
A User-Centered Design Approach to Develop a Privacy Awareness
Application
Anika Tabassum Era
1
, Tanjila Kanij
2 a
, John Grundy
3 b
and Md Al Mamun
1
1
Rajshahi University of Engineering & Technology, Rajshahi, Bangladesh
2
Swinburne University of Technology, Melbourne, Australia
3
Monash University, Melbourne, Australia
Keywords:
User-Centered Design, Persona, Prototype, Usability Evaluation.
Abstract:
There are more than 50 million Facebook users in Bangladesh. Despite its wide usage, Facebook has resulted
in negative impacts on individuals and the community, mostly due to improper use of the media. In our prior
research, from a survey of almost 200 Facebook users in Bangladesh, we found that some Facebook users
had (1) diverse demographic characteristics, (2) varied levels of understanding, and (3) reluctance to learn the
features needed help to understand the features to use Facebook properly. In this research, we designed a low-
fidelity prototype with interactive video tutorials and quizzes to help them improve their awareness of privacy
on Facebook, especially with complicated privacy settings. We conducted a detailed usability evaluation and
collected feedback from eleven participants and adjusted the prototype based on the received feedback. Once
developed the application will be helpful to improve the overall Facebook experience of users in Bangladesh.
We also reflect on the experience of the User-Centered Design (UCD) and recommend how UCD can be
planned for other similar user groups.
1 INTRODUCTION
Bangladesh was 8th globally in terms of Facebook
users April 2024 (Dixon, 2024). Due to the re-
cent “Digital and Smart Bangladesh” initiatives of the
government in the country, digital devices have be-
come easily accessible and Facebook is competent to
be used by anyone (Knautz and Baran, 2016). All
these made Facebook the most popular social me-
dia in the country which has brought numerous ben-
efits to the lives of people in Bangladesh, includ-
ing F-commerce to empower women (Zabeen et al.,
2013; Basak, 2022). However, Facebook has had
many negative consequences for society, including
spreading misinformation and breach of privacy (Ali,
2020). A major reason behind the negative conse-
quences is an insufficient understanding of privacy,
which is often influenced by the varying digital liter-
acy (Kanij et al., 2023) and complicated privacy set-
tings (Kshetri, 2011).
To understand the perception of privacy among
the general population of Bangladesh, we conducted
a
https://orcid.org/0000-0002-5293-1718
b
https://orcid.org/0000-0003-4928-7076
a broad survey where we identified three groups of
Facebook users - (1) understand the privacy features
and use those properly, (2) do not understand the
privacy features very well and are reluctant to learn
new features, and (3) understand the privacy features,
however, do not use those properly. The second and
third groups of Facebook users needed some help to
improve their privacy protection behavior, for that we
developed an interactive quiz-based application.
As suggested by Grundy et al., diverse user char-
acteristics should be incorporated into the process of
designing and developing any software solution for
diverse end users (Grundy et al., 2020). Therefore, we
followed a User-Centered Design (UCD) approach
to develop an interactive privacy awareness applica-
tion for the diverse Facebook users in Bangladesh.
The UCD approach recommends that solutions be
designed iteratively and incrementally together with
users. In this research, we developed a low-fidelity
interactive privacy awareness application prototype
and evaluated the interface with eleven participants.
Based on their feedback, we improved the applica-
tion. Once developed, the application will help Face-
book users in Bangladesh understand the complex
privacy settings.Reflecting on our UCD process with
692
Era, A. T., Kanij, T., Grundy, J. and Al Mamun, M.
A User-Centered Design Approach to Develop a Privacy Awareness Application.
DOI: 10.5220/0013430100003928
In Proceedings of the 20th International Conference on Evaluation of Novel Approaches to Software Engineering (ENASE 2025), pages 692-699
ISBN: 978-989-758-742-9; ISSN: 2184-4895
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)

Facebook users in Bangladesh, we also recommend
to future researchers and developers how UCD can be
used for other diverse end-user groups.
2 BACKGROUND
User-Centered Design (UCD), introduced by Nor-
man in the 1980s (Norman and Draper, 1986), is
the concept of ensuring user participation through-
out the design process (Abras et al., 2004). Initially
used in Human-Computer Interaction (HCI), UCD
has been adopted to software development method-
ology where end-users are placed at the center of the
process (Lowdermilk, 2013). The benefits of UCD in-
clude the sense of ownership, higher satisfaction, and
chances of adoption by the end-users (Preece et al.,
2015). Some prominent UCD principles are Nor-
man’s seven principles (Norman, 1988), Shnieder-
man’s eight golden rules (Shneiderman, 1986), and
Neilsens’s heuristics (Nielsen, 1995). All the princi-
ples emphasize simplicity, visibility, ease of learning
and use, precise mapping between action and effect,
and feedback and interpretation (Abras et al., 2004).
