally, those operating in multiple sectors must report
to various regulatory bodies using different methods
and deadlines. This process is time-consuming and
resource-intensive. Participants expressed a need for
more harmonization in reporting methods to alleviate
these burdens.
4.5 IT Infrastructure Management
Monitoring: All participants emphasized the neces-
sity of continuous IT infrastructure monitoring to
detect abnormal behavior. This is challenging due
to the complexity of CI operators’ IT environment.
Participants noted that various systems require unique
monitoring approaches and custom adaptations: ”We
have legacy systems that cannot be integrated into
modern monitoring solutions.” Hiring specialized
experts might be necessary but is not always feasible,
often resulting in outsourcing monitoring to external
partners, adding another layer of complexity.
Access Controls: Most participants stated that
they had implemented access controls to prevent
unauthorized users from taking unwanted actions on
their systems. The most common methods for access
control were 2FA authentication, role-based access
control, and data encryption. Participants emphasized
that managing these controls is an ongoing process,
necessitating regular updates. Additionally, two par-
ticipants utilized private intranet networks to shield
internal communications from external interference.
A significant challenge mentioned was the resistance
from end-users, who often viewed these measures as
overly restrictive.
Cybersecurity Challenges in Critical Infrastructure: A Perspective on Regulations and Competence in Luxembourg
21

Legacy Systems: Legacy systems pose significant
challenges due to their susceptibility to modern
threats. They often lack essential security features,
have unpatched vulnerabilities, or use weak authenti-
cation methods. Participants also noted that monitor-
ing these systems is not always feasible. However,
migration projects are complex, costly, and some-
times impractical, making it difficult for organizations
to comply with regulatory requirements.
4.6 Operational Governance
Ensuring Business Continuity: Most participants
emphasized the need for a business continuity plan,
noting that the constantly changing environment
requires frequent risk re-evaluations. Additionally,
testing and training are crucial for validating a plan’s
effectiveness. Two participants mentioned recent re-
silience tests simulating large-scale attacks to assess
the crisis management team’s response and process
robustness, with one test conducted in coordination
with ENISA. Four participants stated they were using
the ISO/IEC 27000 international standard, while one
mentioned employing the ISA/IEC 62433 standard
within their organization.
User Awareness Training: All participants reported
using user awareness training. A common strategy
involves targeted phishing campaigns, where a
user’s failure to detect a phishing email leads to
mandatory training for the user. Participants also
discussed other training methods designed to raise
awareness of cybersecurity threats, often tailored to
specific organizational roles. Various training formats
include group seminars, individual conversations,
and e-learning platforms. A common challenge is
that not all users are comfortable with technology,
and cybersecurity can be perceived as dull, making it
difficult to motivate staff to learn best practices. One
participant mentioned that gamification techniques
helped engage users in cybersecurity training. An-
other emphasized the importance of explaining the
reasons behind certain restrictions and processes to
users, noting that transparent and open communica-
tion enhances acceptance of cybersecurity practices
within the organization.
Managing External Service Providers: Organiza-
tions face significant challenges managing cyberse-
curity risks from third-party service providers. The
primary approach is written contracts, including data
protection clauses and sometimes detailed processes
to ensure cyber resilience. A major challenge is the
limited control over external providers’ security prac-
tices. Three participants implemented screening or
auditing processes to mitigate risks, though these can
be time-consuming. One participant noted that while
robust contracts are essential, they can be challenging
to execute due to disagreements over responsibilities,
prolonging negotiations, and increasing costs.
5 DISCUSSION
This section discusses the findings from six themes
presented in the previous section and relates the find-
ings to previous research. The first theme, the regula-
tory challenges and compliance, focused on the com-
plex regulatory landscape for CI operators in Lux-
embourg due to varying interpretations and compli-
ance requirements of European Directives like NIS1
and NIS2 across member states. Participants noted
that some regulatory bodies excel in specific domains
but not necessarily in IT, leading to inconsistent com-
pliance and confusion. This issue aligns with previ-
ous research by Rawindaran et al., suggesting sector-
specific support from government entities for cyberse-
curity strategies (Rawindaran et al., 2023). The glob-
alization of IT infrastructure, including cloud solu-
tions, further complicates compliance, exposing orga-
nizations to varied requirements that can conflict with
European and foreign regulations. This necessitates
international agreements to harmonize regulations.
