
Implementation of Rank Attack and Its Mitigation in RPL-Based IoT
Networks
Madhu Yadav and Rajbir Kaur
Department of CSE, The LNMIIT, Jaipur, 302031, Rajasthan, India
Keywords:
IoT, LLN, RPL, Rank Attacks.
Abstract:
The burgeoning interest in the Internet of Things (IoT) has led to the widespread deployment of Low-power
and Lossy Networks (LLNs). The Routing Protocol for Low-Power and Lossy Networks (RPL) is a standard
protocol designed for networks with resource-constrained devices and high packet loss rates. However, RPL is
vulnerable to various attacks, particularly rank attacks, which can disrupt network performance and compro-
mise security. This paper addresses this gap by implementing rank attacks in RPL using the Cooja Simulator
in Contiki OS and analyzing their impact on network performance. While rank attacks are extensively dis-
cussed in the literature, practical implementations remain limited. To mitigate these attacks, we propose a
novel trust-based mitigation strategy that integrates seamlessly with resource-constrained IoT devices. Our
approach dynamically computes trust metrics to detect and isolate malicious nodes, thereby improving net-
work security, reducing power consumption, and ensuring reliable packet transmission. Comparative analysis
demonstrates the superiority of our approach over existing techniques, offering enhanced scalability and adapt-
ability for secure IoT deployments.
1 INTRODUCTION
IoT devices operate under significant resource con-
straints, such as limited memory, power, and pro-
cessing capabilities. Routing protocols are essen-
tial for efficient data transmission in IoT, with the
Routing Protocol for Low-Power and Lossy Networks
(RPL)—developed by the IETF RoLL working group
(Baccelli and Philipp, 2013)—serving as a fundamen-
tal solution. RPL, integrated into the IoT protocol
stack (Figure 1), works alongside IEEE 802.15.4 to
enable interoperability and efficient communication
in low-power wireless networks.
However, IoT faces significant security challenges
due to its constrained nature, exposing devices and
networks to various attacks that threaten data integrity
and system functionality. Addressing these chal-
lenges is crucial for the secure and widespread de-
ployment of IoT systems.
Figure 1: Overview of the IoT protocol stack.
The remainder of this paper is organized as fol-
lows: - Section 2 reviews related work on rank at-
tacks and mitigation. - Section 3 introduces RPL and
its role in IoT security. - Section 4 presents a taxon-
omy of RPL attacks with a focus on rank attacks. -
Section 5 analyzes the simulation and impact of rank
attacks. - Section 6 describes rank attack detection
using a trust-based energy metric.
- Finally, Section 7 concludes with key findings
and contributions.
2 RELATED WORK
RPL (Baccelli and Philipp, 2013) is vulnerable to rank
attacks such as increase, decrease, and worst parent
attacks, which degrade network performance by in-
creasing energy consumption and reducing reliability
(Mayzaud et al., 2016) (Raoof et al., 2018). Mitiga-
tion strategies include IDS (Simoglou et al., 2021),
machine learning (Said et al., 2020), and trust-based
methods (Liu, 2021). Approaches like SecTrust-
RPL, DCTM (Hashemi and Aliee, 2019), and MRTS
(Djedjig et al., 2020) improve energy efficiency and
throughput. Statistical methods (Iuchi et al., 2015)
and deep learning (Choukri et al., 2020) show promise
Yadav, M. and Kaur, R.
Implementation of Rank Attack and Its Mitigation in RPL-Based IoT Networks.
DOI: 10.5220/0013205100003944
In Proceedings of the 10th International Conference on Internet of Things, Big Data and Security (IoTBDS 2025), pages 215-222
ISBN: 978-989-758-750-4; ISSN: 2184-4976
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
215

Figure 2: A network configuration with two RPL instances,
and 3 DODAGs.
but face challenges. Our model focuses on energy ef-
ficiency and trust evaluation without relying on hard-
ware or historical data, offering a lightweight solution
for rank attack mitigation.
3 THE RPL PROTOCOL
The Routing Protocol for Low-Power and Lossy
Networks (RPL) (Baccelli and Philipp, 2013) is
a distance-vector protocol designed for resource-
constrained devices in environments with high packet
loss. It constructs Destination Oriented Directed
Acyclic Graphs (DODAGs) combining tree and mesh
structures, with multiple instances optimized for met-
rics like energy consumption. RPL uses four ICMPv6
control messages (DIS, DIO, DAO, DAO-ACK), and
the trickle algorithm updates DIOs. Security is pro-
vided in three modes: Unsecured, Pre-Installed, and
Authenticated. Despite these measures, security chal-
lenges persist, emphasizing the need for lightweight
monitoring solutions. Figure 2 illustrates a net-
work configuration with two RPL instances and three
DODAGs.
4 RPL ATTACKS
The attacks are categorized into resource depletion,
topology disruption, and traffic manipulation de-
pending on the attacks’ effect on the IoT network
(Mayzaud et al., 2016). This taxonomy provides a
concise overview of RPL attacks, aiding in under-
standing and mitigating potential threats to network
security.
