
A Reflection on Process-Oriented Industrial IoT Security Management
Markus Hornsteiner
a
, Linda Koelbel
b
, Daniel Oberhofer
c
and Stefan Schoenig
d
University of Regensburg, Regensburg, Germany
Keywords:
Internet of Things, Process Management, IIoT Security.
Abstract:
The increasing adoption of the Industrial Internet of Things (IIoT) brings significant cybersecurity challenges
due to the complexity and interconnectedness of industrial systems. This paper explores how business process
management (BPM) can be applied to overcome these challenges by embedding security considerations into
each phase of the BPM lifecycle: discovery, modeling, execution, and monitoring. Bringing together different
research directions, including process mining, BPMN extensions and security compliance monitoring, this
work provides a comprehensive overview of existing approaches to improve IIoT security. The paper presents
opportunities for integrating security-aware processes into IIoT environments and provides insights into how
organizations can use BPM to ensure continuous security enforcement and compliance. The study highlights
current gaps and outlines opportunities for future development in the integration of BPM and IIoT security.
1 INTRODUCTION
The Industrial Internet of Things (IIoT) represents a
paradigm shift in industrial environments, enabling
increased connectivity, automation, and data-driven
decision-making (Palattella et al., 2016; Sisinni et al.,
2018). As organizations leverage IIoT technologies
to enhance productivity and efficiency, they face un-
precedented cybersecurity challenges, henceforth re-
ferred to as security (Serror et al., 2021). The in-
terconnected nature of IIoT systems, often spanning
legacy infrastructure, real-time operations, and di-
verse devices, creates a broad and dynamic attack sur-
face. Securing these complex environments requires
holistic approaches that go beyond traditional IT se-
curity frameworks and integrate security into business
processes from the beginning - security by design.
(Tange et al., 2020).
To address IIoT’s unique security challenges, tra-
ditional controls can be complemented by process-
centric approaches that consider the entire indus-
trial lifecycle (Sch
¨
onig et al., 2022). This paper ex-
plores how Business Process Management (BPM), a
method traditionally used to improve organizational
efficiency, can be adapted to enhance security in IIoT
environments. BPM offers potentials to enhance IIoT
a
https://orcid.org/0000-0002-8024-1220
b
https://orcid.org/0009-0006-6907-2784
c
https://orcid.org/0009-0008-9078-0149
d
https://orcid.org/0000-0002-7666-4482
security by providing a structured way to design, an-
alyze, and monitor processes, enabling direct integra-
tion of security mechanisms (Oberhofer et al., 2024).
By formalizing and visualizing security-aware work-
flows, BPM helps organizations understand device,
data, and network interactions, ensuring security is
embedded throughout the process lifecycle. By em-
bedding process-centric security measures, organiza-
tions can define processes that are robust and adapt-
able to evolving threats (Sch
¨
onig et al., 2022). Build-
ing on our previous work by Sch
¨
onig et al. (2022),
which highlighted the potential of applying BPM con-
cepts to IIoT security management, this paper ad-
dresses the challenges and intersections identified in
that study. Using the IIoT security management pro-
cess as a foundation, we illustrated how BPM meth-
ods can enhance IIoT security and discussed future
challenges and areas for improvement. Since the pub-
lication of the initial paper, we have successfully re-
solved these challenges and addressed the open ques-
tions through the contributions presented in this paper.
This work synthesizes existing approaches in the
application of BPM to IIoT security management and
describes a comprehensive framework summarized in
Figure 2. The answered research questions and con-
tributions of the framework therefore are threefold:
We investigate (i) the benefits and propositions (Why
BPM is effective for IIoT security?), (ii) the proce-
dures and guidelines (How to integrate and perform
process-centric IIoT security management?), and (iii)
242
Hornsteiner, M., Koelbel, L., Oberhofer, D. and Schoenig, S.
A Reflection on Process-Oriented Industrial IoT Security Management.
DOI: 10.5220/0013163500003899
In Proceedings of the 11th International Conference on Information Systems Security and Privacy (ICISSP 2025) - Volume 1, pages 242-253
ISBN: 978-989-758-735-1; ISSN: 2184-4356
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)

the concrete necessary concepts and techniques (Us-
ing which technical tools and methods?). By offer-
ing a structured overview of BPM methods applied to
IIoT security, the aim is to provide both practitioners
and researchers with an insight into how security can
be systematically embedded in IIoT processes. Addi-
tionally, this synthesis highlights existing gaps in re-
search and identifies opportunities for further devel-
opment in this emerging field.
The structure of the paper is as follows: Sec-
tion 2 provides background information on impor-
tant topics and describes the structure of the indi-
vidual sub-areas. Section 3 introduces the overar-
ching challenges of IIoT security and the benefits
and propositions of BPM in addressing these chal-
lenges. Section 4 presents procedures and guidelines
for applying BPM methods to IIoT security man-
agement. Section 5 delves into each phase of the
BPM lifecycle, presenting concrete technical meth-
ods and approaches that can support IIoT security at
each stage. Section 6 addresses open questions and
possible future research approaches, followed by Sec-
tion 7, which provides concluding thoughts and direc-
tions for future research.
2 BACKGROUND
2.1 Business Process Management
Business Process Management (BPM) encompasses
all tasks and measures to make processes more ef-
ficient and effective (Hansen et al., 2019). BPM
should serve as a decision-making aid for process
improvement and support the management of orga-
nizations (Weske, 2012). In particular, the aim is
to shorten throughput times, increase efficiency, save
costs and minimize error rates, which then contributes
to increasing competitiveness (Dumas et al., 2018;
Bernardo et al., 2017). BPM is also seen as a strategy
for gaining a competitive advantage, whereby numer-
ous definitions exist (zur Muehlen and Ho, 2005).
2.2 Industrial IoT Security
The IIoT constitutes a new era in industrial produc-
tion since it marks the beginning of a fundamental
paradigm shift (ENISA, 2018). By utilizing IoT tech-
nologies, it is possible to network machines, people,
and whole factories. Thereby, new production pro-
cesses, such as personalized products on an industrial
scale, and new business models, like data-driven ser-
vices, are possible. In addition to the new opportu-
nities offered by the IIoT, there are also new chal-
lenges. For example, the networking of industrial
components opens up new opportunities for attackers
to infiltrate, interrupt or maliciously modify processes
(ENISA, 2018). One unique aspect of IIoT security
is that, in contrast to IT security, it is primarily con-
cerned with the security of OT and therefore avail-
ability (Tange et al., 2020). To ensure this, industry
standards such as IEC62443 call for the security by
design paradigm (IEC, 2009). This means that the se-
curity of processes and components must already be
guaranteed during the design process. To consider se-
curity in industrial processes, there is a need for an
inclusive modeling approach of security- and IIoT-
aware processes (Sch
¨
onig et al., 2022). In this pa-
per, the term security mechanisms is used as an um-
brella term to encompass a range of security-related
concepts such as policies, rules, attributes, controls,
protocols, measures, and requirements. These mecha-
nisms represent various ways to address security con-
cerns in IIoT environments. Additionally, security
controls refers specifically to the concrete, actionable
components within a system, such as access controls,
data encryption, and network isolation, which are im-
plemented to enforce security at different points in the
process. By defining these terms upfront, the discus-
sion of security in IIoT environments is streamlined,
ensuring clarity when referring to different aspects of
IIoT security throughout the paper.
