
Managing a Ransomware Attack: The Resilience of a Swedish
Municipality – A Case Study
Anton Holmstr
¨
om
a
Institution of System and Space Science, Lule
˚
a University of Technology, Lule
˚
a, Sweden
Keywords:
Cyber Resilience, Information Security, Cyber Security, Incident Management, Ransomware, Business
Continuity, Crisis Management, Cyber Crisis.
Abstract:
As cyber threats grow in complexity, organizations must rethink their approach to information security, mov-
ing beyond technical solutions to focus on building organizational resilience. Previous research has primarily
relied on a technical perspective, often overlooking the broader interdependencies between different organi-
zational departments. This case study examines how a ransomware attack impacted a Swedish municipality
by conducting semi-structured interviews with key individuals from IT, social services, and management, sup-
plemented by internal documentation, police reports, and news coverage. The findings underscore the crucial
role of cross-departmental collaboration and coordination in managing cyber incidents. Specifically, the study
highlights how IT, social services, and management were interdependent in handling the crisis, demonstrating
the need for their inclusion in the overall information security planning. This case provides valuable insights
into the challenges public-sector organizations face during a cyberattack, offering a detailed understanding of
how one municipality responded, recovered, and adapted to such an incident.
1 INTRODUCTION
At the end of 2021, the small Swedish municipality of
Kalix gained national attention after being subjected
to a large-scale ransomware attack that severely dis-
rupted its operations and tested its overall resilience.
This event presents a valuable opportunity to exam-
ine how different parts of an organization respond
to cyberattacks, revealing the interconnectedness of
technical, social, and managerial processes in inci-
dent handling. The attack forced the entire social ser-
vices department to revert to analog operations, re-
quired the IT department to rebuild its infrastructure
from scratch, and placed significant political and me-
dia pressure on the municipal leadership.
As cyber threats continue to rise globally, ran-
somware remains one of the primary concerns for
organizations. According to recent reports by Ver-
izon (2024) and ENISA (2024), the number of cy-
berattacks is increasing, with ransomware attacks still
among the most prevalent. Ransomware typically in-
volves threat actors taking control of a target’s assets
and demanding a ransom to restore access (ENISA,
2024). In response to this evolving threat land-
a
https://orcid.org/0000-0002-0498-4858
scape, organizations invest heavily in security solu-
tions, such as technical tools, employee training, and
security personnel (Carpenter and Roer, 2022; Shaikh
and Siponen, 2023). While these proactive invest-
ments are crucial, they must be supplemented with
reactive measures, which prepare organizations to re-
spond effectively when preventive security controls
fail (Baskerville et al., 2014). Incident and risk man-
agement provide a structured approach to responding
to cyber incidents. However, as Beno
ˆ
ıt Dupont (2019)
notes, reactive measures alone are insufficient for en-
suring an organization’s long-term resilience. The
concept of cyber resilience—the ability to withstand,
recover from, and adapt to digital disruptions—has
emerged as a critical factor for organizational survival
in the digital age (Seyedehsaba Bagheri et al., 2023;
Bj
¨
orck et al., 2015; Linkov and Kott, 2019). Cyber re-
silience involves a continuous cycle of activities, from
planning and detection to response and adaptation,
to strengthen defenses against future threats (Beno
ˆ
ıt
Dupont, 2019).
This paper aims to provide a detailed account of
how a ransomware attack impacted a Swedish munic-
ipality, demonstrating how technical, social, and man-
agerial responses were interdependent throughout the
crisis. An organizational crisis is a low-probability,
Holmström, A.
Managing a Ransomware Attack: The Resilience of a Swedish Municipality – A Case Study.
DOI: 10.5220/0013110900003899
In Proceedings of the 11th International Conference on Information Systems Security and Privacy (ICISSP 2025) - Volume 1, pages 199-208
ISBN: 978-989-758-735-1; ISSN: 2184-4356
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
199

high-impact event that threatens an organization’s
continuity, and its cause, effect, and resolution are
clouded with uncertainty, alongside the perception
that rapid decision-making is necessary. (Pearson and
Clair, 1998). The study views the case by following
the cyclical approach of preparedness, response, re-
covery, and lessons learned principles, often found in
crisis and incident management frameworks (Boeke,
2018). Applying this cyclical approach to different
organizational perspectives allows for a view of the
systemic approach necessary to plan for, respond to,
and recover from such an incident. Highlighting the
importance of collaboration and coordination when
facing adversity provides valuable insights for future
research on how organizations can enhance their pre-
paredness and resilience against similar cyber inci-
dents.
2 METHODOLOGY
2.1 Case Study
This study employs a case study approach to exam-
ine the widespread effects of a ransomware attack on
a Swedish municipality (Yin, 2018). Over several
weeks, the attack disrupted IT, social services, and
core business operations. The case study focuses on
the municipality’s responses, strategies, and adapta-
tions during the crisis. This approach is well-suited
for capturing the complexity and dynamics of real-
world incidents (Walsham, 1995).