4.1 Resource Depletion Attacks
Resource depletion attacks aim to exhaust network
resources such as bandwidth, memory, and energy.
These attacks can disrupt normal network operations.
Rank Increase Attack increases energy consumption
by influencing nodes to choose more distant nodes as
parents. This is shown in (Figure 3(I)). Here, a mali-
Figure 3: RPL attacks (I).Rank Increase Attack (II).Rank
Decrease Attack (III).Worst Parent Attack
cious node 4 advertises a rank higher than node 2 and
node 3, causing nodes 6, 7 and 8 to select a distant
node 4 as their parent (Raoof et al., 2018).
4.2 Traffic Manipulation Attacks
Traffic manipulation attacks in Low-Power and Lossy
Networks (LLNs) occur when malicious entities dis-
rupt data flow by creating fake identities or injecting
malicious traffic.
Decrease Rank Attack involves advertising lower
ranks to disrupt the normal traffic flow, causing sub-
optimal or incorrect routes. This manipulation can
isolate nodes, impair communication, and potentially
lead to network partitioning, resulting in traffic dis-
ruptions and degraded overall network performance.
In (Figure 3(II)), a malicious node 3 advertises a
lower rank than node 2 and node 4, causing one-hop
neighbors of nodes 2 and 4 to choose the adversary as
their preferred parent (Raoof et al., 2018).
4.3 Topology Disruption Attacks
Topology disruption attacks target the RPL net-
work’s structure, affecting the routing paths and over-
all communication within the network. Malicious
nodes hinder optimal convergence and render nodes
communication-incapable.
In Worst Parent Attack, malicious nodes manipulate
parent selection, leading to suboptimal routing and
disrupting the network’s topology. In (Figure 3(III)),
a malicious node 3 advertises its unmodified rank or
a lower rank than its neighbors. The child nodes for-
ward the data traffic to 3. Instead of forwarding the
traffic to its legitimate parent (node 1), the malicious
node 3 forwards the traffic to the adversary’s worst
parent 6 (assuming node 6 has the highest rank among
node 3’s neighbors) (Raoof et al., 2018).
5 RANK ATTACKS: SIMULATION
AND ANALYSIS
We implement rank attacks using the Cooja simulator
on Contiki OS, which supports TCP/IP, multithread-
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
216

ing, and hardware abstraction. C programming and
protothreads are used, with Cooja enabling code
development. Java handles mote configuration, log
analysis, and visualization, while XML configures
simulations.
To evaluate the impact of rank attacks on network
performance, we use several performance metrics that
provide a comprehensive assessment of resource con-
sumption within the Contiki OS and Cooja simulation
environment.
Packet Delivery Ratio (PDR): Measures net-
work reliability by calculating the ratio of received
data packets to the total generated packets.
PDR =
∑
packet received
∑
packet sent
× 100%
Power Consumption: Quantifies the amount of
energy consumed by a device in performing various
operations in the network. We calculated power
consumption using the Powertrace tool in Contiki
OS, considering transmission, listening, CPU usage,
and low-power mode.
Energy(mJ) = (Transmit × 19.5mA + Listen ×
21.5mA + CPU × 1.8mA + LPM × 0.0545mA) × 3V
/ 32768
PowerConsumption(mW ) = Energy(mJ)/Time(sec)
Our analysis includes the implementation of rank
increase, rank decrease, and worst parent attacks.
The simulation parameters configured in InstantCon-
tiki3.0/Cooja are detailed in Table 1.
5.1 Rank Increase Attack
Specific modifications are needed in the source
code to execute a rank increase attack in Contiki’s
RPL implementation, focusing on files in the ”con-
tiki/core/net/rpl/” directory. In the ”rpl-private.h”
file (Figure 4), which contains declarations and con-
stants pertinent to the calculation of Directed Acyclic
Graph (DAG) ranks, modifications need to be made to
compromise the protective measures within the rank
computation algorithm.
Moreover, within ”rpl-timers.c” (Figure 5), which
oversees RPL timer functions, the segment of code re-
sponsible for managing node rank recalculations re-
quires modifications to deactivate this process, thus
maintaining the impact of the rank increase attack.
Figure 6a depicts the simulated network network
for a rank increase attack in the Contiki/COOJA sim-
ulator. A green circle represents the transmission
range of a node. Node 1 is designated as the sink
Table 1: Simulation Parameters.
Parameter Value
Coverage Area 110m x 110m
Number of Nodes 8 normal and 1 Malicious in
rank decrease attack, 12 nor-
mal and 1 malicious in rank
increase and worst parent at-
tack
Number of Nodes
mitigation simu-
lation
7 normal and 3 attacker,
3 malicious, 3 mitigation
nodes
Node Placement Random
Transmission
Range
50m
Interference
Range
60m
Transmission Ra-
tio
100
Reception Ratio 30-100 (variable)
Routing Protocol RPL
Network Protocol IPv6
Simulation Start
Delay
500 milliseconds
Radio Medium UGDM Distance Loss
Simulation Dura-
tion
60 minutes for rank increase
and rank decrease attack, 20
minutes for worst parent at-
tack, 1 hour 12 minutes for
rank attack mitigation
Figure 4: rpl private.h code modification.