2.3 Method
The discussion of the individual sub-areas presented
in Section 5 follows a structured approach that en-
sures systematic identification of research gaps and
artifacts aimed at addressing these gaps. The steps
outlined below form the core methodology applied to
each sub-area in Section 5, ensuring a consistent and
rigorous approach across the entire study:
• Definition of Research Questions. Each subarea
begins with the identification and formulation of
one or more research questions. These guide the
exploration of specific challenges in that area and
focus on how BPM can improve IIoT security.
The research questions serve as the basis for the
research and are aligned with the overarching ob-
jectives of this work.
• Literature Review. If necessary, a suitable liter-
ature review is presented. This sets out the scien-
tific basis for the problem and provides a compre-
hensive overview of the research area. This step
ensures that all developments, trends and limita-
tions in the literature are identified and lays the
foundation for revealing research gaps.
A Reflection on Process-Oriented Industrial IoT Security Management
243
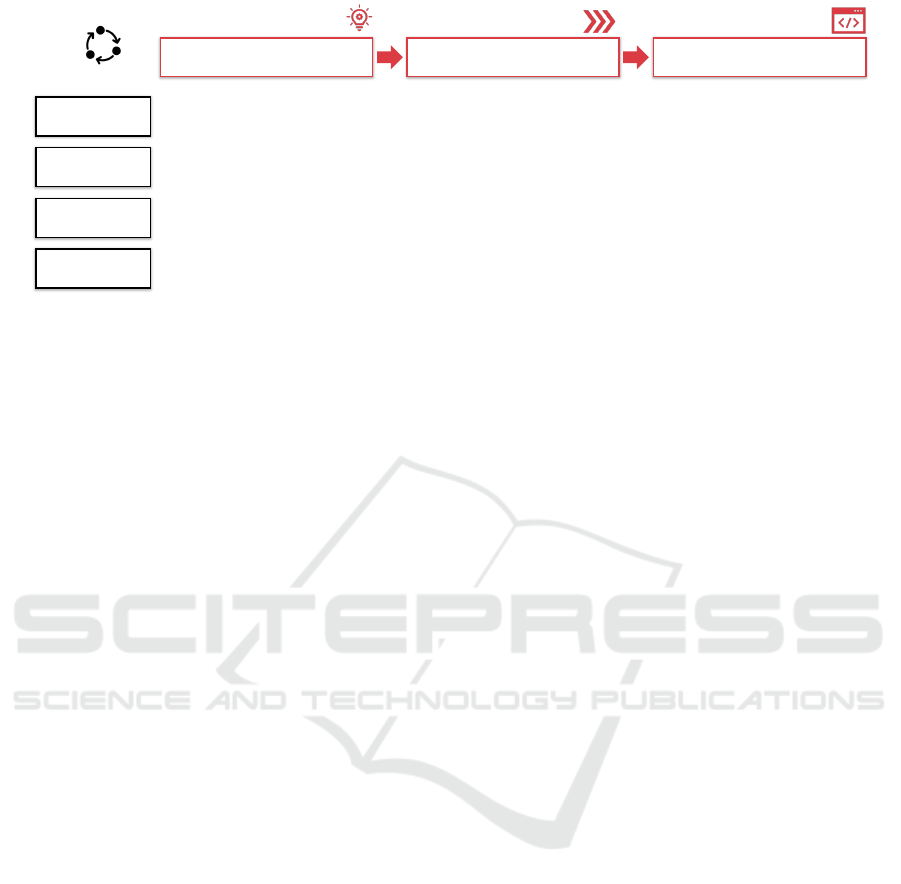
Benefits and Propositions Procedures and Guidelines
Concrete Concepts,
Systems and Techniques
Why?
How? Using?
Discovery
Modeling
Execution
Monitoring
BPM
Lifecycle Phases
-
Identifying
vulnerabilities
-
Assessing
risks
-
Explicit representation
of security
- Ensuring
security-by-design
-
Embedding
security into processes
-
Enforcement
of security controls
-
Reference model
for monitoring
-
Automated compliance
monitoring
- Initial process
inventory
-
Identify
and
document
processes
-
Modeling security
aspects
-
Validate models
against standards
-
Translate
models to
rules
-
IDS
integration
-
Continuous compliance
monitoring
-
Incident response
and feedback
- Process
discovery method
for IIoT
- Process mining on network data
- Security-aware
BPMN notation
-
IEC62443
standard integration
-
Formal syntax
definition
-
Transformation
of models to rules
- Compliance
monitoring framework
-
Automated
compliance
rule check
Figure 1: Overview of the presented process-centric IIoT security management framework.
• Identification of Research Gaps. On the basis of
the literature, one or more research gaps are iden-
tified and, in the following, approaches to closing
them are presented. The identification of these
gaps is critical, as it shapes the direction of the
research and pinpoints the specific challenges that
the developed artifacts must address.
• Presentation of Approaches. To address the re-
search gaps, one or more artifacts are discussed,
such as frameworks, models, methods, or tools.
The artifact’s development, presentation, testing,
and evaluation are explained to determine its ef-
fectiveness in closing the research gap. This in-
cludes a critical evaluation of how well the artifact
addresses the research gap and thus contributes to
the expansion of knowledge in the field.
2.4 Effectiveness for IIoT Security
Contextual Awareness for Enhanced Security.
Traditional security measures like IDS and firewalls
are essential, but their effectiveness improves signif-
icantly with a deeper understanding of the processes
they protect (Parker et al., 2023). BPM provides this
context by clarifying data flows, device interactions,
and information exchange within the system, enabling
more tailored security rules (Oberhofer et al., 2024).
For instance, understanding device communication
conditions allows for more precise monitoring and re-
sponse mechanisms, resulting in stronger security.
Holistic Approach to Security. Individual security
tools often address specific threats but can overlook
the broader context (Pulsipher et al., 2022). BPM
offers a holistic approach by mapping system work-
flows and understanding process functions, enabling a
comprehensive security strategy that integrates seam-
lessly with operations. This approach ensures security
is proactive, not just reactive.
Adaptability in Dynamic Environments. Indus-
trial systems are dynamic, with constant changes in
users, devices, and connections. Static security con-
trols quickly become outdated, increasing vulnerabil-
ity (Pulsipher et al., 2022). BPM keeps processes
well-defined and current, allowing continuous adjust-
ments to security mechanisms. This adaptability re-
duces the risk of legacy issues and maintains relevant,
effective security over time.