User Modeling: Persona. A persona represents a
group of end users of a software application (Grudin
and Pruitt, 2002). A persona is often described with
names, images, and demographic information (Pruitt
and Adlin, 2010) and background, goals, interests,
and frustrations (Cooper, 1999). Personas give a
real impression of the end-users and help developers
build empathy with them. Usually, there are three
broad approaches to persona development: qualita-
tive, quantitative, and mixed (Tu et al., 2010). The
qualitative approaches include exploratory user re-
search with a medium sample size to understand end-
user characteristics and behaviour through an itera-
tive process (McGinn and Kotamraju, 2008). Quan-
titative persona development approaches focus on a
large pool of data collected through surveys, online
data sources, and algorithmic analysis (Jansen et al.,
2022). The third and final approach is called the
mixed approach, which combines quantitative and
qualitative approaches, usually targeting one end-user
group such as the elderly (Cooper et al., 2007). One
of the most popular ways of developing personas is
Nielsen’s ten-step process for persona development,
which is considered a generalized mixed method for
developing persona (Nielsen, 2004).
Design Solution: Prototypes. A prototype is an
early-stage design of an application. The design can
be presented as sketches on paper, with diagrams or
the frontend interface. Some of the purposes of hav-
ing prototypes are to communicate the design idea,
to get early feedback to refine the designs, explore
new design ideas, and learn more about the design
space (Camburn et al., 2017). Prototyping can be
iterative, where design is refined through iterations
(Reed Doke, 1990). Prototyping can also be parallel,
where different designs are developed independently
to compare and select (Borowski, 2012).
Usability Evaluation. Usability evaluation is the
process of evaluating the design solution (prototype).
This can be conducted as a laboratory study with or
without real users (heuristic testing), as field studies
to understand the users’ experience, and as a hands-
on measurement to find usability measures (Nayebi
et al., 2012). A usability evaluation including real
users gives them some tasks to complete on the de-
sign solution.
3 RELATED WORK
Privacy and Facebook: Privacy on a social media
platform has always been a matter of concern. How-
ever, after the Cambridge Analytica incident, privacy
related to Facebook brought the issue into the lime-
light (Senate, 2018). A review of Facebook privacy-
related literature indicates that the privacy protec-
tion behavior of Facebook users is influenced by (ei-
ther as causal or as consequential) several aspects
such as “threats”, “understanding of privacy settings
provided by Facebook”, “literacy”, “experience” and
“culture” (Brown, 2020; Nyoni and Velempini, 2018;
Teresa L. Mendoza and Jun P. Mariani, 2022; Alkire
et al., 2019). As the number of Facebook users in
Bangladesh is growing at a very high rate, all of these
aspects are important to study in the context of Face-
book users in Bangladesh. This will help understand
the level of awareness and the consequent behavior
and identify the interventions needed.
Privacy Norm in Bangladesh: Privacy related to
digital devices and internet usage in Bangladesh is in-
fluenced by surveillance, cultural context, and lack of
knowledge and practice (Jay et al., 2018). Mobile de-
vices are often registered to a different person than
the actual phone user (Ahmed et al., 2017b), and de-
vices are shared among the family members (Ahmed
et al., 2017c). A similar practice of device sharing is
also seen in nearby nations such as India and Pakistan
(Sambasivan et al., 2018). Overall, the perception of
privacy differs greatly from that of any Western cul-
ture (Sambasivan et al., 2018). The differences in per-
ceptions of privacy and device sharing practices often
lead to privacy violations, resulting in negative conse-
quences.
Facebook Privacy in Bangladesh: Facebook
A User-Centered Design Approach to Develop a Privacy Awareness Application
693
privacy-related research in Bangladesh can be divided
into two broad themes: (1) studying usage behavior
and (2) suggesting “tips” for safe use of Facebook.
In a recent survey, Rahman found that although most
Facebook users in their sample understood and were
welcoming to the privacy features provided by Face-
book, a few of them practiced those, including chang-
ing passwords, using two-factor authentication, and
checking for alerts (Rahman, 2022). The behaviour
resembles a phenomenon called privacy paradox re-
ported by Barth, and Jong (Barth and de Jong, 2017).
In suggesting Tips for safe usage, Rahman and Ul-
lah provided six privacy settings to protect informa-
tion from being visible to the public and third parties
(Facebook ads) (Rahaman and Ullah, 2013). Ahmed
et al. suggest setting the privacy options depending on
priorities, regularly checking privacy settings, think-
ing before accepting stranger friend requests, restrict-
ing wall posts to friends only, and blocking unneces-
sary or irritating users. They prioritize women Face-
book users, as the majority of victims of cybercrime
were women (Ahmed et al., 2017a). To deal with ha-
rassment and bullying in Facebook groups (especially
against women), the group admins take different ap-
proaches, such as connecting among themselves (Sul-
tana et al., 2020).