The second theme, industry landscape and adapta-
tion, emphasized the constantly evolving cyber threat
landscape, posing significant challenges to CI oper-
ators. Increased sophistication of attacks and inter-
connected systems require continuous vigilance and
adaptation. This underscores the need for costly cy-
bersecurity measures to ensure the resilience of es-
sential services. Participants highlighted the difficulty
in aligning cybersecurity initiatives with business pri-
orities and gaining decision-makers support, empha-
sizing the need for enhanced cybersecurity awareness
within organizations and society. Government ini-
tiatives and campaigns can also help increase public
awareness and build a cyber-resilient society. Chaud-
hary et al. previously highlighted the challenges
in gaining decision-makers support for cybersecurity
initiatives (Chaudhary et al., 2023). Moreover, Lux-
embourg’s high cost of living has made talent acqui-
sition difficult despite traditionally high salaries at-
tracting global talent. Participants noted the struggle
to find cybersecurity experts due to unmatched salary
expectations.
The third theme, resource management, relates to
the challenges in managing internal resources. Lim-
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
22

ited budgets and operational constraints necessitate
careful resource allocation, balancing investment in
advanced security technologies with maintaining op-
erational efficiency. Human resource management is
also critical, with varying degrees of CISO detach-
ment from daily IT operations. Larger organizations
favor more detachment, while smaller ones face lim-
ited personnel and operational demands. These find-
ings correlate with previous research on resource con-
straints and the need for strategic allocation (Hussain
et al., 2020; Javaid et al., 2023; Chaudhary et al.,
2023).
The fourth theme, external collaboration and sup-
port, concerns collaboration with national cybersecu-
rity agencies and other entities. Collaboration is vital
but varied, with overlapping responsibilities between
agencies like CIRCL and GovCert creating confusion
and hindering efforts. Different reporting methods
imposed by agencies lead to inefficiencies, highlight-
ing the need for harmonization. Previous research
supports these findings, noting that new regulations
have increased administrative work (Gonc¸alo et al.,
2019). Overall, improved communication from na-
tional security agencies is needed to support CI oper-
ators effectively.
The fifth theme addresses the challenges in man-
aging IT infrastructure. Effective management is es-
sential for detecting anomalies and safeguarding criti-
cal systems, but the complexity of CI IT environments
and resource constraints pose significant challenges.
Customized monitoring solutions and the need for
specialized expertise often lead to outsourcing, in-
creasing costs. Centralizing monitoring operations in
the public sector could reduce the resource burden on
individual organizations and improve efficiency.
The last theme, operational governance, is the
evolving threat landscape, necessitating regular re-
evaluation of risks and resilience strategies, includ-
ing implementing business continuity plans. Par-
ticipants strive to adhere to cybersecurity standards
like ISO/IEC 27000 or ISA/IEC 62433. User aware-
ness training is also crucial, with tailored programs
and transparent communication enhancing engage-
ment and understanding. While previous studies
suggested government-provided training for the gen-
eral population, such initiatives are already in place
in Luxembourg. Participants emphasized explain-
ing new decisions and processes to all end-users
to increase awareness and satisfaction, fostering a
healthy cybersecurity culture. Managing external ser-
vice providers through contracts and agreements is
common, but ensuring alignment with organizational
standards remains challenging. Screening and audit-
ing processes could mitigate risks but can also be
resource-intensive.
This analysis highlights the multifaceted chal-
lenges CI operators face in Luxembourg and the need
for strategic approaches to enhance cybersecurity re-
silience.
6 CONCLUSIONS
Revisiting the research question ”What are the chal-
lenges associated with implementing cybersecurity
measures in critical infrastructure, and what poten-
tial solutions exist to address them?”, we identified
six distinct challenges. Addressing these requires
a multifaceted approach, including regulation har-
monization, talent development, resource optimiza-
tion, streamlined reporting methods, and a continuous
commitment to enhancing cybersecurity practices.
A short- to medium-term solution involves reduc-
ing the impact of new regulations on already over-
stretched CI operators. This can be achieved by
streamlining reporting to a single method used by all
regulators and increasing support from national cy-
bersecurity agencies. Redefining the precise scope of
activities for these agencies and improving their abil-
ity to assist CI operators would enhance collabora-
tion, reduce resource strain, and increase efficiency.
Additionally, recognizing that organizations and reg-
ulatory agencies alone cannot solve national cyber-
resilience. Therefore, government initiatives must ad-
dress labor market challenges and increase public cy-
bersecurity awareness.
