
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR
Wojciech Penczek
1 a
, Laure Petrucci
2 b
and Teofil Sidoruk
1 c
1
Institute of Computer Science, Polish Academy of Sciences, Poland
2
LIPN, CNRS UMR 7030, Université Sorbonne Paris Nord, France
Keywords:
Temporal Logics, Timed Automata, Multi-Agent Systems, Strategic Ability, Parametric Verification,
Satisfiability Checking, Model Synthesis.
Abstract:
The satisfiability problem for Timed CTL (TCTL) is well known to be undecidable in general. Therefore, we
propose a bounded approach, involving parametric encoding of all possible timed automata up to a given size
(with certain restrictions). For this parametric timed automaton and an input formula, we synthesise parameter
values using the IMITATOR model checker, and thus obtain a concrete model in which the formula is satisfied
(if one exists within the bound). In other words, we define a partial algorithm for TCTL satisfiability check-
ing. Moreover, we show how to represent memoryless strategies of agents with imperfect information via an
auxiliary set of IMITATOR parameters, thereby applying our method also to Strategic TCTL (STCTL), the
recently proposed extension of TCTL with the strategic modality. We evaluate practical feasibility on three
benchmarks, including scalable instances.
1 INTRODUCTION
Strategic Timed Computation Tree Logic (STCTL),
recently introduced in (Arias et al., 2023), has been
defined with both the discrete and continuous time
representations, an important advantage over Timed
Alternating-time Temporal Logic (TATL), which
only uses the former (Laroussinie et al., 2006). Fur-
thermore, STCTL offers the extra expressiveness of
the strategic modality over Timed CTL (TCTL),
while retaining the same computational complexity of
model checking for memoryless strategies of agents
with imperfect information (ir-strategies). The latter
semantics of strategic ability is usually better suited
for modeling real-world scenarios, since it seldom
makes sense for agents to have full knowledge about
the global state of a system (perfect information).
STCTL is therefore of practical interest for verify-
ing strategic abilities, for example, to analyze and
formally prove desired properties of electronic vot-
ing protocols (Jamroga et al., 2022) or in security
scenarios. The multi-agent representation of security
scenarios introduces a new perspective compared to
formalisms like attack-defense trees (Petrucci et al.,
2019; Arias et al., 2020), enabling the study of op-
a
https://orcid.org/0000-0001-6477-4863
b
https://orcid.org/0000-0003-3154-5268
c
https://orcid.org/0000-0002-4393-3447
posing coalitions of intruders and defenders within a
strategic context. Furthermore, STCTL is particu-
larly well-suited for specifying and verifying timed
systems where a discrete representation is insuffi-
cient, such as in automated control. A model check-
ing algorithm for this logic was demonstrated for the
first time in (Arias et al., 2023).
In this work, we aim to tackle the other notable
decision problem regarding STCTL, namely satisfia-
bility. The main obstacle here is the well-known result
stating that the satisfiability problem is undecidable in
general for TCTL (Alur et al., 1993a), and thus also
for STCTL. Nonetheless, one may still consider sat-
isfiability checking for a class of models whose size
is limited by some constant, analogous to bounded
model checking (BMC). Even then, solving the prob-
lem requires overcoming the challenges presented by
continuous time semantics, which induces infinitely
many possible timed automata of any given size.
Thus, the main focus of our approach is on pre-
senting a finite, parametric encoding that allows for
representing all timed automata with a fixed number
of locations. We then leverage the parametric verifi-
cation capabilities of the IMITATOR model checker
(André, 2021). Since the tool supports TCTL, we
begin with (bounded) satisfiability checking for this
logic. Extending the method to STCTL involves
adding an auxiliary set of parameters in the IMITA-
144
Penczek, W., Petrucci, L. and Sidoruk, T.
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR.
DOI: 10.5220/0013257700003890
In Proceedings of the 17th International Conference on Agents and Artificial Intelligence (ICAART 2025) - Volume 1, pages 144-155
ISBN: 978-989-758-737-5; ISSN: 2184-433X
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)

TOR model, so as to restrict the choices of coalition
agents, ensuring they form valid ir-strategies. In fact,
we use the same technique as in (Arias et al., 2023)
for STCTL model checking.
Notably, using a parametric verifier in this man-
ner allows not only for obtaining an entire model sat-
isfying some input property, but also for partial syn-
thesis of one or more (often critical) components of a
larger system whose remaining parts are already spec-
ified. Therefore, in our experimental evaluation, we
include both full and partial synthesis of models. The
latter option is particularly relevant, given the high
computational cost of full satisfiability checking, and
could be used in practice for a number of applica-
tions, e.g., in automated control or security systems
(Dubinin et al., 2015), offering a new approach to ef-
ficiently obtain controller modules enforcing the de-
sired behaviour in such scenarios. In fact, the pro-
posed method guarantees that the optimal, i.e., small-
est possible, component will be produced, which fol-
lows directly from our iterative, bounded approach to
satisfiability checking.
Related Work. STCTL was proposed in (Arias
et al., 2023), including a method for model check-
ing STCTL formulae over asynchronous multi-agent
systems (AMAS) (Jamroga et al., 2020). Relevant
logical formalisms include especially Alternating-
time Temporal Logic ATL
∗
and its subset ATL (Alur
et al., 2002), which extend linear temporal logic LTL
with the strategic modality (in case of ATL it has to
be immediately followed by a single temporal opera-
tor), and over the last two decades have become the
most popular logics for reasoning about the strategic
abilities of agents. ATL
∗
model checking algorithms
have been proposed for memoryless and perfect recall
strategies (Alur et al., 2002) of agents with imper-
fect and perfect information (Jamroga, 2015) about
the state of the system (except for the combination of
imperfect information and perfect recall, where the
problem is undecidable (Dima and Tiplea, 2011)).
They have been applied for the verification of syn-
chronous (Lomuscio and Raimondi, 2006) as well as
asynchronous models (Jamroga et al., 2022); in the
latter case, efficient reduction techniques have been
adapted from LTL to mitigate state explosion (Jam-
roga et al., 2020). TATL (Laroussinie et al., 2006) ex-
tends ATL with time representation; several variants
of TATL have been investigated, including a counting
strategy semantics (see comparison in (Knapik et al.,
2019)), but only in conjunction with discrete time.
On the other hand, the satisfiability problem has
not been investigated nearly as broadly for the afore-
mentioned logics, due to its significantly higher com-
plexity than model checking (e.g., EXPTIME vs.
PTIME for ATL with perfect information). One ap-
proach involves tableau-based procedures, success-
fully used for both ATL (Goranko and Shkatov,
2009) and ATL
∗
(David, 2015). The other leverages
Boolean monotonic theories (SMMT) solvers, origi-
nally proposed for CTL (Klenze et al., 2016), later
extended to ATL (Kacprzak et al., 2020; Niewiadom-
ski et al., 2020), and even a subset of Strategy Logic
(Kacprzak et al., 2021), a more expressive formalism
originally proposed in (Belardinelli et al., 2019).
Timed extensions of these temporal and strate-
gic logics present a further challenge to satisfiability
checking. In particular, adopting the continuous se-
mantics of time typically means the problem becomes
undecidable, such as for the real-time extensions of
classical linear and branching temporal logics: Met-
ric Temporal Logic MTL (Bouyer, 2009; Alur and
Henzinger, 1993) and TCTL (Alur et al., 1993a).
This motivates the pursuit for bounded approaches,
such as the one presented in this paper. In particu-
lar, (Kacprzak et al., 2023) proposes such a method
for Strategic MTL (SMTL), obtaining partial model
synthesis via SMT-solvers combined with parametric
model checking,
Finally, the recent paper (Arias et al., 2024) con-
siders STCTL model checking and partial model syn-
thesis, making it the closest related work. The in-
vestigated approach is declarative, based on rewrit-
ing logic (Meseguer, 1992; Meseguer, 2012), and in-
cludes practical evaluation using the Maude verifier,
obtaining promising results. However, both the partial
specification and the synthesised component in (Arias
et al., 2024) do not contain any timing constraints,
effectively making it an instance of the problem for
SCTL, the untimed subset of the logic. As such,
the results are not directly comparable with those ob-
tained by our method, which also considers timing
constraints in synthesised automata and therefore is
much more broadly applicable.
Contribution. The novel contribution of the paper
can be summarised as follows.