Streamlined Compliance Management. Stan-
dards like IEC 62443 require not only compliance
but also proof over time (IEC, 2009). Integrating se-
curity into business processes simplifies traceability,
allowing for continuous compliance management and
streamlined audits. BPM ensures security measures
can be verified throughout the process lifecycle,
supporting long-term governance.
Proactive Security and Operational Continuity.
Security measures can sometimes disrupt operations
unexpectedly (Goncharov, 2018). By incorporating
security into process design, BPM aligns security
mechanisms with operational needs from the start.
This proactive approach prevents conflicts between
security and functionality, ensuring that processes re-
main secure and fully operational, thus supporting
both security and smooth business operations.
3 LEVERAGING BPM METHODS
FOR IIoT SECURITY
To address IIoT’s unique security challenges, tra-
ditional controls can be complemented by process-
centric approaches that consider the entire industrial
lifecycle (Sch
¨
onig et al., 2022). BPM offers poten-
tial to enhance IIoT security by providing a struc-
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
244

tured way to design, analyze, and monitor processes,
enabling direct integration of security mechanisms
(Oberhofer et al., 2024). By formalizing and visualiz-
ing workflows, BPM helps organizations understand
device, data, and network interactions, ensuring secu-
rity is embedded throughout the process lifecycle.
This chapter explores how IIoT security can be
supported by means of the four key phases of the pro-
cess lifecycle: process discovery, modeling, execu-
tion, and monitoring. Each phase offers opportuni-
ties to strengthen security by systematically integrat-
ing controls into the design, execution, and monitor-
ing of processes.
3.1 Discovery
Process discovery identifies and documents existing
processes in an IIoT environment, clarifying how de-
vices, systems, and human operators interact (van der
Aalst, 2010). This helps organizations identify their
workflows, serving as the foundation for modeling,
execution, and monitoring phases. From a security
perspective, process discovery is crucial for identify-
ing vulnerabilities and gaps (Myers et al., 2017).
BPM-driven process discovery formalizes and
maps as-is processes, capturing data flows between
IIoT devices, systems, and control points. It identifies
critical tasks, data exchanges, and supporting infras-
tructure. For example, process discovery can reveal
how data flows from sensors to control systems and
storage platforms. It also uncovers risks like unmon-
itored data flows, vulnerable connections, or legacy
systems lacking security mechanisms.
BPM-driven process discovery helps create an in-
ventory of IIoT assets and interactions (Hornsteiner
et al., 2024), determining where to apply security con-
trols. Understanding the process landscape allows
teams to assess risks like unauthorized access or weak
authentication, prioritizing security mechanisms dur-
ing modeling and execution.
Insights from systematic process discovery also
help understand operational disruptions, such as cas-
cading effects from compromised devices. This sup-
ports proactive security mechanisms to guard against
threats. For example, if a critical sensor is identified,
additional monitoring or controls can be applied to
protect multiple processes.
3.2 Modeling
Process modeling formally represents business pro-
cesses using techniques like BPMN (Mendling et al.,
2010). In IIoT security, this step is key to defining in-
teractions between connected devices, data flows, and
actors. Explicitly modeling these interactions pro-
vides a transparent and comprehensive view of the op-
erational landscape, making it easier to identify vul-
nerabilities and enforce security mechanisms.
BPM methods provide a structured way to cap-
ture processes visually and formally. During model-
ing, critical security aspects - such as communication
paths, data exchanges, and access control points - are
mapped. For instance, BPMN diagrams can illustrate
how data moves from servers to control systems and
cloud storage. These workflows help security teams
to identify vulnerable points, such as unauthorized
data access or malicious device interactions.
Process modeling also allows the explicit repre-
sentation of security mechanisms within the process.
Controls such as data encryption, device authentica-
tion, or network segmentation can be integrated di-
rectly into the model, serving as templates for the
security mechanisms used during real-time monitor-
ing (Hornsteiner and Sch
¨
onig, 2023). By incorpo-
rating security early in the modeling phase, organiza-
tions ensure that it becomes integral to process design
rather than an afterthought.
BPM helps standardize and optimize interactions
typical in IIoT, reducing ambiguity and ensuring con-
sistent application of security across systems. Clear
documentation of process flows and interactions in
BPMN also improves communication between IT,
OT, and security teams, fostering a shared understand-
ing of system security requirements.
3.3 Execution
In the process execution phase, formally defined pro-
cesses are executed in real-time using automation
tools and systems. In IIoT environments, execution
involves the interaction of multiple devices, sensors,
and actuators, contributing to real-time operations of
critical processes. This phase is crucial for security,
as executing processes opens potential attack vectors
like unauthorized device access, data manipulation,
and network intrusion.
BPM enhances security during execution by em-
bedding security mechanisms directly into executable
processes. Formalizing workflows through model-
based execution allows for the tight integration of se-
curity controls, such as authentication, authorization,
and encryption-at the operational level (Hornsteiner
and Sch
¨
onig, 2023). For instance, BPM tools can
enforce access controls for actors (e.g., machines or
operators), ensuring that only authorized entities can
trigger actions, thereby reducing the risk of unautho-
rized access.
BPM methods standardizes data flows and com-
A Reflection on Process-Oriented Industrial IoT Security Management
245

munication channels between IIoT devices. Modeling
these interactions establishes clear security mecha-
nisms for device communication. Such specifications
mitigate risks like man-in-the-middle attacks or data
tampering by enforcing secure communication proto-
cols during BPM-driven executions.
Moreover, BPM-based execution frameworks can
incorporate real-time security monitoring as part of
the process. Embedding security checks into exe-
cuted workflows ensures continuous security assess-
ment. For example, if a device behaves anomalously,
predefined BPM rules can trigger alerts or initiate fail-
safe protocols to mitigate potential breaches.
3.4 Monitoring
The process monitoring phase is an ongoing step to
ensure the security and stability of IIoT environments.
Here, defined processes are continuously monitored
to ensure they conform to expected behaviors and se-
curity mechanisms. Effective monitoring is crucial
for detecting anomalies, identifying threats, and re-
sponding to incidents in real time. In IIoT, where sys-
tems are distributed and interconnected, monitoring
must be comprehensive and adaptive to detect devia-
tions across diverse devices and networks.
BPM plays a key role by providing a reference
model against which activities are monitored. BPM
models serve as benchmarks for secure operations,
enabling monitoring systems to track IIoT processes
in real time by comparing actual interactions with ex-
pected behaviors (Oberhofer et al., 2024).
Aligning monitoring systems with BPM-based
rules allows for targeted and efficient monitoring.
Specific events and interactions - such as unautho-
rized communication or anomalously sensor readings
- can trigger alerts. E.g., if the BPM model specifies
that a sensor sends data only during a defined win-
dow, any communication outside of that window can
be flagged for investigation. This reduces false posi-
tives and helps security teams focus on real threats.
BPM-driven monitoring also supports automated
incident response. When an anomaly is detected, pre-
defined actions - such as isolating devices, restricting
access, or triggering emergency protocols - can be ini-
tiated automatically, reducing response time and mit-
igating impacts.
