
Objective- and Utility-Based Negotiation for Access Control*
Aditya Sissodiya
a
, Ulf Bodin
b
and Olov Schelén
c
Luleå University of Technology, Luleå, Sweden
Keywords:
Negotiation, Access Control, Automation, Digital Ecosystems, Stakeholder Collaboration, Interoperability.
Abstract:
Access control in modern digital ecosystems is challenging due to dynamic resources and diverse stakehold-
ers. Traditional mechanisms struggle to adapt, causing inefficiencies and inequities. We propose a novel
algorithm that automates access control policy negotiation via objective optimization and utility-based meth-
ods. It enables stakeholders to jointly select policies aligned with their preferences, provided a suitable policy
exists. Suggested criteria guide the evaluation of predefined policies, and a mathematical formulation quanti-
fies stakeholder preferences with utility functions, using optimization to achieve consensus. The algorithm’s
multilinear scalability is demonstrated through time and space complexity analysis. An evaluation tool sup-
ports practical testing, and the approach enhances efficiency and trust by ensuring equitable data access within
digital ecosystems.
1 INTRODUCTION
The evolution of access control mechanisms is pivotal
in the landscape of digital ecosystems for enabling
circular economies, especially with emerging tech-
nologies like Digital Product Passports (DPPs) (King
et al., 2023; Jansen et al., 2023). As these ecosys-
tems become increasingly intricate with the involve-
ment of multiple stakeholders, the limitations of tra-
ditional access control models become more appar-
ent (Servos and Osborn, 2017; Zhang et al., 2015). By
using negotiation to address and reconcile differences
in security policies, stakeholders can achieve a higher
level of interoperability (Gligor et al., 2002; Martins
and Guerreiro, 2019). This approach enables them
to work together more effectively, leveraging their re-
spective systems and security measures to ensure col-
lective protection.
Negotiation facilitates the integration of diverse
security policies without the need for each entity
to overhaul their systems (Gligor et al., 2002).
a
https://orcid.org/0009-0009-9695-2308
b
https://orcid.org/0000-0001-5194-4421
c
https://orcid.org/0000-0002-4031-2872
∗
The work presented in this paper was supported by
the European Regional Development Fund, Region Nor-
rbotten, Skellefteå Municipality, Luleå University of Tech-
nology, and industrial companies. The work has also been
funded by Digitala Stambanan IndTech, a Swedish collabo-
rative project between the Vinnova strategic innovation pro-
grams PiiA and Produktion 2030.
This integration is crucial in maintaining security
while enabling collaboration among various organiza-
tions (Subramaniam et al., 2019; Shojaiemehr et al.,
2018). For example, in dynamic cross-enterprise col-
laborations, a negotiation framework can help recon-
cile different access control rules by inferring rela-
tionships between disparate attributes, thereby facil-
itating smoother and secure interactions (Preuveneers
et al., 2018; Martins and Guerreiro, 2019). Hence, the
need for an advanced access control negotiation algo-
rithm that can address dynamic access control and the
specific challenges of complex digital environments
is justified.
Viewing these conflicts as objective optimiza-
tion problems grounded in cooperative game the-
ory offers structured strategies for consensus (Moura
et al., 2019), balancing stakeholder interests. Ob-
jective optimization refines policies amid competing
goals (Marden and Shamma, 2018; Shamma, 2020;
Medvet et al., 2015), aiding usability, accessibility,
and more (Zhang and He, 2015; Wang et al., 2019;
Ma, 2015; Zhao et al., 2008).
We propose an automated access control negotia-
tion algorithm using objective optimization to address
modern ecosystem challenges. Its context-aware ap-
proach enables flexible, secure, and equitable policies
unattainable by standalone systems (Bharadwaj and
Baras, 2003b; Bharadwaj and Baras, 2003a). Lever-
aging optimization and access control creates poli-
cies that are secure, privacy-preserving, adaptable,
Sissodiya, A., Bodin, U. and Schelén, O.
Objective- and Utility-Based Negotiation for Access Control.
DOI: 10.5220/0013130000003899
In Proceedings of the 11th International Conference on Information Systems Security and Privacy (ICISSP 2025) - Volume 2, pages 493-501
ISBN: 978-989-758-735-1; ISSN: 2184-4356
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
493

and representative of diverse interests (Moura et al.,
2019; Zhang et al., 2016; Vamvoudakis and Hes-
panha, 2018).
Contributions:
• We identify key challenges in complex digi-
tal ecosystems (Section 2) and introduce IDSA-
aligned criteria to guide negotiation (Section 3).
• We provide a mathematical definition of our ne-
gotiation algorithm (Section 4).
• We evaluate the algorithm through simulations
(Section 5), analyze complexity (Section 6).
A tool for evaluating the algorithm’s performance
is available on (GitHub), and related work is dis-
cussed in Section 7.
2 CHALLENGES IN ACCESS
CONTROL
As digital ecosystems grow more interconnected and
complex, traditional access control mechanisms must
be reevaluated (Subramaniam et al., 2019). Our ne-
gotiation algorithm addresses critical needs arising in
collaborative digital platforms.
• Dynamic Requirements and Automation: Dig-
ital ecosystems change rapidly in resources, roles,
and contexts (Subramaniam et al., 2019). Tradi-
tional methods struggle to adapt (Servos and Os-
born, 2017; Zhang et al., 2015), and existing NAC
frameworks rely on manual negotiation. By au-
tomating negotiation via mathematical optimiza-
tion, our algorithm efficiently adapts to modern
ecosystems.
