
Cybersecurity Early Education: A Review of Current Cybersecurity
Education for Young Children
Elham Ebrahimi
a
, Marjorie Pare, Geoff Stoker
b
and Shauna White
Compu , U.S.A.
ebrahimie@uncw.edu, parem@uncw.edu, stokerg@uncw.edu, whitest@uncw.edu
Keywords:
Cybersecurity, Educational Games, Active Learning, k-12 Education.
Abstract:
Cybersecurity education is critical for children growing up in a digital world where learning to navigate the
internet safely is as important as learning to safely cross a busy street. Interacting with engaging games is
an excellent way for children to learn complex cybersecurity concepts. Students are increasingly engaged in
online activities at school, via social media, and on gaming platforms. Cybersecurity education helps them
recognize and avoid potential threats, like phishing scams, online predators, and privacy breaches. Teaching
children to protect their personal information (like names, addresses, and locations) can help prevent iden-
tity theft and reduce the risks of cyberbullying. Furthermore, cybersecurity education fosters digital literacy,
enabling children to understand the broader digital environment, including the ethical use of technology and
the consequences of their online actions. Early exposure to cybersecurity concepts also cultivates interest
in STEM, which opens doors to future technical careers and builds valuable problem-solving and analytical
skills. This article aims to provide an overview of available games on cybersecurity topics for primary and
secondary school students and to describe the implementation of a browser-based game platform for primary
school students.
1 INTRODUCTION
Games are highly effective for teaching complex con-
cepts to younger age groups. They engage children
in natural, enjoyable, and memorable ways, allowing
them to explore, experiment, and build understanding
at their own pace (Lamrani and Abdelwahed, 2020).
More than that, games make learning enjoyable by in-
corporating elements of play. This not only sustains a
child’s attention during creative activities longer than
traditional methods but also makes learning an excit-
ing and interesting journey (Behnamnia et al., 2020).
This is especially beneficial when learning chal-
lenging or abstract topics, as children are more likely
to stick with them. Games encourage hands-on in-
teraction, allowing children to learn by doing rather
than just observing or listening (Yannier et al., 2021).
Complex concepts are often easier to understand
when children can experiment and receive instant
feedback on their actions, which helps them under-
stand cause-and-effect relationships and learn from
mistakes (Alam, 2022). This quick feedback loop en-
a
https://orcid.org/0000-0001-9431-557X
b
https://orcid.org/0009-0001-0495-3162
ables children to self-correct and gain confidence in
tackling complex ideas (Murtazaev and Shukrulloev,
2024).
Moreover, many educational games are designed
to involve problem-solving and decision-making,
which build critical thinking skills (Mao et al., 2022).
For example, math-based puzzles or strategy games
teach logical thinking, strategic planning, and per-
sistence, which are foundational for understanding
more advanced topics (Murtazaev and Shukrulloev,
2024). Games also often feature levels or stages that
increase in difficulty, providing a scaffolded approach
to learning. Children can start with simple tasks that
gradually become more challenging, allowing them
to build foundational knowledge before tackling ad-
vanced concepts (Janson et al., 2020). Additionally,
games often involve visual, auditory, and sometimes
even tactile interactions, engaging multiple senses.
Multi-sensory learning has been shown to improve
memory retention, making it more likely that children
will remember complex information (Aaron, 2017).
Gamification elements like points, badges, and re-
wards boost motivation by giving children a sense
of accomplishment as they progress. This encour-
ages children to continue learning and to push through
822
Ebrahimi, E., Pare, M., Stoker, G. and White, S.
Cybersecurity Early Education: A Review of Current Cybersecurity Education for Young Children.
DOI: 10.5220/0013501000003932
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 17th International Conference on Computer Supported Education (CSEDU 2025) - Volume 1, pages 822-833
ISBN: 978-989-758-746-7; ISSN: 2184-5026
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

challenges, even when faced with complex topics (Al-
sawaier, 2018; Buckley and Doyle, 2016; Chapman
and Rich, 2018). In this paper, we review some of the
existing cybersecurity content and our game-based
platform focused on cybersecurity themes for primary
school students for early cybersecurity education and
training.
2 LITERATURE REVIEW
Importance of k-12 Cybersecurity Education. Stu-
dents are increasingly engaged in online activities at
school, via social media, and on gaming platforms.
Cybersecurity education helps them recognize and
avoid potential threats like phishing scams, online
predators, and privacy breaches. Teaching children
to protect their personal information (like names, ad-
dresses, and locations) can help prevent identity theft
and reduce the risks of cyberbullying. Furthermore,
cybersecurity education fosters digital literacy, en-
abling children to understand the broader digital envi-
ronment, including the ethical use of technology and
the consequences of their online actions (Quayyum
et al., 2021).
There is currently a paucity of cybersecurity cur-
ricula designed to teach students in grades 3-5, due
to their basic computer skills and knowledge (Zepf
and Arthur, 2013). Additionally, young children of-
ten learn better in early years so introducing cyberse-
curity in elementary schools can offer them greater
opportunities for future careers. It is critical that
we offer early exposure to cybersecurity principles to
protect young children from “negative experiences”
(Zepf and Arthur, 2013; National Science Foundation,
2020; Giannakas et al., 2019). Offering curricula ear-
lier may improve student awareness of the dangers of
cyberattacks while also introducing them to topics as-
sociated with cybersecurity. From an early age, stu-
dents are exposed to and engaged in online practices.
For instance, by age 11, 50% of children have their
own social media accounts, 64% have access to the
Internet via their own laptop or tablet, and 38% have
access to the Internet via their phone (Influence Cen-
tral, 2016).
There are three primary areas of vulnerability that
children encounter online: content, contact, and con-
duct. Middle school youth are susceptible to all three
and start to engage in inappropriate cyber activity
such as bullying or hacking (Keeley and Little, 2017).
The grades 3-5 population allows researchers to mit-
igate developmental and behavioral, and technology-
access issues associated with older students, and to
longitudinally assess the impact of the training on ear-
lier students’ perceptions of cybersecurity once they
reach middle school. Research suggests that students
begin to focus on their academic ability as a “fixed
quality” in middle and high school grades, and there-
fore, withdraw from subjects for which they lack con-
fidence (Jethwani et al., 2016; Rhodewalt and Tra-
gakis, 2002), or sense of belonging (Margolis and
Fisher, 2002; Jethwani et al., 2017). This effort cre-
ates the scaffolding to engage students earlier in crit-
ical STEM areas of cybersecurity and supports ex-
ploratory learning in later grades. Concurrently, this
directly correlates to students’ interests in cyberse-
curity: educators’ lack of cybersecurity self-efficacy
(Agamba and Keengwe, 2012; Ertmer et al., 2003).
