
Anomaly Detection for Traffic Management Purposes at Urban
Intersections Using Infrastructure-Generated Vehicle-to-X Messages
Ina Partzsch, Adrien Bellanger
a
, Michael Kl
¨
oppel-Gersdorf
b
, Rutuja Mohekar,
Friedrich Trauzettel and Thomas Otto
Fraunhofer IVI, Fraunhofer Institute for Transportation and Infrastructure Systems, Dresden, Germany
{ina.partzsch, adrien.bellanger, michael.kloeppel-gersdorf, rutuja.mohekar, friedrich.trauzettel,
thomas.otto}@ivi.fraunhofer.de
Keywords:
Traffic Management, Vehicle-to-Everything Communication, Intersections.
Abstract:
Reliable detection of problematic system states in traffic management poses a significant challenge. Fail-
ures in detection can result in the inability to intervene in a timely manner, while excessive detection may
lead to operator fatigue, causing critical information to be ignored amidst an overload of irrelevant messages.
Light-controlled intersections represent both safety and efficiency-critical locations within urban traffic net-
works. Anomalies in these traffic system units can manifest at various levels: technically/physically within the
control systems (actuators, sensors, communication technology), at the traffic data level (reliability and com-
pleteness of collected traffic data), and in traffic observation (unusual traffic flows, unusual objects). Anomaly
detection occurs across these different levels using various methods (technical and algorithmic). Vehicle-to-
Everything (V2X) communication provides an additional data source for monitoring the correct and efficient
operation of traffic signal systems. This paper presents strategies for leveraging the diverse messages from
V2X communication to identify unusual system states across these levels. We demonstrate our approaches at
an urban intersection within the Digital Testbed Dresden.
1 INTRODUCTION
Intersections are critical components of urban road
networks with regard to efficiency and safety. As con-
flicts in these areas are a main reason for severe urban
accidents (Destatis, 2022) as well as bottlenecks for
the overall throughput of a network, effective traffic
flow and incident management is a major task at ur-
ban intersections.
Traffic monitoring has therefore been studied for
decades (Aymerich and Novo, 1992), and a broad
range of detectors is available for this task (Klein,
2020).
An emerging additional source is the growing
V2X communication with standardized messages al-
lowing all traffic participants, including the infra-
structure, to share information about the current traffic
situation.
There is a steadily growing number of cities im-
plementing the necessary communication infrastruc-
ture at signalized intersections (Auerswald et al.,
a
https://orcid.org/0009-0002-8345-427X
b
https://orcid.org/0000-0001-9382-3062
2019). In Europe, the European C-Roads initiative
(C-Roads Germany, 2024) has advanced the standard-
ization and implementation of V2X messages, in-
cluding cross-border testing. Since 2019, the Digital
Testbed Dresden has been part of this initiative, mark-
ing the transition of C-ITS to urban test sites. Conse-
quently, C-Roads serves as a foundation for further
scientific projects, such as STREAM
1
.
On the other hand, the number of vehicles
equipped with the necessary communication equip-
ment is rising as well (Yu et al., 2022).
As already stated, urban traffic management in-
cluding online detection of incidents and anomalies
has been studied for decades. To our knowledge, us-
ing V2X messages for reliable anomaly detection in
productive urban traffic monitoring is, however, an
open issue.
In this paper, we will discuss the current state of
the art concerning V2X communication as well as
anomaly detection in traffic monitoring in Section 2.
We will outline a methodology for using standardized
1
Project reference: https://www.europa-frdert-sachsen.
de/de/projekte/49528
Partzsch, I., Bellanger, A., Klöppel-Gersdorf, M., Mohekar, R., Trauzettel, F. and Otto, T.
Anomaly Detection for Traffic Management Purposes at Urban Intersections Using Infrastructure-Generated Vehicle-to-X Messages.
DOI: 10.5220/0013404700003941
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 11th International Conference on Vehicle Technology and Intelligent Transport Systems (VEHITS 2025), pages 565-570
ISBN: 978-989-758-745-0; ISSN: 2184-495X
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
565

V2X messages as a basis for anomaly detection in
Section 3 and show its application at an urban inter-
section of the Digital Testbed Dresden in Section 4.