Facebook Initiatives: Facebook has initiated the
“We Think Digital” program in the Asia Pacific re-
gion in collaboration with experts (Meta, 2022a). The
core aim of the program is to make a skillful digital
citizen with their open source learning modules and
resources (Meta, 2022c) and knowledge-based ques-
tions (Meta, 2022b). Their web portal for Bangladesh
has a well-organized learning modules, links to the
privacy center of Facebook, and a few videos, how-
ever, these are not interactive (Meta, 2023).
4 APPLICATION DESIGN
In previous research to understand the perceptions
of privacy and the privacy behaviors of Facebook
users in Bangladesh, we conducted an online survey
with 188 Facebook users in Bangladesh (reference re-
moved for anonymous review). From the survey find-
ings, it was clear that Facebook users in Bangladesh
are concerned about their privacy on Facebook. How-
ever, some of them do not understand all the privacy
settings properly. Moreover, those who understand
the privacy settings do not use them properly. It was
also found that some of the Facebook settings are very
complicated, as already reported by Kshetri (Kshetri,
2011). For some users, understanding the settings just
by reading the description was not helpful. We de-
rived the idea of a privacy awareness application from
our survey findings.
4.1 Development of Persona
From the survey responses, we noticed different clus-
ters of Facebook users in the context of privacy. The
first group of users had an in-depth understanding of
the privacy feature and were mostly adults under 42.
A second group of Facebook users mainly over the
age of 42, did not have a good understanding of the
privacy features Facebook provides due to their un-
willingness to learn the settings. However, interest-
ingly, this group of Facebook users also communi-
cated their concerns about hacking, mobile banking-
related problems, and so on. A third group of Face-
book users mainly was from the 13-18 age group who
had some basic understanding of making new con-
nections and tagging, profile locking and two-factor
authentication. However, they do not know about
review-tagged posts and search engine features. We
developed one persona for the second and the third
group of Facebook users as we believe those two
groups required the privacy awareness application.
We followed Nielsen’s ten-step (Nielsen, 2004) ap-
proach to develop personas. Figure 1 represents the
persona of the second group.
Experience
Age: 60 years
Gender: Male
Babu lives with his wife and adult son. He is very near to retirement. As
Babu has no other work after office his son introduced him to Facebook to get
connected with his friends and colleagues. Babu enjoys browsing his news feed,
which has almost become an addiction.
Active Presence on Facebook
Babu’s interests include - political viewpoints and current world affairs. He
considers Facebook as a great medium to gain knowledge regardless of justifying
authentic news. Lately, he has not focused on any real-life socialization rather
he is indulging in Facebook content.
Facebook Common Feature Usage
When Babu finds any interesting video or post regarding politics, he tries to
share his opinion. He gets influenced by other people who comment. The
posts being public, Babu often gets negative messages from other people whose
ideology does not match his. All these unwanted behaviors make him mentally
upset. Despite all these problems, he experienced a wonderful moment, when he
was tagged to a colleague’s post, one of his childhood friends got connected to
him and it made him really happy. His friend happened to be a cousin of his
colleague.
Facebook Privacy Policy Check
When Babu experiences unpleasant situations from random users, can not figure
out how to react. He often gets triggered and sometimes reacts passively to his
family members. Once his account was hacked and later was recovered logging
out of all devices. Since then he has been cautious not to log in to Facebook
from any other device. He is also afraid of trying anything on Facebook, except
reading posts and reacting with Like, Comment, and Share.
Babu
Figure 1: Persona Babu.
ENASE 2025 - 20th International Conference on Evaluation of Novel Approaches to Software Engineering
694

4.2 Specification of Requirements
From the qualitative responses of the survey describ-
ing some of the experiences of the participants with
Facebook privacy settings, especially with compli-
cated ones such as reviewing tagged posts and setting
the audience of each post (interplay with profile au-
dience setting), we identified different scenarios that
could be described to the participants with a video tu-
torial on a mobile application. Moreover, associating
ambiguous scenarios to select the best privacy setting
would make their understanding of the features com-
plete and help them effectively use those on Facebook
itself. A list of primary requirements for the proposed
privacy awareness application is presented in Table 1.
Table 1: Requirements.
1 Video Tutorial
Requirement The application will provide a description of each Facebook pri-
vacy feature with video
Rationale This will help users understand what the feature offers and the
importance of it
Note The video should contain description, demonstrations and exam-
ple scenarios
Source Survey response on review of tagged posts and setting of an au-
dience for posts indicated that users do not understand how these
function
2 Scenario based quiz
Requirement After each video the application should present example scenario
asking for response from the users
Rationale It is difficult to remember and understand the complicated fea-
tures just by knowing those, this feature will help users to logi-
cally work out how the features are used in real-world scenarios
Note Scenarios should be designed in a way that requires users to think
rationally
Source Survey response where users shared their past experiences of not
effectively figuring out what settings to use
4.3 Development of Prototype
We designed a low-fidelity prototype application to
help them describe different privacy features with
video tutorials and scenario-based interactive quizzes.