Figure 5: rpl timers.c code modification.
node, while the remaining nodes act as normal sender
nodes. Node 3 is identified as a malicious node. The
blue lines connecting the nodes indicate potential ra-
dio communication. Double-outlined pink circles il-
lustrate nodes sensing their neighboring nodes within
the transmission range.
Implementation of Rank Attack and Its Mitigation in RPL-Based IoT Networks
217
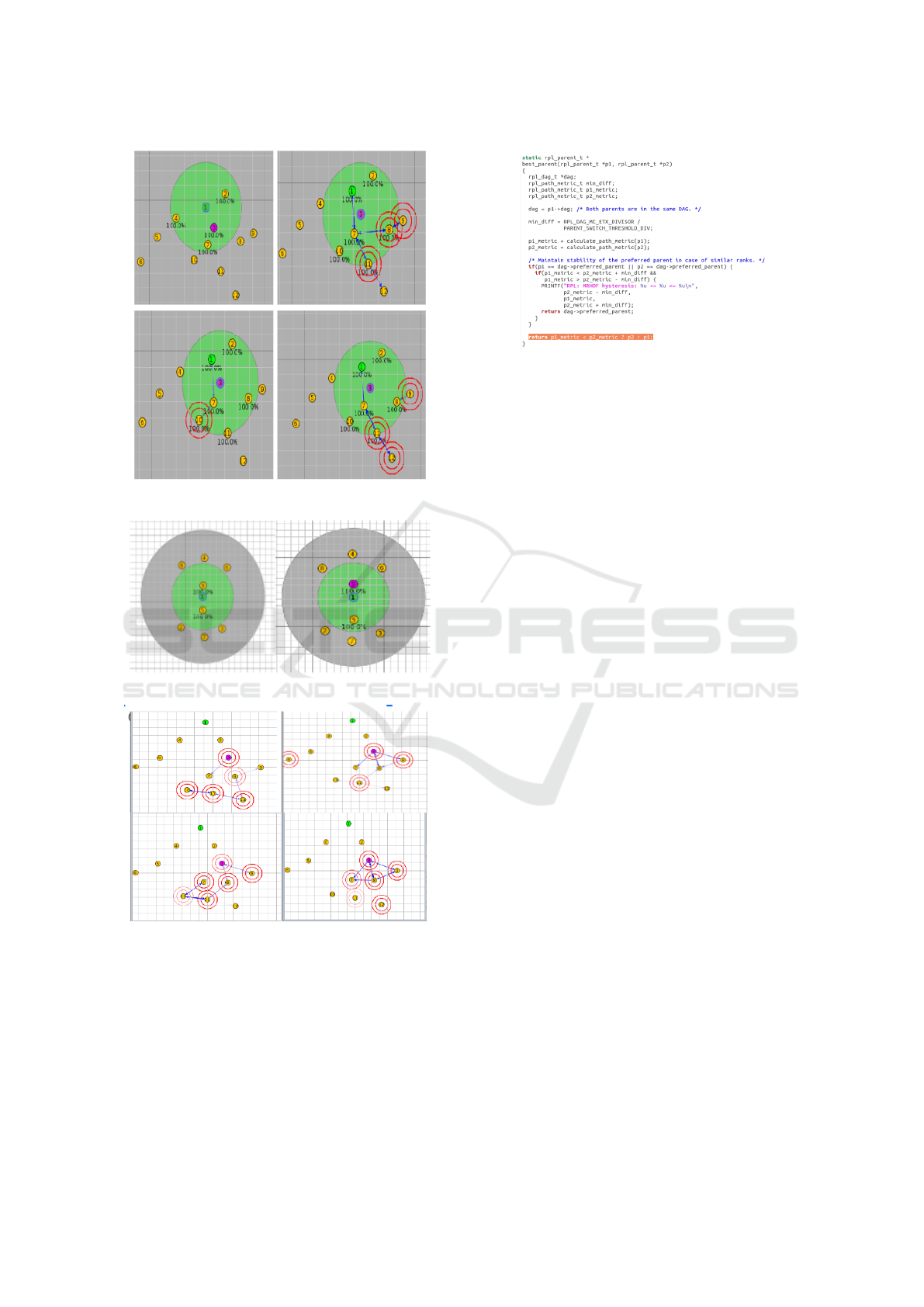
(a) Rank Increase Attack Simulation.
(b) Rank Decrease Attack Simulation.
(c) Worst Parent Attack Simulation.
Figure 6: Simulation Network.
5.2 Decrease Rank Attack
Similar changes are required in the files as mentioned
above 5.1, to execute the rank decrease attack. The
process is identical, involving modifications to con-
stants declared in ”rpl-private.h” and disabling rank
recalculation in ”rpl-timers.c”.
