
Memory-Saving Oblivious RAM for Trajectory Data via Hierarchical
Generation of Dummy Access over Untrusted Cloud Environment
Taisho Sasada
1 a
and Bernard Ousmane Sane
2,3 b
1
Graduate School of Science and Technology, Nara Institute Science and Technology, Ikoma, Japan
2
Graduate School of Media and Governance, Keio University Shonan Fujisawa Campus, Kanagawa, Japan
3
Quantum Computing Center, Keio University, Kanagawa, Japan
Keywords:
Trusted Execution Environment, Encrypted Database, Oblivious Random Access Memory, Access Pattern
Leakage, Homomorphic Encryption, Trajectory Data.
Abstract:
The proliferation of smartphones and IoT devices has led to a rapid increase in the generation of trajectory data.
Managing this continuously generated data poses a significant burden. To alleviate this burden, cloud databases
have become widespread, leading to increased storage of data on servers managed by other individuals and
organizations (third parties). However, if there are adversaries among these third parties, viewing the data
contents could lead to personal information leaks and privacy violations. Therefore, there are expectations
for the use of encrypted databases that allow searching and managing data while it remains encrypted (in
ciphertext form), without revealing the contents. Since data owners (clients) encrypt their data before storing
it, third parties cannot view the actual content. However, it is known that merely encrypting the data is not
sufficient for security, as a vulnerability has been identified where the original data can be inferred from access
patterns to the encrypted database even without seeing the actual data content. In this paper, we propose an
anonymization method for access patterns on trajectory data in encrypted databases. For anonymization,
we apply Oblivious Random Access Memory (ORAM), which generates dummy accesses alongside data
aggregation and updates to make the original accesses unidentifiable. Trajectory data is often aggregated and
updated on a trajectory basis rather than by individual points. Therefore, directly generating dummy accesses
at the point level using ORAM leads to overhead in encrypted memory. In our proposed method, we separate
the data storage memory into upper and lower levels to make access patterns unidentifiable at the trajectory
level rather than the point level. The lower memory contains single points, while the upper memory contains
multiple points (capable of representing part or all of a trajectory), and dummy accesses are generated using
ORAM to make upper memory accesses mutually unidentifiable.
1 INTRODUCTION
Trajectory data records chronological changes in
location information, such as people’s movement
routes, vehicle operation records, and logistics track-
ing. This data is utilized in various fields including
urban planning, traffic optimization, marketing analy-
sis, and understanding behavioral patterns. However,
since it contains large amounts of position coordinates
and timestamps continuously collected from sensors
like GPS, the data volume tends to become enor-
mous, making on-premises management challenging.
Cloud database services have become widespread due
a
https://orcid.org/0000-0003-2144-4949
b
https://orcid.org/0000-0002-9249-8285
to benefits such as reduced server management bur-
den, lower implementation and operational costs, and
centralized data management. As a result, there has
been an increase in storing data on servers managed
by other individuals and organizations (third parties).
However, if there are adversaries among these
third parties, viewing the data contents could lead
to personal information leaks and privacy violations.
Therefore, data owners (clients) have increasingly be-
gun encrypting their data before entrusting it to third-
party servers such as cloud database services. This
allows data to be managed on third-party servers with-
out revealing its contents (keeping it in encrypted
form), and this is called an encrypted database. Un-
like encryption through database functionality itself,
the data is encrypted on the client side, thus pro-
Sasada, T. and Sane, B. O.
Memory-Saving Oblivious RAM for Trajectory Data via Hierarchical Generation of Dummy Access over Untrusted Cloud Environment.
DOI: 10.5220/0013370100003899
In Proceedings of the 11th International Conference on Information Systems Security and Privacy (ICISSP 2025) - Volume 2, pages 635-642
ISBN: 978-989-758-735-1; ISSN: 2184-4356
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
635

tecting privacy even if the database administrator has
malicious intent. But multiple studies have revealed
that encrypted database alone does not provide suf-
ficient protection. A particularly significant vulner-
ability is information leakage through access pattern
disclosure. Access patterns are chronological records
of data access logs, and statistical analysis of these
patterns can enable inference of confidential informa-
tion about the original encrypted data. In fact, (Islam
et al., 2012) demonstrated that 80% of search queries
could be inferred by analyzing access patterns to en-
crypted email repositories, highlighting the severity
of this vulnerability.
To address this vulnerability, access pattern con-
cealment methods using Oblivious Random Access
Memory (ORAM) (Goldreich and Ostrovsky, 1996)
with homomorphic encryption have been proposed.
ORAM is a technology that makes access patterns
unidentifiable by generating dummy accesses in ad-
dition to regular accesses. The good compatibility
between ORAM and homomorphic encryption pri-
marily stems from the ability to eliminate noise in
statistical measurements caused by dummy accesses.
In conventional ORAM, while dummy accesses are
performed to conceal access patterns, these dummy
accesses would create noise in statistical measure-
ments. By using homomorphic encryption, the con-
tent of dummy accesses can be set to encrypted zeros
(or other neutral values). This allows for increasing
the number of accesses to hide access patterns while
simultaneously preventing any impact on statistical
measurements (Moataz et al., 2015; Liu et al., 2018;
Falk et al., 2023).