XR and Game-Based Learning (GBL) can serve to de-
mystify cybersecurity and build self-efficacy for edu-
cators and students alike.
eXtended Reality and advantages of XR and Gam-
ification. Teaching and learning have always been
intertwined. Learning occurs more naturally when
teaching is optimal and fits the learning style of the
learners (Proserpio and Gioia, 2007). Thus, educators
teaching the virtual generation should take advantage
of new technologies, such as internet-based tools and
games to increase participation and fulfill learning ob-
jectives. Research has shown that virtual technolo-
gies could enhance student’s performance (Scoville
and Buskirk, 2007; Han, 2020). Consequently, game-
based technology and strategies have gained momen-
tum in educational settings and have been shown to
increase knowledge retention (Putz et al., 2020; Ortiz-
Rojas et al., 2019; Kim et al., 2018). Virtual tech-
nologies or eXtended Reality (XR) refers to the spec-
trum of experiences including Augmented Reality
(AR), Mixed Reality (MR), and Virtual Reality (VR).
In general, Extended Reality includes any human-
machine interactions generated by computer technol-
ogy and wearables. XR has wide-ranging applica-
tions that include a large training and education sub-
set. Within XR, students can visualize abstract con-
cepts and complete related hands-on tasks rather than
imagining them (Trindade et al., 2002; Javidi, 1999;
Christou, 2010). A growing body of research indi-
cates that when students interact and control events in
extended reality environments, they become more ac-
tively involved in constructing knowledge through an
immersive experience rather than learning by lecture
or reading expository text (Roussou, 2004; Dewey,
2004).
Cybersecurity Workforce Development. Improving
STEM skills is a current and future need that must be
addressed to solve the social and economic challenges
our society faces (English, 2016). This goal’s ur-
gency is based on the shortages in the current and fu-
Cybersecurity Early Education: A Review of Current Cybersecurity Education for Young Children
823

ture STEM workforce (Hopkins et al., 2014; Charette,
2015). According to the Committee on STEM Educa-
tion of the National Science and Technology Council
(2018) (on STEM Education, 2018), STEM skills are
important not only for STEM careers, but all career
paths in general as these skills can help people to be
successful in their lives.
Elementary-High School Cybersecurity Educa-
tion is more effective if it is grounded in situated cog-
nition theory, which emphasizes “knowing is doing”
and that how knowledge is applied is only as impor-
tant as to how and where the knowledge will be ap-
plied (Brown et al., 1989; Putnam and Borko, 2000).
Problem-Based Learning (PBL) has garnered positive
outcomes for students in the areas of collaboration
(Boaler, 1997; Penuel, 2006), student engagement
(Belland et al., 2006; Brush and Saye, 2008), critical
thinking, and problem-solving skills (Mergendoller
et al., 2006). PBL requires students to solve realistic
problems, gain control over learning, and use teach-
ers as inquiry coaches, while working collaboratively
(Darling-Hammond et al., 2015; Thomas, 2000). Re-
search indicates that PBL can increase long-term re-
tention and improve test scores and problem solv-
ing (Ravitz, 2009). Further, PBL can offer students
learning scaffolds that enrich inquiry and increase
student engagement (Brush and Saye, 2000; Ertmer
and Simons, 2006; Jonassen, 2011; Mergendoller and
Thomas, 2005; Tamim and Grant, 2013). The integra-
tion of technology into PBL assists teachers because it
can promote self-discovery and independence (Grant,
2002; Krajcik et al., 2014).
Additionally, science education available to stu-
dents in rural, low-income areas further aggra-
vates student engagement, particularly for those with
diverse learning needs (Potkonjak et al., 2016).
For instance, instruction traditionally delivered in a
textbook-lecture format frequently involves a sub-
stantial amount of independent, self-regulated anal-
ysis of expository writing and worksheet activities
(Scruggs and Mastropieri, 1994a; Scruggs and Mas-
tropieri, 1994b; Scruggs et al., 2010). Students often
experience difficulty in a learning environment where
they are rapidly introduced to new theories, facts, and
vocabulary in an inconsistent and unpredictable man-
ner (Downing et al., 2002) and many practicing gen-
eral education teachers have little training or expe-
rience in identifying and accommodating the needs
of students with special needs (Moon et al., 2012;
McGinnis and Stefanich, 2007; Norman et al., 1998;
Villanueva et al., 2012). Proper integration of tech-
nologies into the curriculum are shown to overcome
some of these obstacles (Merchant et al., 2014; Hew
and Cheung, 2010; Annetta et al., 2009; Sim
˜
oes et al.,
2013; de Marcos et al., 2016; Potkonjak et al., 2016;
Hsieh et al., 2008).
3 CURRENT CYBERSECURITY
EDUCATION EXAMPLES
Young children often learn better in their early years,
so early exposure to cybersecurity principles must be
offered before they reach middle school to protect
them from negative experiences. Most current cyber-
security education for children is predominantly pas-
sive, where students watch videos and follow along
with minimal interaction, limiting engagement and re-
tention of knowledge. Where interactive games do
exist, they are often designed for older children and
are too complex or inaccessible for younger learners.
This creates a gap in educational tools for elementary-
aged students who need simplified, hands-on expe-
riences to grasp basic cybersecurity principles (e.g.,
online safety). Additionally, most activities fail to in-
corporate any form of knowledge assessment, leav-
ing educators and parents without clear indicators of
how well children understand and can apply the ma-
terial. This lack of interactive, age-appropriate con-
tent combined with the absence of measurable learn-
ing outcomes highlights a critical need for better-
designed cybersecurity education activities for young
audiences.
There are two main categories of cybersecurity ed-
ucation for elementary school students, each with dis-
tinct approaches to teaching and engagement:
• Passive Learning. In this method, students re-
ceive information in a more traditional, one-
directional manner, without significant interaction
or hands-on participation. The focus is on absorb-
ing knowledge through methods such as lecture-
based learning, reading informational materials,
and watching videos or demonstrations. While
this approach is effective for conveying founda-
tional concepts and theoretical knowledge, it may
not fully engage younger learners or encourage
deep understanding. However, it can serve as a
useful introduction to cybersecurity topics before
moving on to more interactive approaches.
• Active or Gamified Learning. This approach ac-
tively involves students in the learning process,
encouraging critical thinking, problem-solving,
and participation. It often incorporates game el-
ements such as challenges, points, levels, and re-
wards to make learning more engaging and in-
teractive. By immersing students in hands-on
activities, puzzles, simulations, or cybersecurity-
ERSeGEL 2025 - Workshop on Extended Reality and Serious Games for Education and Learning
824

themed games, this method fosters deeper un-
derstanding and retention of cybersecurity princi-
ples. Gamified learning also promotes collabora-
tion, decision-making, and a proactive approach
to online safety, making it particularly effective
for younger audiences who benefit from experi-
ential learning.