At the European and international levels, regula-
tors should gather feedback on regulatory challenges
faced by CI operators to revise and adapt legislation as
necessary. Continued efforts to harmonize regulations
across nations will simplify operational activities for
CI operators.
One can argue that the interviewee’s statements
are ”common sense.” However, they provide a lo-
calized and context-specific understanding of Lux-
embourg’s critical infrastructure cybersecurity chal-
lenges. While certain observations, such as the im-
portance of regulatory compliance or the need for ad-
equate resources, may seem self-evident, they are still
relevant in Luxembourg’s unique regulatory and or-
ganizational landscape. The insights from the inter-
views help illustrate how general cybersecurity prin-
ciples manifest in real-world scenarios, particularly in
smaller nations with limited resources and complex
international regulatory demands. By contextualiz-
ing ”common sense” observations within the specific
challenges faced by CISOs in Luxembourg, the study
bridges the gap between theoretical knowledge and
Cybersecurity Challenges in Critical Infrastructure: A Perspective on Regulations and Competence in Luxembourg
23

practical implementation, offering valuable lessons
for policymakers and CI operators, particularly in
similar-sized nations or regions navigating similar cy-
bersecurity landscapes.
The study’s validity depends on accurate data col-
lection, but the subjective nature of thematic analy-
sis introduces the possibility of interpretation bias.
Despite using techniques like member checking, the
findings may be influenced by participants’ articula-
tion and the researcher’s interpretation. Participants
received copies of their transcripts for validation.
Interpretation subjectivity challenges qualitative
research reliability. Efforts were made to ensure that
the inherent subjectivity of qualitative analysis hin-
ders accurate translations but perfect consistency. The
study’s findings, limited by sample size and partic-
ipant demographics, may not be broadly applicable.
Replicating interview conditions precisely is difficult
due to the dynamic nature of human interactions. Ex-
tending results to diverse populations should be done
cautiously, recognizing these limitations for future re-
search.
Future research could expand into more detailed
analysis by studying an entire strategy implementa-
tion process within a selected organization, identify-
ing internal challenges more precisely through inter-
views or questionnaires at various hierarchical levels.
Another valuable area of research would be to inves-
tigate national cybersecurity agencies in more detail
to identify national coordination problems. Replicat-
ing similar research in other European countries could
reveal common challenges and potentially offer new
solutions for foreign organizations or governments to
implement.
REFERENCES
115th Congress of the United States (2018). Clarifying
Lawful Overseas Use of Data (CLOUD) Act. Pub-
lic Law No: 115-141. https://www.congress.gov/bill/
115th-congress/house-bill/4943.
Ait Maalem Lahcen, R., Caulkins, B., Mohapatra, R., and
Kumar, M. (2020). Review and insight on the be-
havioural aspects of cybersecurity. Cybersecurity,
3(10).
Alessandro, A., Fabio, N., and Giulia, P. (2020). Under-
standing the management of cyber resilient systems.
Computers & Industrial Engineering, 149:1–18.
Amin, H., Amin, R., Stefano, G., Mohsen, A., Riccardo,
T., Avi, O., and Katherine, B. (2020). A review of
cybersecurity incidents in the water sector. Journal of
Environmental Engineering, 146(5).
Antova, G. (2020). Wie k
¨
onnen wir die digitalisierung
der kritischen infrastrukturen sicher gestalten?
https://digitaleweltmagazin.de/wie-koennen-wir-die-
digitalisierung-der-kritischen-infrastrukturen-sicher-
gestalten/. Accessed: 2024-04-12.
Beil, L. (2023). Kritische infrastruktur in gefahr? https://
www.tagesschau.de/wissen/technologie/infrastruktur-
cybersicherheit-cyberattacken-101.html. Accessed:
2024-04-12.
Bundesamt f
¨
ur Sicherheit in der Informationtechnik (2022).
Die lage der it-sicherheit in deutschland 2022. Tech-
nical report, Bundesamt f
¨
ur Sicherheit in der Informa-
tiontechnik, Berlin.
CERT governmental Luxembourg (2023). Govcert. https:
//www.govcert.lu/en/. Accessed: 2023-05-11.
Chaudhary, S., Gkioulos, V., and Katsikas, S. (2023). A
quest for research and knowledge gaps in cyberse-
curity awareness for small and medium-sized enter-
prises. Computer Science Review, 50.