In this paper, we propose Memory-saving
ORAM for trajectory Data Over Encrypted Database,
MORADO. While we apply ORAM for anonymiza-
tion, trajectory data is often aggregated and updated
on a trajectory basis rather than by individual points.
Therefore, directly generating dummy accesses at the
point level using ORAM leads to overhead in the en-
crypted database. In our proposed method, we sep-
arate the ORAM memory that stores data into up-
per and lower levels to make access patterns uniden-
tifiable at the trajectory level rather than the point
level. The ORAM lower memory contains single
points, while the ORAM upper memory contains mul-
tiple points (capable of representing part or all of a
trajectory), and dummy accesses are generated us-
ing ORAM to make upper memory accesses mutually
unidentifiable. This enables anonymization of access
patterns at the trajectory level. The structure of this
paper is as follows: In Section 2, we explain the basic
technologies such as ORAM, TDX in this research.
In Section 3, we explore the detailed design of pro-
posed method and flow of dummy access generation.
In Section 4, we present the results of the experi-
mental evaluation. In Section 2, we outline related
works on databases utilizing homomophirc encryp-
tion, TEE, and their challenges. Finally, in Section
6, we conclude the paper by summarizing the contri-
butions of this research.
2 PRELIMINARY
2.1 Partially Homomorphic
Cryptosystem
A Partially Homomorphic Cryptosystem is a special
encryption scheme that allows operations (particu-
larly addition) between ciphertexts. When the result
of these operations is decrypted, it matches the re-
sult of performing the same operations on the original
plaintexts. One representative additive homomorphic
encryption scheme is the Paillier Homomorphic En-
cryption (PHE).
The key generation in PHE proceeds as follows.
First, select two large prime numbers p and q, and
calculate their product n and the least common mul-
tiple λ of p − 1 and q − 1. Next, choose an integer g
from Z
∗
n
2
and calculate the multiplicative inverse µ of
L(g mod n
2
) modulo n, where:
L(u) =
u − 1
n
(1)
The resulting public key is (n, g) and the private key is
(λ, µ). In the encryption process, a random value r is
selected from Z
∗
n
, and for a plaintext m, the ciphertext
is computed as:
c = g
m
· r
n
mod n
2
(2)
For decryption, given a ciphertext c, the plaintext is
recovered by computing:
m = L(c
λ
mod n
2
) · µ mod n (3)
An important point is that while both encryption and
decryption use modular exponentiation, decryption
has a higher computational cost. This is because the
base of exponentiation during decryption is the ci-
phertext. The size of ciphertext is significantly larger
than the public key n. An important property of PHE
is that when the product of two ciphertexts is de-
crypted, it yields the sum of the corresponding plain-
texts. That is:
Dec(Enc(m
1
) · Enc(m
2
) mod n
2
) = m
1
+ m
2
mod n
(4)
This property enables additive operations to be per-
formed on encrypted data.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
636

2.2 Trust Domain Extensions
Intel Trust Domain Extensions (TDX) is a TEE based
on secure virtualization (Intel, 2023). TDX has the
capability to deploy hardware isolated virtual ma-
chines called trust domains (TD). TDs are isolated
from virtual machine manager (VMM)/hypervisor
and any other software which are not related to TD as
shown. This strong isolation provides the required se-
curity guarantees for a TEE system. Moreover, Intel
TDX uses multi-key total memory encryption (MK-
TME) and hashing to maintain the confidentiality and
integrity of the code and data in TD. Intel TDX mod-
ule is designed to run in Secure Arbitration Mode
(SEAM). SEAM introduces an expansion to the Vir-
tual Machine Extension (VMX) architecture, estab-
lishing a fresh VMX root mode known as SEAM
root. This SEAM root mode serves as the platform for
accommodating a CPU-attested module designed for
generating VM guests termed TD. SEAM mode can
be used as two logical modes: TDX non-root mode
and TDX root mode. TDX root mode is used for
Host side operations and non-root mode is used for
TD guest operations.
2.3 Oblivious Random Access Memory
ORAM (Oblivious RAM) (Goldreich and Ostrovsky,
1996) is a primitive that obscures a user’s (proces-
sor’s) access patterns to storage (DRAM). ORAM
transforms a user’s sequence of program address ac-
cesses into access patterns that appear random. While
physical access locations remain visible to an at-
tacker, the ORAM interface guarantees that physi-
cal access patterns are independent of logical access
patterns, preventing leakage of data-dependent access
patterns. Additionally, it uses probabilistic encryption
to protect data content and hide whether updates have
occurred.
Path ORAM (Stefanov et al., 2018) is currently
the most efficient and well-researched ORAM imple-
mentation. It consists of two main hardware compo-
nents: binary tree storage and an ORAM controller.
Each node in the binary tree can store up to Z useful
data blocks, with dummy blocks filling empty slots.
The ORAM controller is trusted hardware that in-
cludes a position map and stash. In Path ORAM,
accessing a data block involves consulting the posi-
tion map, reading and decrypting blocks along the
path, remapping to a new random position, and writ-
ing blocks back from the stash. This ensures each
ORAM access is random and untraceable. How-
ever, Path ORAM incurs significant energy and per-
formance penalties compared to regular DRAM.
Write-only ORAM (WoORAM) (Li and Datta,
2017) is a lightweight version of ORAM that only
obscures write access patterns. It offers better perfor-
mance than full ORAM against attackers who cannot
monitor read access patterns. Li and Datta’s scheme
was proposed for private information retrieval in data
centers but is not efficient in the context of secure pro-
cessors.
