
A Comparative Analysis of Anonymous and Non-Anonymous
Authorization Architectures for IoT Environments in Cooperative
Intelligent Transport Systems
Hannes Salin
a
Swedish Transport Administration, Department of Information and Communication Technology, Borl
¨
ange, Sweden
fi
Keywords:
Trust Model, Trust Architecture, Cryptographic Accumulators, Group Signatures, Anonymous Credentials,
C-ITS, Authentication, Authorization.
Abstract:
In this paper, we present a comparative analysis of two distinct authorization architectures with a focus on
their applicability in dynamic and cooperative intelligent transportation networks (C-ITS) suitable for low-
powered IoT devices. Both architectures leverage accumulators for authorization and secret key storage, while
our modification of the original architecture introduces an enhanced privacy feature enabling anonymous de-
vice access via a proxy node. This modification results in increased communication complexity, trading off
anonymity against increased interaction overhead. We provide a proof of concept implementation with per-
formance experiments, and conclude that the cryptographic computational performance remains relatively
unaffected between the two architectures. Our findings suggest a potential for different deployment strategies
of these architectures; in urban settings with a dense presence of proxy nodes, but also in sparser regions where
privacy is not paramount due to minimal vehicle presence.
1 INTRODUCTION
Connected transport infrastructures, also referred to
Cooperative Intelligent Transport Systems (C-ITS),
consist of both mobile and stationary nodes, where
these nodes may be personal devices, vehicles,
roadside- or central units. Also, having drones and
other types of UAV devices are not excluded from C-
ITS environments (Valle et al., 2021). C-ITS in the
automotive sector primarily aims to improve commu-
nication between vehicles and nearby structures, lead-
ing to increased road safety and smoother traffic flow
(Zeddini et al., 2022). C-ITS employs established
short-range communication methods (such as ETSI
ITS G5 (European Telecommunications Standards In-
stitute, 2018)) and will be supplemented by broader
communication technologies like 3G, 4G, and 5G.
This setup will enable vehicles to interact with other
vehicles, traffic lights, road infrastructure, and other
types of infrastructure participants using Internet of
Things (IoT) or Industrial IoT (IIoT) devices. In
essence, the wireless communication among various
nodes and ITS stations, along with their associated
functions, is termed cooperative V2X communica-
a
https://orcid.org/0000-0001-6327-3565
tion. The utilization of the connectedness thus en-
ables a range of informational, alert, and support ser-
vices, which are set to roll out progressively in the
forthcoming innovation stages (C2C-CC, 2023).
In these connected ad-hoc type of environments,
the utilization of IoT and IIoT creates fruitful oppor-
tunities for novel and more efficient use cases. As
an implication, involving more devices and allowing
more nodes to interact, the need for secure and scal-
able trust architectures is crucial (Shahab et al., 2022;
Galego and Pascoal, 2022). For the European con-
text, not only must the General Data Protection Reg-
ulation be considered (European Commission, 2016)
but also ITS-specific safety and security standardiza-
tions (European Telecommunications Standards In-
stitute, 2018). However, there is currently no de-
tailed specifications of authorization nor anonymiza-
tion implementations for C-ITS environments, leav-
ing the industry and academia open to work to-
wards technological harmonization. Previously, the
secure accumulator-based architecture AccA was pro-
posed (Salin, 2023a) to address a suitable authoriza-
tion mechanism for IoT-driven C-ITS environments.
Expanding that work, we now develop a stronger
and even more secure architecture conceptualized via
anonymous credentials (Chaum, 1985). For this rea-
Salin, H.
A Comparative Analysis of Anonymous and Non-Anonymous Authorization Architectures for IoT Environments in Cooperative Intelligent Transport Systems.
DOI: 10.5220/0013324700003944
In Proceedings of the 10th International Conference on Internet of Things, Big Data and Security (IoTBDS 2025), pages 281-288
ISBN: 978-989-758-750-4; ISSN: 2184-4976
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
281

son, our work addresses two main areas: we pro-
pose a secure and anonymized authorization architec-
ture based on cryptographic accumulators for C-ITS
purposes, and we provide a performance comparison
evaluation and analysis of the original AccA architec-
ture and our new, anonymized architecture.
1.1 Anonymous Credentials
Anonymous credentials (AC), was originally intro-
duced by Chaum in 1985 (Chaum, 1985) and later
realized as the first fully anonymous scheme in 2001
(Camenisch and Lysyanskaya, 2001). These type of
schemes are cryptographic mechanisms that let users
validate attributes like their identity or group member-
ship without disclosing personal details. AC schemes
can be realized in various ways, where the group
signature-based approach seems to be the more effi-
cient and solid approach (Kakvi et al., 2023). This,
however, requires a set of participants being able to
collectively sign an authorization access.