Beyond security, BPM-based monitoring aids in
performance optimization and compliance. Continu-
ous monitoring against the BPM model helps detect
inefficiencies, enabling real-time adjustments to keep
processes secure and aligned with operational objec-
tives and regulatory requirements.
4 PROCEDURES AND
GUIDELINES
The following section outlines a structured approach
for organizations to leverage BPM techniques to en-
hance security in IIoT environments. By system-
atically integrating security considerations into each
phase of the process lifecycle, the framework aims to
help organizations better manage cyber risks in com-
plex IIoT ecosystems.
4.1 Process Discovery
Objective: Identify and understand all processes in
the IIoT environment, including potential security
risks.
Step 1: Initial Process Inventory. The first step
in the framework is to conduct a comprehensive in-
ventory of all IIoT-related processes within the or-
ganization. This includes identifying both business
workflows and the technical processes that underlie
IIoT operations. A combination of manual and auto-
mated methods is recommended for this phase. Man-
ual methods can include interviews with stakehold-
ers, document analysis, and workshops. Automated
methods, such as process mining, can further assist in
discovering workflows from system logs and network
data.
By discovering these processes, organizations
gain an understanding of how data flows between de-
vices, systems, and users. This serves as the foun-
dation for subsequent security analysis, providing a
clear view of the overall operational landscape where
security risks must be managed.
Step 2: Identify Security-Sensitive Points. Once the
process inventory is established, the next step is to
identify security-sensitive points within each discov-
ered process. These points are typically areas where
data exchange occurs between devices, through com-
munication channels, or at access points that could be
targeted by attackers. It is critical to engage security
experts during this step to conduct a thorough evalua-
tion of potential vulnerabilities in these processes.
The identification of security-sensitive points al-
lows organizations to focus their security efforts on
the most critical areas of the process. For example,
any communication between IIoT devices that involve
sensitive or critical data must be carefully examined
for vulnerabilities such as unencrypted transmissions,
weak authentication, or insufficient access control.
Step 3: Document Security Requirements. After
identifying security-sensitive points, the next step is
to document security requirements for each process,
ensuring objectives like confidentiality, integrity, and
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
246

availability are met. These requirements should align
with standards like IEC 62443 and may include en-
cryption, access controls, and data integrity checks.
This structured approach integrates security mecha-
nisms into the BPM cycle, providing a foundation for
continuous compliance monitoring and proactive risk
management in IIoT environments.
4.2 Process Modeling
Objective: Create security-aware models of the IIoT
process using BPMN or similar modeling techniques.
Step 1: Modelling Security Aspects. The next step
involves process modelling notations like BPMN.
Process knowledge from the previous phase is used
to formally visualize and model workflows of the IIoT
environment. Here, security mechanisms and controls
are incorporated directly into the IIoT process mod-
els. This includes embedding components such as
access control, data encryption, and communication
monitoring into the process workflows. It is essential
that these security controls are integrated in alignment
with industry standards like IEC 62443 to ensure ro-
bust security coverage.
Step 2: Validate Models Against Security Stan-
dards. Once the models are developed, they must
be continuously validated against relevant security
standards and organizational policies. This process
should involve collaboration between business and se-
curity stakeholders to ensure that both operational ef-
ficiency and security requirements are met.
4.3 Execution and Enforcement
Objective: Ensure the secure execution of processes
and real-time monitoring of compliance with security
mechanisms.
Step 1: Translate Models into Executable Rules.
The first step involves translating security-aware
BPMN models into executable rules that can be im-
plemented by security systems, such as Intrusion De-
tection Systems (IDS) or firewalls. Tools or middle-
ware should be used to convert the security attributes
embedded in the BPMN models into enforceable poli-
cies that ensure processes adhere to the defined secu-
rity requirements during execution. This step bridges
the gap between formal process models and their real-
world implementation in IIoT environments.
Step 2: Real-Time Monitoring and IDS Integra-
tion. Once the processes are translated into exe-
cutable rules, continuous monitoring is critical. This
involves integrating with an IDS to track compliance
with security mechanisms in real-time. The system
monitors key aspects of the process execution, such
as encrypted communications, access control enforce-
ment, and potential suspicious network behavior. This
ensures that any deviation from the modeled security
requirements is detected and addressed immediately.
Step 3: Adapt to Dynamic Threats. To main-
tain robust security, the system must be adaptable to
evolving IIoT threats. Automated updates to security
mechanisms should be enabled, allowing the system
to respond to new threats as they arise. Leveraging
AI and machine learning algorithms, the system can
identify emerging attack vectors and adjust security
controls in real-time, ensuring continued protection as
the threat landscape changes.
4.4 Monitoring and Compliance
Objective: Continuously monitor process execution
for compliance with security standards and respond
to any violations or anomalies.
Step 1: Continuous Compliance Monitoring. In
this step, continuous compliance monitoring mech-
anisms are implemented to ensure scalability and
adaptability in complex and heterogeneous IIoT en-
vironments. By incorporating machine learning tech-
niques, the system can predict potential security vi-
olations or breaches before they occur, allowing for
dynamic adjustments to compliance controls based on
real-time network behavior.
Step 2: Incident Response and Feedback Loop.
When a security violation or anomaly is detected,
predefined incident response workflows are triggered
immediately. This step also establishes a feedback
loop where insights gathered from continuous mon-
itoring are fed back into the discovery and modeling
phases. This iterative approach improves process se-
curity over time, enhancing overall system resilience
against emerging threats.
5 CONCEPTS AND TECHNIQUES
In Section 4 we showed that BPM can also help to ad-
dress challenges of security management in IIoT envi-
ronments. BPM methods provide a systematic way to
integrate security mechanisms such as policies, con-
trols, and monitoring in the operational process life-
cycle, ensuring that security is embedded from the
outset rather than treated as an afterthought.