• We propose a partial algorithm for STCTL satisfia-
bility checking (a problem undecidable in general),
applicable to the fragment of the logic supported
in the latest version of the verifier IMITATOR, i.e.,
non-nested formulas of the form ⟨⟨A⟩⟩∃F , ⟨⟨A⟩⟩∀F ,
and ⟨⟨A⟩⟩∀G ¬. Since we allow for equalities in
clock constraints (La Torre and Napoli, 2000), the
problem remains undecidable also for this subset of
STCTL, motivating our bounded approach.
• We experimentally evaluate our approach using
several scalable benchmarks, including scenarios
that involve both full and partial synthesis of timed
automata networks.
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR
145

Outline. The paper is structured as follows. Sec-
tion 2 recalls the theoretical background of STCTL
and the multi-agent formalism used. Then, we present
our method in Section 3, first for TCTL, and extend
it to STCTL. To demonstrate its practical feasibility,
we generate scalable test instances and conduct ex-
periments with IMITATOR, summarised in Section 4.
Section 5 concludes the paper.
2 PRELIMINARIES
In this section, we recall from (Arias et al., 2023) the
asynchronous multi-agent formalism with continuous
(dense) time, and the logical framework for reasoning
about strategic abilities of agents in such models.
2.1 Continuous-Time AMAS
Asynchronous Multi-Agent Systems (AMAS (Jamroga
et al., 2020)) are similar to networks of automata that
synchronise on shared actions, and interleave local
transitions to execute asynchronously (Fagin et al.,
1995; Lomuscio et al., 2010). However, to deal with
agent coalitions, automata semantics must resort to
algorithms and additional attributes. In contrast, by
linking protocols to agents, AMAS are a natural com-
positional formalism to analyse multi-agent systems.
Augmenting AMAS with continuous time involves
some of the standard notions of timed systems (Alur
and Dill, 1990). By N and R
0+
, we denote the sets of
natural numbers and non-negative reals, respectively.
Definition 1 (Clocks). We denote a finite set of
clocks, with a fixed ordering assumed for simplicity,
by X = {x
1
,... ,x
|X |
}, where x
i
∈ R
0+
. A clock valu-
ation on X is a |X |-tuple v. We denote:
• by v(x
i
) or v(i), the value of clock x
i
in v;
• by v
′
= v + δ, the increment of all clocks x ∈ X by
δ ∈ R
0+
;
• by v
′
= v[X := 0], the reset of a subset of clocks X ⊆
X , such that v
′
(x) = 0 for all x ∈ X, and v
′
(x) = v(x)
for all x ∈ X \ X.
Definition 2 (Clock constraints). The set C
X
collects
all clock constraints over X , defined by the grammar:
cc := true | x
i
∼ c | x
i
− x
j
∼ c | cc ∧ cc, where x
i
,x
j
∈
X , c ∈ N, and ∼∈ {≤,<, =, >,≥}. For cc ∈ C
X
, the
satisfaction relation |= is inductively defined as:
v |= true,
v |= (x
i
∼ c) iff v(x
i
) ∼ c,
v |= (x
i
− x
j
∼ c) iff v(x
i
) − v(x
j
) ∼ c, and
v |= (cc ∧ cc
′
) iff v |= cc and v |= cc
′
.
JccK denotes the set of all valuations satisfying cc.
In continuous-time AMAS (CAMAS), all agents
have an associated set of clocks and a local invari-
ant function defining a clock constraint for each local
state. Clocks evolve at the same rate (across agents),
thus allowing for delays and instantaneous actions.
Definition 3 (CAMAS). A continuous-
time AMAS (CAMAS) consists of n agents
A = {1,.. .,n}, each associated with a 9-tuple
AG
i
= (L
i
,ι
i
,Act
i
,P
i
,X
i
,I
i
,T
i
,PV
i
,V
i
) including:
• a finite non-empty set of local states L
i
=
{l
1
i
,l
2
i
,... ,l
n
i
i
};
• an initial local state ι
i
∈ L
i
;
• a finite non-empty set of local actions Act
i
=
{a
1
i
,a
2
i
,... ,a
m
i
i
};
• a local protocol P
i
: L
i
→ 2
Act
i
\ {
/
0};
• a set of clocks X
i
;
• a local invariant I
i
: L
i
→ C
X
i
;
• a (partial) local transition function T
i
: L
i
× Act
i
×
C
X
i
×2
X
i
⇀ L
i
such that T
i
(l
i
,a,cc,X ) = l
′
i
for some
l
′
i
∈ L
i
iff a ∈ P
i
(l
i
), cc ∈ C
X
i
, and X ⊆ X
i
;
• a finite non-empty set of local propositions PV
i
=
{p
1
i
,... ,p
r
i
i
};
• a local valuation function V
i
: L
i
→ 2
PV
i
.
For a local transition t := l
a,cc,X
−−−→ l
′
, l and l
′
are
the source and target states, a is the executed action,
clock condition cc is called a guard, and X is the set
of clocks to be reset. By Agent(a) = {i ∈ A|a ∈ Act
i
},
we denote the set of agents that “own” action a. Note
that T
i
is defined on local actions only. This is also
reflected in the formal definition of CAMAS models,
or Interleaved Interpreted Systems (Lomuscio et al.,
2010; Jamroga et al., 2020).
Definition 4 (Model). The model of a CAMAS is an
8-tuple M = (A,S,ι, Act, X ,I , T,V), including:
• the set of agents A = {1,..., n};
• the set of global states S =
∏
n
i=1
L
i
;
• the initial global state ι = (ι
1
,... ,ι
n
) ∈ S;
• the set of actions Act =
S
i∈A
Act
i
;
• the set of clocks X =
S
i∈A
X
i
;
• the invariant I (s) =
V
i∈A
I
i
(s
i
), where s
i
∈ L
i
de-
notes agent i’s local component of global state s;
• the global transition function T : S × Act × C
X
×
X → S, such that T (s, a,
V
i∈Agent(a)
cc
i
,X ) = s
′
iff
∀i ∈ Agent(a), T
i
(s
i
,a,cc
i
,X
i
) = s
′i
, whereas ∀i ∈
A \ Agent(a), s
i
= s
′i
;
• the valuation function V : S → 2
PV
, where PV =
S
n
i=1
PV
i
.
The continuous (dense) semantics of time defines
concrete states as tuples of global states and non-
negative real clock valuations.
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
146

Definition 5 (ACTS). The concrete model of a CA-
MAS model M = (A ,S, ι,Act,X ,I , T,V) is given
by its Asynchronous Continuous Transition System
(ACTS): a 5-tuple M = (A,C S ,q
ι
,→
c
,V
c
), includ-
ing:
• the set of agents A = {1,..., n};
• the set of concrete states C S = S × R
|X |
0+
;
• the concrete initial state q
ι
= (ι,v) ∈ C S , s.t. ∀x
i
∈
X , v(x
i
) = 0;
• the transition relation →
c
⊆ C S ×(Act ∪R
0+
)×C S ,
defined by time- and action- successors as follows:
(s,v)
δ
−→
c
(s,v+δ) for δ ∈ R
0+
and v,v +δ ∈ JI (s)K,
(s,v)
a
−→
c
(s
′
,v
′
) iff there are a ∈ Act, cc ∈ C
X
, X ⊆
X s.t.: s
a,cc,X
−−−→ s
′
∈ T , v ∈ JccK, v ∈ JI (s)K, v
′
=
v[X := 0], v
′
∈ JI (s
′
)K;
• the valuation function V
c
((s,v)) = V (s).
Intuitively, delays
δ
−→
c
increase the clock valua-
tion(s) by a given δ but do not change the global state,
while actions
a
−→
c
move to a successor state, possibly
resetting some clocks.
Definition 6 (Execution). An execution of ACTS M =
(A,C S , q
ι
,→
c
,V
c
) from concrete state q
0
= (s
0
,v
0
) is
a sequence ρ = q
0
,δ
0
,q
′
0
,a
0
,q
1
,δ
1
,q
′
1
,a
1
,... , where
q
i
= (s
i
,v
i
), q
′
i
= (s
i
,v
i+1
), such that for each i ≥ 0,
we have: δ
i
∈ R
0+
, a
i
∈ Act, q
i
δ
i
−→
c
q
′
i
a
i
−→
c
q
i+1
.
Note that due to the infinite number of con-
crete states, in practice we use the symbolic se-
mantics of (parametric) zone graphs, where zones
are convex polyhedra corresponding to clock con-
straints (Penczek and Pólrola, 2006). Moreover,
we parametrise CAMAS by replacing constants with
variables in clock constraints, as standard in Paramet-
ric Timed Automata (Penczek and Pólrola, 2006; An-
dré et al., 2016; André, 2019).