1.2 Problem Statement
Trust management and authorization mechanisms in
IoT environments remains a challenge in general
(Sharma et al., 2020; Hammi et al., 2022). Consid-
ering the context of short-lived ad-hoc vehicle net-
works where IoT and IIoT devices may be utilized
in both moving and stationary nodes, we need to in-
vestigate authorization mechanisms that also provides
anonymity. This includes finding an efficient and se-
cure authorization architecture that allows for easy
implementations. We also consider the case where
the accessing nodes, given an authorization access,
can retrieve data or services from another node in a
completely anonymous way. This is desired since C-
ITS environments can be open for location privacy
threats, e.g., (Liao et al., 2018) and (Salin, 2023b).
We summarize our research goals, addressing these
challenges as follows:
• Investigate the extension of an accumulator-based
authorization mechanism, providing anonymous
access.
• Compare the anonymous and non-anonymous
authorization mechanisms using a performance
analysis.
1.3 Contribution
We provide a comparison between two accumulator-
based authorization architectures tailored for C-ITS
environments: the first with no anonymity but de-
centralization of authorization, and a second which is
our modification of the latter with anonymity but re-
lying on a proxy node. We provide a proof of concept
implementation of both architectures, coupled with
performance experiments. From the analysis we are
then able to suggest when the two different architec-
tures are suitable for implementation.
2 RELATED WORK
Some research in using cryptographic accumulators
have previously been investigated, related to the do-
main of ad-hoc networking and C-ITS. However,
the use-cases are more relevant for other scenarios,
e.g., (Zuo et al., 2021; Salin et al., 2021; F
¨
orster
et al., 2014; Heng et al., 2022). No group sig-
nature based accumulator architecture for authoriza-
tion was found in the current literature. Lauinger et
al. proposed an authorization scheme for Internet of
Vehicles (IoV), building on cryptographic accumula-
tors and zero-knowledge proofs. However, the pro-
posed architecture needs a managing root authority
for the accumulators and is not self-contained in the
vehicles (Lauinger et al., 2021). In a recent survey
of accumulators, Ren et al., shows that accumulator
based schemes exists for anonymous credentials, but
these are developed for cloud data sharing and mo-
bile payments (Ren et al., 2022). Also, in the com-
prehensive study by Khan et al. on IoT-specific au-
thorization schemes, no accumulator-based solutions
utilizing anonymous credentials were to be found ei-
ther (Khan et al., 2022). The main difference of the
accumulator-based architectures with other type of
technologies is primarily on the chosen underlying
cryptographic primitives whereas the accumulator-
based architecture uses an interactive protocol to en-
able the de-centralization of authentication and autho-
rization between nodes.
3 PRELIMINARIES
We designate H as a secure hash function H :
{1, 0}
∗
→ {1, 0}
n
for a predetermined n, which is se-
cure against preimage attacks. The resultant hash di-
gest H (m) belongs to a secure group G. The gen-
erator of this secure group G is denoted as g. A se-
curity parameter λ is a value that determines the key
sizes during the initial setup of a particular scheme. A
key par is denoted (sk, pk) where sk is the secret key
and pk the corresponding public key. The analyzed
architectures use the efficient Boneh-Lynn-Shacham
(BLS) short signature scheme (Boneh et al., 2001).
This scheme is based on bilinear pairings where a
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
282

signature σ of a message m is then computed by
H
g
(m)
sk
= σ and the signature is verified by checking
that ˆe(σ, g)
?
= ˆe(H (m), pk) holds.
3.1 System Settings
In this section we describe the system C-ITS setting,
which includes multiple IoT nodes and vehicles. Any
type of device capable of sending or receiving data
using wireless communication channels, are referred
to as objects, and we denote such object as OBJ .
Each object have a hardware security module, de-
noted HSM. This is a memory segment of the de-
vice’s architecture being able to securely store secret
keys and generate pseduo random numbers to be used
in secure protocols.
A vehicular ad-hoc network (VANET) with multi-
ple connections (at least two objects) is denoted NET.
Although our C-ITS system is primarily a VANET, we
do not limit the NET to be exclusively such network;
any cluster of IoT devices capable of short range com-
munication can be considered. The underlying logi-
cal network of the NET is thus bounded for a desig-
nated area, e.g. a smart home network, a clustered
drone network or a standard VANET. Moreover, in
the NET there is at least one registration authority ob-
ject denoted OBJ
R
. This object allows other objects
to register into the NET and is trusted by the NET
holder, e.g. the infrastructure or network segment
in the eco-system. Therefore, OBJ
R
is considered
trusted in this particular setup. However, in contrast to
the scenarios found in isolated public key infrastruc-
ture (PKI) settings where various functions might be
overseen by a centralized authority (CA), in our sys-
tem architecture, object registration holds a singular
focus: it serves exclusively for the registration of the
object. This is a crucial distinction because, following
this registration process, all subsequent procedures in-
volving authentication and authorization are handled
autonomously by the objects themselves, without a
need for an overseeing authority, including revoca-
tion. This decentralization arises from the capabil-
ity of these objects to facilitate a range of accessible
functionalities within their own individual devices.
Thus, instead of relying on a centralized system to
manage authentications and authorizations, this task
is dispersed amongst the network of objects, each
holding its own control and maintaining the network’s
functionality. This implies a self-sustained ecosystem
where IoT devices independently manage the valida-
tions, bringing both efficiency and robustness to the
system’s operations.
