
Stacked Ensemble Deep Learning for Robust Intrusion Detection in IoT
Networks
Marwa Amara
1,2 a
, Nadia Smairi
2
and Mohamed Jaballah
2
1
Depatment of Computer Sciences, Faculty of Sciences, Northern Border University, Arar, Saudi Arabia
2
LARIA UR22ES01, ENSI, Manouba University, Tunisia
Keywords:
Stacked Ensemble Model, Class Imbalance, CICIDS2017 Dataset, Cyber Threat Detection.
Abstract:
Intrusion Detection Systems (IDS) are critical for addressing the growing complexity of cyber threats in the
Internet of Things (IoT) domain. This paper introduces a novel stacked ensemble approach combining Convo-
lutional Neural Networks (CNN), Temporal Convolutional Networks (TCN), and Long Short-Term Memory
(LSTM) models through a logistic regression meta-model. The proposed approach leverages the distinct
strengths of each classifier; sequential pattern recognition by LSTMs, temporal dependency modeling by
TCNs, and spatial feature extraction by CNNs to create a robust and reliable detection framework. To address
the class imbalance problem, we applied various balancing techniques, including Oversampling, Undersam-
pling, and a hybrid Meet-in-the-Middle method. The effectiveness of the approach is demonstrated on the
CICIDS2017 dataset, achieving an accuracy of 99.99% and an F1-score of 100% with Oversampling, and
99.93% accuracy with the Meet-in-the-Middle technique.
1 INTRODUCTION
In the rapidly evolving domain of cybersecurity, IDS
play a pivotal role in safeguarding networks against
unauthorized access and increasingly sophisticated
cyber threats. Traditional IDS approaches often strug-
gle to adapt to the dynamic and evolving nature of
modern cyber attacks, resulting in reduced effective-
ness in real-world scenarios. To address these chal-
lenges, we introduce a novel ensemble learning-based
approach that combines the strengths of multiple deep
classifiers. Ensemble learning, a technique that inte-
grates multiple learning algorithms, has proven to be
transformative in the field of machine learning (Mo-
hammed and Kora, 2023). By leveraging the diver-
sity of multiple models, ensemble methods achieve
superior prediction accuracy, particularly for com-
plex tasks like intrusion detection. The aggregation
of decision-making processes from various classifiers
enables ensemble models to overcome the limitations
of individual estimators and deliver robust and reli-
able predictions (Mohammed and Kora, 2023).
In this paper, we propose a Stacked Ensem-
ble Deep Learning Approach, which integrates three
powerful deep learning models: CNN, TCN, and
LSTM. Each base classifier captures distinct aspects
of the network traffic data—spatial patterns, temporal
dependencies, and sequential behaviors, respectively.
a
https://orcid.org/0000-0002-4521-0867
These individual predictions are then combined in a
stacked architecture. The logistic regression meta-
model is trained on the meta-features generated by the
base models, combining their predictions to optimize
the final classification performance.
To address the prevalent issue of class imbalance
in intrusion detection datasets, we evaluate three bal-
ancing techniques; Oversampling, Undersampling,
and Meet-in-the-Middle approach. This comprehen-
sive strategy ensures that the model maintains high
generalization performance while reducing the risks
of bias introduced by imbalanced data. The effective-
ness of our proposed model is evaluated using well-
established metrics, including accuracy, precision, re-
call, and F1-score.
The remainder of this paper is structured as fol-
lows: Section 2 offers a thorough examination of ex-
isting research in the field of IDS. In Section 2.1, we
delve into our proposed ensemble model. The evalua-
tion of our model’s performance, is presented in Sec-
tion 3. Finally, Section 4 summarizes our findings .
2 RELATED WORKS
This section explores the utilization of Deep learn-
ing (DL) in intrusion detection, highlighting its piv-
otal role in revolutionizing IDS. DL has demonstrated
remarkable potential in enhancing the accuracy of
1146
Amara, M., Smairi, N. and Jaballah, M.
Stacked Ensemble Deep Learning for Robust Intrusion Detection in IoT Networks.
DOI: 10.5220/0013290700003890
In Proceedings of the 17th International Conference on Agents and Artificial Intelligence (ICAART 2025) - Volume 3, pages 1146-1153
ISBN: 978-989-758-737-5; ISSN: 2184-433X
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)

IDS, providing advanced mechanisms to safeguard
networks against evolving cyber threats.
Recent studies have proposed innovative ap-
proaches to leverage DL for intrusion detection. For
instance, (Vijayanand et al., 2019) introduced an in-
novative attack detection system that leverages DL al-
gorithms to scrutinize smart meter communications.
This system employs a hierarchical arrangement of
multi-layer DL algorithms, enhancing its ability to
accurately pinpoint cyber-attacks. Similarly, (Lee
and Hong, 2020) developed a DL-based algorithm
targeting Dynamic Link Library (DLL) injection at-
tacks in SCADA systems, utilizing Windows API
functions to detect and mitigate such threats. In ad-
dition, (Li and Hedman, 2019) proposed monitor-
ing techniques for detecting irregularities in branch
flows and load deviations, addressing false data injec-
tion (FDI) attacks through a two-pronged detection
method. Focusing on SCADA security, (Aldossary
et al., 2021) employed Bidirectional Long Short-Term
Memory (Bi-LSTM) to effectively detect denial-of-
service (DoS) attacks. Expanding on DL applica-
tions, (Agarwal et al., 2021) combined deep neural
networks (DNNs) with a feature selection-whale opti-
mization algorithm, achieving high accuracy in DDoS
detection. Exploring various algorithms for cyberse-
curity identification, (Ahakonye et al., 2021) found
that decision tree and K-nearest neighbor algorithms
(KNN) yielded satisfactory results in cybersecurity
identification. Advancing the field further, (Farrukh
et al., 2021) proposed a two-tier hierarchical machine
learning model. This model demonstrated a remark-
able 95.44% accuracy in detecting cyber-attacks. It
operates by first distinguishing between normal and
cyberattack modes in its initial layer, thereby stream-
lining the detection process. For Software Defined
Networking ,(Fouladi et al., 2022) offered a DDoS
attack detection and countermeasure technique us-
ing discrete wavelet transform (DWT) and an auto-
encoder neural network. In pursuit of optimal fea-
ture selection for IDS, (Fatani et al., 2021) employed
a swarm intelligence technique alongside an Aquila
optimizer model, yielding reasonable results with a
CNN classifier integrated with a particle swarm op-
timization model(PSO). In a notable contribution to
Smart Grid security, (Diaba and Elmusrati, 2023), de-
veloped a hybrid DL algorithm to enhance the secu-
rity of the Smart Grid against Distributed DoS attacks.