Figure 7: Modifications in rpl-mrhof.c.
Figure 6b illustrates the simulated network for a
rank decrease attack in the Contiki/COOJA simulator.
The left side of the figure represents the normal sce-
nario with no malicious node. Node 1 is assigned as
the sink node, and the remaining nodes function as
normal sender nodes. Node 9 is identified as a mali-
cious node on the right side of the figure. It intention-
ally discards packets originating from nodes 4, 6, and
8, leading to the isolation of these nodes and disrup-
tion of the network topology.
5.3 Worst Parent Attack
To simulate rank attacks in Contiki OS, we mod-
ified the metric evaluation function in the ”rpl-
mrhof.c” (Figure 7) file. Specifically, we modified
the ’best-parent’ function in the file. The parameters
of the function are two nodes that are candidates for
becoming the parent of a node. We modified the code
to select the weakest candidate as the preferred par-
ent. The ’rpl-select-parent()’ in ”rpl-dag.c” uses the
outcome of the ’best-parent()’ function to determine
the preferred parent in the DODAG structure.
Figure 6c presents the simulation network depict-
ing a worst-parent attack in the Contiki/COOJA sim-
ulator. Node 1 is designated as the sink node, and
the remaining nodes operate as normal sender nodes.
Node 3 is marked as a malicious node. Instead of
directing the packets toward the sink node, it inten-
tionally routes them through the worst path, leading
to delays and potential routing loops.
5.4 Analysis of the Effects of Rank
Attacks
In this section, we analyze the effects of rank at-
tacks on network performance parameters, such as the
packet delivered at the sink and power consumption.
1. In a rank increase attack, malicious nodes inten-
tionally manipulate the RPL (Routing Protocol
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
218
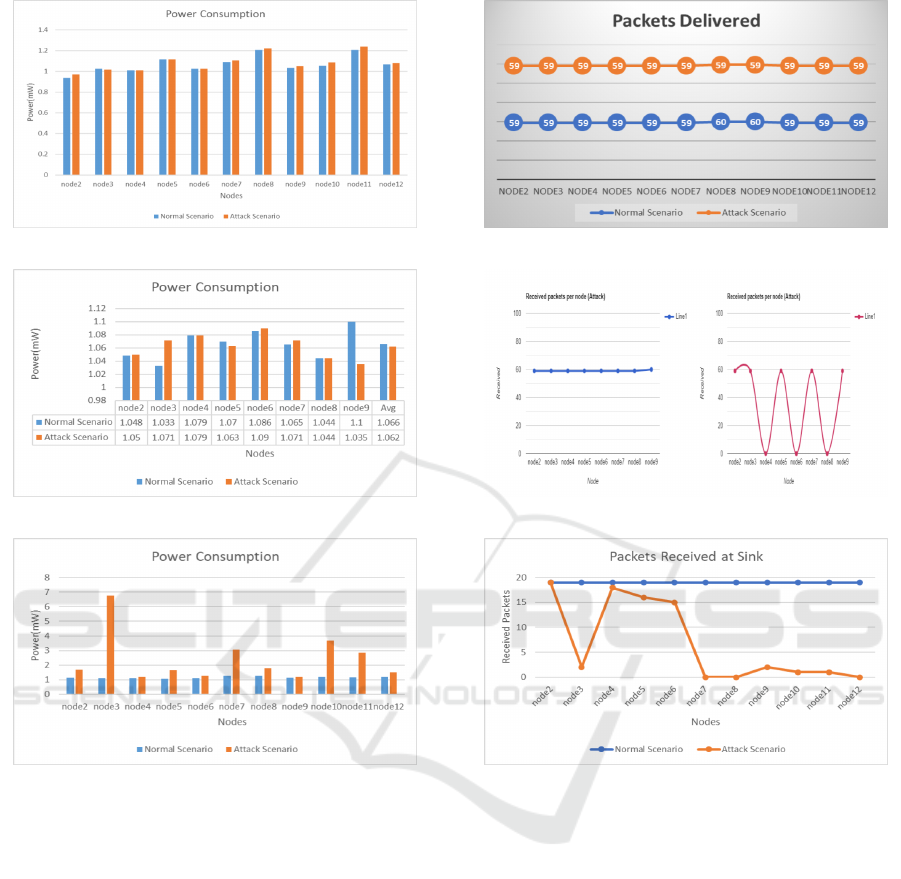
(I) Rank Increase
(II) Rank Decrease
(III) Worst Parent
Figure 8: Power Consumption.
for Low-Power and Lossy Networks) by choosing
suboptimal parents based on the objective func-
tion. This strategy increases energy consump-
tion (Figure 8(I)) and overhead traffic in the net-
work.(Figure 9 (I)) represents the packets deliv-
ered at the sink during the 60-minute simulation
period in both normal and attack scenarios.