2.2 Data Collection
Data collection incorporated multiple sources to un-
derstand the incident and the municipality’s response.
Using Walsham (1995) interpretive approach, I ex-
plored the subjective experiences of stakeholders.
Nineteen semi-structured interviews (Kvale, 2012)
were conducted with IT personnel, management,
and social services employees (see Table 1). Inter-
views covered preparation, actions taken, and lessons
learned from the crisis, with most lasting about an
hour. While most were recorded and transcribed,
some were not due to the topic’s sensitivity.
To complement the interviews, I collected and an-
alyzed various types of related data sources. This in-
cluded:
• Police Report. Detailed the investigation and
provided insights into the legal and procedural as-
pects of the attack.
• Internal Documentation. Included security poli-
cies, project reports, and internal communications
related to the incident.
• Media Coverage. National and international
news articles highlighted public narratives and ex-
ternal perceptions of the municipality’s crisis re-
sponse.
• Consultancy Reports. Updates from consultancy
firms offered external perspectives on the techni-
cal and strategic measures taken during the crisis.
This combination of interviews and other rele-
vant sources provided a solid foundation for analyz-
ing the incident from multiple perspectives, ensuring
a comprehensive understanding of the municipality’s
response.
2.3 Data Analysis
I employed a reversed root cause analysis to sys-
tematically trace the effects of the ransomware at-
tack across the municipality, following the method
outlined by Andersen and Fagerhaug (2006). This
technique allowed me to work backward from the
observed consequences of the attack, identifying the
underlying factors and connecting them to the ini-
tial technical incident. By focusing on the impact
rather than the cause, I could map how different de-
partments—IT, Social Administration, and Manage-
ment—were affected and how their responses were
interrelated.
This analysis highlights the interdependencies
within the organization and demonstrates how techni-
cal, social, and managerial factors combined to shape
the response to the attack. By identifying these con-
nections, the root cause analysis helped reveal the
systemic nature of the incident, emphasizing the im-
portance of cross-departmental coordination and col-
laboration in managing such crises. This systems
overview forms the basis for the case description, pro-
viding a comprehensive understanding of the organi-
zational response to the ransomware attack.
3 RESULT
3.1 Kalix: A Swedish Municipality
Kalix municipality is a Swedish municipality lo-
cated in Norrbotten County, with the major city be-
ing Kalix. With around 15,480 inhabitants, it is a
small municipality (Statistics Sweden (SCB), 2024).
Swedish municipalities consist of a political function
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
200

Table 1: Interviews Conducted During the Incident Investigation.
Interviewee Role and Description
IT-Consultant External consultant working with incident handling.
IT-Consultant Working as incident manager and forensic lead.
IT Manager Current head of the IT Unit. Initial and follow-up interview.
Security Manager Head of Security. Initial and follow-up interview.
IT-Controller Quality assurance and monitoring. Initial and follow-up interview.
Staff Manager (Stabschef) Manager for the IT unit during the crisis.
Head of Communications Responsible for communication and information.
Head of Social Administration Senior official in the social services department. Initial and follow-up
interview.
Head of Unit Manager for a work unit in elderly care.
Area Manager Manager for ordinary housing at the social administration.
Assistant Nurse Working at an elderly home care service unit.
Coordinator Digital locks and vehicle coordinator at social administration.
Information Security Coordinator Working with information security at social administration.
Area Manager Working with information security questions at social administration.
and an administrative organization. The elected mu-
nicipal council (kommunfullm
¨
aktige) sets the overall
direction and budget, while the administrative orga-
nization implements these decisions (Kalix Kommun,
2024). Municipalities are divided into areas and units
responsible for various local governance and public
services (Rabe and Lidskog, 2024). Swedish munici-
palities have significant autonomy and responsibility,
implementing national policies locally in areas like
climate adaptation, sustainability, and public welfare.
Their decentralized governance structure enables tai-
lored approaches to local needs while aligning with
national objectives (Rabe and Lidskog, 2024). This
autonomy also makes municipalities central to local
governance and crisis management, allowing for flex-
ible and responsive strategies with minimal hierarchi-
cal oversight (van Laere and Lindblom, 2019).
3.2 Narrative of the Incident: The
Cyber Crisis
In the early hours of December 16th, night shift em-
ployees in elderly home care found their planning and
business systems unexpectedly unavailable. Initially
dismissed as a routine disruption, it soon became clear
that a more significant issue was unfolding within the
municipality’s IT infrastructure. When the head of the
social administration arrived at work later that morn-
ing, she received reports from different units also fac-
ing unavailable systems, indicating that the situation
had escalated. Down at the IT department, similar
reports came through from other administrative units.
At this point, the IT manager realized that it was more
than a routine disruption, started an investigation, and
contacted external consultants for support.