Different entities are categorized as types. A spe-
cific object within this network could establish a stan-
dard trust configuration of certain types that it can en-
gage with and respond to.
We summarize the system setting in the following
components:
OBJ : an object, manifested as a device with short
range communication capabilities and computa-
tional power equally strong as IoT or IIoT devices.
Each object can store and execute authentication
and authorization protocols.
HSM: a hardware security module, i.e. a memory
area within the device architecture, being able to
store secret keys or generate random values.
RA: a registration authority object, trusted by the net-
work facilitator and have the ability to register
new objects into the network.
NET: the overall network where registered objects
OBJ
R
, OBJ
1
, ..., OBJ
n
communicate, consisting
of the registration object as a minimum. Can be
manifested as a stationary road side unit at a cer-
tain road- and network segment in a larger C-ITS
eco-system.
3.2 Threat Model
We consider the following threat model where an ad-
versary A has two different capabilities: A either pas-
sively observe the NET from the outside, or A is it-
self registered and connected to the NET as a nor-
mal participant, i.e., the adversary is an object within
the given system setting, as described in Sec. 3.1.
A also have the ability to capture data transfers be-
tween any two nodes in the NET. However, A does
not have computational capacity to steal or manipu-
late any memory segments nor data within any other
objects. It cannot access any secret keys. The remain-
ing participants in the NET are considered honest and
non-tampered objects OBJ
1
, ..., OBJ
k
. The formal-
ized threat model is found in (Salin, 2023a) and de-
fined as two security experiments Exp
A
1
and Exp
A
2
,
where the former captures the case where A tries to
gain access to function f
i
in object OBJ
k
but have
no registered access, and the latter captures the case
where A is not even registered in the NET.
4 AUTHORIZATION
ARCHITECTURE
In this section we introduce a modified AccA architec-
ture for authentication and authorization of in-vehicle
services and data, namely AccA − GS. The core part
of the architecture is built on the what is referred to as
A Comparative Analysis of Anonymous and Non-Anonymous Authorization Architectures for IoT Environments in Cooperative Intelligent
Transport Systems
283

the authorization matrix M . It embeds an authentica-
tion vector V . These two are combined and securely
stored in the object’s HSM as an accumulated element
of a secure accumulator Z. Due to space constraints,
we refer to (Salin, 2023a) for a complete description
of the architecture.
4.1 Group Signatures for a Modified
Architecture with Anonymity
In this section we will detail an architecture using a
standard AC, but adjusted for the previously described
scenario of C-ITS authorization. The main goal is to
construct a simple alternative to AccA for compari-
son, in order to analyze the differences of using non-
collaborative but non-anonymous access, with collab-
orative but anonymous access. We modify the AccA
architecture to handle group signatures to incorporate
an AC approach (Kakvi et al., 2023), which implies a
stronger dependency on RA. Therefore, our proposed
architecture is the natural modification of AccA into a
group signature version we will call AccA − GS. This
modification is inspired by the original work proposed
by Camenisch and Lysyanskaya, incorporated as an
AC system (Camenisch and Lysyanskaya, 2004). The
main difference between the two architectures is that
AccA is self-contained after object registration with
the RA, where AccA −GS relies heavily on the RA as
a proxy to ensure privacy.
4.2 Modified Architecture
We propose a modified AccA architecture with the
following re-defined sub-protocols:
Reg
RA
(OBJ
j
, RA): this protocol runs just as in the
original AccA architecture. However, after the
computation of α
j
and storage of pk
j
, OBJ
j
and
RA executes the Join protocol as a second step.
Reg
OBJ
(OBJ
1
, OBJ
2
, RA): this protocol is ad-
justed as follows:
1. OBJ
1
sends a request ρ
register
= (σ
i,1
=
H (OBJ
1
||α
1
)
sk
1
, α
1
, f
i
, σ
GS
1
) to the RA re-
questing function f
i
in object OBJ
2
. This in-
cludes the group signature σ
GS
1
which is com-
puted by OBJ
1
using the Sign protocol where
the message m = σ
i,1
.
2. The RA sends (σ
i,1
, σ
GS
1
) to OBJ
2
.
3. OBJ
2
run the Verify protocol to verify the sig-
nature σ
GS
1
.
4. OBJ
2
creates (or updates) a binary string b
i,1
that corresponds access to f
i
for the specific sig-
nature σ
i,1
. Note that OBJ
2
only knows that it
is a valid signature but not from whom it is cre-
ated, i.e. the index 1 is not signifying a particu-
lar identity.
5. OBJ
2
accumulates σ
i,1
into Z and in particu-
lar V
1
using the Acc procedure, which in turn
output corresponding witnesses ω
1
and w
i
, re-
spectively. The witness is encrypted as w
pk
RA
i
and ω
1
is stored locally in OBJ
2
.
6. OBJ
2
sends w
pk
RA
i
to RA.
7. RA decrypt w
pk
RA
i
into w
i
and sends w
pk
1
i
to
OBJ
1
.