The paper is concluded in the final section.
2 STATE OF THE ART
Conventional traffic monitoring relies on various
types of traffic flow detectors, such as induction
loops, radar, and infrared sensors. These devices
are typically embedded in the road surface or posi-
tioned alongside the roadway to collect data on ve-
hicle counts, speeds, and classifications. Induction
loops, for example, detect the presence of vehicles
by measuring changes in inductance caused by the
metal mass of vehicles passing over them. While
these methods have been effective for many years,
they have limitations in terms of coverage, flexibility,
and the granularity of data collected.
As traffic management systems evolve, the inte-
gration of V2X communication presents significant
advantages over conventional methods. V2X commu-
nication units can generally be divided into Road-Side
Units (RSUs), which are, e.g., installed at (signalized)
intersections, and On-Board Units (OBUs), which are
mounted in various types of vehicles, like passenger
cars, buses or trams. The following are key types
of V2X messages currently available (Rondinone and
Correa, 2018) and operational in the Testbed Dres-
den ((Strobl et al., 2019), (Auerswald et al., 2019),
(Kl
¨
oppel-Gersdorf et al., 2021)):
• Map Extended Message (MAPEM): This mes-
sage contains detailed information about the
topology of an intersection, including lane config-
urations, road geometry, and other relevant traffic
features.
• Signal, Phase and Timing Extended Message
(SPATEM): This message provides information
on the current signal status of traffic lights at
an intersection, informing vehicles of the phase
and timing of signals to optimize traffic flow and
safety. In addition, SPATEM may also contain
prognosis data on future traffic light states, fa-
cilitating Green-Light Optimized Speed Advisory
(GLOSA).
• Cooperative Awareness Message (CAM): This
message conveys the current status of traffic par-
ticipants, including their position, speed, and di-
rection, enabling vehicles to maintain awareness
of their surroundings.
• Collective Perception Message (CPM): This
message includes information about objects de-
tected by traffic participants and infrastructure, fa-
cilitating a shared understanding of the environ-
ment and enhancing situational awareness.
• Decentralized Environmental Notification
Message (DENM): This message includes infor-
mation about possibly dangerous road situations
like traffic jams, broken down vehicles, etc.
Such messages directly aid in the detection of
anomalies.
V2X technology significantly extends the detec-
tion range and facilitates real-time data fusion from
diverse sources, including vehicles and infrastructure.
This integration allows for a more comprehensive un-
derstanding of traffic conditions, ultimately leading to
enhanced traffic flow, safety, and efficiency.
An anomaly within any road monitoring system is
identified when there is a deviation from the expected
state across multiple levels of analysis. Anomaly de-
tection have been established based on conventional
detection methods, leveraging metrics such as the
Level of Service as defined by (Transportation Re-
search Board, 2000) and (FGSV, 2015). V2X mes-
sages however deliver information at a much more de-
tailled level, such as vehicle trajectories. Trajectories
have not been reflected in current standards.
In the TrafficIQ project (von der Ruhren et al.,
2011), a methodology centered on data quality moni-
toring has been developed, emphasizing that high data
quality is crucial for accurate and reliable anomaly
detection.
However, to our knowledge, the application of
V2X technology for anomaly detection has been lim-
ited, as seen in (Kl
¨
oppel-Gersdorf et al., ), which fo-
cuses on Level of Service (LoS) calculations.
This paper aims to present a comprehensive ap-
proach to evaluating urban traffic detection setups,
with a particular focus on incorporating V2X mes-
sages for anomaly detection.
3 METHODOLOGY FOR
DETECTING ANOMALIES
BASED ON V2X
The methodology for detecting anomalies in con-
nected and automated driving systems leverages the
extensive data provided by V2X communication.
High data quality is essential for reliable anomaly de-
tection. Therefore, the initial step toward anomaly de-
tection is establishing a data monitoring framework.