Both methods have their place in cybersecurity ed-
ucation. While passive learning provides essential
knowledge and background information, active or
gamified learning helps students internalize and apply
cybersecurity concepts in a meaningful way. A bal-
anced approach that incorporates both strategies can
create an effective and engaging cybersecurity cur-
riculum for elementary school students.
Here are some examples of passive and ac-
tive/gamified methods used to teach cybersecurity to
young audiences with a significant number of sub-
scribers.
Tynker, a company dedicated to teaching K-12
student coding, provides an expansive website with a
variety of activities and games focused on several dif-
ferent aspects of coding and software development.
Tynker offers both a subscription-based website ser-
vice and an app store product. Starting with pre-
made coding blocks, players follow lessons to create
graphics and learn code. The scaffolded learning ap-
proach allows individuals to complete goals at their
own pace. As users improve, they are introduced to
different coding languages, statistics, and data analyt-
ics, as well as more expansive art and design tools for
creative coding (from BYJU’S, 2024). Users also get
the freedom to create interactive games and tools out-
side of lessons. The site allows users to create projects
and share them with the community, so students re-
ceive feedback from others and are not just graded
based on completion.
Unfortunately, the curriculum relating to cyberse-
curity and internet safety is relegated to videos with
quizzes based on the source material. These cartoons
provide fantastical scenarios in which to introduce cy-
bersecurity concepts and provide educational material
that discusses them in a way that users can under-
stand. These videos, while helpful, do not provide
an enriching interactive experience. Going through
the actions of what makes an individual’s data secure
could solidify the concept in the user’s minds.
Trend Micro Cyber Academy is a collection of
videos related to cybersecurity concepts such as pass-
word safety, scams, and privacy. This 12-episode
series educates learners on the importance of inter-
net safety and how to keep yourself protected (Mi-
cro, 2022). These videos are packed with information
from start to finish, which allows them to provide a
Figure 1: A collection of children’s educational videos from
Tynker, Trend Micro, and Malwarebytes, respectively. The
colorful visuals and approachable material keep viewers en-
gaged despite the passive learning style.
dense summary of the topics. However, the videos
lack much narrative and can potentially lose viewer
attention if the concepts are hard for an individual to
grasp. The passive nature of videos lacks the oppor-
tunity to assess viewer retention as well, so parents
and educators are unsure of what viewers have learned
without supplemental material.
LearningMole is a website offering a variety of
educational videos for young learners, ranging from
history and geography to science and math. These
videos break down topics for viewers in a cartoony,
easy-to-digest format (Mole, 2024). The informa-
tion relating to cybersecurity and password safety is
limited to only a few videos, but they are simple
and easy to understand. More experienced learners
might not feel engaged with the material Learning-
Mole provides, as each video provides an introductory
overview of each topic.
MalwareBytes, the antivirus protection company,
offers one video teaching young learners about cy-
bersecurity. This video emphasizes the dangers of
being unprotected by creating a scenario focused on
the attacker’s perspective. It provides a series of ex-
ample situations that children are susceptible to, and
demonstrate ways they can be exploited (Malware-
bytes, 2021). Although helpful, this video lacks ed-
ucational material explaining how to protect against
these attacks. The solution suggested to create a
Cybersecurity Early Education: A Review of Current Cybersecurity Education for Young Children
825
strong password lacks extra information on how to
build strong passwords, and telling kids to ”avoid any-
thing that looks weird” without showing examples
could lead to some confusion in the future without
additional guidance.
Smile and Learn is a company offering educa-
tional videos and interactive activities for children on
a wide array of topics. Smile and Learn offers their
material in 6 different languages, and allows for per-
sonalized goals to be set for each student (Smile and
learn, 2021). This company offers some educational
videos on cybersecurity and internet safety, with a fo-
cus on phone use and practicing good social habits.
These videos offer recommendations and warnings in
a fun way to encourage viewers to protect themselves
online. These videos go over a wide array of situ-
ations involving cyberbullying and how to maintain
your first mobile device, but lack information for a
slightly younger audience.
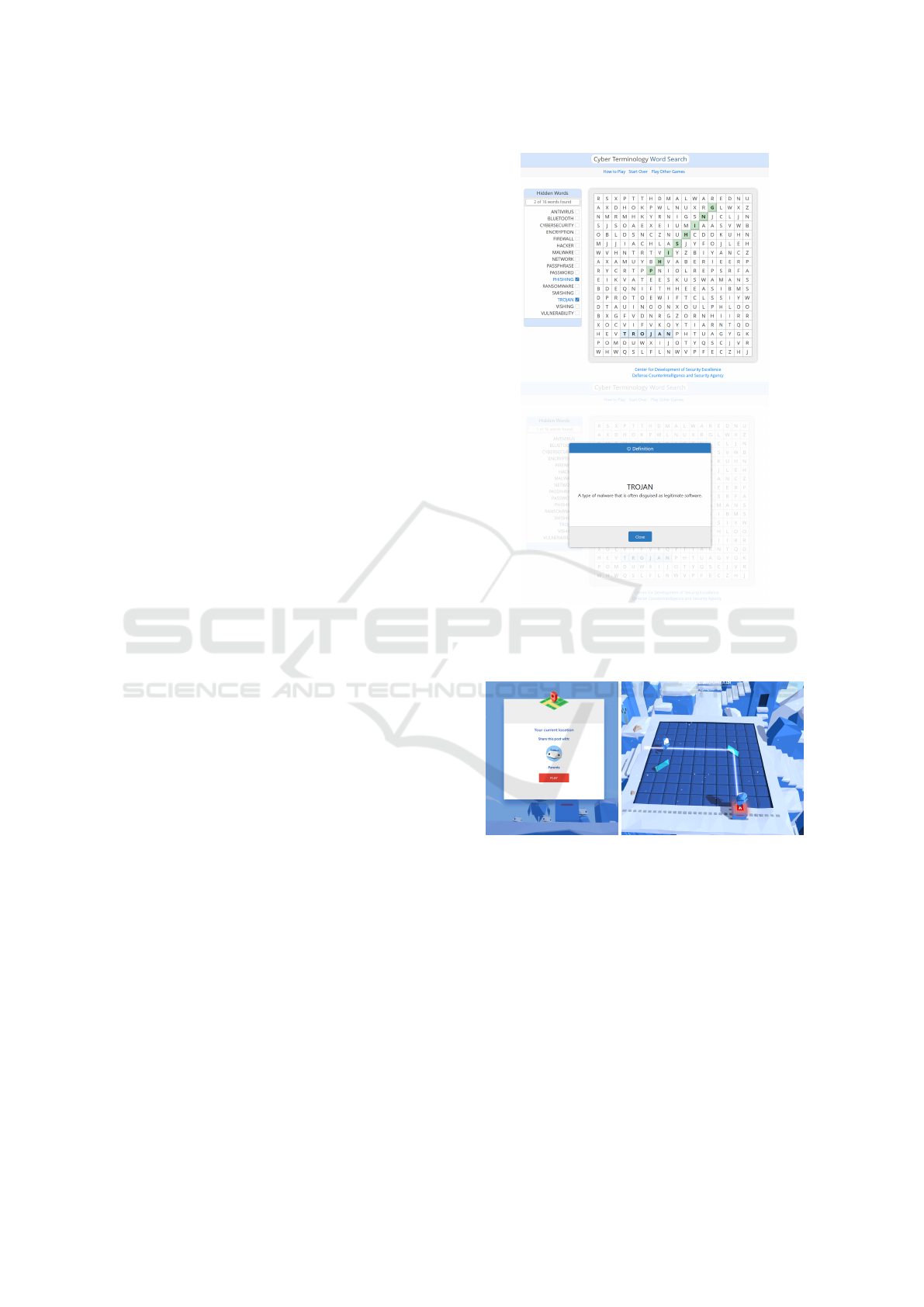
The Center for Development of Security Ex-
cellence offers several crosswords and word searches
related to cybersecurity (for Development of Secu-
rity Excellence, 2024). The information presented
is directed towards a more adult audience, and aims
to encourage companies to use these games as a re-
fresher for different cybersecurity and internet safety
concepts. The word searches provide a definition of
the word when discovered. There are also a few inter-
active games centered around identifying workplace
vulnerabilities. The games require a lot of reading,
which can lower engagement for individuals even at
their target demographic. Additionally, they lack im-
mediate auditory feedback and provide little incentive
to play longer than a few minutes.