This algorithm integrates the strengths of CNNs and
Gated Recurrent Unit models. Simulation tests using
a cybersecurity dataset from the Canadian Institute of
Cybersecurity showed that this novel algorithm sur-
passes existing IDS , achieving an impressive overall
accuracy rate of 99.7%.
Reflecting on the diverse approaches in cyberse-
curity, various researchers have proposed DL mod-
els for intrusion detection, each with distinct findings
and limitations. (Alzughaibi and El Khediri, 2023)
developed a DNN using Backpropagation, trained on
the CSE-CICIDS2018 dataset, and achieved 98.41%
accuracy in multiclass classification. However, the
model’s validation was limited to a single dataset,
raising questions about its broader applicability. Ad-
ditionally, the study did not address training and vali-
dation times, which are crucial for further research.
Similarly, (Thakkar and Lohiya, 2023) also pro-
posed a Deep neural network (DNN), training it
on NSL-KDD, UNSWNB-15, and CIC-IDS-2017
datasets. The model achieved accuracies of 99.84%,
89.03%, and 99.80%, respectively. Despite its high
detection rate, the model’s training time was lengthy,
and validation time was not reported.
Addressing the need for more current and com-
prehensive dataset validation, (Sharma et al., 2023)
presented a DNN trained on the NSL-KDD dataset,
attaining a 99.3% accuracy rate. However, the model
lacked validation with newer and larger datasets, and
the study did not provide information on training and
validation durations.
Innovating in model optimization, (El-Ghamry
et al., 2023) introduced an optimized CNN model,
VGG16-PSO, for intrusion detection, trained and val-
idated using the NSL-KDD dataset. While the model
showed excellent performance, it was evaluated using
a dataset over two decades old, and the study did not
disclose the time consumed for training and valida-
tion.
(Wu and Chen, 2023) proposed a simple DNN
that achieved a 97% accuracy rate. The validation
of this model was restricted to the CSE-CICIDS2018
dataset, and the study omitted details on training and
inference times.
Likewise, (Hnamte et al., 2023) proposed an
LSTM-AE model, trained and validated using CI-
CIDS2017 and CSE-CICIDS2018, achieving 99.99%
and 99.10% accuracy, respectively. The training time
for the model was lengthy and required high-end com-
puting for larger datasets. Continuing the trend of
model innovation, (Chanu et al., 2023) developed
an MLP-GA model that achieved a 98.9% detec-
tion accuracy rate. However, the model’s validation
was limited to the CICIDS2017 dataset, and its ac-
curacy decreased when validated with newer, larger
datasets. In contrast, (Hnamte and Hussain, 2023a),
a DC-NNBiLSTM model was proposed and trained
on CICIDS2018 and EDGEIIoT 2 datasets, achieving
100% and 99.64% accuracy, respectively. The model
was also compared with other models in terms of ac-
Stacked Ensemble Deep Learning for Robust Intrusion Detection in IoT Networks
1147
curacy, loss rate, training time, and inference time,
both on CPU and GPU. Despite its high accuracy, the
model was complex and had a lengthy training dura-
tion.
In a significant breakthrough, (Hnamte and Hus-
sain, 2023b). developed an intrusion detection frame-
work leveraging deep CNNs. Trained on extensive
datasets, the DCNN model achieves detection accu-
racy levels between 99.79% and 100%. Its effective-
ness is validated using four distinct IDS datasets, in-
cluding ISCX-IDS 2012 and CICIDS2018.
Similarly, (Patthi et al., 2024) introduced a
two-layer classification model combining KNN and
SVMs. The first layer categorizes data into Nor-
mal, Major, and Minor Attack groups, while the sec-
ond layer further classifies Major and Minor Attacks.
Tested on the NSL-KDD dataset, the model notably
excels in detecting Minor Attacks.
Addressing IoT networks’ vulnerability, (Latif
et al., 2024) proposed a DL model for intrusion detec-
tion, tested on NSL-KDD and UNSW-NB 15 datasets,
demonstrating superior accuracy. This study incorpo-
rated explainable AI techniques like LIME and SHAP
for model interpretability.
In the context of the Smart Healthcare System and
IoMT, (Alzubi et al., 2024) introduced a novel IDS
solution employing a DL framework that combines
CNN and LSTM, tested on the CSE-CIC-IDS 2018
dataset, and demonstrated superior accuracy com-
pared to existing methods.
While these works highlight the transformative
potential of DL in IDS, several critical gaps per-
sist. First, many studies focus on individual DL ar-
chitectures, limiting their ability to fully capture the
diverse patterns in network traffic, such as spatial,
temporal, and sequential dependencies. This lack
of synergy between different DL architectures often
results in suboptimal performance, particularly for
complex attack scenarios. Second, much of the ex-
isting research overlooks the challenge of unbalanced
datasets, which are common in intrusion detection
scenarios. This neglect raises concerns about model
robustness and the ability to generalize effectively to
real-world data distributions.