• Complexity and Scalability: Multiple stakehold-
ers with varied interests complicate access con-
trol (Shojaiemehr et al., 2018). Our approach
centralizes utility aggregation and resolves con-
flicts objectively, reducing communication com-
plexity from quadratic to linear and enabling scal-
able stakeholder and policy management.
• Equitable Access and Efficient Negotiation:
Equitable resource access is essential (Subrama-
niam et al., 2019; Steinbuss et al., 2021), but exist-
ing frameworks, including blockchain-based ones
like FairAccess (Ouaddah et al., 2016) and Pol-
icychain (Chen et al., 2021), often enforce im-
mutable policies. Our negotiation mechanism al-
lows transparent, compromise-driven policy ad-
justments without excessive latency.
• Regulatory Compliance and Adaptability:
Regulations like GDPR and CCPA (Dasgupta
et al., 2019; Otto et al., 2021) demand ongoing
compliance. By continuously negotiating policies
according to current laws, our algorithm helps
avoid legal risks and protects organizational repu-
tation.
3 CRITERIA FOR NEGOTIATION
Our negotiation algorithm’s success depends on the
criteria used to evaluate access control policies. To
ensure these are comprehensive and robust, we base
them on principles from the International Data Spaces
Association (IDSA).
IDSA standards provide a technical foundation
for secure, reliable data exchange (Otto et al., 2021).
In manufacturing, where data sovereignty is crucial,
these criteria meet diverse stakeholder needs (Larri-
naga, 2022). By aligning with proven frameworks,
we improve access and usage control (Steinbuss et al.,
2021) while ensuring compliance aligned with IDSA
and GAIA-X, thus reducing legal risks and maintain-
ing secure practices (Otto et al., 2021; Huber et al.,
2022). The criteria are as follows:
1. Applicability: Reflects the practical benefits and
functionality that the policy provides to stakehold-
ers. This includes how well the policy supports
the operational goals and needs of each stake-
holder.
2. Usability: Assesses how understandable and
user-friendly the policy is for those who must ap-
ply it. A user-friendly policy reduces friction, en-
hances the overall user experience, and mitigates
the risk of misinterpretation or accidental non-
compliance.
3. Accessibility: Determines the ease with which
stakeholders can access the resources they need.
This criterion ensures that policies do not unduly
restrict legitimate access or create barriers to col-
laboration.
4. Compliance: Ensures that the policy adheres to
relevant legal and regulatory standards, minimiz-
ing legal risks and promoting trust among stake-
holders.
These criteria keep negotiations relevant and user-
friendly as contexts change, reducing complexity in
multi-stakeholder scenarios.
3.1 Policy Evaluation Guidance
We propose a scoring framework (1-10) for each cri-
terion, with guidelines for interpreting scores. Stake-
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
494
holders value criteria differently, and subjective rat-
ings reflect their preferences, leading to satisfactory
outcomes.
1. Applicability:
• 1-3 (Low Applicability): The policy offers min-
imal or no benefits to the stakeholder’s needs.
• 4-6 (Moderate Applicability): The policy is
somewhat relevant but may not fully support
the stakeholder’s needs.
• 7-8 (High Applicability): The policy aligns
well with the stakeholder’s needs, providing
significant benefits.
• 9-10 (Very High Applicability): The policy is
essential, offering maximal benefit and align-
ment.
2. Usability:
• 1-3 (Low Usability): Complex, difficult to im-
plement, causing frustration/errors.
• 4-6 (Moderate Usability): Requires multiple
approvals/specialized knowledge.
• 7-8 (High Usability): User-friendly, clear in-
structions, minimal complexity.
• 9-10 (Very High Usability): Highly intuitive,
streamlined, enhancing user experience.
3. Accessibility:
• 1-3 (Low Accessibility): Severely restricts ac-
cess, impeding tasks.
• 4-6 (Moderate Accessibility): Allows access
but with limiting constraints.
• 7-8 (High Accessibility): Adequate access, en-
abling effective task performance.
• 9-10 (Very High Accessibility): Seamless,
barrier-free access.
4. Compliance:
• 1-3 (Low Compliance): Fails key regulatory re-
quirements, posing legal risks.
• 4-6 (Moderate Compliance): Complies par-
tially, lacking in some areas.
• 7-8 (High Compliance): Meets all relevant
compliance requirements.
• 9-10 (Very High Compliance): Exceeds stan-
dards, anticipating regulatory changes.
4 ACCESS CONTROL
NEGOTIATION ALGORITHM
This section represents the negotiation algorithm in-
corporating objective optimization and stakeholder
preferences through utility functions mathematically:
• Let A = {a
1
, a
2
, . . . , a
n
} denote the set of stake-
holders involved in the negotiation.
• Let P = {P
1
, P
2
, . . . , P
m
} represent the set of po-
tential policies up for negotiation.