Anomalies are defined as deviations from expected
data in terms of both quality and content (e.g., traf-
fic events)
VEHITS 2025 - 11th International Conference on Vehicle Technology and Intelligent Transport Systems
566

3.1 General Approach for Anomaly
Detection
The established method of data quality monitors
(von der Ruhren et al., 2011) can be applied to V2X
communication as follows:
1. Technical Availability: Ensuring that detection
systems are operational and functioning as speci-
fied. Anomalies may arise from technical failures,
such as RSU outages or sensor malfunctions. De-
vice monitors track the health of individual com-
ponents, including video capture systems and de-
tection software.
2. Data Quality Level: Ensuring that traffic data
streams are available and meet predefined qual-
ity criteria. Anomalies in this context indicate a
loss of data quality, which can stem from inac-
curacies in sensor data or communication disrup-
tions. Monitoring the data streams involves evalu-
ating parameters like sensor data accuracy and the
plausibility of CPM messages.
3. Traffic Event Level: This research focuses on
anomalies in observed traffic situations that devi-
ate from expected patterns. By comparing real-
time traffic data with prior knowledge, unexpected
traffic situations can be identified. This includes
analyzing traffic metrics, such as traffic volumes
and vehicle types, as well as finding anomalies
in traffic scenes. The authors of (Santhosh et al.,
2019) categorized anomalies at traffic event level
in detail.
The process of anomaly detection involves several
key steps, including anomaly definition, data acquisi-
tion, preprocessing, feature extraction, and the appli-
cation and evaluation of machine learning algorithms.
This procedure follows the Cross-Industry Standard
for Data Mining (Chapman et al., 2000).
1. Anomaly Definition: As stated above, anoma-
lies are defined as deviations from the normal
state of traffic monitoring systems, taking into
account technical, functional, and qualitative as-
pects. Although we will discuss this broad spec-
trum of anomalies in the next subsection, we will
focus our measurements and discussions on traffic
quality-related anomalies.
2. Data Acquisition: The initial step involves col-
lecting V2X messages from smart intersections
equipped with RSUs and OBU. These mes-
sages include CAM, CPM, MAPEM, DENM, and
SPATEM.
3. Data Preprocessing: The raw data undergoes
preprocessing to ensure quality and consistency.
This includes handling missing values, filtering
out erroneous data, and synchronizing timestamps
from different sources. The goal is to create a
clean dataset that accurately reflects real-world
conditions.
4. Feature Extraction: Relevant features are ex-
tracted from the processed data to facilitate
anomaly detection. Key features include vehi-
cle speed, trajectory information, lane association,
and temporal data.
5. Machine Learning Algorithms: To identify and
classify anomalies, machine learning algorithms
such as Support Vector Machines (SVM) and
Random Forest can be employed. These models
may be trained on labeled datasets to learn pat-
terns associated with normal and anomalous be-
havior.
By implementing this comprehensive methodol-
ogy, the research aims to enhance situational aware-
ness and safety in traffic environments.
3.2 Anomaly Detection Algorithms
Following concrete anomaly detection algorithms
have been implemented.
Technical Availability. The detection technology
(e.g., RSU, OBU) must be operational and function-
ing according to specifications. Anomalies include
technical failures such as RSU outages or sensor mal-
functions.
Additional metrics used for calculating technical
availability include:
• Public network latency (> 100ms),
• Availability of internal network connection to
RSU (yes/no),
• Availability of internal network connection to
cameras (yes/no),
• Network stack is running on RSU (yes/no),
• Video processing is running (yes/no).
Data Quality. V2X data streams must be avail-
able and meet predefined quality criteria (e.g., accu-
racy, completeness). Anomalies are identified when
data quality falls below these standards, indicating po-
tential errors in traffic reporting.
Traffic Event Level. The primary focus is on un-
expected traffic situations that deviate from the ex-
pected patterns. Anomalies can be detected by com-
paring real-time traffic data against historical patterns
or established norms.