Untimed AMAS are a special case of Def. 3,
where X
i
=
/
0 for all i ∈ A. Since the set of clocks is
empty, the concrete model contains only action tran-
sitions, and thus it is identical to the model itself.
2.2 Strategies and Outcomes
Strategies are conditional plans that dictate the choice
of an agent in each possible situation, classified based
on agents’ state information: perfect (I) vs. imper-
fect (i), and their recall of state history: perfect (R)
vs. imperfect (r) (Schobbens, 2004). We consider
strategies of type ir.
Definition 7 ((Joint) ir-strategy). A memoryless im-
perfect information (ir) strategy for i ∈ A is a function
σ
i
: L
i
→ Act
i
such that σ
i
(l) ∈ P
i
(l) for each l ∈ L
i
.
A joint strategy σ
A
of coalition A ⊆ A is a tuple of
strategies, one for each agent i ∈ A.
The outcome of a joint strategy σ
A
collects all exe-
cutions consistent with σ
A
, i.e., such that the coalition
A strictly follows the strategy, while opponents freely
choose actions allowed by their protocols.
Definition 8 (Outcome). Let M be an ACTS, A ⊆ A,
and ρ = q
0
,δ
0
,q
′
0
,a
0
,q
1
,δ
1
,q
′
1
,a
1
,... , where q
j
=
(s
j
,v
j
), q
′
j
= (s
j
,v
j+1
), an execution of M . The out-
come of ir-strategy σ
A
in state q
0
of M , denoted by
out
ir
M
(q
0
,σ
A
), collects all executions ρ such that for
each i ∈ A and j ≥ 0 we have: if i ∈ Agent(a
j
) ∩ A
then a
j
= σ
i
(s
i
j
).
Providing the semantics for STCTL requires in-
terpreting formulas along executions ρ of ACTS. To
that end, we recall from (Penczek and Pólrola, 2006)
the notion of a path corresponding to ρ.
Definition 9 (Corresponding path). Let ρ be an exe-
cution of an ACTS. By the dense path corresponding
to ρ, denoted by π
ρ
, we mean a mapping from R
0+
to
a set of concrete states, given by π
ρ
(r) = (s
i
,v
i
+ δ),
for r = Σ
i−1
j=0
δ
j
+ δ, where i ≥ 0 and 0 ≤ δ < δ
i
.
2.3 Syntax and Semantics of STCTL
Assume a countable set PV of atomic propositions,
and a finite set A of agents. The syntax of STCTL
(Arias et al., 2023) is defined as:
ϕ ::= p | ¬ϕ | ϕ ∧ ϕ | ⟨⟨A⟩⟩γ,
γ ::= ϕ | ¬γ | γ ∧ γ | ∀X γ | ∃X γ | ∀γU
I
γ | ∃γU
I
γ,
where p ∈ PV, A ⊆ A, and I ⊆ R
0+
is an interval with
bounds [n,n
′
], [n, n
′
), (n, n
′
], (n,n
′
), (n, ∞), or [n,∞),
for n,n
′
∈ N. The operator ⟨⟨A⟩⟩ states that coalition A
has a strategy to enforce the temporal property that
follows. ∀ (“for all paths") and ∃ (“there exists a
path") are standard CTL path quantifiers. U (“strong
until”) and X (“next”, untimed only) are standard tem-
poral operators. G (“always”), F (“eventually”), R
(“release”), and Boolean connectives can be derived
as usual. SCTL is obtained by restricting the time
intervals to I = [0,∞) and removing them from the
STCTL syntax. TCTL is obtained by removing the
strategic modality ⟨⟨A⟩⟩ from the STCTL syntax.
Note that we use a continuous-time representa-
tion, so the next-step operator X is not applicable
when real-valued clocks are involved. However, fol-
lowing (Arias et al., 2023), we keep the operator X in
the syntax, which allows to conveniently define other
logics (SCTL, CTL) as subsets of STCTL.
Definition 10 (STCTL Semantics). Let M =
(A,C S , q
ι
,→
c
,V
c
) be an ACTS, q
0
= (s,v) =
(s
0
,v
0
) ∈ C S a concrete state, A ⊆ A, ϕ,ψ be STCTL
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR
147

formulae, ρ = q
0
,δ
0
,q
′
0
,a
0
,... an execution of M
where q
k
= (s
k
,v
k
), q
′
k
= (s
k
,v
k+1
), and π
ρ
be the
dense path corresponding to ρ. The ir-semantics of
STCTL is given as:
• M ,(s,v) |= p iff p ∈ V
c
(s,v),
• M ,(s,v) |= ¬ϕ iff M,(s,v) ̸|= ϕ,
• M ,(s,v) |= ϕ∧ψ iff M,(s,v) |= ϕ and M,(s,v) |= ψ,
• M ,(s,v) |= ⟨⟨A⟩⟩γ iff there exists a joint strategy σ
A
such that we have M ,out
ir
M
((s,v),σ
A
) |= γ, where:
• M ,out
ir
M
((s,v),σ
A
) |= ϕ iff M, (s,v) |= ϕ,
• M ,out
ir
M
((s,v),σ
A
) |= ∀X γ iff for each ρ ∈
out
ir
M
((s,v),σ
A
) we have M ,(ρ,σ
A
,ir) |= X ϕ,
• M ,out
ir
M
((s,v),σ
A
) |= ∀γ
1
U
I
γ
2
iff for each ρ ∈
out
ir
M
((s,v),σ
A
) we have M , (ρ,σ
A
,ir) |= γ
1
U
I
γ
2
,
• M ,out
ir
M
((s,v),σ
A
) |= ∃γ
1
U
I
γ
2
iff for some ρ ∈
out
ir
M
((s,v),σ
A
) we have M , (ρ,σ
A
,ir) |= γ
1
U
I
γ
2
,
where:
• M ,(ρ,σ
A
,ir) |= X γ iff M , out
ir
M
(s
1
,σ
A
) |= γ
(untimed only)
• M ,(ρ,σ
A
,ir) |= γ
1
U
I
γ
2
iff there is r ∈ I:
M ,out
ir
M
((π
ρ
(r)), σ
A
) |= γ
2
and for all 0 ≤ r
′
<
r: M ,out
ir
M
((π
ρ
(r
′
)),σ
A
) |= γ
1
,
3 ALGORITHMS FOR
SATISFIABILITY CHECKING
In this section, we present our approach to TCTL sat-
isfiability checking and then extend it for Strategic
TCTL.
3.1 Satisfiability Checking for TCTL
It has been known for over three decades that in gen-
eral, TCTL satisfiability is not decidable (Alur et al.,
1993a). As such, no algorithm solving this problem
exists. However, what we can offer is a partial al-
gorithm; one that is guaranteed to stop, but can only
prove the satisfiability (and not the unsatisfiability) of
a given TCTL formula. The idea is as follows. We
use the parametric model checker IMITATOR (An-
dré, 2021), which supports a fragment of TCTL, to
check the satisfiability of the same fragment of the
logic.
1
In fact, we aim at solving the problem of
bounded satisfiability as we are able to check whether
there exists a timed automaton of size up to some
k ∈ N whose model satisfies our formula. Consider
1
Note that the problem remains undecidable for the
fragment supported by IMITATOR, unless equalities in tim-
ing constraints are omitted (La Torre and Napoli, 2000).
a TCTL formula ϕ of the form ϕ = ∃F ..., ϕ = ∀F ...,
or ϕ = ∀G ¬..., which corresponds to the subset sup-
ported by the latest version of IMITATOR, formally
defined by the following grammar.
Definition 11 (Supported subset of TCTL). The sub-
set of TCTL supported by IMITATOR is defined as:
γ ::= ϕ | ¬γ | γ ∧ γ | ∀F
I
ϕ | ∃F
I
ϕ | ∀G
I
ϕ,
ϕ ::= p | ¬ϕ | ϕ ∧ ϕ.
where p ∈ PV and I ⊆ R
0+
are defined as in Sec. 2.3.
Parametric Timed Automata. Crucially, IMITA-
TOR is a parametric model checker, that is, it allows
for input model (i.e., networks of automata analogous
to CAMAS) in which the constants in state invariants
and transition guards have been replaced by parame-
ters. The output, given a TCTL formula and a Para-
metric Timed Automaton (PTA), is then one or more
sets of parameter valuations for which the formula is
satisfied, or UNSAT if no such valuations exist. For
our purpose, it is sufficient to obtain just one valu-
ation, therefore we use the #witness keyword rather
than #synth in the IMITATOR property specification.