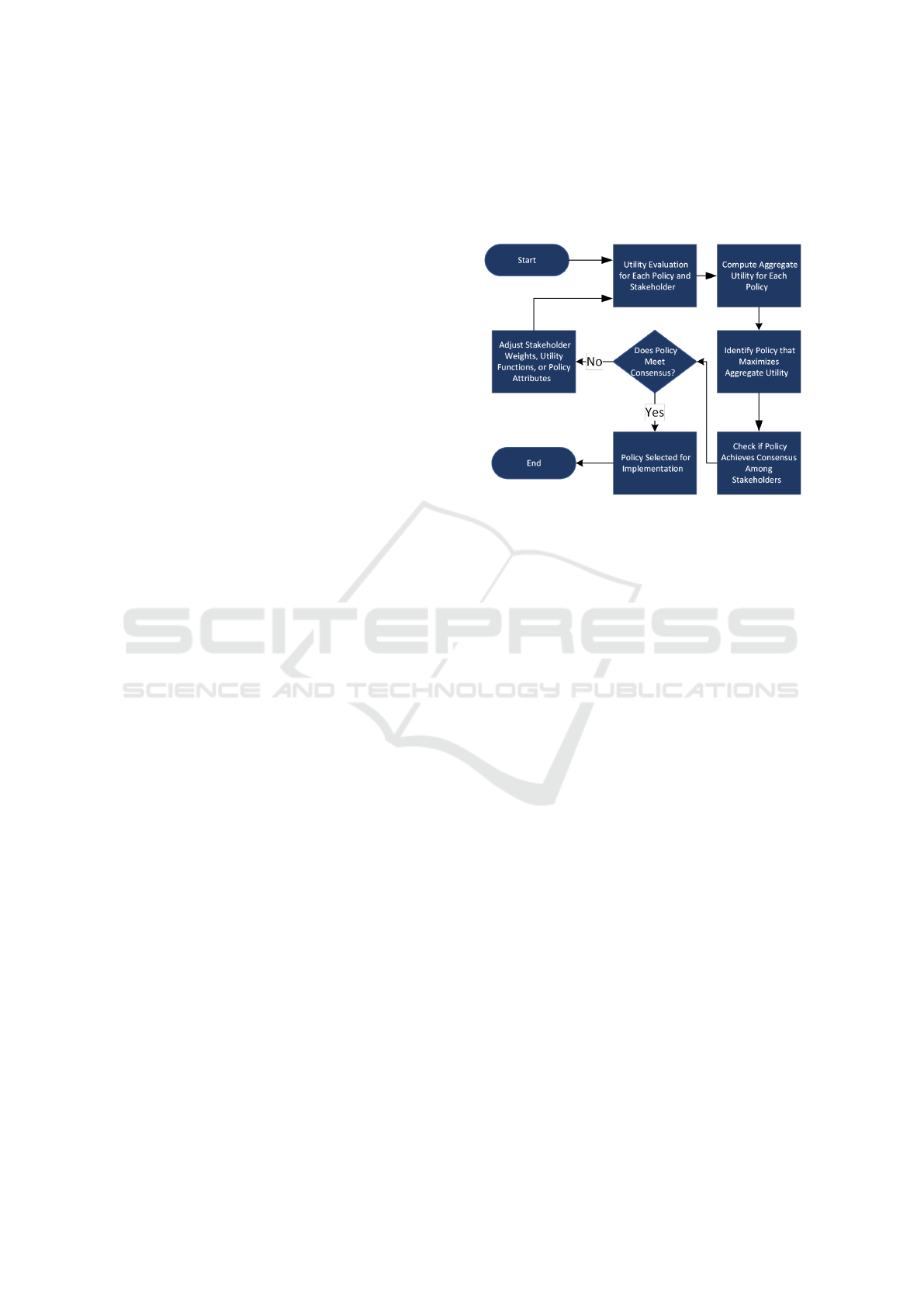
4.1 Algorithm Steps
Figure 1: Algorithm for Negotiation.
• Utility Evaluation: Calculate the utility U
a
i
(P
j
)
for each policy P
j
from the perspective of each
stakeholder a
i
.
• Aggregate Utility Calculation: Compute the ag-
gregate utility U
agg
(P
j
) for each policy.
• Optimization: Identify the policy P
∗
that maxi-
mizes U
agg
(P
j
).
• Consensus Check: Verify whether P
∗
achieves
consensus among stakeholders.
• Policy Selection: If P
∗
meets the consensus crite-
rion, it is selected for implementation. Otherwise,
adjust stakeholder weights, utility functions, or re-
consider policy attributes, followed by a repetition
of the steps until a satisfactory policy is identified.
4.1.1 Aggregate Utility Function
For a generalized mathematical representation focus-
ing solely on the utility functions, we abstract the
stakeholders and their preferences towards a set of
policies.
Each stakeholder a
i
∈ A has a utility function U
a
i
:
P → R, which maps each policy P
j
to a real number
representing the stakeholder’s preference for that pol-
icy. The utility functions are defined as follows:
U
a
i
(P
j
) = w
a
i
,1
· f
1
(P
j
) + w
a
i
,2
· f
2
(P
j
) + ···+ w
a
i
,k
· f
k
(P
j
)
• f
1
(P
j
), f
2
(P
j
), . . . , f
k
(P
j
) are functions that evalu-
ate policy P
j
based on criteria important to stake-
holder a
i
. These criteria might include aspects
such as the policy’s security level, its impact on
usability, or compliance with regulations.
Objective- and Utility-Based Negotiation for Access Control
495

• w
a
i
,1
, w
a
i
,2
, . . . , w
a
i
,k
are weights chosen by stake-
holder a
i
that reflect the importance of each crite-
rion in their utility function.
The utility function for each stakeholder is a
weighted sum of evaluations based on multiple cri-
teria, allowing for a nuanced expression of preference
that takes into account various aspects of each policy.