2. The rank decrease attack overloads the network,
causing resource consumption attacks that drain
node batteries(Figure 8 (II)) and congest the RPL
network. The consequences include significant
disruption in traffic and the RPL’s DODAG (Des-
tination Oriented Directed Acyclic Graph), with
legitimate nodes connecting to the DODAG via
the attacker. This diverts much traffic, disrupting
the network’s topology and reducing the packet
delivery ratio(Figure 9 (II)).
(I) Rank Increase
(II) Rank Decrease
(III) Worst Parent
Figure 9: Packet Delivered at Sink.
3. The attacker’s systematic selection of the least-
preferred parent results in suboptimal paths and
poor overall network performance, including high
power consumption(Figure 8 (III)) and a low
number of packets delivered at the sink(Figure 9
(III)). Furthermore, the attacker may use the de-
creased rank method to attract more nodes as
parents, resulting in increased delays or routing
loops. To summarize, the worst parent attack
leads to network sub-optimization and heightened
end-to-end delays.
Implementation of Rank Attack and Its Mitigation in RPL-Based IoT Networks
219
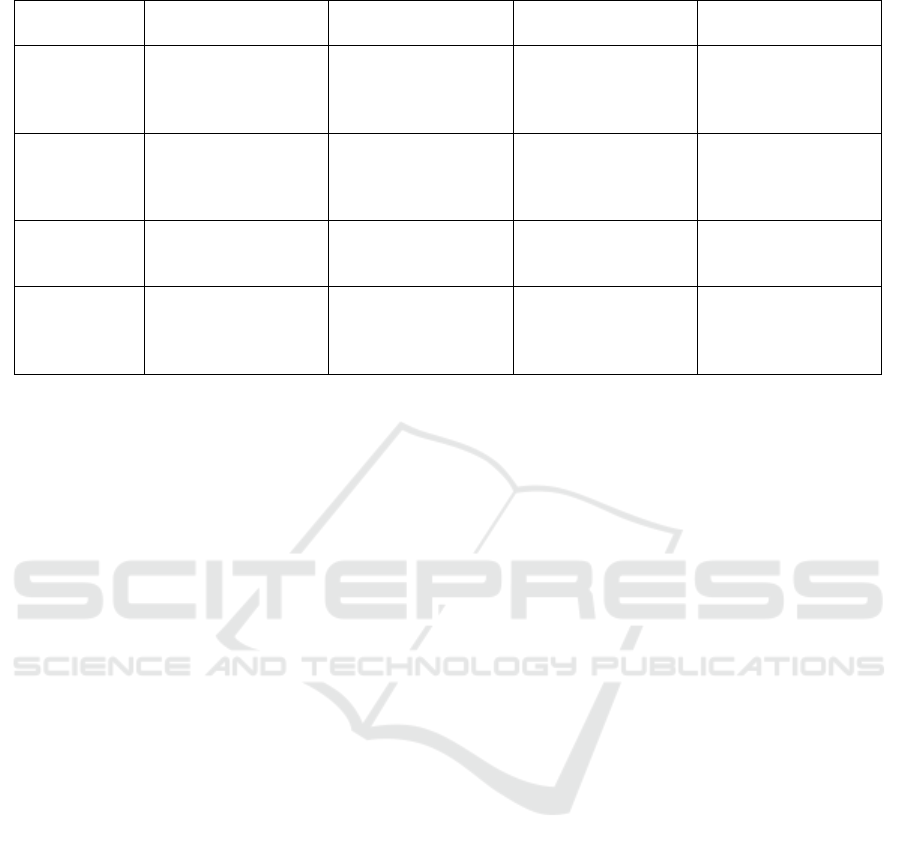
Table 2: Comparison of Rank Attack Analysis and Mitigation Approaches in RPL-Based IoT Networks.
Criteria Our Approach (Rouissat et al.,
2023)
(Algahtani et al.,
2021)
(A. Hkiri and
Machhout, 2024)
Attack Types
Covered
Three rank-based
attacks: rank in-
crease, decrease,
worst-parent.
Silent decreased rank
attack only.
Covers multiple RPL
attacks, no focus on
rank-based attacks.
Decreased rank at-
tack only.
Mitigation
Strategy
Trust-based real-time
mitigation to detect
and isolate malicious
nodes.
Lightweight counter-
measure for silent de-
creased rank attack.
Simulation frame-
work, no specific
mitigation strategies.
No mitigation or
real-time defense
proposed.
Performance
Metrics
Evaluated
Energy, PDR, la-
tency, overhead, and
other metrics.
Energy, latency, and
overhead only.
Focuses on generat-
ing data, not defense
analysis.
PDR, throughput,
and power consump-
tion.
Attack Anal-
ysis and Mit-
igation Inte-
gration
Comprehensive anal-
ysis and integrated
mitigation in real-
world IoT scenarios.
Focus on single at-
tack and countermea-
sure.
Attack simulation
tools only, no inte-
gration of mitigation.
Focus on attack im-
pact without practi-
cal defenses.