8. OBJ
1
receive and decrypt w
pk
1
i
and stores w
i
.
Auth(OBJ
1
, OBJ
2
, f
i
): this protocol runs between
two registered objects where OBJ
1
seek access
to f
i
in OBJ
2
. The protocol is using the RA as
a proxy for keeping the privacy of the original
sender of the request, although the signature is not
telling the original signer.
1. OBJ
1
sends
σ
ρ
, ρ
access
= (α
1
, σ
i,1
, w
pk
RA
i
)
to
RA, where σ
ρ
is a standard BLS-signature over
ρ
access
.
2. RA verifies that
e(g
1
z
1
, α
1
)
?
= e(pk
1
, g). (1)
3. RA verifies σ
ρ
with the standard BLS signature
verification procedure.
4. RA decrypt w
pk
RA
i
into w
i
and sends ρ
′
access
=
(α
1
, σ
i,1
, w
pk
2
i
) to OBJ
2
.
5. OBJ
2
receive ρ
′
access
and decrypt w
pk
2
i
into w
i
.
6. OBJ
2
performs validation of two witness
proofs in the accumulators, i.e. verifying ω
1
for the internal check and w
i
for access to f
i
.
7. If successful, either send back f
pk
RA
i
and use
same procedure as in Reg
OBJ
to proxy the data
back to OBJ
1
, or if it was to trigger a certain
function f
i
in the device of OBJ
2
that will then
execute.
Rev(OBJ
1
, OBJ
2
, f
i
): this protocol revokes access
of f
i
in OBJ
2
for OBJ
1
. In all its simplicity,
OBJ
2
runs the accumulator procedure Del to re-
move σ
i,1
. Similarly, the standard Revoke proto-
col for the RA is run as in the original scheme of
Camenish and Lysyanskaya.
Note that even if the group signature scheme pro-
vides anonymity of the original signer, we cannot
have OBJ
1
directly communicate with OBJ
2
since
it would be obvious for OBJ
2
who is requesting ac-
cess. Therefore, the RA function as a proxy and en-
sure that the anonymous access request is verified by
OBJ
2
. Moreover, since we only use the RA public
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
284

Setup procedure: each object initializes their own accumulator (if not already setup), i.e. running Generate(λ, N), and the RA runs KeyGen.
Setup keys: each object OBJ
i
generates (
i
,
i
).
Modified Authentication and Authorization protocols using group signatures
Sub-protocol
OBJ
j
RA OBJ
k
Reg
RA
1. Sends pk
j
= g
sk
j
to RA
6. Receive and store α
j
7. Run protocol Join(OBJ
j
, RA)
2. Receive pk
j
.
3. Generate α
j
=
g
sk
j
z
j
where z
j
←
$
Z
4. Store (
1
z
j
, z
j
,
j
)
5. Sends α
j
to OBJ
j
.
Reg
OBJ
1. Sends ρ
register
= (σ
i, j
= H (OBJ
j
||α
j
)
sk
j
, α
j
, f
i
, σ
GR j
) to RA
where f
i
is the function to access in OBJ
k
.
8. Receive and stores w
j
i
.
2. Sends (σ
i, j
, σ
GS j
) to OBJ
k
.
7. Decrypt w
RA
i
into w
i
and send w
j
i
to OBJ
j
.
3. Run protocol Verify(σ
GS j
, σ
i, j
).
4. If successful, update M .
5. Run Acc(σ
i, j
) to generate w
i
.
6. Send w
RA
i
to RA.
Auth 1. Sends (σ
ρ
, ρ
access
= (α
1
, σ
i,1
, w
RA
i
) to RA
9. Receive f
j
i
from RA and decrypt.
2. Receive (σ
ρ
, ρ
access
) and verifies σ
ρ
using BLS.
3. Verifies e(g
1
z
1
, α
1
)
?
= e(g,
1
).
4. Decrypt w
RA
i
and send ρ
′
access
= (α
1
, σ
i,1
, w
2
i
)
to OBJ
k
.
8. Decrypt f
RA
i
into f
i
and send f
j
i
to OBJ
j
.
5. Receive ρ
′
access
and decrypt w
2
i
.
6. Run accumulator Verify.
7. If successful, send f
RA
i
to RA.
Rev Run Rev protocol.
Figure 1: The proposed modified authentication and authorization architecture with group signatures. Additional steps in the
protocols are highlighted in bold.
key for anonymous credentials of all registered users
there is no scalability issue as in traditional PKI. The
modified architecture protocol is shown in Fig. 1.
5 SECURITY ANALYSIS
The security analysis for the original AccA scheme
is provided by (Salin, 2023a). Therefore, we limit
this paper to include a complementary analysis for the
AccA − GS scheme, showing correctness and privacy,
based on the previous analysis and from the original
scheme of Camenisch and Lysyanskaya.
Theorem 1. The verification e(g
1
z
j
, α
j
)
?
= e(g, pk
j
) in
AccA − GS is correct and authenticates OBJ
j
.