In a more generalized form, the utility function for
a stakeholder a
i
regarding a policy P
j
can be repre-
sented as:
U
a
i
(P
j
) =
k
∑
l=1
w
a
i
,l
· f
l
(P
j
)
where k is the number of criteria considered, w
a
i
,l
is
the weight assigned to criterion l by stakeholder a
i
,
and f
l
(P
j
) is the evaluation of policy P
j
based on cri-
terion l.
4.1.2 Objectives Optimization
The optimization step focuses on identifying the
policy, denoted as P
∗
, that maximizes the aggre-
gate utility, U
agg
(P
j
), across all considered policies.
Mathematically, this process aims to find the pol-
icy that yields the highest level of collective satisfac-
tion or preference among all stakeholders based on
the predefined utility functions and their associated
weights (Enkhbat et al., 2015; Allahviranloo and Ax-
hausen, 2018).
• A set of potential policies P = {P
1
, P
2
, . . . , P
m
},
• The aggregate utility function for a policy P
j
,
U
agg
(P
j
), which combines the preferences of all
stakeholders for policy P
j
,
The objective of the optimization step is to find the
policy P
∗
where that maximizes U
agg
(P
j
):
P
∗
= argmax
P
j
∈P
U
agg
(P
j
)
4.1.3 Evaluate Aggregate Utility for Each Policy
For every policy P
j
in the set P, calculate the aggre-
gate utility U
agg
(P
j
) as previously defined:
U
agg
(P
j
) =
n
∑
i=1
α
i
·U
a
i
(P
j
)
where α
i
is the weight reflecting the importance of
stakeholder a
i
and U
a
i
(P
j
) is the utility of policy P
j
according to stakeholder a
i
.
4.1.4 Selection of Optimal Policy
The policy P
∗
with the highest aggregate utility is se-
lected as the optimal policy. Formally, this selection
process can be represented as:
P
∗
= argmax
P
j
∈P
n
∑
i=1
α
i
·U
a
i
(P
j
)
!
A policy P
j
is selected if it satisfies the following
criteria:
• Maximizing Aggregate Utility: It has the highest
aggregate utility among all policies.
• Consensus Achievement: It meets or exceeds
a predetermined utility threshold for consensus
among stakeholders, which can be formalized as:
Consensus(P
j
) =
(
True if U
a
i
(P
j
) ≥ θ, ∀a
i
∈ A
False otherwise
where θ is the consensus threshold.
4.2 Algorithm Evaluation Tool
We developed an Algorithm Evaluation Tool to as-
sist in evaluating and optimizing various access con-
trol policies by considering the influence of different
stakeholders and the weights they assign to various
policy attributes. This tool, available on GitHub un-
der the MIT license, empowers users to add policies
and stakeholders, assign and update weights, and cal-
culate the optimal policy based on the aggregate util-
ity, ensuring that stakeholder consensus is considered.
It uses Flask and PostgreSQL for the backend and
HTML/CSS/JavaScript for the frontend, and is con-
tainerized with Docker for easy deployment.
• Features:
– Add Policies: Introduce new policies with at-
tributes like security, applicability, privacy, ac-
cessibility.
– Add Stakeholders: Include stakeholders and
define influence levels.
– Assign Weights: Set weights for policy at-
tributes per stakeholder perspective.
– Calculate Optimal Policy: Identify the policy
with highest aggregate utility.
– Check Consensus: Confirm if the chosen policy
meets the defined utility threshold across stake-
holders.
(Implementation of the algorithm and the tool is
available at this GitHub repository.)
5 REAL-WORLD SCENARIO
EVALUATION
Consider a connected car ecosystem with multi-
ple stakeholders sharing sensitive data like vehicle
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
496

telemetry, maintenance records, and user information:
• Car Owner (O): Values privacy and control over
data access.
• Car Manufacturer (M): Needs performance data
to improve designs.
• Insurance Company (I): Uses driving and main-
tenance data for risk assessment.
• Car Workshop (W): Requires diagnostics and
history for better service.
They must agree on a policy that balances all in-
terests. Three proposed policies are:
• Policy P
1
: Open access without owner consent.
• Policy P
2
: Role-based access, with personal data
requiring owner consent.
• Policy P
3
: Owner approval needed for every data
request.
Each stakeholder rates these policies and assigns
weights to each criterion (summing to 1).
5.1 Algorithm Steps
• Step 1: Define Priorities and Weights
– O: Places a high priority on Compliance and
Usability due to privacy concerns and the need
for ease in managing permissions. w
O,A
= 0.1,
w
O,U
= 0.3, w
O,Ac
= 0.1, w
O,C
= 0.5.
– M: High priority on Applicability and Accessi-
bility to access data for improvements. w
M,A
=
0.4, w
M,U
= 0.1, w
M,Ac
= 0.4, w
M,C
= 0.1.
– I: Prioritizes Applicability and Compliance.
w
I,A
= 0.5, w
I,U
= 0.1, w
I,Ac
= 0.3, w
I,C
= 0.1.
– W: Places a high priority on Applicability and
Accessibility, with a moderate emphasis on Us-
ability w
W,A
= 0.4, w
W,U
= 0.2, w
W,Ac
= 0.3,
w
W,C
= 0.1.
• Step 2: Stakeholder Ratings for Policies. Each
stakeholder rates each policy on a scale from 1 to
10 for each criterion, as shown in Table 2.
