
AADT: Asset-Driven Attack-Defense Tree
Nan Messe
1 a
and Avi Shaked
2 b
1
IRIT, CNRS, UT2, France
2
Department of Computer Science, University of Oxford, Oxford, OX1 3QD, U.K.
Keywords:
Attack Tree, Risk Management, Security Modelling and Assessment, Usable Security.
Abstract:
Attack trees are widely used in threat modelling and risk analysis to describe threats and identify attacks that
realize them. Their extension, attack-defense trees, allows for depicting interactions between attackers and
defenders. However, current graphical representations of attack(-defense) trees focus primarily on threat sce-
narios and do not account for the representation of domain elements and their hierarchical organization. Com-
promised domain elements (e.g., systems, sub-systems, components, etc.) are thus not directly highlighted in
any of these tree representations, which requires additional effort from decision-makers during impact anal-
ysis. To help make impact analysis more explicit and enable stakeholders to assign and evaluate security
controls more effectively, we propose a novel methodology for graphical secure system modelling and as-
sessment, the “Asset-Driven Attack-Defense Tree” (AADT). AADT is an extension of the attack-defense tree,
combining the security and system views for seamless secure system development. AADT’s main contribution
lies in bridging the system and security views while representing domain elements, associated vulnerabilities,
and security controls at different levels of abstraction, which is aligned with the system development lifecy-
cle. This layered representation is especially useful in the fast-evolving cyber threat landscape, where diverse
attack techniques often exploit similar vulnerabilities. By associating vulnerability categories with domain
elements and proposing high-level security controls, AADT helps stakeholders manage a broad spectrum of
attacks targeting similar vulnerabilities, thus enabling a more proactive and structured approach to secure sys-
tem development. We also present a formalism for AADT and illustrate the AADT methodology using a
simple, real-world scenario based on the existing security body of knowledge.
1 INTRODUCTION
Establishing the security of systems is a dynamic
and ongoing effort. The number of cyberattacks
grows, the attackers are active and attack techniques
are sophisticated and diverse. This is exacerbated in
times of stressful, real-world events, such as the war
in Ukraine and the COVID-19 pandemic (Ramadan
et al., 2021). The constant stream of data breaches
and harmful cyberattacks has demonstrated that at-
tack intensity and sophistication will only increase in
the future. Attack tree (Schneier, 1999) is a concep-
tual representation that is widely used for securing
systems. It provides a systematic way of characteriz-
ing diverse system threats and attack scenarios (Gady-
atskaya and Trujillo-Rasua, 2017).
Typically, an attack tree design activity necessi-
tates both system domain expertise and security ex-
a
https://orcid.org/0000-0002-3766-0710
b
https://orcid.org/0000-0001-7976-1942
pertise, with the former providing in-depth knowl-
edge of the system and the latter offering secu-
rity knowledge and experience (Gadyatskaya and
Trujillo-Rasua, 2017). However, current graphical
representations of an attack tree focus primarily on
threat scenarios. They do not account for the rep-
resentation of domain elements and their hierarchi-
cal organization. In addition, the standard approach
for attack trees, in which only leaf nodes are anno-
tated with values, can be restrictive, as information for
intermediate nodes are often more readily available
than that of the leaf nodes (Gadyatskaya and Trujillo-
Rasua, 2017).
Attack-defense tree is an extension of attack
tree (Kordy et al., 2014). It allows nodes that repre-
sent defensive measures to appear as leaf nodes of the
tree. This is useful for depicting interactions between
attackers and defenders. However, how can one be
certain that a defensive measure implemented today
will still be effective in the future? How can newly
Messe, N. and Shaked, A.
AADT: Asset-Driven Attack-Defense Tree.
DOI: 10.5220/0013310100003928
In Proceedings of the 20th International Conference on Evaluation of Novel Approaches to Software Engineer ing (ENASE 2025), pages 565-572
ISBN: 978-989-758-742-9; ISSN: 2184-4895
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
565

discovered attacks and defenses be documented in a
systematic and efficient manner? More importantly,
how can stakeholders assign and evaluate the effec-
tiveness of security controls in system designs and
threat scenarios?
To answer these questions, we propose an ex-
tension of attack-defense tree, termed Asset-Driven
Attack-Defense Tree (AADT). This extension in-
cludes information about systems’ assets and their
vulnerabilities, in addition to attack activities and de-
fensive measures. AADT highlights compromised
and protected assets, making impact analysis more
concrete for decision makers.
This paper is structured as follows. In Section 2
we review related work about attack tree, its com-
mon extensions and its integration with risk manage-
ment. In Section 3, we introduce AADT, formalize
AADT and illustrate its graphical representation. A
case study is described in Section 4. In Section 5, we
discuss the significance of our work and future work.
Finally, we conclude this paper in Section 6.
2 RELATED WORK
In this section, related works about attack tree, its ex-
tensions and its integration with risk management are
reviewed.