Our proposed stacked ensemble approach directly
addresses these challenges by integrating three mod-
els into a unified framework. Our method provides
a holistic analysis of network traffic, significantly
enhancing detection accuracy. Moreover, the inclu-
sion of balancing techniques, such as Oversampling,
Undersampling, and the Meet-in-the-Middle method,
further strengthens the model’s ability to handle im-
balanced data, a common challenge in IDS.
2.1 Proposed Approach
In addressing the complexities of IoT intrusion detec-
tion, our approach utilizes a stacked ensemble model
to integrate multiple DL models, each designed to
capture unique patterns within network traffic data.
By combining the spatial feature recognition capabil-
ities of a CNN,TCN, and the sequential pattern anal-
ysis of LSTM, our method ensures a comprehensive
understanding of both benign and malicious traffic.
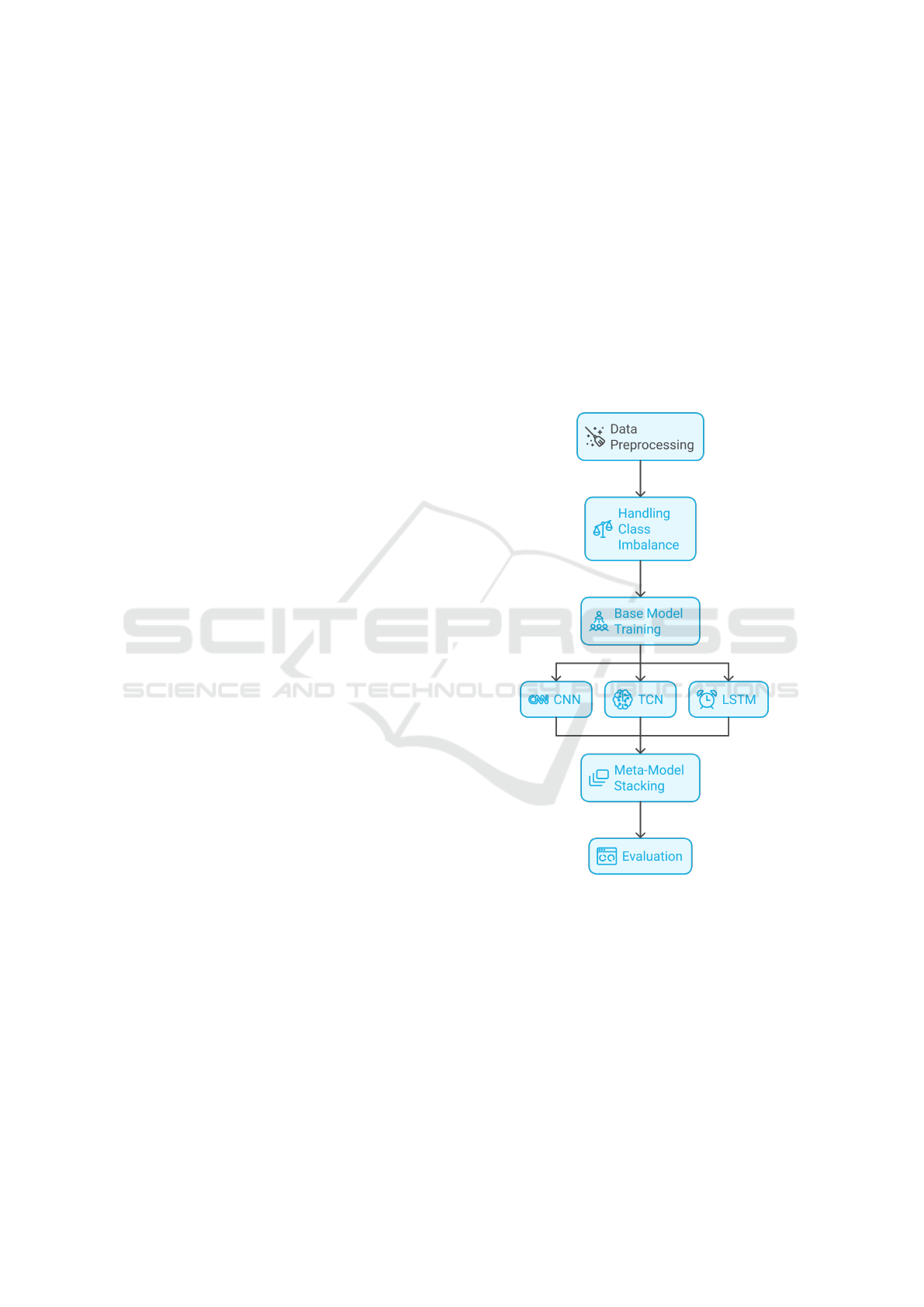
This ensemble approach, visualized in Figure 1, al-
lows each base model to contribute distinct insights,
which are then optimized through a meta-model for
enhanced accuracy.
Figure 1: Stacked Ensemble Model Architecture for IoT
Intrusion Detection.
Such a layered strategy enables the system to
adapt to diverse IoT traffic behaviors, resulting in
more reliable and balanced classification. The algo-
rithm 1 outlines the steps of our stacked ensemble ap-
proach for IoT intrusion detection.
This algorithm is followed by a detailed break-
down of each component, highlighting the importance
of base models, the construction of the meta-feature
matrix, and the role of the meta-model in refining
classification accuracy.