By 10:00, a couple of hours after the initial dis-
ruption, the head of social administration contacted
the municipality director. After being informed of
the situation, the municipality director called for the
first crisis meeting to assess the scope and impact
of the disruption. During the analysis, it became
clear that disruption had impacted all administrative
units. At this stage, the municipality director activated
’stabsl
¨
age’ (staff mode). Staff mode can be described
as the lowest or first level of preparedness for a crisis
or resource-intensive operation. It is commonly used
in healthcare and emergency services when a situation
escalates beyond normal operations, requiring a more
organized and centralized command structure.
At this point, the municipality still treated the dis-
ruption as an operational failure, adopting a 48-hour
planning perspective. This perspective meant they
were preparing for the disruption to last for the next
two days, focusing on short-term solutions and stabil-
ity.
The disruption affected the virtual private network
(VPN) and operations across the municipality for ex-
ample, the city library switched to analog lending, and
the indoor swimming pool allowed free entry when its
payment system failed.
At 11:30, the municipality informed the public on
its website about the situation. Not knowing that it
was a cyber-attack, the only information released was
that a serious disruption had affected the entire munic-
Managing a Ransomware Attack: The Resilience of a Swedish Municipality – A Case Study
201

ipality’s operations. Further information was dissem-
inated through the local TV channel around 12:00.
An hour later, at 13:00, the IT department and the
consultants could confirm, through their analysis, that
the municipality was under attack. A ransomware at-
tack had infected almost all servers, affecting most
business systems.
By 15:00, a second crisis management meeting
confirmed the ransomware attack. The IT manager
reported that most servers were encrypted, sensitive
data may have been extracted, and a ransom note,
signed ”Nothing personal, just business,” threatened
to publish the data. The crisis team promptly decided
against paying the ransom and filed a police report.
The municipality’s political leadership was briefed to
ensure oversight.
By 15:30, a press release was issued, followed by
a live press conference at 16:30, where the head of
communications, alongside the municipality director,
publicly acknowledged the ransomware attack and
outlined the municipality’s response strategy. Mean-
while, the IT manager engaged with the Swedish Na-
tional Operations Department (NOA), providing criti-
cal information to aid the ongoing criminal investiga-
tion.
The following day, December 17th, the crisis
management team gathered to review their response
plan. At this stage, the impact of the attack was so
severe that recovery would take longer than first es-
timated, forcing the team to switch focus from a 48-
hour perspective to a longer crisis plan. Moving for-
ward, the crisis management team would meet twice
a day to assess the situation and update their response
strategies.
Later in the day, on December 17th, the IT depart-
ment decided, for security reasons, to take the entire
internal network offline. This was to start the recov-
ery and gather evidence for the police investigation.
The network shutdown affected all assets relying on
internet connectivity, including internal and external
websites. By 12:30, the municipality held a digital
press conference to update the public on the ongoing
situation.
To summarize the steps taken as the situation un-
folded and moving forward:
• December 17th. A temporary external web-
site was launched to provide updates while email
servers remained offline. Social media also played
a role in disseminating information.
• December 18th. Cyber-attacks targeted the mu-
nicipality director’s personal accounts, likely in
retaliation for refusing to pay the ransom.
• December 20th. Salary payments were manually
processed with help from external financial con-
sultants, ensuring on-time payments despite sys-
tem disruptions.
• December 23rd. All employee computers were
collected for a full security overhaul, including re-
installing operating systems and endpoint protec-
tions—a process that took 3–4 weeks.
• December 28th. The original municipal web-
site was restored, marking a major recovery mile-
stone.
• January 7th. Employees changed account pass-
words using BankID, with alternative verification
options provided.
• January 10th–14th. Schools reopened, requiring
IT to check and reinstall 300 additional comput-
ers. A final press conference addressed questions
on the attack, its impact, and associated costs.
• January 17th. Unpaid invoices and year-end fi-
nancial processes were completed cautiously to
avoid reintroducing risks. A new VPN with multi-
factor authentication enabled remote work.
• January 18th. The new intranet was launched,
restoring internal communications.
• February 10th. The preliminary police investiga-
tion closed due to insufficient evidence. Further
attack attempts from the same and other IP ad-
dresses were blocked thanks to the strengthened
security measures.
The full restoration of business systems took ap-
proximately three weeks, marking the end of an in-
tense period of cyber crisis management. The inci-
dent highlighted the municipality’s resilience and re-
inforced the importance of robust cybersecurity and
transparent communication strategies.
3.3 Technical Analysis of the Attack
This section provides a detailed technical overview
of the ransomware attack. While the details such as
IP addresses and usernames remain confidential in
the police report an attack sequence was developed
based on the gathered data. Supplementary informa-
tion was sourced from third-party forensic analysis of
the malware identified on platforms such as Virus-
Total and RecordedFuture (Recorded Future Triage,
2024; VirusTotal, 2024). Figure 1 illustrates the at-
tack sequence.