2.1 Attack Trees
Attack trees allow structuring diverse threat scenarios
and reasoning about these scenarios at different lev-
els of abstraction (Gadyatskaya and Trujillo-Rasua,
2017). It was originally proposed by Bruce Schneier
in 1999 (Schneier, 1999). The security community
uses attack trees to model threat scenarios in various
domains, such as Automated Teller Machines (Fraile
et al., 2016), Supervisory Control and Data Acqui-
sition systems (Nielsen, 2011) (Ten et al., 2007)
and Radio Frequency Identification systems (Bagnato
et al., 2012).
In an attack tree, the final goal of an attacker is
represented by the root of the tree, which is subse-
quently refined and decomposed into sub-goals cap-
tured by child nodes. The actions that can be directly
executed by the attacker are represented by the leaf
nodes.
Research in attack trees mainly focuses on
improving the expressiveness of the formalism
through new operators. Prominent examples include
adding the sequential-AND operator (Jhawar et al.,
2015) (Arnold et al., 2014), designing various quan-
titative assessment methods to prioritize risks (Bag-
nato et al., 2012) (Mauw and Oostdijk, 2006) (Buldas
et al., 2006) (Kordy et al., 2012) (Gadyatskaya et al.,
2016c) and proposing extensions of attack trees, such
as the ones described in the following subsection.
Furthermore, new attack tree semantics are also
being developed, and support the transformation of
attack trees into other formalisms, such as timed
automata (Kumar et al., 2015) (Gadyatskaya et al.,
2016a), stochastic games (Aslanyan et al., 2016) and
Markov chains (Jhawar et al., 2016). These for-
malisms offer advanced computational capabilities
but they do not address the coordination of attack
trees between security experts, system engineers, risk
managers and other decision makers, which remains
a gap.
2.2 Extending Attack Trees to
Incorporate Defenses
Several attack tree extensions have been proposed
in the literature, to introduce the defenders’ view-
point into attack trees. Prominent extensions in-
clude attack-defense tree (ADTree) (Kordy et al.,
2014) (Fraile et al., 2016), attack response tree
(ART), attack countermeasures tree (ACT) (Roy
et al., 2012a) (Roy et al., 2012b) and attack protec-
tion tree (APT) (Ali and Gruska, 2019).
ADTree (Kordy et al., 2014) provides an intuitive
and visually appealing representation of interactions
between an attacker and a defender of a system. In
ADTree, defense measures – alternately security con-
trols – are only applied to leaf nodes. ACT (Roy
et al., 2012a), on the other hand, extends the defense
tree with countermeasures to mitigate attackers’ ac-
tions, where defenses can be applied to any level of
nodes in the tree. ART extends the attacker-defender
interaction to find an optimal policy from a list of
countermeasures. However, ART is not popular as
it suffers from a state-space explosion problem (Roy,
2010). APT allows to define a set of protection ac-
tions at the point in which the attacker interacts with
the system. It is worth noting that all above exten-
sions do not include the domain aspect – i.e., the do-
main elements and their organizational structure – in
the representation of the tree structure. This omission
necessitates additional effort from system engineers
when integrating the security aspect into the system
development, potentially leading to increased com-
plexity, higher risk of errors, and prolonged develop-
ment times.
ENASE 2025 - 20th International Conference on Evaluation of Novel Approaches to Software Engineering
566

2.3 Integration with Risk Management
Research efforts have also been put into the integra-
tion of attack trees with security risk management
methodologies (Pieters and Davarynejad, 2014) (Paul
and Vignon-Davillier, 2014) (Gadyatskaya et al.,
2016b). The security design process and risk manage-
ment life cycle typically include the following main
phases (Force and Initiative, 2013) (Messe, 2021):
• The identification of the critical assets to be pro-
tected;
• The analysis of vulnerabilities of the identified as-
sets;
• The threats that may exploit these vulnerabilities;
• The prioritization of risks relating to threats, vul-
nerabilities and assets;
• The selection and implementation of the security
controls that are needed to protect the identified
assets;
• The assessment and the monitoring of security
controls in order to verify that they are properly
implemented.
Asset identification is fundamental for the success of
secure system development, since its results directly
influence the subsequent steps in risk management.
The lack of support for asset identification in attack-
tree-based methods hinders the ability of pertinent
stakeholders, namely systems engineers, risk man-
agers and decision makers to evaluate the potential
impact of threats on systems. For example, TRADES
Tool (Shaked, 2023) is a research informed open-
source systems security design and assessment tool,
supporting the security design process and risk man-
agement life cycle. While the tool has recently been
extended to support the analysis of assets with respect
to vulnerabilities (Shaked et al., 2024), it does not of-
fer a graphical representation to communicate the de-
sign between stakeholders and support their decision
making.
3 ASSET-DRIVEN ATTACK
DEFENSE TREE (AADT)
In this section, we first define AADT terminologies
and then formalize them. We then illustrate the graph-
ical representation of AADT.
3.1 Terminology
A vulnerable asset is any asset that has vulnerabilities
that can be exploited by attackers. The exploitable
vulnerabilities make the vulnerable asset valuable to
the attackers, who can use it to compromise a sys-
tem. Previous work has shown that common types
of vulnerable assets can be extracted from widely
used security knowledge bases, such as CAPEC
1
,
CWE
2
, CVE
3
, OWASP
4
, and ATT@CK
5
(Messe
et al., 2020). Attack and mitigation information are
also associated with those extracted vulnerable as-
sets. Vulnerable assets extracted from these knowl-
edge bases are independent of a specific domain and,
thus, reusable. Vulnerable assets that are involved
in domain modelling are annotated as vulnerable do-
main assets.