Note that compared to PTA as originally proposed in
(Alur et al., 1993b), the input models of IMITATOR
are augmented with several features (André, 2021).
We refer the reader to the tool’s website and user man-
ual available at https://www.imitator.fr for more de-
tails on the supported PTAs and their formal defini-
tions.
Bounded Satisfiability Checking. In order to prove
the (bounded) satisfiability of formula ϕ, one needs
to demonstrate the existence of a timed automaton
of size k such that ϕ holds in its model (Laroussinie
et al., 1995). While it is not possible to generate
all such timed automata, (since there are infinitely
many due to the infinite number of clock expressions
in guards and invariants), it is possible to symbol-
ically encode all of them using a finite number of
parametric clock expressions. Note that our approach
can only be compared to Bounded Model Checking
(BMC) in the sense that both of them set an upper
bound within which to tackle a very challenging prob-
lem. The way BMC is done is completely different,
and typically involves encoding (possibly symbolic)
of finite paths in the model to SAT or SMT, and then
leveraging the corresponding solver to handle subse-
quent instances.
In the following subsection, we discuss this en-
coding and formally define the parametric timed au-
tomaton (PTA) that symbolically represents all possi-
ble timed automata with k locations. Then, in Sec. 3.7
we discuss an extension of this approach to the logic
STCTL, i.e., TCTL augmented with the strategic op-
erator ⟨⟨⟩⟩.
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
148

3.2 Parameters and Restrictions
In this work, our main aim is to establish the feasibil-
ity of the proposed approach to TCTL (and STCTL)
satisfiability checking. To that end, we establish cer-
tain restrictions in order to limit the blow-up in the
size of the IMITATOR model in practical experi-
ments. In particular, to avoid duplicating all locations,
we assume all invariants to be of one particular form,
and use one clock per automaton.
Furthermore, when dealing with a network of
timed automata, the different combinations of pri-
vate and shared actions between local components
induce yet additional complexity. To mitigate the
issue, rather than synthesise the entire network, we
aim at obtaining a single parametric timed automaton
(PTA), and assume the specifications of the remaining
parts of the network are known in advance (including
which of their transitions are intended to be shared
with the newly generated component).
We now detail the constants and parameters used
in the IMITATOR model and the constraints imposed
on them. Then, we formally define the parametric
timed automaton that encodes all possible timed au-
tomata meeting these constraints.
• We restrict the number of clocks x ∈ R
0+
to one
per automaton.
2
Note that this class of timed au-
tomata remains a relevant subset studied in the lit-
erature (Laroussinie et al., 2004; Chen and Lu,
2008); moreover, it may be possible to reduce the
number of clocks if more are present (Daws and
Yovine, 1996; Guha et al., 2014). Clock expres-
sions are of the form x ∼ c, where x ∈ X , c ∈ N and
∼∈ {≤,<, =,>,≥}, i.e., only non-diagonal con-
straints.
• We encode a single parametric timed automaton. In
other words, we either assume this PTA to represent
an AMAS model (cf. Def. 4), or to be part of an au-
tomata network (i.e., AMAS) whose other compo-
nents are known and already specified.
• By k ∈ N, we denote the (fixed) number of locations
in the automaton. Without loss of generality, we
arbitrarily designate one of them as initial.
• Each location l
i
is associated with one invariant, as-
sumed to be of the form x ≤ p
I
l
i
, i.e., without diago-
nal clock constraints, where p
I
l
i
∈ N is the invariant
parameter.
• There are k
2
possible transitions, one for each pair
of locations (l
i
,l
j
), including self-loops.
2
If needed, we may also use an auxiliary variable t ∈
R
0+
to represent elapsed global time in the IMITATOR
model, see Sec. 4.
• Each transition t is associated with a guard of one
of two forms: p
G
t
≤ x ≤ p
′G
t
or p
G
t
≤ x, i.e., with-
out diagonal clock constraints, where p
G
t
, p
′G
t
∈ N
are the guard parameters. We will sometimes write
p
G
(l,l
′
)
, p
′G
(l,l
′
)
instead of p
G
t
, p
′G
t
to denote the guard
parameters associated with transition t : l → l
′
.
• We assume that for any pair of locations l
i
,l
j
, there
exists at most one transition l
i
→ l
j
, i.e., multiple
variants wrt. guard forms and clock resets (see be-
low) cannot coexist in one concrete model.
• Due to different combinations of guards and clock
resets, each transition t, for any source and target
states l
i
,l
j
, occurs in one of the following variants
var ∈ {1,... ,4}:
1. Transition l
i
→ l
j
with a guard of the form p
G
t
≤
x ≤ p
′G
t
, resetting the clock x,
2. Transition l
i
→ l
j
with a guard of the form p
G
t
≤
x, resetting the clock x,
3. Transition l
i
→ l
j
with a guard of the form p
G
t
≤
x ≤ p
′G
t
without a clock reset,
4. Transition l
i
→ l
j
with a guard of the form p
G
t
≤ x
without a clock reset,
Note that the possibility where no transition exists
from l
i
to l
j
is also covered; in this case IMITATOR
will synthesise some other value var /∈ {1, ... , 4}.
The restrictions on the types of guards and invari-
ants are relatively minor and can always be relaxed,
albeit at the cost of increasing the encoding size. Lim-
iting each automaton to a single clock is somewhat
more restrictive, but this class of automata remains
an interesting subset frequently studied in the litera-
ture. The restriction to encoding a single parametric
timed automaton is strongly motivated by its greater
manageability and its suitability for typical scenarios,
such as synthesizing a single controller based on the
specifications of other existing modules.
3.3 Encoding
In the following, we assume x ∈ X is a clock, and
the sets of guards, invariants, and parameters are as
follows:
Guards = {p
G
t
≤ x ≤ p
′G
t
, p
G
t
≤ x},
Invariants = {p
I
l
≤ x},
Params = Params
G
∪ Params
I
∪ Params
T
=
{p
G
(l
1
,l
1
)
,... , p
′G
(l
k
,l
k
)
} ∪ {p
I
l
1
,... , p
I
l
k
} ∪
{p
T
l
1
,... , p
T
l
k
},
where p
G
(l
i
,l
j
)
, p
′G
(l
i
,l
j
)
, and p
I
l
i
, p
T
l
i
are associated with
transition l
i
→ l
j
and location l
i
, respectively, and all
are integers.
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR
149

These are, respectively, the parameters that ap-
pear in guards, invariants, and transition variants. In
the latter case, they are evaluated in equations of
the form PExpr = {p
T
l
= var | p
T
l
∈ Params ∧ var ∈
{1,... ,4}} in the transitions of P T A
P
ϕ
k
, see below.
Definition 12. The parametric timed automaton
P T A
P
ϕ
k
for ϕ, with k ∈ N locations and pa-
rameters P = Params, is defined as P T A
P
ϕ
k
=
(L,ι,Act,X ,I ,T,PV,V ), where:
• L = {l
1
,l
2
,... ,l
k
};
• ι = l
1
;
• Act = {a
(1,1)
,... ,a
(1,k)
,... ,a
(k,1)
,... ,a
(k,k)
};
• X = {x};
• I : L → Invariants,
• T ⊆ L × Act × Guards × PExpr × X × L, defined
as:
T =
S
l,l
′
∈L
(T
1
(l, l
′
) ∪ ·· · ∪ T
4
(l, l
′
)), where:
T
1
(l, l
′
) = {(l,a
(l,l
′
)
,(p
G
(l,l
′
)
≤ x ≤ p
′G
(l,l
′
)
),(p
T
l
= 1),{x},l
′
)},
T
2
(l, l
′
) = {(l,a
(l,l
′
)
,(p
G
(l,l
′
)
≤ x),(p
T
l
= 2),{x},l
′
)},
T
3
(l, l
′
) = {(l,a
(l,l
′
)
,(p
G
(l,l
′
)
≤ x ≤ p
′G
(l,l
′
)
),(p
T
l
= 3),
/
0,l
′
)},
T
4
(l, l
′
) = {(l,a
(l,l
′
)
,(p
G
(l,l
′
)
≤ x),(p
T
l
= 4),
/
0,l
′
)}.
• PV = Prop(ϕ) = {p
1
,p
2
,... ,p
k
};
• ∀
l∈L
V (l) ∈ 2
PV
, where PV is a set of Boolean vari-
ables corresponding to locations.