In our current setup we defined following undis-
closed list of anomalies:
Anomaly Detection for Traffic Management Purposes at Urban Intersections Using Infrastructure-Generated Vehicle-to-X Messages
567

• Speed Associated Anomalies: Deviations in ve-
hicle speed from expected norms
– Overspeeding Anomaly: For this work we used
50 km/h as boundary to detect overspeeding at
the intersection. This is the official speed limit
for that intersection.
– Static Object Anomaly: Speed of an object
traversing the intersection is recorded as 0 km/h
for an extended amount of time.
• Lane Associated Anomalies:
– Lane Anomaly: Unauthorized lane usage by ve-
hicles based on the definitions in the MAPEM
for that intersection.
– U-turn Anomaly: Unauthorized u-turn based
on the authorized lane changes defined in the
MAPEM for that intersection.
• Traffic Flow Anomalies: Irregularities in traffic
counts that deviate from expected distributions.
– Traffic Count Irregualrities: Traffic volume per
direction shows major deviation from hourly
normal for a typical similar day.
– Traffic Count Proportions: Percentage of
trucks amongst all detected vehicles exceeding
historical levels, in the given case exceeding
15%.
While this work focusses on the usage of CPM, an
earlier study demonstrated the usage of CAM for LoS
monitoring in (Kl
¨
oppel-Gersdorf et al., ). If LoS ex-
ceeds certain predefined values, a LoS anomaly could
also be defined.
Further traffic scene specific anomalies could also
be defined, such as persons at critic regions of the in-
tersection, larger groups of persons on the road or an
abnormal distribution of recognized vehicle types, as
well as abnormal forms of trajectories of any object.
4 RESULTS AND DISCUSSION
4.1 Data Collection
The anomaly detection methodology was applied
during Rutuja Mohekar’s master’s thesis (Mohekar,
2024). Within the framework of our SmartTrack in-
tersection, our second smart intersection in the Digi-
tal Testbed Dresden (the first one had been presented
by (Kl
¨
oppel-Gersdorf et al., 2021)), we collected
available V2X messages during the months June to
July 2024, especially CAM, CPM and MAPEM.
This urban intersection is located at the junction of
Bergstraße, Mommsenstraße, and Haeckelstraße. At
Figure 1: Overview of SmartTrack Intersection (Lan-
deshauptstadt Dresden, 2024).
the top of a building belonging to the Technical Uni-
versity Dresden, a Flir Dual Aid Camera has been in-
stalled to monitor traffic in the entire conflict area of
this intersection. A sketch of the setup is shown in
Fig. 1.
4.2 Detected Traffic Anomalies
During the anomaly detection analysis, various traf-
fic flow anomalies were identified in a one-hour as-
sessment. The analysis reveals that the distribution of
anomalies strongly correlates with the distribution of
vehicles: the more vehicles counted, the more anoma-
lies are detected. An overview of the anomaly distri-
bution can be found in Fig. 2.
Detecting these anomalies is crucial for under-
standing and improving traffic management at urban
intersections.
A large proportion of static objects were left-
turning vehicles. These turns regularly led to stop-
ping vehicles in the conflict area of the intersection, as
the vehicles had to wait for conflicting traffic streams.
These vehicles are currently labeled as ”Static Object
Anomalies”, as they are static objects in the intersec-
tion area. In future approaches, we will also use the
SPAT message and the stopping duration to classify
the type of static object anomaly.
