
OTRA: A Risk Management Ontology for Transparent Service Level
Agreements in Federated Cloud Environment
Giulia Biagioni
1 a
, Resul Serkan Keskin
1 b
, Lawrence Cook
2 c
, Edwin Harmsma
1 d
and
Erik Langius
1 e
1
Netherlands Organisation for Applied Scientific Research (TNO), The Hague, The Netherlands
2
BIT, Ede, The Netherlands
{giulia.biagioni, serkan.keskin, edwin.harmsma, erik.langius}@tno.nl, lawrence@bit.nl
Keywords:
Cloud Federation, Service Level Agreement, Risk Management Ontology, Bow-Tie RDF-Based
Implementation.
Abstract:
Cloud Federation, a model where multiple cloud providers collaborate to offer interconnected services, has
become increasingly renowned in cloud computing. In this environment, Service Level Agreements (SLAs)
play a critical role by formalising service expectations and fostering transparency between providers and con-
sumers. Although existing SLA ontologies provide a semantic foundation for standardised SLA management,
they lack components for detailed risk management and representation within SLA. This paper presents our
work on developing OTRA - Ontology for Transparent Agreement - specifically designed for risk manage-
ment within SLAs in federated cloud environments. By integrating structured risk identification, prevention
and mitigation strategies, our ontology extends the Gaia-X Core Ontology. We validate our ontology through a
controlled simulation that demonstrates its effectiveness in structuring SLA risk information, offering a foun-
dation for transparent, accountable service agreements.
1 INTRODUCTION
In the evolving landscape of cloud computing, cloud
federation - a model where multiple cloud service
providers (CSPs) collaborate to deliver an intercon-
nected network of services (Kurze et al., 2011) -
is gaining increasing popularity. This environment
offers significant benefits such as data sovereignty,
which allows organisations to store and manage
their data within specific jurisdictions, ensuring com-
pliance with regional regulations (Holfelder et al.,
2022)(De Filippi and McCarthy, 2012). Addition-
ally, cloud federation helps avoid vendor lock-in, giv-
ing organisations the flexibility to choose services
from different providers without being tied to a sin-
gle vendor’s ecosystem (Bermbach et al., 2013). This
flexibility ensures better resource optimisation, cost
management, and control over critical infrastructure
choices (Bonfiglio, 2021).
a
https://orcid.org/0000-0002-9005-7945
b
https://orcid.org/0000-0002-4844-7982
c
https://orcid.org/0009-0008-0536-0511
d
https://orcid.org/0009-0009-8892-4593
e
https://orcid.org/0009-0006-2765-6781
Within this model, Service Level Agreements
(SLAs) play a crucial role. SLAs are formal con-
tracts that define the expected level of service between
providers and consumers. They ensure transparency
and accountability, helping to maximise value for all
parties by clearly defining expectations and mitigat-
ing legal risks (L
ˆ
e and Nguyen, 2020).
Several ontologies have been developed to repre-
sent SLAs in the context of cloud federation, such as
CSLAOnto (Labidi et al., 2016) and the generic SLA
ontological model of SLAVIDES (Karamanlioglu and
Alpaslan, 2018). These ontologies address the need
for standardised, automated, and flexible SLA man-
agement. They offer a semantic-based format that
enables automatic monitoring, understanding and en-
forcement of SLAs, ensuring that service agreements
are clearly defined and adhered to. When integrated
into expert systems, they enable the detection of SLA
violations across multiple sectors, potentially lead-
ing towards improving compliance and performance
management in federated cloud ecosystems.
Despite the considerable efforts made in the land-
scape of SLA ontology development, semantic mod-
els specifically designed to delineate risks in SLAs for
cloud federation have not been developed to the same
Biagioni, G., Keskin, R. S., Cook, L., Harmsma, E. and Langius, E.
OTRA: A Risk Management Ontology for Transparent Service Level Agreements in Federated Cloud Environment.
DOI: 10.5220/0013209300003950
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 15th International Conference on Cloud Computing and Services Science (CLOSER 2025), pages 119-126
ISBN: 978-989-758-747-4; ISSN: 2184-5042
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
119

extent. Semantic-based formats that could be fed into
expert systems to trigger strategies aimed at prevent-
ing the occurrence of hazardous events, or mitigating
their impact are still under development. This gap
represents an opportunity for further advancements
in the integration of risk management and prevention
mechanisms into the SLA frameworks used in cloud
federation.