Proof. The verification is correct since:
e(g
1
z
j
, α
j
) = e(g
1
z
j
, g
sk
j
z
j
) (2)
= e
g, g
sk
j
z
j
z
j
= e(g, pk
j
). (3)
The only party who knows
1
z
j
is the RA who also gen-
erated that value (and stores it in a HSM internally).
Moreover, since the RA also generated α
j
during the
setup phase, there is no way to construct an α
′
j
which
is based on another public key than pk
j
. Finally, since
the RA receives a BLS signature σ
ρ
over the request,
the only way to forge it is to break the BLS scheme,
namely the security of the privacy is reduced to the
security of BLS.
Corollary 1. For the modified version Acca − GS the
correctness and security provided in the original pa-
per (Camenisch and Lysyanskaya, 2004) implies the
privacy of the proposed architecture since we only ap-
plied this already secure construction on the already
proved secure AccA architecture (Salin, 2023a), un-
der the threat model of security experiments Exp
A
1
and Exp
A
2
.
We note that in the modified request and response
interactions for the REG
OBJ
and Auth sub-protocols,
witnesses and functions f
i
are sent encrypted using
the public keys of the receiving parties; the exponen-
tiation encryption is secure under the discrete loga-
rithm problem. Moreover, we underscore that the pro-
tocol is secure under the defined security experiments
Exp
A
1
and Exp
A
2
as defined in (Salin, 2023a), hence
we have not analyzed Acca − GS utilizing stronger
models or different attack vectors.
6 EXPERIMENTS
We implemented the main parts of the AccA and
AccA − GS architectures, and ran several tests to eval-
uate their performances. We used the Python wrapper
of the MCL library (Mitsunari, 2019) with a type A
curve, BLS12
381. We also used the same approach
A Comparative Analysis of Anonymous and Non-Anonymous Authorization Architectures for IoT Environments in Cooperative Intelligent
Transport Systems
285
for the hashing to group elements and byte conversion
as in (Salin, 2023a), namely the hashAndMapTo func-
tion in the MCL-library. Another technical detail, that
was particularly considered in the AccA − GS archi-
tecture, is that the underlying signature scheme by Ca-
menisch and Lysyanskaya recommends a Fiat-Shamir
heuristic in the proof signature step (Camenisch and
Lysyanskaya, 2004), but for many implementations it
is replaced by a hash function (Chen et al., 2021). We
used the standard SHA-256 in our experiments, con-
figured as follows from the Hazmat library:
c = public_key.encrypt(message,
padding.OAEP(mgf=padding.MGF1
(algorithm=hashes.SHA256()),
algorithm=hashes.SHA256(),
label=None)
The first experiments were sub-protocol perfor-
mance tests that were executed 1000 times, and the
average timings are noted in Tab. 1 for the AccA ar-
chitecture, and Tab. 2 for the AccA − GS architecture.
The tests included the computational crypto functions
in each sub-protocol. Tests were executed on two dif-
ferent devices, D
1
: an Intel Core i5, 2.7GHz platform,
and D
2
: a lightweight single board device with a dual
core Cortex-A72, 1.5GHz platform.
Table 1: Computational performance in each object (ms) in
the AccA architecture on device D
1
and device D
2
.
Protocol (D
1
) OBJ
j
RA OBJ
k
Reg
RA
- 0.0901 -
Reg
OBJ
0.0233 - 1.5101
Auth - - 2.7701
Rev - - 0.1103
Protocol (D
2
) OBJ
j
RA OBJ
k
Reg
RA
- 0.1053 -
Reg
OBJ
0.0275 - 2.1970
Auth - - 4.0361
Rev - - 0.0932
Table 2: Computational performance in each object (ms) in
the AccA − GS architecture on device D
1
and device D
2
.