Intuitively, when executing action a
(l,l
′
)
from lo-
cation l the automaton makes a choice, by setting
the corresponding transition parameter p
T
i
to var ∈
{1,... ,4}, to fire one of four copies T
1
(l, l
′
), T
2
(l, l
′
),
T
3
(l, l
′
), T
4
(l, l
′
).
3.4 Complexity and Correctness
We now analyse the computational complexity of
the encoding and show that the parametric timed au-
tomaton P T A
P
ϕ
k
defined above encodes all timed au-
tomata of size k (assuming the restrictions detailed in
Sec. 3.2).
Lemma 1. The encoding of parametric timed au-
tomaton P T A
P
ϕ
k
is of size O(k
2
) and uses O(k
2
) vari-
ables and parameters.
Proof. Clearly, encoding P T A
P
ϕ
k
in IMITATOR first
requires exactly k variables corresponding to its k ∈ N
locations. Note that each location induces one invari-
ant parameter, one transition choice parameter, and 2k
guard parameters (one guard per transition, indexed
by its source and target states). Therefore, the to-
tal number of variables/parameters is k · (2k + 2) =
2k
2
+ 2k, and thus in O(k
2
).
Since we first initialize 2k
2
+ 2k variables (see
above), and then define 4k
2
transitions (four variants
per transition per location), the size of the encoding is
6k
2
+ 2k, which is also in O(k
2
).
Theorem 1. P T A
P
ϕ
k
encodes all the timed automata
with k locations within the restrictions outlined above
in Sec. 3.2.
Proof. First, note that P T A
P
ϕ
k
always has k loca-
tions, and all possible transitions between them are
accounted for: from each location to the k − 1 others
plus a self loop (for a total of k
2
transitions). Fur-
thermore, it is not possible for multiple variants of a
single transition to occur simultaneously, as they are
associated with the same parameter (only one value
of which will be synthesised by IMITATOR). This
is consistent with the established restrictions on the
structure of P T A
P
ϕ
k
, and each variant corresponds to
the allowed forms of guards, with or without resets.
For a discussion of the parameter synthesis algorithm
implemented in IMITATOR and its correctness, we
refer the reader to (André et al., 2019).
3.5 Using IMITATOR
IMITATOR supports parametric model checking for
a fragment of TCTL (see Def. 11), including non-
nested formulas ϕ of the form ∃F ..., ∀F ... or ∀G ¬....
For an input formula ϕ it returns the set P
ϕ
of param-
eters for which we have that M ,q
ι
|= ϕ, where M is
the concrete model (ACTS) of P T A
P
ϕ
k
. If P
ϕ
=
/
0,
then ϕ is not satisfiable within the bound k on the
number of locations in the automaton. While IMI-
TATOR supports Boolean combinations of predicates
embedded in formulas, relevant combinators are not
provided for formulas themselves, e.g., ∃F φ
1
∧ ∃F φ
2
.
However, one can run the verifier separately for both
disjuncts (resp. conjuncts) and take the union (resp.
intersection) of the resulting sets of parameters:
• for an input formula ϕ = ϕ
1
∨ϕ
2
, IMITATOR is run
for ϕ
1
and for ϕ
2
, and P
ϕ
= P
ϕ
1
∪ P
ϕ
2
,
• for an input formula ϕ = ϕ
1
∧ϕ
2
, IMITATOR is run
for ϕ
1
and for ϕ
2
, and P
ϕ
= P
ϕ
1
∩ P
ϕ
2
.
3.6 Complete Satisfiability Checking
The procedure for checking whether a TCTL formula
ϕ is satisfiable is as follows. We initially start Alg. 1
for k = 1.
Clearly, the algorithm is always guaranteed to ter-
minate, returning SAT if the input formula ϕ is satis-
fiable within the chosen bound, or UNSAT otherwise.
Moreover, in the former case it ends with the smallest
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
150

1: Run IMITATOR for input automaton P T A
P
ϕ
k
and property ϕ.
2: if P
ϕ
̸= ∅ then
3: return SAT
4: else if (P
ϕ
= ∅ and k < bound) then
5: return SAT
TCTL
(ϕ,k + 1,bound)
6: else
7: return UNSAT
8: end if
Algorithm 1: SAT
TCTL
(ϕ,k,bound)
number of locations k ≤ bound which allows for the
formula satisfaction (with our additional constraints
specified in Sec. 3.2).
Example 1. Let propositions in PV = {eat
1
,think
1
}
denote that a philosopher is dining and thinking, re-
spectively. Consider the property φ = ∃F
[0,60]
think
1
.
For this small example, our PTA network will consist
of a single automaton with the number of locations
bounded to 2. Note that due to the way IMITATOR
handles local variables, eat
1
and think
1
are effec-
tively tied to local states. We begin with a model with
2 states and all possible transitions between them, de-
fined as in Def. 12. In particular, we use parameters to
ensure only one variant of each transition is present,
see Fig. 1. Note that to model the time interval [0, 60]
subscribed to temporal operator F , we add an extra
clock representing global time in IMITATOR.
3.7 Satisfiability Checking for STCTL
ir
We now discuss the extension of the approach pre-
sented above for TCTL to formulas of STCTL. For-
mally, the supported subset of STCTL is defined as in
Def. 11, except the strategic modality ⟨⟨A⟩⟩ is added
to each element of γ.
The intuition behind this extension is analogous to
the approach used in (Arias et al., 2023) where agents’
strategies were encoded as parameters to leverage IM-
ITATOR’s capabilities for STCTL model checking.
Essentially, the change consists in further restrict-
ing the transition choice parameters p
T
l
i
in each loca-
tion l
i
of the parametric timed automaton, but only for
the coalition agents. For a given agent coalition A, we
encode its strategies on top of the existing approach
detailed in Sec. 3.1 using a parametric timed automa-
ton P T A(A)
P
ϕ
k
, defined as follows:
Definition 13. Let A ⊆ A be an agent coalition.
The automaton P T A(A)
P
ϕ
k
is defined as previously in
Def. 12, except for each location l
i
, the corresponding
parametric expression is defined as: PExpr = {p
T
l
=
var | p
T
l
∈ Params ∧ var ∈ {1,..., 4,... ,4k}}, and it
is now checked in T as follows:
var x, time: clock;
p_guard_11, q_guard_11, p_guard_12, q_guard_12,
p_guard_21, q_guard_21, p_guard_22, q_guard_22,
p_invariant1, p_invariant2, t1, t2: parameter;
automaton pta
loc eat1: invariant x <= p_invariant1 & time <= 60
(* four copies of a^(1,1) *)
when p_guard_11 <= x & x <= q_guard_11
& t1 = 1 do {x:=0} goto eat1;
when p_guard_11 <= x
& t1 = 2 do {x:=0} goto eat1;
when p_guard_11 <= x & x <= q_guard_11
& t1 = 3 goto eat1;
when p_guard_11 <= x & t1 = 4 goto eat1;
(* four copies of a^(1,2) *)
when p_guard_12 <= x & x <= q_guard_12
& t1 = 1 do {x:=0} goto eat2;
when p_guard_12 <= x
& t1 = 2 do {x:=0} goto eat2;
when p_guard_12 <= x & x <= q_guard_12
& t1 = 3 goto eat2;
when p_guard_12 <= x & t1 = 4 goto eat2;
(* violation upon reaching 60 global time *)
when time > 60 goto violation;
loc eat2: invariant x <= p_invariant2 & time <= 60
(* location eat2 defined analogously *)
[...]
loc violation: invariant True (* auxiliary location *)
end
init := {
discrete = loc[pta] := eat1;
continuous = time >= 0 & x = 0
& p_guard_11 >= 0 & q_guard_11 >= 0
& p_guard_12 >= 0 & q_guard_12 >= 0
& p_guard_21 >= 0 & q_guard_21 >= 0
& p_guard_22 >= 0 & q_guard_22 >= 0
& p_invariant1 >= 0 & p_invariant2 >= 0
& t1 > 0 & t2 > 0;
}
end
property := #witness EF(loc[pta] = loc2);
Figure 1: IMITATOR model and property specification for
Example 1.
p
T
l
i
= 4 · (i − 1) + 1 for T
1
(l, l
′
),
p
T
l
i
= 4 · (i − 1) + 2 for T
2
(l, l
′
),
p
T
l
i
= 4 · (i − 1) + 3 for T
3
(l, l
′
),
p
T
l
i
= 4 · (i − 1) + 4 for T
4
(l, l
′
).