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
1148
Data: Balanced IoT dataset D after
preprocessing
Result: Final classification ˆy of traffic as
benign or malicious
Step 1: Train Base Models
for each base model
M
i
∈ {CNN, TCN, LSTM} do
Train M
i
on D
train
;
Obtain predictions ˆy
M
i
for each sample in
D
train
;
end
Step 2: Construct Meta-Feature Matrix
Combine ˆy
CNN
, ˆy
TCN
, ˆy
LSTM
into meta-feature
matrix F;
Step 3: Train Meta-Model
Train logistic regression (LR) on F to learn
optimal weights for { ˆy
M
i
};
Step 4: Evaluate Stacked Model
for each sample x
j
in D
test
do
Obtain final classification ˆy
j
= LR(F
j
);
Calculate evaluation metrics: Accuracy,
Precision, Recall, F1-Score;
end
Output: Final classifications { ˆy
j
} for all
samples in D
test
;
Algorithm 1: Stacked Ensemble Model for IoT Intrusion
Detection.
2.1.1 Data Preprocessing
In IoT-based intrusion detection, preparing the data is
essential for reliable performance of machine learn-
ing classifiers. Raw network traffic data often in-
cludes inconsistencies such as missing values, infini-
ties, duplicates, and features that provide no useful in-
formation. These issues can interfere with a model’s
ability to correctly identify attacks, so an effective
preprocessing process is critical to create streamlined
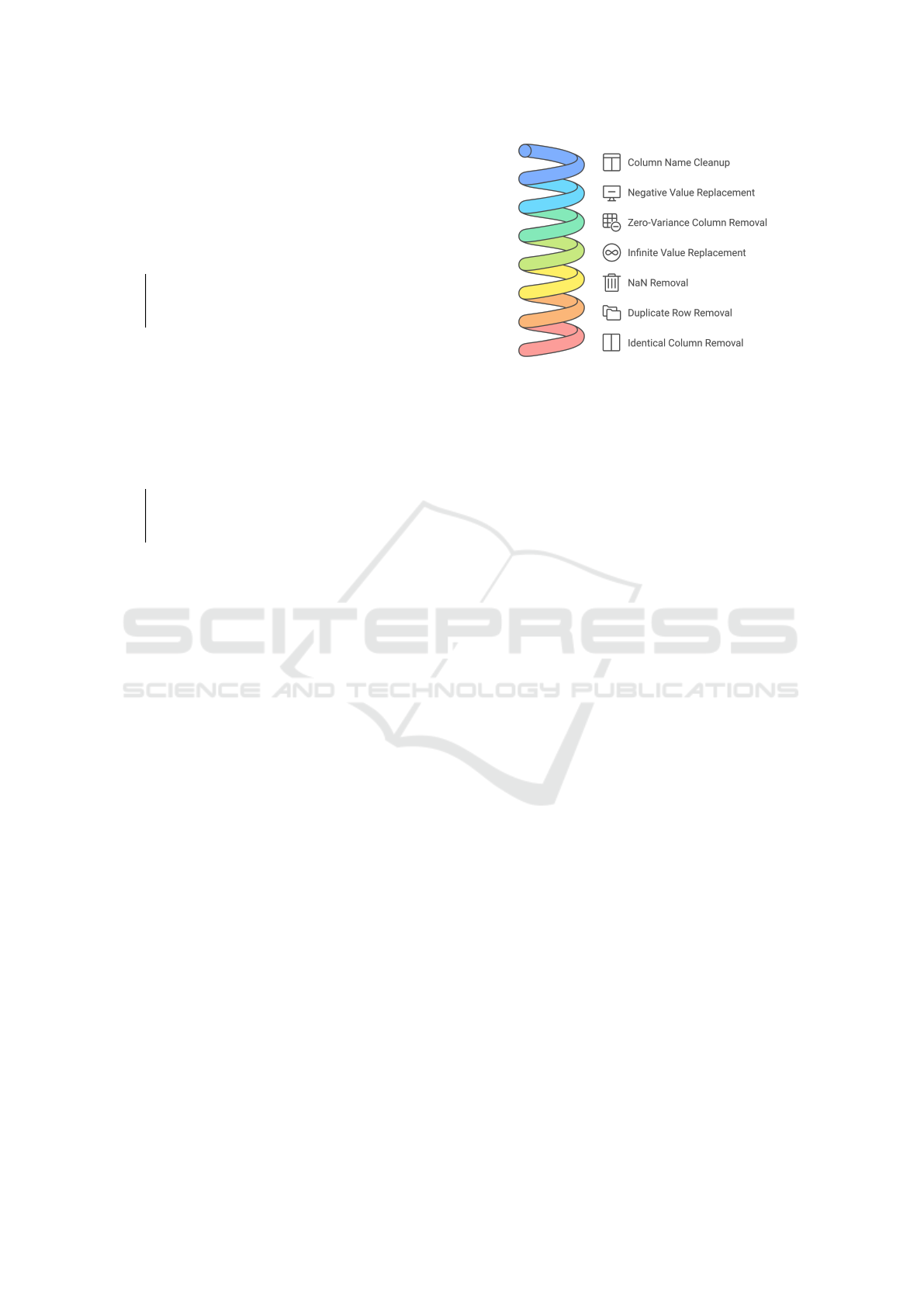
dataset. The figure 2 summarizes the cleaning steps in
the pre-processing phase, which ultimately improves
model performance and robustness in distinguishing
between benign and malicious IoT traffic.
The preprocessing procedure begins by standard-
izing column names by stripping extra spaces for con-
sistency. Negative values are replaced with zero to
maintain logical bounds. Duplicate rows are removed
to ensure the dataset is free from repetitive informa-
tion. Columns with zero variance(those containing
the same value for every record) are also eliminated,
as they add no value to the learning process and can
unnecessarily increase computational overhead. In-
finite values, which can disrupt calculations, are re-
placed with NaNs, and rows containing NaNs are re-
moved to ensure a complete dataset. Finally, identi-
Figure 2: Data Preprocessing for Attack Detection.
cal columns are eliminated to streamline the data and
improve efficiency. The result of this preprocessing
phase is a simplified and consistent dataset, prepared
for feature selection and classifier training. This care-
ful preparation helps improve the model’s ability to
detect intrusions accurately by allowing it to focus on
meaningful patterns in the data.