The attack began when the attacker obtained a
username and potentially a password. Although the
precise acquisition method is unknown, plausible sce-
narios include retrieval from a leaked database or a so-
cial engineering attack, such as phishing. The attack-
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
202

ers likely employed brute force or password-spraying
techniques to access the system.
The compromised account had domain adminis-
trator privileges, enabling the attackers to escalate
their access quickly. They used these credentials
to gain access to the organization’s VPN. Once in-
side the internal network, the attackers achieved un-
restricted access to critical infrastructure, including
servers and databases, such as the Active Directory,
which manages user accounts and permissions.
With administrative-level access, the attackers be-
gan preparations for the deployment of their ran-
somware payload:
• Creation of Hidden Admin Accounts. The at-
tackers created a new domain administrator ac-
count, allowing them to operate with elevated
privileges without raising suspicion. This step fa-
cilitated continued access and operational control
within the network.
• Neutralization of Endpoint Security. They ac-
cessed the Group Policy Management system to
disable all endpoint security policies. This criti-
cal step neutralized existing defenses and exposed
systems to the subsequent malware deployment.
After compromising endpoint security, the attack-
ers used PowerShell commands to download and ex-
ecute the ransomware across the network. Forensic
analysis of the malware revealed the following behav-
iors:
• Shadow Copies Deletion. The ransomware re-
moved Volume Shadow Copies, eliminating a
critical backup mechanism and preventing file
restoration.
• Boot Configuration Modification. Using the
bcdedit command, the malware altered the sys-
tem’s boot configuration data, complicating re-
covery by disrupting the startup environment.
• System State Backups Deletion. Through
wbadmin.exe, the malware deleted system state
backups, essential for restoring configurations and
operational data.
• File Extension Modification. The ransomware
encrypted files and changed their extensions to in-
dicate compromise. These unique extensions ren-
dered the files unusable without the decryption
key.
• Self-Deletion. After encrypting files, the ran-
somware deleted itself to minimize forensic traces
and evade detection.
As the encryption process unfolded, critical systems
began failing progressively. The attack culminated in
widespread disruption, rendering large portions of the
network inoperable. Significant damage had already
occurred when the IT department detected the breach,
leaving core business systems offline and operational
capabilities severely compromised.
4 INTERPRETATION OF
NARRATIVE
Three perspectives are directly relevant to the pre-
sented narrative: the IT unit, the social services ad-
ministration, and the Management Administration.
These three areas were particularly exposed during
the cyber-attack and will be the study’s perspectives.
4.1 IT-Department
The IT department, run by the IT manager, is tasked
with supporting service delivery and is divided into
different areas: operations, service and support, work-
place, network and communication, data center, and
business development and projects. The IT unit is
also the system owner for the municipality’s overall
IT infrastructure, with each business unit responsible
for its systems.
The IT department’s role in managing the cyber
attack was crucial, and its efforts can be understood
by looking at the issue from a technical perspective.
When reports of disruptions began to pile up at the
IT department. The technicians were already hard at
work investigating the situation and trying to identify
a root cause for the disruption. With a growing suspi-
cion, the technicians could not yet confirm the cyber
attack but could, based on their analysis, determine
that this was no regular disruption. Feeling the grow-
ing weight of the situation, the IT department con-
tacted external IT consultants to aid in the situation.
The IT department and consultants analyzed fire-
wall and server logs, confirming a ransomware attack.
Technicians calmly identified infected clients and dis-
covered ransomware notes on most servers, realizing
the encryption was already underway. However, they
isolated one server while the malware encrypts a large
file, capturing it before it could delete itself. Upload-
ing the ransomware to VirusTotal revealed it was a
novel strain, as it had not been analyzed before.
By this point, most servers were encrypted, ex-
cept for some clients not connected to Active Direc-
tory (AD) or running older operating systems. Tech-
nicians reconstructed a timeline of events using server
and firewall logs to understand the attack vector and
methods, which formed the basis for the police report.
The analysis revealed that attackers gained access via
a VPN lacking multi-factor authentication (MFA) and
Managing a Ransomware Attack: The Resilience of a Swedish Municipality – A Case Study
203

Figure 1: Attack Sequence.
exploited domain admin accounts to disable antivirus
protections and deploy ransomware. Details of the at-
tack are outlined in Section 3.3. The reconstructed
timeline also guided the restoration process, helping
technicians identify safe backups to avoid reintroduc-
ing malware.
The widespread impact of the attack exposed gaps
in the existing IT infrastructure, prompting a com-
plete rebuild. The team reconstructed the system us-
ing backups with Microsoft 365 cloud services and
Microsoft Defender Security System. They manu-
ally restored and reinstalled all clients, ensuring they
were clean by connecting them to Microsoft’s end-
point solutions via an isolated SIEM system. The net-
work was rebuilt with segmentation and tiered user
levels, and a VPN with geo-fencing was implemented
to support remote work during the COVID-19 pan-
demic while restricting access to specific geographi-
cal areas. An infrastructure overhaul initially planned
for three years was completed in just four weeks.