VEHITS 2025 - 11th International Conference on Vehicle Technology and Intelligent Transport Systems
568
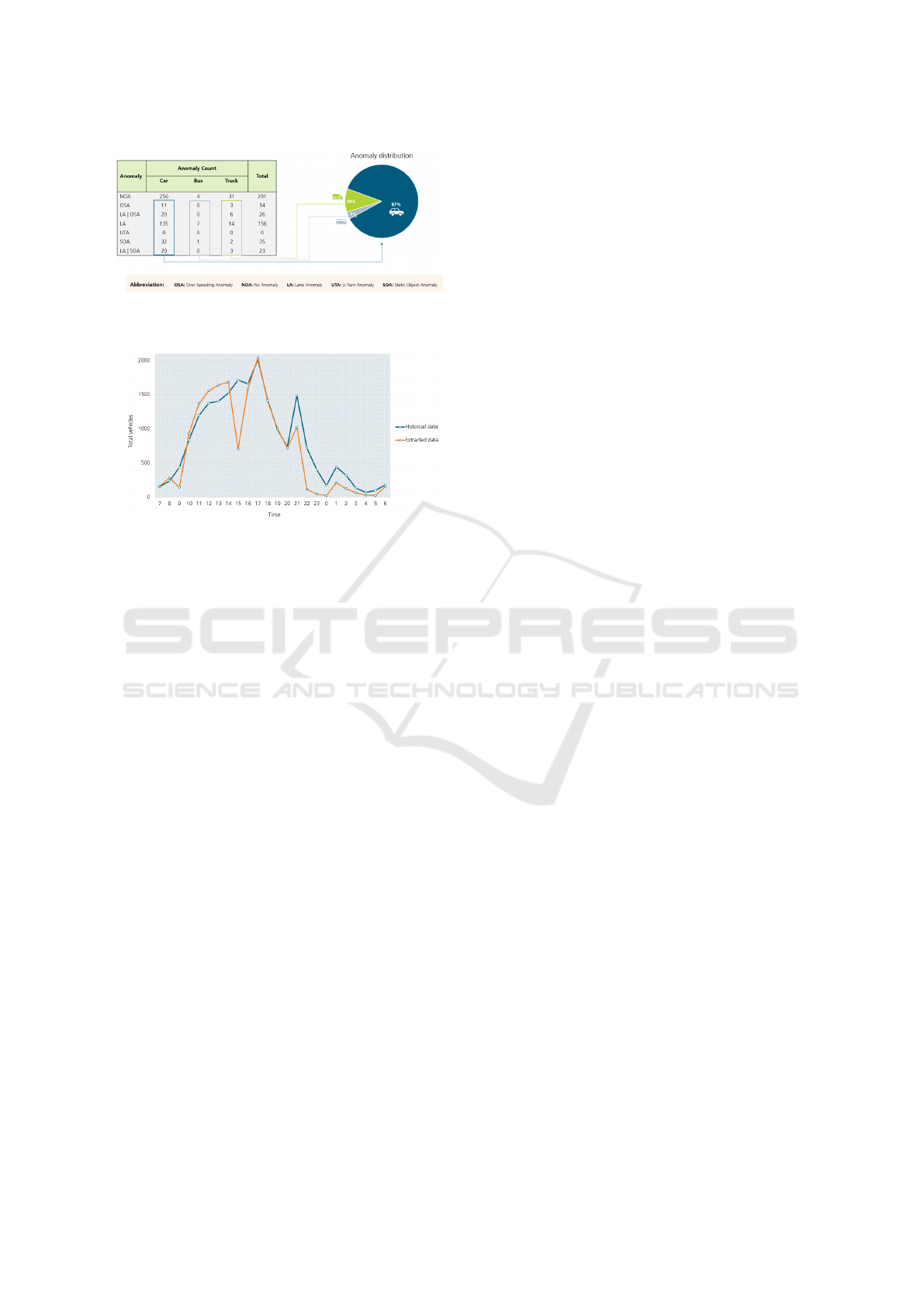
Figure 2: Distribution of detected anomalies per anomaly
type and vehicle type.
Figure 3: Comparison of inductive loop counts and CPM
traffic flow showing traffic flow anomaly.
One example of a detected flow anomaly is de-
picted in Fig. 3. To determine traffic flow anoma-
lies, we compared the incoming V2X data stream with
data from nearby inductive loops. On the day depicted
in Fig. 3, we encountered a considerable drop in the
number of vehicles around 15:00. For that case, we
can show an anomaly in the V2X data stream, which
might have occurred due to technical reasons. The in-
ductive loop data show the inductive loop counts for
that day as an example of historical data for that site.
However, mean values for the current day’s category
(day of the week, days in conjunction with holidays,
seasons, events) could also be used for comparison.
4.3 System Quality Monitoring
The identified anomalies serve not only for detecting
traffic issues but also for monitoring system quality.