Considering the personas we developed, we tried to
make the prototype as simple and intuitive as possi-
ble. The prototype was developed based on Nielsen’s
recommendations (Nielsen, 2004). Our prototype was
designed with Figma, a widely accepted tool for pro-
totype design, and developed in both Bangla and En-
glish to cater to different audiences. The prototype is
presented in Figure 2, showing the English interface.
For simplicity, we will describe the English ver-
sion of the prototype; the Bangla version works ex-
actly the same as the English one. The key features of
the prototype included - an introductory view with the
general description of the application, a home page
listing different Facebook features, a tutorial page on
each of the Facebook features (listed on the home
page), an interactive quiz page based on each feature,
and a feedback page for showing the feedback on quiz
response.
Consider the user persona “Babu”. When “Babu”
visits the “PA App” he notices the introduction page
(“PA App - Introduction E”) describing the applica-
tion. Clicking on the “Start” button on this page
“Babu” is taken to the home page view (“PA App -
Homepage E”). The home page contains the list of
Facebook features; for the initial version, we listed
four features of Facebook such as - 1) Passwords, 2)
Friends, 3) Tagging, and 4) Audience. “Babu” can
click one of the features and will be taken to the tu-
torial for the respective feature. For the first iteration,
we developed a video tutorial for the “Audience” fea-
ture only. Therefore, as soon as “Babu” clicks the
option “Audience”, he will be on the “Tutorial page”
(“PA App - Tutorial Page E”). In the “Tutorial page”
(“PA App - Tutorial Page E”), “Babu” can watch the
video tutorial for the “Audience” feature of Facebook.
When “Babu” has completed the video tutorial he can
click on the “Quiz” button to get to the next page.
In the “Quiz” page (“PA App - Quiz Page E”), a
scenario-based incident related to audience settings
on Facebook is presented in the form of a quiz, and
“Babu” is asked what his preferred audience for such
a case. He makes his choice and clicks on the “Feed-
back” button to visit the (“PA App - Feedback Page
E”). This page shows a message that describes what
option would have been appropriate according to the
scenario. The feedback also contains a description of
all the options with an explanation of what would be
appropriate in which scenario.
5 USABILITY EVALUATION
We presented our prototype to several Facebook users
and collected their feedback to refine the prototype.
The evaluation was conducted according to the Hu-
man Research Ethics protocols and consent was col-
lected from all participants before evaluation. There
were a total of 15 questions (11 closed, 4 open-
ended). We used SUS (Brooke, 1995) questionnaires
to collect feedback on usability. Participants were
asked to complete one tutorial and the relevant quiz
in the prototype and answer questions such as how
easy/difficult it was to use and learn, whether they
needed help, how often they would use the applica-
tion, whether the prototype was helpful, and so on.
They also provided feedback on the open-ended ques-
tions on the overall prototype, the challenges and im-