We define an Asset-Driven Attack-Defense Tree
(AADT) as a node-labelled tree describing three in-
formation items: (i) the attack measures (strategies
and actions) an attacker might employ to compromise
a vulnerable domain asset; (ii) the defense measures
(strategies and actions) that a defender can use to pro-
tect the vulnerable domain asset; and (iii) the vulner-
able domain asset itself. Accordingly, an AADT has
three types of nodes: attack nodes, defense nodes and
vulnerable domain asset nodes. It is worth noting that
non-vulnerable assets are not considered in this paper,
as we deal exclusively with the security aspect.
The purpose of AADT is to model systems to-
gether with attack-defense scenarios. The first two
key features of an AADT are the representation of
refinement and the representation of decomposition.
Each node may have one or more children that either
represent the refinement of the parent node or repre-
sent its decomposition. A leaf-node is defined as a
node that does not have any children.
For attack and defense nodes, the refinement of a
node of an AADT is disjunctive. The goal of a dis-
junctively refined node is achieved when at least one
of its children’s goals is achieved. The decomposi-
tion of a node is conjunctive. The goal of a conjunc-
tively decomposed node is achieved when all of its
children’s goals are achieved.
For vulnerable domain asset nodes, the refinement
of node A into node B means that A is the type or
generalization of B, or B is a specialization of A. The
decomposition from node A into node B means that
A contains B or B is a component of A.
Another key feature of an AADT is the represen-
tation of association, which aims at connecting dif-
ferent types of nodes. Each vulnerable domain asset
node can be associated with attack nodes and defense
1
https://capec.mitre.org/
2
https://cwe.mitre.org/
3
https://cve.mitre.org/
4
https://owasp.org/
5
https://attack.mitre.org/
AADT: Asset-Driven Attack-Defense Tree
567
nodes.
As explained shortly, when drawing an AADT,
we depict vulnerable domain asset nodes by trian-
gles, attack nodes by circles and defense nodes by
rectangles, as shown in Figure 1. Refinement rela-
tions are indicated by solid directional lines between
nodes, and decomposition relations are indicated by
dotted directional lines. Association relations con-
necting different types of nodes are described by solid
non-directional lines.
3.2 AADT Formalism
To formalize AADT, we denote an attacker by A and
a defender by D. We represent the set of measures
that can be employed by the attacker as β, and the
set of defense measures as P. We denote by L = {s
1
,
s
2
, ..., s
n
} the set of vulnerable domain asset nodes
in the tree. The attack measures are defined on the
attack nodes as a function A : L → 2
β
, and defense
measures are associated with nodes to block the attack
measures D : L → 2
P
. This expresses that an attacker
tries to perform attack measure b ∈ A(s) on a given
vulnerable domain asset node s, and that there is a
defense measure assigned by the defender α ∈ D(s)
that will block the malicious activity and protect the
vulnerable domain asset. For simplicity, we denote
this interaction as s
α
b
.
For a vulnerable domain asset node s, if each b ∈
A(s) is associated with a defense measure α ∈ D(s),
then the vulnerable domain asset node is said to be
protected. We denote this as s ⊢ (A, D). For example,
consider a vulnerable domain asset “weak password”
as the root node s
0
∈ L. This asset is subject to the
attack measure “password brute forcing attack” b ∈
β. A defense measure to protect the s against b can
be “implementing a password throttling mechanism”
α ∈ P. The general syntax of AADT is generated by
the following formula:
T = op(s
0
(t(s
1
), t(s
2
), ..., t(s
n
))) (1)
Where T is a tree, op = {OR, AND} is either the re-
finement relation (OR) or the decomposition relation
(AND). Each node except leaf nodes is either AND
or OR node. Each asset node can be associated with
the two other types of nodes. s
0
is the root vulnerable
domain asset node and t(s
i
) is a subtree (alternatively,
an intermediate tree) with the root s
i
. Based on this
syntax, we formalize AADT as follows.
Definition 1. An Asset-Driven Attack-Defense Tree
(AADT) is a tuple T = (L, E, β, P, A, D), where L is
the set of vulnerable domain asset nodes; E is the set
of links between nodes (either refinement, decompo-
sition or association); β, P are the disjoint attack mea-
sures and the defend measures, respectively; A, D rep-
resent the attacker – A : L → 2
β
– and the defender –
D : L → 2
P
– respectively.
The vulnerable domain asset node s
i
∈ L is said to
be secure if ∀b ∈ A(s
i
), ∃α ∈ D(s
i
) : s
α
b
i
. If for each s
i
,
we have s
i
⊢ (A, D), then this means that all vulnerable
domain asset nodes are protected. We denote this as
S ⊢ (A, D).
In the above example of the weak password vul-
nerable domain asset, the attack node “password brute
forcing attack” can be refined by the child attack node
“dictionary-based password attack” b
1
∈ β. Defend-
ers can perform protection measures such as “lever-
aging multifactor authentication” α
1
∈ P to defend
against this attack and protect the vulnerable asset
“word-based password” s
1
∈ L, which is a refinement
of s
0
.