• Step 3: Calculate Individual Utilities. For each
stakeholder and policy, calculate the utility using
the formula:
U
a
i
(P
j
) =
k
∑
l=1
w
a
i
,l
× f
l
(P
j
)
– w
a
i
,l
= weight of criterion l for stakeholder a
i
– f
l
(P
j
) = rating of policy P
j
on criterion l by
stakeholder a
i
U
O
(P
1
) = (0.1 × 2) + (0.3 × 2) + (0.1 × 8) +
(0.5 × 1) = 2.1
Similarly, we calculate the individual utilities for
each stakeholder and get the following values, as
shown in Table 1.
Table 1: Utility Values for Each Stakeholder and Policy.
Stakeholder U
a
i
(P
1
) U
a
i
(P
2
) U
a
i
(P
3
)
Car Owner (O) 2.1 7.1 7.4
Car Manufacturer (M) 8.3 6.9 4.5
Insurance Company (I) 8.2 6.1 3.7
Car Workshop (W) 8.2 7.0 5.5
• Step 4: Compute U
agg
(P
j
) for Each Policy. As-
suming equal importance for all stakeholders, we
set the weights α
i
= 1 for all i.
U
agg
(P
j
) =
n
∑
i=1
U
a
i
(P
j
)
– U
agg
(P
1
) = U
O
(P
1
) + U
M
(P
1
) + U
I
(P
1
) +
U
W
(P
1
) = 2.1 + 8.3 + 8.2 + 8.2 = 26.8
– U
agg
(P
2
) = U
O
(P
2
) + U
M
(P
2
) + U
I
(P
2
) +
U
W
(P
2
) = 7.1 + 6.9 + 6.1 + 7.0 = 27.1
– U
agg
(P
3
) = U
O
(P
3
) + U
M
(P
3
) + U
I
(P
3
) +
U
W
(P
3
) = 7.4 + 4.5 + 3.7 + 5.5 = 21.1
• Step 5: Identify the Optimal Policy P
∗
.
P
∗
= argmax
P
j
U
agg
(P
j
)
U
agg
(P
1
) = 26.8, U
agg
(P
2
) = 27.1 (Highest),
U
agg
(P
3
) = 21.1.
Therefore, the optimal policy is P
∗
= P
2
.
• Step 6: Consensus Check. We need to ensure
that P
∗
meets a minimum acceptable utility θ for
all stakeholders. Let’s set θ = 5.0.
Check U
a
i
(P
2
) for each stakeholder:
– Car Owner (O): U
O
(P
2
) = 7.1 ≥ 5.0 ✓
– Car Manufacturer (M): U
M
(P
2
) = 6.9 ≥ 5.0 ✓
– Insurance Company (I): U
I
(P
2
) = 6.1 ≥ 5.0 ✓
– Car Workshop (W): U
W
(P
2
) = 7.0 ≥ 5.0 ✓
All stakeholders have a utility equal to or above
the threshold θ. Therefore, consensus is achieved.
This detailed walkthrough demonstrates how the
negotiation algorithm facilitates collaborative pol-
icy selection in complex, multi-stakeholder environ-
ments, ensuring that the final decision is both optimal
and equitable.
Objective- and Utility-Based Negotiation for Access Control
497
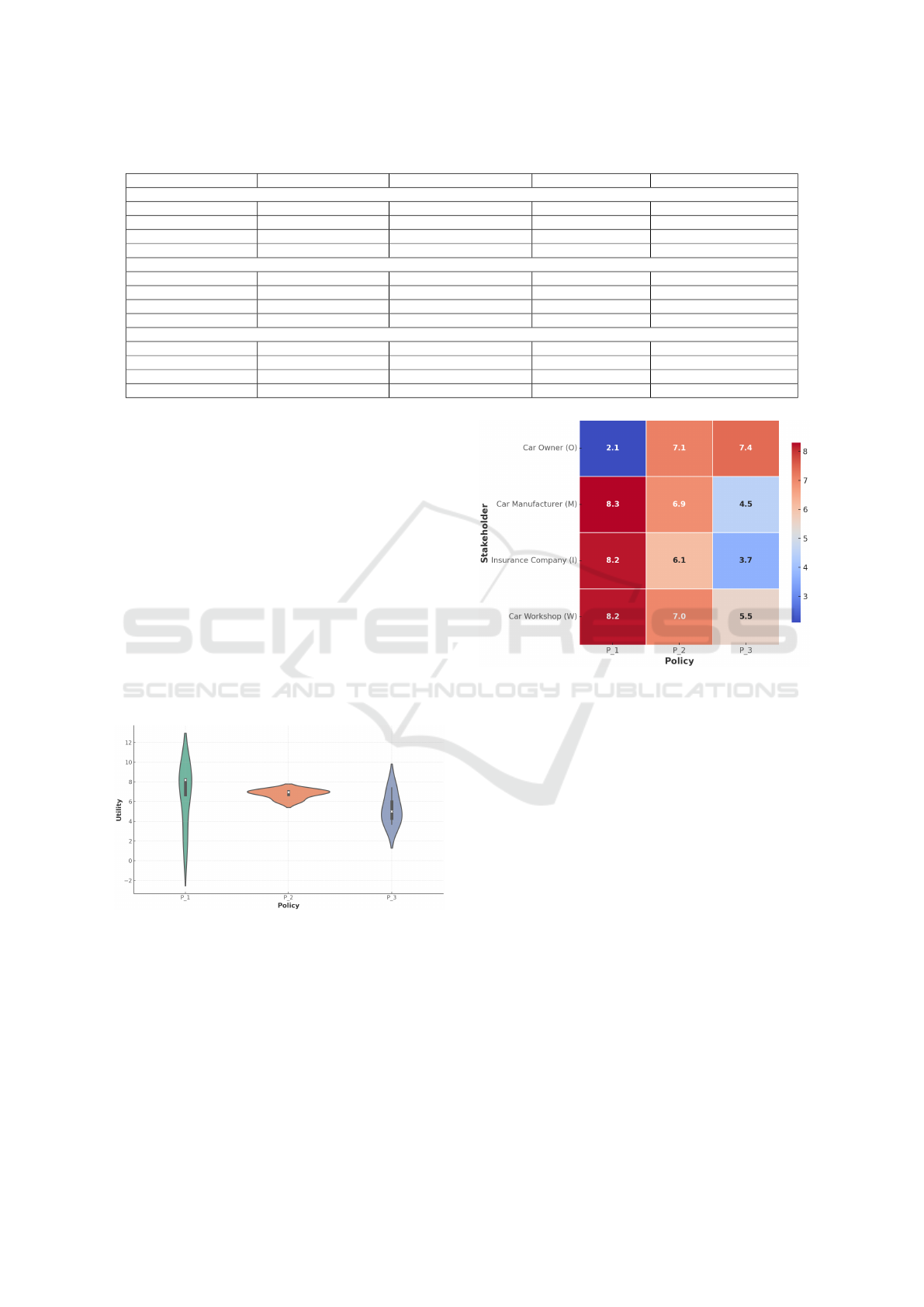
Table 2: Stakeholder ratings for Policies P
1
, P
2
, and P
3
.
Stakeholder Applicability (A) Usability (U) Accessibility (Ac) Compliance (C)
Policy P
1
: Open Access Without Consent
Car Owner (O) 2 (Low benefit) 2 (Poor usability) 8 (High for others) 1 (Fails privacy)
Car Manufacturer (M) 9 (High benefit) 8 (Easy access) 9 (Very high) 3 (Regulatory issues)
Insurance Company (I) 9 (High benefit) 7 (Easy integration) 9 (Very high) 3 (Privacy concerns)
Car Workshop (W) 9 (High benefit) 8 (Easy diagnostics) 9 (Very high) 3 (Compliance issues)