DetWoORAM (Deterministic Write-only ORAM)
(Roche et al., 2017) is a deterministic Write-only
ORAM scheme that doesn’t require a stash. It gener-
ates fixed, deterministic physical write access patterns
regardless of logical write access patterns. While this
eliminates the need for a stash, it requires additional
accesses to move data from temporary storage to per-
sistent main memory, resulting in performance penal-
ties. Hardware implementation complexity also re-
mains a challenge.
3 PROPOSED METHOD
3.1 Threat Model
For the architectural design of the proposed method,
we define a threat model centered on protecting data
and access patterns. This model serves as the founda-
tion for protecting sensitive data and its usage patterns
in cloud environments. In the threat model, we con-
sider the Cloud Service Provider (CSP) as the primary
threat actor. We assume the CSP has extensive access
rights across all software layers (OS, hypervisor, and
other system components). These access rights po-
tentially enable the CSP to observe and analyze the
original data and its processing. Among the CSP’s
attack capabilities, we particularly focus on memory
dump attacks and cold boot attacks (Yitbarek et al.,
2017; Halderman et al., 2009). In memory dump at-
tacks, the CSP can acquire and analyze system mem-
ory contents at any time, risking exposure of unen-
crypted data and access patterns. In cold boot attacks,
original data might be extracted from residual RAM
data by acquiring memory contents immediately after
system power-down. Furthermore, CSP can contin-
uously monitor and view data loaded into memory.
This capability enables the CSP to track data flows
and processing patterns in detail and analyze tempo-
ral correlations. This suggests the possibility of in-
ferring not only data contents but also access patterns
and DO’s behavior patterns.
In addition to CSP-related threats, malware and
malicious software targeting the cloud must also be
considered. These can lead to the theft of sensi-
tive information such as usernames and passwords,
Memory-Saving Oblivious RAM for Trajectory Data via Hierarchical Generation of Dummy Access over Untrusted Cloud Environment
637
as well as entire databases hosted in clusters. This
means that beyond data interception and tampering,
there are threats of access to pattern observation and
recording. Specific threats include malware such as
Siloscape, which targets Windows containers in cloud
environments, and Kinsing Malware, which targets
Docker/Kubernetes clusters. These malware speci-
mens can remain dormant in systems for extended pe-
riods, secretly monitoring data flows and access pat-
terns. As a summary, the main protection targets in
this model are the confidentiality of DO’s data and
the privacy of its access patterns. In addition to pro-
tecting data content, information about who accesses
the data, when and how is treated as equally important
protection targets.
3.2 Overall Architecture
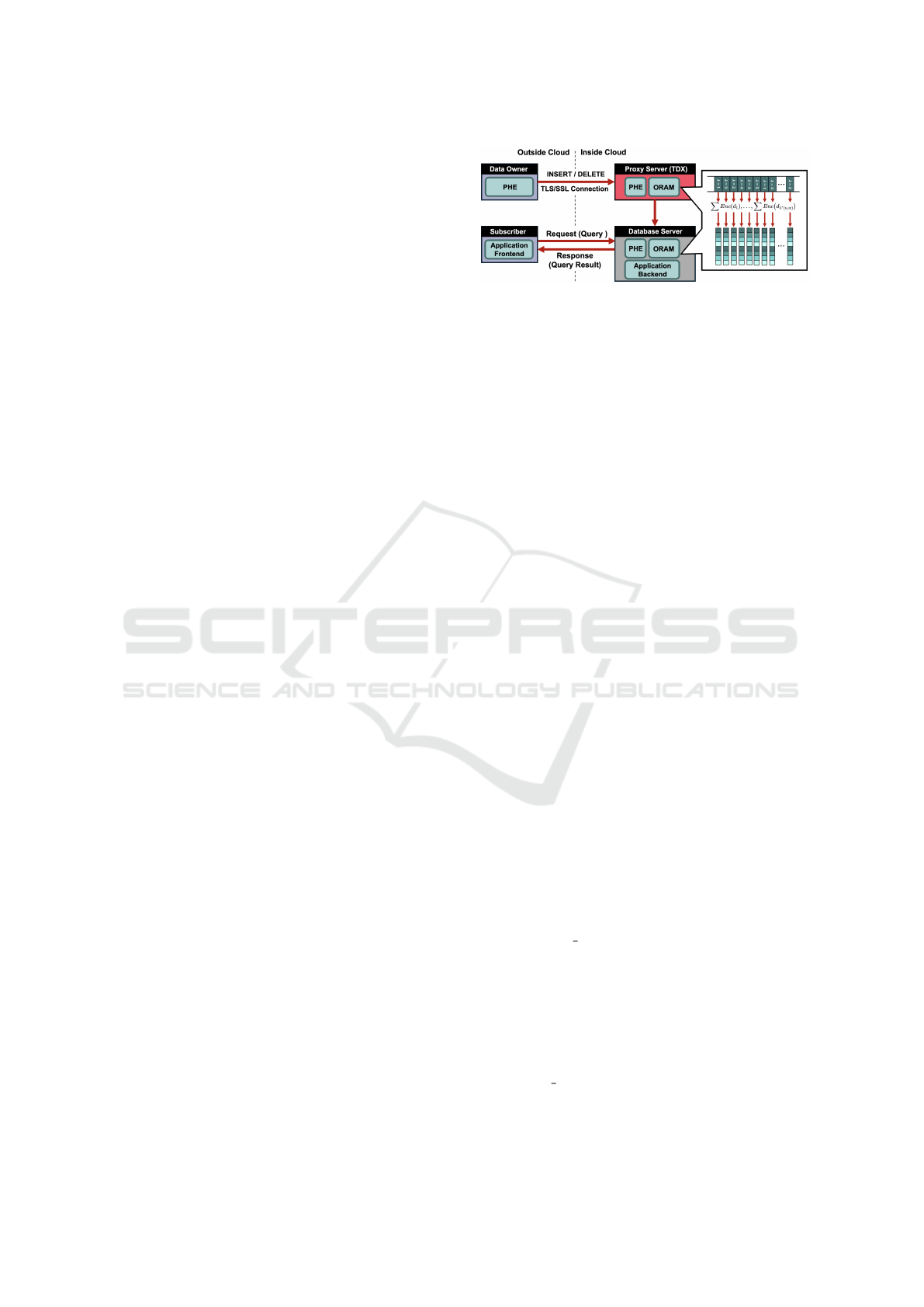
The concept of the proposed method is shown in
the Figure 1. The proposed method leverages the
fact that, in the context of trajectory data insertion,
the majority of queries are trajectory-unit rather than
point-unit queries, thereby reducing the total amount
of dummy accesses generated by ORAM. The archi-
tecture of the proposed method is broadly divided
between inside and outside the cloud. Within the
cloud, memory is divided into several upper and lower
memories. Each upper memory consists of mul-