In this article, we introduce our work on develop-
ing OTRA, a specialised ontology for risk manage-
ment within SLAs in federated cloud environments.
This ontology is designed to fill existing gaps in SLA
frameworks by explicitly modelling and representing
risks, which are essential in cloud federation scenar-
ios where multiple Cloud Service Providers (CSPs)
interact and collaborate across varying regulatory en-
vironments. The ontology aims to provide a struc-
tured and semantic foundation for risk identifica-
tion, prevention, and mitigation within SLAs, thereby
enhancing transparency and accountability for both
providers and consumers.
This article is structured as follows: following the
introduction, Section 2 provides an overview of the
state of the art in ontology development for risk man-
agement and SLAs, summarising existing approaches
and identifying gaps that motivate our work. Section
3 details the ontology design of OTRA, presenting its
conceptual underpinnings through First-Order Logic
(FOL) axioms. This approach ensures that our con-
ceptualisation remains technologically agnostic, al-
lowing for flexible implementation across different
languages and evolving standardised semantics.
In Section 4, we describe the evaluation process of
the ontology, including a simulation designed to val-
idate its effectiveness in a controlled operational en-
vironment, achieving a Technology Readiness Level
(TRL) of 5. Section 5 discusses the results of this
evaluation, interpreting the ontology’s performance
and insights gained from the simulation. Finally, Sec-
tion 6 outlines future work, exploring potential exten-
sions to enhance the ontology’s applicability and ex-
pressiveness in dynamic cloud federation contexts.
2 STATE OF THE ART
Ontologies, in the context of RDF, are formal repre-
sentations of knowledge that define concepts, entities,
and the relationship between them within a specific
domain. Regarding their technical application, they
can be used for enabling interoperability and connect-
ing data silos (Roussey et al., 2011)(Allemang et al.,
2020)(Blumauer et al., 2020), feeding expert systems
with structured knowledge (Prapakorn and Chittaya-
sothorn, 2009), where example of such applications
can be found in domains like health (Mustafa et al.,
2023) and energy (Pruvost et al., 2023), allowing
machines to understand the meaning of information
(Hogan, 2020), and enhancing AI trustworthiness by
providing explainable reasoning when integrated with
machine learning-driven methods (Pan et al., 2023).
In risk management, the Open Risk community
1
has contributed significantly to developing ontolog-
ical models, promoting open-source risk analysis
tools for transparency within financial sectors. Their
frameworks, such as the Description of a Model On-
tology (DOAM)
2
and the Risk Function Ontology
(RFO)
3
, offer structured means to annotate and cat-
egorise key concepts in risk modelling and manage-
ment roles.
DOAM, for example, facilitates the semantic or-
ganisation of risk model components, while RFO
structures essential skills, occupations, and functions
to support interoperability. Though valuable for anal-
ysis, both ontologies prioritise metadata-level anno-
tation, which limits their direct application in expert
systems or within service-level agreements (SLAs)
between providers and consumers in cloud federa-
tions.
Incorporating detailed risk-related information
within SLAs between providers and consumers is crit-
ical for: reducing ambiguity, ensuring awareness of
conditions, clarifying mitigation strategies, and mak-
ing implicit assumptions explicit (Uriarte et al., 2016)
(Alkhamees, 2022). If DOAM and RFO lack the ca-
pability to directly map risk frameworks onto data due
to their analytical focus and financial sector orien-
tation, SLA-specific ontologies like SLAVIDES and
CSLAOnto similarly miss essential components for
representing risk and management strategies within
service agreements.
CSLAOnto is specifically designed for cloud com-
puting SLAs, focusing on standardising terms related
to service quality, performance, and responsibilities
(Labidi et al., 2016), thus enhancing semantic in-
teroperability but not directly addressing risk man-
agement. SLAVIDES (Karamanlioglu and Alpaslan,
2018), while formalising SLA terms, similarly lacks
built-in risk representation and management compo-
nents. Consequently, these ontologies offer valuable
structure but are not yet at a readiness level for com-
prehensive, risk-sensitive applications in operational
1
Regarding the Open Risk Community, cf: https://
www.openriskmanagement.com
2
https://www.openriskmanual.org/ns/doam/index-
en.html
3
https://www.openriskmanual.org/ns/rfo/index-
en.html
CLOSER 2025 - 15th International Conference on Cloud Computing and Services Science
120

environments.