Policy P
2
: Role-Based Access with Owner Consent
Car Owner (O) 7 (Moderate benefit) 6 (Complex management) 6 (Acceptable) 8 (Aligns with regulations)
Car Manufacturer (M) 7 (Good access) 6 (Some restrictions) 7 (Acceptable) 7 (Better compliance)
Insurance Company (I) 6 (Some access) 6 (Moderate complexity) 6 (Restricted) 7 (Improved compliance)
Car Workshop (W) 7 (Adequate access) 7 (User-friendly) 7 (Acceptable) 7 (Good compliance)
Policy P
3
: Owner Approval for Each Request
Car Owner (O) 9 (Full control) 5 (Burdensome approval) 5 (Impedes services) 9 (Highly compliant)
Car Manufacturer (M) 4 (Limited access) 5 (Complicated process) 4 (Low accessibility) 8 (Compliant)
Insurance Company (I) 3 (Difficult data access) 5 (Cumbersome) 3 (Low accessibility) 8 (Compliant)
Car Workshop (W) 5 (Access delays) 6 (User-friendly) 5 (Moderate access) 8 (Compliant)
5.2 Quantitative Analysis
By systematically applying the negotiation algorithm,
stakeholders were able to:
• Quantify Preferences: Stakeholders expressed
their preferences numerically, allowing for objec-
tive comparisons.
• Balance Priorities: The algorithm balanced the
diverse priorities, ensuring that no stakeholder’s
essential needs were ignored.
• Ensure Compliance: Policies that failed to meet
regulatory requirements (like P
1
) were effectively
penalized in the utility calculations.
5.2.1 Utility Distribution Plot
Figure 2: Utility Distribution Across Policies (Violin Plot).
• P
1
: Higher values for most stakeholders, but the
car owner’s utility is much lower.
• P
2
: Balanced distribution, values clustered around
the median, indicating broad agreement.
• P
3
: Lower overall values, except for the car owner,
indicating varied stakeholder opinions.
Figure 3: Stakeholder Utility Heatmap.
5.2.2 Stakeholder Utility Heatmap
• Darker colors mean higher satisfaction. P
2
shows
balanced support, while P
1
pleases most but not
the car owner.
• Clear conflicts appear (e.g. Car Owner vs. others
on Policy P
1
). P
2
is more acceptable to all.
• P
3
favors the Car Owner but not others, prioritiz-
ing privacy over accessibility.
6 ALGORITHM COMPLEXITY
ANALYSIS
• Time Complexity
– Utility Calculation: O (c), where c is the num-
ber of criteria.
– Aggregate Utility Calculation: O(p × s ×
O(c)), where p is the number of policies and s
is the number of stakeholders and O(c) is called
for each policy.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
498

– Optimal Policy Evaluation: O(p), as it needs
to iterate through the aggregate utilities of all
policies once to find the maximum.
– Consensus: O(p), as it checks the Aggregate
Utility value for each policy against the set
threshold.