3.3 Graphical Representation of AADT
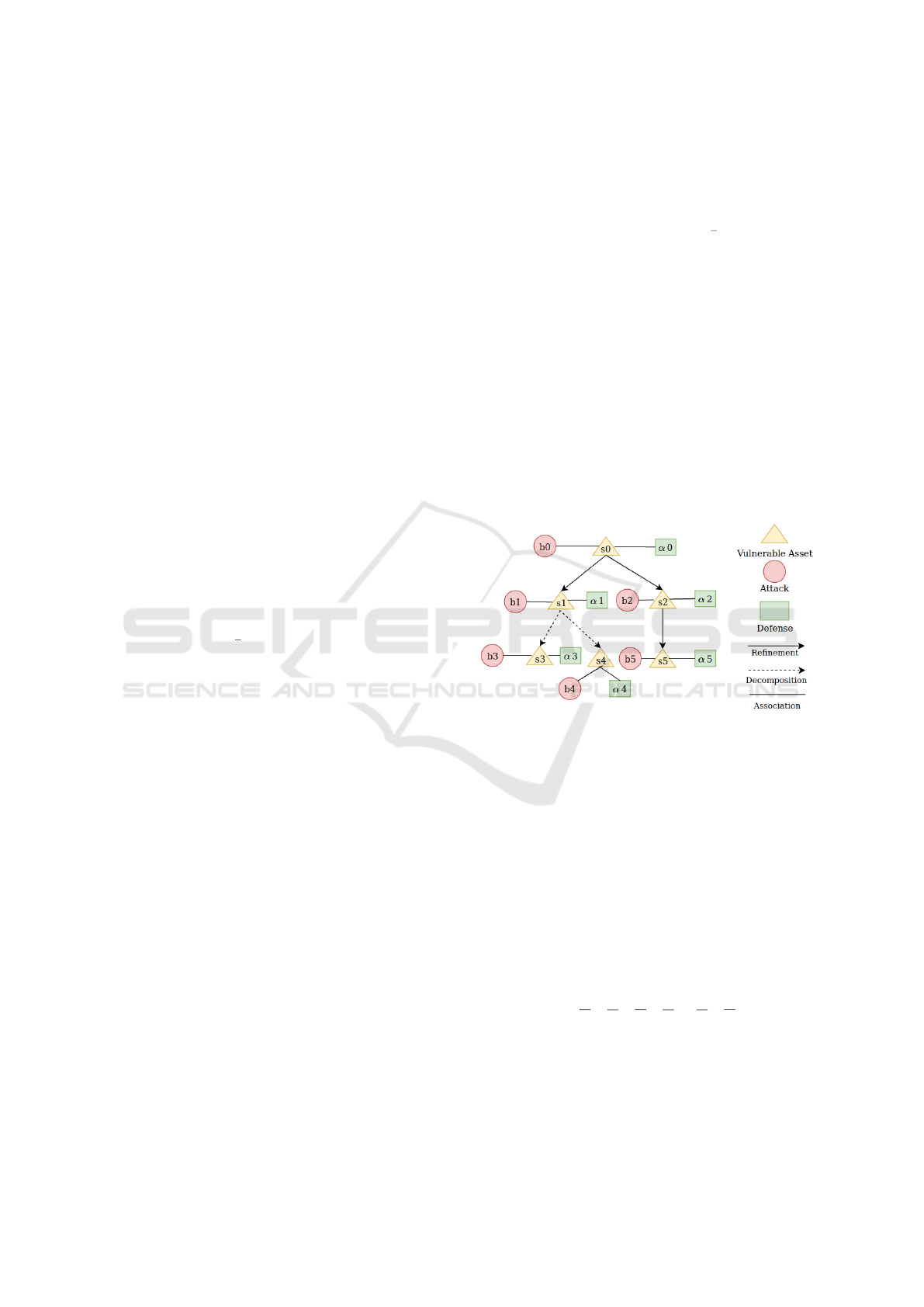
Figure 1: An example of Asset-Driven Attack Defense Tree.
Figure 1 illustrates the graphical representation of an
AADT, with six vulnerable domain asset nodes and
corresponding attack and defense nodes. For sim-
plicity and readability, we only show one-to-one re-
lations, knowing that one-to-many relations are also
possible. s
3
, s
4
and s
5
are leaf nodes. Equation 2
presents the corresponding AADT (T
1
) construction
that can capture three types of nodes. In T
1
, s
0
is the
root vulnerable domain asset node. It is refined by ei-
ther s
1
or s
2
, with the latter refined by s
5
. The node
s
1
is decomposed into s
3
and s
4
. Each vulnerable do-
main asset node s
i
is threatened by the attack node b
i
and protected by the defense node α
i
.