2.2 Data Imbalance Handling
In IoT intrusion detection, class imbalance is a preva-
lent issue, with benign traffic often significantly out-
numbering malicious samples. To handle this chal-
lenge, we tested multiple resampling techniques , in-
cluding the oversampling, undersampling, and meet-
in-the-middle approach. Each technique provides a
unique way to balance the classes (Islam and Mustafa,
2023), and we evaluated each method to identify the
most effective approach for our dataset. To ensure the
integrity of the evaluation, the dataset was split into
80% training data and 20% test data, with all resam-
pling techniques applied exclusively to the training
data to prevent data leakage into the test set. Over-
sampling duplicates instances from the minority class
(malicious traffic) until its size matches that of the
majority class (benign traffic), resulting in equal rep-
resentation of both classes in the training data. This
method can be represented mathematically as:
N
′
minority
= N
majority
(1)
where N
′
minority
is the new size of the minority class
after oversampling, and N
majority
is the size of the ma-
jority class. Undersampling, in contrast, reduces the
size of the majority class by randomly selecting a sub-
set of instances, equalizing it with the minority class.
This technique is represented as:
N
′
majority
= N
minority
(2)
where N
′
majority
is the new size of the majority class,
which helps prevent the model from favoring the ma-
Stacked Ensemble Deep Learning for Robust Intrusion Detection in IoT Networks
1149

jority class, though it results in a smaller, balanced
dataset.
Finally, we implemented a custom approach
called meet-in-the-middle, which balances the classes
by finding a midpoint between the sizes of the major-
ity and minority classes. This method involves under-
sampling the majority class to the midpoint size and
oversampling the minority class to match this size,
avoiding excessive duplication or data loss. The mid-
point M is calculated as:
M =
N
majority
+ N
minority
2
(3)
where M is the target class size after resampling, and
N
majority
and N
minority
represent the original sizes of
the majority and minority classes, respectively.
Each resampling technique was evaluated based
on key metrics, including accuracy, precision, re-
call, and F1-score. By comparing these metrics, we
identified the most effective technique, enhancing the
model’s ability to distinguish effectively between be-
nign and malicious traffic.
2.3 Base Models and Stacking
Ensemble Approach
Our methodology leverages a stacked ensemble ap-
proach using three DL base models; CNN, TCN, and
LSTM, to capture diverse aspects of IoT data patterns.
Each model is trained on resampled datasets, enabling
the ensemble to harness unique feature representa-
tions for improved performance in detecting network
anomalies.
The CNN model extracts local feature patterns
from the data, detecting specific types of network traf-
fic anomalies. Mathematically, the convolutional op-
eration in a CNN is given by:
h
i j
= f
M
∑
m=1
w
m
x
i+m−1, j
+ b
!
(4)
where h
i j
represents the output feature map, w
m
is
the convolutional kernel, x
i+m−1, j
represents the input
data, and b is the bias term. The CNN’s hierarchical
spatial properties allow it to identify patterns in high-
dimensional network traffic data effectively.
The TCN model, which incorporates dilated con-
volutions, captures long-range dependencies in se-
quential IoT data. This allows the TCN to recognize
temporal patterns across extended periods, which is
valuable for network traffic analysis. The dilated con-
volution in a TCN is mathematically expressed as:
y(t) =
K−1
∑
k=0
w
k
x(t − d · k) (5)
where y(t) is the output at time t, w
k
are the filter
weights, x(t −d ·k) is the input at the dilated time step,
and d is the dilation factor. By adjusting d, the TCN
can capture dependencies across various time spans.
The LSTM model, known for its memory cell and
gating mechanisms, captures sequential dependencies
in the network traffic, effectively recognizing tempo-
ral patterns present in IoT traffic. The LSTM cell up-
dates are formulated as:
c
t
= f
t
⊙ c
t−1
+ i
t
⊙ ˜c
t
(6)
where c
t
is the cell state at time t, f
t
, i
t
, and ˜c
t
are the
forget, input, and candidate cell states, respectively,
and ⊙ denotes element-wise multiplication. This up-
date mechanism allows the LSTM to retain informa-
tion over long sequences, making it effective for se-
quential data like network traffic.
Each of these base models is trained indepen-
dently on resampled versions of the dataset. Their
outputs, representing predictions for each input in-
stance, form a matrix of meta-features, F ∈ R
n×m
,
where n is the number of samples and m is the number
of base models. Let f
i
(X) denote the prediction from
the i-th base model for input X, then:
F =
f
1
(X
1
) f
2
(X
1
) . . . f
m
(X
1
)
f
1
(X
2
) f
2
(X
2
) . . . f
m
(X
2
)
.
.
.
.
.
.
.
.
.
.
.
.
f
1
(X
n
) f
2
(X
n
) . . . f
m
(X
n
)
(7)
The meta-feature matrix F is then used to train
a Logistic Regression model, g(F), which serves as
the meta-model. The logistic regression learns a
weighted combination of the base models’ predictions
to yield a final classification decision. Mathemati-
cally, the meta-model’s prediction ˆy is:
ˆy = g(F) = σ
m
∑
j=1
α
j
f
j
(X) + β
!
(8)
where σ is the logistic sigmoid function, α
j
are the
learned weights for each base model’s predictions,
and β is the bias term.
By combining predictions from each base model,
the meta-model leverages their complementary
strengths, resulting in improved overall performance.
This stacked ensemble approach enhances classifica-
tion robustness, as each model contributes unique in-
sights into the data. The CNN captures local spa-
tial patterns, the TCN detects long-term dependen-
cies, and the LSTM captures sequential patterns. The
meta-model effectively integrates these diverse repre-
sentations, leading to more accurate and reliable in-
trusion detection.