The overall time complexity of the algorithm is
the sum of the complexities of its parts, primar-
ily dominated by Aggregate Utility Calculation:
O(p × s × O(c)) + O(p) + O(s). Since O (p × s ×
O(c)) is the most significant term, we can sim-
plify the overall complexity to O(p × s × O(c)).
Therefore the complexity would be considered
multilinear rather than strictly linear. The compu-
tational cost increases linearly with an increase in
any one of p, s, or c while keeping the others con-
stant, but increases polynomially as all increase
proportionally.
• Space Complexity
– Aggregate Utilities: O(p) since there is one en-
try per policy and a dictionary is where the key
is the policy name and the value is its aggregate
utility score is stored.
– Utility Calculations: Uses a temporary variable
to store the utility score O(1).
– Consensus Check: The maximum space re-
quired is proportional to the number of stake-
holders, O(s).
When considering the space required for input
data and computational storage together, the over-
all space complexity of the algorithm can be rep-
resented as: O(p) + O (s) = O(p + s) this means
the space complexity is linearly proportional to
the sum of the number of policies and the num-
ber of stakeholders.
7 RELATED WORK
Research increasingly recognizes the need for dy-
namic, secure, and collaborative policy manage-
ment in digital ecosystems. Approaches range from
relationship-based access control to blockchain-based
frameworks, helping stakeholders reach consensus on
policies, maintain confidentiality, and enable flexible
mechanisms in complex environments.
Negotiation is critical for managing access con-
trol and privacy in digital systems, including cloud
services, digital ecosystems, and multi-agent plat-
forms (Mehregan and Fong, 2016; Subramaniam
et al., 2019). Traditional methods now incorpo-
rate dynamic negotiation algorithms to handle fine-
grained requirements, letting stakeholders set policies
that reflect various constraints and preferences.
Work on Relationship Based Access Control (Re-
BAC) includes methods for resolving conflicting pri-
vacy needs among co-owners, using SAT solvers
to verify policy satisfiability (Mehregan and Fong,
2016). Negotiation in large-scale and dynamic coali-
tions is explored in (Gligor et al., 2002), while
autonomous agents and a mathematical negotiation
framework are detailed in (Bharadwaj and Baras,
2003b). Adaptive negotiation to manage rapidly
changing digital ecosystems is discussed in (Subra-
maniam et al., 2019).
Blockchain-based solutions support transparent,
decentralized policy management, ensuring auditabil-
ity and trust. Policychain (Chen et al., 2021) uses
blockchain nodes for ABAC policy decisions, en-
suring high availability and autonomy. FairAc-
cess (Ouaddah et al., 2016) removes centralized au-
thorities to enhance security and privacy. AuthPriva-
cyChain (Yang et al., 2020) employs blockchain node
addresses as identities, providing secure encryption
and management of cloud-stored data, including au-
thorization and revocation processes.
Our algorithm addresses a gap by automating dy-
namic, context-aware, and equitable negotiations, re-
flecting all stakeholders’ interests.
8 CONCLUSION
This paper identifies key challenges in multi-party ac-
cess control negotiations and presents both criteria
and an algorithm to address them. The proposed al-
gorithm significantly improves access control in com-
plex, dynamic digital ecosystems by balancing secu-
rity, confidentiality, and usability.
While traditional methods struggle with the mul-
tifaceted needs of diverse stakeholders, our algorithm
employs objective optimization to support fair, struc-
tured negotiations that accommodate various inter-
ests. This fosters trust and cooperation among stake-
holders, enhancing the overall management of digi-
tal resources. By integrating standardized specifica-
tions from the International Data Spaces Association,
the algorithm remains technically sound, enforceable,
and adaptable. Its ability to respond dynamically to
changing conditions underscores its relevance in to-
day’s evolving digital landscape.
Overall, this work not only advances immedi-
ate outcomes in access control negotiation but also
encourages rethinking existing frameworks, driving
ongoing innovation in the management of digital
ecosystems.
Objective- and Utility-Based Negotiation for Access Control
499

REFERENCES
Allahviranloo, M. and Axhausen, K. (2018). An optimiza-
tion model to measure utility of joint and solo activ-
ities. Transportation Research Part B: Methodologi-
cal, 108:172–187.
Bharadwaj, V. G. and Baras, J. S. (2003a). A framework for
automated negotiation of access control policies. In
DARPA Information Survivability Conference and Ex-
position,, volume 3, pages 216–216. IEEE Computer
Society.
Bharadwaj, V. G. and Baras, J. S. (2003b). Towards auto-
mated negotiation of access control policies. In Pro-
ceedings POLICY 2003. IEEE 4th International Work-
shop on Policies for Distributed Systems and Net-
works, pages 111–119. IEEE.
Chen, E., Zhu, Y., Zhou, Z., Lee, S.-Y., Wong, W. E.,
and Chu, W. C.-C. (2021). Policychain: a decentral-
ized authorization service with script-driven policy on
blockchain for internet of things. IEEE Internet of
Things Journal, 9(7):5391–5409.
Dasgupta, A., Gill, A., and Hussain, F. (2019). A con-
ceptual framework for data governance in iot-enabled
digital is ecosystems. In 8th International Confer-
ence on Data Science, Technology and Applications.
SCITEPRESS–Science and Technology Publications.
Enkhbat, R., Enkhbayar, J., and Griewank, A. (2015).