With the new IT environment, the IT team had to
ensure the attackers were no longer present. They
prompted every existing user to change their pass-
words by authenticating themselves using BankID,
Sweden’s most widely used e-ID for digital identifi-
cation, or identify themselves in person with physical
ID (passport or driver’s license).
In the aftermath of the attack, the IT department
was left with many lessons learned, a large list of up-
coming less critical security changes that needed to
be made, and an increased security awareness among
the technicians. The insights and lessons learned led
the technicians to review another part of their unit and
identify new challenges, like establishing a forum for
collaboration between IT, leadership, and the broader
organization to drive security initiatives forward.
4.2 Social Services Administration
Social services are a central part of Kalix municipal-
ity’s core business. It manages various essential ser-
vices related to residents’ welfare and care. The ad-
ministration is divided into two main areas: individual
and family, and elderly and disabled care. These ar-
eas cover everything from support and interventions
for families, children, and young people to care for
the elderly and support for people with disabilities.
The ransomware attack took all digital sys-
tems offline, forcing the elderly care home ser-
vice—normally reliant on digital tools for scheduling,
patient lists, and documentation—to revert to paper
and pen. Experienced staff adapted quickly, drawing
on prior manual work experience and close team co-
operation. However, the transition posed significant
challenges, as critical information had to be retrieved
from old records or memory and transferred manu-
ally. The COVID-19 pandemic worsened the situa-
tion, increasing staff strain and patient safety risks.
The Social Service Administration relied heavily on
swift and decisive management. A home care unit
manager described how crisis meetings and clear in-
structions helped guide staff through the disruption.
Despite criticism over the lack of proactive planning,
they were able to mitigate the crisis’s worst impacts
with strong collaboration and effective communica-
tion.
As the crisis unfolded, frontline social service
teams had to adapt rapidly. While flexibility and
problem-solving were part of their routine, teams with
experienced staff found the transition to analog meth-
ods easier, while newer employees faced greater chal-
lenges. Collaboration emerged as the key to maintain-
ing critical operations. With meetings and planning
conducted in person, many teams reported a strength-
ened collaborative culture, which proved vital during
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
204

the crisis and has since influenced departmental
practices.
The head of Social Service Administration and the
area manager highlighted how the attack fostered a
new level of openness and transparency within the
organization. Due to the attack, most digital com-
munication channels, including internal and external
web pages and email, were disrupted. Extra measures
were taken to ensure everyone had access to the in-
formation they needed, such as holding frequent in-
person meetings and sending information via SMS.
This led to a more transparent communication culture.
Interviewees who had participated in crisis plan-
ning before the attack noted that this preparation
helped them respond more effectively to the new situ-
ation. However, they also emphasized that no formal
crisis planning or exercises specifically for cyber at-
tacks had been previously done. For many employ-
ees, the scale of the attack and the previously unrec-
ognized high reliance on digital systems came as a
surprise, revealing their digital reliance as a vulnera-
bility.
The incident highlighted the need for redundancy
in critical assets, such as paper records and alternative
systems like non-digital locks. In the long term, the
attack prompted changes in working practices and a
stronger focus on security. A key development was
hiring a dedicated information security coordinator to
oversee policies, crisis management plans, and col-
laboration with IT and municipal management on se-
curity issues.
4.3 Municipal Management
Administration
Kalix Municipal Administration plays a central and
guiding role in the municipality’s activities. It is
responsible for leading and coordinating the overall
work of the municipality and ensuring that political
decisions are implemented effectively and by laws
and regulations. The department is responsible for the
municipality’s strategic planning and governance and
controls finances, human resources, and communica-
tions. Here, the municipal director, the highest official
in the municipality, sits and leads the administration.
When news of the incident reached the Munici-
pal Management Administration, they initially con-
sidered it a severe operational disruption. However,
as reports continued to arrive from different parts
of the organization, it became clear that the situa-
tion was more complex than a routine technical is-
sue. The management group swiftly decided to acti-
vate the central crisis management team, which in-
cluded the municipality director, security manager,
and representatives from every administration. The
security manager led the group to conduct a situa-
tional analysis to establish an overview of the disrup-
tion and determine which parts of the organization
were affected, allowing them to allocate resources
where needed. Since the disruption impacted areas
delivering critical societal functions, such as elderly
care and home care, health and safety became the
top priority. Coordinating efforts across administra-
tions was vital, along with maintaining open commu-
nication. Regular meetings with the crisis manage-
ment group and administration leaders ensured infor-
mation flowed steadily, keeping employees informed.