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
1150
3 EXPERIMENTAL RESULTS
In this section, we evaluate the performance of the
proposed stacked ensemble model across different
class balancing techniques: Oversampling, Under-
sampling, and Meet-in-the-Middle.
3.1 Dataset Description
The CICIDS2017 dataset (Sharafaldin et al., 2018), a
benchmark for intrusion detection, was used for our
experiments. The dataset includes network traffic la-
beled as normal or one of several types of attacks. For
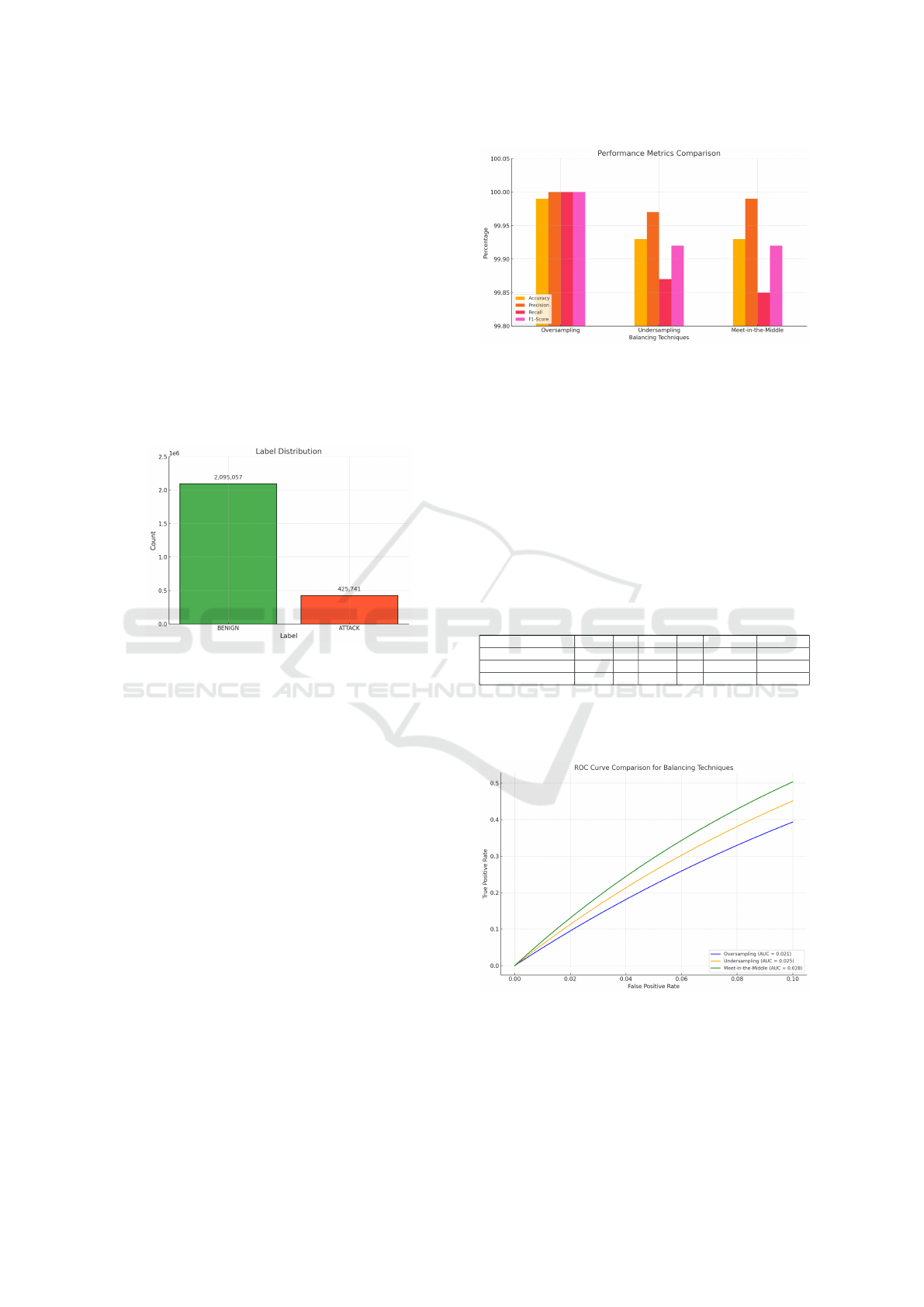
binary classification (Figure 3), all attack types were
grouped under a single ’anomaly’ label, while normal
traffic was labeled ’benign’.
Figure 3: Class Distribution of the CICIDS2017 Dataset .
This study focuses on traffic patterns and anoma-
lies observed on Friday, a subset of the dataset that
captures both routine network behavior and complex
intrusion scenarios. Preprocessing steps, including
handling missing values, feature scaling, and dataset
balancing, were applied to prepare the data for robust
training and evaluation.
3.2 Stacked Model Performance
The stacked ensemble model, combining CNN, TCN,
and LSTM predictions through a logistic regression
meta-model, significantly improves classification per-
formance. By leveraging the strengths of each base
model; spatial features from CNN, temporal de-
pendencies from TCN, and sequential patterns from
LSTM, the stacked model achieves near-perfect clas-
sification metrics. Across all balancing techniques,
the stacked model demonstrates strong performance,
with accuracy exceeding 99.9% and minimal mis-
classifications, as shown in Figure 4. These results
confirm the effectiveness of the stacked ensemble
approach, particularly in maintaining high precision
and recall even under challenging conditions such as
imbalanced data. To further evaluate the balancing
Figure 4: Performance Metrics Comparison Across Balanc-
ing Techniques.
techniques, we analyze the confusion matrices, ROC
curves, and precision-recall metrics for each method.