provements. Data was collected using a Google form.
A User-Centered Design Approach to Develop a Privacy Awareness Application
695
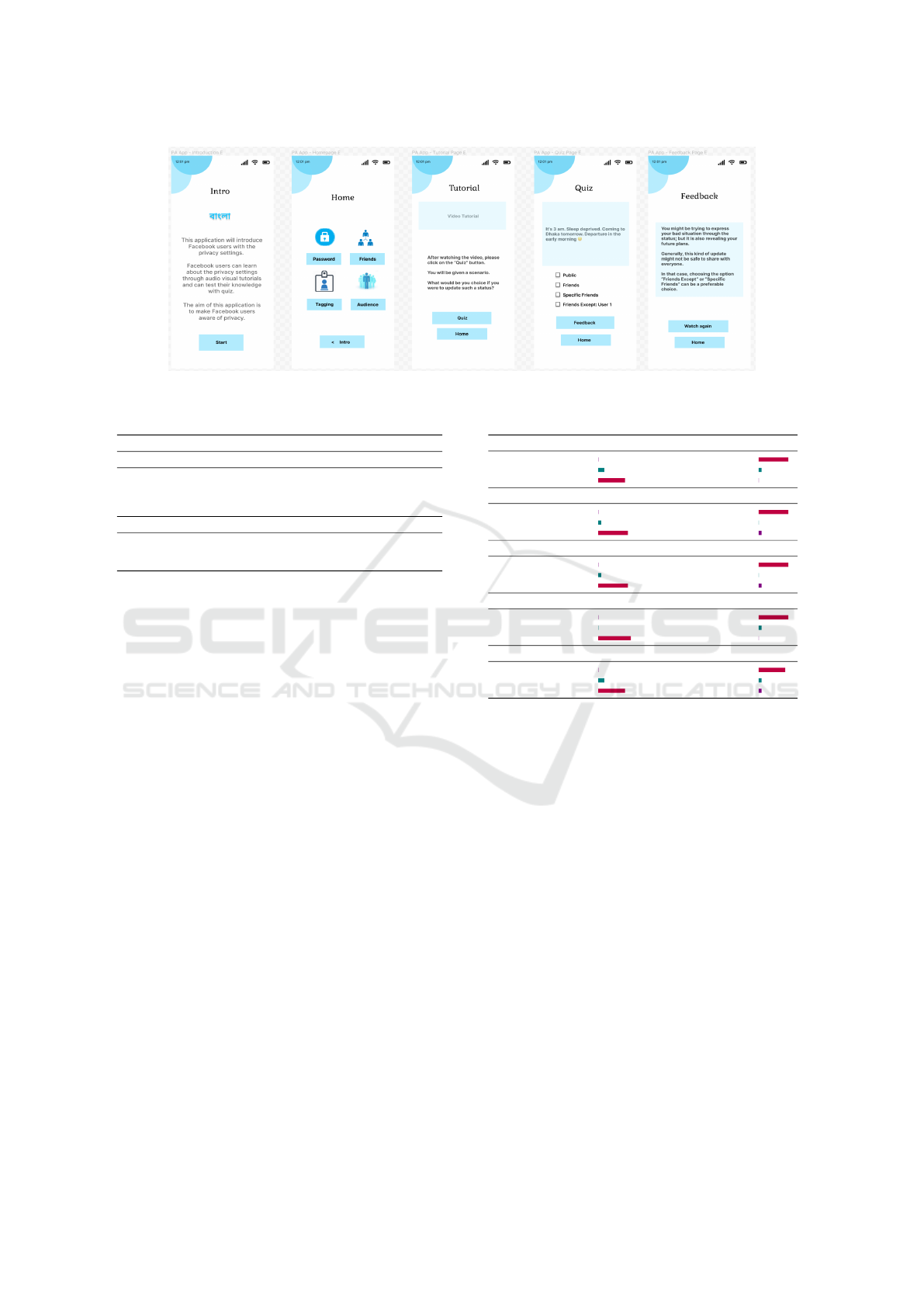
Figure 2: Overview of the Prototype.
Table 2: Evaluation Result on Prototype.
Functionality
Feedback Changes to be made
Personalized quiz Integrate with the Facebook profile of the user or add an introductory quiz
More features Add more topics of tutorial
Involving resourceful persons Recruit UX designers and researchers
More scenarios Add more relevant scenarios for better learning
Usability
Radio button feedback Add hover feature
Old fashioned No change
Color theme No change
Participants were recruited from personal contacts us-
ing convenience sampling. We used Thematic analy-
sis for qualitative data.
There were eleven participants (four male, seven
female) to evaluate the first version of the prototype.
One participant was between 13 and 17 years old, five
were between 18 and 26, four were between 27 and
42, and one was between 43 and 59. We will refer to
them as P1 - P11. All participants except one, said the
difficulty level was either easy or normal. In the open-
ended comments participants provided welcoming re-
sponses. For example, P4 - “It was a good learn. I
made the wrong choice. but later I got to know from
the feedback why I should have chosen otherwise”,
P9 - “Application is well needed. Though I am us-
ing FB for several years now, yet I didn’t know some
of the information”, P10 - “Quite descend applica-
tion. Easy for the new users of social media. Old
people who recently become active in social media
can use this for safety purpose”. The responses to the
closed-ended questions are presented in Table 3. The
five-point Likert scale was converted to a three-point
Likert as there was less diversity in responses. Based
on open-ended responses we derived suggestions to
improve the prototype as listed in Table 2.
Functionality: When asked if they found anything
challenging about the application, most were com-
fortable using it. In response to how we could im-
prove the prototype, most of them said it was all right
except P9 added a valuable comment -“Only if you
Table 3: System Usability Scale Report.
Would Like to Use Frequently? Unnecessary Complex?
Disagree 0 Disagree 10
Neutral 2 Neutral 1
Agree 9 Agree 0
Ease of Usage Technical Person Needed?
Disagree 0 Disagree 10
Neutral 1 Neutral 0
Agree 10 Agree 1
Functions Well Integrated Present of Inconsistency
Disagree 0 Disagree 10
Neutral 1 Neutral 0
Agree 10 Agree 1
Easy to Learn Cumbersome
Disagree 0 Disagree 10
Neutral 0 Neutral 1
Agree 11 Agree 0
Confident to Use Needed to Learn Before Using
Disagree 0 Disagree 9
Neutral 2 Neutral 1
Agree 9 Agree 1
can at first find out what type of post the user usu-
ally posts. Then present the post of the quiz accord-
ing to the user”. Since this prototype is not inte-
grated with the Facebook profile of the user, it is dif-
ficult to provide personalized quiz questions to each
user. The prototype can be improved to either inte-
grate the user’s Facebook profile or present an intro-
ductory quiz at the beginning to understand specific
user preferences. In either case, the feature will need
to be implemented with AI.