Regarding ontological efforts aimed at fostering
interoperability in cloud federations at an operational
and industry-driven level, the Gaia-X initiative offers
a notable example. Gaia-X is an initiative dedicated
to developing digital governance that can be applied
to foster transparency, controllability, portability, and
interoperability in the federated cloud ecosystem and
data spaces
4
. Among its various activities, Gaia-X
supports the collaborative development of ontologi-
cal modules that enable seamless data and service in-
tegration across cloud providers. One of its founda-
tional ontological modules is the Gaia-X Core On-
tology, which structures key concepts such as Par-
ticipants (e.g., Provider, Consumer), Resources (e.g.,
Data, Software Asset), and Service Offerings to en-
hance compatibility across cloud systems. While
the Gaia-X ontologies effectively establish founda-
tional roles and service interactions, they currently
lack the necessary components to define a compre-
hensive risk management framework within SLAs be-
tween providers and consumers.
To address these identified gaps, we have devel-
oped a new risk management ontology specifically
designed for SLAs, aiming to comprehensively rep-
resent risk and management strategies within service
agreements. This ontology extends the Gaia-X Core
Ontology module by facilitating structured, action-
able risk information, allowing its seamless integra-
tion within SLAs. The following section presents our
framework in detail, highlighting its potential to en-
hance transparency and risk management within fed-
erated cloud environments.
3 ONTOLOGY DESIGN FOR
RISK MANAGEMENT
Our risk management ontology, OTRA, is grounded
in the bow-tie method
5
. The bow-tie method is a
structured risk assessment model used in industries
to visualise risks by organising both preventive mea-
sures and mitigation strategies around a central haz-
ardous event (Omidvar et al., 2024) (Kluwer, 2017)
(Kluwer, 2019). Resembling a bow tie, the model
consists of two branches extending from the ”knot”
or core event: the left side represents potential threats
and preventive actions, while the right side outlines
4
https://gaia-x.eu/what-is-gaia-x/about-gaia-x/
5
The bow-tie method reflects conceptual structure out-
lines in the ISO 31000:2018. This standard identifies eight
core concepts critical for effective risk management: Risk,
Risk Management, Stakeholder, Risk Source, Event, Con-
sequence, Likelihood and Control.
potential consequences and mitigation measures. The
bow-tie model is displayed in Figure 1.
Hazard
Control
(Preventive)
Control
(Remedy)
Threats
Impact
Figure 1: The bow-tie diagram for risk assessment.
Industries such as oil and gas (Kbah et al., 2020),
healthcare (McLeod and Bowie, 2020), and aviation
(Aust and Pons, 2020) use the bow-tie method to de-
velop clear action plans for preventing and addressing
the outcomes of hazardous events.
Our ontology structures each Hazardous Event to
include essential elements like Preconditions, Pre-
ventive Mechanisms, Postconditions, and Remedies,
closely mirroring the bow-tie method’s approach to
capture potential triggers and responses. This align-
ment allows our ontology to systematically map risks
and mitigation strategies that apply to SLAs in feder-
ated cloud environments. Key elements include:
• Hazardous Event: Identifies risks that may im-
pact SLA parties, linked to Preconditions (factors
that may trigger the event) and Postconditions (the
resulting outcomes or states after the event).
• Prevention Mechanism: Outlines preventative
actions aimed at reducing identified risks.
• Remedy: Details corrective measures to address
adverse events if they occur.
• Agreement: Serves as the core SLA ele-
ment, connecting Gaia-X Consumer and Gaia-X
Provider roles and embedding risk considerations
within the SLA framework.
In our formal delineation of the ontology, which
subsequently guided its technical implementation,
each Hazardous Event x, representing a risk within
SLA agreements, is linked to a Precondition y that
may act as a trigger. This relationship is expressed in
First-Order Logic (FOL) as:
∀x (HazardousEvent(x) →
∃y(Precondition(y) ∧ hasPrecondition(x, y)))
To reduce the likelihood of hazardous events oc-
curring, each Hazardous Event is linked to a Preven-
tion Mechanism w, which is specifically designed to
counteract its occurrence:
OTRA: A Risk Management Ontology for Transparent Service Level Agreements in Federated Cloud Environment
121
∀x (HazardousEvent(x) →
∃w(PreventionMechanism(w)
∧hasPreventionMechanism(x, w)))
Each Precondition y associated with a Hazardous
Event is also assigned a Prevention Mechanism w to
address conditions that could lead to potential risks.