Chowdhury, N. and Gkioulos, V. (2021). Cyber security
training for critical infrastructure protection: A litera-
ture review. Computer Science Review, 40.
Creos (2022). Le Groupe Encevo victime d’une cy-
berattaque. https://www.creos-net.lu/actualites/
actualites/article/le-groupe-encevo-victime-dune-
cyberattaque.html. Accessed: 2023-05-28.
Cybersecurity Luxembourg (2020). National cybersecu-
rity strategy iv (ncss iv). https://www.cybersecurity.
lu/strategy. Accessed: 2023-05-11.
Denscombe, M. (2021). The Good Research Guide. Open
University Press, New York.
European Commission (2022). Proposal for a regulation
of the european parliament and of the council on
horizontal cybersecurity requirements for prod-
ucts with digital elements (cyber resilience act).
https://eur-lex.europa.eu/resource.html?uri=cellar:
864f472b-34e9-11ed-9c68-01aa75ed71a1.0001.02/
DOC
1&format=PDF. Accessed: 2024-04-12.
European Parliament and the Council of the European
Union (2016). Directive concerning measures for a
high common level of security of network and infor-
mation systems across the union. Official Journal of
the European Union. Directive (EU) 2016/1148.
European Parliament and the Council of the European
Union (2019). Regulation (eu) 2019/881 of the eu-
ropean parliament and of the council of 17 april 2019
on enisa (the european union agency for cybersecu-
rity) and on information and communications technol-
ogy cybersecurity certification and repealing regula-
tion (eu) no 526/2013 (cybersecurity act). https://eur-
lex.europa.eu/eli/reg/2019/881/oj. Accessed: 2024-
04-12.
European Parliament and the Council of the European
Union (2022). Directive on measures for a high com-
mon level of cybersecurity across the union, repealing
directive (eu) 2016/1148. Official Journal of the Eu-
ropean Union. Directive (EU) 2022/2555.
Gonc¸alo, A. T., Miguel, M. d. S., and Ruben, P. (2019). The
critical success factors of gdpr implementation: a sys-
tematic literature review. Digital Policy, Regulation
and Governance, 21(4).
Grigalashvili, V. (2022). The essence of critical infrastruc-
ture in the european union, nato and g7 countries.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
24

International Journal of Innovative Technologies in
Economy, (1(37)).
Gurpree, D., Smith, K., and Hedstr
¨
om, K. (2019). Ensur-
ing Core Competencies for Cybersecurity Specialists,
volume 7, pages 121–133.
Haut-Commissariat
`
a la protection nationale (2023).
Agence nationale de la s
´
ecurit
´
e des syst
`
emes
d’information (anssi). https://hcpn.gouvernement.lu/
fr/service/attributions/missions-nationales/anssi.html.
Accessed: 2023-05-13.
Hussain, A., Mohamed, A., and Razali, S. (2020). A review
on cybersecurity: Challenges & emerging threats. In
Proceedings of the 3rd International Conference on
Networking, Information Systems & Security, pages
1–7.
IBM Security (2023). Ibm security x-force threat intelli-
gence index 2023. Technical report, IBM Security.
Javaid, M., Haleem, A., Singh, R. P., and Suman, R. (2023).
Towards insighting cybersecurity for healthcare do-
mains: A comprehensive review of recent practices
and trends. Cyber Security and Applications, page
100016.
Johnson, M. E. and Goetz, E. (2007). Embedding informa-
tion security into the organization. IEEE Security &
Privacy, 5(3):16–24.
Kampourakis, V., Gkioulos, V., and Katsikas, S. (2023).
A systematic literature review on wireless security
testbeds in the cyber-physical realm. Computers &
Security, 126:103383.
Kollwelter (2022). Cyberattack op 25 wandrieder vun
der firma soler. https://www.rtl.lu/news/national/a/
1876775.html. Accessed: 2023-05-28.
Kshetri, N. (2015). Recent cybersecurity policy initiatives:
Challenges and implications. Computer, 48(7):64–69.
Laegreid, P., Randma-Liiv, T., Rykkja, L. H., and Sarapuu,
K. (2015). Emerging coordination practices of eu-
ropean central governments. International Review of
Administrative Sciences, 81(2):346–351.
Luxembourg House of Cybersecurity (2023). Lux-
embourg house of cybersecurity. https://lhc.lu/
#PageHomeAboutLHC. Accessed: 2023-05-11.