PBS NOVA Labs offers an interactive cybersecu-
rity game called the Cybersecurity Lab (Labs, 2022).
This game puts you into the role of a new mobile
app developer that just launched his application with-
out cybersecurity protocols in place. Now the player
is tasked with keeping all the information secure
by managing currency and working towards grow-
ing your business without compromising assets. The
game lacks audio feedback and requires completion
of a lengthy, non-interactive tutorial before getting
into the missions. The game also requires a large
amount of reading, which could lower user engage-
ment. Despite this, the material offered in this game
could be beneficial for students in a high school set-
ting, to teach them more complex topics relating to
application security while mixing in programming
knowledge.
Google’s Interland is an interactive, browser
based game meant to teach users about internet safety
while exploring different lands. Each area showcases
Figure 2: Cybersecurity Word searches allow players to
learn and understand different definitions when terms are
discovered.
Figure 3: Google’s Interlands teaches privacy safety
through this interactive mirror-based puzzle game. Players
are given a category of people that is allowed to have this
data and must only share it with them.
a different topic to discuss, such as when and how to
share data, who to identify fake information, and how
to practice proper password safety (Interland, 2024).
The concepts shown are abstracted and shown in a
way that is simple to understand and easy to perform,
with plenty of opportunities to take breaks and learn
from mistakes. Each section focuses on a specific area
and allows for a high level of interactivity. All of the
instructions are shown visually through text, as well
as through voice over.
Gameplay varies from selecting the most secure
ERSeGEL 2025 - Workshop on Extended Reality and Serious Games for Education and Learning
826

Figure 4: Cyber Sprinters provides quizzes in the form of
yes or no questions to educate players on cybersecurity con-
cepts.
password from a list, to mirror-based logic puzzles
and endless runners. Overall, this interactive website
offers a really engaging experience for young learn-
ers, and could benefit from being expanded into more
complex topics. Each section ends with a quiz in or-
der to assess the player’s knowledge gained from the
session. Points are awarded based on how well the
user performs and are encouraged to get as high a
score as possible. The game lacks a social and collab-
orative element to it, so users are not encouraged to
replay after they are finished, but this material could
be used as a refresher if topics are forgotten.
Cyber Sprinters, a game developed by the UK
National Cyber Security Center, aims to teach learn-
ers about different cybersecurity topics by avoiding
obstacles in the form of hackers and trojans (Cen-
tre, 2024). Players can also encounter bonus tokens.
When collected, they prompt the user to answer a yes-
or-no quiz question relating to any number of cyber-
security situations. Players are then given extra de-
tails when answering correctly, and provided guide-
lines on how to protect themselves from real-world
scenarios. Additionally, users encounter major threats
in the game that require minigames to defeat. These
minigames range from creating strong passwords to
ensuring devices are updated regularly. The informa-
tion within this game is text-heavy but is informa-
tive and engaging for short gameplay sessions. The
game is fun and interactive, but none of the actions al-
low players to actively practice techniques that would
be performed in real-world situations. Many of the
questions only offer two answers, allowing players to
guess if they are not paying full attention to what is
being asked of them. Despite this, the material of-
fers a simple and engaging way to get introduced to
cybersecurity topics.
Cyber Games UK offers a short, interactive game
called Password Strength Meter on their website (UK,
2023). This game asks you to create a variety of
passwords at different strengths while showing you
what makes a password successful. This short expe-
rience gives players the freedom to practice creating
their own password while seeing the points awarded
for good password choices. The real-time feedback
of this game while writing passwords easily helps
players understand how to improve creating their own
passwords, while giving them the creativity to exper-
iment and play with different combinations. Despite
its simplicity, this game can give young learners a firm
understanding of secure password generation while
maintaining a level of creative freedom.
noindent Summary of Pros and Cons of Passive
and Active Learning. Passive learning offers a struc-
tured and comprehensive way to introduce cybersecu-
rity concepts to young learners, making it easier to de-
liver dense information efficiently. Videos and read-
ings provide a simple and accessible format, allowing
students to learn at their own pace. However, the lack
of interactivity in passive learning can reduce engage-
ment and retention, especially for children who ben-
efit from hands-on experiences. Additionally, these
methods do not provide opportunities for students to
actively apply what they have learned, making it diffi-
cult to reinforce cybersecurity concepts in real-world
contexts. Another limitation is the minimal assess-
ment and feedback, leaving educators and parents un-
certain about how much students have truly absorbed.
In contrast, active learning engages students
through interactive activities, games, and simulations
that encourage critical thinking and problem-solving.
By allowing learners to apply their knowledge in
dynamic ways, active learning improves retention
and helps students understand complex cybersecurity
principles through experience. Immediate feedback
and gamification elements can also make learning
more enjoyable and motivating. However, some inter-
active activities may oversimplify real-world cyber-
security challenges, and the time investment required
for these methods can be greater than passive alter-
natives. Furthermore, some games may lack social
or collaborative elements, limiting their long-term en-
gagement, while text-heavy formats or lengthy tutori-
als may discourage younger audiences from fully par-
ticipating.