tiple smaller lower memories. DO encrypts their
trajectory data using Paillier homomorphic encryp-
tion (PHE) and sends it to the cloud side through a
TLS/SSL connection. Homomorphically encrypted
data insertions from DOs are first aggregated into ap-
propriate lower memories within these upper memo-
ries. Each upper memory is assigned its own ORAM
client, with corresponding ORAM servers existing on
the database server. On the proxy server, to conceal
the distribution of requests, the number of requests
processed by each upper memory is uniformized.
Specifically, a value λ ∗ (u, α) is calculated, repre-
senting the maximum number of requests in all up-
per memories. Each upper memory appears to pro-
cess λ ∗ (u, α) requests, even when the actual num-
ber of requests is lower. On the database server
side, each ORAM server stores homomorphically en-
crypted data (
∑
Enc(d1), ...,
∑
Enc(dλ∗(u, α))) from
the corresponding upper memory. This prevents the
CSP from knowing how many requests each upper
memory is processing.
3.3 Flow of Dummy Access Generation
As input, the algorithm accepts a set E = ε
1
, ..., ε
w
consisting of w homomorphically encrypted values.
Figure 1: MORADO’s System Model Architecture.
Each encrypted value ε
i
is defined as ε
i
= Enc(r
i
),
where Enc is an encryption function applied to
the corresponding original request r
i
. Additionally,
the algorithm requires a target lower memory set
M
lower
= m
lower
1
, ..., m
lower
α
and seed values S = ε
o
1
, ε
o
2
for dummy access generation as input parameters.
The expected output is an indistinguishable assign-
ment of these requests to the target lower memorys.
Phase 1. Access Aggregation: The first phase exe-
cutes system-wide aggregation of encrypted requests.
Specifically, the cumulative value Σε for each lower
memory within all upper memory m
upper
is initialized
to zero. Subsequently, for each lower memory m
lower
j
(1 ≤ j ≤ α), its upper memory m
upper
i
is identified,
and the encrypted value ε
j
is added to the cumulative
value Σε of lower memory m
lower
j
.
Phase 2. Dummy Access Calculation: The second
phase determines the number of dummy accesss re-
quired for privacy protection. For each upper mem-
ory m
upper
i
, the number of non-zero lower memorys λ
i
is calculated. Here, λ
i
represents the crucial metric
of how many lower memorys within m
upper
i
contain
actual requests. Subsequently, the maximum value
λ
∗
= max
1≤i≤u
λ
i
across all upper memorys is de-
rived. This λ
∗
functions as a fundamental parameter
defining the system-wide privacy protection level and
plays a decisive role in the subsequent dummy access
generation process.
Phase 3. Request Processing: The third phase
implements a two-stage refined processing for
each upper memory m
upper
i
. The first stage fo-
cuses on real request processing: for each lower
memory m
lower
j
holding aggregated requests Σε
j
,
an aggregate request(Σε
j
, m
lower
j
) is issued to
ORAM client i. This processing enables secure
transfer of real requests. The second stage handles
dummy access generation and issuance, processing
each index j from λ
i
+ 1 to λ
∗
. During this stage,
a lower memory m
lower
is randomly selected, and
an XOR operation ε
o
= ε
o
1
⊕ ε
o
2
is applied. The re-
sulting value is transmitted to ORAM client i via
aggregate request(ε
o
, m
lower
). Finally, either ε
o
1
or ε
o
2
in seed value S is probabilistically replaced with
ε
o
.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
638

Algorithm 1: MORADO.