Protocol (D
1
) OBJ
j
RA OBJ
k
Reg
RA
0.0013 0.0831 -
Reg
OBJ
0.1241 0.0211 1.0113
Auth 0.2621 2.7131 1.6761
Rev - 0.3217 0.0799
Protocol (D
2
) OBJ
j
RA OBJ
k
Reg
RA
0.0069 0.1012 -
Reg
OBJ
0.2151 0.0329 1.8280
Auth 0.3800 4.6123 2.8493
Rev - 0.4601 0.1142
As demonstrated in Tab. 1, the Auth protocol
emerges as the most resource-intensive, primarily ow-
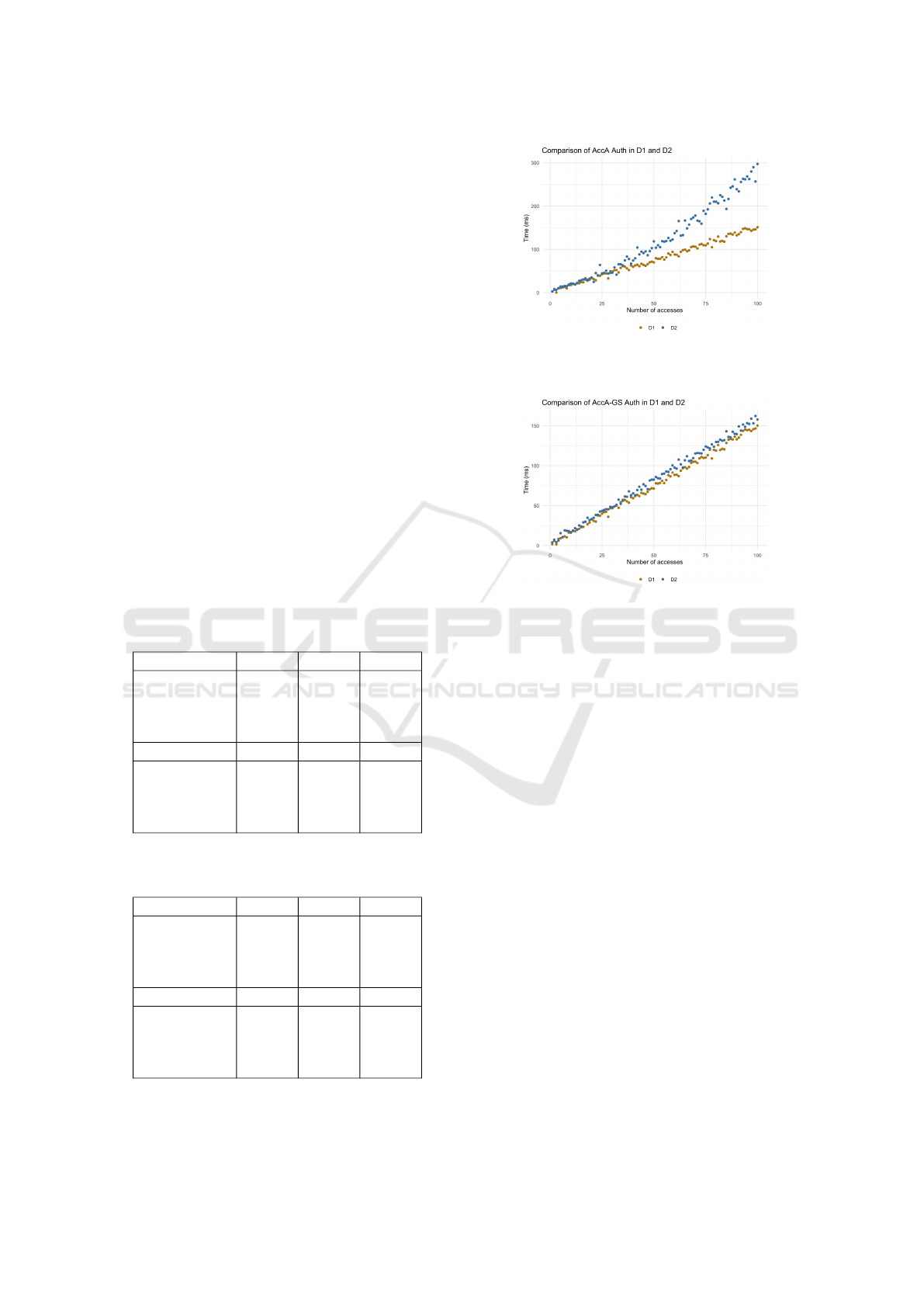
Figure 2: Comparison of running the Auth sub-protocol in
AccA up to 100 times on devices D
1
and D
2
, only the com-
putational part for the verifying object in the protocol.
Figure 3: Comparison of running the Auth sub-protocol in
AccA − GS up to 100 times on devices D
1
and D
2
, only the
computational part for the verifying object in the protocol.
ing to its verification processes. We also did a scala-
bility experiment comparing the two devices’ ability
to run an increased number of authentications. Since
we exclude the communication complexity we did
not investigate how much request and response traf-
fic would jam a device if the number of accesses in-
creased. However, from a computational perspective,
we measured how each device handled an increase of
running the Auth sub-protocol which contains 4 pair-
ing operations. In Fig. 2 we show the difference of
execution time (y-axis) when increasing the number
of runs of Auth in OBJ
k
, i.e., the device that verifies
an authorization of an accessing device OBJ
j
. In D
2
we see that the performance decreases after a while
and we hypothesise that it is due to that it may have
less optimizations in the execution environment such
as efficient caching. Both devices had network traffic
turned on in the background in a first round of the ex-
periment, and when turning of all WiFi connections
and running the experiment again, we got similar re-
sults. Therefore, this was not a significant factor to
the computations on neither device.
When running the same experiment for
AccA − GS we got as expected more aligned re-
sults since the OBJ
k
does not run a sequence of
costly pairings in this protocol; instead much of the
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
286

computations lies on the RA. This would be more
efficient of the RA is a RSU which may have more
computational power than a typical low-powered
IoT device. The result is shown in Fig. 3. We also
note that there are very small shifts in the timing
measurements for both architectures, although fol-
lowing a linear pattern. This is also expected since
there were running operation system processes in the
background on both devices which should affect the
measurements slightly; however the scattering along
the linearity is on a magnitude of a few
1
100
’s of a
millisecond, thus negligible.