While both passive and active learning methods
have their strengths and weaknesses, there is a press-
ing need for fundamental research to better under-
stand their impact on young learners. More stud-
ies are required to examine how each approach in-
fluences knowledge retention, engagement, and skill
development in cybersecurity education. Addition-
ally, research can help determine the most effec-
tive way to balance passive and active methods, en-
suring that young audiences receive a well-rounded
Cybersecurity Early Education: A Review of Current Cybersecurity Education for Young Children
827

Figure 5: 2D point-and-click game that encourages learners to develop their password safety skills through cooking. Their
password strength will be assessed throughout different levels of the game.
and impactful learning experience. By exploring
the best ways to integrate these strategies, educators
and researchers can develop optimized approaches
that maximize both engagement and educational out-
comes.
4 CyberFortress ACADEMY
Cybersecurity awareness will be used to teach chil-
dren safety skills and promote critical thinking in fun
and engaging ways. The goal of our technology is
to teach children how to protect their passwords and
personal information, how to recognize scams, phish-
ing attempts, and cyberbullying, and teach them the
role of trusted adults (parents/teachers) to keep their
devices safe. Our approach ensures that cybersecu-
rity education is age-appropriate, engaging, and im-
pactful, giving children the foundation they need to
be safe and responsible digital citizens. To ensure
that students are absorbing the material effectively,
we will implement regular assessments and simulated
digital attacks. This approach not only makes cyber-
security education accessible and engaging but also
lays a strong foundation for children to become safe
and responsible digital citizens.
We are actively building CyberFortress Academy,
a browser-based game platform designed to pro-
vide grades 2-5 students with essential cybersecu-
rity knowledge, skills, and abilities through engag-
ing, age-appropriate activities. Our technology cur-
rently includes 10 proof-of-concept games covering
topics like two-factor authentication (2FA), strong
password creation, social engineering, phishing, en-
cryption, and malware injections.
The platform will serve as an engaging and im-
mersive learning environment for students. The plat-
form will be designed to allow the collection and stor-
age of relevant data, enabling educators and parents
to easily track student progress and performance. The
games will be integrated into a large, interactive map,
where each section represents a unique themed area.
Students will navigate this map as part of their learn-
ing journey, taking on the role of caretakers or explor-
ers within the virtual world. Each area of the map
will offer distinct challenges and objectives, encour-
aging students to engage with a variety of subjects or
skills. As students complete different modules within
the games, they will unlock rewards such as virtual
pets, tools, or resources that are specific to the map’s
area.
The modules themselves will be designed to
be both fun and educational, combining problem-
solving, critical thinking, and subject-specific skills.
Each area of the map will have a unique focus. To
further enhance engagement, students will have the
opportunity to personalize their pets, tools, and areas
of the map, making the experience uniquely theirs.
Collaboration can also be incorporated by allowing
students to team up to unlock special regions or solve
larger challenges. The end result will not just be a
completed website but a dynamic, evolving platform
that grows with students’ progress, creativity, and en-
gagement.
Our games have been functionally tested by adult
volunteers, and we are continuously working to en-
hance their design and performance. Currently, we
are refining the knowledge assessment components
to measure how effectively the games convey cyber-
security concepts. The first round of testing will
use only three Cybersecurity games (Password Chef,
Two-Step Treasure, and Pelican Phishing) involving
second and third-grade students to ensure the con-
tent is age-appropriate and user-friendly. During this
initial phase, students will engage with the games
and training modules to develop their cybersecurity
knowledge. Following this, they will take on a grand
challenge designed to evaluate their ability to apply
what they have learned through interactive activities.
Password Chef is an educational, 2D point-and-
click game that encourages users to develop their
password safety skills through cooking (Figure 5).
Users are tasked with creating passwords using spe-
cific criteria that get more complex over time by cre-
ating unique recipes. Ingredients are labeled with
different alphanumeric characters and symbols, with
vegetables having the ability to be chopped in order
to make letters lowercase. Other items, such as meats
and spices, serve as both numbers and special char-
ERSeGEL 2025 - Workshop on Extended Reality and Serious Games for Education and Learning
828

Figure 6: Images a-c show how one-step authentication that learners will go through. Learners will practice the one-step
authentication, and then, they will be introduced to two-step authentication - images d-h. There are assessment phases in-
between different phases.
acters, respectively. Users are encouraged to create
long passwords, as that makes it harder for individu-
als to guess the exact combination used. Players in-
teract with the game through simple touch controls,
giving them the ability to drag and drop items onto
different areas of the screen to add them to their pass-
word. This allows players unfamiliar with games to
feel confident in their ability to participate.
Players are encouraged to create recipes that they
can recall and keep secret, as narratively, it is impor-
tant to prevent other chefs from guessing what they
used. After players complete a tutorial explaining
ways to make a secure password, they are given chal-
lenges to complete. These challenges range from us-
ing a specific character to creating a password with
a minimum number of letters and symbols. When
ready, a judge awards points to the dish based on the
length, variability of the characters, and whether or
not the challenge goal was met.
After a set number of challenges are completed,
users are asked to recall one of them at random. This
helps reiterate the need to remember these passwords
so they are not forgotten later. Password Chef aims
to assess players in their ability to create and recall
strong passwords using length, character variability,
and knowledge while maintaining secrecy. The player
should feel excited and empowered when finishing
the game, as the focus is on rewarding successes
rather than delivering harsh punishments for lacking
knowledge.
Two-Step Treasures is a 2D point-and-click
game designed to introduce players to the concept
of two-factor authentication (Figure 6). This game
requires players to create a password from simple
shapes, symbols, and colors and recall them to open
treasure chests. After this knowledge is established,
users are introduced to two-factor authentication con-
cepts by requiring not only the initial password, but a
secondary password on another device to fully unlock
the new treasure chest.
Players are shown a collection of keys that contain
a variety of different symbols on them. Players are
then expected to choose the correct key to unlock the
treasure in front of them. After this, the game asks the
user to try and guess another individual’s password
and unlock their chest. This aims to introduce the
idea that passwords are easy to bypass without proof
of identity, showing that two-factor authentication can
be one way to make access more secure. This intro-
duces the second stage of gameplay, where users put
in their own password key but are then shown a cell-
phone that requires a secondary form of identification
to open, showing another level of security, before a
second set of keys is generated in the play area (Fig-
ure 6.f). The player simply has to unlock their device,
read the number shown on their phone screen, and
find the respective key to open the chest (Figure 6.g).
This game has no time restriction or consequence
for guessing incorrectly, as this game aims to intro-
duce the concept of two-factor authentication in an
easy to understand format. The game allows for more
complexity by adding multiple checks, having users
attempt to guess passwords without access to two-
factor authentication, and similar methods to show
how easy it is to protect yourself when using multi-
ple forms of password safety.