Usability: Overall, all participants seemed to be
happy with the usability of the prototype as illustrated
in Table 2. One participant (P5) shared not being able
to interact with the radio button - “I couldn’t under-
stand which radio button I pressed as the radio didn’t
activate”. There were no radio buttons used, however,
the “PA App - Quiz Page” contains check boxes. We
believe the participant was referring to that. We will
add a “hover” feature to let users know what they are
selecting. In reviewing the usability of the prototype,
P4 said “The app style is old-fashioned. Could have
been more interesting and fun” and P8 said - “Maybe
the color combination? I don’t know. I found it just
ENASE 2025 - 20th International Conference on Evaluation of Novel Approaches to Software Engineering
696

okay”. Since both the participants were not specific,
we did not make any changes.
Improvements: Based on the feedback received in
the evaluation phase with the users, we include more
functional requirements to our original set of high-
level requirements. An updated list is presented in
Table 4. The major update is adding an introduc-
tory quiz, as suggested by P9. The quiz will assess
the level of understanding of the privacy features, and
based on the assessment, appropriate tutorials, and as-
sociated scenario-based quizzes will be provided to
the users. We will make the introductory quiz a peri-
odical one so that users can re-check their understand-
ings.
Table 4: New Requirements After Usability Evaluation.
3 An introductory quiz
Requirement The application will contain a quiz on different privacy features
Rationale The quiz will assess the user’s understanding of privacy features
Note The quiz will be presented at the beginning and can be visited
periodically
Source Usability evaluation (P9)
4 Tutorial and scenario based on understanding level
Requirement The application will present the video tutorial and the scenarios
based on the level of understanding of privacy features as as-
sessed by the introductory quiz
Rationale The purpose of the introductory quiz is to assess the level of un-
derstanding of the privacy features, so that users are presented
with tutorials and scenarios matching their understanding
Note This requirement will ensure that expert users are not presented
with simple scenarios and vice versa
Source Usability evaluation (P9)
6 DISCUSSION
We summarize the lessons we have learned and pro-
pose specific recommendations for different phases of
the UCD process. We also suggest future directions
for the development of the designed privacy aware-
ness applications and aim to replicate the study with
more diverse user groups. Figure 3 presents our rec-
ommendations for each UCD phase.
Demonstration of Concepts: From the detailed sur-
vey responses we found that one group of users in-
dicated confidence in the privacy features; however,
from some shared experiences, we found that they
were not using the privacy features properly (despite
saying they understood those). For example, one par-
ticipant said they hesitated to share a photo of hang-
ing out with friends late at night, as this can upset
their mother. However, earlier, they said they un-
derstood how the audience setting feature “friends
except” worked. This example comment indicates
that the participants did not use the setting to ex-
Figure 3: Recommendations for UCD.
clude someone seeing their post. This indicates that
Facebook users in Bangladesh often cannot use their
privacy settings properly, although they understand
them. This implies the necessity of teaching the set-
tings with example cases. Due to the complex na-
ture of the settings, it wasn’t easy to express the sur-
vey questions with words only. As such, we included
diagrams, images, and example cases. Surprisingly,
some of the survey participants indicated that those
were very helpful. This is another motivation behind
developing a privacy awareness application that will
teach the settings and help the users use rational think-
ing to apply those in example scenarios to prepare bet-
ter for real life.
Importance of Persona: We found that according
to the awareness of privacy features and their applica-
tion, there are different groups of users. We found two
groups of users who needed some training on under-
standing the privacy settings. The privacy awareness
application is designed for the customized needs of
these two groups of users. Personas were very helpful
in understanding and empathizing with those diverse
users. For example, the persona in Figure 1 was reluc-
tant to learn new things. These unique characteristics
were considered while designing the prototype. Exist-
ing literature also reported similar experiences (Kanij
et al., 2023).
Low-Fidelity Prototype: The usability evaluation
with the low-fidelity prototype helped communicate
the concept of a tutorial and scenario-based applica-
tion to the users, getting feedback on the design con-
cept, and refining the prototype with new directions
that gravitated toward what the users expected. Since
awareness-building applications, especially for social
media usage (specifically Facebook usage in Bangla),
are not a familiar concept, the prototype with sample
video and quiz helped the users understand the pur-
pose and flow of the privacy awareness application
under consideration. It will be possible without the
prototype. Moreover, users could navigate through
the application interface on the Figma prototype, and
as such, they provided critical feedback on usability,
A User-Centered Design Approach to Develop a Privacy Awareness Application
697

such as colour and highlighting options. Most impor-
tantly, they provided an excellent idea of customiz-
ing the content based on users’ level of understand-
ing. This led to the addition of an introductory quiz to
assess the level of knowledge of privacy features.