We also compared the AccA − GS against the per-
formance assessment carried out by Ometov et al.,
since the original AccA architecture was theoretically
compared in the original paper. Simplifying the the-
oretical comparison, an Intel Edison, 500 MHz Dual-
Core device would execute a pairing verification and
a curve point multiplication in 580 ms and 0.1 ms re-
spectively. For the AccA − GS architecture the com-
putation does not require any pairings on the OBJ
k
side, but instead the decryption of a witness and a ac-
cumulator verification. A theoretical conversion of
these operations on a Intel Edison device gives 0.4
ms. However, the RA node will have a similar com-
putational performance as the OBJ
k
in the AccA ar-
chitecture since it includes a BLS verification which
is a pairing verification, and an additional pairing ver-
ification.
6.1 Analysis
Although not run as an experiment, we conclude that
the communication complexity for each architecture
differs as detailed in Tab. 3. The AccA − GS has in
total 3 more send/receive operations. Given the com-
putational complexity found in tables 1 and 2 we note
that there is a generally a larger factor between D
1
and
D
2
in the sub protocols where pairings are included,
e.g., the Auth protocol. This is noted in both archi-
tectures and we hypothesise that it could be related
to how the MCL library runs on different (computer)
architectures. However, in REG
RA
where the sub-
protocol need to generate random numbers the dif-
ferences are not too big. This should be natural since
the protocol does not exhaust the device entropy by
generating only a few values during the protocol exe-
cution.
Now, given the computational complexity and the
theoretical communication complexity we conclude
that applying the group signature based architecture
is not significantly more expensive, given the assump-
tion that the wireless channels in the NET between the
devices is efficient. Having 3 more interaction steps is
Table 3: Communication complexity in terms of interac-
tions for each architecture, we denote one sending/receiving
operation as one T .
Protocol AccA AccA − GS
Reg
RA
2T 3T
Reg
OBJ
4T 4T
Auth 2T 4T
not optimal, and also relying on a third party for every
request is not optimal in the sense of not being able to
access a device if the RA is down. This could hap-
pen due to DDoS attacks or similar events. For that
reason, if the NET environment does not require full
privacy of the objects’ identities, the original AccA
architecture is more suitable.
7 CONCLUSION
Our proposed modified version of AccA have an addi-
tional privacy property where each access to a device
is made anonymously but require a proxy node, i.e.,
the RA. Thus, we trade anonymity for an increased
communication complexity. Our experiments shows
that the cryptographic computational performance be-
tween the protocols does not differ significantly, but
instead the additional interactions in AccA − GS gives
the architecture a slower overall performance as ex-
pected. Depending on the wireless technology used
in the NET environments, infrastructure and vehi-
cle stakeholders may need to balance anonymity with
the reliance on proxy nodes, where urban areas with
dense proxy nodes can support collaborative setups,
while in sparse regions, deploying the AccA architec-
ture may be more advantageous.
REFERENCES
Boneh, D., Lynn, B., and Shacham, H. (2001). Short
signatures from the weil pairing. In Advances in
Cryptology–ASIACRYPT ’01, LNCS, pages 514–532.
Springer.
C2C-CC (2023). CAR 2 CAR Communication Consor-
tium. https://www.car-2-car.org/about-c-its. Ac-
cessed: 2023-08-23.
Camenisch, J. and Lysyanskaya, A. (2001). An efficient
system for non-transferable anonymous credentials
with optional anonymity revocation. In Pfitzmann,
B., editor, Advances in Cryptology — EUROCRYPT
2001, pages 93–118, Berlin, Heidelberg. Springer
Berlin Heidelberg.
Camenisch, J. and Lysyanskaya, A. (2004). Signature
schemes and anonymous credentials from bilinear
maps. In Franklin, M., editor, Advances in Cryptol-
A Comparative Analysis of Anonymous and Non-Anonymous Authorization Architectures for IoT Environments in Cooperative Intelligent
Transport Systems
287

ogy – CRYPTO 2004, pages 56–72, Berlin, Heidel-
berg. Springer Berlin Heidelberg.
Chaum, D. (1985). Security without identification: Trans-
action systems to make big brother obsolete. Com-
mun. ACM, 28(10):1030–1044.
Chen, Y., Lombardi, A., Ma, F., and Quach, W. (2021).
Does fiat-shamir require a cryptographic hash func-
tion? In Malkin, T. and Peikert, C., editors, Ad-
vances in Cryptology – CRYPTO 2021, pages 334–
363, Cham. Springer International Publishing.
European Commission (2016). Regulation (EU) 2016/679
of the European Parliament and of the Council of 27
April 2016 on the protection of natural persons with
regard to the processing of personal data and on the
free movement of such data, and repealing Directive
95/46/EC (General Data Protection Regulation) (Text
with EEA relevance).
European Telecommunications Standards Institute (2018).
ETSI TS 123 501 V15.3.0: 5G; System Architecture
for the 5G System. https://www.etsi.org/standards.
Accessed: 2023-08-25.