Pelican Phishing is an educational game focused
on teaching and enforcing concepts of identifying
phishing attempts (Figure 7). The game does this by
showing the player multiple text-based interactions
that could or could not be phishing. This game is
a 2d style game. The goal of the game is to teach
Cybersecurity Early Education: A Review of Current Cybersecurity Education for Young Children
829

Figure 7: This game will be based on a simple text pop-up scene. Each pop-up is the text the player needs to review. The
player will accept or deny communication with each pop-up. The pop-ups will vary in context and style to challenge the
players understanding of phishing. The goal of the player is to not respond to phishing attempts.
the player simple concepts of phishing attempts in
a fun and interactive way. In the Pelican Phishing
game, the player’s goal is to analyze text-based in-
teractions and pop-ups and decide whether or not the
presented scenarios are safe or potential phishing at-
tempts. Through this gameplay, we aim to educate
players in a fun and engaging way about the danger-
ous tactics used by phishers and scammers, as well as
how to identify suspicious online behaviors in order
to avoid them.
The game will focus on players who have zero to
minimal internet or online social interactions but have
some initial gaming experience. Pelican Phishing
aims to provide a light introduction to essential cy-
bersecurity concepts. Through a right-to-left scrolling
mechanic, players will control a fish trying to “get to
work”, while a pelican overhead attempts to “catch”
them using phishing tactics. The player’s success
depends on correctly identifying and responding to
phishing attempts, allowing them to progress further
in their journey. The core mission of Pelican Phish-
ing is to empower young players with the informa-
tion and skills needed to protect themselves online by
recognizing suspicious links, understanding their data
privacy, and resisting social engineering. As players
advance through the game, the difficulty of the phish-
ing scenarios increases, allowing the players to apply
the lessons learned in the earlier stages to more com-
plex situations. This progression is designed to cre-
ate a sense of achievement and growth for the player
while reinforcing gameplay goals. The vision behind
Pelican Phishing is not only about making learning
about phishing fun but also building confidence in
users as they navigate and enter the digital world.
By making the game progressively challenging, play-
ers will feel both entertained and capable of applying
their new cybersecurity knowledge in real-world situ-
ations.
5 NEXT STEPS
We are currently conducting rigorous testing of three
of our cybersecurity games, detailed in section 4, by
implementing them in elementary school classrooms
with both students and teachers. We are collabo-
rating with three schools and will collect data from
four second-grade classes, three third-grade classes,
two fourth-grade classes, two fifth-grade classes, two
technology classes at two elementary schools, and the
Education Laboratory afterschool program at the Wat-
son College of Education at UNCW, targeting over
200 students. This hands-on testing process allows us
to gather valuable real-world feedback, helping us re-
fine the games to enhance engagement, usability, and
educational effectiveness. By observing how young
learners interact with the games and assessing teacher
feedback in the eight 30-session, we can make neces-
sary improvements to ensure the content is both age-
appropriate and impactful in teaching cybersecurity
concepts.
In addition to refining our existing games, we
are committed to expanding our efforts by devel-
oping more cybersecurity-focused educational tools.
This includes creating new interactive games, en-
gaging learning modules, and innovative assessment
methods designed to simplify complex cybersecurity
principles for young learners. Our goal is to make
cybersecurity education more accessible, enjoyable,
and effective by incorporating interactive elements
ERSeGEL 2025 - Workshop on Extended Reality and Serious Games for Education and Learning
830

that encourage critical thinking and problem-solving.
Through ongoing research, collaboration with edu-
cators, and iterative design improvements, we strive
to build a comprehensive suite of resources that em-
power children to navigate the digital world safely
and responsibly. The long-term goal for this project
is to develop a fully functional, browser-based plat-
form that integrates all the games and features a dy-
namic map for immersive gameplay. This platform
hosts a comprehensive curriculum aligned with ed-
ucational standards while fostering critical thinking
and problem-solving skills.
This project offers profound societal benefits by
addressing key gaps in cybersecurity education. This
project allows elementary school students to gain es-
sential knowledge to navigate the digital world safely,
reducing their vulnerability to cybercrimes like fraud,
scams, and identity theft. By building this founda-
tional knowledge, the initiative not only mitigates the
risks of online threats but also promotes digital inclu-
sion. This work enhances research in child-focused
cybersecurity education and effective teaching meth-
ods. A digitally literate population reduces inter-
net crimes and fraud while supporting workforce de-
velopment goals by inspiring students to pursue ca-
reers in cybersecurity, helping meet the growing de-
mand for skilled professionals. In 2022, there were
14,228,545 grades 2-5 public school students in the
US. This sizable audience highlights the potential for
a significant opportunity to make a meaningful local
and national impact by equipping young learners with
essential online safety skills and fostering responsible
digital behavior at an early age.
6 CONCLUSIONS
Cybersecurity education is essential in equipping
young learners with the knowledge and skills needed
to navigate the digital world safely and responsibly.
By reducing their vulnerability to online threats such
as fraud, scams, and identity theft, early cybersecu-
rity education fosters a generation of more informed
and cautious digital citizens. Additionally, promot-
ing cybersecurity awareness helps bridge the digital
divide, ensuring that underserved communities can
safely access online opportunities. Through the de-
velopment and refinement of engaging, interactive
games, we aim to make learning these critical con-
cepts both accessible and enjoyable. By combining
research-driven educational methods with hands-on
experiences, we strive to create a lasting impact, em-
powering children to build safe digital habits that will
benefit them throughout their lives.
REFERENCES
Aaron, J. M. (2017). Auditory, visual, kinesthetic-tactile,
and multi-sensory modalities: A quantitative study of
how preferred modalities create more effective teach-
ing and learning environments. Journal of Neuro-
science and Behavioral Health, 9(1):1–9.
Agamba, J. J. and Keengwe, J. (2012). Pre-service teachers’
perceptions of information assurance and cyber secu-
rity. International Journal of Information and Com-
munication Technology Education (IJICTE), 8(2):94–
101.
Alam, A. (2022). A digital game based learning approach
for effective curriculum transaction for teaching-
learning of artificial intelligence and machine learn-
ing. In 2022 International Conference on Sustain-
able Computing and Data Communication Systems
(ICSCDS), pages 69–74. IEEE.
Alsawaier, R. S. (2018). The effect of gamification on moti-
vation and engagement. The International Journal of
Information and Learning Technology, 35(1):56–79.
Annetta, L., Mangrum, J., Holmes, S., Collazo, K., and
Cheng, M.-T. (2009). Bridging realty to virtual re-
ality: Investigating gender effect and student engage-
ment on learning through video game play in an el-
ementary school classroom. International Journal of
Science Education, 31(8):1091–1113.