T
1
= s
α
0
b
0
0
(s
α
1
b
1
1
(s
α
3
b
3
3
, s
α
4
b
4
4
), s
α
2
b
2
2
(s
α
5
b
5
5
)) (2)
ENASE 2025 - 20th International Conference on Evaluation of Novel Approaches to Software Engineering
568
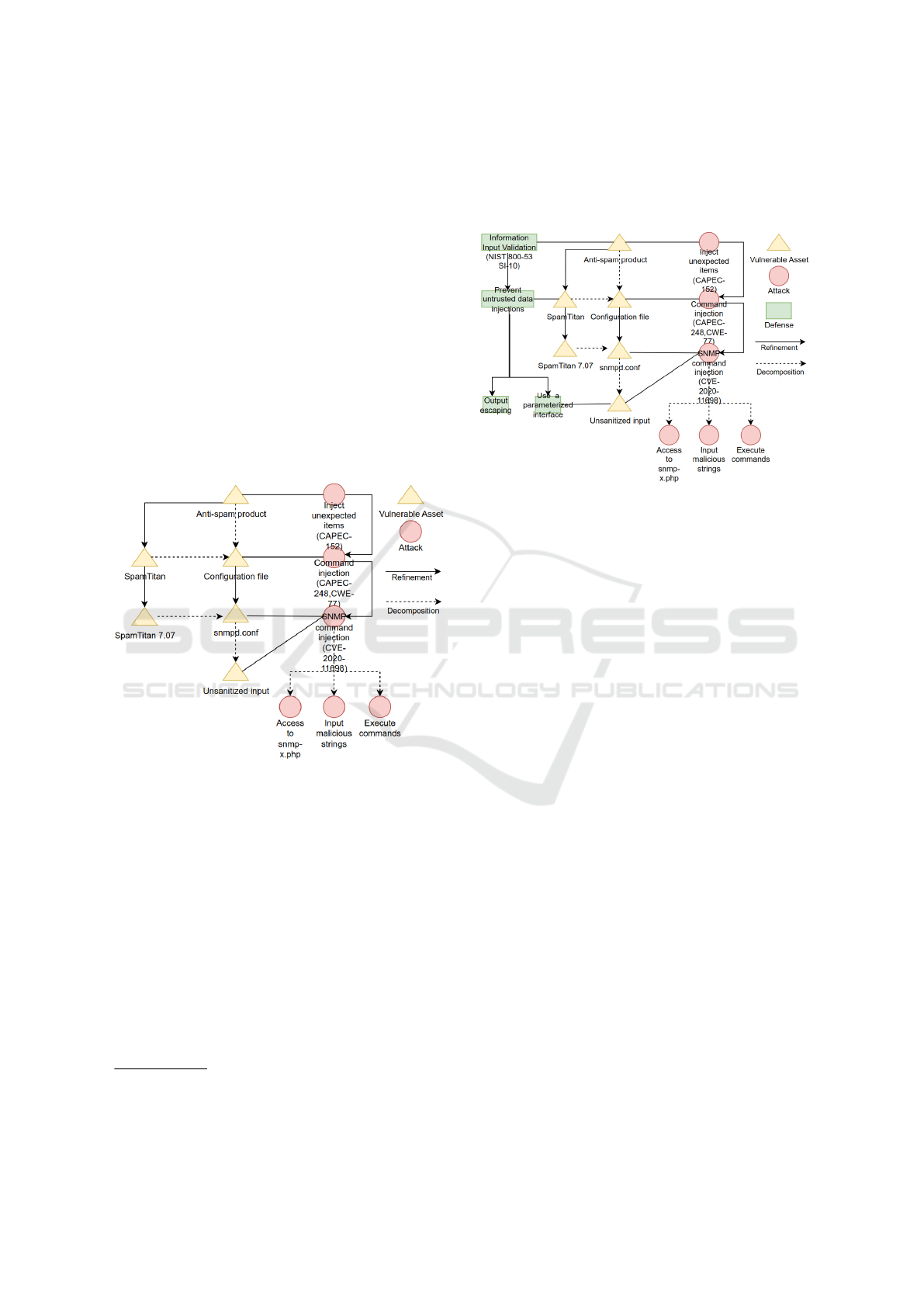
4 EXAMPLE ILLUSTRATION
To illustrate the features of AADT, we consider the
following scenario concerning an anti-spam product,
which can be a system’s component. This scenario is
shown in Figure 2.
To develop a system, a system engineer could re-
quire an anti-spam product as a component of the sys-
tem. This anti-spam product should be modelled as
an architectural element. In this scenario, the system
engineer has chosen the product SpamTitan to play
the role of the anti-spam product. More precisely,
he/she has chosen the version 7.07 of SpamTitan. In
an anti-spam product, such as SpamTitan, configura-
tion files are available. One of the configuration files
in SpamTitan 7.07 is snmpd.conf, which allows con-
trolling the Net-SNMP agent’s operation and the man-
agement information provided.
Figure 2: Using AADT to capture attack scenario for an
anti-spam product.