As IIoT environments and especially security as-
pects are typically not represented and supported in
traditional BPM methods and systems, these require
new and adapted concepts e.g., procedures, nota-
tions, systems and algorithms. Following the research
methodology outlined in Section 2.3, we now address
A Reflection on Process-Oriented Industrial IoT Security Management
247
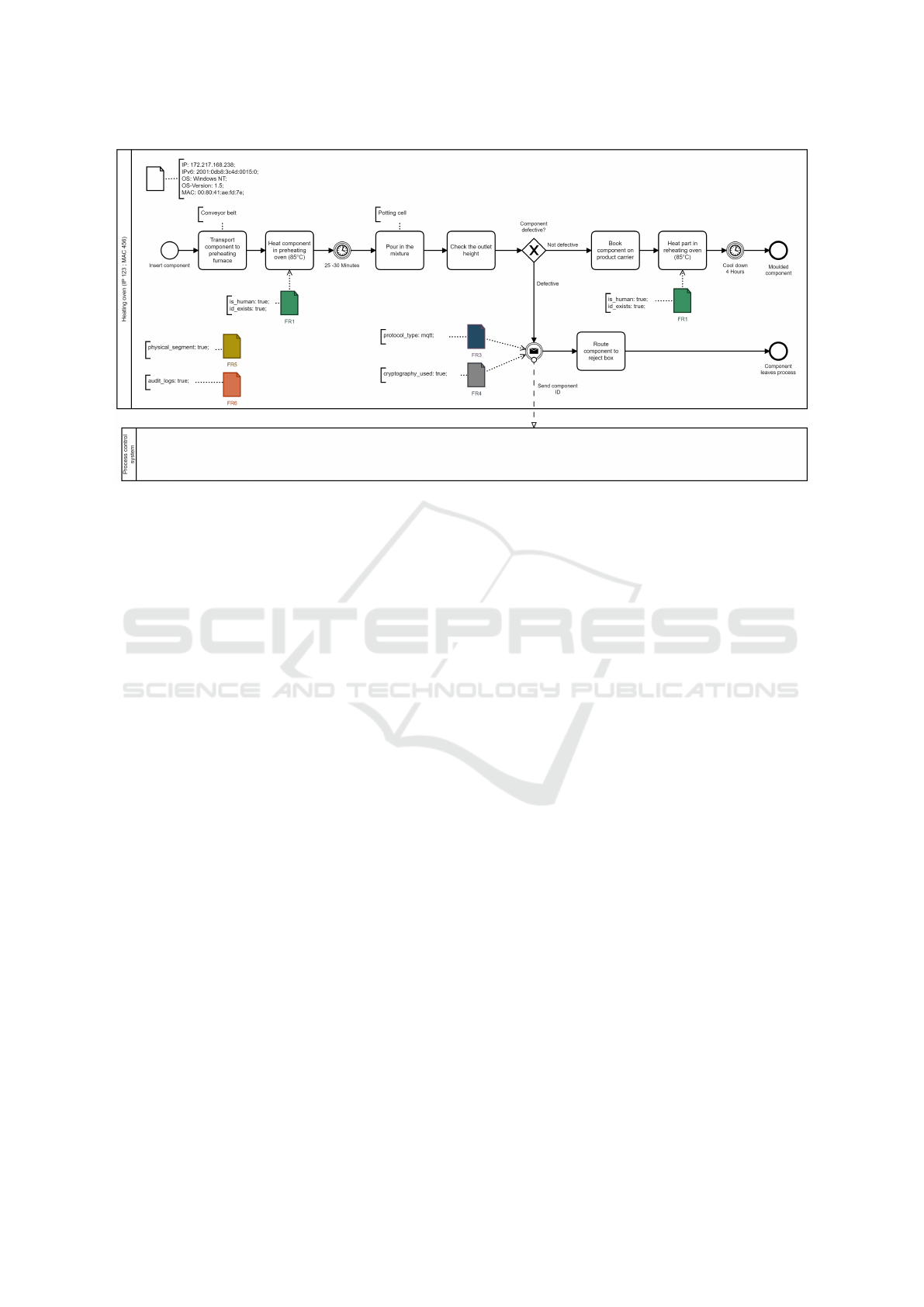
Figure 2: Use case for this paper: Industrial process for heating and filling components.
the key research gaps and highlight the latest scientific
advancements that support the use of BPM technol-
ogy for security management in IIoT scenarios. We
again structure our findings according to the process
lifecycle phases.
5.1 Real-World IIoT Process Use Case
In this section, each phase of the lifecycle is ex-
plained, including the corresponding questions, ap-
proaches, and artifacts, using the industrial process il-
lustrated in Figure 2. This process is an excerpt from
the real-world operations of an industry partner and
was modeled using the framework presented in Sec-
tion 4. In the following, various scientific artifacts are
introduced that support each phase of the lifecycle.
In the process shown in Figure 2, a component un-
dergoes several steps. First, the component is trans-
ported to a furnace for heating. After a specific time,
the component is filled with a material, and the filling
level is measured. If the filling exceeds a predeter-
mined threshold, the component is deemed defective
and rejected. The product ID of the rejected com-
ponent is then transmitted to the process control sys-
tem. If the component meets the required standards, it
is transported to a second furnace for reheating, then
cooled, and the process is completed.
5.2 Manual Process Discovery in IIoT
In the context of IIoT, how can manual process dis-
covery methods be adapted to ensure comprehen-
sive process identification for improved IIoT secu-
rity? Automated techniques are often favored for ef-
ficiency, but manual methods - including document
analysis, observation, interviews, and workshops - re-
main vital for capturing nuanced, human-driven pro-
cesses critical to IIoT security. However, how can
these manual techniques be systematically applied to
IIoT, where physical and cyber systems converge, cre-
ating unique operational complexities?
A review of existing literature (K
¨
olbel et al., 2024)
reveals that while manual discovery methods are well-
studied in traditional business environments, struc-
tured approaches for IIoT environments are scarce.
The integration of physical processes, real-time data,
and machine interactions in IIoT presents challenges
that generic manual methods do not adequately ad-
dress. Literature emphasizes human-driven insights
for identifying security-relevant processes, yet lacks
an adaptable framework for IIoT.
The identified gap is the absence of a structured
procedure for manual process discovery tailored to
IIoT security management. Unlike traditional envi-
ronments, IIoT involves complex cyber-physical in-
teractions, making it difficult to capture all processes
without a framework that considers specific IIoT char-
acteristics, such as device communication, real-time
data flows, and the physical-virtual interface. Current
manual methods, used without adaptation, lead to po-
tential security blind spots.
To address this, K
¨
olbel et al. (2024) introduces
a structured procedure for manual process discovery
targeting IIoT environments. This framework adapts
classic manual methods like document analysis, ob-
servation, and interviews to IIoT needs. For instance,
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
248

document analysis emphasizes operating manuals and
system logs highlighting device communication and
data processing crucial for security.
The framework also proposes a mixed-method ap-
proach combining multiple discovery techniques for a
comprehensive IIoT overview. The evaluation shows
the guidelines benefit both beginners, with step-by-
step instructions, and experts, by ensuring consistent
quality standards during process discovery.
This structured approach ensures accurate identifi-
cation of critical processes in IIoT, providing a foun-
dation for integrating security mechanisms through-
out the process lifecycle.
Using the framework, initial process drafts (Fig-
ure 2) were discovered through a mixed-method ap-
proach: document analysis, followed by interviews,
and observation. Security mechanisms were then
added through expert interviews and document analy-
sis. However, no structured approach currently exists
for discovering these security mechanisms. Section 6
proposes future research to address this gap.
5.3 Process Mining IIoT Network Data
Process mining has become a powerful tool for dis-
covering business processes from data logs, offer-
ing insights into operational efficiency and identify-
ing bottlenecks. However, its application in the IIoT
remains an emerging and unexplored area. This raises
a key question: How can process mining be effec-
tively applied to real-world IIoT network data to en-
hance operational security and efficiency? Given
that IIoT environments generate vast amounts of net-
work data, there is significant potential for uncover-
ing detailed, security-relevant processes through pro-
cess mining. The challenge lies in adapting existing
techniques to deal with the complexities and scale of
IIoT data while addressing real-world industrial ap-
plications rather than simulations.