We represent this relationship in First-Order Logic as
follows:
∀y(Precondition(y) →
∃w(PreventionMechanism(w)
∧hasPreventionMechanism(y, w)))
The hasPreventionMechanism relationship in-
cludes an OR operator in its domain, applying to ei-
ther a Precondition or a HazardousEvent, with a range
on PreventionMechanism.
When a HazardousEvent x occurs, it produces an
outcome represented by the Postcondition z, indicat-
ing the resulting state:
∀x (HazardousEvent(x) →
∃z(Postcondition(z) ∧ hasPostcondition(x, z)))
Lastly, each HazardousEvent is connected to a
Remedy v, which serves as a corrective action to
prevent the resulting Postcondition from manifesting.
This relationship can be formalised as:
∀x (HazardousEvent(x) →
∃v(Remedy(v) ∧ hasRemedy(x, v)))
Each Postcondition z associated with a Hazardou-
sEvent is similarly assigned a Remedy v, ensuring
proactive response measures. This relationship is rep-
resented in First-Order Logic as:
∀z(Postcondition(z) →
∃v(Remedy(v) ∧ hasRemedy(z, v)))
Ultimately, similar to the nature of the
hasPreventionMechanism relationship, the
hasRemedy relationship includes an OR opera-
tor in its domain, indicating it applies to either a
Postcondition or a HazardousEvent, with a defined
range on Remedy.
The Hazardous Events, representing risks in
SLAs, are inherently linked to Agreements. The
Agreement concept formalises the binding between
specific risks and the involved parties. An agreement
a connects to a hazardous event x via the hasRisk re-
lationship, embedding risk considerations within the
contractual terms:
∀a(Agreement(a) →
∃x (HazardousEvent(x)∧ hasRisk(a, x)))
Each agreement a also incorporates both a
consumer c and provider p, represented by the
involvesParty relationship. This connects the en-
tities directly accountable for the risk terms outlined
within the SLA. Formally, we represent this as:
∀a(Agreement(a) →
∃c, p(Consumer(c) ∧ Provider(p)
∧involvesParty(a, c) ∧ involvesParty(a, p)))
The ontology, as formally described above, has
been technically implemented using OWL and RDFs
standardised semantics, capturing the relationships
between key elements such as hazardous events, pre-
conditions, prevention mechanisms, postconditions,
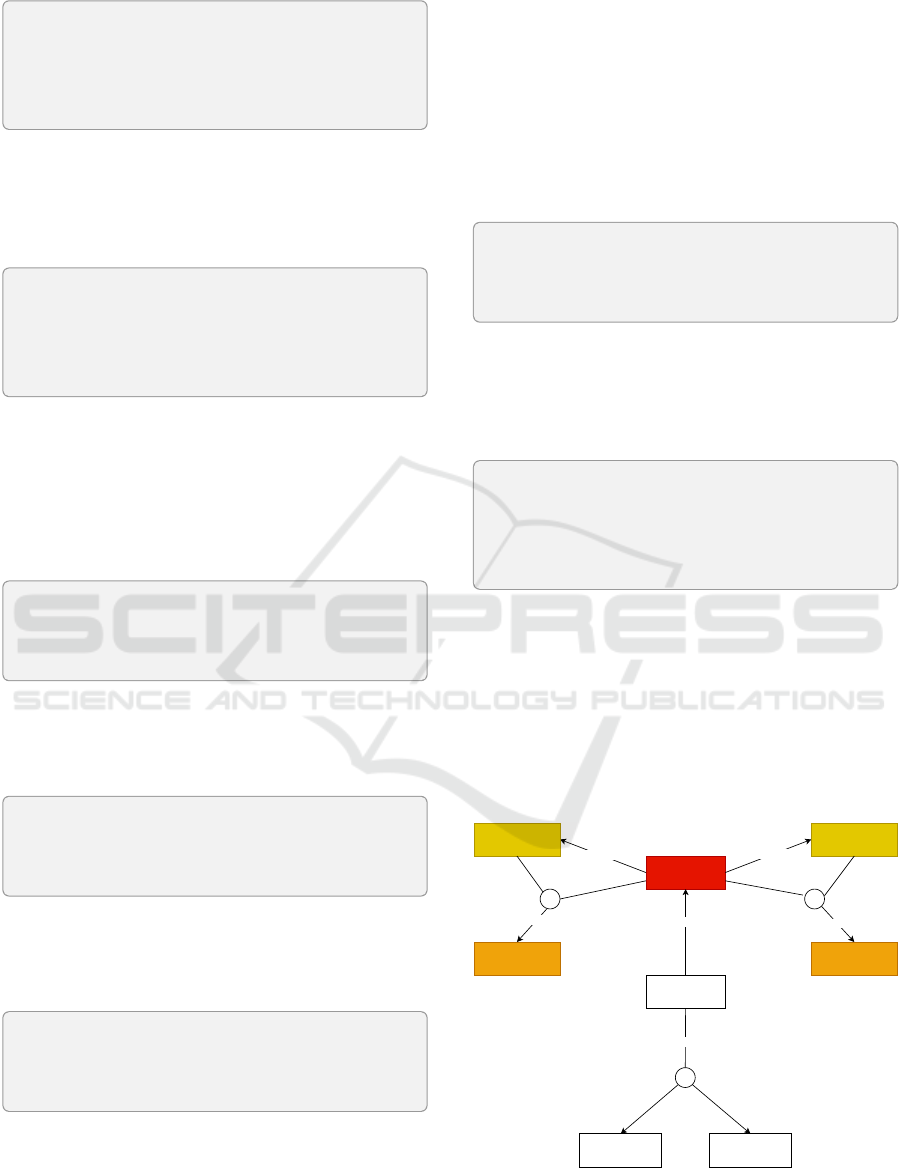
and remedies. This structured semantic model can
be visualised as shown in Figure 2, where rectangles
represent classes, and arrows illustrate object property
relationships.
Hazardous Event
hasPrecondition
Precondition
Prevention
Mechanism
hasPreventionMechanism
hasPostcondition
Postcondition
Remedy
hasRemedy
⨆ ⨆
hasRisk
Agreement
Gaia-X:Consumer Gaia-X:Provider
⨆
involvesParties
Figure 2: Visual representation of the ontology.
CLOSER 2025 - 15th International Conference on Cloud Computing and Services Science
122

The OWL and RDF-based ontology is accessi-
ble for reference and collaborative contributions at