From the attacker’s point of view, there is a pos-
sibility of injecting unexpected items (CAPEC-152
6
)
into a vulnerable anti-spam product, as shown in Fig-
ure 2. As an anti-spam product contains configuration
files, the attacker could carry out command injection
attack (CAPEC-248
7
). In the case of SpamTitan 7.07,
which contains the configuration file snmpd.conf, a
remote attacker could perform SNMP command in-
jection in the file snmpd.conf through the page snmp-
x.php, which alters the system’s behavior from its in-
tended operation
8
. For that, the attacker has to get
access to snmp-x.php file, input strings that contain a
malicious command and execute the command to ob-
6
https://capec.mitre.org/data/definitions/152.html
7
https://capec.mitre.org/data/definitions/248.html
8
https://nvd.nist.gov/vuln/detail/CVE-2020-11698
tain a privilege or capability that the attacker would
not otherwise have. The success of this attack is based
on the fact that snmpd.conf allows unsanitized user
input constructing all or part of a command.
Figure 3: Using AADT to capture attack scenario and de-
fense measures for an anti-spam product.
From the defender’s point of view, to neutral-
ize special elements that could modify the intended
command, all input information should be validated
(NIST SP 800-53 SI-10) (Group, 2020) and filtered
for potentially unwanted characters. Untrusted data
injections may be prevented using a parameterized in-
terface or output escaping (also known as output en-
coding). This is shown in Figure 3. Parameterized
interfaces keep data and code separate, ensuring that
malicious or unintended data cannot alter the meaning
of commands. Output escaping marks specific char-
acters to signal the interpreter’s parser about the trust
level of the data.
5 DISCUSSION
Asset is an essential concept in threat modelling, as
the attackers’ aim is to compromise assets and the de-
fenders’ aim is to protect them. Until now, the con-
cept of asset was absent in attack-trees-based secu-
rity modelling. Here, we propose a novel extension –
Asset-Driven Attack-Defense Tree (AADT) – which
incorporates the fundamental Asset concept into the
attack-trees-based security modelling. We demon-
strated the novelty using a simple scenario. From our
demonstration, it is clear that for any elaboration of
the scenario, the specific AADT in Figure 3 could
be easily extended with new system assets, attacks
and defenses. Future research should provide a more
in-depth evaluation of AADTs, exploring additional,
more complex scenarios and applications.
AADT: Asset-Driven Attack-Defense Tree
569

As time passes, attack techniques become more
and more diverse and defense measures have to evolve
to follow the fast-changing pace of attackers. In
comparison, assetsare relatively stable due to their
domain-specific nature and could therefore be rele-
vant underpinning elements (Uzunov and Fernandez,
2014; Messe et al., 2020). Adding and focusing
on the vulnerable asset perspective as an anchor ad-
dresses the current limitations of the attack-defense
tree, which concentrates on concrete actions without
fully integrating domain elements. We plan to elab-
orate the AADT formalism with a notion of time as
well as relate to information flows within the system.
In contrary to attack-defense tree, which annotates
concrete attack and defense actions, AADT offers a
novel, multi-level approach. This approach allows de-
picting nodes in different levels of abstraction. Us-
ing the refinement relation in AADT, it is possible to
mix abstract assets with concrete ones. This allows
to explicitly capture corresponding attack and defense
categories as well as actions. This characteristic is
particularly useful in architectural design, which can
be performed in several system development stages
and therefore involves domain elements in different
levels of abstraction. Capturing asset/attack/defense
categories promotes the ability to mitigate newly-
discovered attack techniques of existing categories.
For example, a newly-discovered attack about Poetry
Argument Injection has been discovered
9
, as its ab-
straction – Command Injection – has already been in-
cluded in the current AADT in Figure 3. Accordingly,
in our example scenario, the relevant defense mea-
sures were already incorporated into the design, and,
therefore, the anti-spam product is secured against
this specific attack. By organizing vulnerabilities into
abstraction layers, AADT enables the deployment of
adaptable, category-level defenses that remain effec-
tive as new threats emerge within existing vulnerabil-
ity classes. This approach helps ensure that defensive
measures implemented today maintain their relevance
and robustness in the face of future, unanticipated at-
tacks.
Like ART, ADTree and APT, AADT faces the
state-space explosion problem, which hampers its
comprehensibility. It is thus necessary to provide
means for visualizing large AADT, such as the one
proposed by the REsPASS project (Probst et al.,
2015) (Lenin et al., 2016). By structuring the tree in
a circular pattern, linearizing complex attack-defense
scenarios, and allowing zooming in and out, the vi-
sualization can disguise the tree’s complexity to re-
duce the cognitive effort needed to process a com-
9
https://www.cve.org/CVERecord?id=CVE-2022-
36069
plex AADT. We intend to explore the adaptation of
this visualization technique for AADT. We also plan
to experiment with formal verification of AADTs, us-
ing a model checker (e.g. UPPAAL (Behrmann et al.,
2006)).
Creating the AADT representations is labor inten-
sive. We are working towards automating the gener-
ation of AADTs. For example, one of the concrete
methods we are exploring is the automatic extrac-
tion of assets from the CAPEC attack pattern descrip-
tion, which is in natural language. Another direction
we are currently attempting is automatically identi-
fying vulnerabilities/attacks using the Common Plat-
form Enumeration (CPE)
10
as an identifier for assets.
Future work can integrate the new AADT repre-
sentation into security modelling tools. Specifically,
we are considering extending TRADES Tool with
AADT representations. TRADES Tool already sup-
ports the relevant concepts in its models, namely at-
tack and defense measures, assets and relations be-
tween them. TRADES also supports extraction and
association of CVEs with assets based on their CPEs.