Makrakis, G. M., Kolias, C., Kambourakis, G., Rieger, C.,
and Benjamin, J. (2021). Industrial and critical infras-
tructure security: Technical analysis of real-life secu-
rity incidents. IEEE Access, 9:165295–165325.
Maynard, S. B., Onibere, M., and Ahmad, A. (2018). Defin-
ing the strategic role of the chief information security
officer. Pacific Asia Journal of the Association for In-
formation Systems.
Peters, B. G. (2018). The challenge of policy coordination.
Policy Design and Practice, 1(1):1–11.
Rawindaran, N., Jayal, A., Prakash, E., and Hewage, C.
(2023). Perspective of small and medium enterprise
and their relationship with government in overcom-
ing cybersecurity challenges and barriers in wales. In-
ternational Journal of Information Management Data
Insights, 3(2).
Riggs, H., Tufail, S., Parvez, I., Tariq, M., Khan, M. A.,
Amir, A., Vuda, K. V., and Sarwat, A. I. (2023).
Impact, vulnerabilities, and mitigation strategies for
cyber-secure critical infrastructure. Sensors, 23(8).
Serpanos, D. and Komninos, T. (2022). The cyberwarfare
in ukraine. Computer, 55(7):88–91.
Sohrabi Safa, N., Sookhak, M., Von Solms, R., Furnell, S.,
Abdul Ghani, N., and Herawan, T. (2015). Informa-
tion security conscious care behaviour formation in
organizations. Computers & Security, 53:65–78.
Stergiopoulos, G., Gritzalis, D. A., and Limnaios, E.
(2020). Cyber-attakcs on the oil&gas sector: A sur-
vey on incident assessment and attack patterns. IEEE
Access.
Teixeira, G. A., da Silva, M. M., and Pereira, R. (2019). The
critical success factors of gdpr implementation: a sys-
tematic literature review. Digital Policy, Regulation
and Governance, pages 402–418.
Tessian (2020). The psychology of human error. https:
//www.scribd.com/document/621516208/Tessian-
Research-The-Psychology-of-Human-Error. Presen-
tation.
Verizon (2022). 2022 data breach. https://www.
verizon.com/business/resources/reports/dbir/. Ac-
cessed: 2023-03-02.
World Economic Forum (2022). The global risks report
2022. Technical report, World Economic Forum.
Cybersecurity Challenges in Critical Infrastructure: A Perspective on Regulations and Competence in Luxembourg
25
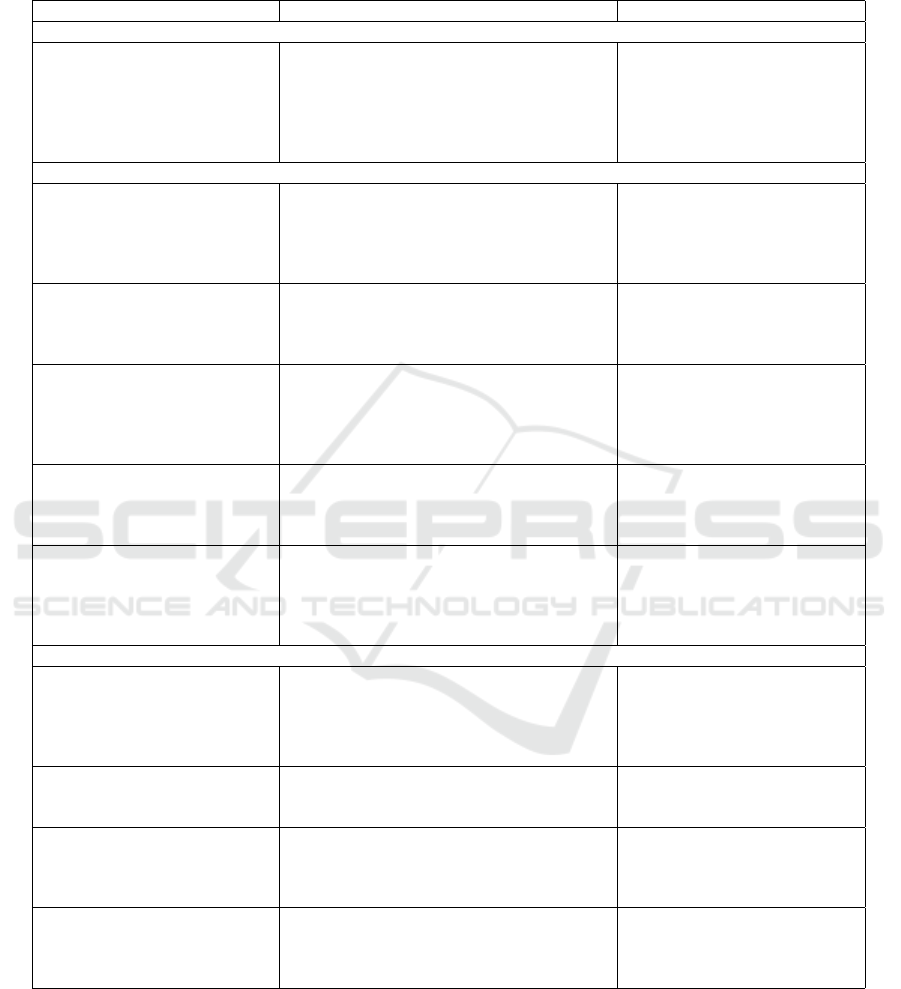
APPENDIX
Table 1.