the following repository: https://github.com/OTRA-
anon/OTRA.
4 EVALUATION PROCESS
OTRA ontology was validated to ensure both struc-
tural consistency and relevance in representing do-
main knowledge effectively. For consistency, we ap-
plied the Hermit 1.4.3.456 reasoner to check the on-
tology’s logic and coherence with and without in-
stance data, confirming its integrity.
To further test the ontology’s effectiveness in or-
ganising SLA risk information, we developed a sim-
ulation of a digital marketplace environment during
the ”Tech-X Conference and Hackathon 2024” event.
This conceptual marketplace was designed to enable
cloud service providers (CSPs) to offer services such
as IaaS, PaaS, and SaaS, with simulated consumers
capable of selecting and combining services across
multiple providers.
For seamless service interoperability within the
simulated cloud federation, we proposed Liqo
6
, an
open-source Kubernetes extension, as a mechanism
to facilitate peering between providers (Iorio et al.,
2022). Although the simulation did not involve actual
users or infrastructure, our conceptual pipeline lever-
aged Liqo’s capability to create ”virtual nodes” that
represent the capacity of a remote cluster within the
local cluster’s environment. This approach enabled
simulated clusters to expand their resource pool dy-
namically, supporting resource sharing and flexible
workload distribution across Kubernetes clusters in a
federated cloud context.
In this model, the consumer cluster, depicted on
the left part of Figure 3, initiates an outgoing peer-
ing relationship with a provider cluster on the right,
thereby gaining access to additional resources from
the provider.
Within this simulated federation, SLAs played a
foundational role in formalising service agreements.
We embedded our risk management ontology in the
SLAs to clearly outline potential risks, preventive
measures, and remedies, thereby creating a struc-
tured, transparent framework for risk management.
This approach aimed to foster informed decision-
making and trust within federated cloud environ-
ments.
The SLA template from BIT
7
was used as a case
6
https://docs.liqo.io/en/stable/index.html
7
https://www.bit.nl/en/home-en
Figure 3: Illustration of Liqo-enabled resource sharing in
a federated cloud environment. In the figure, the directed
arrow signifies the peering connection, which allows the
consumer to offload workloads to the provider, mirroring
the provider’s capacity within its own infrastructure through
a ”virtual node.” This virtual node in the consumer clus-
ter represents the resources of the provider cluster, enabling
workloads or pods to run on the remote infrastructure while
remaining under the consumer’s management framework.
study in our simulation to demonstrate how the ontol-
ogy could support digital, legally binding agreements.