We intend to rely on those to automate the genera-
tion of AADT representations. This would also make
sure that the derived AADTs are synchronized with
the models that represent the systems’ design and se-
curity posture. In addition, this would help to mini-
mize the effort of creating AADTs.
6 CONCLUSION
In this paper, we introduce an extension of attack-
defense trees, the Asset-Driven Attack-Defense Tree
(AADT), which focuses on vulnerable asset infor-
mation as a novel type of node. Unlike traditional
attack-defense trees, which center on threat scenarios
and defensive measures, AADT addresses the need
for representing domain elements and their hierar-
chical structure. By explicitly incorporating vulner-
able assets, such as systems, sub-systems, and com-
ponents, AADT provides decision-makers with a co-
hesive view of system architecture and security, en-
hancing impact analysis and supporting the strategic
design of security controls.
AADT also improves on traditional models by
representing security controls and vulnerabilities at
multiple levels of abstraction. This layered ap-
proach aligns with system development stages, allow-
ing stakeholders to implement adaptable security con-
trols that target both general and specific attack cate-
gories, such as high-level defenses against command
10
https://cpe.mitre.org/
ENASE 2025 - 20th International Conference on Evaluation of Novel Approaches to Software Engineering
570

injection rather than focusing only on individual vul-
nerabilities.
Additionally, the explicit representation of com-
promised assets and associated vulnerabilities allows
stakeholders to evaluate potential threats more effec-
tively and assign security controls with minimal ef-
fort. By associating vulnerability categories with as-
sets, AADT facilitates proactive, category-level miti-
gation strategies that can address future attacks within
the same vulnerability class. We formalize AADT
and demonstrate its unique strengths in refinement
and impact analysis through a case study. Future in-
tegration of the AADT representation into security
modelling tools can facilitate security experts’ under-
standing of systems designs and security posture as
well as their active role in designing trustworthy sys-
tems.
ACKNOWLEDGEMENTS
This work is supported by ICO, Institut Cybers
´
ecurit
´
e
Occitanie, funded by R
´
egion Occitanie, France, and
by Innovate UK, grant number 75243.
REFERENCES
Ali, A. T. and Gruska, D. P. (2019). Attack protection tree.
In CS&P.
Arnold, F., Guck, D., Kumar, R., and Stoelinga, M. (2014).
Sequential and parallel attack tree modelling. In Inter-
national Conference on Computer Safety, Reliability,
and Security, pages 291–299. Springer.
Aslanyan, Z., Nielson, F., and Parker, D. (2016). Quanti-
tative verification and synthesis of attack-defence sce-
narios. In 2016 IEEE 29th Computer Security Foun-
dations Symposium (CSF), pages 105–119. IEEE.
Bagnato, A., Kordy, B., Meland, P. H., and Schweitzer, P.
(2012). Attribute decoration of attack–defense trees.
International Journal of Secure Software Engineering
(IJSSE), 3(2):1–35.
Behrmann, G., David, A., Larsen, K. G., H
˚
akansson, J., Pet-
tersson, P., Yi, W., and Hendriks, M. (2006). Uppaal
4.0.
Buldas, A., Laud, P., Priisalu, J., Saarepera, M., and
Willemson, J. (2006). Rational choice of security
measures via multi-parameter attack trees. In Inter-
national Workshop on Critical Information Infrastruc-
tures Security, pages 235–248. Springer.
Force, J. T. and Initiative, T. (2013). Security and privacy
controls for federal information systems and organi-
zations. NIST Special Publication, 800(53):8–13.
Fraile, M., Ford, M., Gadyatskaya, O., Kumar, R.,
Stoelinga, M., and Trujillo-Rasua, R. (2016). Using
attack-defense trees to analyze threats and counter-
measures in an atm: a case study. In IFIP Working
Conference on The Practice of Enterprise Modeling,
pages 326–334. Springer.
Gadyatskaya, O., Hansen, R. R., Larsen, K. G., Legay, A.,
Olesen, M. C., and Poulsen, D. B. (2016a). Modelling
attack-defense trees using timed automata. In Interna-
tional Conference on Formal Modeling and Analysis
of Timed Systems, pages 35–50. Springer.
Gadyatskaya, O., Harpes, C., Mauw, S., Muller, C., and
Muller, S. (2016b). Bridging two worlds: reconciling
practical risk assessment methodologies with theory
of attack trees. In International Workshop on Graphi-
cal Models for Security, pages 80–93. Springer.
Gadyatskaya, O., Jhawar, R., Kordy, P., Lounis, K., Mauw,
S., and Trujillo-Rasua, R. (2016c). Attack trees for
practical security assessment: ranking of attack sce-
narios with adtool 2.0. In International Conference on
Quantitative Evaluation of Systems, pages 159–162.
Springer.
Gadyatskaya, O. and Trujillo-Rasua, R. (2017). New direc-
tions in attack tree research: catching up with indus-
trial needs. In International Workshop on Graphical
Models for Security, pages 115–126. Springer.