Analyzing the anomalies allows for the identification
of potential algorithmic problems that could impair
the efficiency of traffic detection.
Key issues identified include:
• Geolocation Issues: Difficulties in accurate geo-
location can lead to incorrect detections, particu-
larly with speed and lane anomalies.
• Tracking Issues: Insufficient tracking of vehicles
can result in anomalies not being correctly identi-
fied, thereby affecting the reliability of the system.
By continuously monitoring system quality and an-
alyzing anomalies, strategies can be developed to
enhance algorithm performance and improve overall
traffic safety.
4.4 Key Findings
Following key findings can be stated:
• Anomaly Detection Success: The research suc-
cessfully identified various types of anoma-
lies, including speed-associated anomalies, lane-
associated anomalies, and general traffic count
anomalies. The application of machine learning
algorithms, specifically Support Vector Machines
and Random Forest, demonstrated robust frame-
works for detecting these anomalies effectively.
• Traffic Behavior Insights: The analysis revealed
that the majority of detected anomalies were at-
tributed to cars, aligning with the expected dis-
tribution of vehicle types. The absence of U-
Turn Anomalies indicated compliance with traf-
fic regulations, while the presence of Static Object
Anomalies suggested areas for refining detection
algorithms to reduce false positives.
• Temporal Variations: The study highlighted sig-
nificant variations in traffic volumes across dif-
ferent times of the day, emphasizing the impor-
tance of temporal factors in traffic anomaly de-
tection. Such insights can inform traffic manage-
ment strategies, including signal timing adjust-
ments during peak hours.
5 CONCLUSION & OUTLOOK
The described findings provide valuable insights for
traffic engineers and system operators. By leverag-
ing V2X data, the proposed anomaly detection frame-
work can enhance situational awareness, allowing for
more proactive traffic management and safety mea-
sures at intersections. The ability to identify and
categorize anomalies in real time supports the de-
velopment of smarter, safer transportation networks.
Above, using V2X messages deliveres an appropriate
possibility to detect Vulnerable Road Users (VRUs)
without additional sensors.
In conclusion, this paper contributes to the ad-
vancement of cooperative and automated driving sys-
tems by demonstrating the potential of V2X-based
anomaly detection. The methodologies developed lay
the groundwork for future innovations in smart city
infrastructure, with the ultimate goal of enhancing ur-
ban traffic safety and efficiency.
While the research achieved its objectives, certain
limitations were noted, including the reliance on spe-
Anomaly Detection for Traffic Management Purposes at Urban Intersections Using Infrastructure-Generated Vehicle-to-X Messages
569

cific vehicle types equipped with V2X technology and
challenges related to data completeness.
With a limited amount of data, the value of using
ML approaches is also limited. While we have cre-
ated an initial proof of concept for this topic, a com-
plete application for larger and more reliable data sets
remains a goal for the future.
This approach was tested at one intersection
within the Digital Testbed Dresden. Since this testbed
consists of further RSU-equipped intersections, we
will apply this approach to other intersections with
different traffic detection setups. This demonstrates
the flexibility of the described approach.
Future work should focus on expanding the
dataset to include a broader range of traffic partici-
pants, as well as improving algorithms to handle more
complex or rare anomaly types. The current work
does not use all available V2X information, e.g., the
phase information in the SPATEM could be used to
detect red-light violations and to specifically label
static vehicles which have to wait during left-turns.
ACKNOWLEDGEMENTS
This research is financially supported by the EU and
the Freestate of Saxony during the project “Secured
traffic data for reliable and efficient automated mobil-
ity (STREAM - SIFCO)”.
FhGenie was used for improving spelling and
style (Fraunhofer, 2023).
REFERENCES
Auerswald, R., Dod, M., Franke, L., Fritzsche, R., Haber-
jahn, M., Jungmann, A., Kl
¨
oppel-Gersdorf, M.,
Krems, J. F., Lorenz, S., Kreißig, I., et al. (2019).
Heterogeneous infrastructure for cooperative driving
of automated and non-automated connected vehicles.