This ensures that the same choice is always made
not just between the three variants of a transition, but
across all outgoing transitions from a state, thus pro-
ducing a valid ir-strategy.
We note that conjunctions of the form ⟨⟨A⟩⟩ϕ
1
∧
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR
151
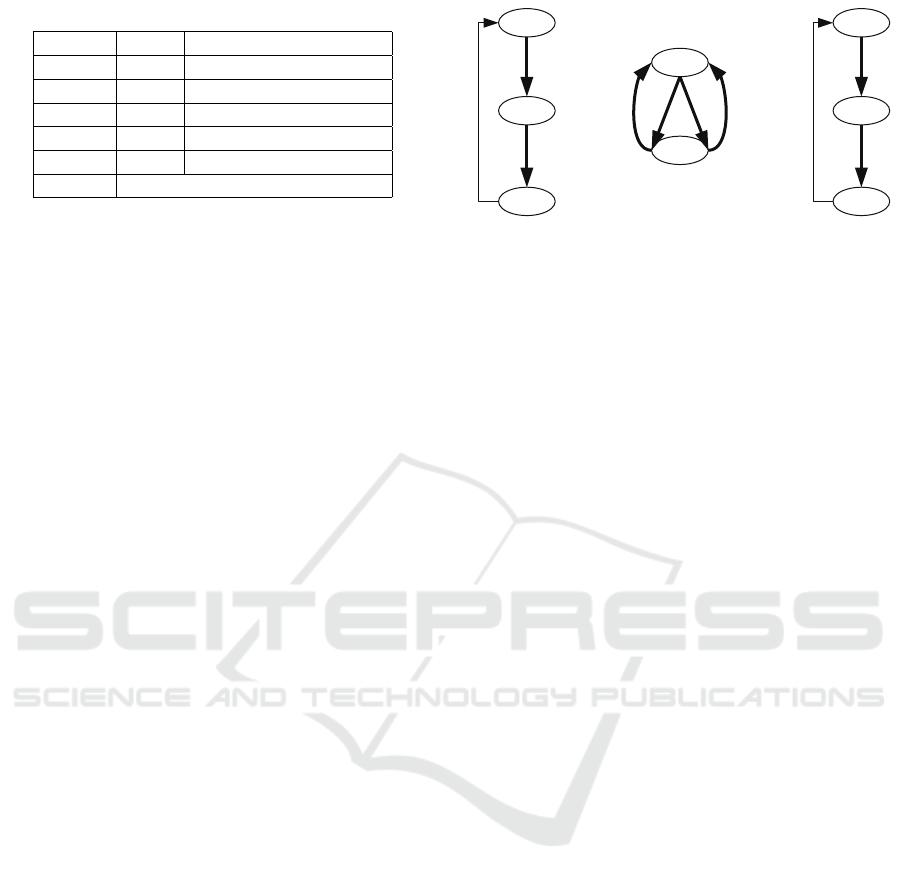
Table 1: Results for the Dining Philosophers benchmark.
# states result running time (seconds)
2 sat 0.01
5 sat 0.16
10 sat 11.4
15 sat 199
20 sat 1856
25 memout
⟨⟨B⟩⟩ϕ
2
can be handled via overapproximation, i.e.,
by taking the intersection A ∩ B of all involved agent
coalitions and checking the satisfiability of formula
⟨⟨A ∩ B⟩⟩ϕ
1
∧ ⟨⟨A ∩ B⟩⟩ϕ
2
. The same approach could
also be applied for nested strategic operators, how-
ever as pointed out in Sec. 3.1, nested formulas are
currently not supported by IMITATOR.
4 EXPERIMENTAL RESULTS
In this section, we discuss experimental results. To
demonstrate the practical feasibility of our approach,
we used three sets of scalable benchmarks, detailed
below. The IMITATOR binaries were run via Win-
dows Subsystem for Linux (WSL) on a Windows 10
PC with a 4.0 Ghz CPU and 64 GB RAM. As per the
default WSL configuration, the running process was
terminated if its memory usage exceeded half of the
total available, indicated by memout.
4.1 Full Synthesis
The first benchmark involves full synthesis of the en-
tire CAMAS.
Simple Dining Philosophers. This is a scaled ver-
sion of the simple model introduced in Example 1,
with the number of locations n in the synthesised PTA
ranging from 2 to 25. The set of propositional vari-
ables is PV = {eat
1
,think
1
,... ,eat
n
,think
n
}. Each
location i is associated with propositions eat
i
and
S
1..n
think
j
, where j ̸= i.
The formula φ
1
= ∃F
[0,60]
think
n
remains the same
as in Example 1. Experimental results are sum-
marised in Table 1.
Notice that IMITATOR’s running time is about
half an hour for n = 20 locations, showing that our
approach can be applied to models whose size ex-
ceeds simple toy examples. However, the scalabil-
ity remains somewhat limited, and there remain other
issues, especially the fact we currently synthesise a
single PTA.
Nonetheless, it bears reminding that TCTL and
STCTL synthesis is undecidable in general, and so
W
T
A
G
R
W
T
A
Train1 Train2Controller
a
1
a
1
a
2
a
2
a
3
b
1
b
1
b
2
b
2
b
3
Figure 2: The AMAS for the TGC scenario. Transitions a
3
and b
3
are private; all others (highlighted in bold) may be
shared.
is the bounded satisfiability problem for these logics,
even assuming their restricted subsets supported by
IMITATOR. As such, scaling to a larger number of
locations was always expected to be challenging. Fur-
thermore, obtaining small models satisfying a given
property is typically preferable, and often the only
feasible option given the complexity of the problem.
A potential alternative overcoming these pitfalls,
which we investigate with the next test instances, in-
volves synthesising a single, key component of a par-
tially defined model, rather than the full one.
4.2 Partial Synthesis
In the remaining two scenarios, a single CAMAS
component is obtained based on a partial model spec-
ification.
Train-Gate-Controller. Based on the classical
Train-Gate-Controller (TGC) scenario (Alur et al.,
1993b; Alur et al., 1998; Hoek and Wooldridge,
2002; Jamroga et al., 2020), this benchmark features
two trains and a controller tasked with preventing
both trains from entering a tunnel gate at the same
time.
As opposed to the Simple Dining Philosophers ex-
ample, we start with an automata network for TGC
rather than its product (i.e., model). This allows for
taking into account shared transitions between agents’
local components. Furthermore, it enables partial
synthesis where one or more automata are predefined.
Here, we assume that the specifications for the trains
are already given, while the controller satisfying the
required property (two trains will never be together in
the tunnel) is to be synthesised.
Unfortunately, there is a major drawback to syn-
thesising local components in this manner. In par-
ticular, we have no convenient way of parameteris-
ing shared transitions in IMITATOR. Thus, depend-
ing on the number of non-private actions in the pre-
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
152
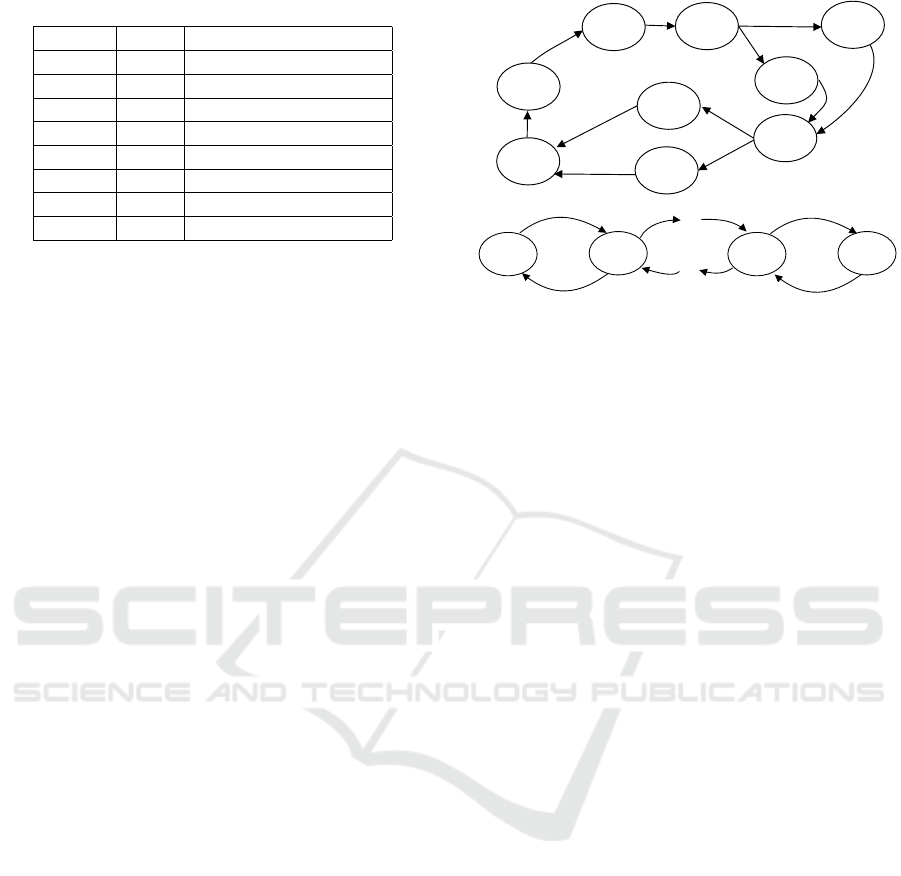
Table 2: Results for the Train-Gate-Controller benchmark.