A review of the literature highlights a growing in-
terest in applying process mining techniques to net-
work data, with a variety of approaches having been
developed in recent years (Engelberg et al., 2021;
Hadad et al., 2023; Wakup and Desel, 2014). Pro-
cess mining on network data has shown promise in de-
tecting anomalies, uncovering hidden processes, and
optimizing operational workflows. However, as indi-
cated in Hornsteiner et al. (2024), these studies focus
on simulated environments or general network data,
leaving a gap when it comes to applying these tech-
niques to industrial network data. Industrial environ-
ments, with their complex interactions between physi-
cal devices, sensors, and control systems, pose unique
challenges that are not yet addressed in existing work.
Moreover, using real-world data for process mining
introduces issues such as data heterogeneity, noisy
logs, and the difficulty of capturing relevant events in
a meaningful way for process discovery.
The primary gap identified is the lack of process
mining approaches applied to real-world industrial
network data. While several studies have demon-
strated the viability of using network data for process
mining, they rely on simulated data or simplified en-
vironments, which do not accurately reflect the com-
plexity of industrial processes. Real-world IIoT net-
work data is far more challenging due to the diver-
sity of devices, the mix of machine-to-machine com-
munications, and the variety of protocols involved.
Furthermore, data from industrial environments of-
ten contains noise or irrelevant information, making
it difficult to extract meaningful event logs for pro-
cess discovery. This creates a significant gap between
the potential of process mining in IIoT and its actual
application in real-world scenarios.
To address this gap, Hornsteiner et al. (2024) in-
troduces a novel approach based on actual industrial
network environments, moving beyond previous stud-
ies that relied on simulated datasets. This shift pro-
vides an accurate representation of challenges and op-
portunities inherent in IIoT, e.g., handling large data
volumes, dealing with noisy or incomplete logs, and
identifying key security and operational events.
The approach begins by recording network data
from an operational IIoT environment, which is then
used to generate event logs from network traffic.
These logs serve as the foundation for discovering ac-
tual process models, enabling businesses to visualize
and analyze their workflows. The methodology con-
siders the unique characteristics of IIoT systems - ma-
chine, sensor, and control system interactions - ensur-
ing the process models are both accurate and action-
able for improving security and operational efficiency.
The developed methodology outlines how raw
network data is transformed into event logs, and how
process mining is applied to uncover previously hid-
den processes. This approach not only addresses
the research gap by applying process mining to real-
world IIoT data but also provides organizations with a
practical tool for gaining deeper operational insights.
Evaluations have shown the approach to be effective
in discovering operational processes, identifying in-
efficiencies, and detecting potential security risks in
IIoT environments. Network data from IIoT systems
is particularly valuable for capturing not only basic in-
formation such as IP addresses, protocols, or encryp-
tion methods, but also more detailed network char-
acteristics, including device communication patterns.
This insight can be used to segment the network and
A Reflection on Process-Oriented Industrial IoT Security Management
249

enhance overall security.
To evaluate the approach, the main control-flow
dependencies of the process depicted in Figure 2
where automatically discovered based on analysing
OPC-UA network data that has been recorded before.
5.4 Modelling Security-Aware Processes
The second phase of the BPM lifecycle focuses on
process modeling, where abstract representations of
processes are defined using notations such as the de-
facto standard BPMN. In IIoT, the challenge arises of
how BPMN can be adapted to not only model opera-
tional processes but also integrate security awareness.
Specifically, the research question is: How can BPMN
be extended to model IIoT processes in a security-
aware manner, ensuring that security requirements
and rules are embedded in the process design and can
be monitored for compliance throughout execution?
A literate review by Hornsteiner et al. (2022) ex-
plores existing research on BPMN modeling in both
IIoT and security contexts. This indicates that, al-
though BPMN extensions exist that are specifically
tailored for either IIoT or security, a comprehensive
solution that fully integrates both domains has yet to
be developed. Current approaches either focus solely
on modeling IIoT operations without considering se-
curity, or address general security concerns without
specific considerations of IIoT environments. This
highlights a critical gap: existing BPMN frameworks
lack the ability to model IIoT processes in a way that
directly incorporates and enforces security measures.
The literature review identified two main gaps:
1. There is no unified framework that integrates both
IIoT modeling elements and security concerns,
which is crucial for securing complex IIoT en-
vironments. Existing BPMN extensions address
either IIoT or security, but lack an integrated ap-
proach to cover both aspects effectively.
2. Although some BPMN extensions capture secu-
rity mechanisms, they provide no process moni-
toring solutions, lacking the continuous controls
necessary for ensuring compliance and mitigating
threats in real time during process execution.
These gaps highlight the need for a BPMN extension
that models and enforces IIoT security mechanisms.
To address this gap, Hornsteiner and Sch
¨
onig
(2023) recently introduces SIREN, a BPMN ex-
tension specifically designed for modeling security-
aware processes in IIoT environments. SIREN ex-
tends BPMN by incorporating elements based on the
IEC 62443 standard, which is well accepted in the
industrial security domain. These new elements al-
low modelers to define and visualize security con-
trols alongside operational processes. For example,
SIREN introduces symbols and annotations for spec-
ifying access control, data integrity, and encryption
protocols that must be enforced during IIoT process
execution.
In addition to providing a framework for security-
aware modeling, SIREN also introduces an approach
for monitoring compliance in real time. The approach
ensures that security controls modeled in BPMN
can be translated into monitorable rules, which are
then implemented within network monitoring sys-
tems. This allows security teams to track whether
processes adhere to the predefined security protocols
and receive alerts if any violations occur. The combi-
nation of process modeling and continuous monitor-
ing ensures that security is not just a design-time con-
cern but is actively enforced throughout the execution
phase of the process lifecycle.
The effectiveness of SIREN was successfully val-
idated through several case studies in industrial set-
tings like the process of Figure 2, demonstrating that
it not only enables the clear and structured modeling
of security concerns within IIoT processes but also fa-
cilitates real-time security monitoring. By providing
both the tools to model and enforce security controls,
SIREN fills the gap identified in the literature and of-
fers a practical solution for organizations seeking to
secure their IIoT operations comprehensively.
5.5 Executing and Monitoring
Security-Aware IIoT Processes
Once processes have been discovered and modeled,
the next challenge is ensuring their correct execu-
tion and continuous monitoring. The guiding research
question is: How can security-aware business process
models in IIoT environments be executed and moni-
tored to enforce security in real-time, ensuring com-
pliance with standards like IEC 62443? While it is
possible to model security mechanisms in BPMN, the
question remains how these can be translated into en-
forceable, monitorable controls during execution.
The literature review of Hornsteiner et al. (2022)
reveals that existing approaches focus on the visual
representation of security mechanisms in BPMN but
fail to address execution and real-time enforcement.