Input: Set of encrypted values
E = {ε
1
, ..., ε
α
} where ε
i
= Enc(r
i
)
Target lower memory set
m
lower
= {p
1
, ..., p
α
}
Seed values S = {ε
o
1
, ε
o
2
}
Output: Indistinguishable m
lower
1 Phase 1: access aggregation
2 foreach upper memory m
upper
i
do
3 foreach lower memory m
lower
j
in m
upper
i
do
4 Σε ← 0
5 end
6 end
7 for j ← 1 to α do
8 Identify m
upper
i
containing m
lower
j
9 Σε
m
lower
j
← Σε
m
lower
j
+ ε
j
10 end
11 Phase 2: dummy access Calculation
12 foreach upper memory m
upper
i
do
13 Calculate λ
i
← number of non-zero lower
memorys in m
upper
i
14 end
15 λ
∗
← max
1≤i≤u
λ
i
16 Phase 3: Request Processing
17 foreach upper memory m
upper
i
do
// Stage 1: Process real
requests
18 foreach lower memory m
lower
j
with
Σε
j
̸= 0 in m
upper
i
do
19 aggregate request(Σε
j
, m
lower
j
) to
ORAM client i
20 end
// Stage 2: Generate and
process dummy accesss
21 for j ← λ
i
+ 1 to λ
∗
do
22 Randomly select lower memory
m
lower
in m
upper
i
23 ε
o
← ε
o
1
⊕ ε
o
2
24 aggregate request(ε
o
, m
lower
) to
ORAM client i
25 Replace either ε
o
1
or ε
o
2
with ε
o
in S
Randomly.
26 end
27 end
3.4 Security Analysis
We prove the security of the MORADO in the fol-
lowing mathematical indistinguishability. In Morado,
an access request R
access
in the form (id, Enc(s), c)
is submitted from DOs. Let D
view
represent the
state (view) of the database prior to R
access
, where
D
view
consists of the aggregate values in all lower
memories. The proxy server generates the updated
view D
′
view
after R
access
. Then, CSP (adversary) A
receive both D
view
and D
′
view
with id and Enc(s).
Then, the proxy server gets the corresponding lower
memory m
lower
= Π(c), and chooses another c
′
̸= c
such that m
lower’
= Π(c
′
) ̸= m
lower
randomly. Both
m
lower
and m
lower’
are submitted to A . The adver-
sary guesses which of m
lower
or m
lower’
corresponds
to access R
access
. The mathematical indistinguishabil-
ity requires that for any probabilistic polynomial-time
adversary A for all possible m, N, and R
access
:
Pr[A(V
D
, V
′
D
, id, Enc(s),m
lower
, m
lower’
) = m
lower
]
(5)
≤
1
2
+ ε(δ) (6)
In this Equation, ε(·) is a mask mechanism and δ
is the security parameter. The adversary downloads
view D
view
from the proxy server. In MORADO,
D
view
contains a sequence of ORAM accesss, and
contain the DO’s ID. Lower memories is in the form
(id
upper
, id
lower
), where id
upper
and id
lower
represent
the upper memory ID and lower memory ID within
the upper memory. After downloading D
view
, the ad-
versary sends the ID to the proxy server, and the proxy
server returns the correct lower memory m
lower
=
(id
upper
, id
lower
) and a false lower memory m
lower’
=
(id
′
upper
, id
′
lower
) for the adversary to estimate between
m
lower
and m
lower’
. In the worst case, the adversary
is enable to match the correct access ID j within the
batch with ID, but the adversary cannot distinguish
between id
upper
and id
′
upper
. The adversary also is not
able to distinguish between id
lower
and id
′
lower
, this is
based on the mathematical security provided by the
ORAM. Then, ORAM determines whether the access
sequences having id
lower
and id
′
lower
are the same or
different. It means, the adversary cannot distinguish
between m
lower
and m
lower’
, and MORADO guaran-
tees indistinguishability.