Question Motivation Hypothesis
Introduction
Tell me about yourself, what is your
background?
How many years of experience do you
have in the industry?
What are your tasks and mission in your
current role?
Introduction question to warm-up and get some more de-
tailed background information about the participants.
All participants have more than 10 years
of experience.
Organisational aspects
How many people work in IT & in what
roles?
Do you have enough personnel? If not,
what would the ideal distribution look
like?
This question aims to address the 12 profiles presented in
the ECSF framework, for which different skills synergies
and interdependencies are presented. These questions
aim to see how organizations are set up compared to the
framework’s examples.
Given the rapidly changing environ-
ment, organizations have difficulties fill-
ing positions and organizing themselves
adequately.
In your opinion, what are the most sig-
nificant organisational challenges that
organizations face when it comes to im-
plementing cybersecurity policies?
This question sets out to investigate where inner hurdles
are faced and what participants regard as the most chal-
lenging aspect.
Many companies lack financial and hu-
man resources to implement policies
properly as demonstrated in relevant lit-
erature.
How do you navigate those challenges
within your organization?
Gather the most significant aspects for a successful im-
plementation from a CISO’s point of view and see if the
same aspects are mentioned between participants.
Given that the NIS2 directive has a
larger scope than NIS1, it is assumed
that already previously affected organi-
sations have a more mature approach to
implementing policies.
How do you keep informed?
What resources do you use?
Find out what communication channels and networks ex-
ist to communicate on these issues and see how many
and what type of sources provide insights to profession-
als.
National cybersecurity entities inform
organizations on a regular basis and help
keep track of ongoing changes and con-
textualize events.
How do you mitigate human error within
your organization?
Are there specific policies, trainings, ac-
cess management rules, etc. you can talk
about?
Given that human error plays such an important part in
most incidents, this question aims to address what mea-
sures organizations specifically put in place to mitigate
it and to whom they apply within the organization.
The assumption is that most organi-
zations offer cybersecurity awareness
training to all employees to some extent.
Regulatory aspects
What regulations and standards are cur-
rently implemented or in the process of
being implemented?
NIS1 has already been implemented, but since NIS2
is currently in the national implementation phase, this
question addresses which legislations are primarily be-
ing focused on and if they overlap with the literature re-
view findings.
Organizations are aware of the upcom-
ing NIS2 directive and are already dis-
cussing implementation strategies for
the upcoming NIS2 or other legislation.
What are your thoughts on the current
state of cybersecurity regulation in Lux-
embourg?
Examine how cybersecurity professionals evaluate the
current state of legislations and regulations and how it
impacts their work.
Some regulations might overlap and
create confusion, and some regulations
might be difficult to implement.
How do you ensure that third-party ven-
dors and partners comply with relevant
cybersecurity regulations when working
with your organization?
GDPR, NIS2, and other regulations all require data con-
fidentiality, integrity, and availability. This question
explores how organizations handle third-party involve-
ment.
Choosing partners who have ISO certi-
fications, extended background checks,
and NDAs signed depending on opera-
tions.
What changes would you like to see in
regulations?
What do you expect in the future?
Bring forward some key changes that would benefit
CISOs’ daily work and gain insights into how the in-
dustry might change in the future (new challenges, new
possibilities).
Possibly more support from government
entities in decision-making and strategy
implementation.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
26