When it became evident that the disruption was a
comprehensive ransomware attack, the management
group was informed that the attack had not only en-
crypted critical parts of the IT infrastructure but also
threatened to steal sensitive data. Despite the attack-
ers’ threats, the management group remained firm
in their decision not to pay the ransom and instead
filed a police report. The IT department had already
taken the entire network offline, affecting significant
parts of the municipality’s operations. To ensure that
residents and employees remained informed and re-
assured, the management team provided continuous
updates through available channels, including press
conferences, announcements on the local TV chan-
nel, and a temporary website continuously updated
with new information. The management group ap-
pointed two key media contacts: the Municipal Di-
rector and the Information Officer. The team also im-
plemented a communication strategy, revising it be-
fore and after each statement as necessary. The group
decided to take ownership of the information early to
prevent rumors and mitigate the spread of false in-
formation. As the IT department worked to restore
operations as quickly as possible, they realized the
need to completely rebuild the existing IT infrastruc-
ture to minimize the risk of future attacks. The man-
agement team decided to proceed with this compre-
hensive rebuild despite the high costs, viewing it as
a reasonable investment given their firsthand experi-
ence of the attack. While managing the immediate
crisis, the management team also began assessing the
financial impact of the attack. The analysis showed
that direct costs amounted to nearly SEK 2.5 million,
with consulting fees accounting for a significant por-
tion. Other costs included investments in security
tools such as Microsoft Defender and overtime ex-
penses for staff involved in incident handling in the
IT department and across the organization. The indi-
rect costs of the incident remain speculative. How-
ever, it is reasonable to assume that long-term ef-
fects include rebuilding trust in the organization and
Managing a Ransomware Attack: The Resilience of a Swedish Municipality – A Case Study
205

allowing recovery time for the employees involved.
In summary, from the municipal management’s per-
spective, the cyberattack represented a significant cri-
sis that required swift decision-making, close coop-
eration between management and administration, and
transparent communication with employees and the
public. Municipal management acted as a central
coordinating force, ensuring that residents and em-
ployees received the information and support needed
while restoring and securing the IT systems that con-
tinued in the background.
4.4 Cross-Analysis of the Three
Perspectives
The ransomware attack demonstrated the intercon-
nectedness of Kalix municipality’s departments, re-
vealing how actions taken by one part of the organi-
zation directly influenced the others. As the IT depart-
ment responded by taking the network offline, this im-
mediately affected the Social Service Administration,
forcing them to switch to manual operations, which
increased the risk to patient care during the COVID-
19 pandemic. Concurrently, the Management Admin-
istration was tasked with activating crisis protocols,
making critical resource allocation decisions, and en-
suring transparent public communication to maintain
trust.
The cause-and-effects represented in Figure 1
highlight the systemic impact of the attack across
the organization. The cascading effects, from the IT
department’s technical containment measures to the
Social Service Administration’s operational changes,
emphasize the need for continuous coordination be-
tween all departments. Each circle in the diagram
shows how actions or disruptions in one area triggered
responses in others, highlighting the importance of
timely communication and strategic alignment.
This analysis shows that the organization’s abil-
ity to respond effectively depended not on any single
department but on the collective actions and commu-
nication between departments. The IT department’s
technical expertise was crucial in containing the at-
tack. However, the close coordination of the Manage-
ment and the cooperation and effort of the Social Ser-
vice Administration ensured the continuity of critical
services, such as elderly care. The incident demon-
strated that resilience is a shared responsibility across
the entire organization.
The case study highlights how the growing com-
plexity of crises, particularly in the digital age, means
managing cyber risks is a key part of resilience
(Sheffi, 2015). This aligns with Williams et al.
(2017), who argues that crisis management and re-
silience are intertwined when facing adversity. How-
ever, while this case illustrates the organization’s ca-
pacity to manage the immediate crisis, it remains dif-
ficult to pinpoint the exact characteristics that de-
fine organizational resilience in this context. Re-
silience is often a complex and multifaceted con-
cept beyond technical or procedural measures (Beno
ˆ
ıt
Dupont, 2019). Resilience in practice often involves
a combination of formal crisis management proto-
cols and informal, human-driven responses, making
it difficult to operationalize and measure (Hillmann
and Guenther, 2021). This is reflected in the Kalix
case, where resilience was demonstrated, but the ex-
act mechanisms—technical, cultural, or leadership-
driven—remain challenging to isolate. Moreover,
whether Kalix’s response exemplifies resilience, ro-
bustness, or even antifragility remains open to in-
terpretation. As Munoz et al. (2022) argues, re-
silience often overlaps with robustness (the ability to
withstand disruptions without degradation) and an-
tifragility (emerging stronger after adversity), mak-
ing it challenging to differentiate between these out-
comes.
5 CONCLUSIONS
In this paper, I describe an extensive ransomware at-
tack that hit a Swedish municipality. Although the
attack originated as a technical incident, its conse-
quences spread throughout the organization, affecting
various departments and functions. This study pro-
vides a comprehensive view of how information se-
curity should be treated as an organizational concern.
Ensuring information and cyber security requires a
systemic approach that integrates all interconnected
parts of the organization into its security framework.