# trains result running time (seconds)
2 sat 0.07
5 sat 0.53
10 sat 2.25
15 sat 5.16
20 sat 9.38
25 sat 14.5
50 sat 58.2
100 sat 284
defined local components of the trains, we need to
enumerate as many choices for each transition vari-
ant in the synthesised automaton of the controller.
As seen in Fig. 2, in this case there are four transi-
tions a
1
,a
2
,b
1
,b
2
of the trains that may or may not
be shared with those of the controller. Therefore, not
only does each of the latter’s transitions come in 4
variants corresponding to different combinations of
guards and resets, but each variant has 5 versions de-
pending on whether it is shared with a
1
, a
2
, b
1
, b
2
, or
private. This amounts to 20 copies of each transition,
making the proposed approach rather unsuitable for
all but the simplest specifications of the given compo-
nents, unless of course they are assumed to use private
transitions exclusively.
The set of propositional variables is PV =
{away
1
,away
2
}, representing train 1 and train 2 hav-
ing gone through the tunnel, respectively, and as-
sociated with the corresponding locations in their
predefined local automata. The formula φ
2
=
⟨⟨Controller⟩⟩∃F
[0,60]
away
1
says that the controller
has a strategy to let the first train through the tun-
nel within 60 time units. Since this is a STCTL
property, we use transition choice parameters accord-
ingly, as per Def. 13. That is, the range of t
1
and t
2
is {1,.. . ,8}, rather than {1,. ..,4} for non-strategic
properties. The results for this benchmark, scaled
with the number of trains, are presented in Table 2.
Indeed, it turns out that partial synthesis in TGC
scales much better than the approach taken in the
previous benchmark, even when the controller has
a significant number of copied transitions that cor-
respond to possible synchronisations with different
trains. Clearly, the complexity induced by synchro-
nisation with the predefined components is far out-
weighed by that stemming from increasing the bound
on the synthesised automaton’s size (the latter evi-
dent in the results for Dining Philosophers). This is
good news, as it demonstrates that our method can be
applied even in larger multi-agent models, provided
that the component to be obtained remains relatively
small (which, realistically, is always a requirement in
today’s state of the art, understandably so given the
think
j
x
j
≤ T
1
hungry
j
waiting
j
releaseL
j
waitL
j
waitR
j
eat
j
x
j
≤ E
1
rel easeR
j
rel eased
j
wantEat
j
x
j
≥ T
2
in
j
getL
j
getR
j
getR
j
x
j
:= 0
getL
j
x
j
:= 0
putR
j
x
j
≥ E
2
putR
j
x
j
≥ E
2
putR
j
x
j
≥ E
2
putL
j
x
j
≥ E
2
out
j
x
j
:= 0
l
0
l
1
l
n−2
l
n−1
out
∗,
in
∗ out
∗,
in
∗
out
∗,
in
∗
out
∗,
in
∗
· · ·
Figure 3: The philosopher (above) and the lackey (below)
in the Timed Dining Philosophers benchmark.
computational complexity of the problem). Note that
the number of locations of the controller is fixed at
2 in this benchmark: since the property φ
2
is already
satisfied, there is no need to attempt synthesising a
larger module. Moreover, incrementing the bound
from an initial minimal value guarantees that an op-
timal (smallest possible) controller will be obtained,
which of course represents a major advantage from a
practical standpoint.
Timed Dining Philosophers. Finally, we also in-
clude a significantly more involved variant of Dining
Philosophers, previously featured in (Kacprzak et al.,
2023) and (Arias et al., 2024).
This version, presented in Fig. 3, includes a sepa-
rate “lackey” agent (to be synthesised), who controls
the philosophers’ access to the dining room. More-
over, the philosophers’ components (given in the par-
tial models specification) are much more complex and
contain timing constraints in the form of invariants
on several locations, as well as guards on transitions.
Some of the latter also reset the clock. As such, this
benchmark allows us to better evaluate how the effi-
ciency of our approach is impacted by the continuous
time representation in the input partial CAMAS spec-
ification. To that end, we consider two additional vari-
ants of each test instance: a reduced model, in which
we make an additional assumption that there are no
clocks and no invariants in the lackey automaton, and
an untimed one, where we also assume no clocks. The
results are summarised in Table 3.
Clearly, the results indicate that even partial syn-
thesis remains a major challenge when timing con-
straints are involved. That is to be expected, as the
continuous time representation is the main source
of the complexity in the verification and satisfiabil-
ity checking of timed strategic and temporal logics.
Note that while the benchmark was previously used
in (Arias et al., 2024), only the untimed case was con-
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR
153

Table 3: Results for Timed Dining Philosophers.
# philos. result model running time (s)
2 sat
full 50
reduced 0.25
untimed 0.06
3 sat
full memout
reduced 447
untimed 16
sidered there in the context of (partial) synthesis for
STCTL. Thus our method, albeit slower, can be ap-
plied to a much broader class of models. Moreover,
the restrictions on components to be obtained can be
relaxed or made stricter as needed, including for spe-
cific locations or transitions that might be known in
advance based on the partial specification, allowing
to precisely tune it to the needs particular application,
and in doing so achieve better efficiency.
We briefly touch upon some aspects of model
synthesis for strategic properties, in particular those
related to synchronisation between transitions, that
remain an interesting subject for further work and
could potentially lead to some optimisations in our
approach. For instance, depending on the scenario, it
may be the case that having no synchronised transi-
tions between certain locations is not a viable option
for the resulting system, and as such the IMITATOR
model can be simplified accordingly. Moreover, when
synthesising a strategy for agents in some coalition A,
one could restrict the set of transitions considered for
synchronisation only to those “owned” by agents in
A, i.e., transitions that are in their local protocols.
5 CONCLUSIONS
We proposed an initial approach to (bounded) satisfi-
ability checking for TCTL and its strategic extension
STCTL under the imperfect information semantics.
Using the IMITATOR verifier, we demonstrated the
practical feasibility of our method by means of model
checking the input formula over a parametric timed
automaton (PTA) encoding all possible PTA up to a
bounded number of locations.
In the future, we intend to investigate whether this
encoding can be improved, which would potentially
lead to better scalability and allow for lifting some
of the current restrictions on guards and shared tran-
sitions. Other ways of tackling TCTL and STCTL
satisfiability also represent potential avenues of fur-
ther research. In particular, one may consider a full-
fledged encoding of the problem to SMT (Klenze
et al., 2016; Kacprzak et al., 2020; Niewiadomski
et al., 2020; Kacprzak et al., 2021; Kacprzak et al.,
2023), or extending the declarative approach of (Arias
et al., 2024) to support synthesis of timed components
and possibly also full models.
ACKNOWLEDGEMENTS
This work was supported by the PHC Polonium
project MoCcA (BPN/BFR/2023/1/00045), CNRS
IRP “Le Trójk ˛at”, the ANR-22-CE48-0012 project
BISOUS, and by NCBR Poland & FNR Luxembourg
under the PolLux/FNR-CORE project SpaceVote
(POLLUX-XI/14/SpaceVote/2023).
REFERENCES
Alur, R., Courcoubetis, C., and Dill, D. L. (1993a).
Model-Checking in Dense Real-Time. Inf. Comput.,
104(1):2–34.
Alur, R. and Dill, D. L. (1990). Automata for Modeling
Real-Time Systems. In Proceedings of ICALP’90,
pages 322–335. Springer.