Behnamnia, N., Kamsin, A., Ismail, M. A. B., and Hay-
ati, A. (2020). The effective components of creativity
in digital game-based learning among young children:
A case study. Children and Youth Services Review,
116:105227.
Belland, B. R., Ertmer, P. A., and Simons, K. D. (2006).
Perceptions of the value of problem-based learning
among students with special needs and their teachers.
Interdisciplinary Journal of Problem-Based Learning,
1(2):1–18.
Boaler, J. (1997). Setting, social class and survival of
the quickest. British educational research journal,
23(5):575–595.
Brown, J. S., Collins, A., and Duguid, P. (1989). Situated
cognition and the culture of learning. Educational re-
searcher, 18(1):32–42.
Brush, T. and Saye, J. (2000). Implementation and eval-
uation of a student-centered learning unit: A case
study. Educational technology research and develop-
ment, 48(3):79–100.
Brush, T. and Saye, J. (2008). The effects of multimedia-
supported problem-based inquiry on student engage-
ment, empathy, and assumptions about history. In-
terdisciplinary Journal of Problem-Based Learning,
2(1):21–56.
Buckley, P. and Doyle, E. (2016). Gamification and stu-
dent motivation. Interactive learning environments,
24(6):1162–1175.
Centre, T. N. C. S. (2024). Cyber sprinter.
Chapman, J. R. and Rich, P. J. (2018). Does educational
gamification improve students’ motivation? if so,
which game elements work best? Journal of Edu-
cation for Business, 93(7):315–322.
Cybersecurity Early Education: A Review of Current Cybersecurity Education for Young Children
831

Charette, R. N. (2015). Stem sense and nonsense. Educa-
tional Leadership, 72(4):79–83.
Christou, C. (2010). Virtual reality in education. In Affec-
tive, interactive and cognitive methods for e-learning
design: creating an optimal education experience,
pages 228–243. IGI Global.
Darling-Hammond, L., Barron, B., Pearson, P. D., Schoen-
feld, A. H., Stage, E. K., Zimmerman, T. D., Cervetti,
G. N., and Tilson, J. L. (2015). Powerful learning:
What we know about teaching for understanding. John
Wiley & Sons.
de Marcos, L., Garcia-Lopez, E., and Garcia-Cabot, A.
(2016). On the effectiveness of game-like and social
approaches in learning: Comparing educational gam-
ing, gamification & social networking. Computers &
Education, 95:99–113.
Dewey, J. (2004). Democracy and education. Courier Cor-
poration.
Downing, J. A., Bakken, J. P., and Whedon, C. K.
(2002). Teaching text structure to improve reading
comprehension. Intervention in School and Clinic,
37(4):229–233.
English, L. D. (2016). Stem education k-12: Perspectives
on integration. International Journal of STEM educa-
tion, 3(1):3.
Ertmer, P. A., Conklin, D., Lewandowski, J., Osika, E.,
Selo, M., and Wignall, E. (2003). Increasing pre-
service teachers’ capacity for technology integration
through the use of electronic models. Teacher Educa-
tion Quarterly, 30(1):95–112.
Ertmer, P. A. and Simons, K. D. (2006). Jumping the pbl
implementation hurdle: Supporting the efforts of k–12
teachers. Interdisciplinary Journal of Problem-based
learning, 1(1):40–54.
for Development of Security Excellence, C. (2024). Secu-
rity awareness games.
from BYJU’S, T. (2024). Cybersecurity - all about comput-
ers.
Giannakas, F., Papasalouros, A., Kambourakis, G., and
Gritzalis, S. (2019). A comprehensive cybersecu-
rity learning platform for elementary education. In-
formation Security Journal: A Global Perspective,
28(3):81–106.
Grant, M. M. (2002). Getting a grip on project-based learn-
ing: Theory, cases and recommendations. Merid-
ian: A middle school computer technologies journal,
5(1):83.
Han, I. (2020). Immersive virtual field trips in education:
A mixed-methods study on elementary students’ pres-
ence and perceived learning. British Journal of Edu-
cational Technology, 51(2):420–435.
Hew, K. F. and Cheung, W. S. (2010). Use of three-
dimensional (3-d) immersive virtual worlds in k-12
and higher education settings: A review of the re-
search. British journal of educational technology,
41(1):33–55.
Hopkins, S., Forgasz, H., Corrigan, D., and Panizzon, D.
(2014). The stem issue in australia: What it is and
where is the evidence. In STEM Conference. Vancou-
ver, Canada (http://stem2014. ubc. ca).
Hsieh, P., Cho, Y., Liu, M., and Schallert, D. L. (2008).
Examining the interplay between middle school
students’ achievement goals and self-efficacy in a
technology-enhanced learning environment. Ameri-
can Secondary Education, 36(3):33–50.
Influence Central (2016). Smartphones & the dramatic
reshaping of american families. http://blog.influence-
central.com/smartphones-the-dramatic-reshaping-of-
american-families/.
Interland, G. (2024). Interland.
Janson, A., Sollner, M., and Leimeister, J. M. (2020). Lad-
ders for learning: is scaffolding the key to teach-
ing problem-solving in technology-mediated learning
contexts? Academy of Management Learning & Edu-
cation, 19(4):439–468.
Javidi, G. (1999). Virtual reality and education.
Jethwani, M., Memon, N., Richer, A., and Seo, W. (2016).
It’s hard to be the only girl. In Journal of The Col-
loquium for Information System Security Education,
volume 4, pages 16–16.
Jethwani, M. M., Memon, N., Seo, W., and Richer, A.
(2017). “i can actually be a super sleuth” promising
practices for engaging adolescent girls in cybersecu-
rity education. Journal of Educational Computing Re-
search, 55(1):3–25.
Jonassen, D. H. (2011). Design problems for secondary
students. National Center for Engineering and Tech-
nology Education.
Keeley, B. and Little, C. (2017). The State of the Worlds
Children 2017: Children in a Digital World. ERIC.
Kim, S., Song, K., Lockee, B., and Burton, J. (2018).
What is gamification in learning and education? In
Gamification in learning and education, pages 25–38.
Springer.
Krajcik, J., Codere, S., Dahsah, C., Bayer, R., and Mun, K.
(2014). Planning instruction to meet the intent of the
next generation science standards. Journal of Science
Teacher Education, 25(2):157–175.
Labs, P. N. (2022). Corporation battle network.
Lamrani, R. and Abdelwahed, E. H. (2020). Game-based
learning and gamification to improve skills in early
years education. Computer Science and Information
Systems, 17(1):339–356.
Malwarebytes (2021). Cybersecurity training for kids.