The represented study of a unique case offers a rare,
detailed look at the far-reaching impacts of a ran-
somware attack beyond the technical domain, under-
scoring the critical importance of social and manage-
rial responses in recovery and resilience. The anal-
ysis illustrates that building effective organizational
resilience against such attacks requires collaboration
and coordination across all departments. The findings
from this case offer valuable insights for both practi-
tioners and researchers, emphasizing the importance
of addressing cyber incidents from a holistic, organi-
zational perspective. This case can serve as a founda-
tion for further research in information security, par-
ticularly in exploring how organizational interdepen-
dencies affect incident response. It also offers a de-
tailed scenario for crisis management and tabletop ex-
ercises, helping organizations simulate real-world cy-
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
206
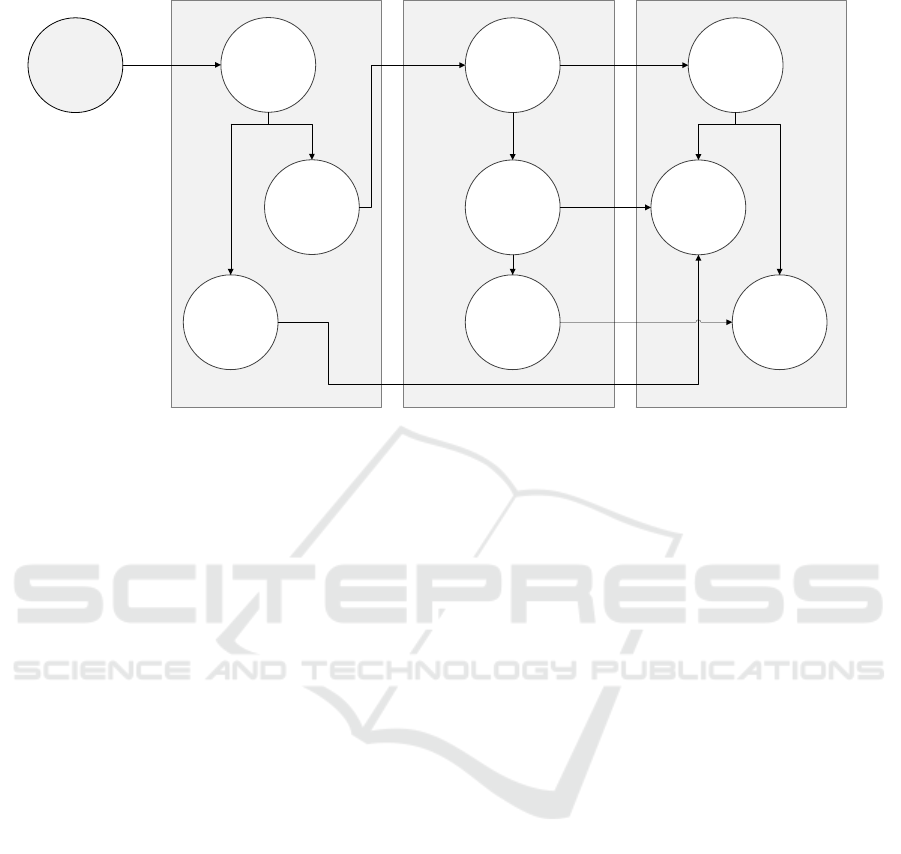
IT‐Department SocialAdministration Management
Ransomware
System
Recoveryand
Security
Improvement
Network
Offline
Malware
Detection&
Containment
System
Outage
Public
Communicati
on
Manual
Operations
Crisis
Management
Activation
Riskto
PatientCare
Resource
Allocation
Figure 2: Chain of effect from the ransomware attack.
ber events and strengthen their preparedness strate-
gies. Additionally, the case study can be used in
higher education as a working example for students
to analyze the complexities of cyber resilience, and in
companies and public-sector organizations as a ref-
erence for improving cybersecurity frameworks and
organizational preparedness. Future research could
delve deeper into how organizations can foster the
drivers of organizational resilience, such as redun-
dancy, cooperation, transparency, and comprehensive
communication, and explore practical ways to imple-
ment and operationalize these strategies.
REFERENCES
Andersen, B. and Fagerhaug, T. (2006). Root cause analy-
sis. Quality Press.
Baskerville, R., Spagnoletti, P., and Kim, J. (2014).
Incident-centered information security: Managing a
strategic balance between prevention and response.
Information & management, 51(1):138–151. Pub-
lisher: Elsevier.
Beno
ˆ
ıt Dupont (2019). The Cyber-Resilience of Financial
Institutions: Significance and Applicability. Journal
of Cybersecurity. https://doi.org/10.1093/cybsec/tyz
013
Bj
¨
orck, F., Henkel, M., Stirna, J., and Zdravkovic, J.