Table 1 presents the True Positive Rate (TPR),
False Positive Rate (FPR), and key confusion matrix
values for each balancing technique. While Oversam-
pling achieves perfect classification (TPR = 100%,
FPR = 0%), the Meet-in-the-Middle approach pro-
vides a highly balanced performance with the lowest
FPR of 0.004%, demonstrating its robustness in han-
dling class imbalance.
Table 1: Confusion Matrix Metrics for Balancing Tech-
niques.
Technique TP FP TN FN TPR (%) FPR (%)
Oversampling 18201 0 24555 0 100.00 0.00
Undersampling 18177 5 24550 24 99.87 0.02
Meet-in-the-Middle 18174 1 24554 27 99.85 0.004
The ROC curves in Figure 5 compare the perfor-
mance of the stacked model across the three balancing
techniques.
Figure 5: ROC Curves Comparing Balancing Techniques.
The ROC curves in Figure 5 illustrate the perfor-
mance of the stacked model across the three balanc-
ing techniques. The Area Under the Curve (AUC)
quantifies the overall performance of a model by sum-
marizing the trade-off between TPR (sensitivity) and
Stacked Ensemble Deep Learning for Robust Intrusion Detection in IoT Networks
1151

FPR across all thresholds. Mathematically, it is com-
puted as:
AUC =
Z
1
0
TPR(t), d(FPR(t)) (9)
AUC values range from 0 to 1, with higher AUCs
indicating better model performance in distinguishing
between classes. Among the evaluated techniques,
the Meet-in-the-Middle approach achieves the high-
est AUC of 0.028, demonstrating the best trade-off
between TPR and FPR and highlighting its robustness
in handling class imbalance under realistic conditions.
While Oversampling (AUC = 0.021) and Undersam-
pling (AUC = 0.025) also perform well, the marginal
advantage of the Meet-in-the-Middle method under-
scores its effectiveness in maintaining generalization
and robust classification.
3.3 Performance Comparison and
Discussion
As a final evaluation of the results presented, we com-
pare our proposed approach with other similar meth-
ods in the literature.
Table 2: Comparison of Our Proposed Stacked Ensemble
Model with Existing Methods in Literature.
Authors Method Ensemble Accuracy (%)
(Kumar et al., 2021b) DLTIF No 99.9
(Latif et al., 2021) DnRaNN No 98.5
(Kumar et al., 2021a) Stacking Yes 96.3
(Khan et al., 2023) Stacking Yes 98.5
(Gad et al., 2022) XGBoost Yes 99.1
Proposed (Oversampling) Stacked Yes 99.99
Proposed (Undersampling) Stacked Yes 99.93
Proposed (Meet-in-the-Middle) Stacked Yes 99.93
Our proposed stacked ensemble model demon-
strates superior performance compared to existing
state of the art methods in IoT intrusion detection,
as shown in Table 2. Traditional approaches, such as
DLTIF and XGBoost, achieve notable accuracy levels
(99.9% and 99.1%, respectively); however, they lack
the synergistic benefits of ensemble techniques. By
combining the strengths of CNN, TCN, and LSTM
models, our proposed stacked approach effectively
captures diverse network traffic patterns, resulting
in improved detection accuracy. Specifically, our
model achieves an accuracy of 99.99% with the Over-
sampling technique, outperforming all previously
reported methods. Additionally, the Meet-in-the-
Middle and Undersampling approaches demonstrate
balanced accuracy levels of 99.93%, providing a ro-
bust trade-off that mitigates overfitting while main-
taining reliable classification performance. These re-
sults underscore the effectiveness of leveraging en-
semble methods to address class imbalance and en-
hance overall intrusion detection accuracy.
4 CONCLUSION
In this paper, we proposed a stacked ensemble model
for IoT intrusion detection, combining the strengths
of CNN, TCN, and LSTM models through a logis-
tic regression meta-model. The approach effectively
addresses the challenges of imbalanced data and cap-
tures diverse data patterns. By employing different
balancing techniques, such as Oversampling, Under-
sampling, and Meet-in-the-Middle, we demonstrated
that the Meet-in-the-Middle approach provides the
best balance between precision and recall. The ro-
bustness and efficiency of the stacked model validate
its suitability for real-world IoT environments, where
high precision and low false positive rates are critical.
While the proposed model excels in binary classi-
fication for a subset of the CICIDS2017 dataset, fu-
ture work will extend the analysis to the entire dataset
for a more comprehensive evaluation. Additionally,
multiclass classification and advanced techniques like
ablation studies and cross-dataset domain adaptation
will be explored to validate and enhance the model’s
generalizability.
REFERENCES
Agarwal, A., Khari, M., and Singh, R. (2021). Detection of
ddos attack using deep learning model in cloud stor-
age application. Wireless Personal Communications,
pages 1–21.
Ahakonye, L. A. C., Nwakanma, C. I., Lee, J.-M., and Kim,
D.-S. (2021). Efficient classification of enciphered
scada network traffic in smart factory using decision
tree algorithm. IEEE Access, 9:154892–154901.
Aldossary, L. A., Ali, M., and Alasaadi, A. (2021). Secur-
ing scada systems against cyber-attacks using artificial
intelligence. In 2021 international conference on in-
novation and intelligence for informatics, computing,
and technologies (3ICT), pages 739–745. IEEE.
Alzubi, J. A., Alzubi, O. A., Qiqieh, I., and Singh, A.
(2024). A blended deep learning intrusion detection
framework for consumable edge-centric iomt indus-
try. IEEE Transactions on Consumer Electronics.
Alzughaibi, S. and El Khediri, S. (2023). A cloud intrusion
detection systems based on dnn using backpropaga-
tion and pso on the cse-cic-ids2018 dataset. Applied
Sciences, 13(4):2276.
Chanu, U. S., Singh, K. J., and Chanu, Y. J. (2023). A
dynamic feature selection technique to detect ddos at-
tack. Journal of Information Security and Applica-
tions, 74:103445.