This allowed all parties (providers and consumers) to
view potential risks and planned response strategies.
In the simulated SLA, an agreement labelled
Agreement34 was formed between the consumer, Al-
ice, and the provider, Company X. This agreement
contained a termination clause specifying conditions
under which Company X could end the contract. Ac-
cording to this clause, Company X reserved the right
to terminate the SLA if Alice engaged in harmful or
non-compliant behaviours, such as unauthorised ac-
cess, denial-of-service attacks, or policy violations.
This termination scenario, modelled as the Hazardous
Event risk5678, represented actions that could lead
to contract termination.
The Hazardous Event risk5678 was directly
linked to both Precondition precondition1245
and Postcondition Termination89. Here,
precondition1245 specified behaviours (e.g.,
data interception, spam, unauthorised access) that
might trigger termination risks. If Alice engaged
in these non-compliant actions, Termination89
would be activated, resulting in contract termination.
This structured linkage created a pathway from
risky behaviour (risk5678) to its consequence
(Termination89) within the SLA.
Our ontology encouraged the CSP to incorporate
preventive and corrective mechanisms, even though
these elements were absent from the original SLA
template.
To reduce the likelihood of termination, a preven-
tion mechanism labelled communication89 (“Com-
munication”) was recommended. This mecha-
nism, associated with both the hazardous event
and the precondition, encouraged proactive man-
OTRA: A Risk Management Ontology for Transparent Service Level Agreements in Federated Cloud Environment
123

agement of minor issues before escalation. In the
event of a violation, the “Compliance as Rem-
edy” (complianceAgreement123) corrective action
would allow both parties to restore SLA adherence
before triggering termination.
5 DISCUSSION
The ontology developed in this study was designed
to enhance risk representation and management in
SLAs within federated cloud environments. Through
our simulation of a digital marketplace, we validated
the ontology’s effectiveness in structuring and con-
veying complex SLA-related risk information to both
providers and consumers. By embedding our risk on-
tology within SLAs, we enabled participants to view
potential risks, preventive measures, and remediation
strategies explicitly, fostering transparency and in-
formed decision-making in cloud service interactions.
The structural integrity of the ontology was ver-
ified using the Hermit 1.4.3.456 reasoner, ensuring
logical consistency both with and without instance
data. This technical validation confirmed that the
ontology operates coherently within the OWL and
RDF frameworks, supporting consistent interpreta-
tion across diverse cloud environments.
A key outcome of the simulation was the ontol-
ogy’s ability to guide CSPs in incorporating preven-
tive and corrective mechanisms, even if these were
absent in the original SLA templates. By system-
atically modelling risk triggers and potential out-
comes, the ontology encouraged CSPs to adopt proac-
tive communication and compliance-based remedies.
This structured risk pathway not only defines actions
and consequences within SLAs but also enhances re-
silience by establishing actionable approaches for risk
mitigation.
We deem that the ontology has the potential to
foster trust within the federated cloud environments
by establishing a shared, transparent structure for risk
representation. Through standardised elements like
hazardous events, preconditions, preventive mecha-
nisms, postconditions, and remedies, the ontology
provides a clear structure that can reduce ambigu-
ity and improve mutual understanding. This trans-
parency is intended to give both consumers and
providers confidence in the reliability of the frame-
work, as each party gains visibility into how risks are
identified, managed, and mitigated within the SLA it-
self prior to signing the contract.
Encouraging CSPs to adopt a structured, replica-
ble approach to risk management, the ontology has
the potential to create a consistent standard within
SLAs, making contractual terms and risk mitiga-
tion strategies more predictable and accessible across
cloud federations. This standardised approach could,
over time, support trust-building in federated cloud
environments by promoting transparency, account-
ability, and a shared commitment to proactive risk
management.
Furthermore, to address international variations in
legal requirements, the ontology’s explicit delineation
of risk offers an adaptable structure well-suited for
federated environments where CSPs and consumers
operate under different jurisdictions. Since SLAs and
legal frameworks vary widely between countries, the
clear representation of risks, preventive measures, and
remedies within the ontology can harmonise under-
standing across regions. By standardising risk ele-
ments within the SLA framework, the ontology fa-
cilitates consistent communication of terms, helping
to bridge differing legal expectations and regulatory
requirements.