6 PROPOSED APPROACH: RANK
ATTACKS MITIGATION
To enhance the security of the Routing Protocol for
Low-Power and Lossy Networks (RPL) against rank
attacks, we propose a Trust Energy-based counter-
measure. We introduce a novel metric called ”Trust
Energy” to assess the trustworthiness of nodes within
the RPL network. The Trust Energy metric is cal-
culated based on behavioral, communication, and
security-related parameters. The block diagram in
Figure 10 shows the steps of our proposed approach.
The following description outlines the steps:
1. Trust Energy Estimation:
The Trust Energy (Trust
i
) of a node is calculated
as follows (Zhou and Gong, 2014):
Trust
i
= (1 − α) · Energy
i
+ β · PDR
i
+ (1)
α · Behavior
i
+ (1 − β) · Trustneighbor
avg
Here, Energy
i
represents the energy level associ-
ated with node ’i’.
Trustneighbor
avg
is average trust value recom-
mended by neighboring nodes. This introduces
a collaborative aspect where a node’s trust is in-
fluenced by the collective trustworthiness of its
neighbors.
The behavior of a node (Behavior
i
) is calculated
using the following parameters.
• Successful Packet Delivery (PDRi): Reflects a
node’s reliability in delivering packets. Higher
success rates contribute positively to trust en-
ergy.
• Adherence to Protocols (Behaviori): Nodes
conforming to communication protocols and
standards are deemed more trustworthy, em-
phasizing expected protocol behavior.
• Reliability in Task Execution: Nodes consis-
tently fulfilling responsibilities enhance trust
energy.
• Communication Analysis:
• Communication Responsiveness: Swift re-
sponses to communication requests positively
impact trust energy (Dahal and Shrestha, 2020).
• Consistency in Communication Patterns: Mon-
itoring and analyzing consistent communica-
tion patterns contribute to trust energy.
• Communication Security Measures: Robust se-
curity measures, such as encryption and au-
thentication, positively influence trust energy.
• Security Credential Assessment:
• Authentication and Authorization: Nodes with
valid credentials and a clean security history
boost trust energy.
• History of Security Incidents: A node’s secu-
rity incident history affects trust energy. The
parameters α and β serve as weighting factors,
allowing the adjustment of each factor’s influ-
ence on the overall trust computation. This
comprehensive approach aims to create a nu-
anced evaluation of node trustworthiness, con-
sidering both individual and collective perfor-
mance metrics.
2. Trust-based Route Selection: Nodes prioritize
routes with higher trust energy to avoid compro-
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
220
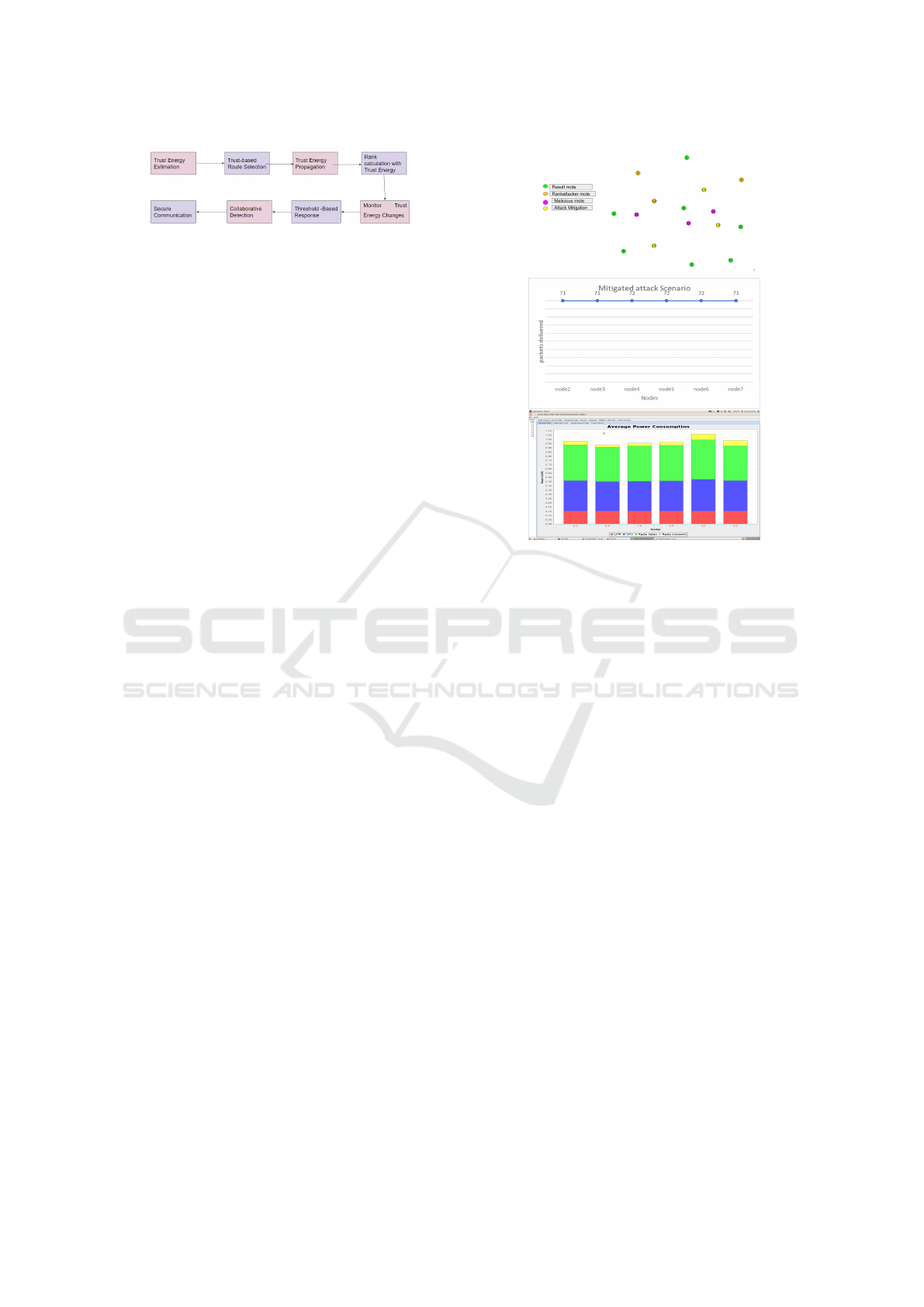
Figure 10: Steps of Proposed Rank Attack Mitigation.