ICAART 2025 - 17th International Conference on Agents and Artificial Intelligence
1152

Diaba, S. Y. and Elmusrati, M. (2023). Proposed algorithm
for smart grid ddos detection based on deep learning.
Neural Networks, 159:175–184.
El-Ghamry, A., Darwish, A., and Hassanien, A. E. (2023).
An optimized cnn-based intrusion detection system
for reducing risks in smart farming. Internet of Things,
22:100709.
Farrukh, Y. A., Ahmad, Z., Khan, I., and Elavarasan, R. M.
(2021). A sequential supervised machine learning
approach for cyber attack detection in a smart grid
system. In 2021 North American Power Symposium
(NAPS), pages 1–6. IEEE.
Fatani, A., Dahou, A., Al-Qaness, M. A., Lu, S., and Elaziz,
M. A. (2021). Advanced feature extraction and se-
lection approach using deep learning and aquila op-
timizer for iot intrusion detection system. Sensors,
22(1):140.
Fouladi, R. F., Ermis¸, O., and Anarim, E. (2022). A ddos
attack detection and countermeasure scheme based on
dwt and auto-encoder neural network for sdn. Com-
puter Networks, 214:109140.
Gad, A. R., Haggag, M., Nashat, A. A., and Barakat, T. M.
(2022). A distributed intrusion detection system us-
ing machine learning for iot based on ton-iot dataset.
International Journal of Advanced Computer Science
and Applications, 13(6).
Hnamte, V. and Hussain, J. (2023a). Dcnnbilstm: An
efficient hybrid deep learning-based intrusion detec-
tion system. Telematics and Informatics Reports,
10:100053.
Hnamte, V. and Hussain, J. (2023b). Dependable intrusion
detection system using deep convolutional neural net-
work: A novel framework and performance evalua-
tion approach. Telematics and Informatics Reports,
11:100077.
Hnamte, V., Nhung-Nguyen, H., Hussain, J., and Hwa-Kim,
Y. (2023). A novel two-stage deep learning model for
network intrusion detection: Lstm-ae. IEEE Access.
Islam, M. T. and Mustafa, H. A. (2023). Multi-layer hybrid
(mlh) balancing technique: A combined approach to
remove data imbalance. Data & Knowledge Engineer-
ing, 143:102105.
Khan, F., Jan, M. A., Alturki, R., Alshehri, M. D., Shah,
S. T., and ur Rehman, A. (2023). A secure ensemble
learning-based fog-cloud approach for cyberattack de-
tection in iomt. IEEE Transactions on Industrial In-
formatics, 19(10):10125–10132.
Kumar, P., Gupta, G. P., and Tripathi, R. (2021a). An
ensemble learning and fog-cloud architecture-driven
cyber-attack detection framework for iomt networks.
Computer Communications, 166:110–124.
Kumar, P., Gupta, G. P., Tripathi, R., Garg, S., and Has-
san, M. M. (2021b). Dltif: Deep learning-driven cyber
threat intelligence modeling and identification frame-
work in iot-enabled maritime transportation systems.
IEEE Transactions on Intelligent Transportation Sys-
tems, 24(2):2472–2481.
Latif, S., Boulila, W., Koubaa, A., Zou, Z., and Ahmad,
J. (2024). Dtl-ids: An optimized intrusion detection
framework using deep transfer learning and genetic
algorithm. Journal of Network and Computer Appli-
cations, 221:103784.
Latif, S., e Huma, Z., Jamal, S. S., Ahmed, F., Ahmad, J.,
Zahid, A., Dashtipour, K., Aftab, M. U., Ahmad, M.,
and Abbasi, Q. H. (2021). Intrusion detection frame-
work for the internet of things using a dense random
neural network. IEEE Transactions on Industrial In-
formatics, 18(9):6435–6444.
Lee, J.-M. and Hong, S. (2020). Keeping host sanity for
security of the scada systems. IEEE Access, 8:62954–
62968.
Li, X. and Hedman, K. W. (2019). Enhancing power sys-
tem cyber-security with systematic two-stage detec-
tion strategy. IEEE Transactions on Power Systems,
35(2):1549–1561.
Mohammed, A. and Kora, R. (2023). A comprehen-
sive review on ensemble deep learning: Opportuni-
ties and challenges. Journal of King Saud University-
Computer and Information Sciences.
Patthi, S., Singh, S., et al. (2024). 2-layer classification
model with correlated common feature selection for
intrusion detection system in networks. Multimedia
Tools and Applications, pages 1–26.
Sharafaldin, I., Lashkari, A. H., Ghorbani, A. A., et al.
(2018). Toward generating a new intrusion detection
dataset and intrusion traffic characterization. ICISSp,
1:108–116.
Sharma, B., Sharma, L., and Lal, C. (2023). Anomaly-based
dnn model for intrusion detection in iot and model ex-
planation: Explainable artificial intelligence. In Pro-
ceedings of Second International Conference on Com-
putational Electronics for Wireless Communications:
ICCWC 2022, pages 315–324. Springer.
Thakkar, A. and Lohiya, R. (2023). Fusion of statistical im-
portance for feature selection in deep neural network-
based intrusion detection system. Information Fusion,
90:353–363.
Vijayanand, R., Devaraj, D., and Kannapiran, B. (2019).
A novel deep learning based intrusion detection sys-
tem for smart meter communication network. In 2019
IEEE International Conference on Intelligent Tech-
niques in Control, Optimization and Signal Process-
ing (INCOS), pages 1–3. IEEE.
Wu, C.-s. and Chen, S. (2023). A heuristic intrusion de-
tection approach using deep learning model. In 2023
International Conference on Information Networking
(ICOIN), pages 438–442. IEEE.
Stacked Ensemble Deep Learning for Robust Intrusion Detection in IoT Networks
1153