BPMN extensions for specific contexts, such as data
security, access control, or integrity, are widely dis-
cussed, but they stop short of bridging the gap to ac-
tual implementation within IIoT environments. Fur-
thermore, existing work on real-time monitoring fo-
cuses heavily on traditional IT systems and does
not fully explore cyber-physical interactions found in
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
250

IIoT, where the complexity of connected devices and
networks poses additional security challenges.
Two major gaps emerge from literature:
• Modeling to Execution. There is a lack of
approaches for translating security-aware BPMN
models into executable processes that can be mon-
itored in real time. While BPMN provides visual
extensions to model security mechanisms, these
are not operationalized into enforceable controls
during process execution in IIoT environments.
• Continuous Compliance Monitoring. Existing
research on process monitoring tends to focus
on IT systems or simulated environments, leav-
ing out industrial network data and the complex-
ities of real-world IIoT. Additionally, many ap-
proaches do not integrate continuous compliance
monitoring mechanisms that ensure security poli-
cies, such as those defined by IEC 62443, are en-
forced throughout the process lifecycle.
To address these gaps, the development and appli-
cation of the SIREN markup language and the Secu-
rity Compliance Monitoring and Verification (SCMV)
framework from Oberhofer et al. (2024) is proposed.
SIREN, as depicted in Figure 2, allows security mech-
anisms, such as access control, encryption, and in-
tegrity, defined during process modeling to be em-
bedded in BPMN models based on IEC 62443 stan-
dards. These mechanisms are then transformed into a
set of actionable controls that can be monitored by an
IDS, ensuring that processes are continuously moni-
tored for compliance during execution.
The SCMV framework integrates real-time moni-
toring of these controls, ensuring that as processes ex-
ecute, compliance with security standards is actively
enforced. For instance, if the model specifies data
encryption, the IDS monitors network traffic to en-
sure compliance with this requirement. Unauthorized
access attempts or deviations from modeled behavior
trigger alerts, enabling early detection of threats. This
approach turns BPMN models from static representa-
tions into dynamic, enforceable security mechanisms
that respond to evolving threats in real-time.
By embedding security in BPMN and leveraging
the IDS to monitor execution, the framework ensures
that IIoT processes maintain compliance with security
requirements. This integrated approach closes the gap
between modeling, execution, and continuous moni-
toring, providing organizations with a robust, scalable
solution to secure IIoT processes in real-time.
6 CHALLENGES AND
INTERSECTIONS
6.1 Procedure for Developing Security
Enhanced Process Models
Before the concepts developed and presented can be
applied, the associated process model and the secu-
rity requirements for the process must be known for
the process under consideration. These are the funda-
mental basis of the concepts. A prerequisite for apply-
ing BPM in IIoT is discovering both, processes and
their security requirements. Manual methods, such
as interviews, observations, or workshops, are com-
monly used to discover process models, while auto-
mated methods like process mining can also be ap-
plied. However, none of these methods currently pro-
vide a structured approach for discovering security re-
quirements within processes.
Future work should address developing methods
for identifying security requirements in processes.
Key questions include:
• Can security requirements be discovered in paral-
lel with or integrated into process discovery?
• How can discovered security requirements be cor-
rectly assigned within models?
• Which manual or automated methods are suitable
for security requirement discovery, and are new
concepts needed?
Further research into process evaluation and security
is needed to answer these questions.
6.2 Security-Aware Models for Holistic
and Automated Risk Management
Security-aware process models can be used for auto-
mated security risk management, specifically support-
ing the interaction between the three steps: Risk As-
sessment, Risk Response, and Risk Monitoring. The
concept of security requirements and the monitoring
of their compliance can be integrated within the risk
management process. Such security controls are dis-
covered during the Risk Assessment, automatically
implemented during Risk Response, and then moni-
tored within the Risk Monitoring phase. This enables
a holistic view of the risk management process, which
is essential for end-to-end automation. Implementing
this automation is a challenging task, dependent on
future advancements. Particularly in the domain of
IIoT, where security functionalities must not compro-
mise system safety, automated, planned, and context-
A Reflection on Process-Oriented Industrial IoT Security Management
251

oriented execution of security processes is more reli-
able than human interactions.
In Risk Assessment, security-aware process mod-
els define a catalog of security controls with their crit-
icality, based on different standards, regulations, or
laws. The process model acts as an output report of
the Risk Assessment process and also serves as in-
put for the second phase. Within the automated Risk
Response, the machine-readable security control cat-
alog is implemented and forms the basis for ongoing
verification of the risk status within Risk Monitoring.
Risk Monitoring benefits from security-aware process
models in the form of compliance monitoring, as de-
scribed in this work.
Another area where process models help improve
automation within security risk management is the
generalization of security controls. After security
controls are discovered and integrated into process
models, they need to be generalized to work with dif-
ferent security standards, regulations, or laws. This
generalization can be achieved within the process
models themselves by defining a common security-
aware process language, for example, based on the
common control framework, in combination with a
mapping of specific security controls (e.g., IEC 62443
security requirements) to similar controls within other
policies. The generalized controls displayed in the
process models should be automatically transformed
into policy-specific versions.
In conclusion, future work should aim to increase
the automation of security risk management by im-
plementing a holistic, process-centered approach that
leverages the potential of integrating security-aware
process models into the risk management lifecycle.
6.3 AI-Based Model Explanation
The concepts in this paper are all designed for the ap-
plication of security requirements. The results are,
among other things, process models with security re-
quirements. One problem that arises is the compre-
hensibility and readability of the models for people
who are not familiar with the modelling language or
who do not know the security requirements and their
origin, or who have no background knowledge of
IT security. Nevertheless, in order to define process
models, security requirements and their origin under-
standable for ‘non-experts’, a way of explaining the
process models is needed. One idea that is already be-
ing realised is the comparison of process models with
security standards and norms using Large Language
Models (LLM). To this end, models are translated into
XMLs for readability by the LLMs. The objective is
to enable LLMs to explain the models and the secu-
rity requirements they contain. LLMs should assess
whether modelled security aspects fulfil the require-
ments of selected standards and explain why these
are or are not fulfilled. In addition, LLMs should
make suggestions for improving the implementation
to date. In order to obtain such a LLM-based explana-
tion, research in the field of prompt engineering must
be carried out and applied to corresponding example
scenarios in the future.