mised nodes, integrating trust metrics with stan-
dard Objective Function metrics.
3. Trust Energy Propagation: Nodes exchange trust
energy values with neighbors (one-hop or two-
hop), using secure protocols to prevent malicious
activity.
4. Rank Calculation with Trust Energy: The Trust
Energy Factor (TEF) is integrated into the RPL
rank calculation (Santos-Boada and Hesselbach,
2019):
R = (DODAGRank × mHRI) + minRankIncrease + α · T EF
5. Monitor Trust Energy Changes: Rapid drops
in trust energy indicate attacks, and nodes
with suspicious changes are isolated or rerouted
(Airehrour et al., 2019).
6. Trust Energy Exchange: Nodes exchange trust
energy values securely with neighbors (Gelogo
et al., 2011).
7. Threshold Based Response: Nodes below a trust
energy threshold trigger isolation and rerouting
actions.
8. Collaborative Detection: Nodes detect and share
rapid trust energy drops to improve attack detec-
tion (Airehrour et al., 2019).
9. Secure Communication: Secure protocols, in-
cluding AES encryption and authentication, pro-
tect trust energy data (Ioulianou et al., 2022)
(Raghavendra et al., 2022).
While Trust Energy-based countermeasures enhance
security in RPL networks, a multi-layered strategy
combining cryptographic methods, intrusion detec-
tion, and anomaly detection is vital for comprehensive
protection (Zhang and Chen, 2018).
6.1 Simulation of Rank Attack
Mitigation
• Figure 11 (I) depicts the simulated node network
designed for detecting rank attacks. The network
comprises four types of nodes: green nodes num-
bered from 1 to 7 serve as result nodes, acting as
UDP sender nodes during bootstrapping. Follow-
ing them are the rank attacker nodes (numbered 7
to 10) and malicious nodes (numbered 11 to 13),
Figure 11: I.Simulation Network II.PDR III.Power Con-
sumption.
which attempt to manipulate rank values. How-
ever, mitigation nodes (numbered 14 to 16) isolate
these attackers and redirect traffic through normal
nodes. .
• The proposed work aims to address attacker ac-
cess and isolate them, leading to improved net-
work packet transmissions (Figure 11 II). A col-
lect view is initiated for node ID 1, and the snap-
shot (Figure 11 III) illustrates the power consump-
tion of nodes, including CPU power, LPM power,
Listen power, and Transmit power. This mitiga-
tion method boasts low power consumption and
minimal computation time, thereby enhancing the
security of the RPL network and ensuring proper
packet transmission.
6.2 Comparative Analysis of Rank
Attacks and Mitigation
This section compares various approaches to address-
ing rank-based attacks in RPL-based IoT networks,
including Our Approach, (Rouissat et al., 2023),
(Algahtani et al., 2021), and (A. Hkiri and Machhout,
2024).Our Approach provides a comprehensive so-
lution for securing IoT networks by analyzing three
rank-based attacks (increase, decrease, and worst-
parent). It features a real-time dynamic trust-based
mitigation strategy that ensures network security dur-
ing attacks. Additionally, it evaluates multiple per-
Implementation of Rank Attack and Its Mitigation in RPL-Based IoT Networks
221

formance metrics, such as energy, PDR, and latency,
to demonstrate how mitigation improves network per-
formance. Furthermore, our Approach integrates both
attack analysis and mitigation into a cohesive frame-
work, offering a holistic solution for securing IoT net-
works. Table 2 provides a comparison of the dis-
cussed approaches.