User-Centered Design: We presented our experi-
ence of a complete UCD process to design a privacy-
awareness mobile application. From understanding
the context of use to evaluating the prototype, we col-
laborated with the users and found that it is neces-
sary to include them in the process as they add valu-
able insight. Once presented with some artifacts, such
as the prototype, they were able to provide very spe-
cific feedback. Based on our experience, we also rec-
ommend including them in the development process.
We suggest that incremental development approaches
such as Scrum be followed.
Adaptive Application: Our preliminary research
found that Facebook users in Bangladesh have differ-
ent perceptions and levels of knowledge of privacy.
We designed a privacy awareness mobile application
for those who we identified as needing help (not un-
derstanding the privacy setting or being reluctant to
learn). However, during the usability evaluation, one
participant suggested customizing the application’s
content based on the users’ understanding level. To
address the suggestion, we included a quiz that will
assess the user’s level of understanding and present
the content accordingly. In this way, the application
can adapt to the users’ needs. This feature request in-
dicates that similar applications must be designed to
be adaptive to user needs.
Usability Evaluation Feedback: Although we used
the SUS questionnaire to obtain a quantitative mea-
sure of our design, we found that the qualitative feed-
back provided by the users was constructive in (1) re-
fining the design (i.e., ambiguity with check boxes
corrected by using Hoover feature) and (2) finding
new requirements (i.e., suggesting to link Facebook
profile or including a quiz to assess the level of un-
derstanding of the user). From this experience, we
recommend that usability evaluations should not only
rely on quantitative measures, but however, should be
complemented with qualitative feedback.
7 CONCLUSION
Although there are millions of users of Facebook in
Bangladesh, not all of them understand the features
provided by Facebook and consequently can use those
properly. We identified the user groups that need help
understanding Facebook features. We developed a
low-fidelity prototype for a privacy awareness appli-
cation, taking the diverse end user needs in mind, and
collected feedback on the prototype. We reflect on
our overall UCD approach to understanding the con-
text of use, specify requirements, design a prototype,
and evaluate those with the users. Based on the feed-
back received during evaluation, the prototype is re-
fined to reflect user expectations more. We found
that the persona to represent diverse end users and the
low-fidelity prototype to communicate the design idea
were very helpful. Based on the experience we pro-
pose to include representative users in developing and
testing the application.
ACKNOWLEDGEMENTS
Kanij and Grundy are supported by ARC Laureate
Fellowship FL190100035.
REFERENCES
Abras, C., Maloney-Krichmar, D., Preece, J., et al. (2004).
User-centered design. Bainbridge, W. Encyclopedia of
Human-Computer Interaction. Thousand Oaks: Sage
Publications, 37(4).
Ahmed, S., Kabir, A., Sharmin, S., and Jafrin, S. (2017a).
Cyber-crimes against womenfolk on social networks:
Bangladesh context. International Journal of Com-
puter Applications, 174.
Ahmed, S. I., Haque, M., Guha, S., Rifat, M. R., and Dell,
N. (2017b). Privacy, security, and surveillance in the
global south: A study of biometric mobile sim regis-
tration in bangladesh.
Ahmed, S. I., Haque, M. R., Chen, J., and Dell, N. (2017c).
Digital privacy challenges with shared mobile phone
use in bangladesh.
Ali, M. S. (2020). Uses of facebook to accelerate violence
and its impact in bangladesh. Global Media Journal,
18.
Alkire, L., Pohlmann, J., and Barnett, W. (2019). Triggers
and motivators of privacy protection behavior on face-
book. Journal of Services Marketing, 33(1).
Barth, S. and de Jong, M. D. (2017). The privacy paradox –
investigating discrepancies between expressed privacy
concerns and actual online behavior – a systematic lit-
erature review. Telematics and Informatics, 34(7).
Basak, S. (2022). Women entrepreneurship through f-
commerce: A qualitative study in bangladesh. Volume
24.
Borowski, S. M. (June 2012). Compettive prototyping in
the department of defense: Suggestions for a better
approach.
Brooke, J. (1995). Sus: A quick and dirty usability scale.
Brown, A. J. (2020). “should i stay or should i leave?”:
Exploring (dis)continued facebook use after the cam-
ENASE 2025 - 20th International Conference on Evaluation of Novel Approaches to Software Engineering
698

bridge analytica scandal. Social Media + Society,
6(1).
Camburn, B., Viswanathan, V., Linsey, J., Anderson, D.,
Jensen, D., Crawford, R., Otto, K., and Wood, K.
(2017). Design prototyping methods: state of the art
in strategies, techniques, and guidelines. Design Sci-
ence, 3.
Cooper, A. (1999). The inmates are running the asylum:
Why high-tech products drive us crazy and how to re-
store the sanity pearson education.
Cooper, A., Reimann, R., and Cronin, D. (2007). About face
3: the essentials of interaction design. John Wiley &
Sons.
Dixon, S. J. (May 2024). Leading countries based on face-
book audience size as of april 2024.