(2015). Cyber Resilience – Fundamentals for a Defini-
tion. Advances in Intelligent Systems and Computing,
353:311–316. https://doi.org/10.1007/978-3-319-164
86-131
Boeke, S. (2018). National cyber crisis management: Dif-
ferent European approaches. Governance, 31(3):449–
464. https://doi.org/10.1111/gove.12309.
Carpenter, P. and Roer, K. (2022). The Security Culture
Playbook: An Executive Guide To Reducing Risk and
Developing Your Human Defense Layer. John Wiley
& Sons.
ENISA (2024). ENISA Threat Landscape 2024. Tech-
nical report, European Union Agency for Cyberse-
curity. Retrieved September 30, 2024, from https:
//www.enisa.europa.eu/publications/enisa-threat-lan
dscape-2024
Hillmann, J. and Guenther, E. (2021). Organizational Re-
silience: A Valuable Construct for Management Re-
search? International Journal of Management Re-
views, 23(1):7–44. https://doi.org/10.1111/ijmr.12239
Kalix Kommun (2024). Kommunens organisation. Re-
trieved August 26, 2024, from http://www.kalix.se
/kommun/Kommunens-organisation/
Kvale, S. (2012). Doing Interviews. SAGE.
Linkov, I. and Kott, A. (2019). Fundamental Concepts
of Cyber Resilience: Introduction and Overview. In
Kott, A. and Linkov, I., editors, Cyber Resilience of
Systems and Networks, pages 1–25. Springer Interna-
tional Publishing, Cham. https://doi.org/10.1007/97
8-3-319-77492-31
Munoz, A., Billsberry, J., and Ambrosini, V. (2022). Re-
silience, robustness, and antifragility: Towards an ap-
preciation of distinct organizational responses to ad-
versity. International Journal of Management Re-
views, 24(2):181–187. https://doi.org/10.1111/ijmr
.12289
Pearson, C. M. and Clair, J. (1998). Reframing Crisis Man-
agement. Academy of Management Review, 23(1):59–
76. https://doi.org/10/cr4s33
Rabe, L. and Lidskog, R. (2024). Planning and Perceptions:
Exploring Municipal Officials’ Views on Residents’
Climate Preparedness. Sustainability, 16(11):4698. ht
tps://doi.org/10.3390/su16114698
Managing a Ransomware Attack: The Resilience of a Swedish Municipality – A Case Study
207

Recorded Future Triage (2024). Malware Analysis. Re-
trieved December 10, 2024, from https://tria.ge/2201
02-2q4ydaagf9
Seyedehsaba Bagheri, Gail Ridley, and Belinda Williams
(2023). Organisational Cyber Resilience: Manage-
ment Perspectives. Australasian Journal of Informa-
tion Systems. https://doi.org/10.3127/ajis.v27i0.4183
Shaikh, F. A. and Siponen, M. (2023). Organizational
Learning from Cybersecurity Performance: Effects on
Cybersecurity Investment Decisions. Information Sys-
tems Frontiers. https://doi.org/10.1007/s10796-023-1
0404-7
Sheffi, Y. (2015). The power of resilience: how the best
companies manage the unexpected. The MIT Press,
Cambridge, Massachusetts London, England.
Statistics Sweden (SCB) (2024). Folkm
¨
angd och befolkn-
ingsf
¨
or
¨
andringar - Kvartal 2, 2024. Retrieved August
26, 2024, from https://www.scb.se/hitta-statistik/stati
stik-efter-amne/befolkning/befolkningens-sammans
attning/befolkningsstatistik/pong/tabell-och-diagram
/folkmangd-och-befolkningsforandringar---manad-k
vartal-och-halvar/folkmangd-och-befolkningsforand
ringar---kvartal-2-2024/
van Laere, J. and Lindblom, J. (2019). Cultivating a longi-
tudinal learning process through recurring crisis man-
agement training exercises in twelve Swedish munic-
ipalities. Journal of Contingencies and Crisis Man-
agement, 27(1):38–49. .https://doi.org/10.1111/1468
-5973.12230
Verizon (2024). Data Breach Investigations Report. Tech-
nical report. Retrieved February 26, 2021, from https:
//enterprise.verizon.com/resources/reports/2020-dat
a-breach-investigations-report.pdf
VirusTotal (2024). VirusTotal. Retrieved December 10,
2024, fromhttps://tinyurl.com/y5xdb7jt
Walsham, G. (1995). Interpretive case studies in IS re-
search: nature and method. European Journal of In-
formation Systems, 4(2):74–81. https://doi.org/10.105
7/ejis.1995.9
Williams, T., Gruber, D., Sutcliffe, K., Shepherd, D., and
Zhao, E. Y. (2017). Organizational Response to Ad-
versity: Fusing Crisis Management and Resilience
Research Streams. The Academy of Management An-
nals, 11. https://doi.org/10.5465/annals.2015.0134
Yin, R. K. (2018). Case study research and applications:
design and methods. SAGE, Los Angeles, sixth edi-
tion edition.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
208