4 EVALUATION
This experiment use a 2016 ride record dataset ob-
tained and processed from the NYC Taxi and Limou-
sine Commission and synthetic data. This dataset
contains approximately 2.08 million records, with
each record consisting of pickup timestamps and GPS
location information for taxi rides. By dividing the
Memory-Saving Oblivious RAM for Trajectory Data via Hierarchical Generation of Dummy Access over Untrusted Cloud Environment
639
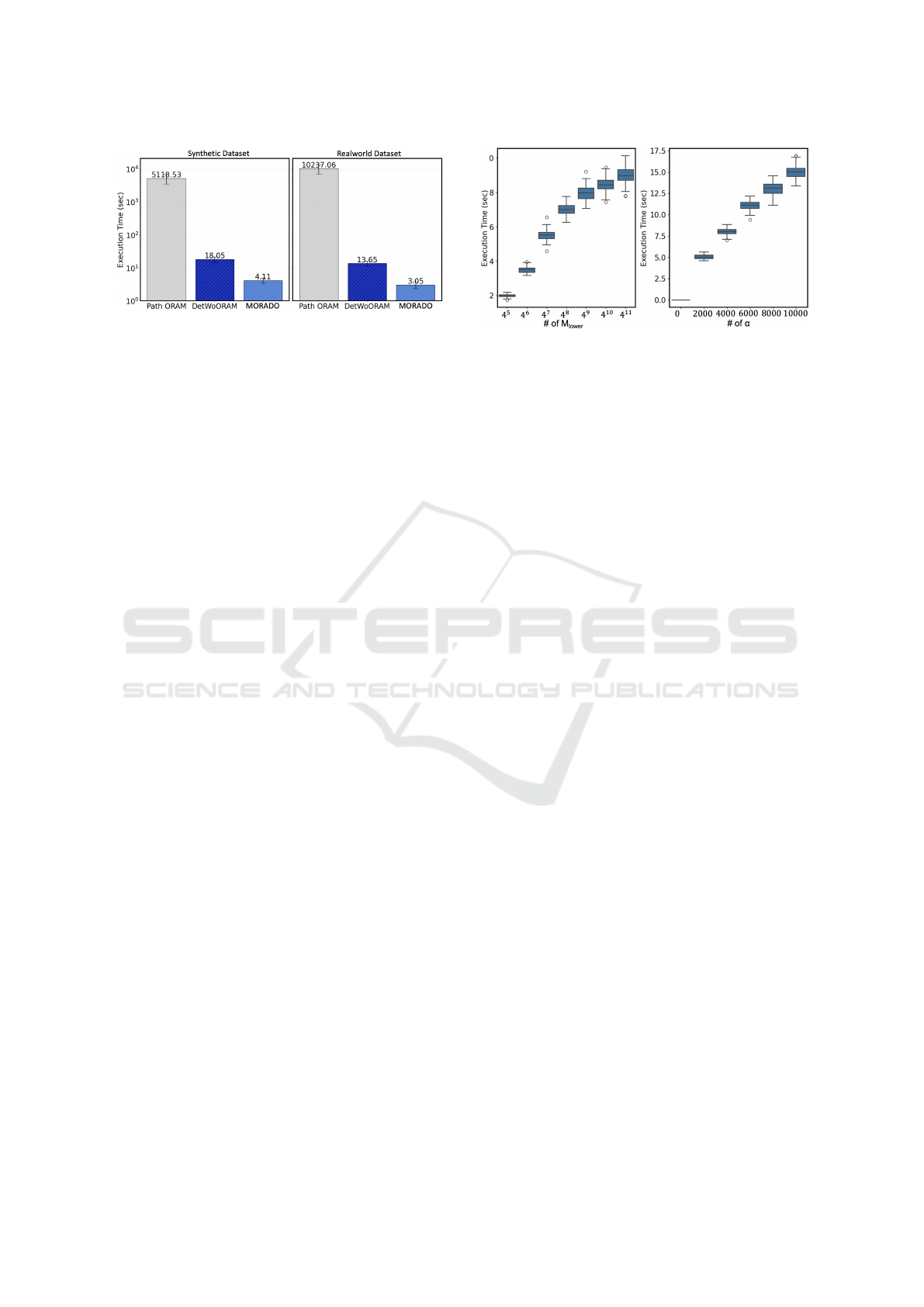
Figure 2: Execution Time.
latitude and longitude points into sufficiently small,
equal-sized waypoints grids and excluding inacces-
sible areas, we ultimately obtained 16,367 location
grids.
4.1 Execution Time
As the Figure 2 showing, the proposed method sig-
nificantly faster than DetWoORAM, which is faster
than Path ORAM. In the synthetic dataset, while Path
ORAM takes approximately 5118.53 seconds to exe-
cute, DetWoORAM requires only 18.05 seconds, and
the proposed method achieves an even shorter time of
4.11 seconds. Similar trends are observed with real-
world datasets, where Path ORAM takes 10237.06
seconds, compared to DetWoORAM’s 13.65 sec-
onds and the proposed method’s 3.05 seconds, show-
ing substantial improvements. Overall, the proposed
method achieves a 51.39% reduction compared to
using DetWoORAM alone. This is because the
DetWoORAM-only approach requires more decryp-
tion operations for each access and experiences re-
dundant updates. What’s particularly noteworthy is
that in both datasets, the improvement from Path
ORAM to DetWoORAM is dramatic (orders of mag-
nitude), and the optimization from DetWoORAM to
the proposed method achieves about a 4x performance
improvement. This demonstrates the high practicality
of the proposed method.
The left boxplot in Figure 3 evaluates the scalabil-
ity of the MORADO framework with respect to the
total number of M
lower
. The graph measures the pro-
cessing time for 1000 accesses while varying M
lower
from 2
10
to 2
22
. The right boxplot in Figure 3 evalu-
ates the system’s scalability when varying the total of
accesses α. It examines how processing time changes
as the number of accesses increases from 0 to 10000,
and the graph shows that the increase in processing
time gradually becomes more moderate as the number
of accesses grows. A notable point is that even with
the current implementation, 10000 accesses can be
processed within about 17.5 seconds, suggesting that
Figure 3: Overhead of access Processing.
further performance improvements can be expected
through parallelization of database query processing.
4.2 Storage Cost
The analysis demonstrates both the bandwidth
charges incurred between TEE and database, and
the primary storage costs for each component, based
on 1,000 access operations. From the graph, we
can see that for TEE storage costs, Path ORAM is
about 35 units and DetWoORAM is about 32 units,
while MORADO shows a slight increase to about 45
units. On the other hand, for database storage costs,
while Path ORAM is very high at about 4,000 units,
DetWoORAM is about 1,500 units, and MORADO
achieves a significant reduction to about 1,200 units.