7 CONCLUSION
This work analyzes the vulnerabilities of the Routing
Protocol for Low-Power and Lossy Networks (RPL),
focusing on rank-based attacks like rank increase,
rank decrease, and worst-parent attacks. We find that
rank-increase attacks raise energy consumption and
overhead, leading to network overload, while rank-
decrease attacks disrupt traffic and the RPL’s Directed
Acyclic Graph (DODAG), affecting packet delivery.
To improve security in low-power networks like
IoT, we propose a trust energy-based mitigation for
RPL, using trust energy for routing, anomaly detec-
tion, and defense. This approach enhances network
resilience against rank-based attacks, providing dy-
namic security that adapts to evolving threats. Fu-
ture work is necessary to refine and address emerging
challenges.
REFERENCES
A. Hkiri, M. Karmani, O. B. B. A. M. M. F. H. A. and
Machhout, M. (2024). Rpl-based iot networks un-
der decreased rank attack: Performance analysis in
static and mobile environments. Faculty of Sciences
of Monastir, Tunisia, and Taif University, Saudi Ara-
bia.
Airehrour, D., Gutierrez, J., and Ray, S. (2019). Sectrust-
rpl: A secure trust-aware rpl routing protocol for inter-
net of things. Future Generation Computer Systems,
93:860–876.
Algahtani, F., Tryfonas, T., and Oikonomou, G. (2021). A
reference implementation for rpl attacks using contiki-
ng and cooja. In Proceedings of the 2021 17th Interna-
tional Conference on Distributed Computing in Sen-
sor Systems (DCOSS), pages 280–286, Pafos, Cyprus.
Baccelli, E. and Philipp, M. (2013). The rpl routing protocol
for low-power and lossy networks. Technical report,
IETF RFC 6550.
Choukri, W., Lamaazi, H., and Bena, N. (2020). Rpl rank
attack detection using deep learning. In 3rd ICT Inter-
national Conference, pages 1–6.
Dahal, S. and Shrestha, P. (2020). A comprehensive survey
of trust management systems in low-power and lossy
networks. IEEE Access, 8:148484–148514.
Djedjig, N., Tandjaoui, D., Medjek, F., and Romdhani, I.
(2020). Trust-aware and cooperative routing protocol
for iot security. Journal of Information Security Ap-
plications, 52:102467.
Gelogo, Y., Caytiles, R., and Park, B. J. (2011). Threats
and security analysis for enhanced secure neighbor
discovery protocol (send) of ipv6 ndp security. In-
ternational Journal of Security, 4:179–184.
Hashemi, S. and Aliee, F. S. (2019). Dynamic and compre-
hensive trust model for iot and its integration into rpl.
Journal of Supercomputing, 75:3555–3584.
Ioulianou, P., Vassilakis, V., and Shahandashti, S. (2022).
A trust-based intrusion detection system for rpl net-
works: Detecting a combination of rank and black-
hole attacks. Journal of Cybersecurity and Privacy,
2:124–152.
Iuchi, K., Matsunaga, T., Toyoda, K., and Sasase, I. (2015).
Secure parent node selection scheme in route con-
struction to exclude attacking nodes from rpl network.
In Proc. 21st Asia–Pac. Conf. Commun. (APCC),
pages 299–303.
Liu (2021). A detection framework against cpma attack
based on trust evaluation and machine learning in iot
network. IEEE Internet of Things Journal, 8:15249–
15258.
Mayzaud, A., R
´
emi, B., and I., C. (2016). A taxonomy of
attacks in rpl-based internet of things. 18.
Raghavendra, T., Anand, M., Munuswamy, S., Kalidoss, T.,
Svn, S. K., and Arputharaj, K. (2022). An intelligent
rpl attack detection using machine learning-based in-
trusion detection system for internet of things. Proce-
dia Computer Science, 215:61–70.
Raoof, A., Ashraf, M., and Horng, L. C. (2018). Routing
attacks and mitigation methods for rpl-based internet
of things. IEEE Communications Surveys Tutorials,
pages 1–11.
Rouissat, M., Belkheir, M., Belkhira, S. A. H., Mokaddem,
A., and Ziani, D. (2023). Implementing and evalu-
ating a new silent rank attack in rpl-contiki based iot
networks. Journal of Electrical Engineering, 74:454–
462.
Said, A., Aymen, Y., Faicel, Y., and Takoua, A. (2020). Ma-
chine learning-based rank attack detection for smart
hospital infrastructure. In Proceedings of the Interna-
tional Conference.
Santos-Boada, G. and Hesselbach, X. (2019). Trust man-
agement for rpl-based networks: A comprehensive
survey. Sensors, 19(24):5385.
Simoglou, G., Violettas, G., Petridou, S., and Mamatas,
L. (2021). Intrusion detection systems for rpl secu-
rity: A comparative analysis. Computers Security,
104:102219.
Zhang, Z. and Chen, H. (2018). A survey of trust manage-
ment in the internet of things. IEEE Access, 6:76007–
76020.
Zhou, L. and Gong, H. (2014). Trust-based secure rout-
ing for rpl in low-power and lossy networks. IEEE
Transactions on Parallel and Distributed Systems,
25(9):2297–2306.
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
222