Global optimization approach to utility maximization
problem. International Journal of Pure and Applied
Mathematics, 103(3):485–497.
Gligor, V. D., Khurana, H., Koleva, R. K., Bharadwaj, V. G.,
and Baras, J. S. (2002). On the negotiation of access
control policies. In Security Protocols: 9th Interna-
tional Workshop Cambridge, UK, April 25–27, 2001
Revised Papers 9, pages 188–201. Springer.
Huber, M., Wessel, S., Brost, G. S., and Menz, N. (2022).
Building trust in data spaces.
Jansen, M., Meisen, T., Plociennik, C., Berg, H., Pomp,
A., and Windholz, W. (2023). Stop guessing in the
dark: Identified requirements for digital product pass-
port systems. Systems, 11(3):123.
King, M. R., Timms, P. D., and Mountney, S. (2023). A
proposed universal definition of a digital product pass-
port ecosystem (dppe): Worldviews, discrete capabil-
ities, stakeholder requirements and concerns. Journal
of Cleaner Production, 384:135538.
Larrinaga, F. (2022). Data sovereignty-requirements analy-
sis of manufacturing use cases.
Ma, S. (2015). Dynamic game access control based on trust.
In 2015 IEEE Trustcom/BigDataSE/ISPA, volume 1,
pages 1369–1373. IEEE.
Marden, J. R. and Shamma, J. S. (2018). Game theory and
control. Annual Review of Control, Robotics, and Au-
tonomous Systems, 1:105–134.
Martins, H. and Guerreiro, S. (2019). Access control chal-
lenges in enterprise ecosystems. Research Anthology
on Blockchain Technology in Business, Healthcare,
Education, and Government.
Medvet, E., Bartoli, A., Carminati, B., and Ferrari, E.
(2015). Evolutionary inference of attribute-based ac-
cess control policies. In Evolutionary Multi-Criterion
Optimization: 8th International Conference, EMO
2015, Guimarães, Portugal, March 29–April 1, 2015.
Proceedings, Part I 8, pages 351–365. Springer.
Mehregan, P. and Fong, P. W. (2016). Policy negotiation for
co-owned resources in relationship-based access con-
trol. In Proceedings of the 21st ACM on Symposium on
Access Control Models and Technologies, pages 125–
136.
Moura, J., Marinheiro, R. N., and Silva, J. C. (2019). Game
theory for cooperation in multi-access edge comput-
ing. In Paving the Way for 5G Through the Con-
vergence of Wireless Systems, pages 100–149. IGI
Global.
Otto, B., Rubina, A., Eitel, A., Teuscher, A., Schleimer,
A. M., Lange, C., Stingl, D., Loukipoudis, E., Brost,
G., Boege, G., et al. (2021). Gaia-x and ids.
Ouaddah, A., Abou Elkalam, A., and Ait Ouahman, A.
(2016). Fairaccess: a new blockchain-based access
control framework for the internet of things. Security
and communication networks, 9(18):5943–5964.
Preuveneers, D., Joosen, W., and Zudor, E. (2018). Pol-
icy reconciliation for access control in dynamic cross-
enterprise collaborations. Enterprise Information Sys-
tems, 12:279 – 299.
Servos, D. and Osborn, S. L. (2017). Current research and
open problems in attribute-based access control. ACM
Computing Surveys (CSUR), 49(4):1–45.
Shamma, J. S. (2020). Game theory, learning, and control
systems. National Science Review, 7(7):1118–1119.
Shojaiemehr, B., Rahmani, A. M., and Qader, N. N. (2018).
Cloud computing service negotiation: a systematic re-
view. Computer Standards & Interfaces, 55:196–206.
Steinbuss, S. et al. (2021). Usage control in the international
data spaces.
Subramaniam, M., Iyer, B., and Venkatraman, V. (2019).
Competing in digital ecosystems. Business Horizons,
62(1):83–94.
Vamvoudakis, K. G. and Hespanha, J. P. (2018). Game-
theory-based consensus learning of double-integrator
agents in the presence of worst-case adversaries.
Journal of Optimization Theory and Applications,
177:222–253.
Wang, Y., Tian, L., and Chen, Z. (2019). Game analysis of
access control based on user behavior trust. Informa-
tion, 10(4):132.
Yang, C., Tan, L., Shi, N., Xu, B., Cao, Y., and Yu, K.
(2020). Authprivacychain: A blockchain-based access
control framework with privacy protection in cloud.
IEEE Access, 8:70604–70615.
Zhang, Y. and He, J. (2015). A proactive access control
model based on stochastic game. In 2015 4th Interna-
tional Conference on Computer Science and Network
Technology (ICCSNT), volume 1, pages 1008–1011.
IEEE.
Zhang, Y., He, J., Zhao, B., Huang, Z., and Liu, R.
(2015). Towards more pro-active access control in
computer systems and networks. Computers & Se-
curity, 49:132–146.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
500

Zhang, Y., He, J., Zhao, B., and Liu, R. (2016). Application
of game theory for dynamic access control in security
systems. International Journal of High Performance
Computing and Networking, 9(5-6):451–461.
Zhao, M., Ren, J., Sun, H., Li, S., and Chen, Z. (2008). A
game theoretic approach based access control mech-
anism. In 2008 The 9th International Conference for
Young Computer Scientists, pages 1464–1469. IEEE.
Objective- and Utility-Based Negotiation for Access Control
501