Alur, R., Henzinger, T., Mang, F., Qadeer, S., Rajamani,
S., and Tasiran, S. (1998). MOCHA: Modularity in
Model Checking. In Proceedings of CAV’98, pages
521–525. Springer.
Alur, R. and Henzinger, T. A. (1993). Real-Time Log-
ics: Complexity and Expressiveness. Inf. Comput.,
104(1):35–77.
Alur, R., Henzinger, T. A., and Kupferman, O. (2002).
Alternating-time Temporal Logic. J. ACM, 49:672–
713.
Alur, R., Henzinger, T. A., and Vardi, M. Y. (1993b). Para-
metric Real-time Reasoning. In Proceedings of STOC
’93, pages 592–601. ACM.
André, É. (2019). What’s Decidable about Parametric
Timed Automata? Int. J. Softw. Tools Technol. Transf.,
21(2):203–219.
André, É. (2021). IMITATOR 3: Synthesis of timing pa-
rameters beyond decidability. In Proceedings of CAV
2021, pages 552–565. Springer.
André, É., Bloemen, V., Petrucci, L., and van de Pol,
J. (2019). Minimal-Time Synthesis for Parametric
Timed Automata. In Tools and Algorithms for the
Construction and Analysis of Systems, pages 211–228.
Springer.
André, É., Knapik, M., Penczek, W., and Petrucci, L.
(2016). Controlling Actions and Time in Parametric
Timed Automata. In Proceedings of ACSD’16, pages
45–54. IEEE.
Arias, J., Budde, C. E., Penczek, W., Petrucci, L., Sidoruk,
T., and Stoelinga, M. (2020). Hackers vs. Security:
ADTrees as Asynchronous Multi-agent Systems. In
Proceedings of ICFEM 2020, pages 3–19. Springer.
Arias, J., Jamroga, W., Penczek, W., Petrucci, L., and
Sidoruk, T. (2023). Strategic (Timed) Computation
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
154

Tree Logic. In Proceedings of AAMAS’23, pages 382–
390. ACM.
Arias, J., Olarte, C., Penczek, W., Petrucci, L., and Sidoruk,
T. (2024). Model checking and synthesis for strate-
gic timed CTL using strategies in rewriting logic. In
Proceedings of PPDP 2024, pages 10:1–10:14. ACM.
Belardinelli, F., Jamroga, W., Kurpiewski, D., Malvone, V.,
and Murano, A. (2019). Strategy Logic with Simple
Goals: Tractable Reasoning about Strategies. In Pro-
ceedings of IJCAI’19, pages 88–94. ijcai.org.
Bouyer, P. (2009). Model-Checking Timed Temporal Log-
ics. Electron. Notes Theor. Comput. Sci., 231:323–
341.
Chen, T. and Lu, J. (2008). Towards the Complexity of
Controls for Timed Automata with a Small Number
of Clocks. In Proceedings of FSKD’08, pages 134–
138.
David, A. (2015). Deciding ATL
*
Satisfiability by
Tableaux. In Proceedings of CADE’15, pages 214–
228. Springer.
Daws, C. and Yovine, S. (1996). Reducing the Number of
Clock Variables of Timed Automata. In Proceedings
of RTSS’96, pages 73–81.
Dima, C. and Tiplea, F. (2011). Model-Checking ATL un-
der Imperfect Information and Perfect Recall Seman-
tics is Undecidable. CoRR, abs/1102.4225.
Dubinin, V., Vyatkin, V., and Hanisch, H.-M. (2015). Syn-
thesis of Safety Controllers for Distributed Automa-
tion Systems on the Basis of Reverse Safe Net Condi-
tion/Event Systems. In Proceedings of TrustCom’15,
pages 287–292.
Fagin, R., Halpern, J. Y., Moses, Y., and Vardi, M. Y.
(1995). Reasoning about Knowledge. MIT Press.
Goranko, V. and Shkatov, D. (2009). Tableau-based De-
cision Procedures for Logics of Strategic Ability in
Multiagent Systems. ACM Trans. Comput. Log.,
11(1).
Guha, S., Narayan, C., and Arun-Kumar, S. (2014). Reduc-
ing clocks in timed automata while preserving bisimu-
lation. In Proceedings of CONCUR 2014, pages 527–
543. Springer.
Hoek, W. and Wooldridge, M. (2002). Tractable Multia-
gent Planning for Epistemic Goals. In Proceedings of
AAMAS’02, pages 1167–1174. ACM Press.
Jamroga, W. (2015). Logical Methods for Specification and
Verification of Multi-Agent Systems. ICS PAS Pub-
lishing House.
Jamroga, W., Masko, L., Mikulski, L., Pazderski, W.,
Penczek, W., Sidoruk, T., and Kurpiewski, D. (2022).
Verification of Multi-Agent Properties in Electronic
Voting: A Case Study. In Proceedings of AiML 2022,
pages 531–556. College Publications.
Jamroga, W., Penczek, W., Sidoruk, T., Dembinski, P., and
Mazurkiewicz, A. W. (2020). Towards Partial Order
Reductions for Strategic Ability. JAIR, 68:817–850.
Kacprzak, M., Niewiadomski, A., and Penczek, W. (2020).
SAT-Based ATL Satisfiability Checking. In Proceed-
ings of KR’20, pages 539–549.
Kacprzak, M., Niewiadomski, A., and Penczek, W. (2021).
Satisfiability Checking of Strategy Logic with Simple
Goals. In Proceedings of KR’21, pages 400–410.
Kacprzak, M., Niewiadomski, A., Penczek, W., and
Zbrzezny, A. (2023). SMT-Based Satisfiability
Checking of Strategic Metric Temporal Logic. In Pro-
ceedings of ECAI’23, pages 1180–1189. IOS Press.
Klenze, T., Bayless, S., and Hu, A. J. (2016). Fast, Flexible,
and Minimal CTL Synthesis via SMT. In Proceedings
of CAV’16, pages 136–156. Springer.
Knapik, M., André, É., Petrucci, L., Jamroga, W., and
Penczek, W. (2019). Timed ATL: Forget Memory, Just
Count. J. Artif. Intell. Res., 66:197–223.
La Torre, S. and Napoli, M. (2000). A decidable dense
branching-time temporal logic. In Proceedings of FST
TCS 2000, pages 139–150. Springer.
Laroussinie, F., Larsen, K. G., and Weise, C. (1995). From
timed automata to logic - and back. In Proceedings of
MFCS’95, pages 529–539. Springer.
Laroussinie, F., Markey, N., and Oreiby, G. (2006). Model-
Checking Timed ATL for Durational Concurrent
Game Structures. In Proceedings of FORMATS’06,
pages 245–259. Springer.
Laroussinie, F., Markey, N., and Schnoebelen, P. (2004).
Model Checking Timed Automata with One or Two
Clocks. In Proceedings of CONCUR’04, pages 387–
401. Springer.
Lomuscio, A., Penczek, W., and Qu, H. (2010). Par-
tial Order Reductions for Model Checking Temporal-
Epistemic Logics over Interleaved Multi-Agent Sys-
tems. Fundam. Informaticae, 101(1-2):71–90.
Lomuscio, A. and Raimondi, F. (2006). Model Check-
ing Knowledge, Strategies, and Games in Multi-Agent
Systems. In Proceedings of AAMAS’06, pages 161–
168. ACM.
Meseguer, J. (1992). Conditional Rewriting Logic as a Uni-
fied Model of Concurrency. Theoretical Computer
Science, 96(1):73–155.
Meseguer, J. (2012). Twenty Years of Rewriting Logic.
Journal of Logic and Algebraic Programming, 81(7-
8):721–781.
Niewiadomski, A., Kacprzak, M., Kurpiewski, D., Knapik,
M., Penczek, W., and Jamroga, W. (2020). MsATL: A
Tool for SAT-Based ATL Satisfiability Checking. In
Proceedings of AAMAS’20, pages 2111–2113. IFAA-
MAS.
Penczek, W. and Pólrola, A. (2006). Advances in Verifica-
tion of Time Petri Nets and Timed Automata: A Tem-
poral Logic Approach. Springer.
Petrucci, L., Knapik, M., Penczek, W., and Sidoruk, T.
(2019). Squeezing State Spaces of ADTrees. In Pro-
ceedings of ICECCS 2019, pages 71–80. IEEE.
Schobbens, P. Y. (2004). Alternating-Time Logic with Im-
perfect Recall. In Proceedings of LCMAS’03, pages
1–12.
Satisfiability Checking for (Strategic) Timed CTL Using IMITATOR
155