Grudin, J. and Pruitt, J. (2002). Personas, participatory de-
sign and product development: An infrastructure for
engagement. In Proc. PDC, volume 2.
Grundy, J., Khalajzadeh, H., McIntosh, J., Kanij, T.,
and Mueller, I. (2020). Humanise: Approaches to
achieve more human-centric software engineering. In
ENASE2020. Springer.
Jansen, B., Jung, S.-G., Nielsen, L., Guan, K., and Salmi-
nen, J. (2022). How to create personas: Three persona
creation methodologies with implications for practical
employment. Pacific Asia Journal of the Association
for Information Systems, 14.
Jay, C., MD Romael, H., Pratyasha, S., Shion, G., Nicola,
D., and Ishtiaque, A. (2018). Internet privacy and se-
curity in bangladesh through the lens of “privacy in
context” framework. In CSCW 2018 Privacy in Con-
text Workshop.
Kanij, T., Anwar, M., Oliver, G., and Khalid Hossain, M.
(2023). Developing software for low socio-economic
end users: Lessons learned from a case study of fisher-
folk communities in bangladesh. In ICSE 2023 SEIS.
Knautz, K. and Baran, K. (2016). Facets of Facebook: Use
and Users. De Gruyter.
Kshetri, N. (2011). Privacy and security aspects of social
media: Institutional and technological environment.
Pacific Asia Journal of the Association for Informa-
tion Systems, 3(4).
Lowdermilk, T. (2013). User-centered design: a devel-
oper’s guide to building user-friendly applications. ”
O’Reilly Media, Inc.”.
McGinn, J. and Kotamraju, N. (2008). Data-driven persona
development. In Proceedings of the SIGCHI confer-
ence on human factors in computing systems.
Meta (2022a). We Think Digital. https://wethinkdigital.fb.
com/. Last checked on Oct 05, 2023.
Meta (2022b). We think digital interactive content. https:
//wethinkdigital.fb.com/interactive-content. Last
checked on Oct 04, 2023.
Meta (2022c). We Think Digital Resources. https://
wethinkdigital.fb.com/resources/. Last checked on
Oct 05, 2023.
Meta (2023). We think digital bangladesh. https://
wethinkdigital.fb.com/bd/bd-bd/. Last checked on
Dec 09, 2024.
Nayebi, F., Desharnais, J.-M., and Abran, A. (2012). The
state of the art of mobile application usability evalua-
tion. In CCECE 2012.
Nielsen, J. (1995). 10 usability heuristics for user interface
design.
Nielsen, L. (2004). Engaging personas and narrative sce-
narios.
Norman, D. A. (1988). The design of everyday things. New
York City, NY, USA: Doubleday.
Norman, D. A. and Draper, S. W. (1986). User centered
system design; new perspectives on human-computer
interaction. L. Erlbaum Associates Inc.
Nyoni, P. and Velempini, M. (2018). Privacy and user
awareness on facebook. South African Journal of Sci-
ence, 114.
Preece, J., Sharp, H., and Rogers, Y. (2015). Interaction
Design: Beyond Human-Computer Interaction. Wi-
ley.
Pruitt, J. and Adlin, T. (2010). The persona lifecycle: keep-
ing people in mind throughout product design. Else-
vier.
Rahaman, A. and Ullah, G. M. (2013). Exploration of
influencing factors that effecting facebook privacy
awareness on bangladeshi undergraduate university
students. SSRN Electronic Journal.
Rahman, M. A. (2022). Facebook in bangladesh: Security
and privacy concerns. International Journal of Inno-
vative Research and Publications.
Reed Doke, E. (1990). An industry survey of emerging pro-
totyping methodologies. Information & Management,
18(4).
Sambasivan, N. et al. (2018). ”privacy is not for me, it’s for
those rich women”: performative privacy practices on
mobile phones by women in south asia. In SOUPS
’18.
Senate, U. (2018). Facebook, social media privacy, and the
use and abuse of data: Joint full committee hearing.
Committee on the Judiciary.
Shneiderman, B. (1986). Designing the user interface:
strategies for effective human-computer interaction.
Addison-Wesley Longman Publishing Co., Inc., USA.
Sultana, S. et al. (2020). Understanding the sensibility of
social media use and privacy with bangladeshi face-
book group users.
Teresa L. Mendoza, A., A. R. P. D. and Jun P. Mariani, M.
(2022). Awareness of data security of facebook users
in the philippines. International Journal of English
Literature and Social Sciences (IJELS).
Tu, N. et al. (2010). Combine qualitative and quantitative
methods to create persona. In 2010 3rd International
Conference on Information Management, Innovation
Management and Industrial Engineering, volume 3.
Zabeen, M., Ara, H., and Sarwar, N. (2013). F-commerce
in bangladesh: “venit, vidit, vicit”. IOSR Journal of
Humanities and social sciences, 17.
A User-Centered Design Approach to Develop a Privacy Awareness Application
699