In Smart Cities, Green Technologies and Intelligent
Transport Systems, pages 270–296. Springer.
Aymerich, M. and Novo, A. (1992). Madrid critical inter-
sections antiblocking strategies. In Road Traffic Mon-
itoring, 1992 (IEE Conf. Pub. 355), pages 70–.
C-Roads Germany (2024). C-Roads Germany accessed on
28.11.2024.
Chapman, P., Clinton, J., Kerber, R., Khabaza, T., Reinartz,
T., Shearer, C., and Wirth, R. (2000). Crisp-dm 1.0.
Technical report, The CRISP-DM Consortium.
Destatis (2022). Verkehrsunf
¨
alle 2021. Statistisches Bun-
desamt.
FGSV (2015). Handbuch f
¨
ur die Bemessung von Straßen-
verkehrsanlagen Teil S - Stadtstraßen Standard,
Forschungsgesellschaft f
¨
ur Straßen- und Verkehrswe-
sen e.V.
Fraunhofer (2023). FhGenie: The Fraunhofer-
Gesellschaft launches an internal AI chatbot.
https://www.fraunhofer.de/en/press/research-
news/2023/august-2023/fhgenie-the-fraunhofer-
gesellschaft-launches-an-internal-ai-chatbot.html.
Accessed: 2024-10-24.
Klein, L. (2020). Traffic Flow Sensors: Technologies, Op-
erating Principles, and Archetypes.
Kl
¨
oppel-Gersdorf, M., Trauzettel, F., Koslowski, K., Pe-
ter, M., and Otto, T. (2021). The Fraunhofer CCIT
Smart Intersection In 2021 IEEE International In-
telligent Transportation Systems Conference (ITSC),
pages 1797–1802. IEEE.
Kl
¨
oppel-Gersdorf, M., Partzsch, I., Chen, H., and Otto, T.
Real-time level of service for signalized urban inter-
sections based on vehicle-to-everything communica-
tion. In Proceedings of the 7th Conference on Sus-
tainable Mobility (CSUM 2024).
Mohekar, R. (2024). Anomaly detection based on v2x mes-
sage in connected-automated driving. Master’s thesis,
Technical University of Dresden, Faculty of Computer
Science, Chair of Traffic Process Automation. Sub-
mitted in partial fulfillment of the requirements for the
degree ”Master of Science”.
Rondinone, M. and Correa, A. (2018). Definition of v2x
message sets. Technical Report D5.1, Universidad
Miguel Hern
´
andez (UMH). Editor: Michele Rondi-
none.
Santhosh, K. K., Dogra, D. P., and Roy, P. P. (2019).
Anomaly detection in road traffic using visual surveil-
lance: A survey. CoRR, abs/1901.08292.
Strobl, S., Kl
¨
oppel-Gersdorf, M., Otto, T., and Grimm, J.
(2019). C-ITS Pilot in Dresden – Designing a modu-
lar C-ITS architecture In 2019 6th International Con-
ference on Models and Technologies for Intelligent
Transportation Systems (MT-ITS), pages 1–8.
Landeshauptstadt Dresden (2024). Themenstadtplan Dres-
den. accessed on 19.12.2024.
Transportation Research Board (2000). Highway capacity
manual. Standard, National Research Council.
von der Ruhren, S., Schimandl, F., Gabloner, S., Spangler,
M., Weisheit, T., K
¨
uhnel, C., Maier, P., Landwehr, M.,
Ludwig, A., Zingsem, A., F
¨
orster, G., and Ryssel, T.
(2011). Traffic IQ - Pilotprojekt Informationsqualit
¨
at
im Verkehrswesen. Technical report, Bundesminis-
terium f
¨
ur Wirtschaft und Technologie.
Yu, G., Li, H., Wang, Y., Chen, P., and Zhou, B. (2022).
A review on cooperative perception and control sup-
ported infrastructure-vehicle system. Green Energy
and Intelligent Transportation, 1(3):100023.
VEHITS 2025 - 11th International Conference on Vehicle Technology and Intelligent Transport Systems
570