This explicit risk delineation is particularly ad-
vantageous in federated cloud contexts where cross-
border collaborations are common. A transparent,
well-defined ontology allows each party to understand
applicable risks and mitigation strategies, regardless
of jurisdictional differences. The ontology’s flexibil-
ity and comprehensiveness provide a foundation for
CSPs to maintain compliance with local regulations
while fostering mutual understanding.
Ultimately, creating a comprehensive framework
for risk management in cloud federations is inher-
ently a collaborative endeavour. While this ontology
establishes a foundational structure for representing
and managing risks within SLAs, we recognise that
the dynamic nature of cloud environments demands
ongoing adaptation and enrichment. We encourage,
therefore, readers of this article to contribute to ex-
panding the ontology’s expressiveness, ensuring that
it continues to meet the evolving needs of federated
cloud ecosystems. Collaboration toward this shared
objective will be essential in building a robust, re-
liable setting for cloud federation, one where trans-
parency, accountability, and mutual trust are embed-
ded at the core of cloud service interactions.
6 FUTURE WORK
With the development of our ontology, we have es-
tablished a framework that allows for the explicit rep-
resentation of risks associated with SLAs in feder-
ated cloud environments, providing a structured view
of risks, preventive measures, and remediation strate-
gies before digitally signing agreements. This foun-
CLOSER 2025 - 15th International Conference on Cloud Computing and Services Science
124

dation facilitates transparency in risk communication
and fosters informed decision-making among cloud
service providers (CSPs) and consumers.
Moving forward, one key area of focus will be in-
tegrating this ontology into an expert system capable
of actively tracking the occurrence of preconditions
linked to potential hazards. This system could mon-
itor real-time data to detect risk factors or precondi-
tions as they emerge, triggering preventive mecha-
nisms proactively to avoid the manifestation of haz-
ardous events. By embedding such predictive func-
tionality, we aim to shift risk management from a
reactive to a more proactive stance, significantly en-
hancing the resilience of federated cloud services.
In addition, we plan to develop a complementary
system for post-event management. Should a haz-
ardous event occur despite preventive measures, this
system would activate remediation strategies, mitigat-
ing the impact on associated postconditions. This
dual-component approach would provide a compre-
hensive risk management framework, covering both
preventive actions and responsive remedies within
SLAs.
Beyond these technical advancements, we envi-
sion continuous collaboration with industry stake-
holders and researchers to enrich the ontology’s ex-
pressiveness, ensuring it remains a robust, adaptable
resource that reflects emerging needs and complexi-
ties within the cloud federation domain.
ACKNOWLEDGEMENTS
This research activity was conducted from the Dutch
ECOFED project which is part of the integrated IP-
CEI CIS project. The early foundation of this research
was established during the Gaia-X Tech-X hackathon
in 2024, in which our participation was facilitated by
the Dutch Gaia-X hub part of the CoE DSC.
REFERENCES
Alkhamees, S. (2022). Sla negotiation and renegotiation
in cloud sla management: Issue and challenges. In
Hussain, W. and Jan, M. A., editors, IoT as a Ser-
vice, pages 159–170, Cham. Springer International
Publishing.
Allemang, D., Hendler, J., and Gandon, F. (2020). Semantic
Web for the Working Ontologist: Effective Modeling
for Linked Data, RDFS, and OWL, volume 33. As-
sociation for Computing Machinery, New York, NY,
USA, 3 edition.
Aust, J. and Pons, D. J. (2020). A systematic methodology
for developing bowtie in risk assessment: Application
to borescope inspection. Aerospace.
Bermbach, D., Kurze, T., and Tai, S. (2013). Cloud federa-
tion: Effects of federated compute resources on qual-
ity of service and cost. In 2013 IEEE International
Conference on Cloud Engineering (IC2E), pages 31–
37.
Blumauer, A., Nagy, H., and edition mono/monochrom
(2020). The Knowledge Graph Cookbook: Recipes
that Work. edition mono/monochrom.
Bonfiglio, F. (2021). Gaia-x, vision & strategy. https://gaia-
x.eu/sites/default/files/2021-12/Vision & Strategy.pdf.
CEO Gaia-X, December 16, 2021.
De Filippi, P. and McCarthy, S. (2012). Cloud computing:
Centralization and data sovereignty. European Jour-
nal of Law and Technology, 3(2).
Hogan, A. (2020). Web of data. The Web of Data.