F
¨
orster, D., Kargl, F., and L
¨
ohr, H. (2014). Puca: A
pseudonym scheme with user-controlled anonymity
for vehicular ad-hoc networks (vanet). In 2014 IEEE
Vehicular Networking Conference (VNC), pages 25–
32.
Galego, N. M. C. and Pascoal, R. M. (2022). Cybersecurity
in smart cities: Technology and data security in intel-
ligent transport systems. In Mesquita, A., Abreu, A.,
and Carvalho, J. V., editors, Perspectives and Trends
in Education and Technology, pages 17–33, Singa-
pore. Springer Singapore.
Hammi, B., Monteuuis, J.-P., and Petit, J. (2022). Pkis in
c-its: Security functions, architectures and projects: A
survey. Vehicular Communications, 38:100531.
Heng, X., Qin, S., Xiao, Y., Wang, J., Tao, Y., and Zhang,
R. (2022). A strong secure v2i authentication scheme
from pki and accumulator. In 2022 2nd International
Conference on Consumer Electronics and Computer
Engineering (ICCECE), pages 98–103.
Kakvi, S. A., Martin, K. M., Putman, C., and Quaglia,
E. A. (2023). Sok: Anonymous credentials. In
G
¨
unther, F. and Hesse, J., editors, Security Standardi-
sation Research, pages 129–151, Cham. Springer Na-
ture Switzerland.
Khan, A., Ahmad, A., Ahmed, M., Sessa, J., and Anisetti,
M. (2022). Authorization schemes for internet
of things: requirements, weaknesses, future chal-
lenges and trends. Complex & Intelligent Systems,
8(5):3919–3941.
Lauinger, J., Ernstberger, J., Regnath, E., Hamad, M., and
Steinhorst, S. (2021). A-poa: Anonymous proof of
authorization for decentralized identity management.
In 2021 IEEE International Conference on Blockchain
and Cryptocurrency (ICBC), pages 1–9.
Liao, D., Li, H., Sun, G., Zhang, M., and Chang, V. (2018).
Location and trajectory privacy preservation in 5g-
enabled vehicle social network services. Journal of
Network and Computer Applications, 110:108–118.
Mitsunari, S. (2019). ”MCL cryptolibrary”. https://github.
com/herumi/mcl.
Ren, Y., Liu, X., Wu, Q., Wang, L., Zhang, W., et al. (2022).
Cryptographic accumulator and its application: A sur-
vey. Security and Communication Networks, 2022.
Salin, H. (2023a). Acca: A decentralized and accumulator-
based authentication and authorization architecture
for autonomous iot in connected infrastructures. In
Wills, G. B., Butty
´
an, L., Kacsuk, P., and Chang, V.,
editors, Proceedings of the 8th International Confer-
ence on Internet of Things, Big Data and Security,
IoTBDS 2023, Prague, Czech Republic, April 21-23,
2023, pages 170–177. SCITEPRESS.
Salin, H. (2023b). Pseudonym swapping with secure accu-
mulators and double diffie-hellman rounds in coopera-
tive intelligent transport systems. In Kallel, S., Jmaiel,
M., Zulkernine, M., Hadj Kacem, A., Cuppens, F., and
Cuppens, N., editors, Risks and Security of Internet
and Systems, pages 223–238, Cham. Springer Nature
Switzerland.
Salin, H., Fokin, D., and Johansson, A. (2021). Authen-
ticated multi-proxy accumulation schemes for dele-
gated membership proofs. In Luo, B., Mosbah, M.,
Cuppens, F., Othmane, L. B., Cuppens, N., and Kallel,
S., editors, Risks and Security of Internet and Systems
- 16th International Conference, CRiSIS 2021, Virtual
Event, Ames, USA, November 12-13, 2021, Revised
Selected Papers, volume 13204 of Lecture Notes in
Computer Science, pages 162–171. Springer.
Shahab, S., Agarwal, P., Mufti, T., and Obaid, A. J. (2022).
Siot (social internet of things): A review. In Fong, S.,
Dey, N., and Joshi, A., editors, ICT Analysis and Ap-
plications, pages 289–297, Singapore. Springer Na-
ture Singapore.
Sharma, A., Pilli, E. S., Mazumdar, A. P., and Gera, P.
(2020). Towards trustworthy internet of things: A sur-
vey on trust management applications and schemes.
Computer Communications, 160:475–493.
Valle, F., Cooney, M., Mikhaylov, K., and Vinel, A. (2021).
The integration of uavs to the c-its stack. In 2021 IEEE
29th International Conference on Network Protocols
(ICNP), pages 1–6.
Zeddini, B., Maachaoui, M., and Inedjaren, Y. (2022). Se-
curity threats in intelligent transportation systems and
their risk levels. Risks, 10(5).
Zuo, X., Li, L., Luo, S., Peng, H., Yang, Y., and Gong,
L. (2021). Privacy-preserving verifiable graph inter-
section scheme with cryptographic accumulators in
social networks. IEEE Internet of Things Journal,
8(6):4590–4603.
IoTBDS 2025 - 10th International Conference on Internet of Things, Big Data and Security
288