Group, J. T. F. T. I. I. W. (2020). Security and pri-
vacy controls for information systems and organiza-
tions. Technical Report NIST Special Publication (SP)
800-53, Rev. 5, Includes updates as of September,
2020, National Institute of Standards and Technology,
Gaithersburg, MD.
Jhawar, R., Kordy, B., Mauw, S., Radomirovi
´
c, S., and
Trujillo-Rasua, R. (2015). Attack trees with sequen-
tial conjunction. In IFIP International Information
Security and Privacy Conference, pages 339–353.
Springer.
Jhawar, R., Lounis, K., and Mauw, S. (2016). A stochastic
framework for quantitative analysis of attack-defense
trees. In International Workshop on Security and Trust
Management, pages 138–153. Springer.
Kordy, B., Mauw, S., Radomirovi
´
c, S., and Schweitzer, P.
(2014). Attack–defense trees. Journal of Logic and
Computation, 24(1):55–87.
Kordy, B., Mauw, S., and Schweitzer, P. (2012). Quanti-
tative questions on attack–defense trees. In Interna-
tional Conference on Information Security and Cryp-
tology, pages 49–64. Springer.
Kumar, R., Ruijters, E., and Stoelinga, M. (2015). Quanti-
tative attack tree analysis via priced timed automata.
In International Conference on Formal Modeling and
Analysis of Timed Systems, pages 156–171. Springer.
Lenin, A., Gadyatskaya, O., Ionita, D., Pieters, W., Tanner,
A., Saraiva, S., Muller, C., Willemson, J., Ford, M.,
and Muller, S. (2016). Technology-supported risk es-
timation by predictive assessment of socio-technical
security.
Mauw, S. and Oostdijk, M. (2006). Foundations of attack
trees, information security and cryptology-icisc 2005.
In 8th international conference, Seoul, Korea, pages
186–198.
Messe, N. (2021). Security by Design: An asset-based ap-
proach to bridge the gap between architects and secu-
rity experts. PhD thesis, Universit
´
e de Bretagne Sud.
AADT: Asset-Driven Attack-Defense Tree
571

Messe, N., Chiprianov, V., Belloir, N., El-Hachem, J.,
Fleurquin, R., and Sadou, S. (2020). Asset-oriented
threat modeling. In 2020 IEEE 19th International
Conference on Trust, Security and Privacy in Comput-
ing and Communications (TrustCom), pages 491–501.
IEEE.
Nielsen, J. R. (2011). Evaluating information assurance
control effectiveness on an air force supervisory con-
trol and data acquisition (scada) system.
Paul, S. and Vignon-Davillier, R. (2014). Unifying tradi-
tional risk assessment approaches with attack trees.
Journal of Information Security and Applications,
19(3):165–181.
Pieters, W. and Davarynejad, M. (2014). Calculating ad-
versarial risk from attack trees: Control strength and
probabilistic attackers. In Data Privacy Management,
Autonomous Spontaneous Security, and Security As-
surance, pages 201–215. Springer.
Probst, C. W., Willemson, J., and Pieters, W. (2015). The at-
tack navigator. In International Workshop on Graphi-
cal Models for Security, pages 1–17. Springer.
Ramadan, R. A., Aboshosha, B. W., Alshudukhi, J. S.,
Alzahrani, A. J., El-Sayed, A., and Dessouky, M. M.
(2021). Cybersecurity and countermeasures at the
time of pandemic. Journal of Advanced Transporta-
tion, 2021.
Roy, A. (2010). Attack countermeasure trees: A non-state-
space approach towards analyzing security and find-
ing optimal countermeasure sets. PhD thesis, Duke
University.
Roy, A., Kim, D. S., and Trivedi, K. S. (2012a). Attack
countermeasure trees (act): towards unifying the con-
structs of attack and defense trees. Security and com-
munication networks, 5(8):929–943.
Roy, A., Kim, D. S., and Trivedi, K. S. (2012b). Scal-
able optimal countermeasure selection using implicit
enumeration on attack countermeasure trees. In
IEEE/IFIP International Conference on Dependable
Systems and Networks (DSN 2012), pages 1–12.
IEEE.
Schneier, B. (1999). Attack trees. Dr. Dobb’s journal,
24(12):21–29.
Shaked, A. (2023). A model-based methodology to support
systems security design and assessment. J. Ind. Inf.
Integr., 33:100465.
Shaked, A., Messe, N., and Melham, T. (2024). Modelling
tool extension for vulnerability management. In Pro-
ceedings of the ACM/IEEE 27th International Con-
ference on Model Driven Engineering Languages and
Systems (MODELS Companion ’24), New York, NY,
USA. ACM.
Ten, C.-W., Liu, C.-C., and Govindarasu, M. (2007). Vul-
nerability assessment of cybersecurity for scada sys-
tems using attack trees. In 2007 IEEE Power Engi-
neering Society General Meeting, pages 1–8. IEEE.
Uzunov, A. V. and Fernandez, E. B. (2014). An extensible
pattern-based library and taxonomy of security threats
for distributed systems. Computer Standards & Inter-
faces, 36(4):734–747.
ENASE 2025 - 20th International Conference on Evaluation of Novel Approaches to Software Engineering
572