Holfelder, W., Mayer, A., and Baumgart, T. (2022).
Sovereign cloud technologies for scalable data spaces.
In Designing Data Spaces, pages 419–436. Springer.
Iorio, M., Risso, F., Palesandro, A., Camiciotti, L., and
Manzalini, A. (2022). Computing without borders:
The way towards liquid computing. IEEE Transac-
tions on Cloud Computing.
Karamanlioglu, A. and Alpaslan, F. N. (2018). An
ontology-based expert system to detect service level
agreement violations. In Shishkov, B., editor, Busi-
ness Modeling and Software Design, pages 362–371,
Cham. Springer International Publishing.
Kbah, Z., Erdil, N. O., and Aqlan, F. (2020). Risk assess-
ment in oil and gas industry using simulation and bow-
tie analysis. International Journal of Industrial Engi-
neering: Theory, Applications and Practice, 27(1).
Kluwer, W. (2017). The history of bowtie.
https://www.wolterskluwer.com/en/solutions/
enablon/bowtie/expert-insights/barrier-based-risk-
management-knowledge-base/the-historie-of-bowtie.
Kluwer, W. (2019). The bowtie method. https:
//www.wolterskluwer.com/en/solutions/enablon/
bowtie/expert-insights/barrier-based-risk-
management-knowledge-base/the-bowtie-method.
Kurze, T., Klems, M., Bermbach, D., Lenk, A., Tai, S., and
Kunze, M. (2011). Cloud federation. The Second In-
ternational Conference on Cloud Computing, GRIDs,
and Virtualization, pages 32–38.
Labidi, T., Mtibaa, A., and Brabra, H. (2016). Cslaonto:
A comprehensive ontological sla model in cloud com-
puting. Journal on Data Semantics, 5.
L
ˆ
e, L.-S. and Nguyen, T.-V. (2020). Digitizing service level
agreements in service-oriented enterprise architecture.
SN Computer Science, 1(5):257.
McLeod, R. W. and Bowie, P. (2020). Guidance on cus-
tomising bowtie analysis for use in healthcare. In
Charles, R. and Golightly, D., editors, Contempo-
rary Ergonomics and Human Factors 2020, CIEHF.
CIEHF, CIEHF. Based on the CIEHF white paper
‘Human factors in barrier management’.
Mustafa, E. M., Saad, M. M., and Rizkallah, L. W. (2023).
Building an enhanced case-based reasoning and rule-
OTRA: A Risk Management Ontology for Transparent Service Level Agreements in Federated Cloud Environment
125

based systems for medical diagnosis. Journal of En-
gineering and Applied Science, 70(1):139.
Omidvar, M., Zarei, E., and Ramavandi, B. (2024). The
Bow-Tie Method: A Hybrid System Safety and Risk
Analysis Approach for Safety–Critical Sociotechnical
Systems, pages 123–149. Springer Nature Switzer-
land, Cham.
Pan, J. Z., Razniewski, S., Kalo, J.-C., Singhania, S., Chen,
J., Dietze, S., Jabeen, H., Omeliyanenko, J., Zhang,
W., Lissandrini, M., Biswas, R., de Melo, G., Boni-
fati, A., Vakaj, E., Dragoni, M., and Graux, D. (2023).
Large Language Models and Knowledge Graphs: Op-
portunities and Challenges. Transactions on Graph
Data and Knowledge, 1(1):2:1–2:38.
Prapakorn, N. and Chittayasothorn, S. (2009). An rdf-based
distributed expert system. WSEAS Transactions on
Computers, 8(5):788–798.
Pruvost, H., Wilde, A., and Enge-Rosenblatt, O. (2023).
Ontology-based expert system for automated monitor-
ing of building energy systems. Journal of Computing
in Civil Engineering, 37.
Roussey, C., Pinet, F., Kang, M. A., and Corcho, O.
(2011). Ontologies for Interoperability, pages 39–53.
Springer.
Uriarte, R. B., Tiezzi, F., and Nicola, R. D. (2016). Dynamic
slas for clouds. In Villari, M., Zimmermann, W., and
Jonas, K., editors, Service-Oriented and Cloud Com-
puting: 5th European Conference, ESOCC 2016, Pro-
ceedings, volume 9846 of Lecture Notes in Computer
Science, pages 34–49. Springer, Cham. First Online:
25 August 2016.
CLOSER 2025 - 15th International Conference on Cloud Computing and Services Science
126