Mao, W., Cui, Y., Chiu, M. M., and Lei, H. (2022). Effects
of game-based learning on students’ critical thinking:
A meta-analysis. Journal of Educational Computing
Research, 59(8):1682–1708.
Margolis, J. and Fisher, A. (2002). Unlocking the club-
house: Women in computing. MIT press.
McGinnis, J. R. and Stefanich, G. P. (2007). Special needs
and talents in science learning. Handbook of research
on science education, pages 287–317.
Merchant, Z., Goetz, E. T., Cifuentes, L., Keeney-
Kennicutt, W., and Davis, T. J. (2014). Effectiveness
of virtual reality-based instruction on students’ learn-
ing outcomes in k-12 and higher education: A meta-
analysis. Computers & Education, 70:29–40.
ERSeGEL 2025 - Workshop on Extended Reality and Serious Games for Education and Learning
832

Mergendoller, J. R., Maxwell, N. L., and Bellisimo, Y.
(2006). The effectiveness of problem-based instruc-
tion: A comparative study of instructional methods
and student characteristics. Interdisciplinary Journal
of Problem-based Learning, 1(2):49–69.
Mergendoller, J. R. and Thomas, J. W. (2005). Managing
project based learning: Principles from the field. Re-
trieved June, 14:2005.
Micro, T. (2022). Trend micro cyber academy.
Mole, L. (2024). Why is it important to create strong pass-
words?
Moon, N. W., Todd, R. L., Morton, D. L., and Ivey, E.
(2012). Accommodating students with disabilities
in science, technology, engineering, and mathematics
(stem). Atlanta, GA: Center for Assistive Technology
and Environmental Access, Georgia Institute of Tech-
nology, pages 8–21.
Murtazaev, M. and Shukrulloev, B. (2024). Unusual meth-
ods of teaching mathematics to elementary school stu-
dents. NRJ, 1(3):929–940.
National Science Foundation (2020). Cybersecurity
education in the age of artificial intelligence.
https://www.nsf.gov/pubs/2020/nsf20072/nsf20072.jsp.
Norman, K., Caseau, D., and Stefanich, G. P. (1998).
Teaching students with disabilities in inclusive sci-
ence classrooms: Survey results. Science Education,
82(2):127–146.
on STEM Education, C. (2018). Charting a course for suc-
cess: America’s strategy for stem education. National
Science and Technology Council, pages 1–48.
Ortiz-Rojas, M., Chiluiza, K., and Valcke, M. (2019). Gam-
ification through leaderboards: An empirical study in
engineering education. Computer Applications in En-
gineering Education, 27(4):777–788.
Penuel, W. R. (2006). Implementation and effects of
one-to-one computing initiatives: A research synthe-
sis. Journal of research on technology in education,
38(3):329–348.
Potkonjak, V., Gardner, M., Callaghan, V., Mattila, P.,
Guetl, C., Petrovi
´
c, V. M., and Jovanovi
´
c, K. (2016).
Virtual laboratories for education in science, technol-
ogy, and engineering: A review. Computers & Educa-
tion, 95:309–327.
Proserpio, L. and Gioia, D. A. (2007). Teaching the vir-
tual generation. Academy of Management Learning &
Education, 6(1):69–80.
Putnam, R. T. and Borko, H. (2000). What do new views of
knowledge and thinking have to say about research on
teacher learning? Educational researcher, 29(1):4–
15.
Putz, L.-M., Hofbauer, F., and Treiblmaier, H. (2020). Can
gamification help to improve education? findings
from a longitudinal study. Computers in Human Be-
havior, page 106392.
Quayyum, F., Cruzes, D. S., and Jaccheri, L. (2021). Cyber-
security awareness for children: A systematic litera-
ture review. International Journal of Child-Computer
Interaction, 30:100343.
Ravitz, J. (2009). Introduction: Summarizing findings and
looking ahead to a new generation of pbl research.
Interdisciplinary Journal of Problem-based Learning,
3(1):4–11.
Rhodewalt, F. and Tragakis, M. (2002). Self-handicapping
and the social self: The costs and rewards of interper-
sonal self-construction. The social self: Cognitive, in-
terpersonal, and intergroup perspectives, pages 121–
143.
Roussou, M. (2004). Learning by doing and learning
through play: an exploration of interactivity in virtual
environments for children. Computers in Entertain-
ment (CIE), 2(1):10–10.
Scoville, S. A. and Buskirk, T. D. (2007). Traditional
and virtual microscopy compared experimentally in
a classroom setting. Clinical Anatomy: The Offi-
cial Journal of the American Association of Clini-
cal Anatomists and the British Association of Clinical
Anatomists, 20(5):565–570.
Scruggs, T. E. and Mastropieri, M. A. (1994a). The con-
struction of scientific knowledge by students with
mild disabilities. The journal of special education,
28(3):307–321.
Scruggs, T. E. and Mastropieri, M. A. (1994b). Success-
ful mainstreaming in elementary science classes: A
qualitative study of three reputational cases. Ameri-
can Educational Research Journal, 31(4):785–811.
Scruggs, T. E., Mastropieri, M. A., Berkeley, S., and Graetz,
J. E. (2010). Do special education interventions im-
prove learning of secondary content? a meta-analysis.
Remedial and Special Education, 31(6):437–449.
Sim
˜
oes, J., Redondo, R. D., and Vilas, A. F. (2013). A social
gamification framework for a k-6 learning platform.
Computers in Human Behavior, 29(2):345–353.
Smile and learn (2021). Online privacy for kids - internet
safety and security for kids.
Tamim, S. R. and Grant, M. M. (2013). Definitions and
uses: Case study of teachers implementing project-
based learning. Interdisciplinary Journal of problem-
based learning, 7(2):3.
Thomas, J. W. (2000). A review of research on project-
based learning.
Trindade, J., Fiolhais, C., and Almeida, L. (2002). Sci-
ence learning in virtual environments: a descriptive
study. British Journal of Educational Technology,
33(4):471–488.
UK, C. G. (2023). Password strength meter.
Villanueva, M. G., Taylor, J., Therrien, W., and Hand, B.
(2012). Science education for students with special
needs. Studies in Science Education, 48(2):187–215.
Yannier, N., Hudson, S. E., Koedinger, K. R., Hirsh-
Pasek, K., Golinkoff, R. M., Munakata, Y., Doebel, S.,
Schwartz, D. L., Deslauriers, L., McCarty, L., et al.
(2021). Active learning:“hands-on” meets “minds-
on”. Science, 374(6563):26–30.
Zepf, I. and Arthur, L. (2013). Cyber-security curricula for
basic users. Technical report, NAVAL POSTGRAD-
UATE SCHOOL MONTEREY CA.
Cybersecurity Early Education: A Review of Current Cybersecurity Education for Young Children
833