The baseline proposed method without redundant up-
dates exceeds both DetWoORAM and Path ORAM in
terms of bandwidth (included storage costs). The pro-
posed method shows increased storage costs on TEE
primarily due to dummy accesses used to hide access
distribution between SPs. However, since the pro-
posed method is based on homomorphic encryption, it
saves network bandwidth during transfers. A partic-
ularly noteworthy point is that the proposed method
(MORADO) achieves approximately 70% reduction
in database storage costs compared to Path ORAM.
This represents a significant advantage in building
practical systems.
5 RELATED WORK
There are many approaches to realizing privacy-
preserving data access. In this section, we explain
different approaches to this problem with and without
TEEs.
In threat models where database administrator
(DBA) are considered adversaries, homomorphic en-
cryption is known as a promising approach. Homo-
morphic encryption is a cryptographic method that
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
640

Figure 4: Storage Cost.
enables computations on encrypted data, allowing for
aggregation and statistical processing without decryp-
tion. In particular, encrypted databases utilizing ho-
momorphic encryption can respond to queries while
keeping the data encrypted (Bian et al., 2023; Poddar
et al., 2016; Popa et al., 2011). However, as pointed
out by Isram et al. (Islam et al., 2012), encrypted
databases can still leak information to DBAs through
access patterns during memory operations. In en-
crypted database searches, the client sends encrypted
search keywords to the server, and the server per-
forms the search using these encrypted values. While
the documents themselves are encrypted, the mapping
of which encrypted keywords are contained in which
documents must be stored on the server side to enable
searching. As a result, the server can learn patterns
about which documents are returned when searching
with particular encrypted keywords.
In threat models where CSP are considered adver-
saries, TEE approaches have garnered attention. TEE
is a technology that provides a trusted execution envi-
ronment, with hardware-based implementations like
Intel SGX being widely used. Using TEE enables
isolation of programs and data running on the cloud,
even from CSP. There is also substantial research
on implementing databases within TEE-generated en-
crypted memory (enclaves) rather than using homo-
morphic encryption (Yang et al., 2024; Suzuki et al.,
2024; Yoshimura et al., 2023; Vinayagamurthy et al.,
2019). However, like homomorphic encryption-based
encrypted databases, information can still leak to the
CSP through access patterns during memory deploy-
ment. TEE (such as Intel TDX or AMD SEV-SNP)
executes protected virtual machines or processes, but
memory management (paging) must depend on the
host OS. This is due to TEE physical memory ca-
pacity limitations, the need for efficient memory man-
agement, and integration with OS-level resource man-
agement. Consequently, information about which
memory pages are accessed, when page faults oc-
cur, and page replacement patterns is exposed, allow-
ing attackers to infer program execution flow, observe
memory access patterns, and collect information at
the cache line level. As a result, control flows like
conditional branches and data-dependent memory ac-
cess patterns are exposed, enabling attackers to in-
fer program behavior and data characteristics through
side-channel attacks, potentially leaking privacy in-
formation. Neither HE nor TEE methods can pre-
vent access pattern leakage. This is why ORAM is
being researched as a technique to conceal access
patterns. There are various oblivious protocols, in-
cluding those that make data packets unidentifiable.
Notable examples include Oblivious Transfer(Rabin,
2005), which allows a receiver to obtain specific in-
formation from multiple pieces of information held
by the sender without the sender knowing which in-
formation was selected. It can be used for decoupling
statistic from data volume(Sasada et al., 2023; Sasada
et al., 2022). Oblivious Message Routing(Kirman and
Martinez, 2010), which prevents information leakage
through communication pattern analysis by conceal-
ing message sources and destinations along the com-
munication path.
6 CONCLUSION
This research paper presents a novel approach to
protecting trajectory data in cloud computing envi-
ronments through a memory-saving ORAM imple-
mentation. The proposed method successfully ad-
dresses the challenges of securing sensitive location
data while maintaining system efficiency. By imple-
menting a hierarchical memory structure that man-
ages both trajectory-level and point-level access pat-
terns, the solution achieves significant performance
improvements over existing approaches. The exper-
imental results demonstrate reduction in storage cost
compared to PathORAM, while maintaining robust
security measures against potential threats from CSP.
However, our security model has vulunerability in
collusion attack between DOs and CSP. First, gen-
erate security parameter δ pseudonymous IDs in our
system. Then, during a short time period id
upper
, emu-
late access from these DOs regarding the target lower
memory m
lower
. If the victim DO id sends a access
during the same period, the colluding CSP succeed in
determining whether m
lower
is the target lower mem-
ory of id’s access by validating whether the total of
ORAM accesses in this update round is δ or δ + 1.
Our future work is prevention from this attack by in-
creasing the cost of making pseudonymous IDs or by
mitigating attack via increasing the number of autho-
rized DOs.
Memory-Saving Oblivious RAM for Trajectory Data via Hierarchical Generation of Dummy Access over Untrusted Cloud Environment
641

ACKNOWLEDGEMENTS
This research was partly supported by JSPS KAK-
ENHI Grant Numbers JP22J23910 and the Daiichi-
Sankyo ”Habataku” Support Program for the Next
Generation of Researchers, NAIST Senju Monju
Project.