7 CONCLUSION AND OUTLOOK
In light of growing security challenges in IIoT en-
vironments, this paper demonstrates the value of in-
tegrating security mechanisms across the entire life-
cycle of BPM. By synthesizing various research
streams, including manual and automated process dis-
covery, security-aware modeling, execution and com-
pliance monitoring, the paper provides a comprehen-
sive insight for embedding security into IIoT pro-
cesses. This approach not only strengthens the en-
forcement of real-time security, but also ensures con-
tinuous alignment with established standards such as
IEC 62443. By incorporating these methods, orga-
nizations can achieve a more resilient IIoT infras-
tructure, where security is integrated into the core of
process management and helps to mitigate risk in in-
creasingly complex industrial systems. The presented
research addresses critical gaps how security can be
effectively modeled, executed, and monitored, and
highlights the need for a holistic perspective when
addressing security in the IIoT. The findings provide
both researchers and practitioners with a structured
path for applying BPM to industrial security, offer-
ing a unifying perspective that ties together several
existing approaches. While this paper lays the foun-
dation for embedding security into the BPM lifecycle
for IIoT environments, it leaves open questions for
future work that could further strengthen this integra-
tion. One important direction is to develop a struc-
tured approach to identifying security requirements.
While methods for process discovery to identify busi-
ness processes in the IIoT have been explored, there
is a need for a dedicated framework that systemati-
cally reveals security requirements during the discov-
ery phase and ensures that security risks are identified
early in the process. Furthermore, future work should
focus on advancing AI-driven and model-based secu-
rity compliance assessment. By employing artificial
intelligence and formal models, it is possible to en-
hance real-time monitoring and automatic compliance
verification, especially in dynamic IIoT environments
where threats develop quickly. AI techniques could
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
252

enable adaptive security mechanisms that respond to
new threats and continuously optimize compliance
monitoring, making security processes more scalable
and adaptable. These advances could further close the
gap between security modeling and real-time enforce-
ment, ensuring that IIoT processes remain secure and
compliant throughout their lifecycle, even as indus-
trial environments become more complex.
REFERENCES
Bernardo, R., Galina, S. V. R., and de P
´
adua, S. I. D. (2017).
The BPM lifecycle: How to incorporate a view ex-
ternal to the organization through dynamic capability.
Bus. Process. Manag. J., 23(1):155–175.
Dumas, M., Rosa, M. L., Mendling, J., and Reijers, H. A.
(2018). Fundamentals of Business Process Manage-
ment, Second Edition. Springer.
Engelberg, G., Hadad, M., and Soffer, P. (2021). From net-
work traffic data to business activities: A process min-
ing driven conceptualization. In Enterprise, Business-
Process and Information Systems Modeling BPMDS,
volume 421, pages 3–18. Springer.
ENISA (2018). Good Practices for Security of Internet of
Things in the context of Smart Manufacturing. Euro-
pean Union Agency for Cybersecurity.
Goncharov, E. (2018). Challenges of industrial cybersecu-
rity. Kaspersky Lab ICS CERT, 5.
Hadad, M., Engelberg, G., and Soffer, P. (2023). From net-
work traffic data to a business-level event log. In En-
terprise, Business-Process and Information Systems
Modeling - 24th International Conference, BPMDS,
volume 479, pages 60–75. Springer.
Hansen, H. R., Mendling, J., and Neumann, G. (2019).
Wirtschaftsinformatik (12. Aufl.). De Gruyter
Studium.
Hornsteiner, M., Empl, P., Bunghardt, T., and Sch
¨
onig, S.
(2024). Reading between the lines: Process mining
on OPC UA network data. Sensors, 24(14):4497.
Hornsteiner, M. and Sch
¨
onig, S. (2023). SIREN: design-
ing business processes for comprehensive industrial
iot security management. In 18th International Con-
ference on Design Science Research in Information
Systems and Technology, DESRIST, volume 13873 of
Lecture Notes in Computer Science, pages 379–393.
Springer.
Hornsteiner, M., Stoiber, C., and Sch
¨
onig, S. (2022).
Towards security- and iiot-aware BPMN: A sys-
tematic literature review. In ICSBT, pages 45–56.
SCITEPRESS.
IEC (2009). Cybersecurity for Operational Technology in
Automation and Control Systems. Standard, Interna-
tional Electrotechnical Commission.
K
¨
olbel, L., Hornsteiner, M., and Sch
¨
onig, S. (2024). Guide-
line for manual process discovery in industrial iot.
CoRR, abs/2410.11915.
Mendling, J., Reijers, H. A., and van der Aalst, W. M. P.
(2010). Seven process modeling guidelines (7PMG).
Inf. Softw. Technol., 52(2):127–136.
Myers, D., Radke, K., Suriadi, S., and Foo, E. (2017).
Process discovery for industrial control system cyber
attack detection. In ICT Systems Security and Pri-
vacy Protection, volume 502 of Advances in Infor-
mation and Communication Technology, pages 61–75.
Springer.
Oberhofer, D., Hornsteiner, M., and Sch
¨
onig, S. (2024).
Process-aware security standard compliance monitor-
ing and verification for the iiot. In 32nd European
Conference on Information Systems ECIS.
Palattella, M. R., Dohler, M., Grieco, L. A., Rizzo, G.,
Torsner, J., Engel, T., and Ladid, L. (2016). Internet of
things in the 5g era: Enablers, architecture, and busi-
ness models. IEEE J. Sel. Areas Commun., 34(3):510–
527.
Parker, S., Wu, Z., and Christofides, P. D. (2023). Cyberse-
curity in process control, operations, and supply chain.
Comput. Chem. Eng., 171:108169.
Pulsipher, D. W., Scott, A., and Reeb, F. (2022). An argu-
ment for a holistic approach to critical infrastructure
security. Intel Corporation.
Sch
¨
onig, S., Hornsteiner, M., and Stoiber, C. (2022).
Towards process-oriented iiot security management:
Perspectives and challenges. In Enterprise, Business-
Process and Information Systems Modeling - 23rd
International Conference, BPMDS, pages 18–26.
Springer.
Serror, M., Hack, S., Henze, M., Schuba, M., and Wehrle,
K. (2021). Challenges and opportunities in securing
the industrial internet of things. IEEE Trans. Ind. In-
formatics, 17(5):2985–2996.
Sisinni, E., Saifullah, A., Han, S., Jennehag, U., and Gid-
lund, M. (2018). Industrial internet of things: Chal-
lenges, opportunities, and directions. IEEE Trans. Ind.
Informatics, 14(11):4724–4734.
Tange, K., Donno, M. D., Fafoutis, X., and Dragoni, N.
(2020). A systematic survey of industrial internet
of things security: Requirements and fog comput-
ing opportunities. IEEE Commun. Surv. Tutorials,
22(4):2489–2520.
van der Aalst, W. M. P. (2010). Process discovery: Captur-
ing the invisible. IEEE Comput. Intell. Mag., 5(1):28–
41.
Wakup, C. and Desel, J. (2014). Analyzing a tcp/ip-protocol
with process mining techniques. In Business Process
Management Workshop, volume 202, pages 353–364.
Weske, M. (2012). Business Process Management -
Concepts, Languages, Architectures, 2nd Edition.
Springer.
zur Muehlen, M. and Ho, D. T. (2005). Risk management in
the BPM lifecycle. In Bussler, C. and Haller, A., ed-
itors, Business Process Management Workshops, Re-
vised Selected Papers, volume 3812, pages 454–466.
A Reflection on Process-Oriented Industrial IoT Security Management
253