REFERENCES
Bian, S., Zhang, Z., Pan, H., Mao, R., Zhao, Z., Jin, Y.,
and Guan, Z. (2023). He3db: An Efficient and Elastic
Encrypted Database via Arithmetic-And-Logic Fully
Homomorphic Encryption. In Proceedings of the
2023 ACM SIGSAC Conference on Computer and
Communications Security, pages 2930–2944.
Falk, B. H., Nema, R., and Ostrovsky, R. (2023). Linear-
Time 2-Party Secure Merge from Additively Homo-
morphic Encryption. Journal of Computer and System
Sciences, 137:37–49.
Goldreich, O. and Ostrovsky, R. (1996). Software Protec-
tion and Simulation on Oblivious RAMs. Journal of
the ACM, 43(3):431–473.
Halderman, J. A., Schoen, S. D., Heninger, N., Clarkson,
W., Paul, W., Calandrino, J. A., Feldman, A. J., Appel-
baum, J., and Felten, E. W. (2009). Lest We Remem-
ber: Cold-Boot Attacks on Encryption Keys. Commu-
nications of the ACM, 52(5):91–98.
Intel (2023). Intel Trust Domain Extensions (Intel
TDX) Module v1.5 Base Architecture Specification.
https://www.intel.com/content/www/us/en/developer/
articles/technical/inteltrust-domain-extensions.html.
Islam, M. S., Kuzu, M., and Kantarcioglu, M. (2012).
Access Pattern Disclosure on Searchable Encryption:
Ramification, Attack and Mitigation. In Network and
Distributed System Security Symposium, volume 20,
page 12. Citeseer.
Kirman, N. and Martinez, J. F. (2010). A Power-Efficient
All-Optical On-Chip Interconnect Using Wavelength-
Based Oblivious Routing. ACM Sigplan Notices,
45(3):15–28.
Li, L. and Datta, A. (2017). Write-Only Oblivious RAM-
Based Privacy-Preserved Access of Outsourced Data.
International Journal of Information Security, 16:23–
42.
Liu, Z., Huang, Y., Li, J., Cheng, X., and Shen, C. (2018).
DivORAM: Towards a Practical Oblivious RAM with
Variable Block Size. Information Sciences, 447:1–11.
Moataz, T., Mayberry, T., and Blass, E.-O. (2015). Constant
Communication ORAM with Small Blocksize. In
Proceedings of the 22nd ACM SIGSAC Conference on
Computer and Communications Security, pages 862–
873.
Poddar, R., Boelter, T., and Popa, R. A. (2016). Arx: A
Strongly Encrypted Database System. IACR Cryptol.
ePrint Arch., 2016:591.
Popa, R. A., Redfield, C. M., Zeldovich, N., and Balakr-
ishnan, H. (2011). CryptDB: Protecting Confidential-
ity with Encrypted Query Processing. In Proceedings
of the twenty-third ACM symposium on operating sys-
tems principles, pages 85–100.
Rabin, M. O. (2005). How to Exchange Secrets with
Oblivious Transfer. IACR Cryptology ePrint Archive,
2005(187).
Roche, D. S., Aviv, A., Choi, S. G., and Mayberry,
T. (2017). Deterministic, Stash-Free Write-Only
ORAM. In Proceedings of the 2017 ACM SIGSAC
Conference on Computer and Communications Secu-
rity, pages 507–521.
Sasada, T., Taenaka, Y., and Kadobayashi, Y. (2022).
Decoupling Statistical Trends from Data Volume on
LDP-Based Spatio-Temporal Data Collection. In
2022 IEEE Future Networks World Forum, pages
262–269. IEEE.
Sasada, T., Taenaka, Y., and Kadobayashi, Y. (2023). Obliv-
ious Statistic Collection with Local Differential Pri-
vacy in Mutual Distrust. IEEE Access, 11:21374–
21386.
Stefanov, E., Dijk, M. v., Shi, E., Chan, T.-H. H., Fletcher,
C., Ren, L., Yu, X., and Devadas, S. (2018). Path
ORAM: An Extremely Simple Oblivious RAM Pro-
tocol. Journal of the ACM, 65(4):1–26.
Suzuki, T., Sasada, T., Taenaka, Y., and Kadobayashi,
Y. (2024). Mosaicdb: An efficient trusted/untrusted
memory management for location data in database.
The Sixteenth International Conference on Advances
in Databases, Knowledge, and Data Applications,
pages 1–6.
Vinayagamurthy, D., Gribov, A., and Gorbunov, S. (2019).
Stealthdb: a scalable encrypted database with full sql
query support. Proceedings on Privacy Enhancing
Technologies.
Yang, X., Yue, C., Zhang, W., Liu, Y., Ooi, B. C., and Chen,
J. (2024). Secudb: An in-enclave privacy-preserving
and tamper-resistant relational database. Proceedings
of the VLDB Endowment, 17(12):3906–3919.
Yitbarek, S. F., Aga, M. T., Das, R., and Austin, T. (2017).
Cold Boot Attacks Are still Hot: Security Analysis of
Memory Scramblers in Modern Processors. In 2017
IEEE International Symposium on High Performance
Computer Architecture, pages 313–324. IEEE.
Yoshimura, M., Sasada, T., Taenaka, Y., and Kadobayashi,
Y. (2023). Memory efficient data-protection for
database utilizing secure/unsecured area of intel sgx.
The Sixteenth International Conference on Advances
in Databases, Knowledge, and Data Applications,
pages 45–50.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
642
